X酷APP逆向分析
这里介绍一下两种不同的挂载证书的方法。
chls.pro/ssl无法在浏览器中下载证书是什么原因解决方法:
法一
1. 挂载系统分区为读写
使用正确的挂载点来挂载系统分区为读写:
sh
su
mount -o remount,rw /dev/uijISjR/.magisk/block/system_root2. 确认挂载成功
挂载成功后,可以通过以下命令确认系统分区是否已经挂载为读写:
sh
mount | grep system_root你应该看到类似于以下的输出,表示系统分区已经挂载为读写:
sh
/dev/uijISjR/.magisk/block/system_root on /system type ext4 (rw,relatime,...)3. 复制文件
挂载成功后,再次尝试复制文件:
sh
cp /storage/emulated/0/HttpCanary/certs/87bc3517.0 /system/etc/security/cacerts/4. 恢复系统分区为只读(可选)
为了安全起见,可以在操作完成后将系统分区恢复为只读:
sh
mount -o remount,ro /dev/uijISjR/.magisk/block/system_root示例操作
以下是完整的操作步骤:
-
获取root权限:
shsu -
挂载系统分区为读写:
shmount -o remount,rw /dev/uijISjR/.magisk/block/system_root -
确认挂载成功:
shmount | grep system_root -
复制文件:
shcp /storage/emulated/0/HttpCanary/certs/87bc3517.0 /system/etc/security/cacerts/ -
恢复系统分区为只读(可选):
shmount -o remount,ro /dev/uijISjR/.magisk/block/system_root
法二
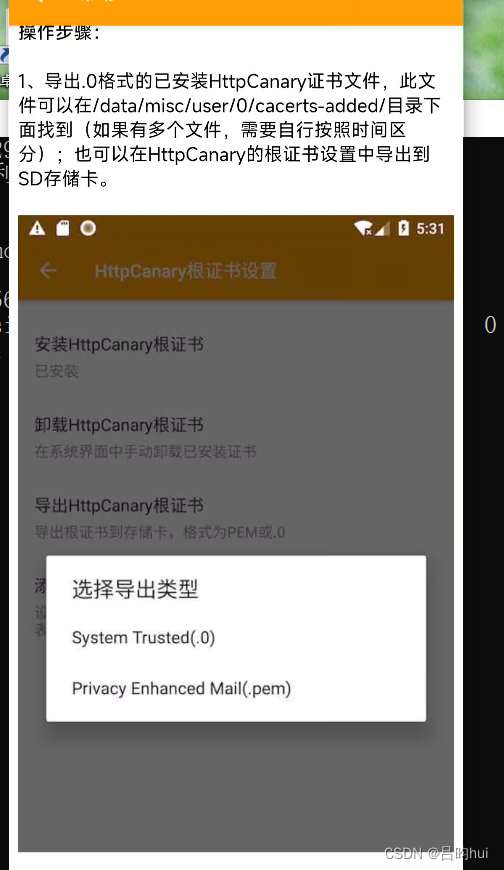
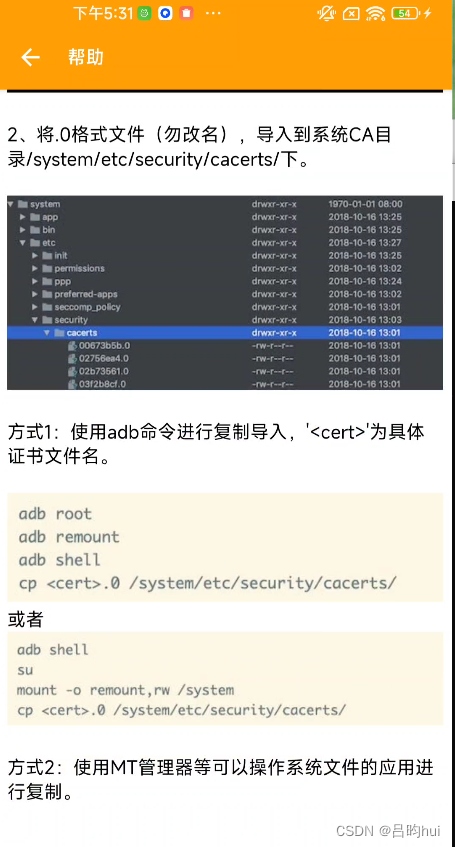
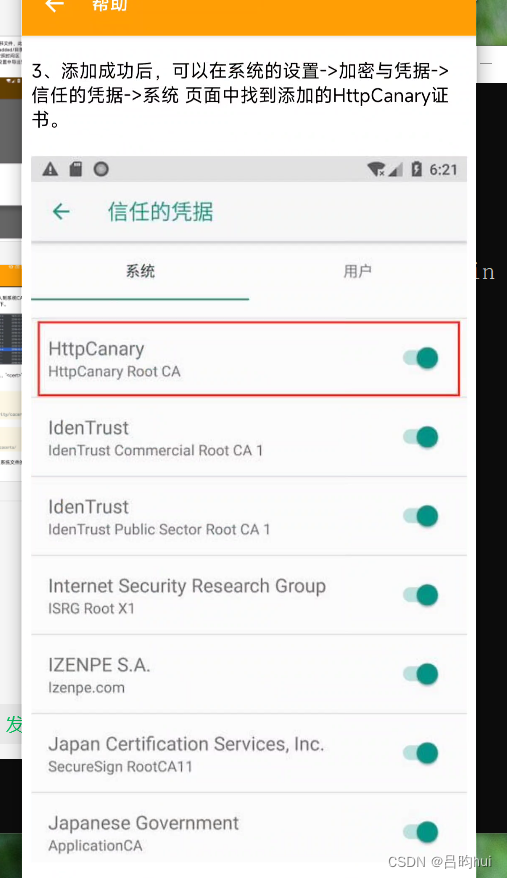
报错显示
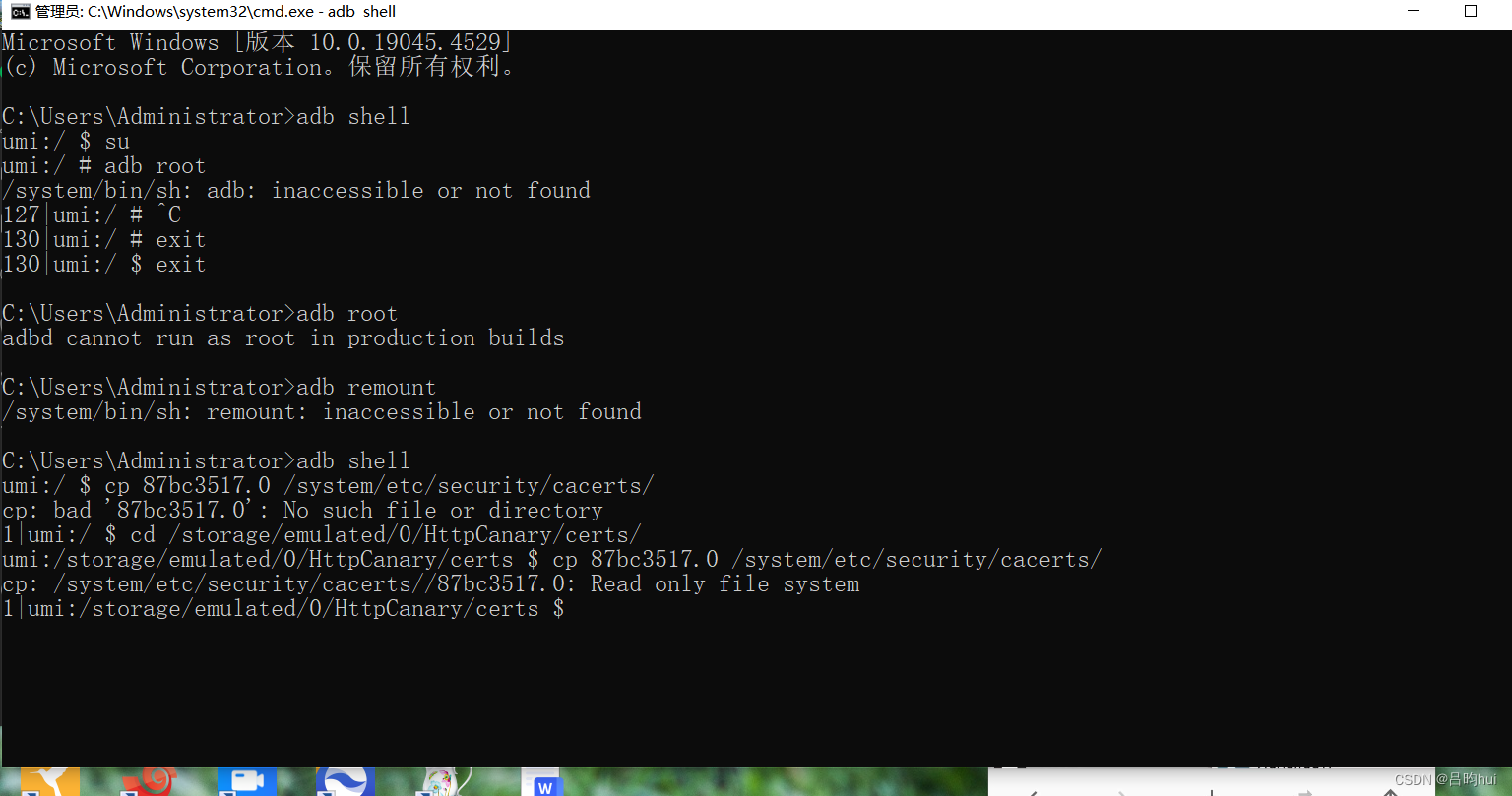
这里要用magisk的插件movecertificate加载后重启手机。才能安装
抓包检测?
分析请求参数
POST /login_jsonp_active.do HTTP/1.1
common: {"uniqueCode":"10266834-3536-4be9-90c9-33f76672ed4f","appId":"com.zcool.community","channel":"zcool","mobileType":"android","versionCode":4638}
BaseInfo: {"uniqueCode":"10266834-3536-4be9-90c9-33f76672ed4f","appId":"com.zcool.community","channel":"zcool","mobileType":"android","versionCode":4638}
Content-Type: application/x-www-form-urlencoded
Content-Length: 608
Host: passport.zcool.com.cn
Connection: Keep-Alive
Accept-Encoding: gzip
Cookie: randomcodetoken=9c55a4bb741f036053196603b2530946
User-Agent: okhttp/3.12.0
app=android&key=dTdlMmtGQjZIQk45Y05ZYlRUbXhTQlJTQ0M1NHBRMUdFYXFuYU5Ceko2dnpBWHZXSjlKSVpEQXFT%250ARmZCZWZCSCtKc3RHNmUzdGxKbQpPb0RkTmRsL3JGQ1QvTnNxVy90VkV0UXVEcEZDVE1tMkRIenJN%250Aa1VVSmdENC9ScW9OUU9NOEpabGNpZmVhckJRcU9IdUdEai9Mb2ppCjVSa1FVZkU5RjJ4RUdmTFYr%250ANFA2a215czV3bmVBbmR5QTRidmNNUHVDTWRNWk0rcmdlWDJmOTdtWDlZQUFXRHRQeTJvOHZSVDJp%250AdDAKNGxWK2hmdFpGREpiUGZ2Y0pOSUl6Q3gyZjdmQzVkRXNqMlhFZWNNS1FFVWZBK0xtdjlRMTFK%250AdnlsK0dveFdxLzVNMjhJeUJDRGQraQo1MGZOcGRJSXpDeDJmN2ZDNWRFc2oyWEVlY09FK1pQVHNm%250ANy9FUVpQbFFXSUhSc0RKODRTN1lIZnpQckN3bThOcjN4L3dQS3VyWE5sCmlBNk9ZaEdoVVJMS2Fx%250Abz0KP2tleUlkPTE%253D%250A使用命令frida -UF -l hook_encrypt.js -o log.txt
可以搜索到我随机输入的账号值。但是不能直接搜索到key,说明key被加密了。

加密模式是ECB,Key
DESede/ECB/PKCS5Padding doFinal data Utf8: {"password":"ghk","common":{"uniqueCode":"10266834-3536-4be9-90c9-33f76672ed4f","appId":"com.zcool.community","channel":"zcool","mobileType":"android","versionCode":4638},"appLogin":"https://www.zcool.com.cn/tologin.do","service":"https://www.zcool.com.cn","appId":"1006","username":"fhj"}
DESede/ECB/PKCS5Padding doFinal data Hex: 7b2270617373776f7264223a2267686b222c22636f6d6d6f6e223a7b22756e69717565436f6465223a2231303236363833342d333533362d346265392d393063392d333366373636373265643466222c226170704964223a22636f6d2e7a636f6f6c2e636f6d6d756e697479222c226368616e6e656c223a227a636f6f6c222c226d6f62696c6554797065223a22616e64726f6964222c2276657273696f6e436f6465223a343633387d2c226170704c6f67696e223a2268747470733a2f2f7777772e7a636f6f6c2e636f6d2e636e2f746f6c6f67696e2e646f222c2273657276696365223a2268747470733a2f2f7777772e7a636f6f6c2e636f6d2e636e222c226170704964223a2231303036222c22757365726e616d65223a2266686a227d
DESede/ECB/PKCS5Padding doFinal data Base64: eyJwYXNzd29yZCI6ImdoayIsImNvbW1vbiI6eyJ1bmlxdWVDb2RlIjoiMTAyNjY4MzQtMzUzNi00YmU5LTkwYzktMzNmNzY2NzJlZDRmIiwiYXBwSWQiOiJjb20uemNvb2wuY29tbXVuaXR5IiwiY2hhbm5lbCI6Inpjb29sIiwibW9iaWxlVHlwZSI6ImFuZHJvaWQiLCJ2ZXJzaW9uQ29kZSI6NDYzOH0sImFwcExvZ2luIjoiaHR0cHM6Ly93d3cuemNvb2wuY29tLmNuL3RvbG9naW4uZG8iLCJzZXJ2aWNlIjoiaHR0cHM6Ly93d3cuemNvb2wuY29tLmNuIiwiYXBwSWQiOiIxMDA2IiwidXNlcm5hbWUiOiJmaGoifQ==
DESede/ECB/PKCS5Padding doFinal result Hex: bbb7b690507a1c137d70d61b4d39b1481452082e78a50d4611aaa768d07327abf3017bd627d24864302a4857c179f047f89b2d1ba7b7b652663a80dd35d97fac5093fcdb2a5bfb5512d42e0e91424cc9b60c7ceb3245142600f8fd1aa835038cf096657227de6ab050a8e1ee1838ff2e88e2e5191051f13d176c4419f2d5fb83fa926cace709de0277720386ef70c3ee08c74c64cfab81e5f67fdee65fd6000160ed3f2da8f2f453da2b74e2557e85fb5914325b3dfbdc24d208cc2c767fb7c2e5d12c8f65c479c30a40451f03e2e6bfd435d49bf297e1a8c56abfe4cdbc2320420ddfa2e747cda5d208cc2c767fb7c2e5d12c8f65c479c384f993d3b1feff11064f9505881d1b0327ce12ed81dfccfac2c26f0daf7c7fc0f2aead7365880e8e6211a15112ca6aaa
DESede/ECB/PKCS5Padding doFinal result Base64: u7e2kFB6HBN9cNYbTTmxSBRSCC54pQ1GEaqnaNBzJ6vzAXvWJ9JIZDAqSFfBefBH+JstG6e3tlJmOoDdNdl/rFCT/NsqW/tVEtQuDpFCTMm2DHzrMkUUJgD4/RqoNQOM8JZlcifearBQqOHuGDj/Loji5RkQUfE9F2xEGfLV+4P6kmys5wneAndyA4bvcMPuCMdMZM+rgeX2f97mX9YAAWDtPy2o8vRT2it04lV+hftZFDJbPfvcJNIIzCx2f7fC5dEsj2XEecMKQEUfA+Lmv9Q11Jvyl+GoxWq/5M28IyBCDd+i50fNpdIIzCx2f7fC5dEsj2XEecOE+ZPTsf7/EQZPlQWIHRsDJ84S7YHfzPrCwm8Nr3x/wPKurXNliA6OYhGhURLKaqo=base64加密的值是
dTdlMmtGQjZIQk45Y05ZYlRUbXhTQlJTQ0M1NHBRMUdFYXFuYU5Ceko2dnpBWHZXSjlKSVpEQXFTRmZCZWZCSCtKc3RHNmUzdGxKbU9vRGROZGwvckZDVC9Oc3FXL3RWRXRRdURwRkNUTW0yREh6ck1rVVVKZ0Q0L1Jxb05RT004SlpsY2lmZWFyQlFxT0h1R0RqL0xvamk1UmtRVWZFOUYyeEVHZkxWKzRQNmtteXM1d25lQW5keUE0YnZjTVB1Q01kTVpNK3JnZVgyZjk3bVg5WUFBV0R0UHkybzh2UlQyaXQwNGxWK2hmdFpGREpiUGZ2Y0pOSUl6Q3gyZjdmQzVkRXNqMlhFZWNNS1FFVWZBK0xtdjlRMTFKdnlsK0dveFdxLzVNMjhJeUJDRGQraTUwZk5wZElJekN4MmY3ZkM1ZEVzajJYRWVjT0UrWlBUc2Y3L0VRWlBsUVdJSFJzREo4NFM3WUhmelByQ3dtOE5yM3gvd1BLdXJYTmxpQTZPWWhHaFVSTEthcW89通过逆向分析堆栈。发现是经过两次
这里有百分号可以判断是url编码。
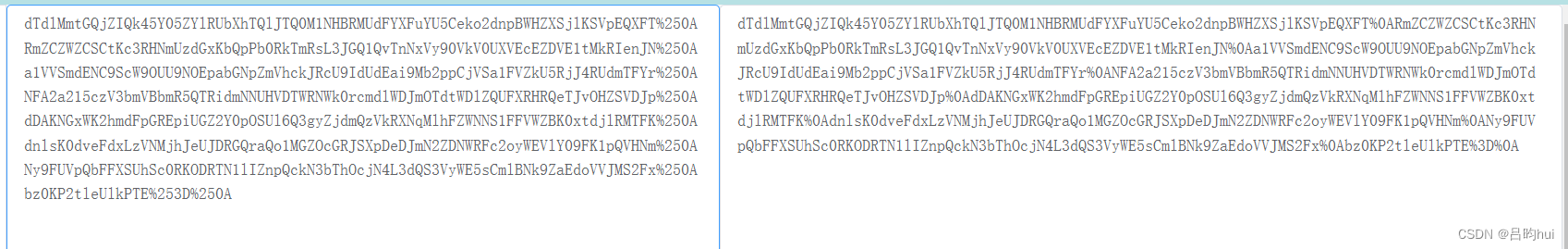
解码后的数据还是包含百分号。所以还要再进行一次url编码
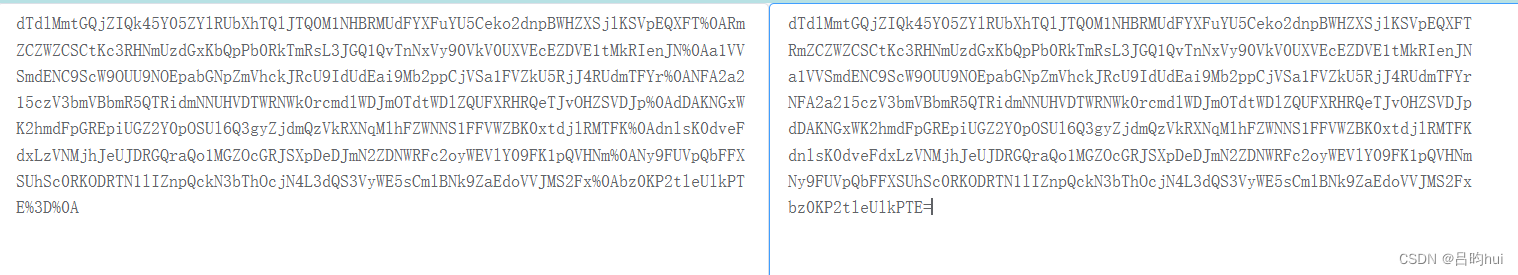
接码后的key值中出现了等号,只有在base64加密时出现位数不足的情况,会出现等号。

可以发现原始的key值经过base64编码后有经过两次url编码,才输出到请求中。
这也是Frida自吐框架的局限性。要自己去逆向分析。这里账号和密码还是明文,方便定位。实际的情况可能所有信息都被加密了,所以很难定位。
Frida自吐算法的局限性:
- 加密在java层,调用标准加密库,但是在加密前后对数据进行特殊处理(比如base64编码或者url编码等)
- 加密位置在so层,用C/C++写算法
- 或者加密在java层的自写算法