
Conference:International Conference on Parallel and Distributed Systems (ICPADS)
CCF level:CCF C
Categories:Computer Architecture/Parallel and Distributed Computing/Storage Systems
Year:2023
Num:28
8
Title:
Money Laundering Detection on Ethereum: Applying Traditional Approaches to New Scene
以太坊上的洗钱检测:将传统方法应用于新场景
Authors:****

Key words:
Ethereum; Anti-money laundering; Money Laundering Detection; Blockchain Security
以太坊;反洗钱;洗钱检测;区块链安全
Abstract:****
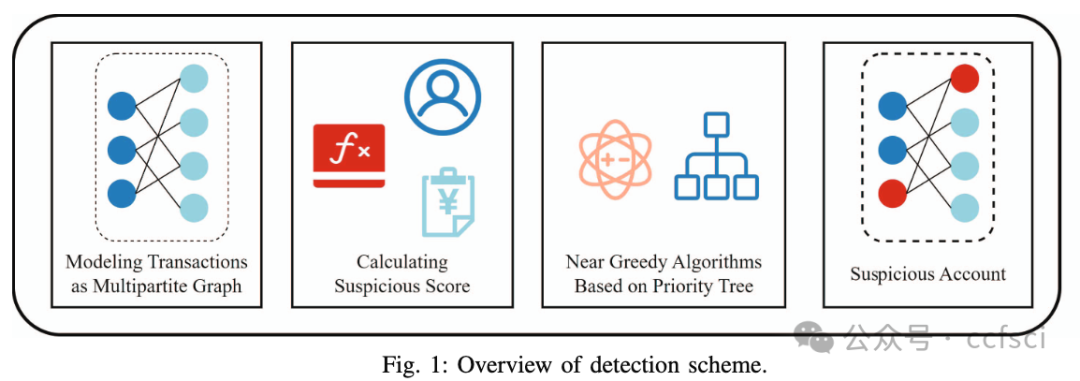
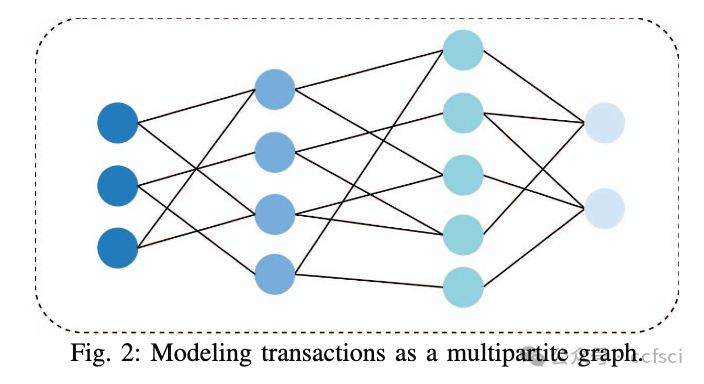
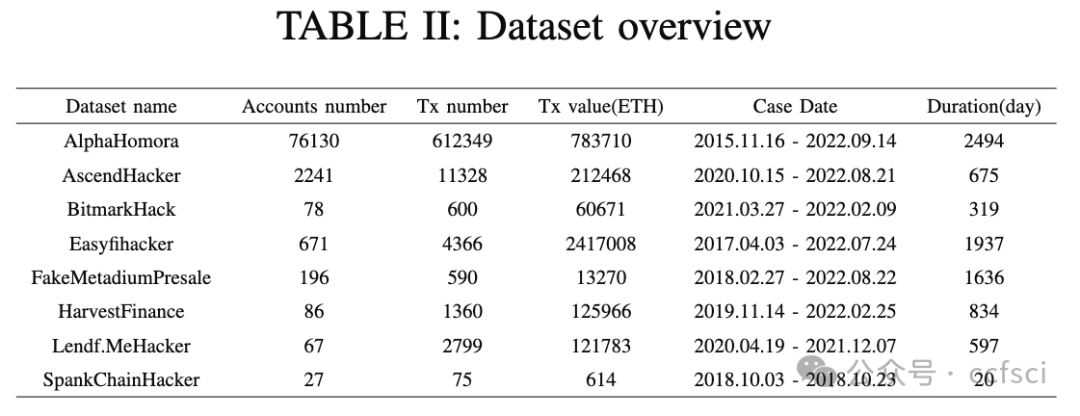
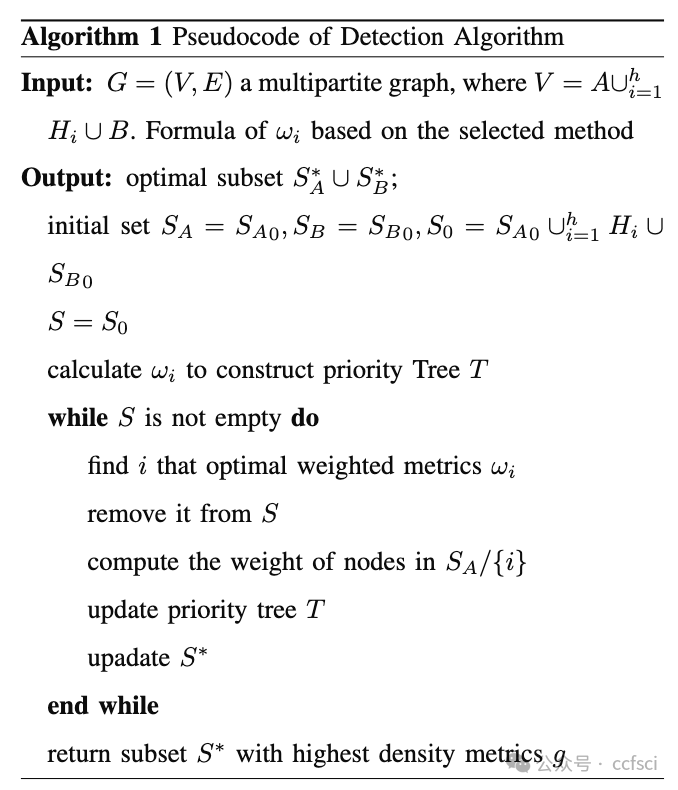
With the continuous evolution of blockchain technology, cryptocurrency platforms such as Ethereum have emerged as centers for digital asset transactions and smart contracts deployment. However, this nascent financial ecosystem also introduces potential money laundering risks. The traditional financial industry has accumulated significant antimoney laundering (AML) experience and technical means for monitoring and detecting money laundering activities. Yet, the adaptability of these established AML algorithms in the context of blockchain remains unclear. This paper aims to investigate the practical adaptability of traditional AML algorithms on Ethereum data through empirical experiments. We gather eight real-world money laundering case datasets collected from Ethereum and conduct experiments using three traditional AML algorithms on these datasets. We evaluate the performance of these algorithms from various angles, including precision, recall, and the distribution of detected accounts' labels in comparison to the original datasets. It turns out algorithms demonstrate distinct performance in diverse money laundering cases, indicating that the adaptability of traditional AML algorithms on Ethereum data presents certain adaptability and limitations. Holoscope's accuracy demonstrates the value of dense subgraph properties in Ethereum money laundering detection, and further research can be conducted based on this model framework combined with the money laundering characteristics of Ethereum. Our study provides valuable insights for strengthening AML mechanisms on blockchain platforms and offers guidance for further research on detecting money laundering accounts in blockchain environments.
随着区块链技术的不断演进,以太坊等加密货币平台逐渐成为数字资产交易与智能合约部署的中心。然而,这一新生的金融生态也引入了潜在的洗钱风险。传统金融行业积累了大量的反洗钱经验以及监测、检测洗钱活动的技术手段,但这些成熟的反洗钱算法在区块链环境下的适应性尚不明确。本文旨在通过实证实验探究传统反洗钱算法在以太坊数据上的实际适应性。我们从以太坊中收集了8个真实洗钱案例数据集,并使用3种传统反洗钱算法在这些数据集上进行实验,从查准率、召回率、检测账户标签分布等多个角度评估这些算法相对于原始数据集的性能。结果表明,算法在不同的洗钱案例中表现出不同的性能,表明传统反洗钱算法在以太坊数据上的适应性存在一定的适应性和局限性。Holoscope 的准确性证明了稠密子图特性在以太坊洗钱检测中的价值,可以在此模型框架基础上结合以太坊的洗钱特点开展进一步的研究。我们的研究为加强区块链平台上的反洗钱机制提供了宝贵的见解,并为进一步研究在区块链环境中检测洗钱账户提供了指导。
Pdf link:
https://ieeexplore.ieee.org/document/10476300
9
Title:
What Determines the Price of NFTs?
什么决定了 NFT 的价格?
Authors:****

Key words:
NFTs, blockchain, artworks, market pricing, big data
NFT、区块链、艺术品、市场定价、大数据
Abstract:****
In the evolving landscape of digital art, NonFungible Tokens (NFTs) have emerged as a groundbreaking platform, bridging the realms of art and technology. NFTs serve as the foundational framework that has revolutionized the market for digital art, enabling artists to showcase and monetize their creations in unprecedented ways. NFTs combine metadata stored on the blockchain with off-chain data, such as images, to create a novel form of digital ownership. It is not fully understood how these factors come together to determine NFT prices. In this study, we analyze both on-chain and off-chain data of NFT collections trading on OpenSea to understand what influences NFT pricing. Our results show that while text and image data of the NFTs can be used to explain price variations within collections, the extracted features do not generalize to new, unseen collections. Furthermore, we find that an NFT collection's trading volume often relates to its online presence, like social media followers and website traffic.
在不断发展的数字艺术领域,非同质化代币 (NFT) 已成为一个突破性的平台,连接了艺术和技术领域。NFT 是彻底改变数字艺术市场的基础框架,使艺术家能够以前所未有的方式展示和货币化他们的作品。NFT 将存储在区块链上的元数据与图像等链下数据相结合,以创建一种新颖的数字所有权形式。目前尚不完全清楚这些因素如何结合在一起决定 NFT 的价格。在本研究中,我们分析了在 OpenSea 上交易的 NFT 收藏品的链上和链下数据,以了解影响 NFT 定价的因素。我们的结果表明,虽然 NFT 的文本和图像数据可用于解释收藏品内的价格变化,但提取的特征并不能推广到新的、从未见过的收藏品。此外,我们发现 NFT 收藏品的交易量通常与其在线存在有关,例如社交媒体关注者和网站流量。
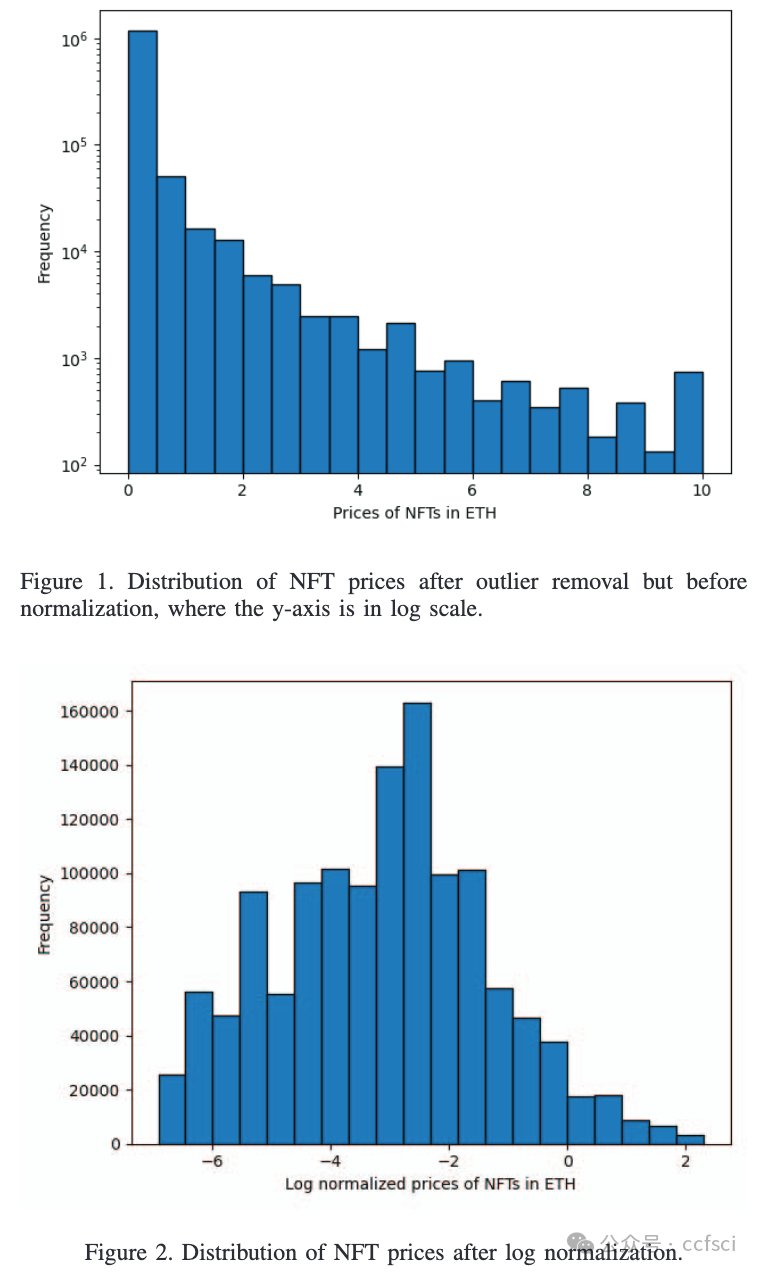
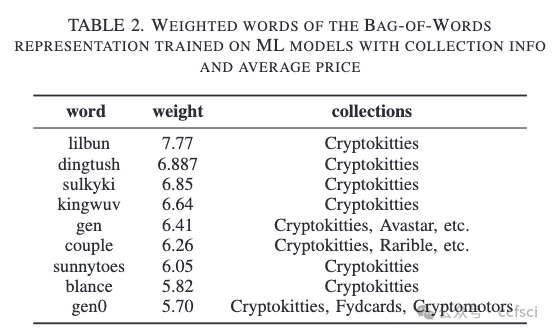
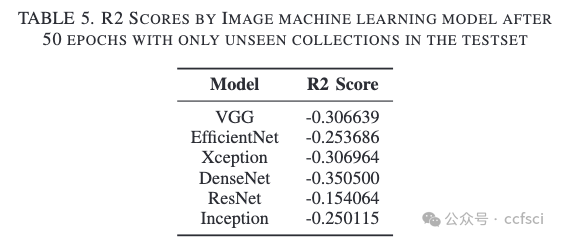
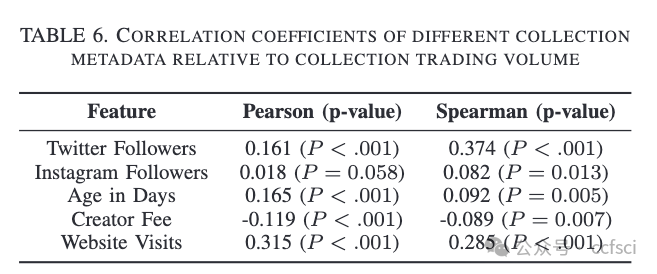
Pdf link:
https://ieeexplore.ieee.org/document/10476294
10
Title:
Data Rights Verification in the Industrial Internet: A Securing Progressive Scheme with Locked-NFTs and Adaptive Federated Learning
工业互联网中的数据权利验证:基于锁定 NFT 和自适应联邦学习的安全渐进方案
Authors:****

Key words:
Data rights verification, Locked-NFTs, Smart Contract, Adaptive federated learning, Industrial Internet
数据确权、Locked-NFT、智能合约、自适应联邦学习、工业互联网
Abstract:****
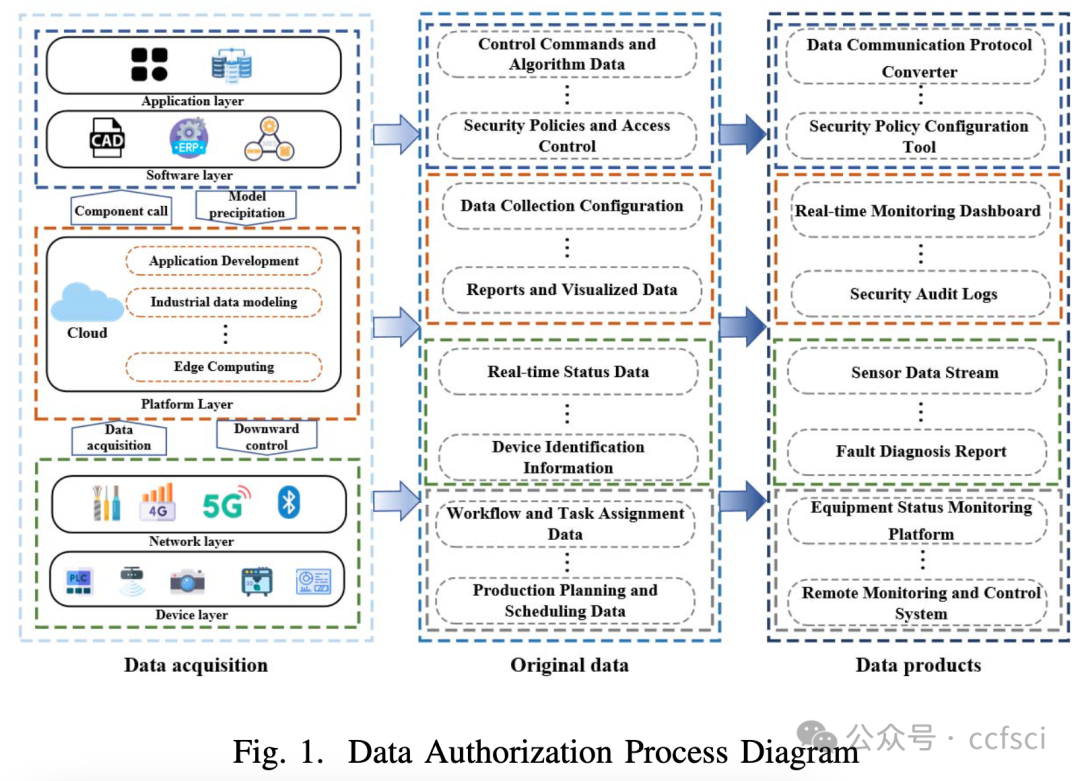
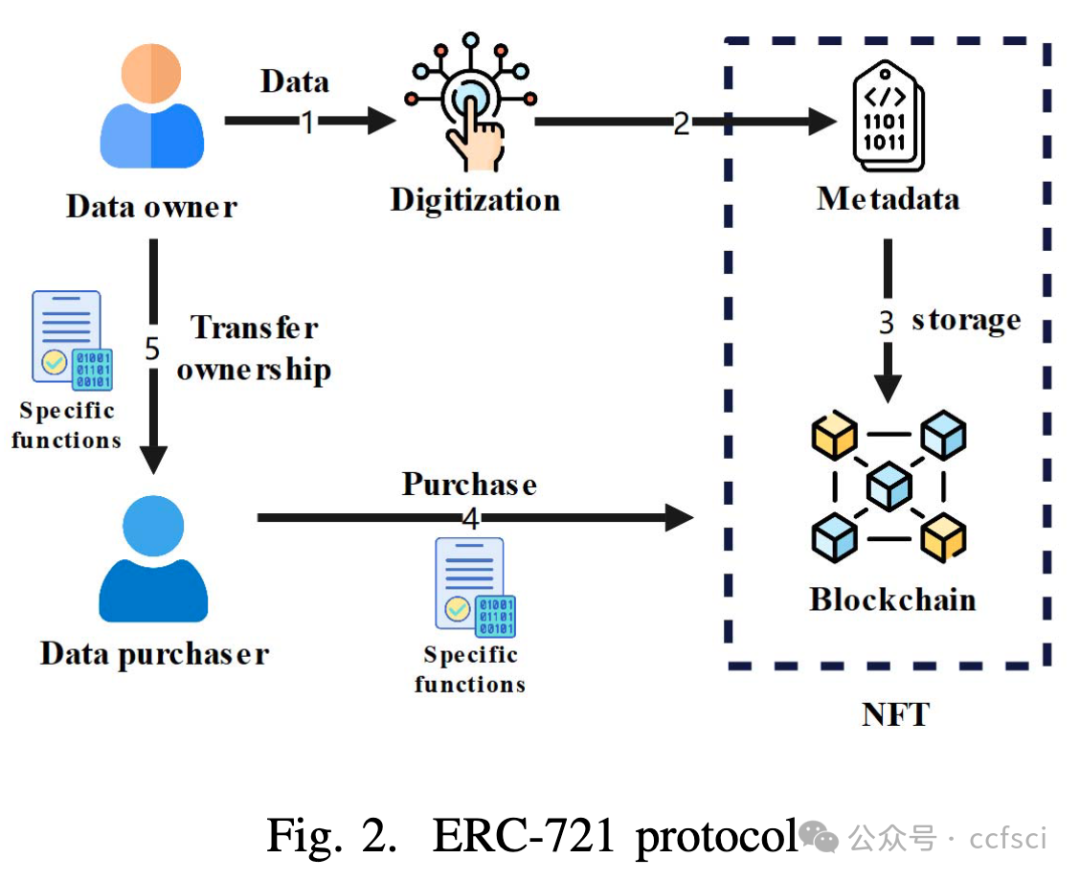
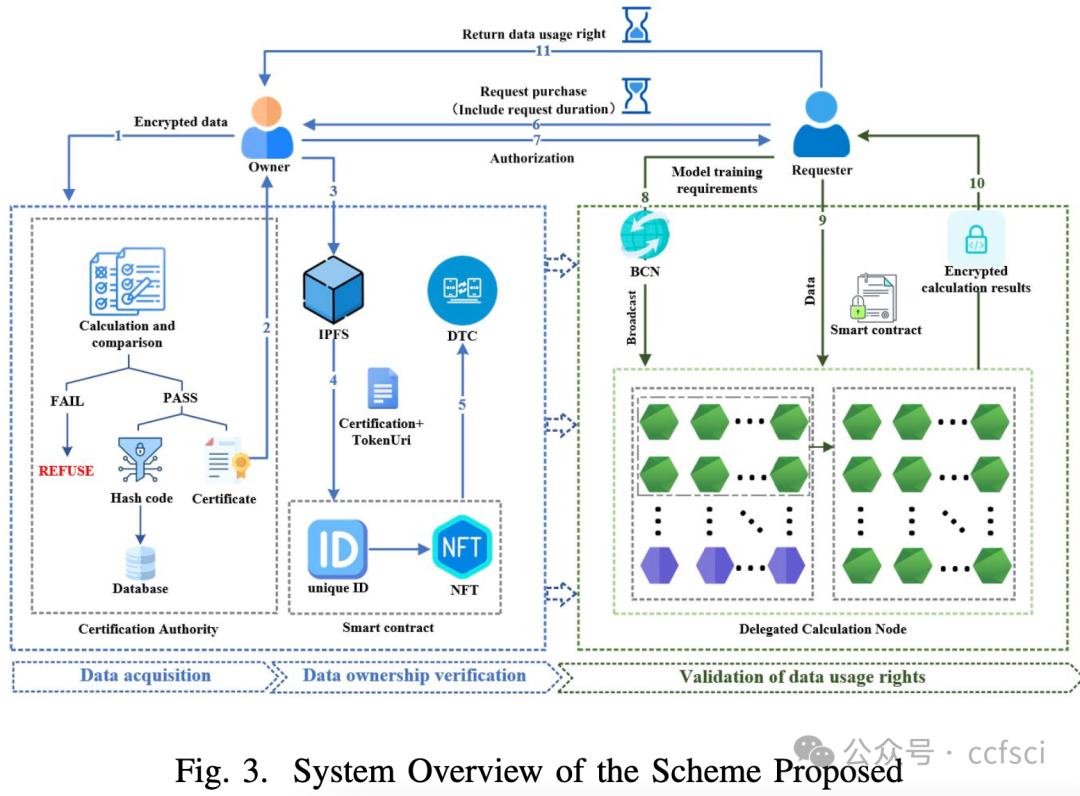
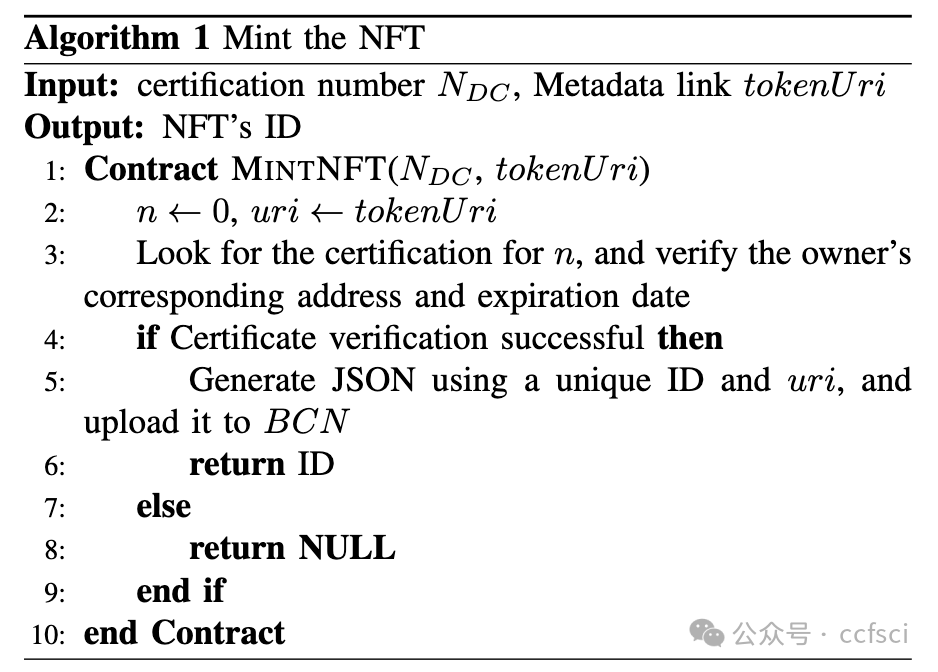
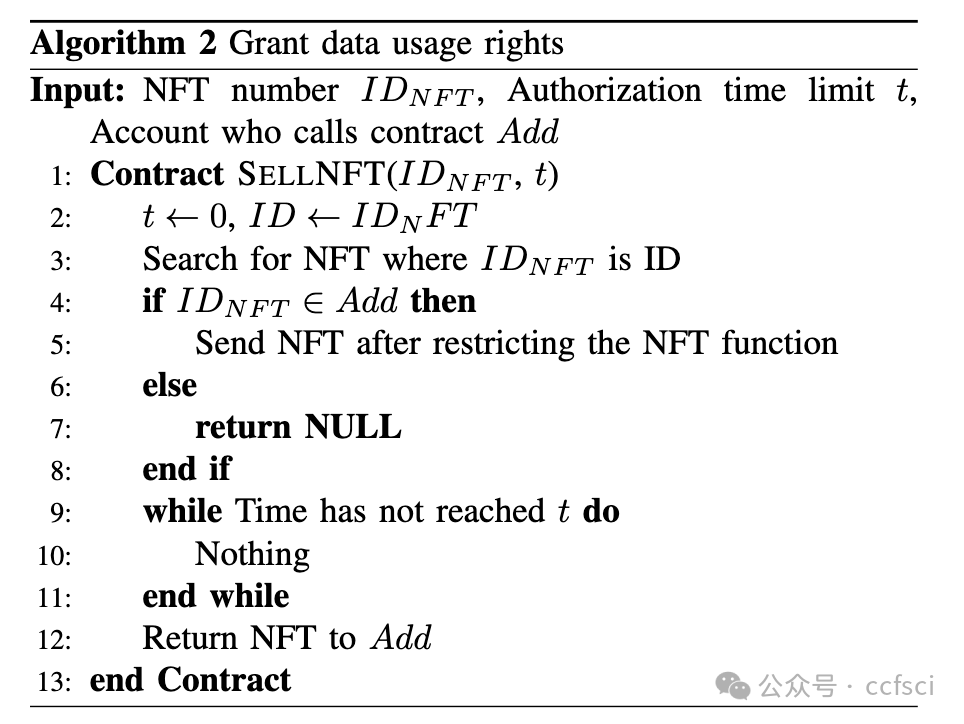
Within the context of the Industrial Internet, data has emerged as an increasingly critical asset in the domains of enterprise production, operation, and management, thereby solidifying its role as a pivotal determinant of competitive advantage for corporate entities. Nonetheless, the intrinsic characteristics of Industrial Internet data, characterized by its diverse origins, substantial volumes, and intricate privacy considerations, have given rise to issues surrounding the unambiguous establishment of data rights and inadvertent disclosure of sensitive information throughout the processes of data propagation and value transmission. To address these multifaceted challenges, this paper introduces a systematic framework for data rights verification, one that incorporates the utilization of Non-Fungible Tokens (NFTs) equipped with a secure locking mechanism in conjunction with adaptive federated learning. This proposed framework bifurcates the data rights verification process into two distinctive phases: data ownership verification and validation of data usage rights. Through the meticulous implementation of smart contracts and the adept utilization of the locking mechanism inherent within NFTs, the framework effectively dissects the intricacies of data rights, thereby ensuring contemporaneousness in data utilization and enabling controlled access. Furthermore, in the phase dedicated to the validation of data usage rights, we introduce an approach firmly rooted in the principles of adaptive federated learning. Leveraging the FedMGDA+ algorithm for distributed storage and computation, this approach successfully validates data usage rights. Empirical findings substantiate the significant advantages encapsulated within this framework, particularly in the domains of data and identity security. Notably, this framework maintains robust precision and scalability throughout the process of data rights verification for distributed model training, thereby exhibiting commendable performance in this intricate domain.
在工业互联网背景下,数据已成为企业生产、运营和管理领域中越来越重要的资产,并成为企业竞争优势的关键决定因素。然而,工业互联网数据本身具有来源多样、数量巨大、隐私保护复杂等特点,在数据传播和价值传递过程中,数据权利难以明确确立、敏感信息容易被无意泄露等问题。针对这些多方面的挑战,本文提出了一个数据权利验证的系统框架,该框架结合了具有安全锁定机制的非同质化代币 (NFT) 和自适应联邦学习。该框架将数据权利验证过程分为两个不同的阶段:数据所有权验证和数据使用权验证。通过对智能合约的细致实施和对 NFT 固有锁定机制的熟练运用,该框架有效地剖析了数据权利的复杂性,从而确保了数据使用的同步性并实现了受控访问。此外,在数据使用权验证阶段,我们引入了一种基于自适应联邦学习原理的方法。该方法利用 FedMGDA+ 算法进行分布式存储和计算,成功验证了数据使用权。实证结果证实了该框架的显著优势,特别是在数据和身份安全领域。值得注意的是,该框架在分布式模型训练的数据权验证过程中保持了强大的精度和可扩展性,从而在这个复杂的领域表现出了令人称赞的性能。
Pdf link:
https://ieeexplore.ieee.org/document/10475992
11
Title:
SecDFS: A Secure and Decentralized File System
SecDFS:安全且去中心化的文件系统
Authors:****

Key words:
Decentralized File System, Trusted Execution Environment, Consortium System
去中心化文件系统、可信执行环境、联盟系统
Abstract:****
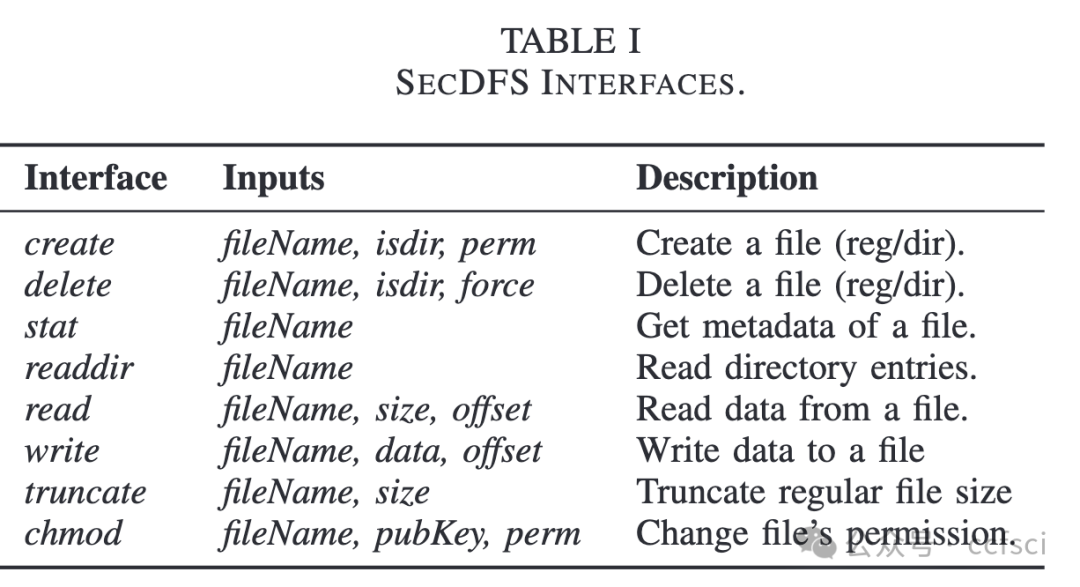
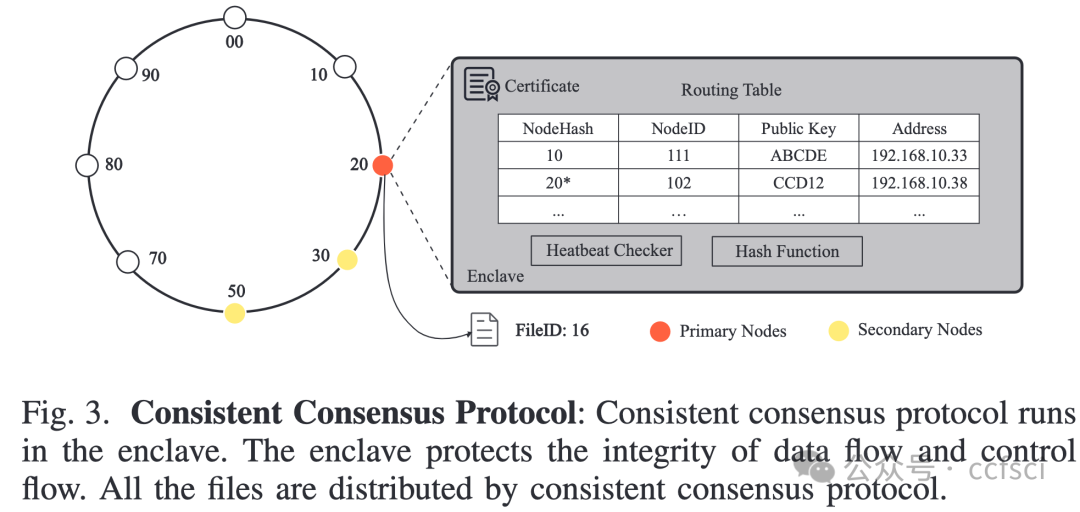
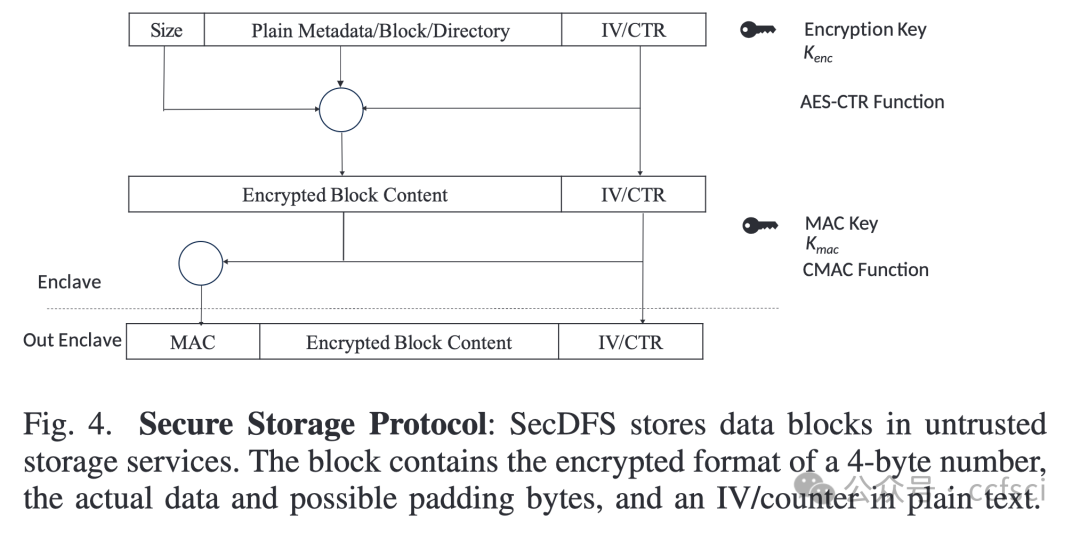
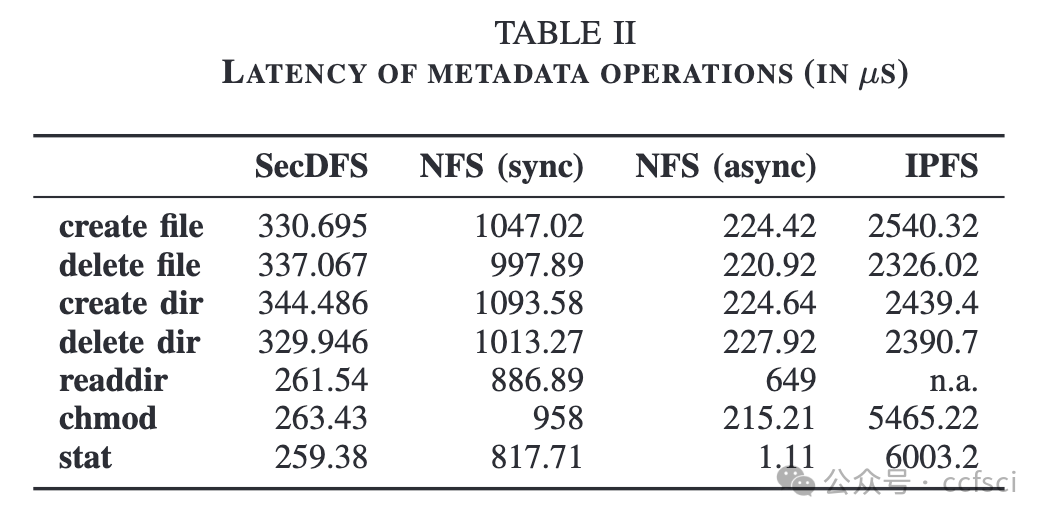
Consortium networks are usually constructed among enterprises and organizations. A consortium network is a specific type of decentralized network which only has a limited number of untrusted nodes. Consortium systems are designed to achieve consensus in such a network and provide stable and trusted services. Meanwhile, secure data sharing plays a crucial role in the consortium network, introducing new requirements to the underlying file system. Firstly, a consortium file system should be decentralized since any party of the consortium network is untrusted. Secondly, it should enforce data confidentiality and integrity and provide access control. Finally, the system should offer high performance. Existing file systems are designed for public decentralized or centralized networks and cannot meet all the above requirements. To address this problem, we present SecDFS, a decentralized, secure, high-performance file system for consortium networks. SecDFS first combines trusted execution environment and consistent hashing to design a consistent consensus protocol, through which SecDFS distributes files across consortium nodes and achieves data consensus. After that, SecDFS introduces a secure storage constructing method to protect the confidentiality and integrity of both the data and metadata, as well as a two-level cache to speed up the file system performance. We have implemented a prototype of SecDFS and performed a detailed evaluation with it. The results show that SecDFS has 74.83X latency speedup compared with the InterPlanetary File System on average.
联盟网络通常由企业和组织组成。联盟网络是一种特定类型的去中心化网络,其不受信任的节点数量有限。联盟系统旨在在这样的网络中达成共识并提供稳定可信的服务。同时,安全的数据共享在联盟网络中起着至关重要的作用,这对底层文件系统提出了新的要求。首先,联盟文件系统应该是去中心化的,因为联盟网络中的任何一方都是不受信任的。其次,它应该强制数据的机密性和完整性并提供访问控制。最后,系统应该提供高性能。现有的文件系统是为公共的去中心化或中心化网络设计的,无法满足上述所有要求。为了解决这个问题,我们提出了一个用于联盟网络的去中心化、安全、高性能的文件系统SecDFS。SecDFS首先结合可信执行环境和一致性哈希来设计一个一致性共识协议,SecDFS通过该协议在联盟节点之间分发文件并达成数据共识。随后,SecDFS引入了安全存储构建方法来保护数据和元数据的机密性和完整性,以及两级缓存来加速文件系统的性能。我们实现了SecDFS的原型并对其进行了详细的评估。结果表明,与星际文件系统相比,SecDFS的平均延迟加速为74.83倍。


Pdf link:
https://ieeexplore.ieee.org/document/10476310
12
Title:
An Incentive Mechanism for Consortium Blockchain-based Cross-Silo Federated Learning
基于联盟区块链的跨孤岛联邦学习激励机制
Authors:****

Key words:
Federated learning, incentive mechanism, blockchain, social welfare
联邦学习、激励机制、区块链、社会福利
Abstract:****
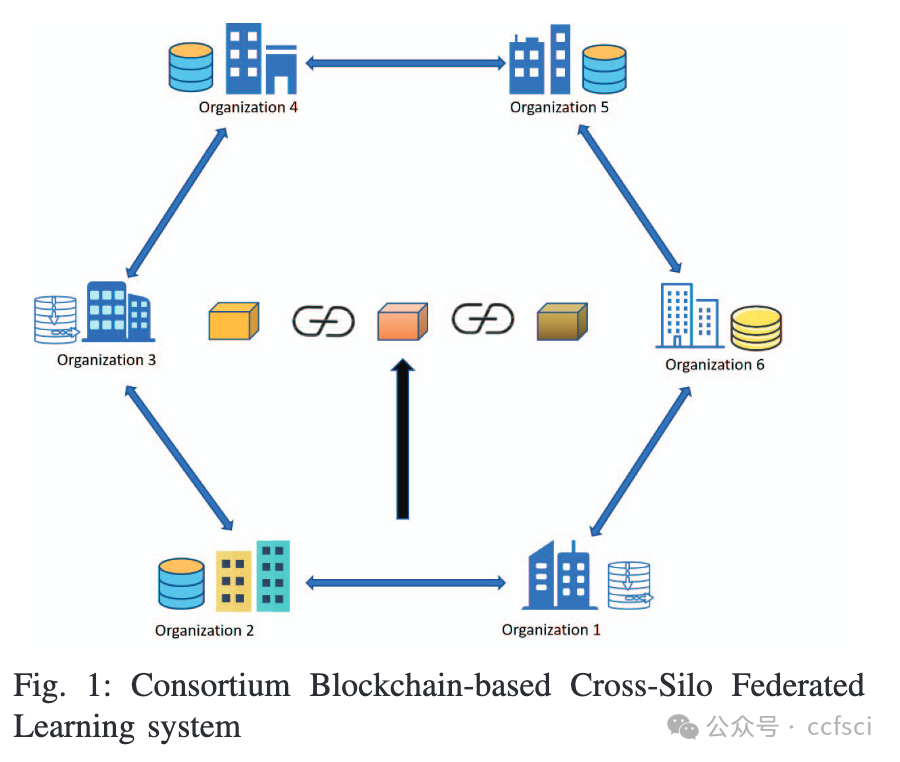
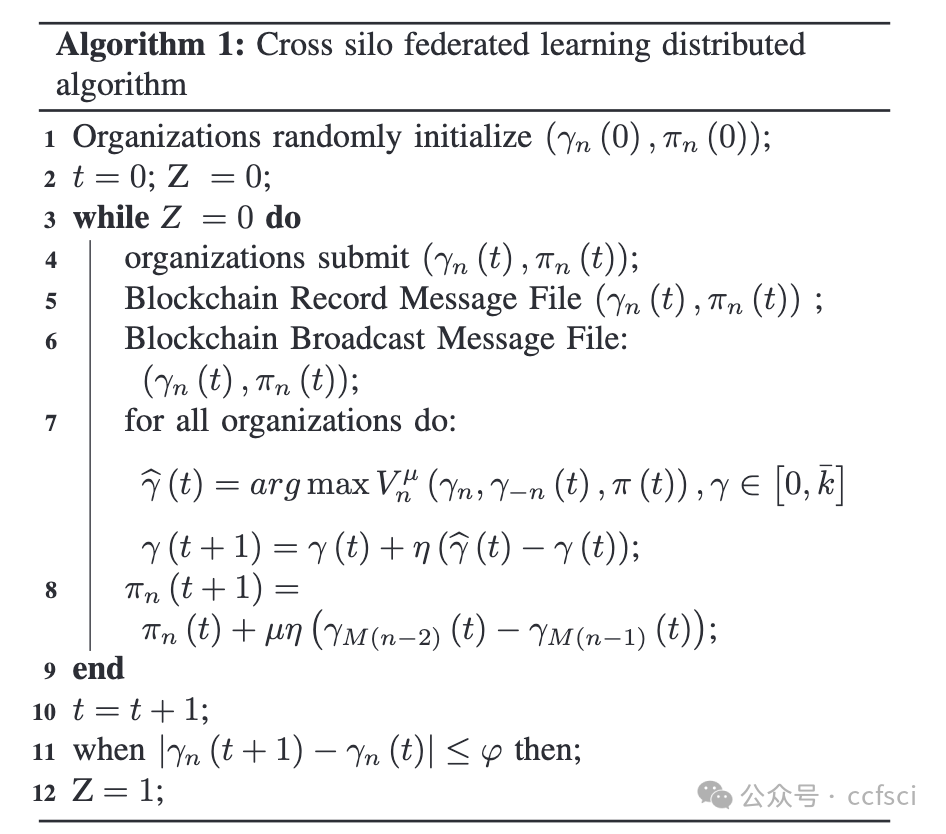
Cross-silo federated learning is a new type of machine learning, where organizations, as model owners, collaborating to train global models with local data. Nevertheless, the heterogeneity caused by differences in training costs within the organization leads to different views on training rounds among different organizations. At the same time, the organizations' communication resources are non-excludable public goods, resulting in free-rider problems. To address the aforementioned concerns, we propose a cross-silo federated learning incentive mechanism based on a consortium blockchain. The consortium blockchain coordinates the training rounds and currency transfers, as well as determines the processing capabilities of each organization's local training, and helps organizations record the training models during the training process. The mechanism models the game between organizations as non-cooperative games. We conducted a theoretical analysis of the mechanism using the MNIST dataset and demonstrated the existence of Nash equilibrium. A distributed algorithm has been proposed to maximize social welfare for organizations under information asymmetry conditions. The simulation results show that the algorithm has fast convergence.
跨孤岛联邦学习是一种新型的机器学习,各组织作为模型拥有者,通过本地数据协同训练全局模型。然而,组织内部训练成本差异带来的异质性导致不同组织对训练轮次的看法不同。同时,组织的通信资源属于非排他性公共物品,存在搭便车问题。针对上述问题,我们提出了一种基于联盟链的跨孤岛联邦学习激励机制。联盟链负责协调训练轮次和货币转账,确定各组织本地训练的处理能力,并帮助组织在训练过程中记录训练模型。该机制将组织间的博弈建模为非合作博弈。我们使用MNIST数据集对该机制进行了理论分析,证明了纳什均衡的存在性。提出了一种在信息不对称条件下最大化组织社会福利的分布式算法。仿真结果表明该算法具有快速收敛性。
Pdf link:
https://ieeexplore.ieee.org/document/10476089
13
Title:
Detecting Ethereum Phishing Scams via Multi-transaction-view Graph Attention Network
通过多交易视图图注意力网络检测以太坊钓鱼诈骗
Authors:****

Abstract:****
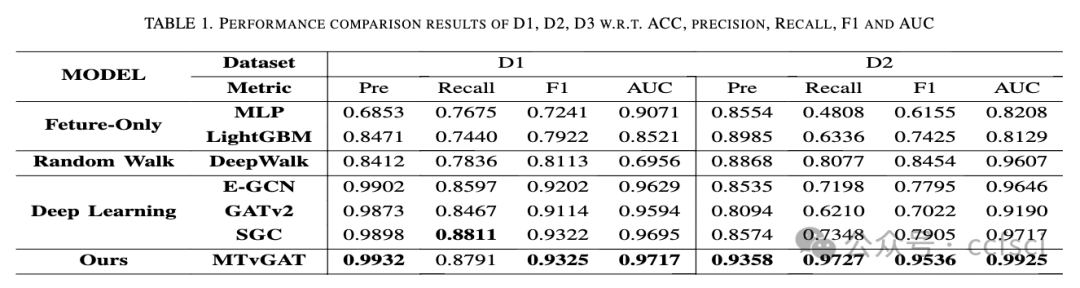
Cryptocurrency phishing scams is a significant treat to Ethereum, one of the most popular blockchain platforms. Most of existing Ethereum phishing detection methods are based on traditional machine learning or graph representation learning, which mostly rely on only statistical and structural features in local scope. In this paper, we propose Multi-transaction-view Graph Attention Network (MTvGAT), a novel phishing scam detection model that can make use of transaction patterns of different scopes. To obtain global-view information, we apply graph clustering and construct the global-view graph with multiple clusters, including all the nodes of the original transaction network. To obtain local view information, we apply neighborhood sampling, and construct local-view graphs with target nodes and their neighborhood nodes. Then, node features, edge features, and attention coefficients are aggregated to merge multi-view information into representation of nodes. We further combine global-view and local-view representations to finally identify phishing addresses from target nodes. Extensive experiments demonstrate that the proposed method can outperform existing ones with significant improvement.
xx货币钓鱼诈骗对最受欢迎的区块链平台之一以太坊来说是一大威胁。现有的以太坊钓鱼检测方法大多基于传统的机器学习或图表示学习,大多仅依赖于局部范围内的统计和结构特征。本文提出了一种新型的钓鱼诈骗检测模型------多交易视图图注意力网络(MTvGAT),可以利用不同范围的交易模式。为了获得全局视图信息,我们应用图聚类并构建具有多个聚类的全局视图图,其中包括原始交易网络的所有节点。为了获得局部视图信息,我们应用邻域采样,并构建具有目标节点及其邻域节点的局部视图图。然后,聚合节点特征、边特征和注意力系数以将多视图信息合并为节点表示。我们进一步结合全局视图和局部视图表示,最终从目标节点识别钓鱼地址。大量实验表明,所提出的方法可以显著优于现有方法。
Pdf link:
https://ieeexplore.ieee.org/document/10476281
14
Title:
Secure and Trusted Copyright Protection for Educational Data on Redactable Blockchains
可编辑区块链上教育数据的安全可信版权保护
Authors:****

Key words:
Redactable blockchain, educational multimedia data, copyright, consensus mechanism, Proof of Behavior
可编辑区块链、教育多媒体数据、版权、共识机制、行为证明
Abstract:****
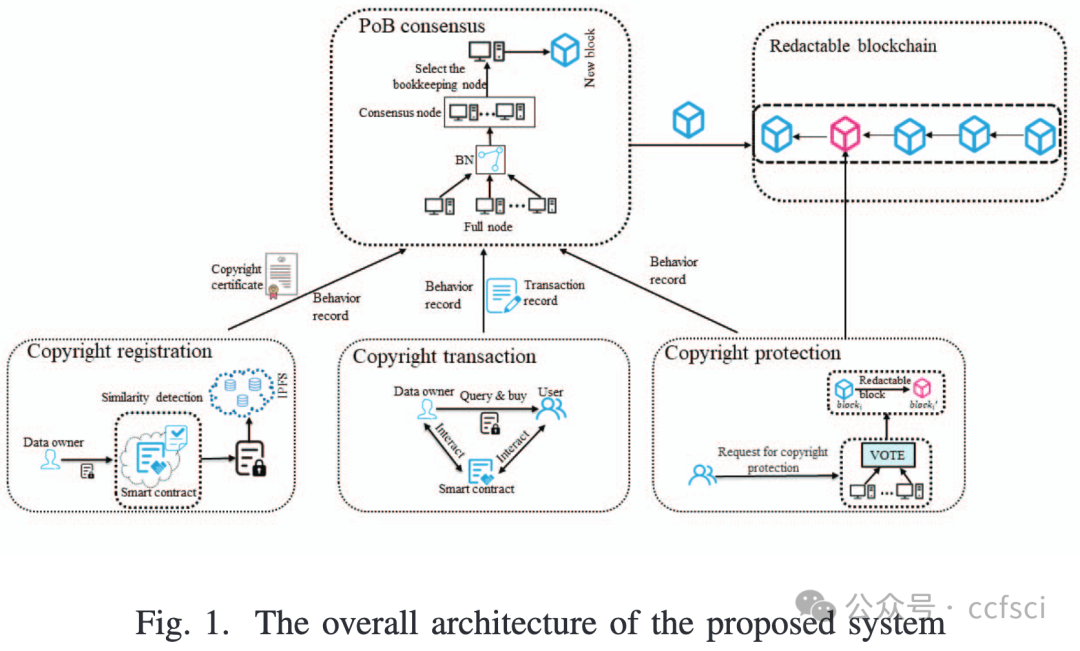
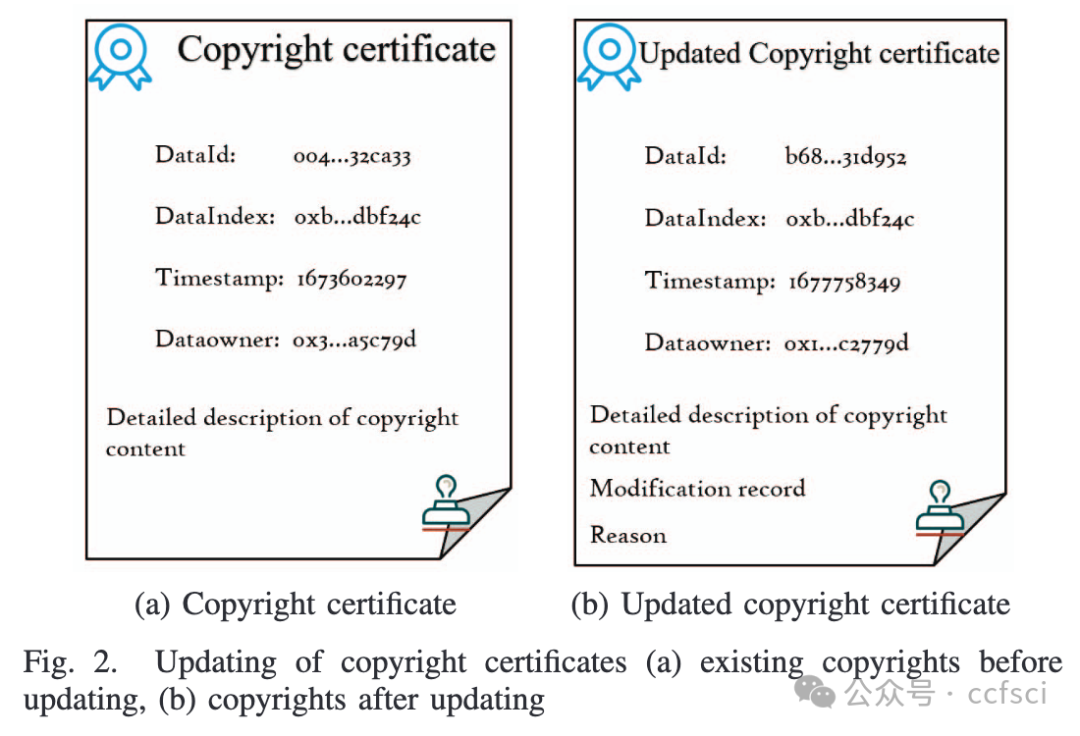
Due to the explosion of online educational resources, the protection and management of educational multimedia data have become more challenging. Blockchain has emerged as a promising technology for copyright management due to its decentralized and traceable nature. However, it still faces problems such as difficulties in copyright maintenance and delays in the consensus process, especially for educational multimedia data with large amounts of data, high demand for privacy, and many participants. This paper proposes a secure and trustworthy copyright protection method based on a redactable blockchain to address these issues. We use a decentralized chameleon hash function for copyright maintenance to enable trusted blockchain editing. This can promptly modify infringing copyrights to complete efficient copyright maintenance. For the delay during consensus, we design a consensus mechanism called Proof of Behavior (PoB) based on the Bayesian network (BN), which can achieve fast and reliable consensus by predicting user behavior and selecting highly trusted nodes to participate in consensus. Finally, We conduct simulation experiments to validate the performance of our proposed approach. Specifically, our approach effectively reduces storage space by 5%-10% comparable to other blockchain solutions and enhances system scalability and security.
由于在线教育资源的激增,教育多媒体数据的保护和管理变得更加具有挑战性。区块链凭借其去中心化和可追溯的特性,已成为一种有前途的版权管理技术。然而,它仍然面临着版权维护困难、共识过程延迟等问题,尤其是对于数据量大、隐私要求高、参与人数多的教育多媒体数据。针对这些问题,本文提出了一种基于可编辑区块链的安全可信版权保护方法。我们使用去中心化的变色龙哈希函数进行版权维护,实现可信的区块链编辑。这可以及时修改侵权版权,完成高效的版权维护。针对共识过程中的延迟,我们基于贝叶斯网络(BN)设计了一种称为行为证明(PoB)的共识机制,通过预测用户行为并选择高度可信的节点参与共识,实现快速可靠的共识。最后,我们进行了模拟实验来验证我们提出的方法的性能。具体来说,与其他区块链解决方案相比,我们的方法有效地减少了 5%-10% 的存储空间,并增强了系统的可扩展性和安全性。

Pdf link:
https://ieeexplore.ieee.org/document/10476019
篇幅有限,下篇文章将继续分享剩余论文

关注ccfsci,持续接收区块链最新论文
洞察区块链技术发展趋势
Follow us to keep receiving the latest blockchain papers
Insight into Blockchain Technology Trends