
Conference:22nd IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom)
CCF level:CCF C
Categories:Network and Information Security
Year:2023
Num:30
Conference time:1-3 November 2023
11
Title:
EPPVChain: An Efficient Privacy-Preserving Verifiable Query Scheme for Blockchain Databases
EPPVChain:一种高效的区块链数据库隐私保护可验证查询方案
Authors:****

Key words:
Blockchain, Verifiable query, Query privacy, Symmetric Hidden Vector Encryption, Bloom filter
区块链、可验证查询、查询隐私、对称隐向量加密、布隆过滤器
Abstract:****
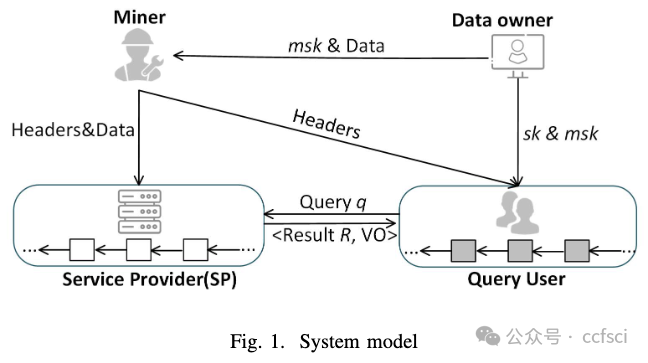
Blockchain databases have been exploited in many applications to construct trust and share data among multiple participants. However, maintaining the entire blockchain locally will cause heavy communication and storage overhead for users with limited resources. Alternatively, the user could act as a light node that stores block headers only and delegates queries to full nodes that maintain the entire blockchain. However, introducing a light node raises several concerns about query integrity and privacy. In this paper, we propose EPPVChain, the first scheme that simultaneously achieves efficient, privacy-preserving and verifiable conjunctive query for blockchain databases. EPPVChain resorts to a novel symmetric cryptographic primitive named Symmetric Hidden Vector Encryption (SHVE), and deploys several new techniques to achieve the desired goals. In specific, we design a new SHVE-based authenticated data structure to support privacy-preserving verifiable conjunctive queries. We further propose two improved schemes to aggregate data records to optimize query performance. Finally, we propose a dual-chain key escrow protocol to securely escrow the symmetric key of SHVE without relying on any trusted third party. The security analysis and evaluation confirm EPPVChain's ability to achieve query privacy and integrity with high efficiency.
区块链数据库已在许多应用程序中被利用来在多个参与者之间建立信任和共享数据。然而,在本地维护整个区块链将给资源有限的用户带来繁重的通信和存储开销。或者,用户可以充当仅存储区块头的轻节点,并将查询委托给维护整个区块链的完整节点。然而,引入轻节点引发了一些关于查询完整性和隐私的担忧。在本文中,我们提出了 EPPVChain,这是第一个同时实现区块链数据库的高效、隐私保护和可验证连接查询的方案。EPPVChain 采用了一种名为对称隐向量加密 (SHVE) 的新型对称加密原语,并部署了几种新技术来实现预期目标。具体来说,我们设计了一种新的基于 SHVE 的认证数据结构来支持隐私保护的可验证连接查询。我们进一步提出了两种改进的方案来聚合数据记录以优化查询性能。最后,我们提出了一个双链密钥托管协议,可以安全地托管SHVE的对称密钥,而无需依赖任何可信的第三方。安全性分析和评估证实了EPPVChain能够高效地实现查询隐私和完整性。

Pdf link:
https://ieeexplore.ieee.org/document/10538574
12
Title:
Enhancing Tunnel Safety for Dangerous Goods Vehicles through Blockchain-Based Time-Stamping
通过基于区块链的时间戳提高危险货物车辆隧道安全性
Authors:****

Key words:
timestamping, signatures, dangerous goods vehicles, blockchain, ethereum
时间戳、签名、危险品运输车辆、区块链、以太坊
Abstract:****
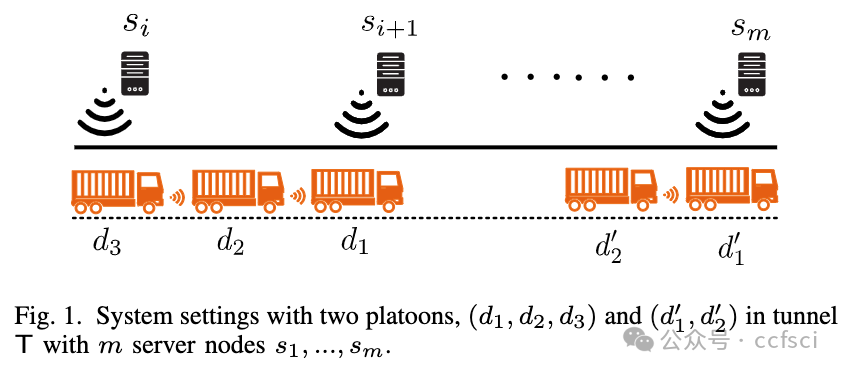
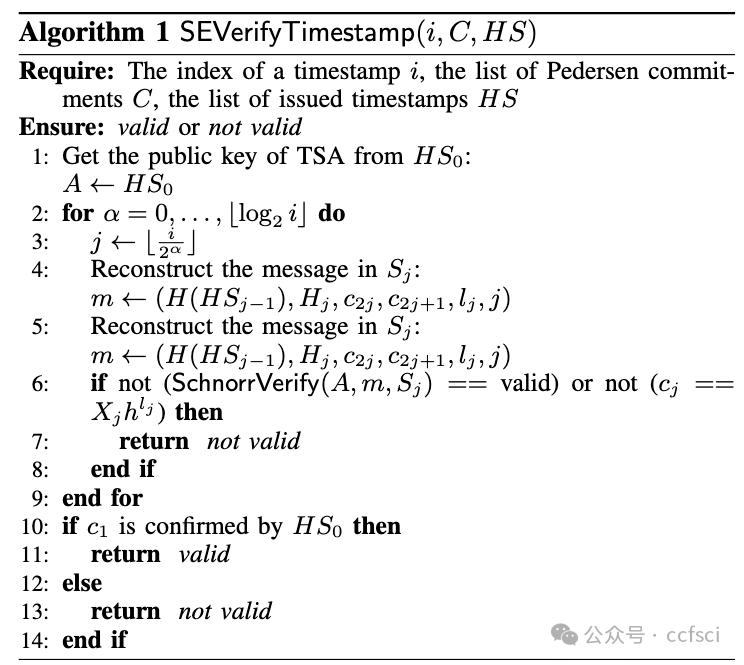
In this study, we explore the potential of integrating blockchain technology and cryptographic primitives such as Schnorr signatures and Pedersen commitments, via a Stamp and Extend scheme, in order to develop a trusted and reliable timestamping system. Our proposed architecture aims to facilitate the safe and reliable platooning of dangerous goods vehicles in C-ITS enabled tunnels. We have implemented a proof-of-concept on the Ethereum platform, demonstrating the feasibility and survivability of our proposed architecture. A series of performance experiments further underscore the potential of our system, reinforcing its value in fostering secure and trusted coordination of dangerous goods transport in connected vehicle tunnels.
在本研究中,我们探索了通过 Stamp and Extend 方案将区块链技术与 Schnorr 签名和 Pedersen 承诺等加密原语集成在一起的潜力,以开发一个值得信赖的时间戳系统。我们提出的架构旨在促进 C-ITS 隧道中危险货物车辆的安全可靠排队。我们在以太坊平台上实施了概念验证,证明了我们提出的架构的可行性和生存能力。一系列性能实验进一步强调了我们系统的潜力,增强了其在促进联网车辆隧道中危险货物运输的安全可信协调方面的价值。
Pdf link:
https://ieeexplore.ieee.org/document/10538825
13
Title:
A Secure Blockchain-based Authentication and Key Agreement Protocol for 5G Roaming
基于区块链的 5G 漫游安全认证和密钥协商协议
Authors:****

Key words:
Authentication, AVISPA tool, Blockchain, Elliptic Curve-Cryptography (ECC), Internet of Things (IoT), Scyther tool, ROR logic
身份验证、AVISPA 工具、区块链、椭圆曲线密码学 (ECC)、物联网 (IoT)、Scyther 工具、ROR 逻辑
Abstract:****
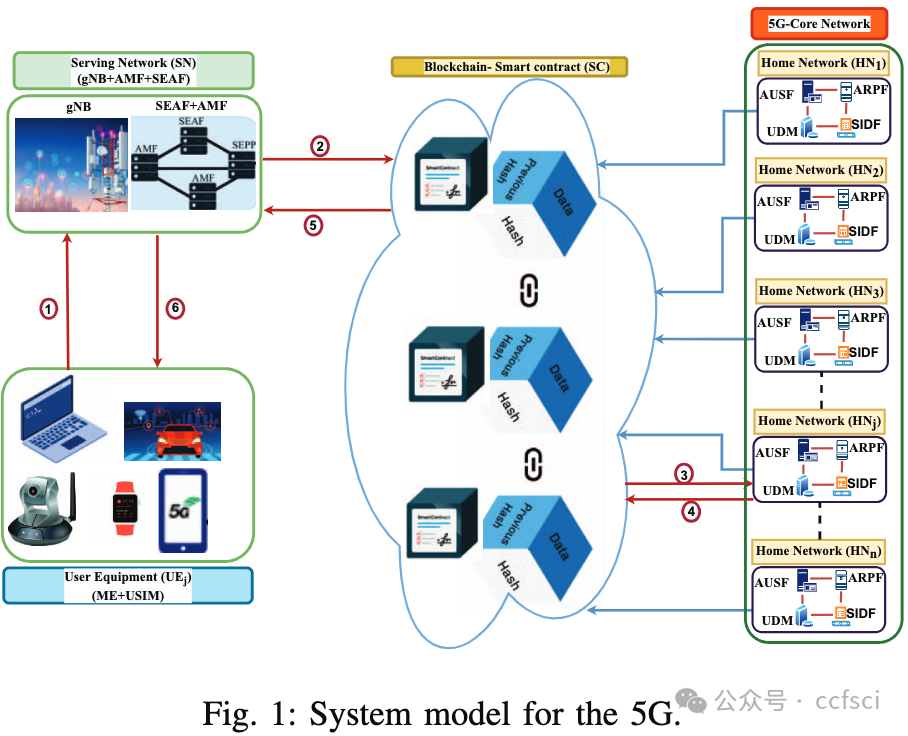
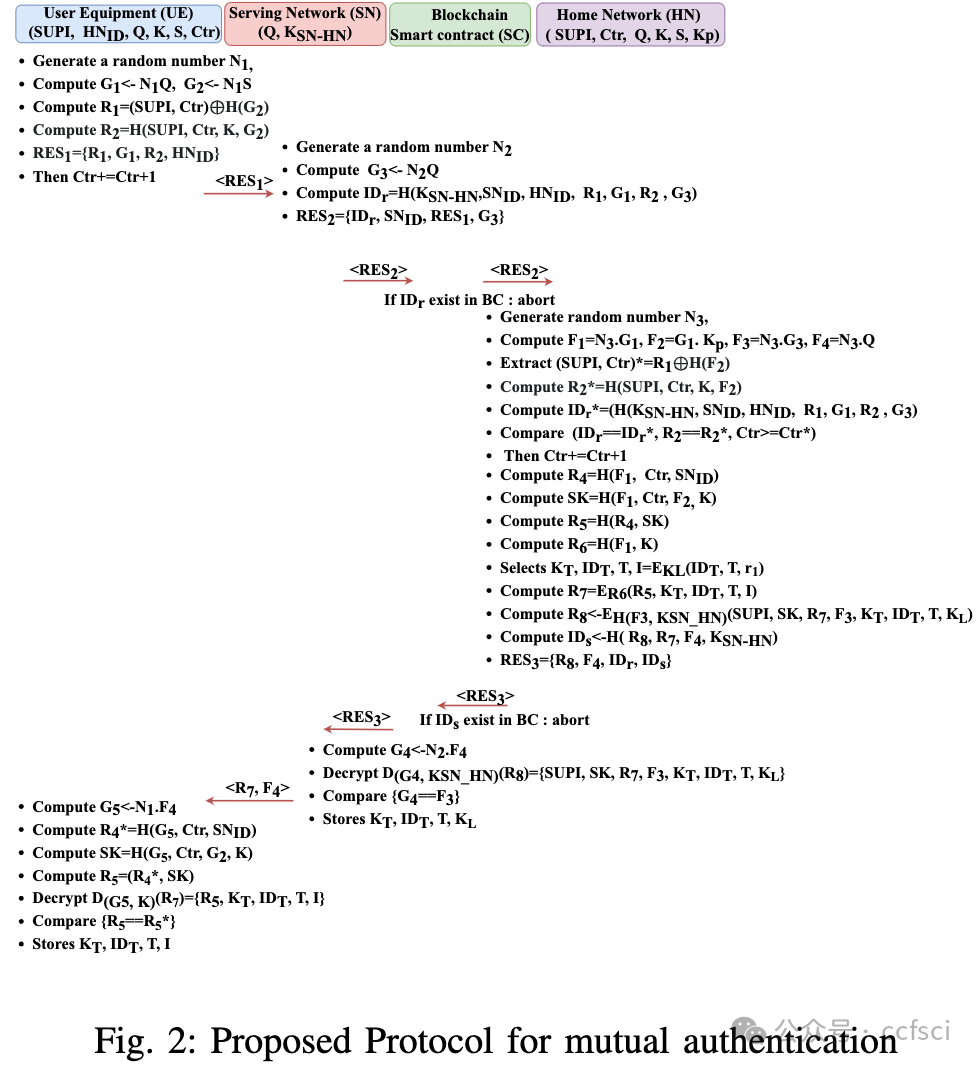
The fifth generation (5G) is now widely used to access network services due to the emergence of the Internet of Things (IoT) and mobile devices. To secure 5G communication, the Third Generation Partnership Project (3GPP) organization created the 5G-Authentication and Key Agreement (AKA) protocol. Security evaluations have found a number of problems in the 5G-AKA, including a violation of perfect forward secrecy, a traceability attack, and denial of service (DoS) attacks. To address the shortcomings of 5G-AKA, several enhanced versions have been developed. However, it has been shown that either these versions are expensive or do not address security issues. Additionally, less effort is put into providing security when a user utilizes roaming mobile services while a malicious Serving Network (SN) is present. This paper introduces an authentication mechanism to handle the above issues. In addition to this, a handover mechanism is also designed for re-connection. The authentication and handover phase security assessment uses the mathematical model Real-Or-Random (ROR), AVISPA, and Scyther tool. Furthermore, the performance comparison depicts that the authentication and handover phase is more efficient than existing protocols. An assessment of the smart contract function's cost and effectiveness is also provided.
由于物联网 (IoT) 和移动设备的出现,第五代 (5G) 现已广泛用于访问网络服务。为了确保 5G 通信的安全,第三代合作伙伴计划 (3GPP) 组织创建了 5G 认证和密钥协商 (AKA) 协议。安全评估发现 5G-AKA 存在许多问题,包括违反完美前向保密、可追溯性攻击和拒绝服务 (DoS) 攻击。为了解决 5G-AKA 的缺点,已经开发了几个增强版本。然而,事实证明这些版本要么价格昂贵,要么没有解决安全问题。此外,当用户在存在恶意服务网络 (SN) 的情况下使用漫游移动服务时,在提供安全性方面投入的努力较少。本文介绍了一种处理上述问题的认证机制。除此之外,还设计了一种切换机制用于重新连接。身份验证和切换阶段的安全评估使用数学模型 Real-Or-Random (ROR)、AVISPA 和 Scyther 工具。此外,性能比较表明身份验证和切换阶段比现有协议更有效。还提供了对智能合约功能的成本和有效性的评估。



Pdf link:
https://ieeexplore.ieee.org/document/10538827
14
Title:
Blockchain-based and Privacy-Preserving Data Collection for Vehicular Crowdsensing
基于区块链的车辆群智感知隐私数据收集
Authors:****

Key words:
Vehicular crowdsensing, data collection, privacy preserving, sequence number, blockchain
车辆群智感知 数据采集 隐私保护 序列号 区块链
Abstract:****
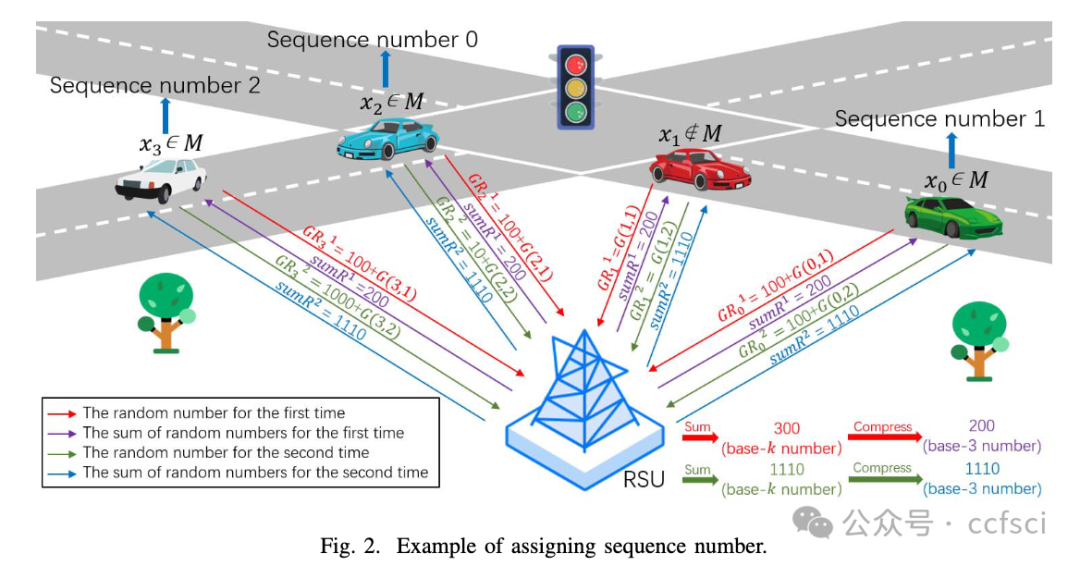
In vehicular crowdsensing, vehicles frequently sense and transmit data, which poses a challenge in the privacy protection of vehicles. Existing privacy-preserving techniques often have a large computation or communication cost and the identity privacy protection is not well addressed. In this article, we propose a blockchain-based and privacy-preserving data collection scheme for vehicular crowdsensing, named BPDV. It aims to efficiently collect sensing data from vehicles while preserving the privacy of vehicles and requesters. BPDV assigns a sequence number to each vehicle that senses data by using a base-k 1-head random number, in order to protect the identity privacy. To save resources, the data from multiple vehicles are sent in one round of data collection with a well-designed "yield" mechanism. Additionally, RSUs store the sensing data on a blockchain to achieve decentralized and reliable data storage. Finally, extensive experiments show that BPDV has small computation and communication costs compared with other schemes, while providing the identity and data privacy preserving.
在车辆群智感知中,车辆频繁感知和传输数据,对车辆的隐私保护提出了挑战。现有的隐私保护技术往往具有较大的计算或通信成本,并且身份隐私保护问题尚未得到很好的解决。在本文中,我们提出了一种基于区块链的车辆群智感知隐私保护数据收集方案BPDV。它旨在高效地从车辆收集感知数据,同时保护车辆和请求者的隐私。BPDV使用以k为底的1头随机数为每辆感知数据的车辆分配一个序列号,以保护身份隐私。为了节省资源,来自多辆车辆的数据在一轮数据收集中通过精心设计的"收益"机制发送。此外,RSU将感知数据存储在区块链上,以实现去中心化和可靠的数据存储。最后,大量实验表明,与其他方案相比,BPDV具有较小的计算和通信成本,同时提供身份和数据隐私保护。

Pdf link:
https://ieeexplore.ieee.org/document/10538670
15
Title:
BC-FL k-means: A Blockchain-based Framework for Federated Clustering
BC-FL k-means:基于区块链的联合聚类框架
Authors:****

Key words:
Blockchain, Federated Learning, Collaborative Learning, Privacy, Reputation, Committee Consensus
区块链、联邦学习、协作学习、隐私、声誉、委员会共识
Abstract:****
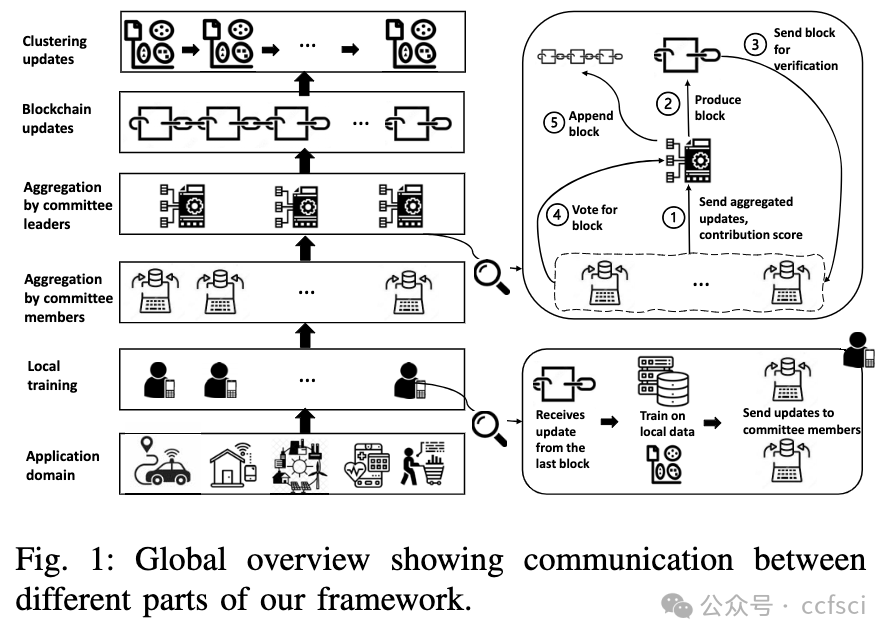
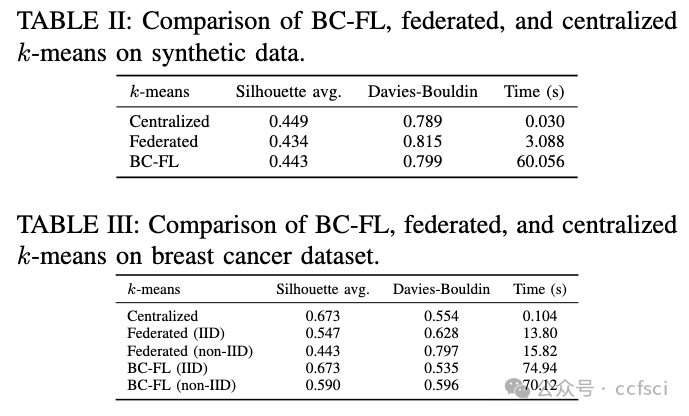
This work presents a novel framework to train clustering models collaboratively without compromising accuracy while accommodating privacy and security in a decentralized manner. Our decentralized collaborative learning model removes the single point of failure and excludes unreliable input by designing a committee-based consensus method in a blockchain-based federated learning, which is equipped with a reputation system. We present a prototype implementation of our approach and show that its performance is comparable with centralized clustering regardless of the distribution of data among devices.
这项研究提出了一种新颖的框架,用于以协作方式训练聚类模型,同时不会损害准确性,并以去中心化的方式兼顾隐私和安全。我们的去中心化协作学习模型通过在基于区块链的联邦学习中设计基于委员会的共识方法消除了单点故障并排除了不可靠的输入,该方法配备了声誉系统。我们介绍了我们方法的原型实现,并表明无论数据在设备之间的分布如何,其性能都与集中式聚类相当。
Pdf link:
https://ieeexplore.ieee.org/document/10538665
篇幅有限,下篇文章将继续分享剩余论文

关注我们,持续接收区块链最新论文
洞察区块链技术发展趋势
Follow us to keep receiving the latest blockchain papers
Insight into Blockchain Technology Trends