1 拓扑
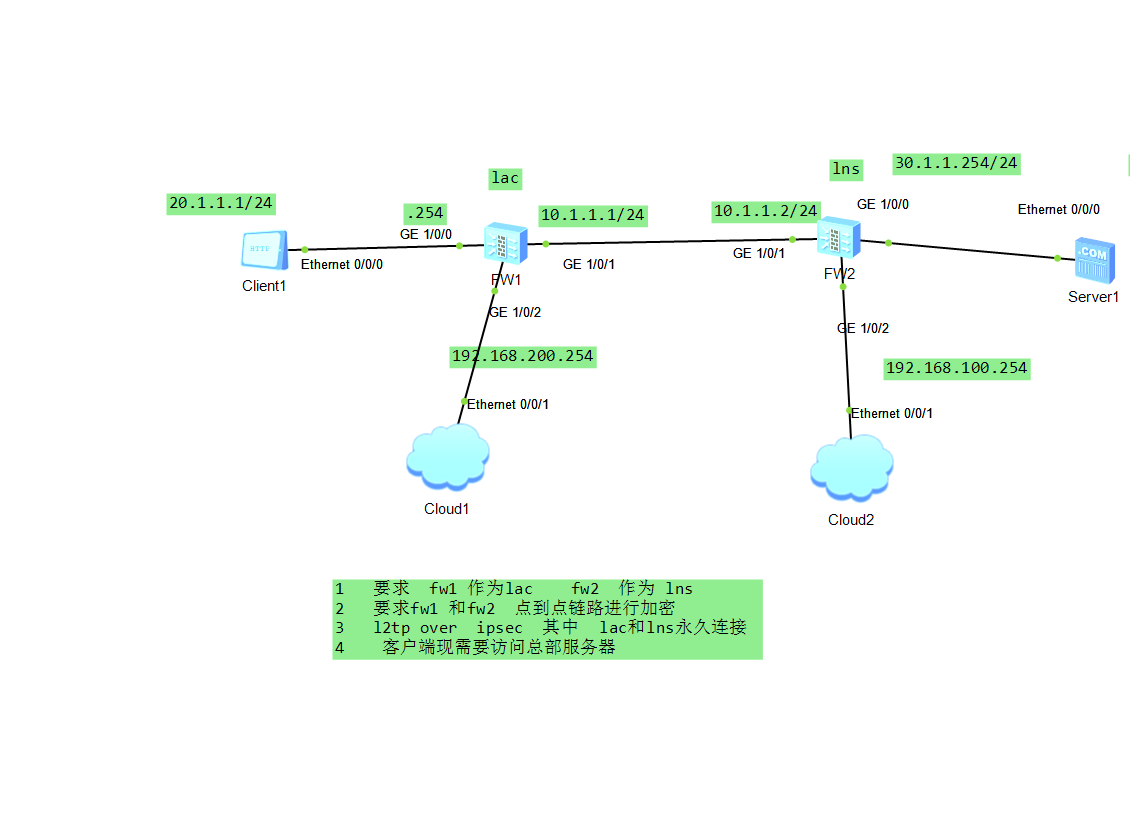
2 基础配置
接口配置,地址配置,防火墙登入配置,准备工作要做好
fw1 的基础配置
update schedule sa-sdb daily 03:05
update schedule cnc daily 03:05
update schedule file-reputation daily 03:05
ip vpn-instance default
ipv4-family
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%Ca[}-ynC3X"Nh:Jj%'a)/4pan,*0760/6<WMNE'ir-4>4pd/@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%ra0vLsyz+ET/fd6J#UiQ9J3&5*|>XVNHs*"=v"1)P3M/J3)9@%@%
level 15
manager-user admin
password cipher @%@%KROL2&8u,2@fn8"171|>`<Jn0fsU=NR2lI8N9e&<"ll:<Jq`@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
l2tp-group default-lns
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 20.1.1.254 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.1.1.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
interface GigabitEthernet1/0/2
undo shutdown
ip address 192.168.200.250 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
interface GigabitEthernet1/0/3
undo shutdown
interface GigabitEthernet1/0/4
undo shutdown
interface GigabitEthernet1/0/5
undo shutdown
interface GigabitEthernet1/0/6
undo shutdown
interface Virtual-if0
interface NULL0
**firewall zone local
set priority 100
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/2
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
firewall zone dmz
set priority 50
#**
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
firewall detect ftp
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
pki realm default
sa
location
multi-linkif
mode proportion-of-weight
right-manager server-group
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
user-manage server-sync tsm
security-policy
rule name 20.1.1.0
source-zone local
source-zone trust
destination-zone local
destination-zone trust
source-address 20.1.1.0 mask 255.255.255.0
destination-address 20.1.1.0 mask 255.255.255.0
action permit
rule name 192.168.200.0
source-zone local
source-zone trust
destination-zone local
destination-zone trust
source-address 192.168.200.0 mask 255.255.255.0
destination-address 192.168.200.0 mask 255.255.255.0
action permit
rule name 10.1.1.0
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 10.1.1.0 mask 255.255.255.0
destination-address 10.1.1.0 mask 255.255.255.0
action permit
#
auth-policy
traffic-policy
policy-based-route
nat-policy
quota-policy
pcp-policy
dns-transparent-policy
rightm-policy
return
fw2 的基础配置
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
firewall dataplane to manageplane application-apperceive default-action drop
undo ips log merge enable
decoding uri-cache disable
update schedule ips-sdb daily 22:30
update schedule av-sdb daily 22:30
update schedule sa-sdb daily 22:30
update schedule cnc daily 22:30
update schedule file-reputation daily 22:30
ip vpn-instance default
ipv4-family
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%@.51F"Im9LPnClL{+jgQz5M,gx<62i%qs)hQE~&P@.h.5M/z@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%GkMC1Pv@::4zb,#~ktj<i85IU:!A5!1X2@)J7}I|l,DS85Li@%@%
level 15
manager-user admin
password cipher @%@%B8o,Ha9T%>L)u,Oc:dI8->b3U&UI-M#{3O>~6;03`nl>>b6-@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
l2tp-group default-lns
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
interface GigabitEthernet1/0/0
undo shutdown
ip address 30.1.1.254 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
interface GigabitEthernet1/0/1
undo shutdown
ip address 10.1.1.2 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 192.168.100.250 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
#
interface GigabitEthernet1/0/3
undo shutdown
interface GigabitEthernet1/0/4
undo shutdown
interface GigabitEthernet1/0/5
undo shutdown
interface GigabitEthernet1/0/6
undo shutdown
interface Virtual-if0
interface NULL0
firewall zone local
set priority 100
**firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/2
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
firewall zone dmz
set priority 50
#**
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
firewall detect ftp
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
pki realm default
sa
location
multi-linkif
mode proportion-of-weight
right-manager server-group
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
user-manage server-sync tsm
security-policy
rule name 10.1.1.0
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 10.1.1.0 mask 255.255.255.0
destination-address 10.1.1.0 mask 255.255.255.0
action permit
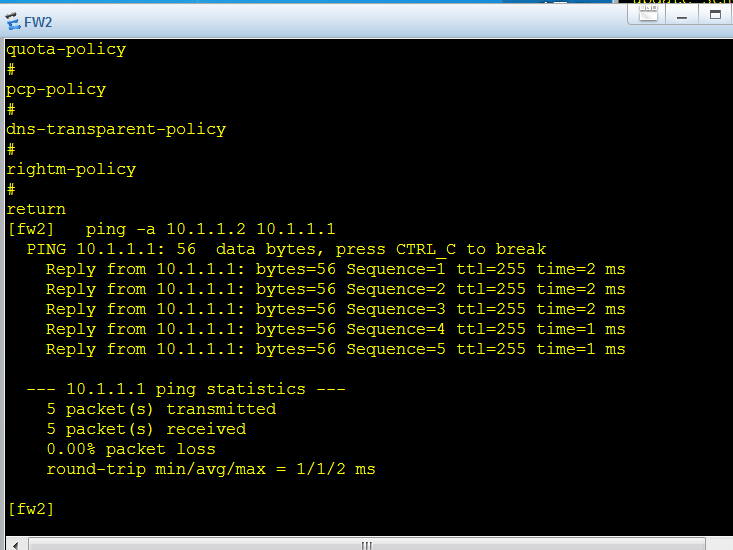
基础测试完成 ,保证防火墙的直连接口可以通信
3 先做ipsec的配置把fw1 和fw2 直连网段ipsec打通
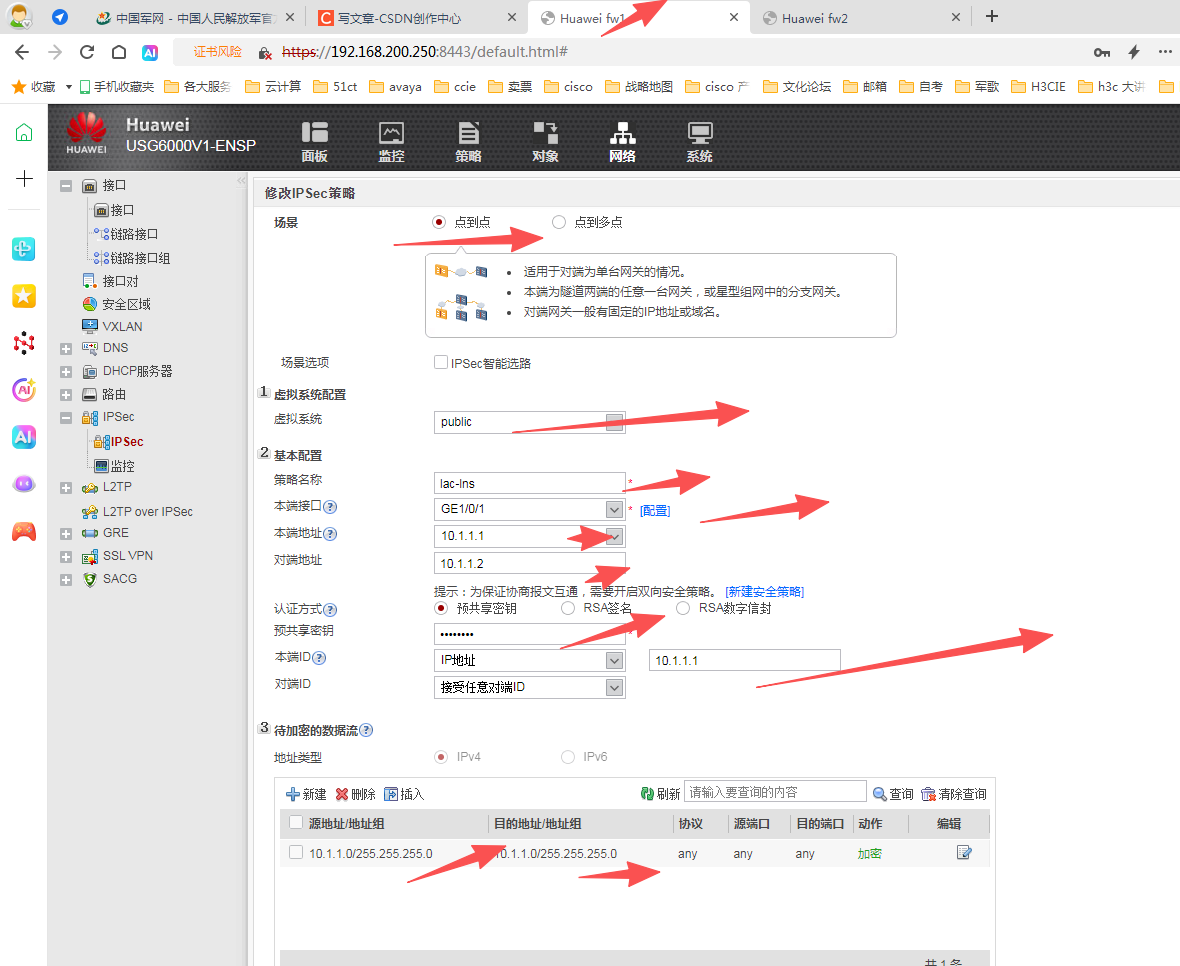
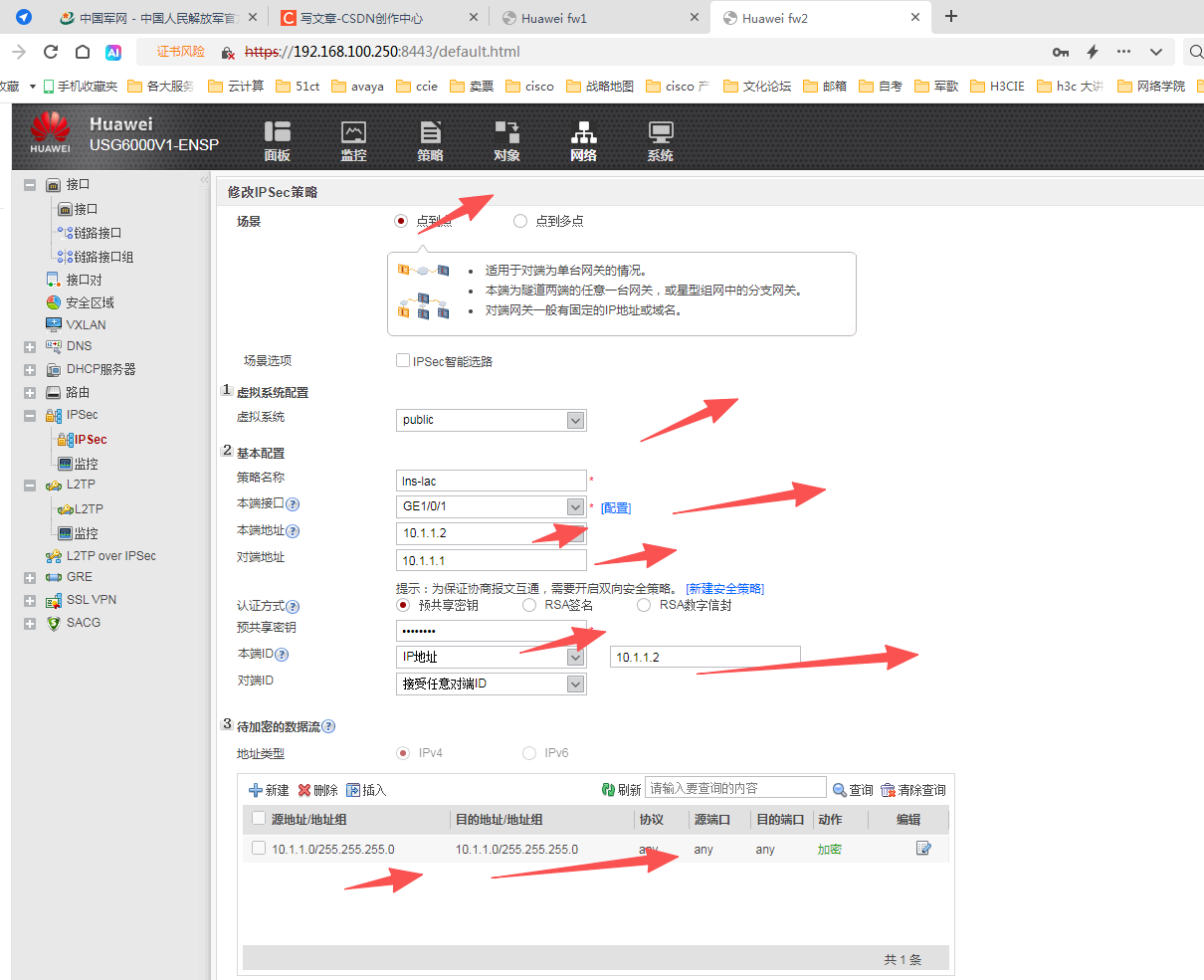
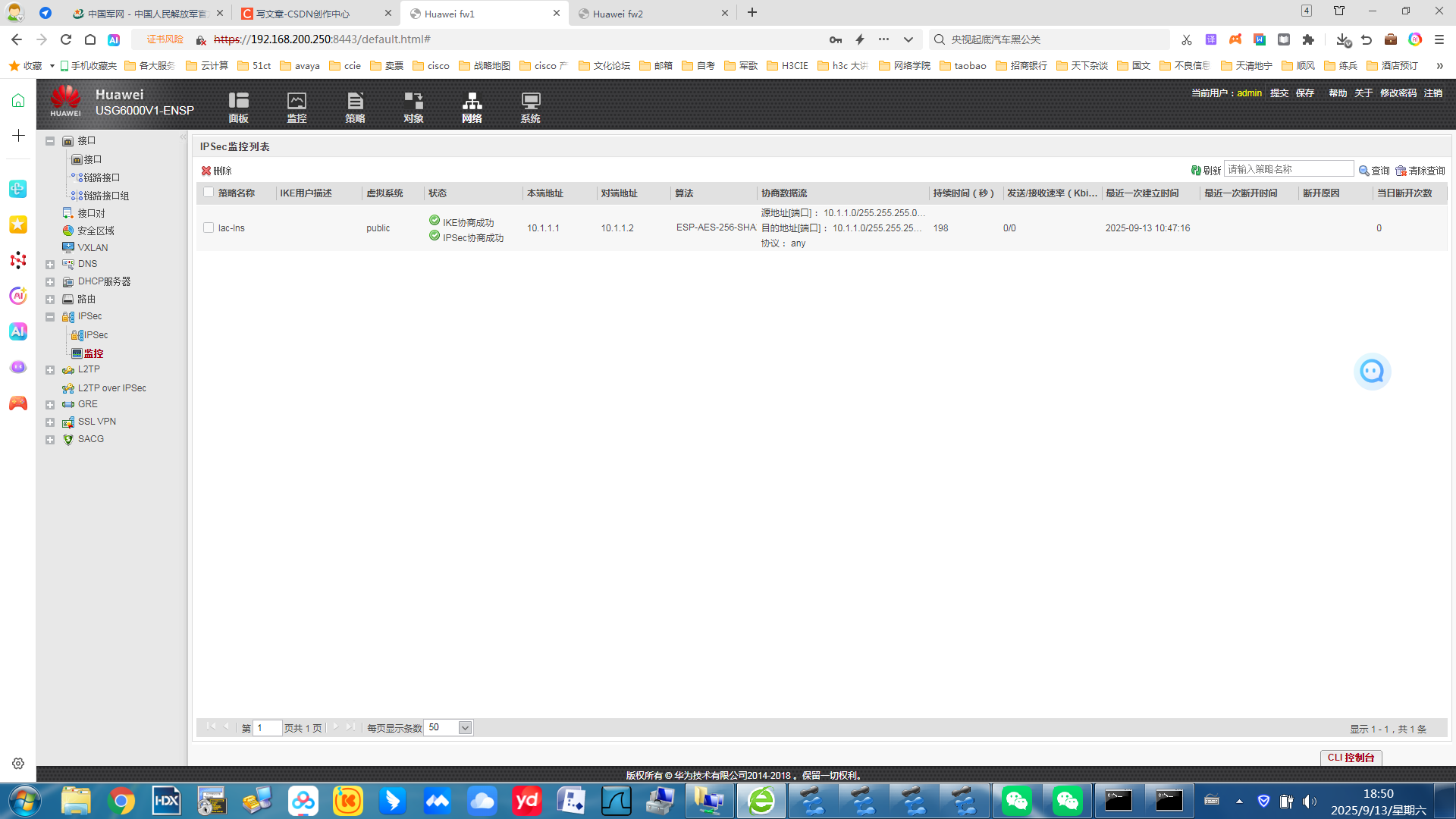
<fw1>display ike sa
2025-09-13 10:50:56.680
IKE SA information :
Conn-ID Peer VPN Flag(
s) Phase RemoteType RemoteID
4 10.1.1.2:500 RD|A
v2:2 IP 10.1.1.2
3 10.1.1.2:500 RD|A
v2:1 IP 10.1.1.2
Number of IKE SA : 2
Flag Description:
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP
M--ACTIVE S--STANDBY A--ALONE NEG--NEGOTIATING
<fw1> dis
<fw1> display ipsa
<fw1> display ips
<fw1> display ipsec sa
<fw1> display ipsec sa
2025-09-13 10:51:01.200
ipsec sa information:
===============================
Interface: GigabitEthernet1/0/1
===============================
IPSec policy name: "ipsec1391845572"
Sequence number : 1
Acl group : 3000
Acl rule : 5
Mode : ISAKMP
Connection ID : 4
Encapsulation mode: Tunnel
Holding time : 0d 0h 3m 44s
Tunnel local : 10.1.1.1:500
Tunnel remote : 10.1.1.2:500
Flow source : 10.1.1.0/255.255.255.0 0/0-65535
Flow destination : 10.1.1.0/255.255.255.0 0/0-65535
Outbound ESP SAs
SPI: 198188983 (0xbd01fb7)
Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128
SA remaining key duration (kilobytes/sec): 0/604576
Max sent sequence-number: 8
UDP encapsulation used for NAT traversal: N
SA encrypted packets (number/bytes): 7/588
Inbound ESP SAs
SPI: 185357876 (0xb0c5634)
Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128
SA remaining key duration (kilobytes/sec): 0/604576
Max received sequence-number: 1
UDP encapsulation used for NAT traversal: N
SA decrypted packets (number/bytes): 7/588
Anti-replay : Enable
Anti-replay window size: 1024
<fw1>
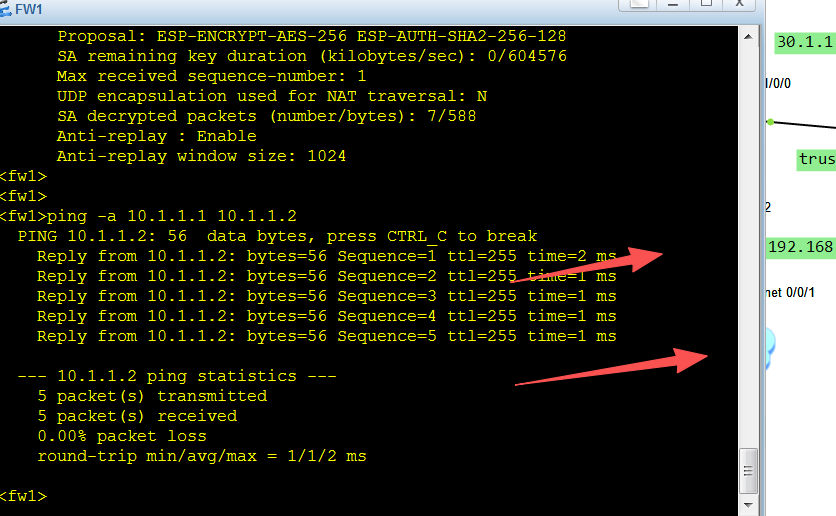
做到这里ipsec 算是成功了
4 做lac 和lns
lns 配置
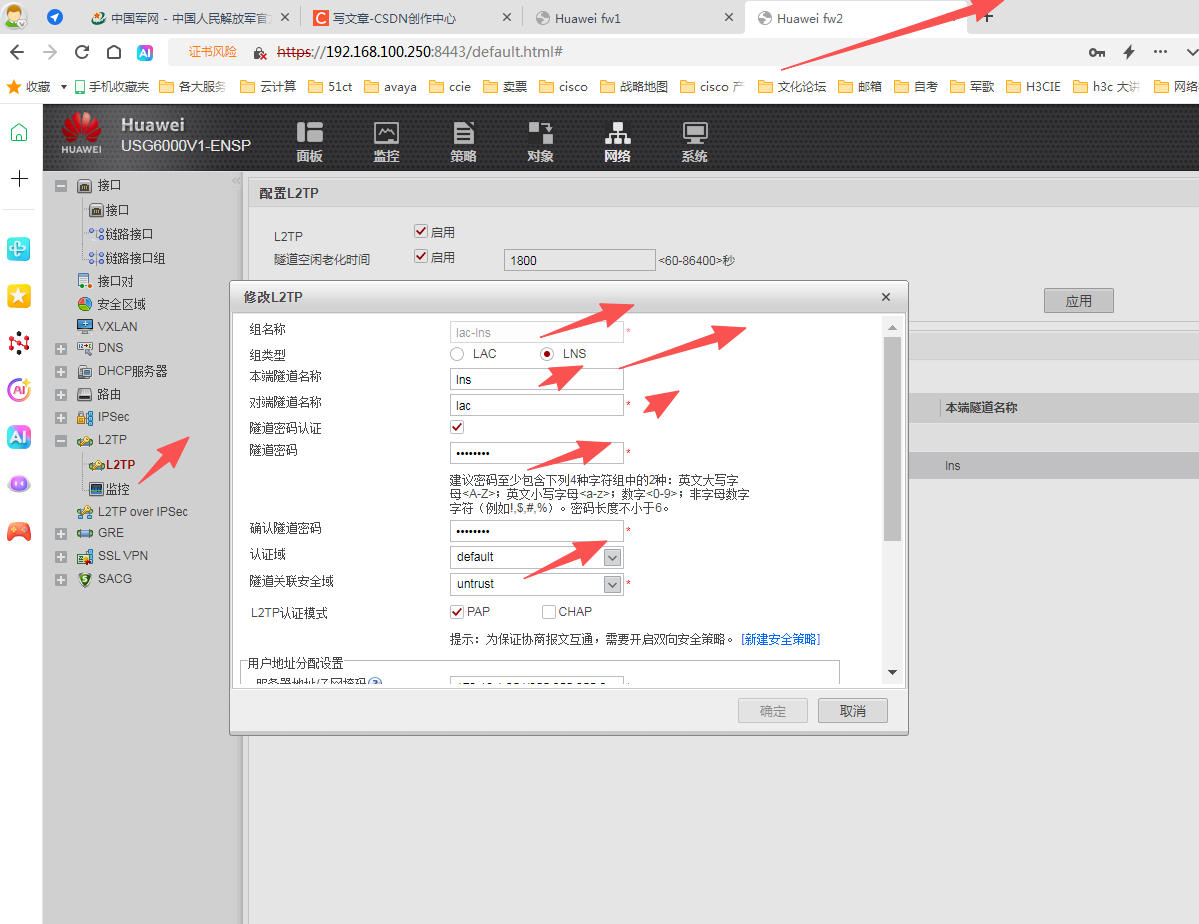
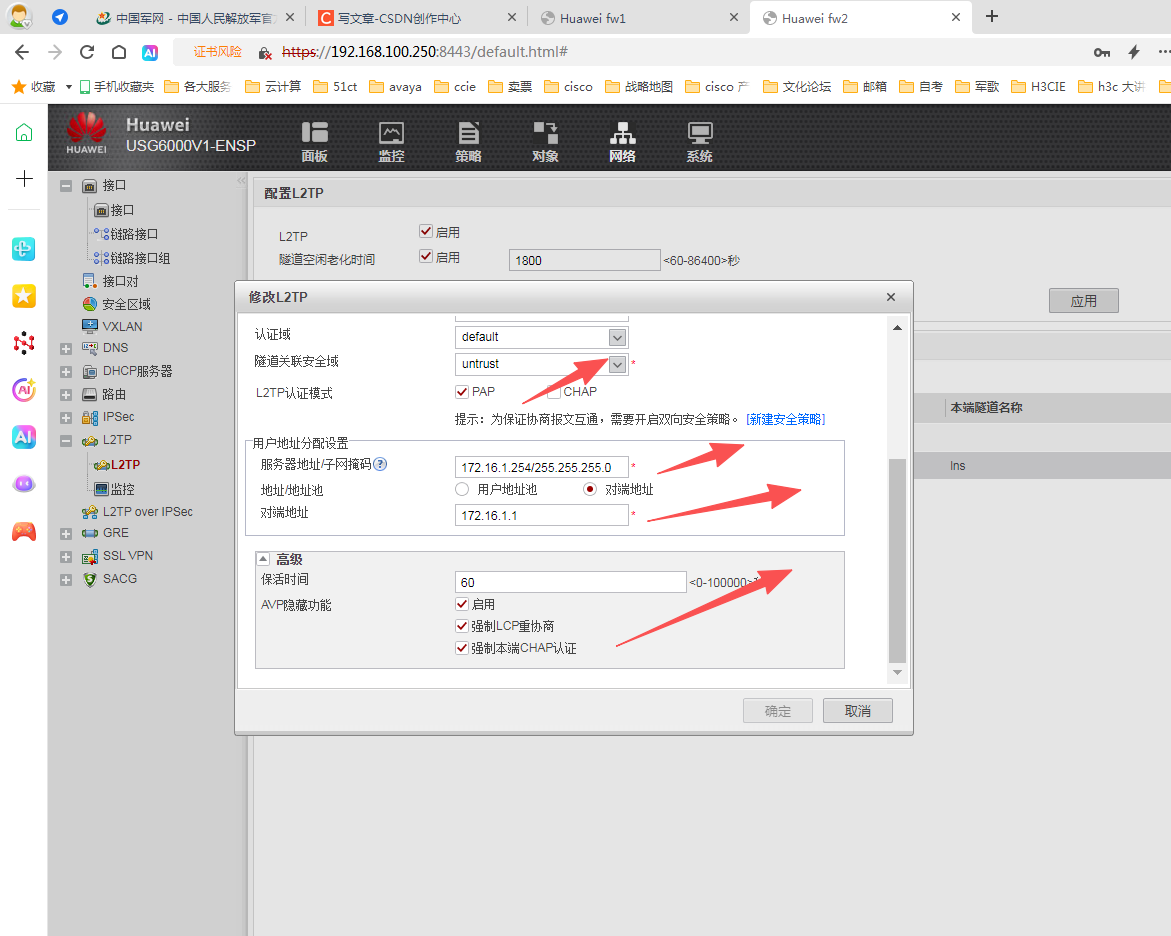

穿件本地用户
lac 侧配置
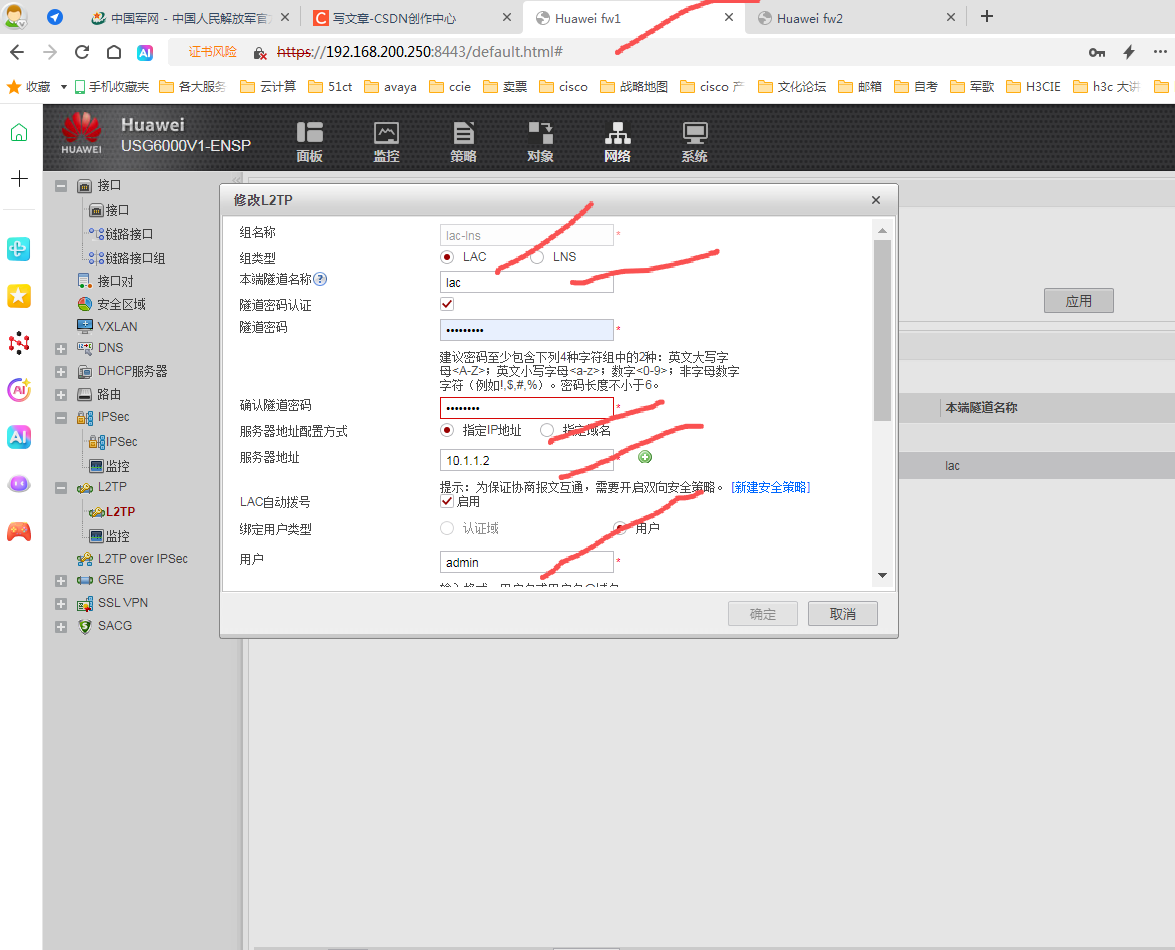
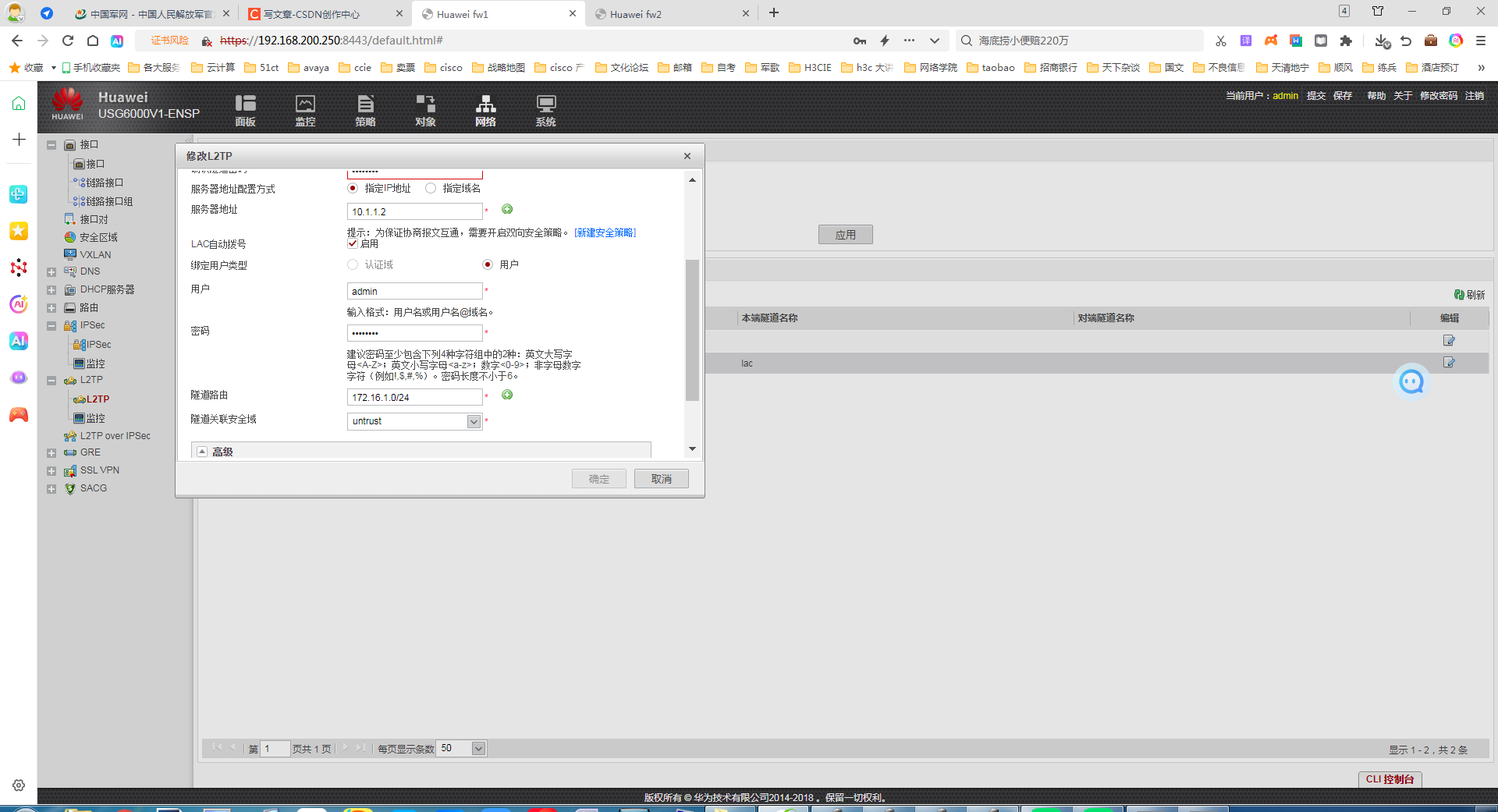
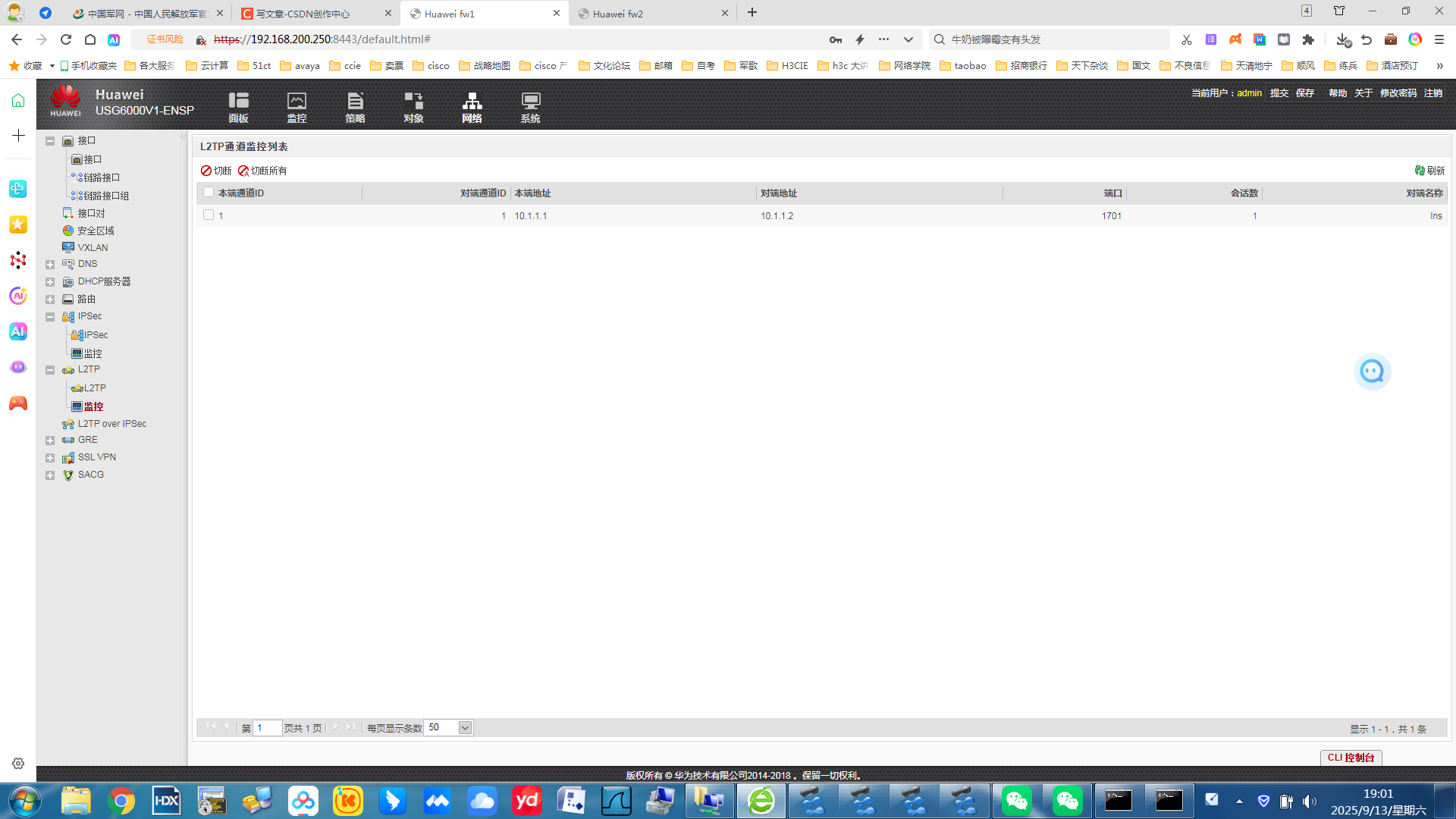
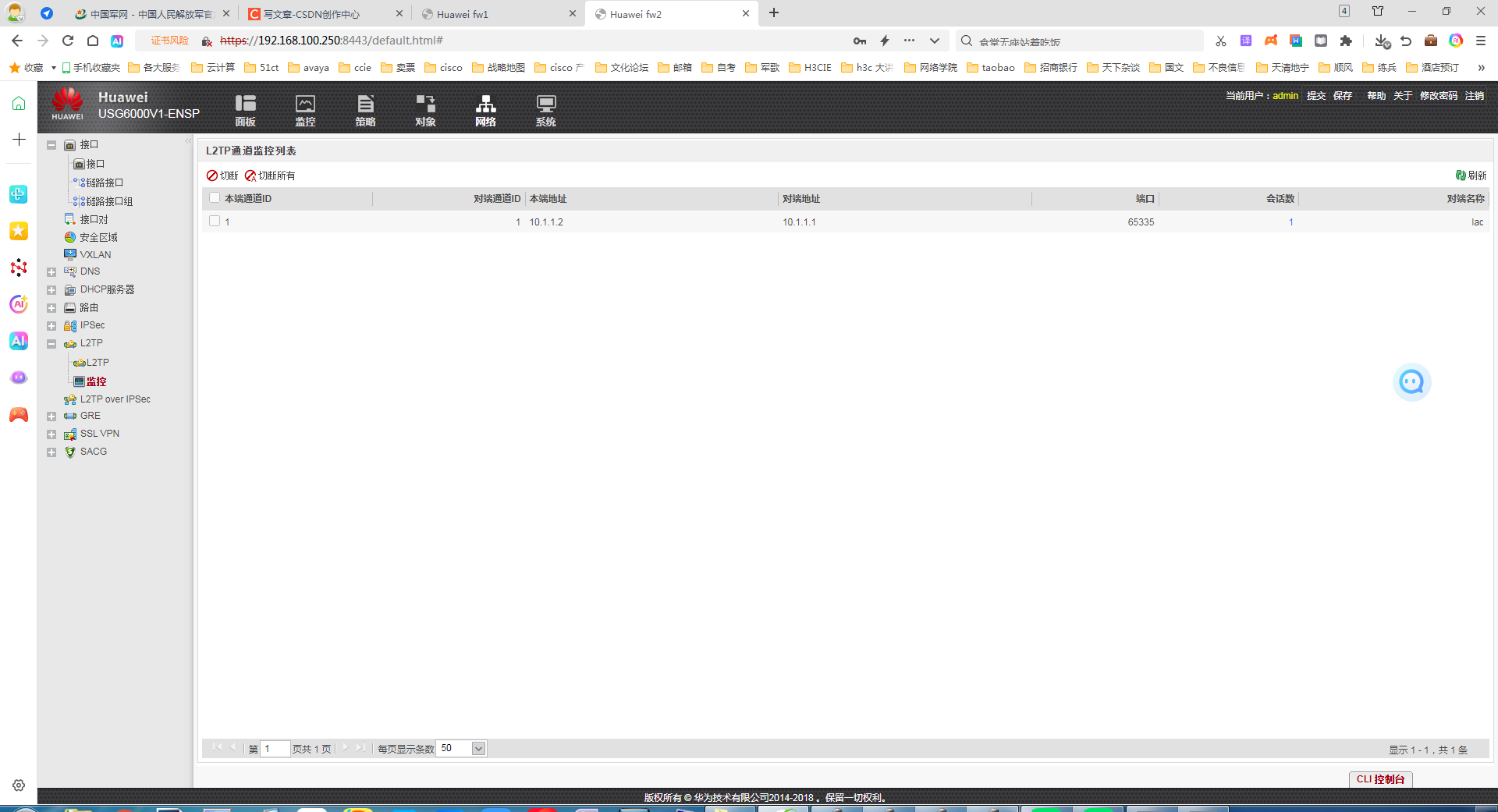
很明显lac和lns的隧道成功了
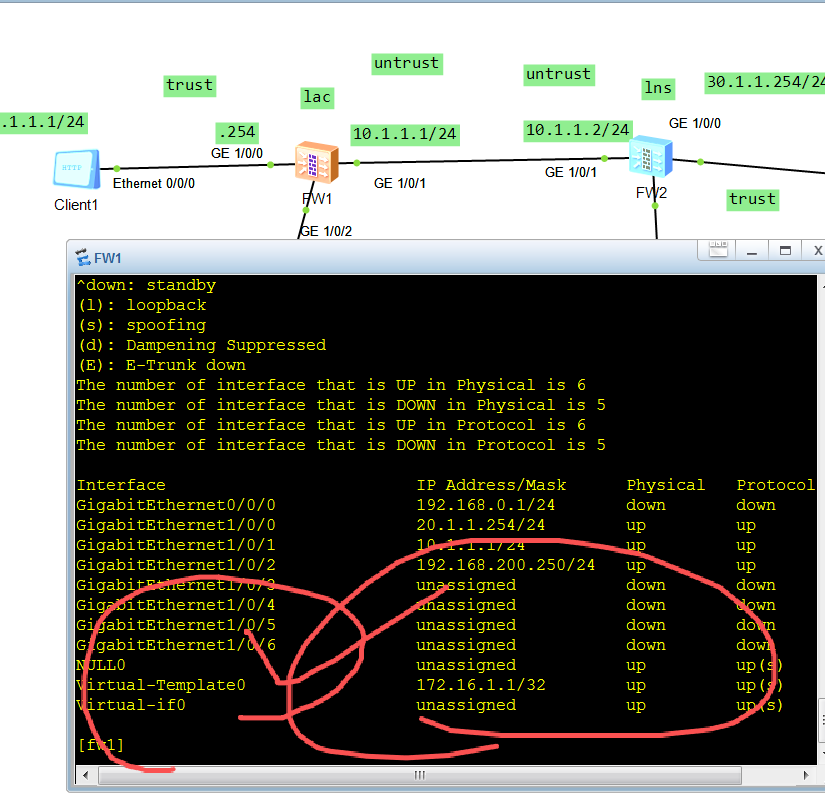
注意事项
fw1\]interface Virtual-Template 0 \[fw1-Virtual-Template0
fw1-Virtual-Template0\]dis th 2025-09-13 11:07:15.050 # interface Virtual-Template0 ppp authentication-mode chap pap ppp chap user admin ppp chap password cipher %$%$\]pRhHRe\~R,4x\*RP(9p!2\&O9\]%$%$ ppp pap local-user admin password cipher %$%$\[l"x2\|f_KA,p(HX\\x\~;#cnW@%$%$ ip address ppp-negotiate call-lns local-user admin binding l2tp-group lac-lns alias L2TP_LAC_0 **service-manage http permit service-manage https permit service-manage ping permit service-manage ssh permit service-manage snmp permit service-manage telnet permit** # return rule name l2tp source-zone local source-zone untrust destination-zone local destination-zone untrust source-address 172.16.1.0 mask 255.255.255.0 destination-address 172.16.1.0 mask 255.255.255.0 action permit fw2 上注意的配置 \[fw2-Virtual-Template0\]dis th 2025-09-13 11:08:21.620 # interface Virtual-Template0 ppp authentication-mode pap remote address 172.16.1.1 ip address 172.16.1.254 255.255.255.0 alias L2TP_LNS_0 service-manage http permit service-manage https permit service-manage ping permit service-manage ssh permit service-manage snmp permit service-manage telnet permit # return \[fw2-Virtual-Template0
rule name l2tp
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 172.16.1.0 mask 255.255.255.0
destination-address 172.16.1.0 mask 255.255.255.0
action permit
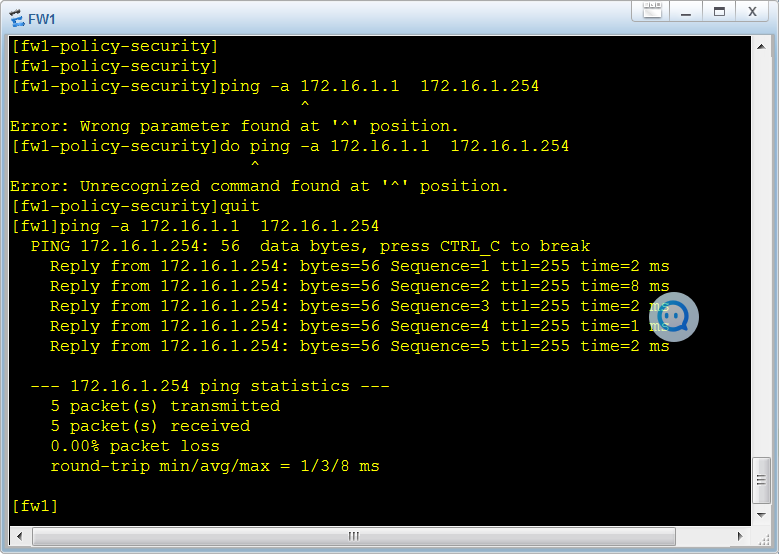
5 pc 访问ftp
fw1 上的配置
rule name vi-30.1..10
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 172.16.1.0 mask 255.255.255.0
source-address 30.1.1.0 mask 255.255.255.0
destination-address 172.16.1.0 mask 255.255.255.0
destination-address 30.1.1.0 mask 255.255.255.0
action permit
ip route-static 30.1.1.0 255.255.255.0 Virtual-Template0
ip route-static 172.16.1.0 255.255.255.0 Virtual-Template0
------------------------------------------------------------fw1 shang
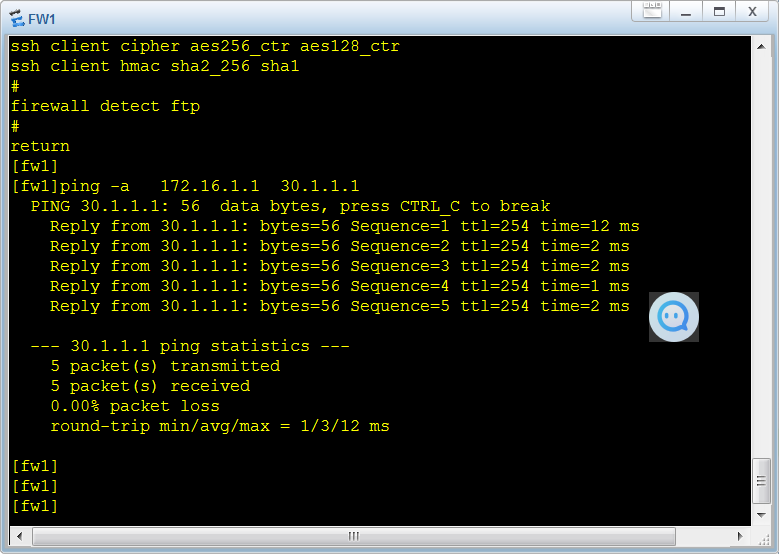
rule name ftp
source-zone local
source-zone trust
source-zone untrust
destination-zone local
destination-zone trust
destination-zone untrust
source-address 172.16.1.0 mask 255.255.255.0
source-address 30.1.1.0 mask 255.255.255.0
destination-address 172.16.1.0 mask 255.255.255.0
destination-address 30.1.1.0 mask 255.255.255.0
action permit
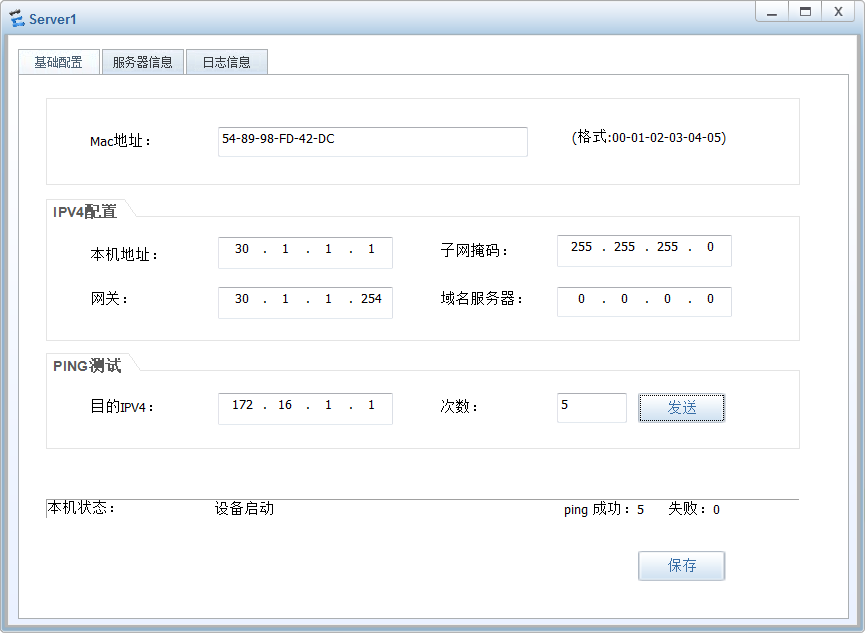
=====================================================fw2 上的配置
pc 上网
rule name pc
source-zone trust
destination-zone untrust
source-address 10.1.1.0 mask 255.255.255.0
source-address 20.1.1.0 mask 255.255.255.0
action permit
fw1-policy-nat\]dis th 2025-09-13 11:24:16.900 # nat-policy rule name pc source-zone trust destination-zone untrust source-address 10.1.1.0 mask 255.255.255.0 source-address 20.1.1.0 mask 255.255.255.0 action source-nat easy-ip # 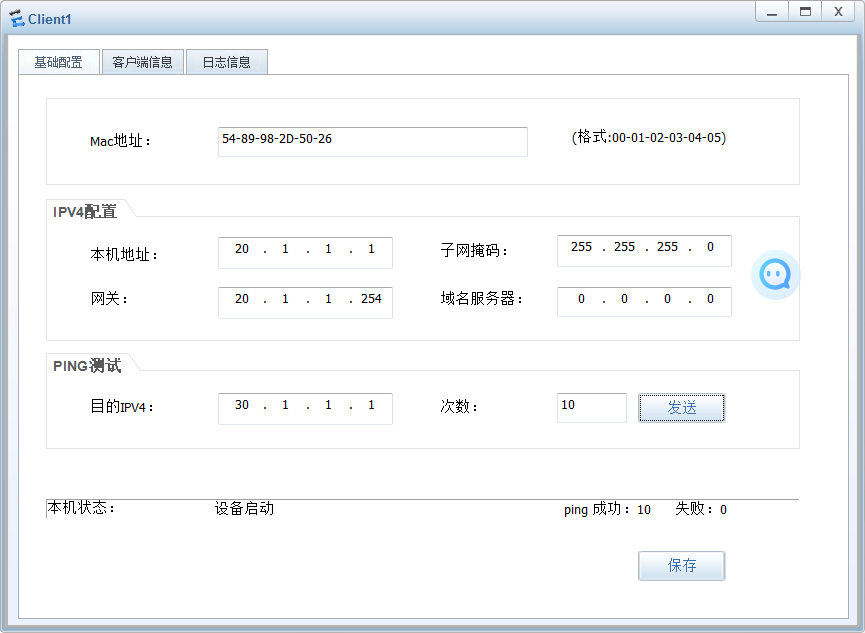 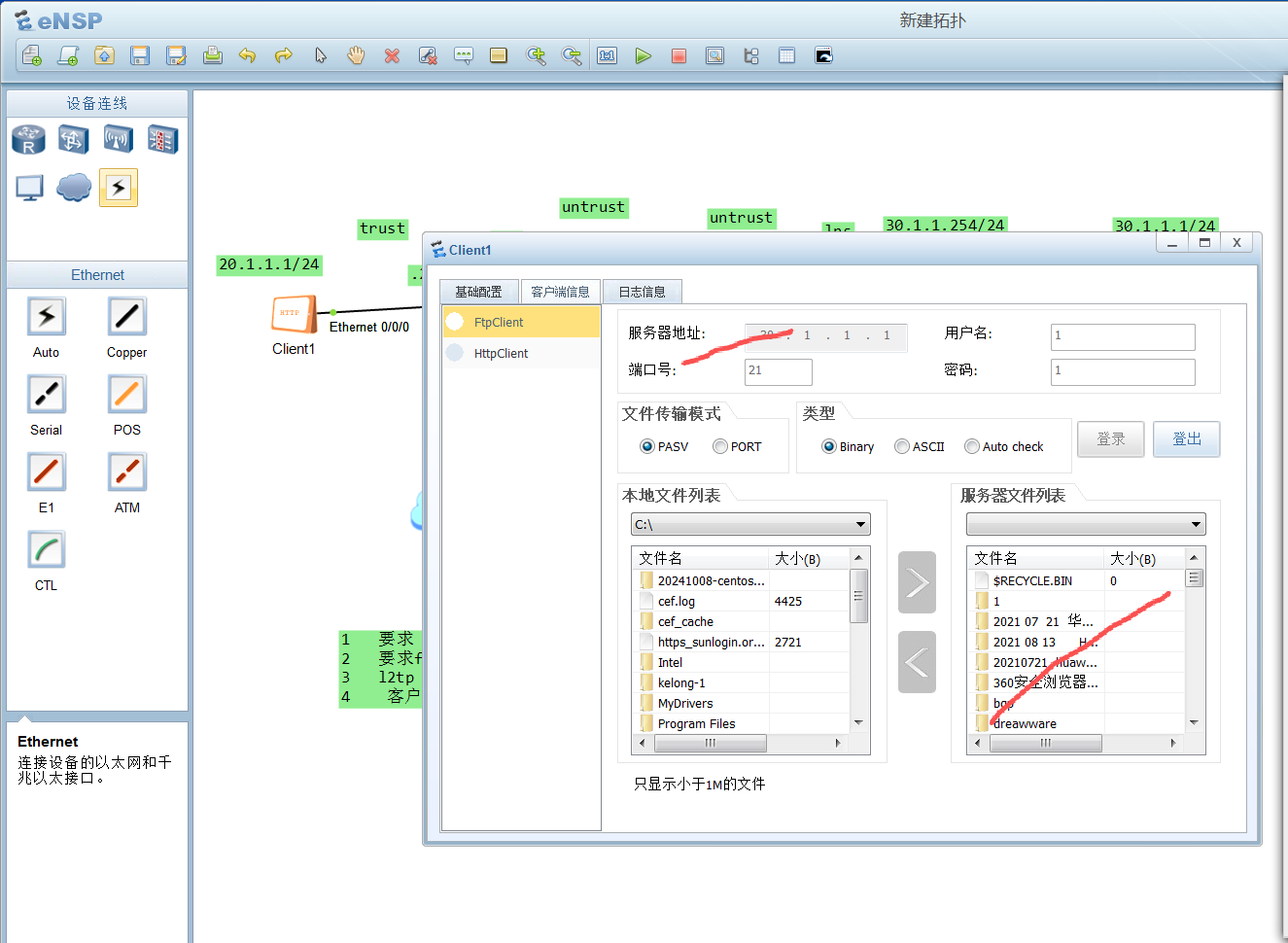 很明显访问 30.1.1.1 文件服务可以测试成功