CA+https+动态WEB页面部署
一、CA 证书获取
- 生成服务器私钥及证书签名请求(CSR),CSR 包含域名、组织等信息
- 向可信 CA 提交 CSR,通过域名所有权验证后,获取 SSL 证书及中间证书
二、HTTPS 配置
- 将私钥、SSL 证书和中间证书存储在服务器指定目录
- 配置 Web 服务器(如 Nginx、Apache)启用 443 端口,关联证书文件,启用合适的 TLS 协议及加密套件
- 配置 HTTP(80 端口)请求自动跳转至 HTTPS,确保所有流量加密传输
- 验证配置并重启 Web 服务器使设置生效
三、动态 Web 页面部署
- 将动态页面程序(如基于 PHP、Python、Java 等开发的代码)部署到服务器指定目录,确保文件权限正确
- 配置 Web 服务器,将动态请求转发至对应的应用服务器(如 PHP-FPM、Tomcat、Node.js 服务)处理
- 启动应用服务器,确保其与 Web 服务器正常通信,能够处理动态内容生成、数据库交互等请求
案例:
CA服务器配置信息
[root@syf ~]# vim /etc/pki/tls/openssl.cnf 生成私钥:
[root@syf ~]# cd /etc/pki/CA
[root@syf CA]# ls
certs crl newcerts private
[root@syf CA]# ls certs/
[root@syf CA]# ls private/
[root@syf CA]# cd
[root@syf ~]# vim /var/named/ovo.com
...
ca IN A 192.168.100.10
...
[root@syf ~]# systemctl restart named
[root@syf ~]# (umask 077;openssl genrsa -out /etc/pki/CA/private/cakey.pem)
Generating RSA private key, 2048 bit long modulus
........................................................+++
.+++
e is 65537 (0x10001)私钥生成后,需要生成自签名证书
[root@syf ~]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -out /etc/pki/CA/cacert.pem -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:LQ
Organizational Unit Name (eg, section) []:linux
Common Name (eg, your name or your server's hostname) []:ca.example.com
Email Address []:root@example.com
[root@syf ~]# cd /etc/pki/CA/
[root@syf CA]# ls
cacert.pem certs crl newcerts private
[root@syf CA]# touch index.txt
[root@syf CA]# echo 01 > serial
[root@syf CA]# ls
cacert.pem certs crl index.txt newcerts private serial配置Web服务器:
[root@syf2 ~]# vim /etc/sysconfig/network-scripts/ifcfg-ens33
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=none
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens33
UUID=b3c12754-7b61-4487-993b-48f8f9b9b5e8
DEVICE=ens33
ONBOOT=yes
IPADDR=192.168.100.20
PREFIX=24
IPADDR1=192.168.100.200
PREFIX1=24
GATEWAY=192.168.100.254
DNS1=192.168.100.10
IPV6_PRIVACY=no
[root@syf2 ~]# systemctl restart network
[root@syf2 ~]# nslookup ca.example.com
Server: 192.168.100.10
Address: 192.168.100.10#53
Name: ca.example.com
Address: 192.168.100.10
[root@syf2 ~]# cd /etc/httpd/
[root@syf2 httpd]# ls
conf conf.d conf.modules.d logs modules run
[root@syf2 httpd]# mkdir ssl
[root@syf2 httpd]# cd ssl/
[root@syf2 ssl]# (umask 077;openssl genrsa -out /etc/httpd/ssl/httpd.key)
Generating RSA private key, 2048 bit long modulus
.............................................................................................................+++
.....................................................................................+++
e is 65537 (0x10001)
[root@syf2 ssl]# openssl req -new -key /etc/httpd/ssl/httpd.key -out /etc/httpd/ssl/httpd.csr -days 365
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:LQ
Organizational Unit Name (eg, section) []:linux
Common Name (eg, your name or your server's hostname) []:syf2.example.com
Email Address []:root@example.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@syf2 ssl]# ls
httpd.csr httpd.key
[root@syf2 ssl]# scp httpd.csr root@ca.example.com:/etc/pki/CA/
The authenticity of host 'ca.example.com (192.168.100.10)' can't be established.
ECDSA key fingerprint is SHA256:UN0UZbtBfFQeLR3836aFd9k4cm9na95JOPqBnPk05VU.
ECDSA key fingerprint is MD5:20:05:39:25:84:f6:1b:bb:8b:b3:ed:b9:bf:96:99:ba.
Are you sure you want to continue connecting (yes/no)? YES^H^H
Warning: Permanently added 'ca.example.com' (ECDSA) to the list of known hosts.
root@ca.example.com's password:
Permission denied, please try again.
root@ca.example.com's password:
httpd.csr 100% 1037 368.7KB/s 00:00
[root@syf CA]# ls
cacert.pem crl index.txt private
certs httpd.csr newcerts serial
[root@syf CA]# openssl ca -in /etc/pki/CA/httpd.csr -out /etc/pki/CA/httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Aug 12 11:59:53 2025 GMT
Not After : Aug 12 11:59:53 2026 GMT
Subject:
countryName = CN
stateOrProvinceName = HB
organizationName = LQ
organizationalUnitName = linux
commonName = syf2.example.com
emailAddress = root@example.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
92:17:56:41:46:DD:A9:9E:52:0C:D6:02:08:F1:29:15:DB:69:13:24
X509v3 Authority Key Identifier:
keyid:EB:73:CF:E6:F6:CC:4B:C8:F0:2F:CD:D5:55:19:AC:C3:BE:B3:8B:AD
Certificate is to be certified until Aug 12 11:59:53 2026 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@syf CA]# ls
cacert.pem httpd.crt index.txt.attr private
certs httpd.csr index.txt.old serial
crl index.txt newcerts serial.old
[root@syf ~]# vim /var/named/ovo.com
$TTL 1D
@ IN SOA shenyifeng.example.com. root.example.com. (
2025081101 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS shenyifeng.example.com.
shenyifeng IN A 192.168.100.10
lisi IN A 192.168.100.10
ca IN A 192.168.100.10
syf2 IN A 192.168.100.20 //写入syf2
[root@syf ~]# systemctl restart named
[root@syf CA]# vim /etc/sysconfig/network-scripts/ifcfg-ens33
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=none
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=ens33
UUID=676edb9b-16d3-4a22-8aa2-0394e6a68bf5
DEVICE=ens33
ONBOOT=yes
IPADDR=192.168.100.10
PREFIX=24
GATEWAY=192.168.100.254
DNS1=192.168.100.10
[root@syf CA]# systemctl restart network
[root@syf CA]# scp httpd.crt root@syf2.example.com:/etc/httpd/ssl/
The authenticity of host 'syf2.example.com (192.168.100.20)' can't be established.
ECDSA key fingerprint is SHA256:UN0UZbtBfFQeLR3836aFd9k4cm9na95JOPqBnPk05VU.
ECDSA key fingerprint is MD5:20:05:39:25:84:f6:1b:bb:8b:b3:ed:b9:bf:96:99:ba.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'syf2.example.com' (ECDSA) to the list of known hosts.
httpd.crt 100% 4571 2.8MB/s 00:00
[root@syf2 ssl]# ls
httpd.crt httpd.csr httpd.key
[root@syf2 ~]# yum -y install mod_ssl
Loaded plugins: fastestmirror, langpacks
Loading mirror speeds from cached hostfile
qvq | 3.6 kB 00:00
Resolving Dependencies
--> Running transaction check
---> Package mod_ssl.x86_64 1:2.4.6-88.el7.centos will be installed
--> Finished Dependency Resolution
Dependencies Resolved
====================================================================
Package Arch Version Repository
Size
====================================================================
Installing:
mod_ssl x86_64 1:2.4.6-88.el7.centos qvq 112 k
Transaction Summary
====================================================================
Install 1 Package
Total download size: 112 k
Installed size: 224 k
Downloading packages:
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : 1:mod_ssl-2.4.6-88.el7.centos.x86_64 1/1
Verifying : 1:mod_ssl-2.4.6-88.el7.centos.x86_64 1/1
Installed:
mod_ssl.x86_64 1:2.4.6-88.el7.centos
Complete!
[root@syf2 ~]# cd /etc/httpd/
[root@syf2 httpd]# ls
conf conf.d conf.modules.d logs modules run ssl
[root@syf2 httpd]# cd conf.d/
[root@syf2 conf.d]# ls
autoindex.conf README userdir.conf
httpd-vhosts.conf ssl.conf welcome.conf
[root@syf2 conf.d]# vim ssl.conf
...
SSLCertificateFile /etc/httpd/ssl/httpd.crt
...
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key
...
[root@syf2 conf.d]# ls
autoindex.conf README userdir.conf
httpd-vhosts.conf ssl.conf welcome.conf
[root@syf2 conf.d]# vim httpd-vhosts.conf
...
<VirtualHost 192.168.100.20:443>
DocumentRoot "/var/www/test"
ServerName syf2.example.com
SSLEngine on
SSLCertificateFile /etc/httpd/ssl/httpd.crt
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key
</VirtualHost>
[root@syf2 conf.d]# systemctl restart httpd
[root@syf3 ~]# nslookup syf2.example.com
Server: 192.168.100.10
Address: 192.168.100.10#53
Name: syf2.example.com
Address: 192.168.100.20
[root@syf3 ~]# scp root@192.168.100.10:/etc/pki/CA/cacert.pem .
The authenticity of host '192.168.100.10 (192.168.100.10)' can't be established.
ECDSA key fingerprint is SHA256:UN0UZbtBfFQeLR3836aFd9k4cm9na95JOPqBnPk05VU.
ECDSA key fingerprint is MD5:20:05:39:25:84:f6:1b:bb:8b:b3:ed:b9:bf:96:99:ba.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.100.10' (ECDSA) to the list of known hosts.
root@192.168.100.10's password:
cacert.pem 100% 1383 448.7KB/s 00:00
[root@syf3 ~]# ls
anaconda-ks.cfg Desktop Downloads Music Public Videos
cacert.pem Documents initial-setup-ks.cfg Pictures Templates点击浏览器
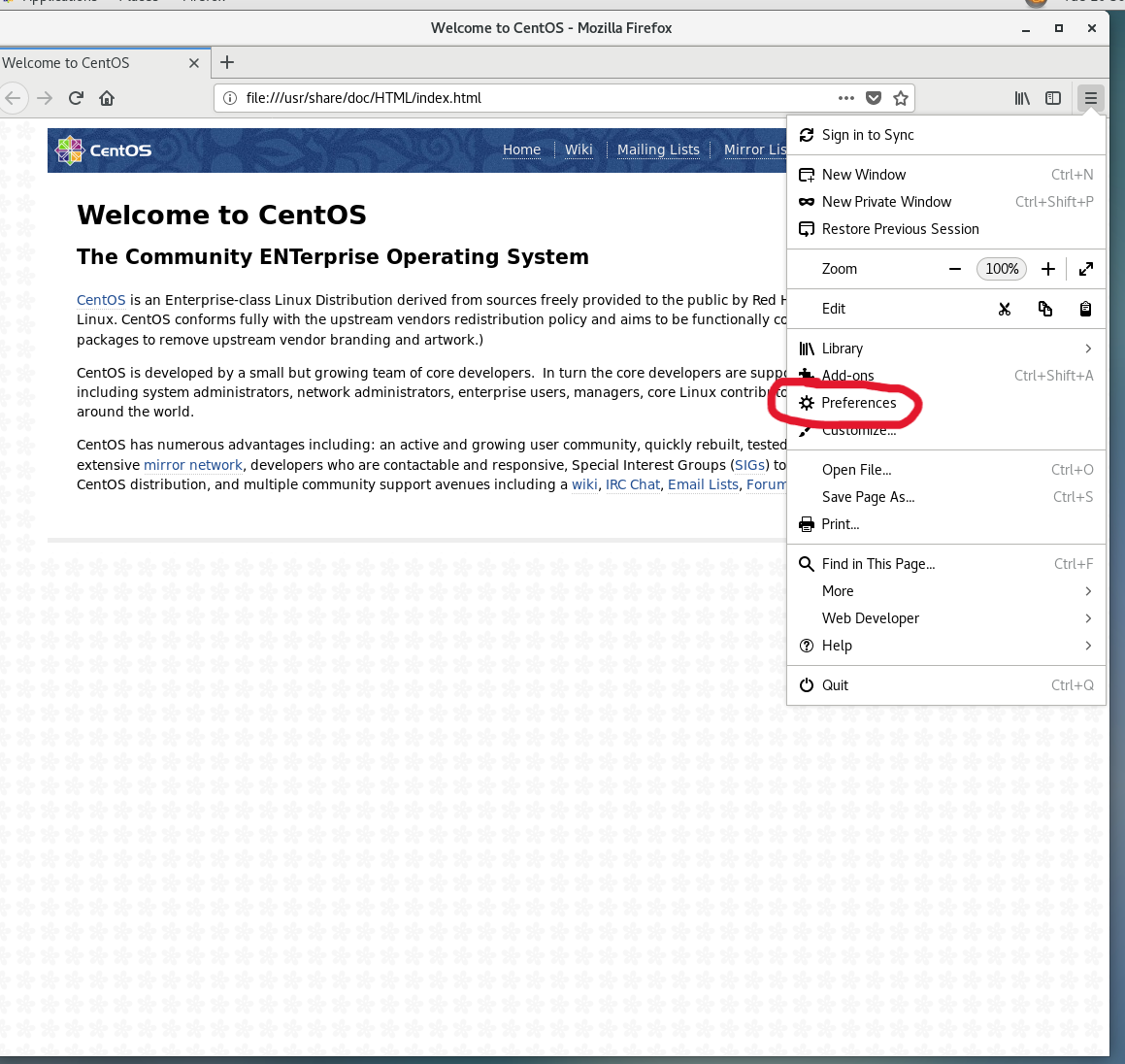
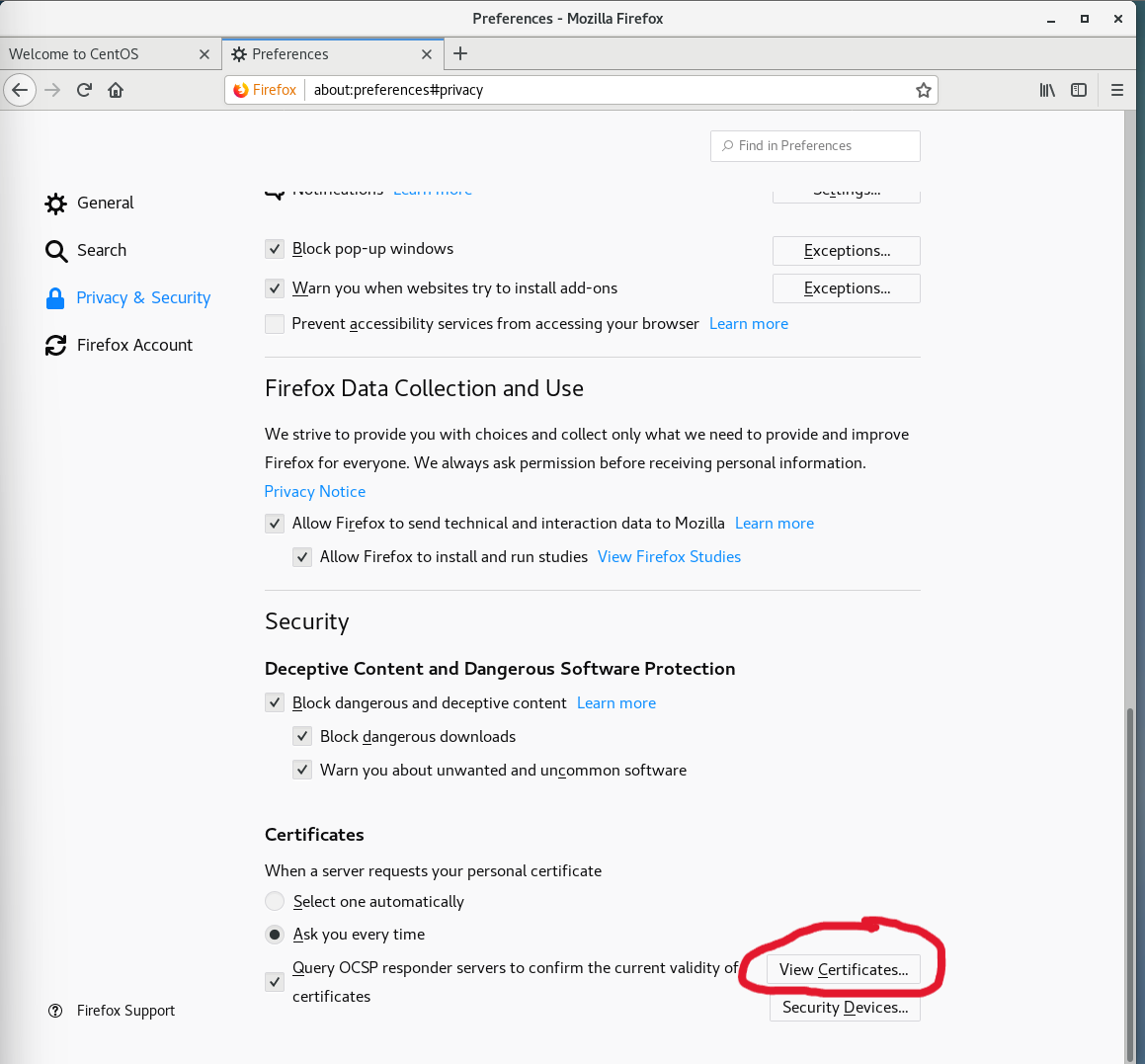
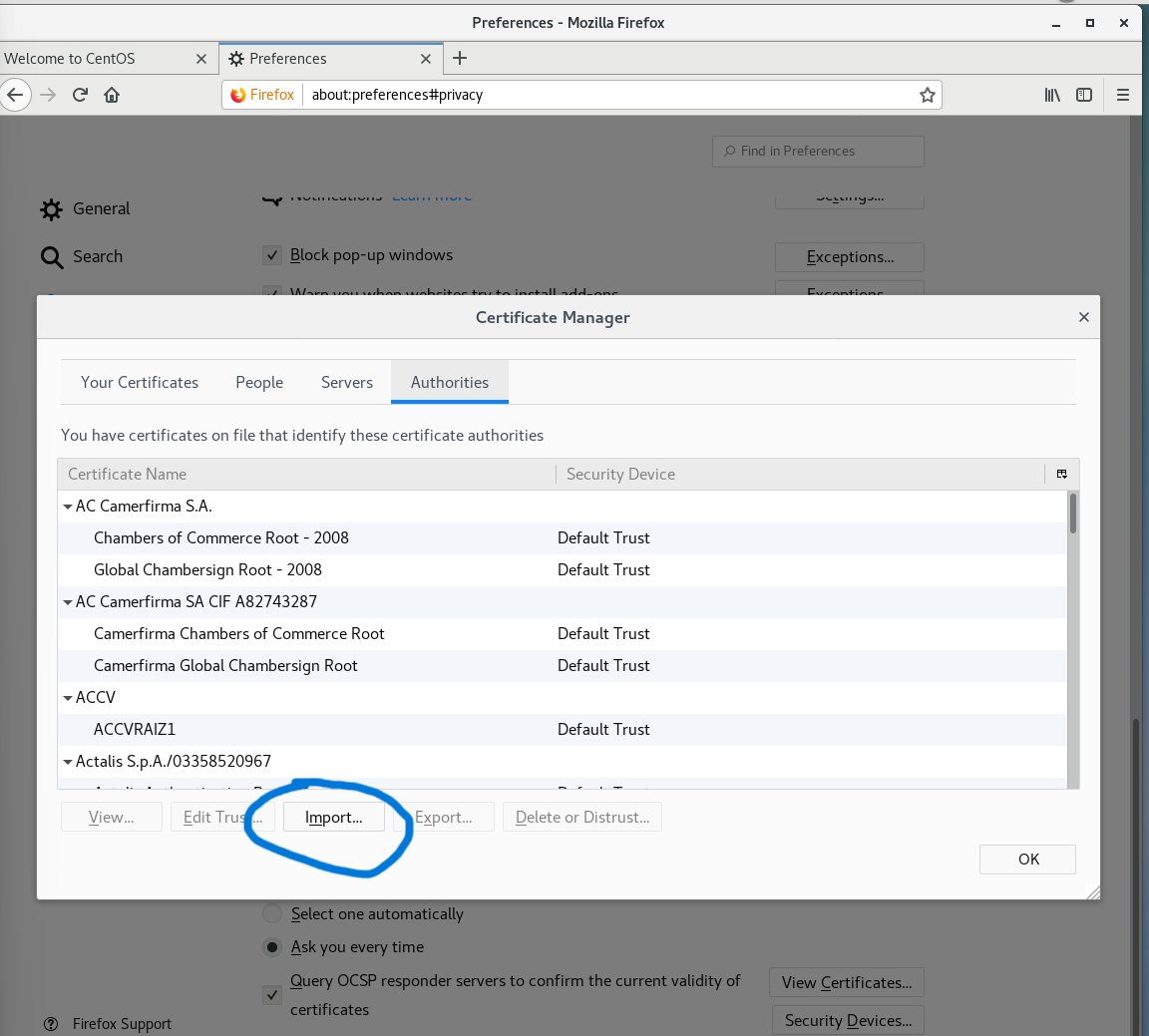
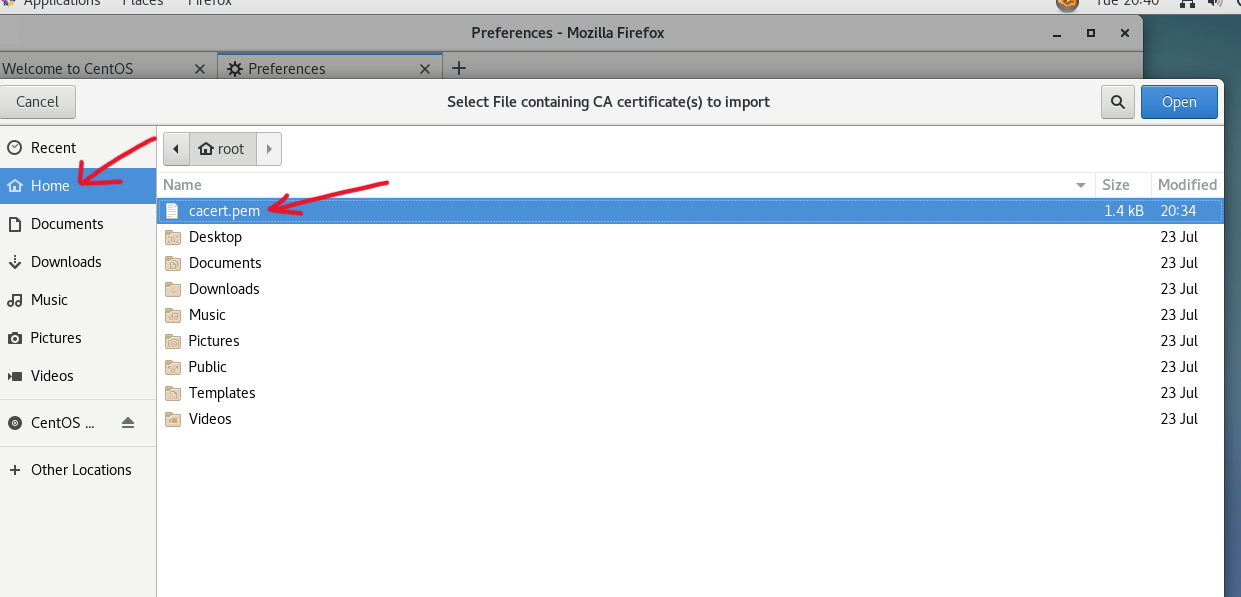
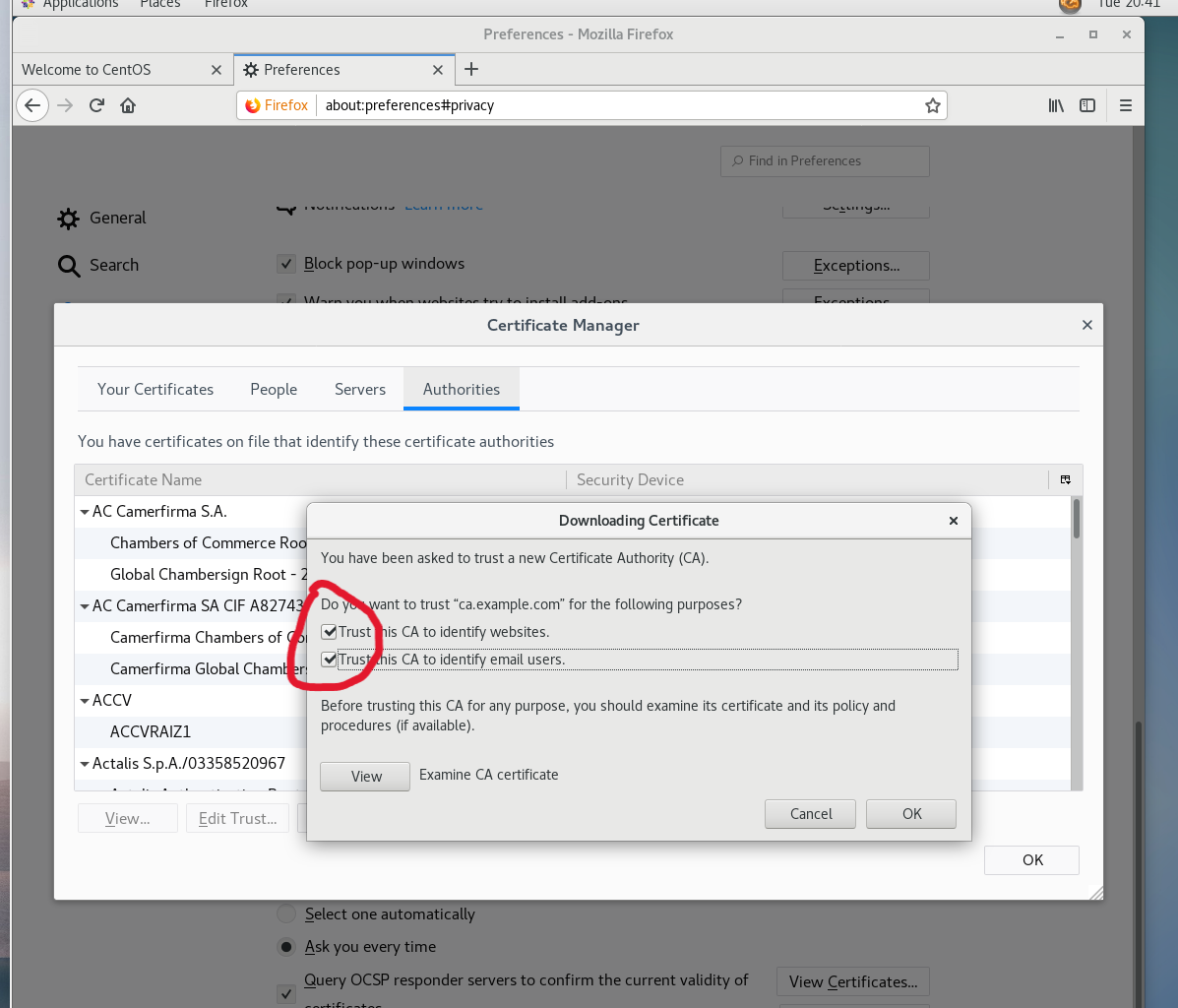
勾选,OK
[root@syf2 conf.d]# cd /var/www/
[root@syf2 www]# ls
cgi-bin html qvq syf
[root@syf2 www]# mkdir test
[root@syf2 www]# cd test/
[root@syf2 test]# echo 123456 > index.html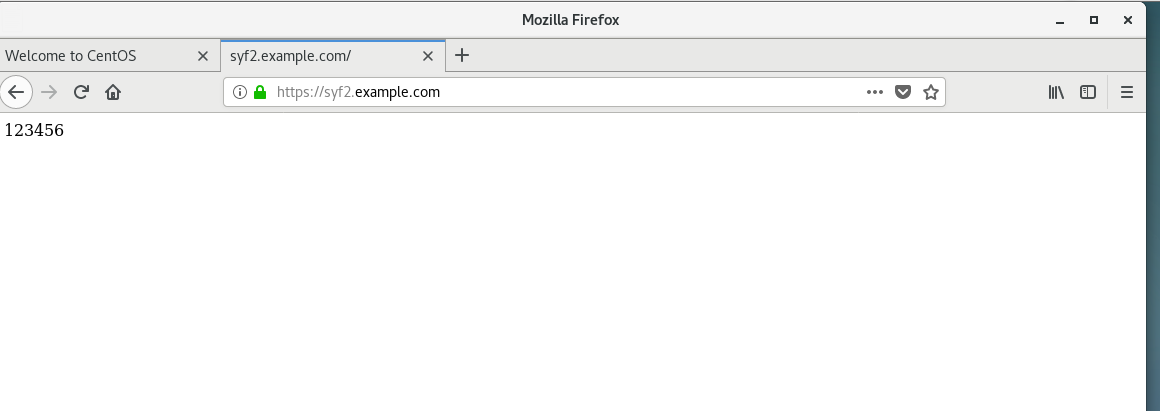
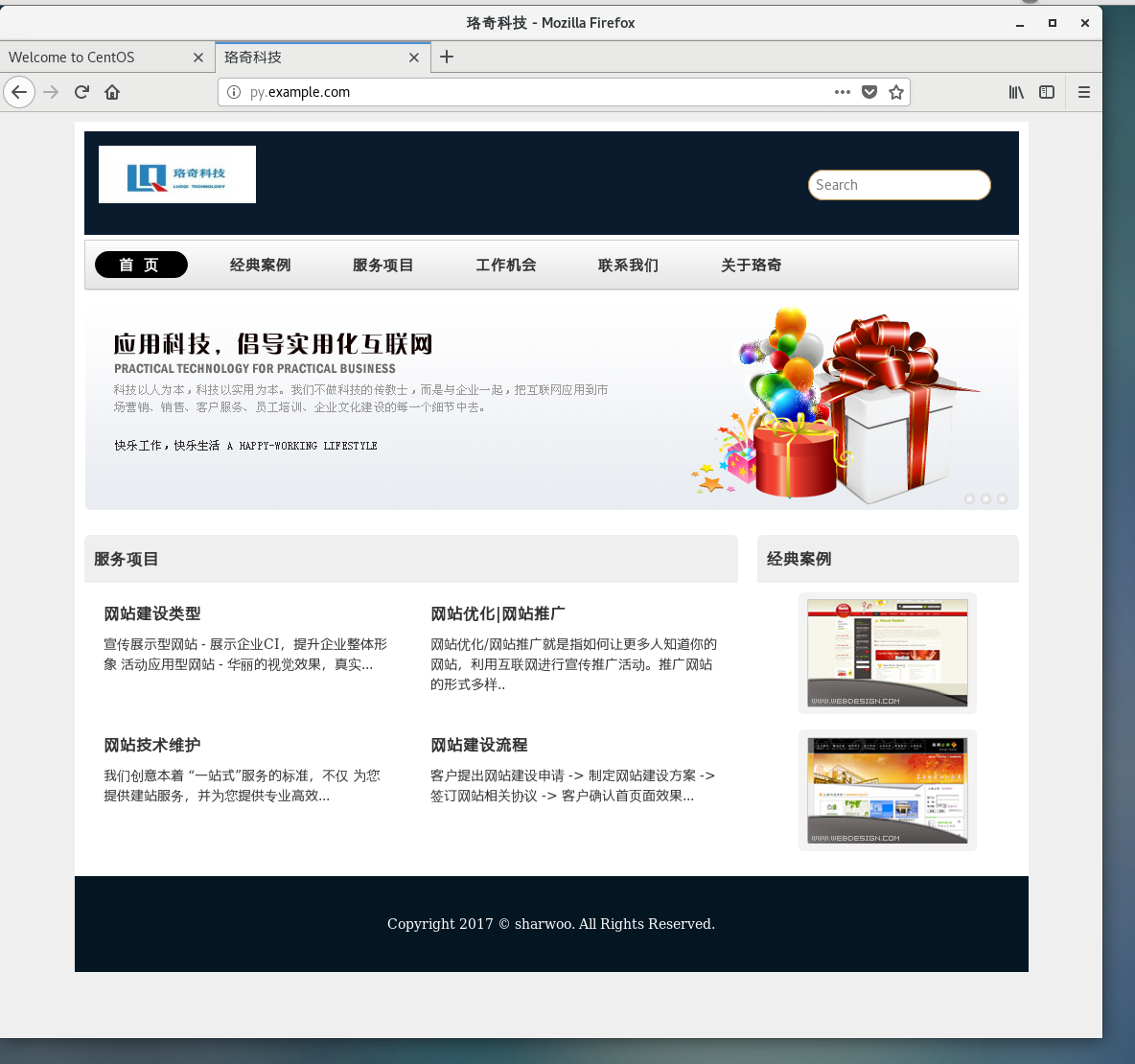
[root@syf3 ~]# curl -k https://syf2.example.com
123456动态网页:
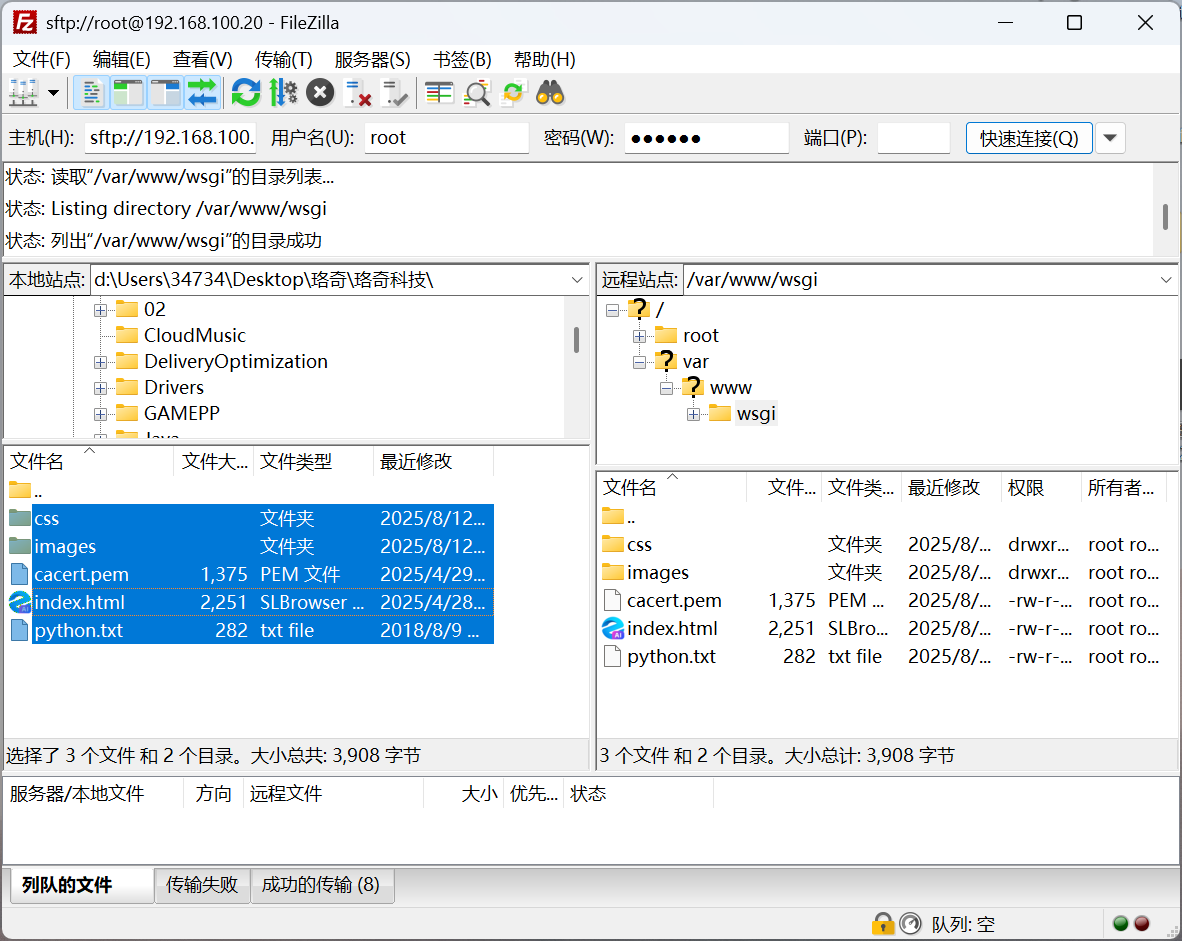
[root@syf2 ~]# mkdir /var/www/wsgi
[root@syf2 ~]# cd /var/www/wsgi
[root@syf2 wsgi]# ls
[root@syf2 wsgi]# ls
cacert.pem css images index.html python.txt
[root@syf2 wsgi]# vim /etc/httpd/conf.d/httpd-vhosts.conf
[root@syf ~]# vim /var/named/ovo.com
$TTL 1D
@ IN SOA shenyifeng.example.com. root.example.com. (
2025081101 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
NS shenyifeng.example.com.
shenyifeng IN A 192.168.100.10
lisi IN A 192.168.100.10
ca IN A 192.168.100.10
syf2 IN A 192.168.100.20
py IN A 192.168.100.20
[root@syf ~]# systemctl restart named
[root@syf2 ~]# cd "/var/www/wsgi"
[root@syf2 wsgi]# cat python.txt
def application(environ, start_response):
status = '200 OK'
output = 'Hello World!'
response_headers = [('Content-type', 'text/plain'),
('Content-Length', str(len(output)))]
start_response(status, response_headers)
return [output]
[root@syf2 wsgi]# mv python.txt test.py
[root@syf2 wsgi]# ll
total 12
-rw-r--r-- 1 root root 1375 Aug 12 21:03 cacert.pem
drwxr-xr-x 2 root root 23 Aug 12 21:03 css
drwxr-xr-x 2 root root 68 Aug 12 21:03 images
-rw-r--r-- 1 root root 2251 Aug 12 21:03 index.html
-rw-r--r-- 1 root root 282 Aug 12 21:03 test.py
[root@syf2 wsgi]# chmod +x test.py
[root@syf2 wsgi]# ll
total 12
-rw-r--r-- 1 root root 1375 Aug 12 21:03 cacert.pem
drwxr-xr-x 2 root root 23 Aug 12 21:03 css
drwxr-xr-x 2 root root 68 Aug 12 21:03 images
-rw-r--r-- 1 root root 2251 Aug 12 21:03 index.html
-rwxr-xr-x 1 root root 282 Aug 12 21:03 test.py
[root@syf2 wsgi]# vim /etc/httpd/conf.d/httpd-vhosts.conf
...
<VirtualHost 192.168.100.20:80>
DocumentRoot "/var/www/wsgi"
WSGIScriptAlias / "/var/www/wsgi/test.py"
ServerName py.example.com
</VirtualHost>
...
[root@syf2 wsgi]# systemctl restart httpd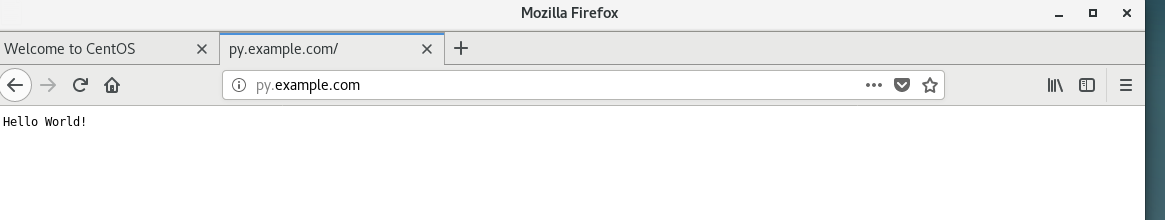
[root@syf2 wsgi]# vim /etc/httpd/conf.d/httpd-vhosts.conf
...
<VirtualHost 192.168.100.20:80>
DocumentRoot "/var/www/wsgi"
#WSGIScriptAlias / "/var/www/wsgi/"
ServerName py.example.com
</VirtualHost>
...
[root@syf2 wsgi]# systemctl restart httpd