
Conference:ACM Conference on Computer and Communications Security (CCS)
CCF level:CCF A
Categories:network and information security
Year:2023
Num:25
8
Title:
ParBFT: Faster Asynchronous BFT Consensus with a Parallel Optimistic Path
ParBFT:具有并行优化路径的更快异步BFT共识
Authors:****

Key words:
Byzantine fault tolerance, Byzantine generals, consensus, blockchain
拜占庭容错,拜占庭将军,共识,区块链
Abstract:****
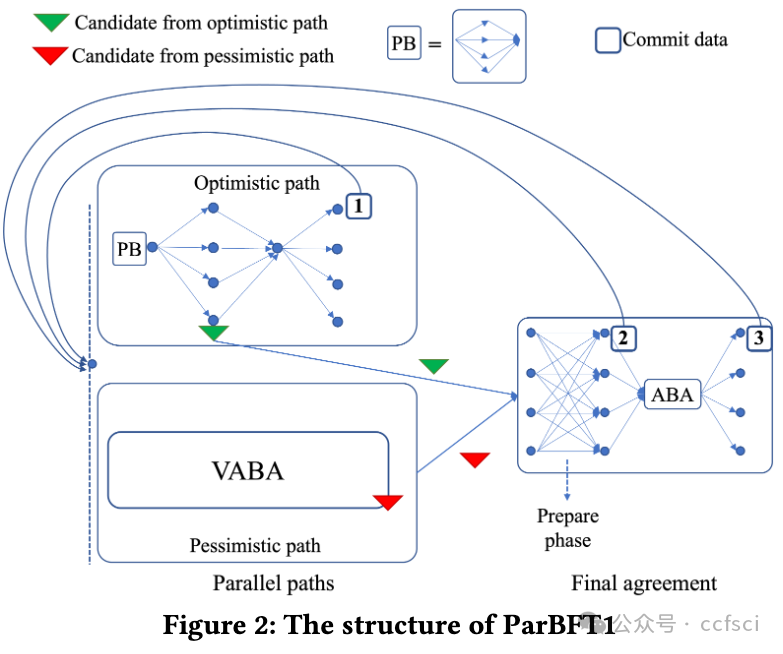
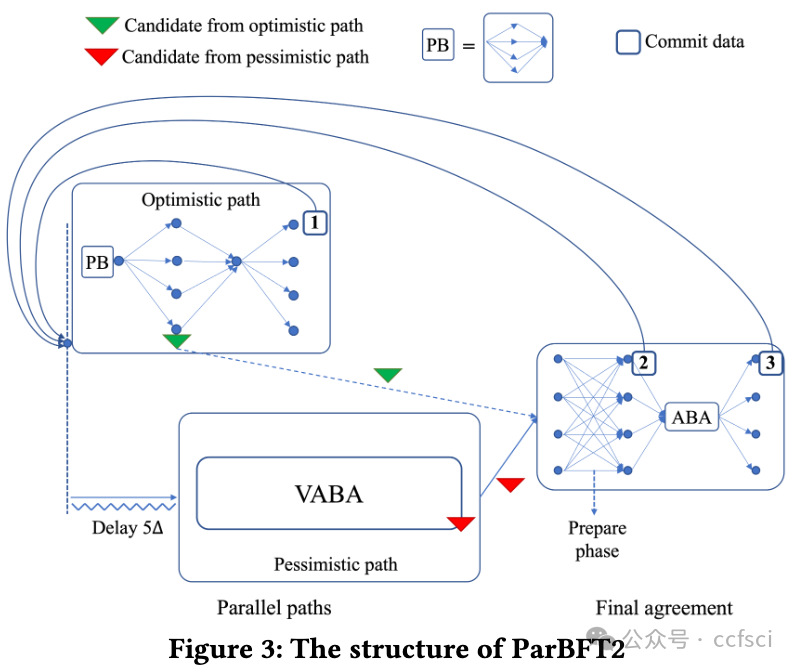
To reduce latency and communication overhead of asynchronous Byzantine Fault Tolerance (BFT) consensus, an optimistic path is often added, with Ditto and BDT as state-of-the-art representatives. These protocols first attempt to run an optimistic path that is typically adapted from partially-synchronous BFT and promises good performance in good situations. If the optimistic path fails to make progress, these protocols switch to a pessimistic path after a timeout, to guarantee liveness in an asynchronous network. This design crucially relies on an accurate estimation of the network delay Δ to set the timeout parameter correctly. A wrong estimation of Δ can lead to either premature or delayed switching to the pessimistic path, hurting the protocol's efficiency in both cases. To address the above issue, we propose ParBFT, which employs a parallel optimistic path. As long as the leader of the optimistic path is non-faulty, ParBFT ensures low latency without requiring an accurate estimation of the network delay. We propose two variants of ParBFT, namely ParBFT1 and ParBFT2, with a trade-off between latency and communication. ParBFT1 simultaneously launches the two paths, achieves lower latency under a faulty leader, but has a quadratic message complexity even in good situations. ParBFT2 reduces the message complexity in good situations by delaying the pessimistic path, at the cost of a higher latency under a faulty leader. Experimental results demonstrate that ParBFT outperforms Ditto or BDT. In particular, when the network condition is bad, ParBFT can reach consensus through the optimistic path, while Ditto and BDT suffer from path switching and have to make progress using the pessimistic path.
为了减少异步拜占庭容错(BFT)共识的延迟和通信开销,通常会增加一条乐观路径,其中最先进的代表是 Ditto 和 BDT。这些协议首先尝试运行一条乐观路径,该路径通常由部分同步 BFT 改编而来,并承诺在良好的情况下具有良好的性能。如果乐观路径无法取得进展,这些协议会在超时后切换到悲观路径,以保证异步网络中的有效性。这种设计主要依赖于对网络延迟 Δ 的准确估计,以正确设置超时参数。对 Δ 的错误估计会导致过早或延迟切换到悲观路径,在这两种情况下都会损害协议的效率。为解决上述问题,我们提出了采用并行乐观路径的 ParBFT。只要乐观路径的领导者没有问题,ParBFT 就能确保低延迟,而无需准确估计网络延迟。我们提出了 ParBFT 的两个变体,即 ParBFT1 和 ParBFT2,并在延迟和通信之间进行了权衡。ParBFT1 可同时启动两条路径,在领导者出现故障的情况下可实现较低的延迟,但即使在良好的情况下也会产生二次信息复杂度。ParBFT2 通过延迟悲观路径降低了良好情况下的信息复杂度,但代价是在领导者出错的情况下延迟时间较长。实验结果表明,ParBFT 优于 Ditto 或 BDT。特别是当网络状况不佳时,ParBFT 可以通过乐观路径达成共识,而 Ditto 和 BDT 则受到路径切换的影响,不得不使用悲观路径取得进展。
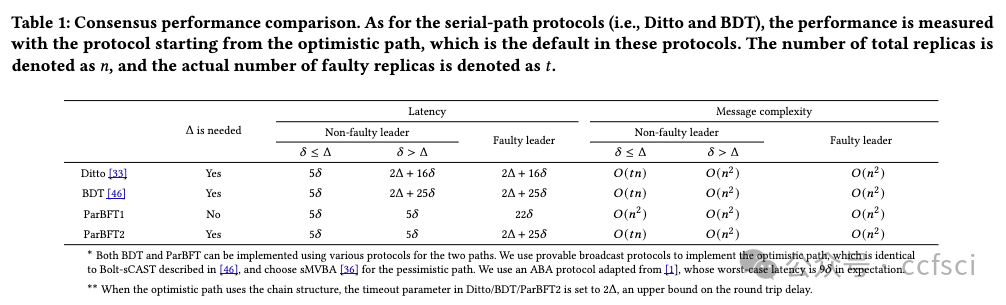
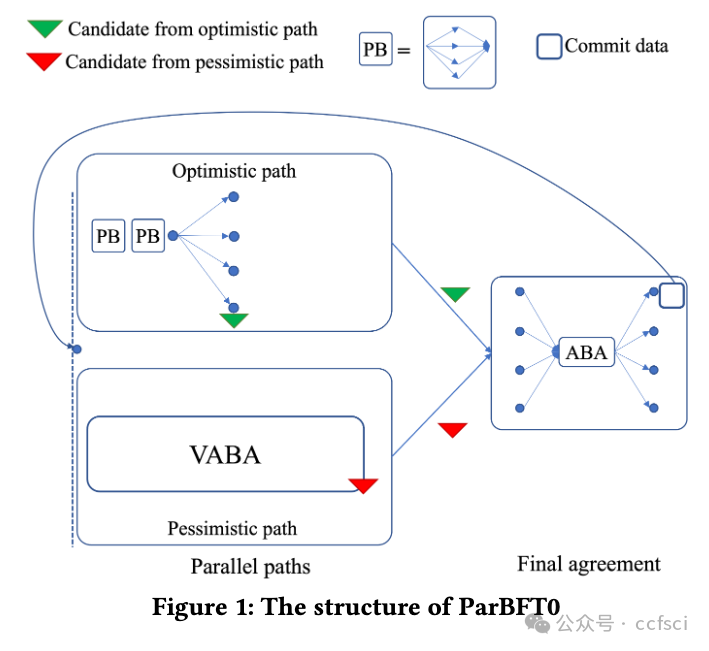
注:Provable Broadcast (PB),Asynchronous Binary Agreement (ABA) protocol,Validated Asynchronous Byzantine Agreement (VABA) protocols
Pdf link:
https://dl.acm.org/doi/10.1145/3576915.3623101
9
Title:
Abraxas: Throughput-Efficient Hybrid Asynchronous Consensus
Abraxas:吞吐量高效的混合异步共识
Authors:****

Key words:
State Machine Replication, Asynchrony, Hybrid Protocol
状态机复制、异步、混合协议
Abstract:****
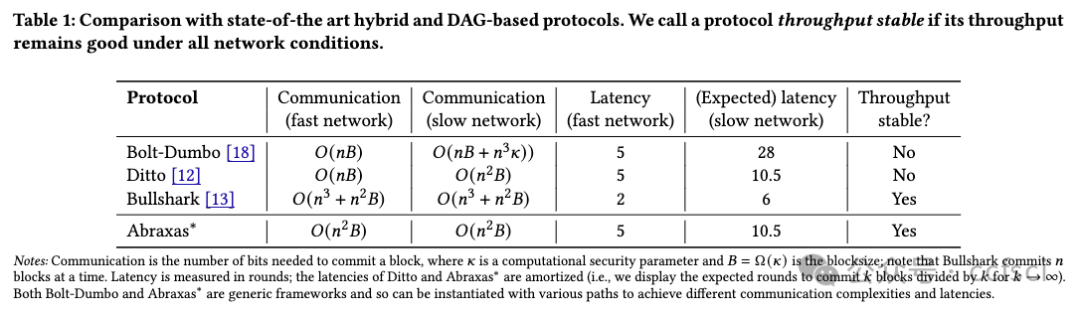
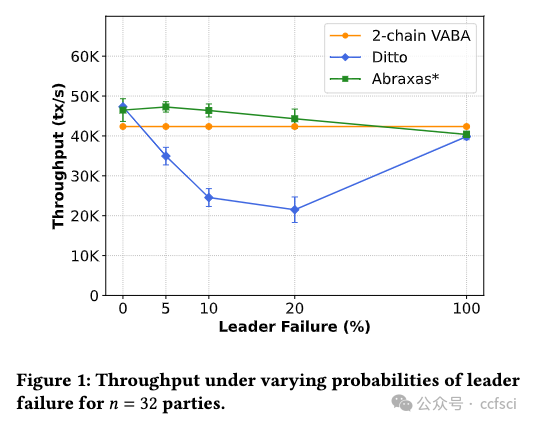
Protocols for state-machine replication (SMR) often trade off performance for resilience to network delay. In particular, protocols for asynchronous SMR tolerate arbitrary network delay but sacrifice throughput/latency when the network is fast, while partially synchronous protocols have good performance in a fast network but fail to make progress if the network experiences high delay. Existing hybrid protocols are resilient to arbitrary network delay and have good performance when the network is fast, but suffer from high overhead (''thrashing'') if the network repeatedly switches between being fast and slow, e.g., in a network that is typically fast but has intermittent message delays. We propose Abraxas, a generic approach for constructing a hybrid protocol from any ''fast'' protocol Πfast and asynchronous protocolΠslow to achieve (1) security and performance equivalent to Πslow under arbitrary network behavior, and (2) performance equivalent to Πfast when conditions are favorable. We instantiate Abraxas with the best existing protocols for Πfast (Jolteon) and Πslow (2-chain VABA), and show experimentally that the resulting protocol significantly outperforms Ditto, the previous state-of-the-art hybrid protocol.
状态机复制(SMR)协议通常以性能换取对网络延迟的适应能力。特别是,异步状态机复制协议可容忍任意网络延迟,但在网络速度较快时,会牺牲吞吐量/延迟,而部分同步协议在快速网络中性能良好,但如果网络延迟较高,则无法取得进展。现有的混合协议能抵御任意网络延迟,在网络快速时性能良好,但如果网络在快速和慢速之间反复切换,例如,在通常快速但有间歇性信息延迟的网络中,则会出现高开销("thrashing")。我们提出的 Abraxas 是一种通用方法,用于从任意 "快 "协议Πfast 和异步协议Πslow 构建混合协议,以实现:(1) 在任意网络行为下等同于Πslow 的安全性和性能;(2) 在条件有利时等同于Πfast 的性能。我们将 Abraxas 与现有的最佳 Πfast 协议(Jolteon)和 Πslow 协议(2-chain VABA)进行实例化,并通过实验证明,所产生的协议大大优于之前最先进的混合协议 Ditto。
Pdf link:
https://dl.acm.org/doi/10.1145/3576915.3623191
10
Title:
Analyzing the Real-World Security of the Algorand Blockchain
分析 Algorand 区块链在现实世界中的安全性
Authors:****

Key words:
State Machine Replication, Asynchrony, Blockchain
状态机复制、异步、区块链
Abstract:****
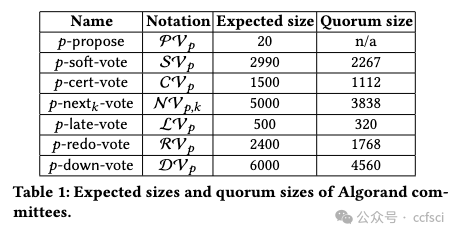
The Algorand consensus protocol is interesting both in theory and in practice. On the theoretical side, to achieve adaptive security, it introduces the novel idea of player replaceability, where each step of the protocol is executed by a different randomly selected committee whose members remain secret until they send their first and only message. The protocol provides consistency under arbitrary network conditions and liveness under intermittent network partitions. On the practical side, the protocol is used to secure the Algorand cryptocurrency, whose total value is approximately 850M at the time of writing. The Algorand protocol in use differs substantially from the protocols described in the published literature on Algorand. Despite its significance, it lacks a formal analysis. In this work, we describe and analyze the Algorand consensus protocol as deployed today in Algorand's ecosystem. We show that the overall protocol framework is sound by characterizing network conditions and parameter settings under which the protocol can be proven secure.
Algorand 共识协议在理论和实践上都很有趣。在理论方面,为了实现自适应安全性,该协议引入了 "参与者可替换性 "的新理念,即协议的每一步都由随机选择的不同委员会执行,这些委员会的成员在发送第一条也是唯一一条信息之前都是保密的。该协议可在任意网络条件下保持一致性,并在间歇性网络分区下保持有效性。在实际应用方面,该协议用于保护 Algorand 加密货币的安全,在撰写本文时,该加密货币的总价值约为 8.5 亿美元。使用中的 Algorand 协议与已发表的 Algorand 文献中描述的协议有很大不同。尽管它非常重要,但却缺乏正式的分析。在这项工作中,我们描述并分析了目前部署在 Algorand 生态系统中的 Algorand 共识协议。我们通过描述网络条件和参数设置来证明整个协议框架是合理的,在这些条件和参数设置下,协议可以被证明是安全的。
Pdf link:
https://dl.acm.org/doi/10.1145/3576915.3623167
11
Title:
Fait Accompli Committee Selection: Improving the Size-Security Tradeoff of Stake-Based Committees
既成事实委员会的选择:改善基于stake的委员会的规模与安全权衡
Authors:****
Key words:
Consensus; Delegation; Distributed ledgers; Committee selection
共识;授权;分布式账本;委员会选举
Abstract:****
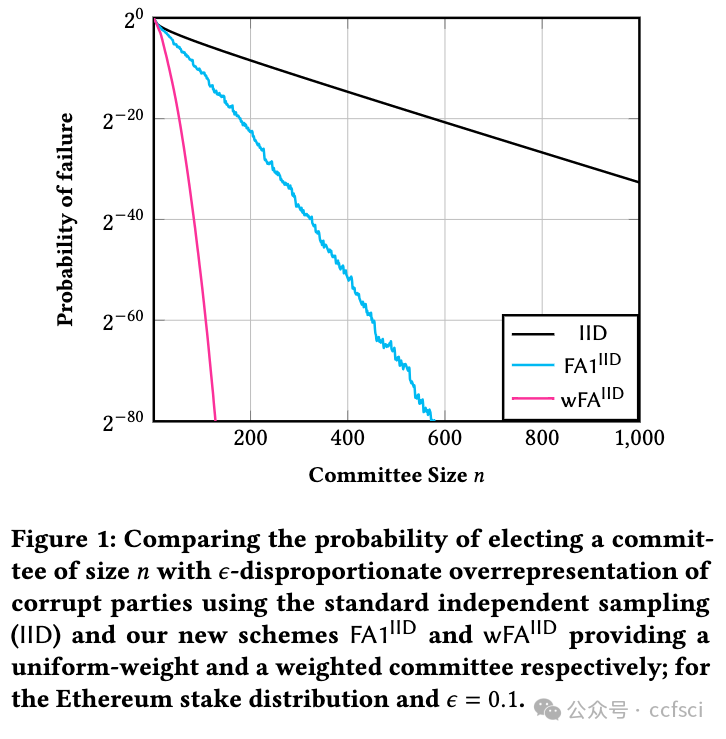
We study the problem of committee selection in the context of proof-of-stake consensus mechanisms or distributed ledgers. These settings determine a family of participating parties---each of which has been assigned a non-negative ''stake''---and are subject to an adversary that may corrupt a subset of the parties. The challenge is to select a committee of participants that accurately reflects the proportion of corrupt and honest parties, as measured by stake, in the full population. The trade-off between committee size and the probability of selecting a committee that over-represents the corrupt parties is a fundamental factor in both security and efficiency of proof-of-stake consensus, as well as committee-run layer-two protocols. We propose and analyze several new committee selection schemes that improve upon existing techniques by adopting low-variance assignment of certain committee members that hold significant stake. These schemes provide notable improvements to the size--security trade-off arising from the stake distributions of many deployed ledgers.
我们在权益证明共识机制或分布式账本的背景下研究委员会选择问题。这些设置确定了一系列参与方------每个参与方都被分配了一个非负的"股份"------并且受到可能破坏参与方子集的对手的影响。面临的挑战是选择一个参与者委员会,该委员会能够准确反映腐败团体和诚实团体在全体中的比例(按股份衡量)。委员会规模和选择一个过多代表腐败方的委员会的可能性之间的权衡是权益证明共识以及委员会运行的第二层协议的安全性和效率的基本因素。我们提出并分析了几种新的委员会选择方案,这些方案通过对持有大量股份的某些委员会成员采用低方差分配来改进现有技术。这些方案显着改善了许多已部署账本的权益分配带来的规模安全权衡。
Pdf link:
https://dl.acm.org/doi/10.1145/3576915.3623194
12
Title:
LedgerLocks: A Security Framework for Blockchain Protocols Based on Adaptor Signatures
LedgerLocks:基于适配器签名的区块链协议安全框架
Authors:****

Key words:
Adaptor Signatures, Universal Composability, Security
适配器签名、通用可组合性、安全性
Abstract:****
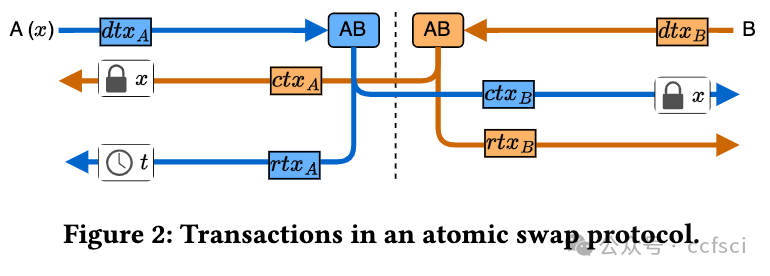
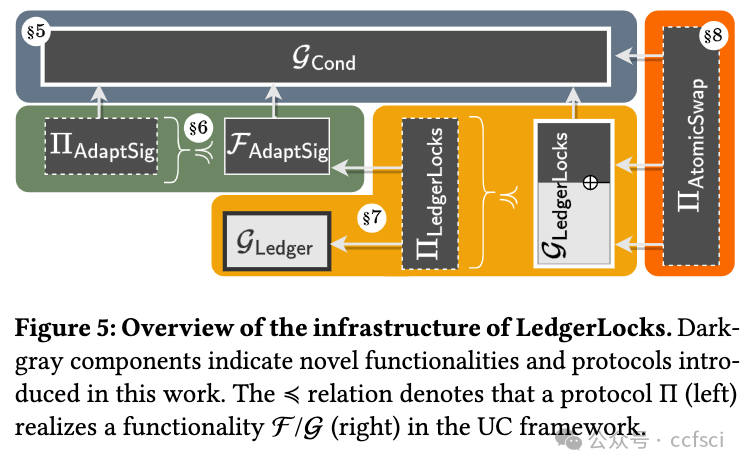
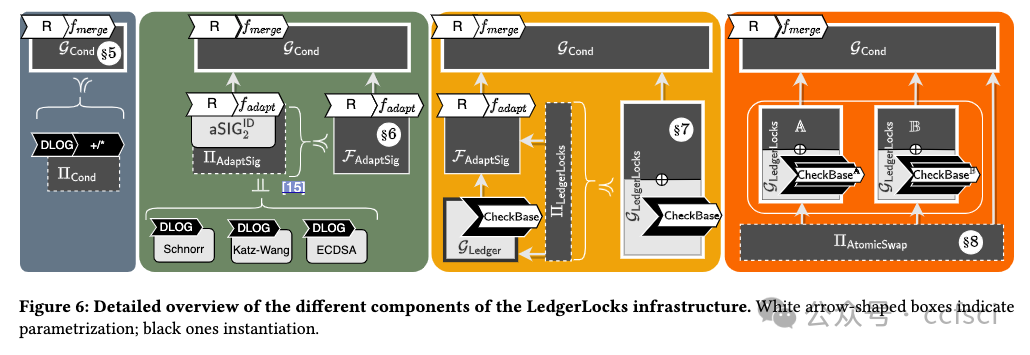
The scalability and interoperability challenges in current cryptocurrencies have motivated the design of cryptographic protocols that enable efficient applications on top and across widely used cryptocurrencies such as Bitcoin or Ethereum. Examples of such protocols include (virtual) payment channels, atomic swaps, oracle-based contracts, deterministic wallets, and coin mixing services. Many of these protocols are built upon minimal core functionalities supported by a wide range of cryptocurrencies. Most prominently, adaptor signatures (AS) have emerged as a powerful tool for constructing blockchain protocols that are (mostly) agnostic to the specific logic of the underlying cryptocurrency. Even though AS-based protocols are built upon the same cryptographic principles, there exists no modular and faithful way for reasoning about their security. Instead, all the works analyzing such protocols focus on reproving how adaptor signatures are used to cryptographically link transactions while considering highly simplified blockchain models that do not capture security-relevant aspects of transaction execution in blockchain-based consensus. To help this, we present LedgerLocks, a framework for the secure design of AS-based blockchain applications in the presence of a realistic blockchain. LedgerLocks defines the concept of AS-locked transactions, transactions whose publication is bound to the knowledge of a cryptographic secret. We argue that AS-locked transactions are the common building block of AS-based blockchain protocols and we define GLedgerLocks a realistic ledger model in the Universal Composability framework with built-in support for AS-locked transactions. As LedgerLocks abstracts from the cryptographic realization of AS-locked transactions, it allows protocol designers to focus on the blockchain-specific security considerations instead.
当前加密货币的可扩展性和互操作性挑战促使人们设计加密协议,以便在广泛使用的加密货币(如比特币或以太坊)之上和之间实现高效的应用。此类协议的示例包括(虚拟)支付渠道、原子交换、基于预言机的合约、确定性钱包和硬币混合服务。许多此类协议都建立在各种加密货币支持的最小核心功能之上。最突出的是,适配器签名 (AS) 已成为构建区块链协议的强大工具,这些协议(大部分)与底层加密货币的特定逻辑无关。即使基于 AS 的协议建立在相同的加密原理之上,也没有模块化和可靠的方法来推理它们的安全性。相反,所有分析此类协议的工作都侧重于证明如何使用适配器签名以加密方式链接交易,同时考虑高度简化的区块链模型,这些模型不会捕获基于区块链的共识中交易执行的安全相关方面。为了实现这一点,我们提出了 LedgerLocks,这是一个在存在现实区块链的情况下基于 AS 的区块链应用程序的安全设计框架。LedgerLocks 定义了 AS 锁定交易的概念,即交易的发布与加密秘密的知识绑定在一起。我们认为 AS 锁定交易是基于 AS 的区块链协议的共同构建块,我们在 Universal Composability 框架中定义了 GLedgerLocks 这个现实的账本模型,内置了对 AS 锁定交易的支持。由于 LedgerLocks 从 AS 锁定交易的加密实现中抽象出来,因此它允许协议设计者专注于特定于区块链的安全考虑。



Pdf link:
https://dl.acm.org/doi/10.1145/3576915.3623149
13
Title:
Phoenix: Detect and Locate Resilience Issues in Blockchain via Context-Sensitive Chaos
Phoenix:通过上下文敏感混沌检测和定位区块链中的弹性问题
Authors:****

Key words:
blockchain systems, chaos engineering, bug reproduce
区块链系统、混沌工程、bug重现
Abstract:****
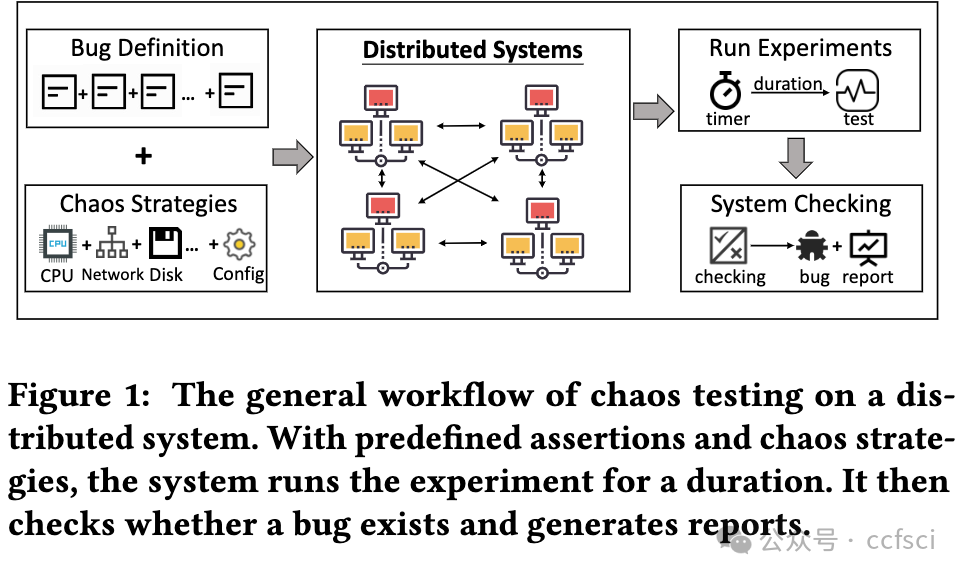
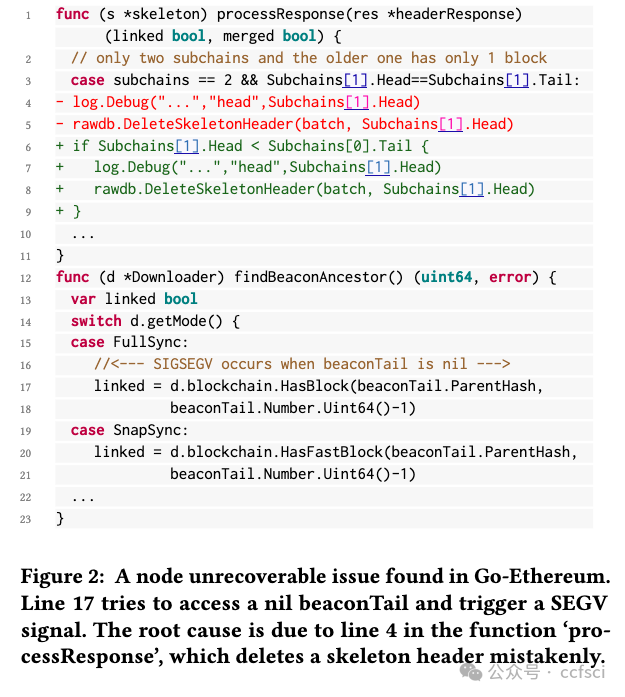
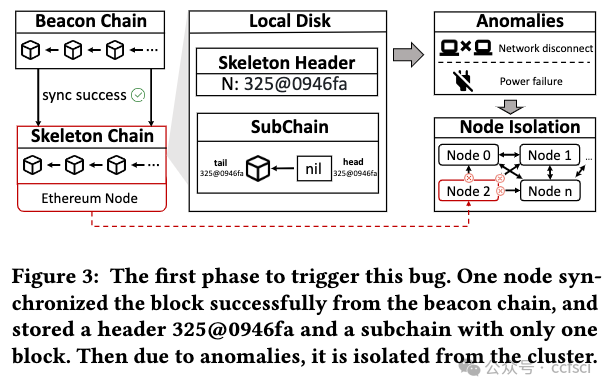
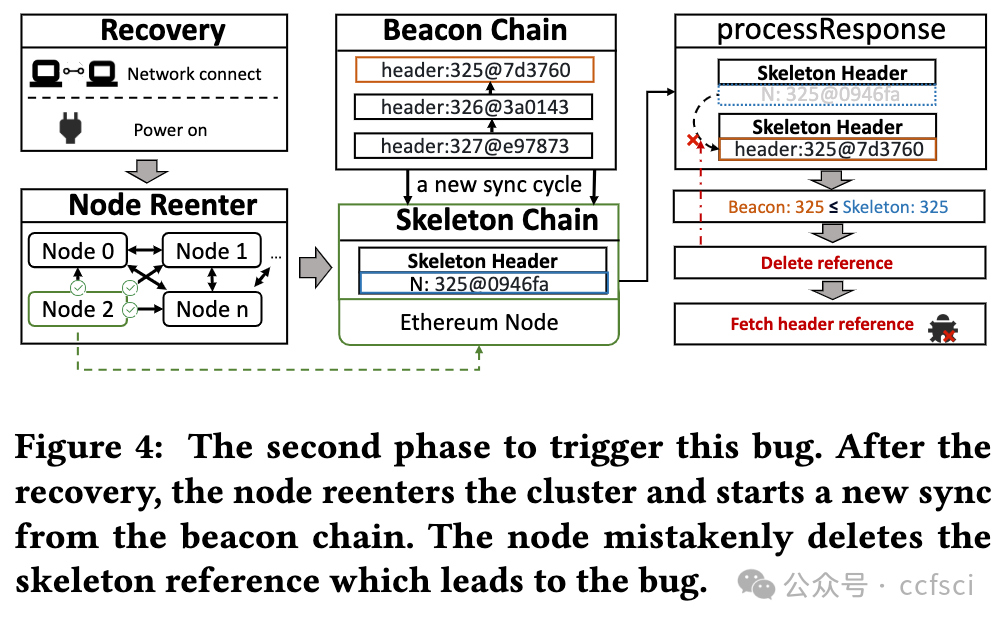
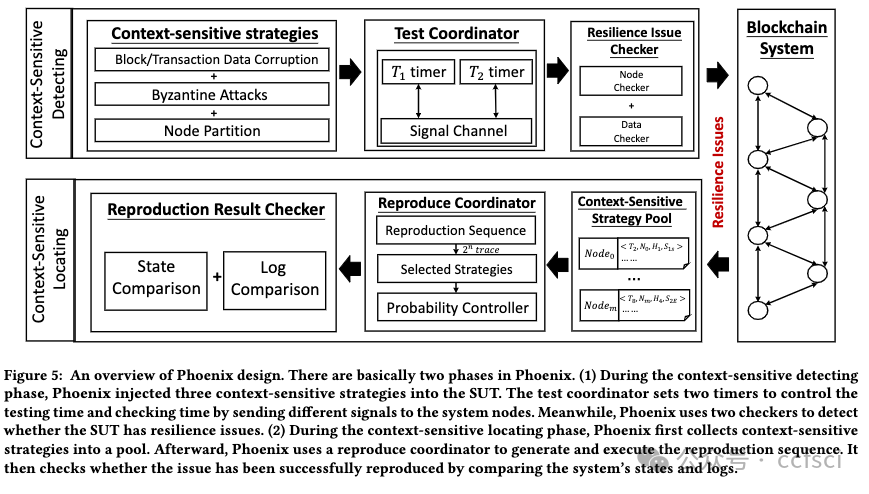
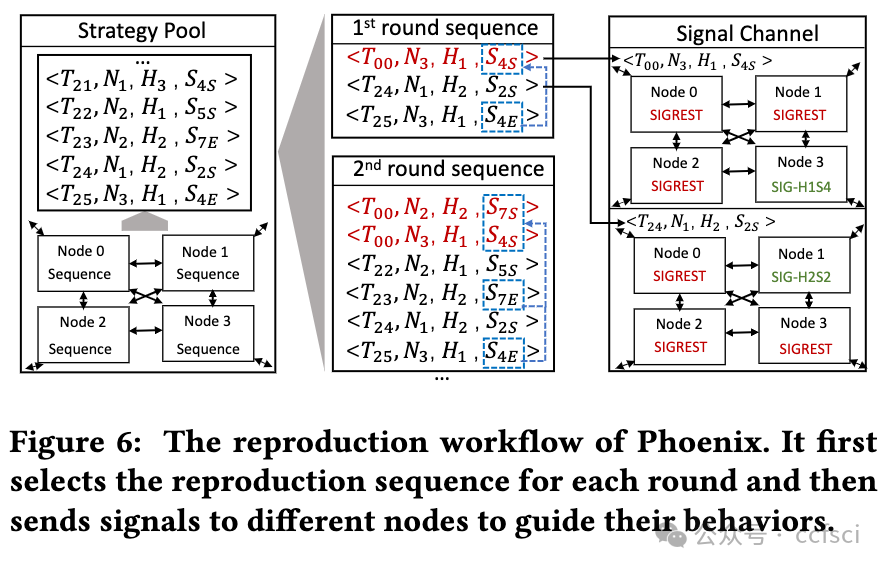
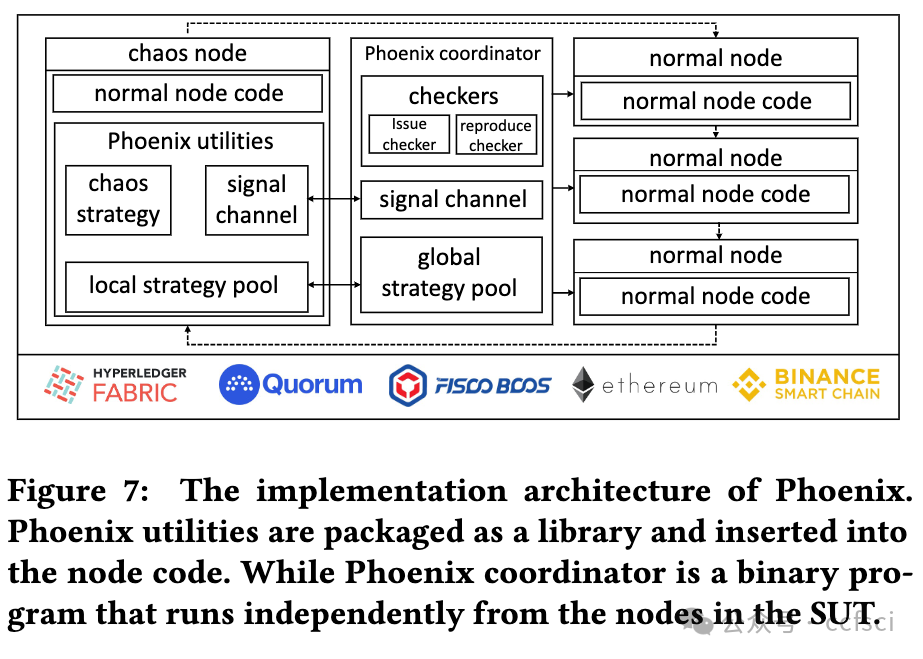
Resilience is vital to blockchain systems and helps them automatically adapt and continue providing their service when adverse situations occur, e.g., node crashing and data discarding. However, due to the vulnerabilities in their implementation, blockchain systems may fail to recover from the error situations, resulting in permanent service disruptions. Such vulnerabilities are called resilience issues. In this paper, we propose Phoenix, a system that helps detect and locate blockchain systems' resilience issues by context-sensitive chaos. First, we identify two typical types of resilience issues in blockchain systems: node unrecoverable and data unrecoverable. Then, we design three context-sensitive chaos strategies tailored to the blockchain feature. Additionally, we create a coordinator to effectively trigger resilience issues by scheduling these strategies. To better analyze them, we collect and sort all strategies into a pool and generate a reproducing sequence to locate and reproduce those issues. We evaluated Phoenix on 5 widely used commercial blockchain systems and detected 13 previous-unknown resilience issues. Besides, Phoenix successfully reproduces all of them, with 5.15 steps on average. The corresponding developers have fixed these issues. After that, the chaos resistance time of blockchains is improved by 143.9% on average. This indicates that Phoenix can significantly improve the resilience of these blockchains.
弹性对于区块链系统至关重要,可帮助它们在发生不利情况(例如节点崩溃和数据丢弃)时自动适应并继续提供服务。但是,由于其实施中的漏洞,区块链系统可能无法从错误情况中恢复,从而导致永久性服务中断。此类漏洞称为弹性问题。在本文中,我们提出了 Phoenix,这是一个通过上下文敏感混沌帮助检测和定位区块链系统弹性问题的系统。首先,我们确定了区块链系统中两种典型的弹性问题:节点不可恢复和数据不可恢复。然后,我们设计了三种针对区块链特性的上下文敏感混沌策略。此外,我们创建了一个协调器,通过调度这些策略来有效触发弹性问题。为了更好地分析它们,我们将所有策略收集并分类到一个池中,并生成一个重现序列来定位和重现这些问题。我们在 5 个广泛使用的商业区块链系统上评估了 Phoenix,并检测到 13 个以前未知的弹性问题。此外,Phoenix 成功重现了所有问题,平均需要 5.15 步。相应的开发人员已经修复了这些问题。之后区块链的抗混乱时间平均提升了143.9%,这意味着Phoenix可以显著提高这些区块链的弹性。
Pdf link:
https://dl.acm.org/doi/10.1145/3576915.3623071
篇幅有限,下篇文章将继续分享剩余论文

关注ccfsci,持续接收区块链最新论文
洞察区块链技术发展趋势
Follow us to keep receiving the latest blockchain papers
Insight into Blockchain Technology Trends