认证的步骤:
- 启用认证插件。
- 创建用户。
- 给用户分配认证信息(扩展:账号密码 等)。
- 请求时,带上认证信息。
key-auth:
创建用户:
[root@localhost etc]# curl -i -X POST http://localhost:8001/consumers --data username=user1
HTTP/1.1 201 Created
Date: Fri, 02 Dec 2022 08:18:01 GMT
Content-Type: application/json; charset=utf-8
Connection: keep-alive
Access-Control-Allow-Origin: *
Content-Length: 117
X-Kong-Admin-Latency: 24
Server: kong/3.0.1
{"custom_id":null,"tags":null,"id":"e04b610e-4bde-4eaf-88d7-ae8a874e668e","created_at":1669969081,"username":"user1"}[root@localhost etc]#
给user1 设置需要校验的key值。
193 curl -i -X POST http://localhost:8001/consumers/user1/key-auth --data key=top-secret-key
校验key值的参数:apikey。(启用插件)
194 curl -i -X POST http://localhost:8001/plugins --data name=key-auth --data "config.key_names=apikey"
不带key
195 curl -i http://localhost:8000/tomcat82
带错误的key
196 curl -i http://localhost:8000/tomcat82 -H "apikey:asdasd"
带正确的key
197 curl -i http://localhost:8000/tomcat82 -H "apikey:top-secret-key"basic-auth:
创建用户:
curl -i -X POST http://localhost:8001/consumers --data username=user2启用basic-auth的插件:注意不能直接全局开启,需要在services上或者 routes上开启。
curl -i -X POST http://localhost:8001/services/myTomcat/plugins --data name=basic-auth --data "config.hide_credentials=true"给用户创建凭证
curl -X POST http://localhost:8001/consumers/user2/basic-auth --data "username=user2" --data "password=123456"请求的时候,带上 凭证,前提需要做base64的转换。
"user2:123456" 转换成 base64:dXNlcjI6MTIzNDU2
不带凭证:
[root@localhost etc]# curl http://localhost:8000/tomcat82
{
"message":"Unauthorized"
}[root@localhost etc]#
正确的凭证:
curl http://localhost:8000/tomcat82 --header "Authorization: Basic dXNlcjI6MTIzNDU2"
tomcat-8082,82,82
错误的凭证:
[root@localhost etc]# curl http://localhost:8000/tomcat82 --header "Authorization: Basic dXNlcjI6MTIzNDU21"
{
"message":"Invalid authentication credentials"
}[root@localhost etc]#jwt:
删除插件:(注意:最后是 插件的ID,不是名称)
[root@localhost etc]# curl -X DELETE http://localhost:8001/services/myTomcat/plugins/2fe25deb-22a8-484a-aa1a-22bbd778e339
[root@localhost etc]#删除用户:
[root@localhost etc]# curl -X DELETE http://localhost:8001/consumers/userJwt-
启用认证插件。
[root@localhost etc]# curl -X POST http://localhost:8001/services/myTomcat/plugins --data name=jwt {"id":"d4c3714a-114b-4f5e-b8ac-ebcd5c44f531","created_at":1670138890,"service":{"id":"02c6b845-a25b-46d9-9fd0-704feeab3a63"},"route":null,"consumer":null,"tags":null,"enabled":true,"protocols":["grpc","grpcs","http","https"],"name":"jwt","config":{"cookie_names":[],"header_names":["authorization"],"key_claim_name":"iss","claims_to_verify":null,"maximum_expiration":0,"run_on_preflight":true,"anonymous":null,"uri_param_names":["jwt"],"secret_is_base64":false}}[root@localhost etc]# -
创建用户。
[root@localhost etc]# curl -X POST http://localhost:8001/consumers --data username=useJwt {"custom_id":null,"tags":null,"id":"6d52c09c-185b-432f-bc61-f8acd7cb2d98","created_at":1670138991,"username":"useJwt"}[root@localhost etc]# [root@localhost etc]# -
给用户分配认证信息(扩展:账号密码 等)。
[root@localhost etc]# curl -X POST http://localhost:8001/consumers/useJwt/jwt {"id":"7026a984-454e-4f19-a9d3-25ecd2616168","algorithm":"HS256","consumer":{"id":"6d52c09c-185b-432f-bc61-f8acd7cb2d98"},"tags":null,"secret":"82shAj6BMPHoIcHgUbzQnc0tp6dp9bQh","created_at":1670139121,"rsa_public_key":null,"key":"BvWi05tgEijty9ItznMZ696XitLvgG4U"}[root@localhost etc]# -
请求时,带上认证信息。
生成认证信息:网址:https://jwt.io/#debugger-io
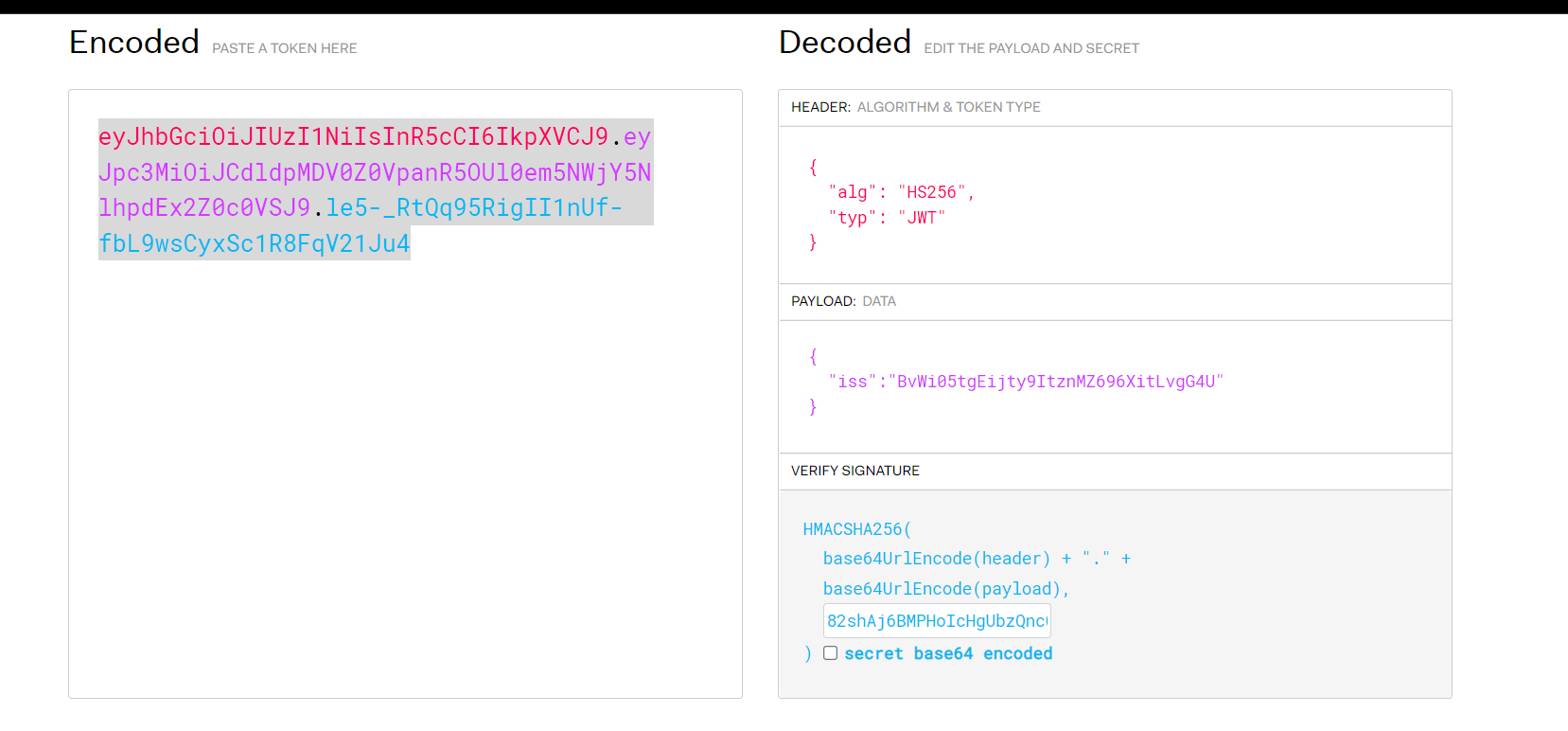
生成的token:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJCdldpMDV0Z0VpanR5OUl0em5NWjY5NlhpdEx2Z0c0VSJ9.le5-_RtQq95RigII1nUf-fbL9wsCyxSc1R8FqV21Ju4请求:
[root@localhost etc]# curl -X GET http://localhost:8000/tomcat82 -H 'Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJCdldpMDV0Z0VpanR5OUl0em5NWjY5NlhpdEx2Z0c0VSJ9.le5-_RtQq95RigII1nUf-fbL9wsCyxSc1R8FqV21Ju4'
tomcat-8082,82,82
[root@localhost etc]#jwt组成:
HEADER:base64(json ). base64(payload). 下面的代码块。
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
82shAj6BMPHoIcHgUbzQnc0tp6dp9bQh
)