假设有这么一个需求,开发人员要求你创建一个账号test,要求这个账号有创建表,查询,更新,删除表的权限, 如下例子所示
SQL
mysql> select version();
+-----------+
| version() |
+-----------+
| 8.4.5 |
+-----------+
1 row in set (0.00 sec)
mysql> create database if not exists kerry
-> default character set utf8mb4
-> default collate utf8mb4_general_ci;
query ok, 1 row affected (0.02 sec)
mysql> create user `test`@`%` identified by 'Test@#$123456';
Query OK, 0 rows affected (0.02 sec)
mysql>
mysql> grant create, drop ,select,update on kerry.* to test@'%';
Query OK, 0 rows affected (0.00 sec)
mysql> flush privileges;
Query OK, 0 rows affected (0.01 sec)
mysql>然后我们以test用户登录数据库, 此时你执行下面SQL,你会发现,你不光有drop掉表的权限,甚至连数据库kerry都可以drop掉.如下所示
SQL
mysql> select current_user();
+----------------+
| current_user() |
+----------------+
| test@% |
+----------------+
1 row in set (0.00 sec)
mysql> create table t1(id int, name varchar(12));
Query OK, 0 rows affected (0.02 sec)
mysql> drop table t1;
Query OK, 0 rows affected (0.01 sec)
mysql> drop database kerry;
Query OK, 0 rows affected (0.01 sec)
mysql> 然后你会发现,test用户不光有drop掉数据库kerry的权限,而且有创建数据库kerry的权限(仅仅是创建/删除kerry这个数据库.没有创建/删除其它数据库的权限 ),
如下所示:
SQL
mysql> select current_user();
+----------------+
| current_user() |
+----------------+
| test@% |
+----------------+
1 row in set (0.00 sec)
mysql> create database if not exists kerry
-> default character set utf8mb4
-> default collate utf8mb4_general_ci;
query ok, 1 row affected (0.01 sec)
mysql> drop database kerry;
query ok, 0 rows affected (0.00 sec)
mysql> create database kkk;
error 1044 (42000): access denied for user 'test'@'%' to database 'kkk'
mysql> drop database k2;
ERROR 1044 (42000): Access denied for user 'test'@'%' to database 'k2'
mysql>其实具体原因是你没有留意MySQL官方文档关于CREATE/DROP权限的详细说明,你以为的CREATE权限是创建表的权限,DROP权限是DROP表的权限.其实不然, 如下截图所示,CREATE权限包含创建数据库、表或索引的权限,而DROP权限包DROP数据库、表或视图的权限. 至于为什么MySQL没有细化这些权限.我们也不清楚.但是从上面实验来看, 我都倾向于这个是一个逻辑上的"Bug".
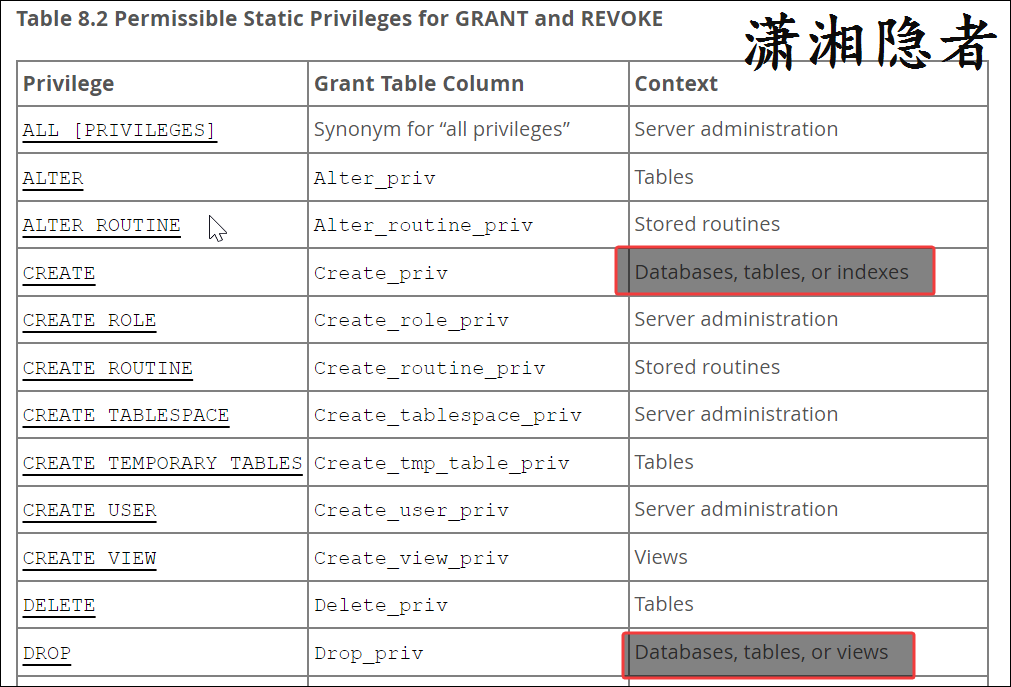
那么如果这样授权,会有什么问题呢? **如果账号授予了DROP权限,那么这就是一个安全权限的"漏洞", SQL注入式攻击都可以利用这个"漏洞"直接将数据库给删除了. **
解决方案
MySQL中没有单独的CREATE TABLE, DROP TABLE的权限,我们只能另避蹊径,先收回账号test的DROP权限,然后创建一个角色drop_tab,这个角色授予数据库kerry中具体每一个表的DROP权限,最后授予用户这个角色. 如下所示:
SQL
mysql> select current_user();
+----------------+
| current_user() |
+----------------+
| root@localhost |
+----------------+
1 row in set (0.01 sec)
mysql> show grants for test@'%';
+---------------------------------------------------------------+
| Grants for test@% |
+---------------------------------------------------------------+
| GRANT USAGE ON *.* TO `test`@`%` |
| GRANT SELECT, UPDATE, CREATE, DROP ON `kerry`.* TO `test`@`%` |
+---------------------------------------------------------------+
2 rows in set (0.00 sec)
mysql> revoke drop on `kerry`.* from `test`@`%`;
Query OK, 0 rows affected (0.06 sec)
mysql> flush privileges;
Query OK, 0 rows affected (0.01 sec)
mysql> create role drop_tab;
Query OK, 0 rows affected (0.01 sec)
mysql> select
-> table_name
-> ,table_type
-> ,concat('grant drop on ', table_schema, '.', table_name , ' to test@''%'';') as grant_cmd
-> from information_schema.tables
-> where table_schema='kerry';
+------------+------------+-------------------------------------+
| TABLE_NAME | TABLE_TYPE | grant_cmd |
+------------+------------+-------------------------------------+
| t1 | BASE TABLE | grant drop on kerry.t1 to test@'%'; |
| t2 | BASE TABLE | grant drop on kerry.t2 to test@'%'; |
+------------+------------+-------------------------------------+
2 rows in set (0.00 sec)
mysql>
mysql> grant drop on kerry.t1 to test@'%';
Query OK, 0 rows affected (0.01 sec)
mysql> grant drop on kerry.t2 to test@'%';
Query OK, 0 rows affected (0.00 sec)
mysql> grant drop_tab to test@'%';
Query OK, 0 rows affected (0.00 sec)
mysql> flush privileges;
Query OK, 0 rows affected (0.00 sec)
mysql> 此时,账号test就没有删除数据库kerry的权限了.
SQL
mysql> select current_user();
+----------------+
| current_user() |
+----------------+
| test@% |
+----------------+
1 row in set (0.00 sec)
mysql> drop table t1;
Query OK, 0 rows affected (0.02 sec)
mysql> drop database kerry;
ERROR 1044 (42000): Access denied for user 'test'@'%' to database 'kerry'
mysql> 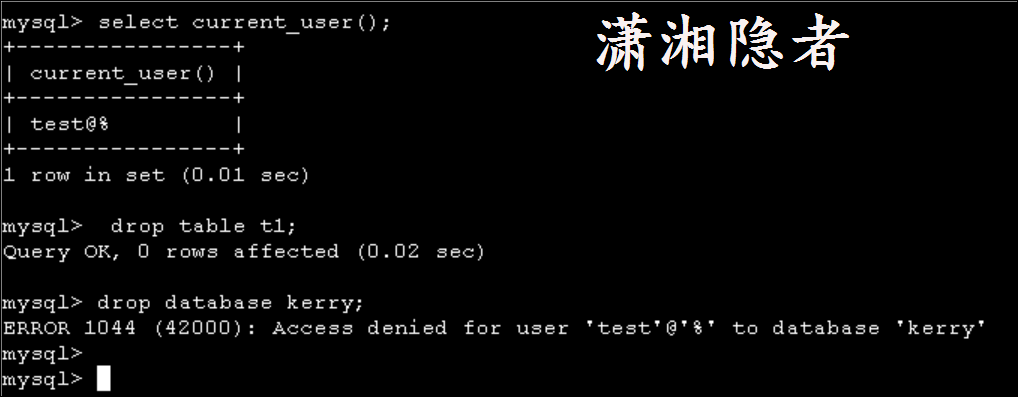
总结
关于数据库的权限,我们还是要细心与谨慎. 数据库授权,一般要秉着权限越小越好的原则,避免权限过大带来不必要的麻烦. 另外,就是MySQL这种权限设计, 其实是设计上的一大缺陷.很容易让人踩一个大坑.