看题目,将base64解密,然后dump下来,再拉进ida里,发现为tea加密
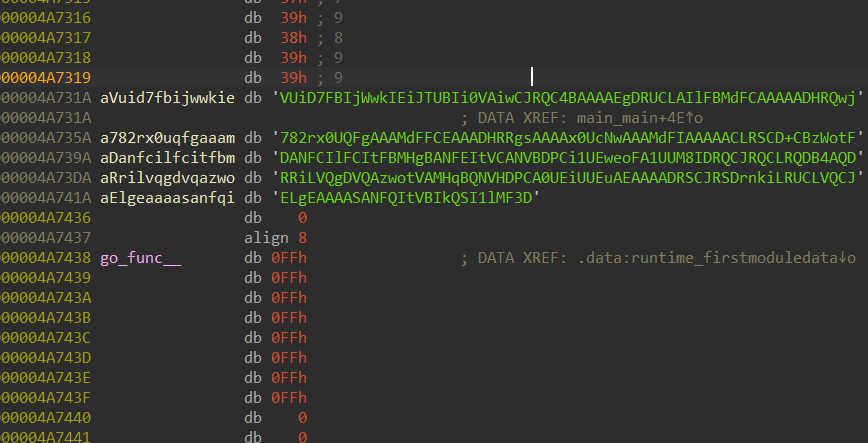
在tea加密中得到key
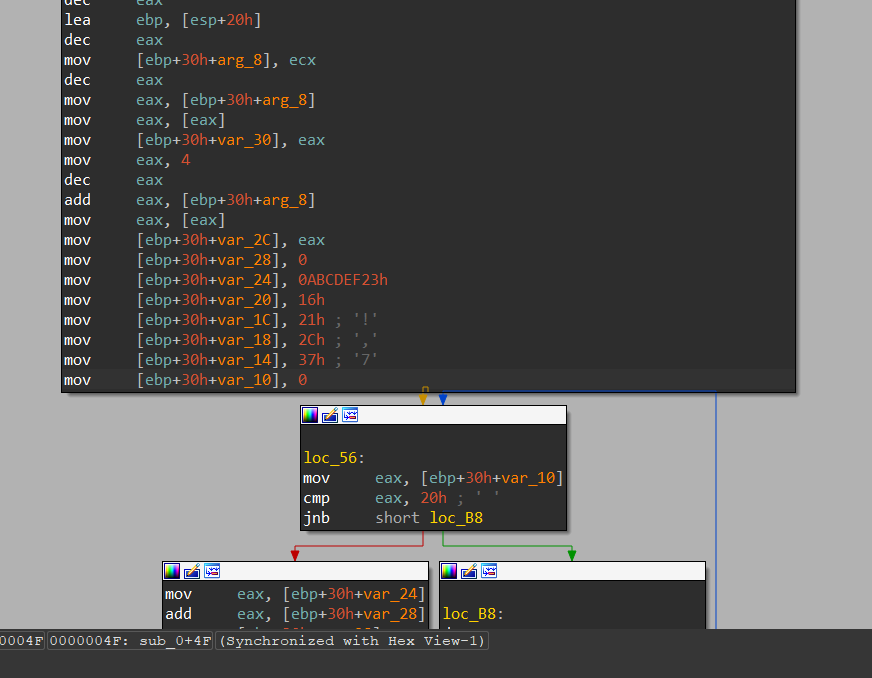
密文就是另外的一个文件
exp
python
import re
from ctypes import *
import libnum
def decrypt(v, k):
v0, v1 = c_uint32(v[0]), c_uint32(v[1])
delta = 0xABCDEF23
k0, k1, k2, k3 = k[0], k[1], k[2], k[3]
total = c_uint32(delta * 32)
for i in range(32):
v1.value -= ((v0.value << 4) + k2) ^ (v0.value + total.value) ^ ((v0.value >> 5) + k3)
v0.value -= ((v1.value << 4) + k0) ^ (v1.value + total.value) ^ ((v1.value >> 5) + k1)
total.value -= delta
return v0.value, v1.value
s = """
mov [ebp+30h+var_20], 16h
mov [ebp+30h+var_1C], 21h ; '!'
mov [ebp+30h+var_18], 2Ch ; ','
mov [ebp+30h+var_14], 37h ; '7'
"""
p = r', (\w+)h'
m = re.findall(p, s)
k = ['0x' + x for x in m]
print(k)
k = [int(j, 16) for j in k]
print(k)
with open(r"D:\desktop\REVERSE\nssctf\shellcode\outputdir\flag.enc", 'rb') as f:
enc = f.read()
print(enc)
e = list(map(lambda i: (int(enc[i:i + len(enc) // 10][::-1].hex(), 16)), range(0, len(enc), len(enc) // 10)))
print(e)
print(b''.join(
map(lambda x: libnum.n2s(x[0])[::-1] + libnum.n2s(x[1])[::-1],
list(map(lambda x: decrypt([e[x], e[x + 1]], k), range(0, len(e), 2))))))