问题
需要对IAM用户强制使用MFA方式进行登陆。
步骤
创建强制MFA登陆策略
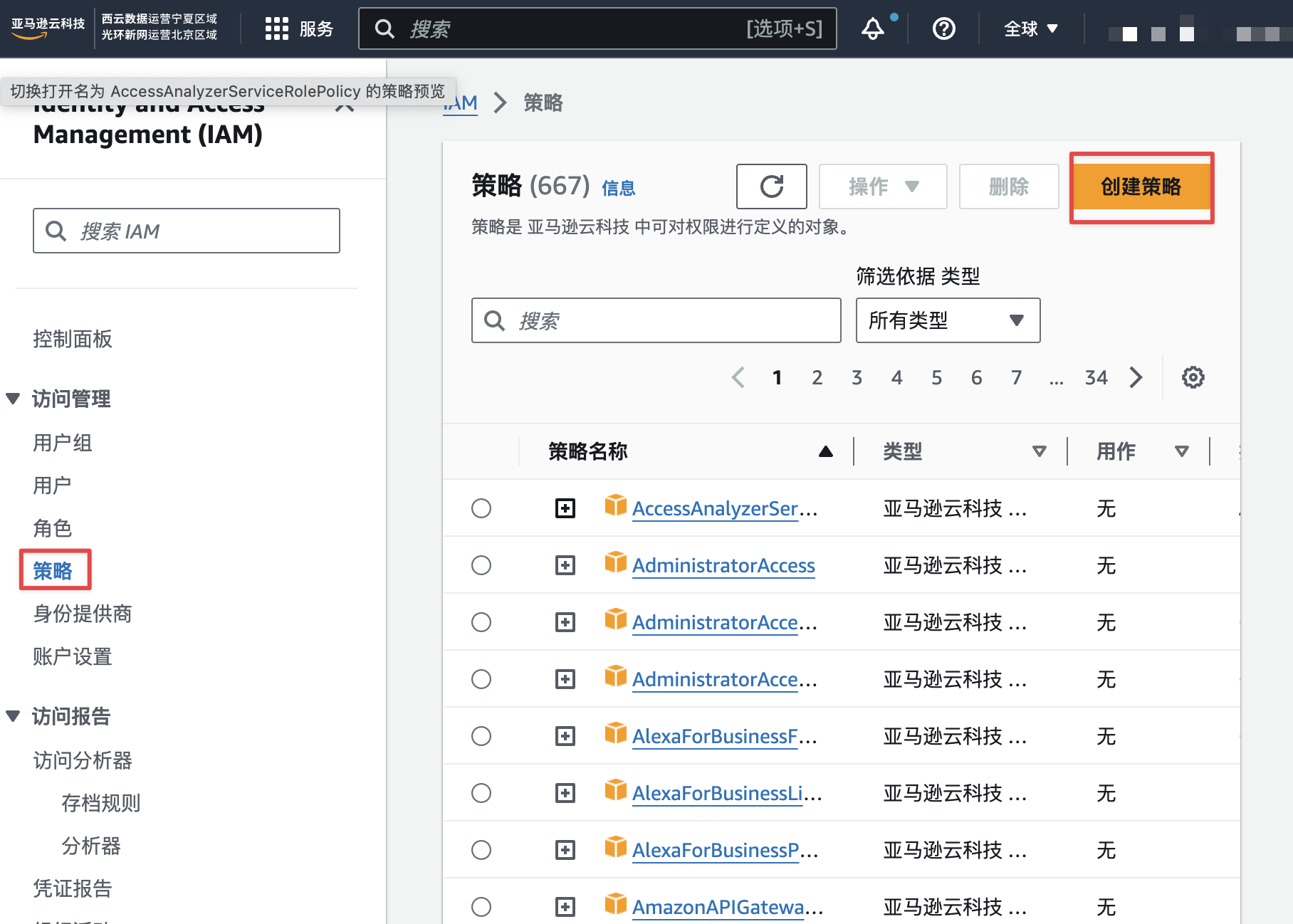
找到策略创建入口,如下图:
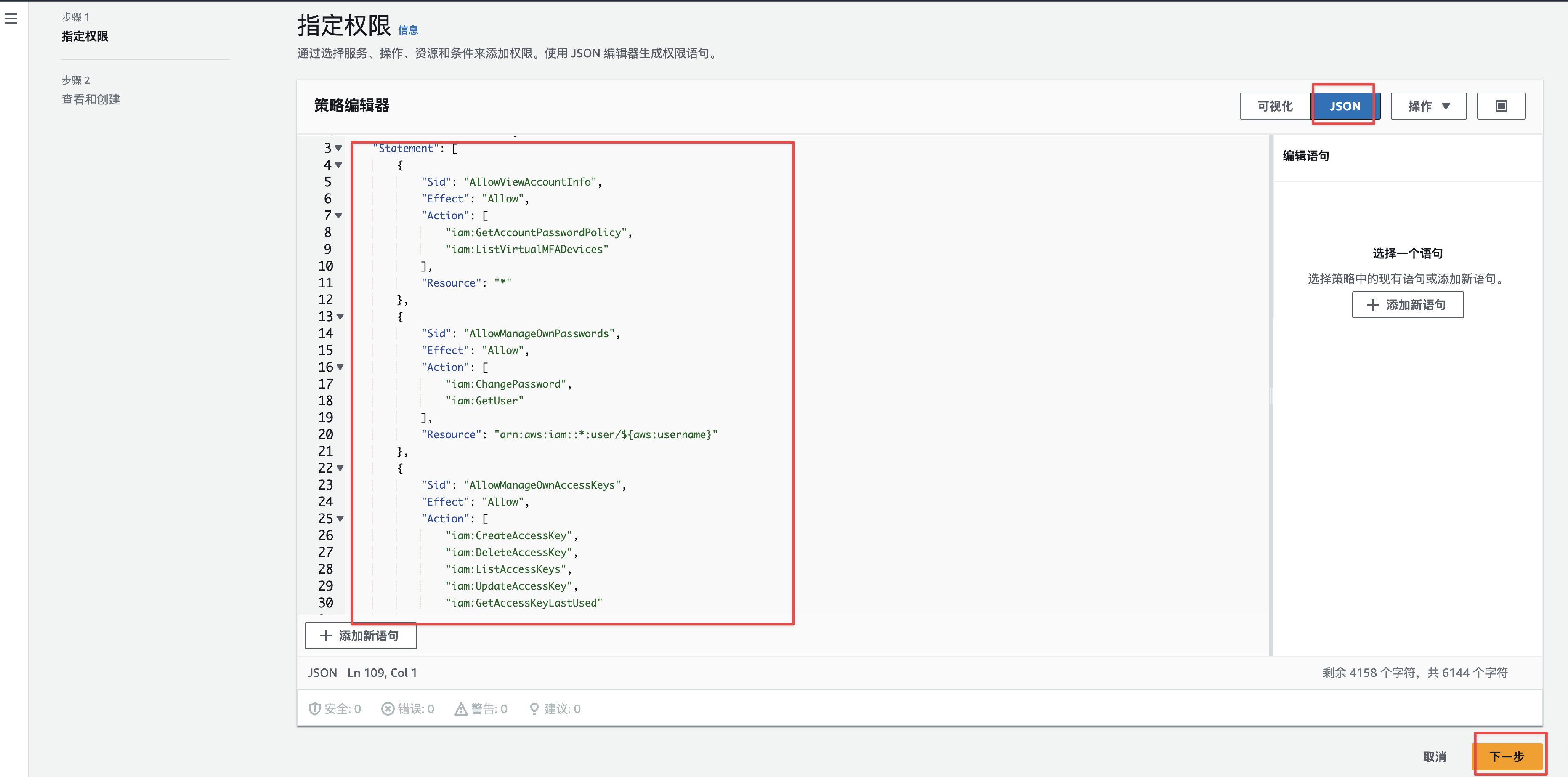
将下述内容json策略内容,复制到编辑器里面,具体内容和操作如下:
json
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowViewAccountInfo",
"Effect": "Allow",
"Action": [
"iam:GetAccountPasswordPolicy",
"iam:ListVirtualMFADevices"
],
"Resource": "*"
},
{
"Sid": "AllowManageOwnPasswords",
"Effect": "Allow",
"Action": [
"iam:ChangePassword",
"iam:GetUser"
],
"Resource": "arn:aws-cn:iam::*:user/${aws:username}"
},
{
"Sid": "AllowManageOwnAccessKeys",
"Effect": "Allow",
"Action": [
"iam:CreateAccessKey",
"iam:DeleteAccessKey",
"iam:ListAccessKeys",
"iam:UpdateAccessKey",
"iam:GetAccessKeyLastUsed"
],
"Resource": "arn:aws-cn:iam::*:user/${aws:username}"
},
{
"Sid": "AllowManageOwnSigningCertificates",
"Effect": "Allow",
"Action": [
"iam:DeleteSigningCertificate",
"iam:ListSigningCertificates",
"iam:UpdateSigningCertificate",
"iam:UploadSigningCertificate"
],
"Resource": "arn:aws-cn:iam::*:user/${aws:username}"
},
{
"Sid": "AllowManageOwnSSHPublicKeys",
"Effect": "Allow",
"Action": [
"iam:DeleteSSHPublicKey",
"iam:GetSSHPublicKey",
"iam:ListSSHPublicKeys",
"iam:UpdateSSHPublicKey",
"iam:UploadSSHPublicKey"
],
"Resource": "arn:aws-cn:iam::*:user/${aws:username}"
},
{
"Sid": "AllowManageOwnGitCredentials",
"Effect": "Allow",
"Action": [
"iam:CreateServiceSpecificCredential",
"iam:DeleteServiceSpecificCredential",
"iam:ListServiceSpecificCredentials",
"iam:ResetServiceSpecificCredential",
"iam:UpdateServiceSpecificCredential"
],
"Resource": "arn:aws-cn:iam::*:user/${aws:username}"
},
{
"Sid": "AllowManageOwnVirtualMFADevice",
"Effect": "Allow",
"Action": [
"iam:CreateVirtualMFADevice"
],
"Resource": "arn:aws-cn:iam::*:mfa/*"
},
{
"Sid": "AllowManageOwnUserMFA",
"Effect": "Allow",
"Action": [
"iam:DeactivateMFADevice",
"iam:EnableMFADevice",
"iam:ListMFADevices",
"iam:ResyncMFADevice"
],
"Resource": "arn:aws-cn:iam::*:user/${aws:username}"
},
{
"Sid": "DenyAllExceptListedIfNoMFA",
"Effect": "Deny",
"NotAction": [
"iam:CreateVirtualMFADevice",
"iam:EnableMFADevice",
"iam:GetUser",
"iam:GetMFADevice",
"iam:ListMFADevices",
"iam:ListVirtualMFADevices",
"iam:ResyncMFADevice",
"sts:GetSessionToken"
],
"Resource": "*",
"Condition": {
"BoolIfExists": {
"aws:MultiFactorAuthPresent": "false"
}
}
}
]
}
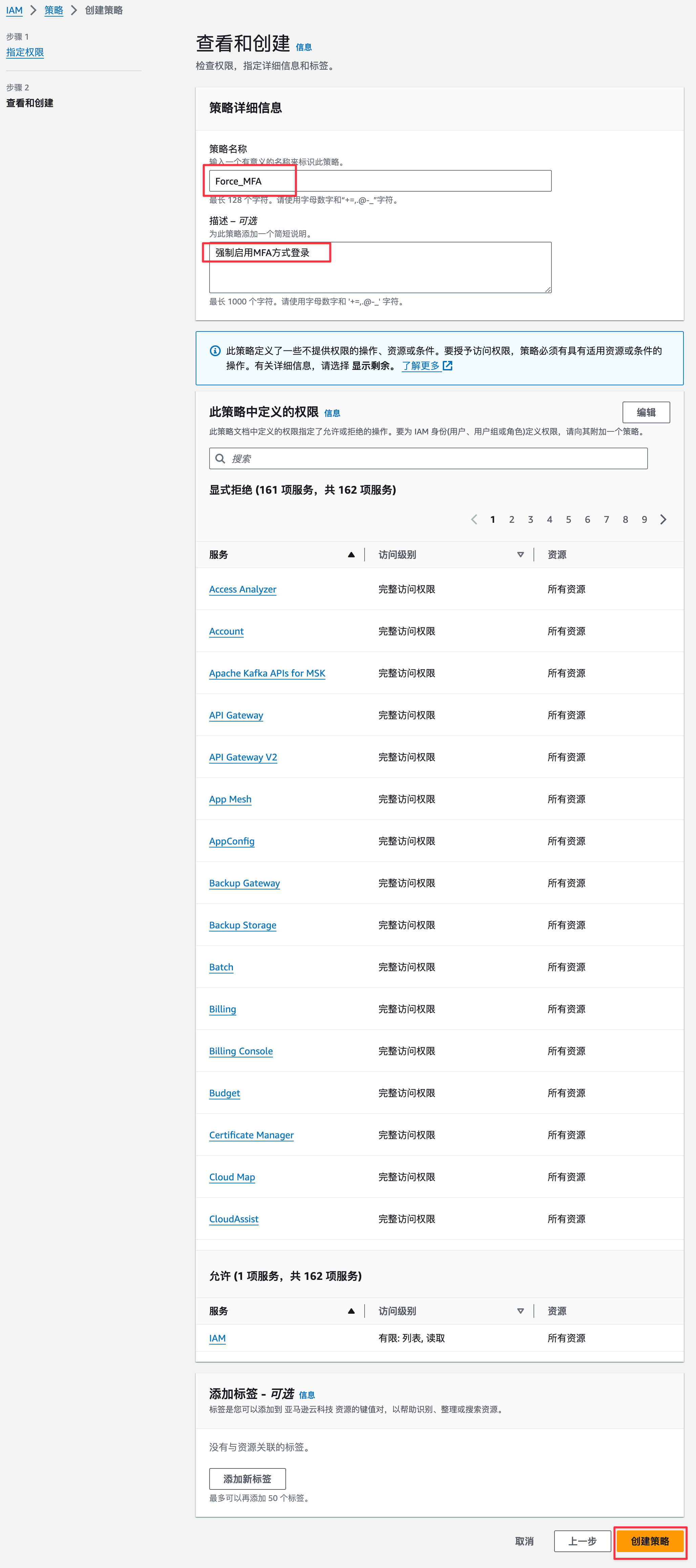
设置策略名称和描述,审计完后,没问题就可以点击创建策略按钮了。具体如下图:
设置用户组权限策略
强制MFA策略创建成功后,将该策略添加到需要使用到用户组中,即对添加了上述强制MFA策略的用户组用户启用强制MFA方式登录。添加步骤如下图:
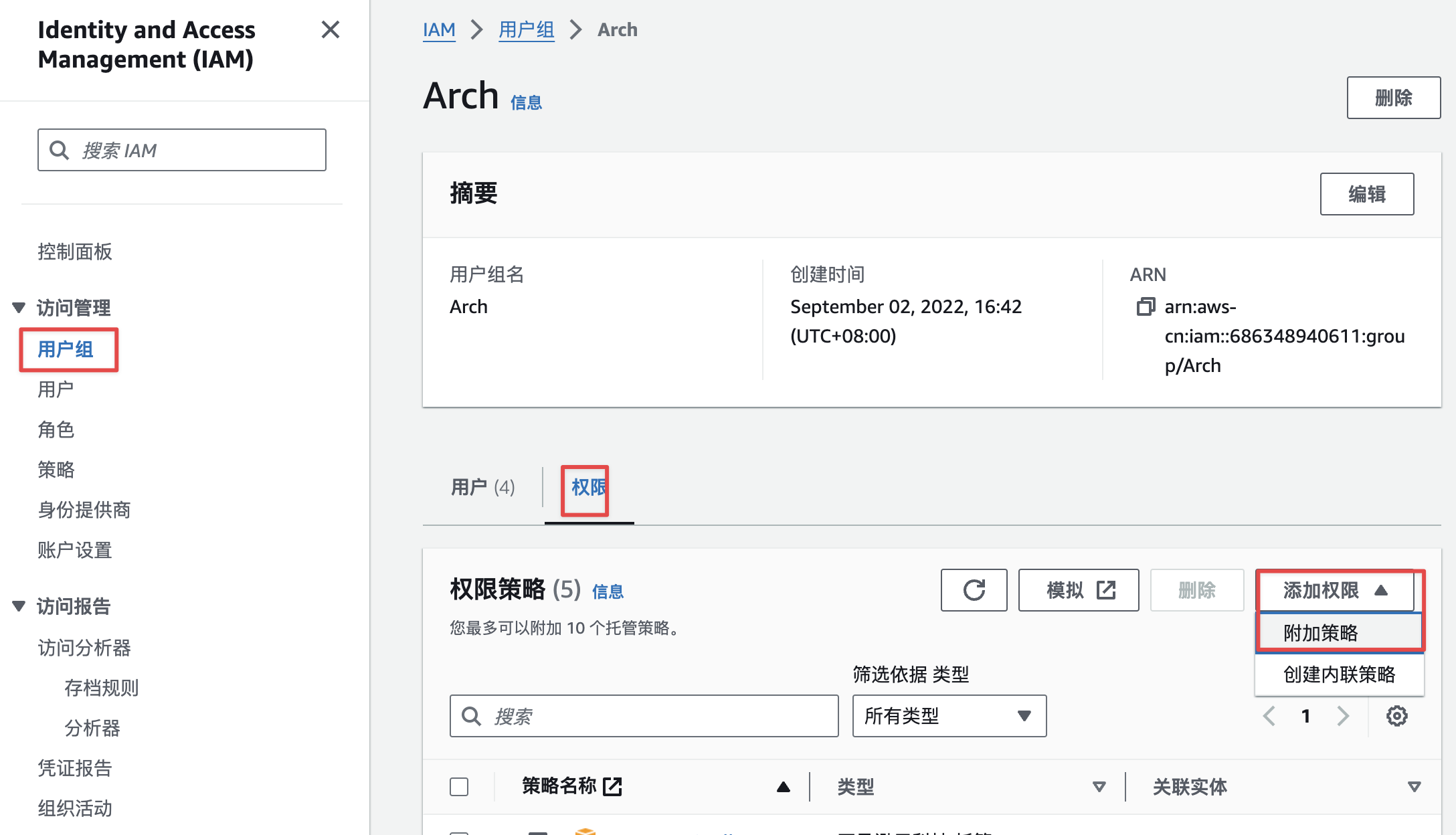
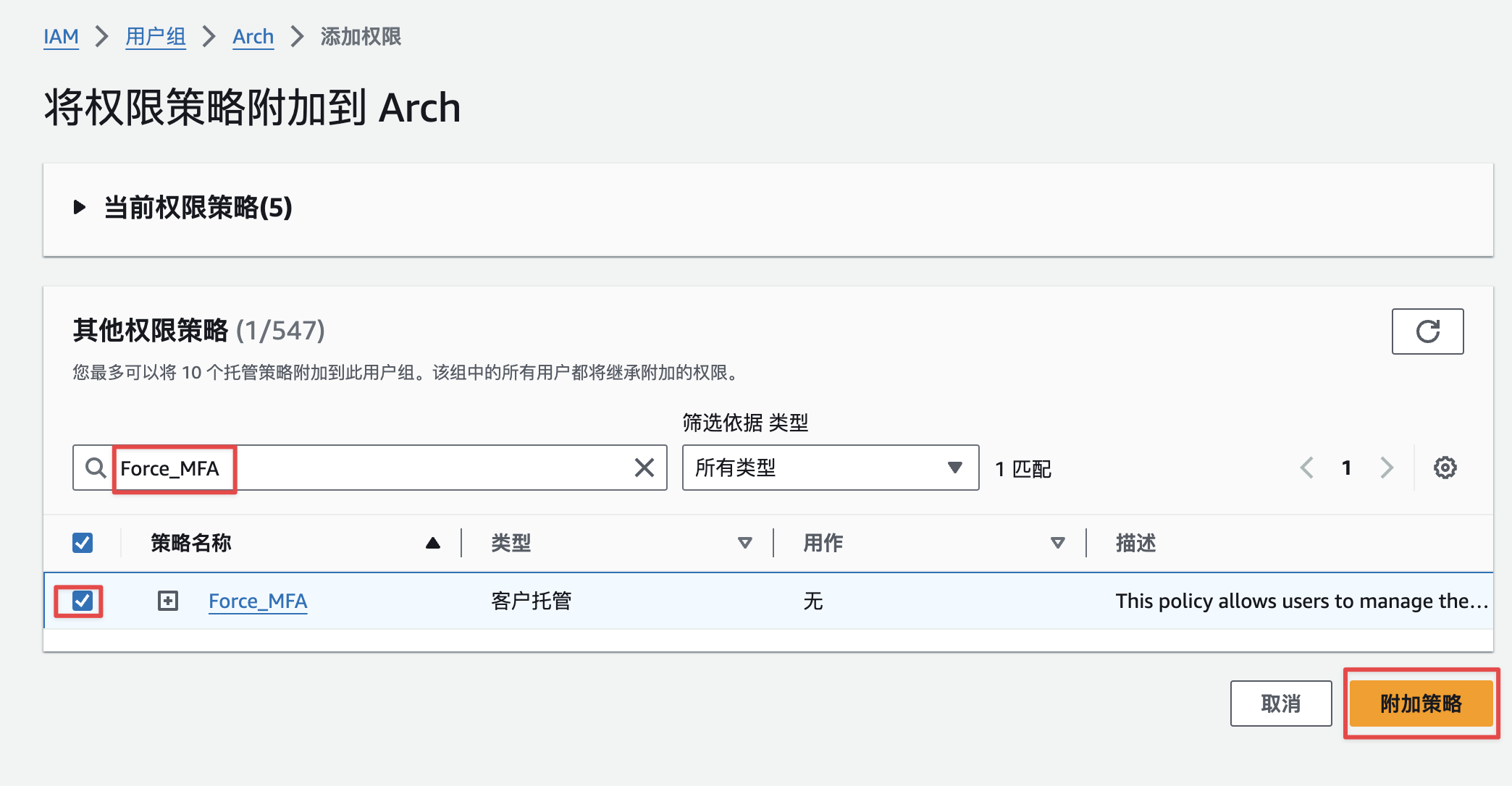
找到Force_MFA策略,进行添加如下图:
注意
新的用户,首次登录不要强制修改密码,不然这个策略一启用,这个新用户就永远在强制修改密码页面了。还有一点就是绑定MFA的过程中,千万不要刷新页面,如果中途刷新了页面,又没有完全走完绑定流程,最后就只能找管理员去帮新用户删MFA设备了。具体命令如下:
查找MFA设备命令:
bash
$ aws iam list-virtual-mfa-devices | grep zyl
arn:aws:iam::xxx:mfa/zyl删除MFA设备命令:
bash
aws iam delete-virtual-mfa-device --serial-number arn:aws:iam::xxx:mfa/zyl总结
强制MFA设备策略,虽然,安全了,但是AWS中国登录的页面,并不会引导新用户去MFA绑定页面进行绑定,而且中途中断的话,得拼命找管理员删设备。就这两点我觉得这个产品还有很大提升的地方。