文章目录
- [0, 证书过期的问题](#0, 证书过期的问题)
- 1,生成ssl证书
- 2,配置ES使用ssl证书
0, 证书过期的问题
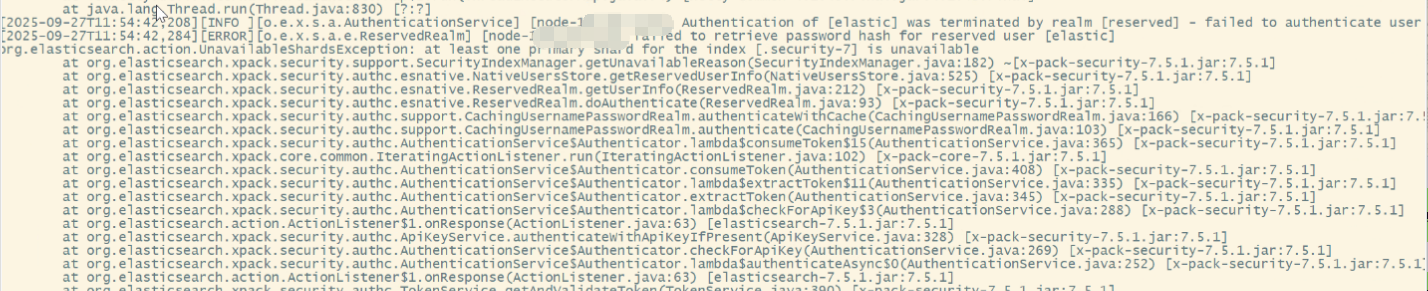
- 证书过期后,客户端或节点无法验证证书的有效性(如签名过期、信任锚失效),会触发 PKIX path validation failed或 CertificateExpiredException等错误,导致加密连接中断。此时,集群内部的节点认证(如传输层通信)和外部客户端的访问(如 HTTP 请求)均会失败
- 证书过期后,因为启用Xpack后,集群节点之间通过 TLS/SSL加密进行数据同步(如主分片选举、副本复制),导致节点无法通过其他节点的身份验证,会被视为"不可信",导致节点脱离集群(掉节点)。严重时会引发集群分裂(Split Brain),影响数据的完整性和可用性
- 证书过期后,ES master节点频繁添加、移除data节点,导致数据不可用,用户认证失败
1,生成ssl证书
bash
#1,生成ca证书
[root@es1 elasticsearch]# ./bin/elasticsearch-certutil ca
This tool assists you in the generation of X.509 certificates and certificate
signing requests for use with SSL/TLS in the Elastic stack.
...
Please enter the desired output file [elastic-stack-ca.p12]: es-ca.p12
Enter password for es-ca.p12 :
[root@es1 elasticsearch]# ll
total 664
drwxr-xr-x 2 znyw znyw 4096 Aug 4 2023 bin
drwxr-xr-x 3 znyw znyw 272 Jul 25 09:41 config
-rw------- 1 root root 2672 Sep 28 10:09 es-ca.p12
...
#2,根据ca,生成客户端cert证书
#证书有效期:默认3年,可指定有效期为100年=36500天
# ./bin/elasticsearch-certutil cert --ca es-ca.p12 --ca-pass '123456' --pass '123456' --days 36500
[root@es1 elasticsearch]# ./bin/elasticsearch-certutil cert --ca es-ca.p12 #
This tool assists you in the generation of X.509 certificates and certificate
...
Enter password for CA (es-ca.p12) :
Please enter the desired output file [elastic-certificates.p12]: es-cert.p12
Enter password for es-cert.p12 :
Certificates written to /opt/elasticsearch/es-cert.p12
[root@es1 elasticsearch]# ll
total 668
drwxr-xr-x 2 znyw znyw 4096 Aug 4 2023 bin
drwxr-xr-x 3 znyw znyw 272 Jul 25 09:41 config
-rw------- 1 root root 2672 Sep 28 10:09 es-ca.p12
-rw------- 1 root root 3596 Sep 28 10:10 es-cert.p12
...
#3,查看客户端cert证书有效期
[root@es1 elasticsearch]# openssl pkcs12 -in es-cert.p12 -nokeys --password pass:'123456' |openssl x509 -enddate -noout
notAfter=Sep 27 02:10:49 2028 GMT
#4,分发客户端cert证书到各ES节点2,配置ES使用ssl证书
bash
#5,配置ES,启用Xpack,使用该客户端cert证书
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.monitoring.collection.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: /opt/selasticsearch/es-cert.p12
xpack.security.transport.ssl.truststore.path: /opt/selasticsearch/es-cert.p12
#6,重启所有es节点,先重启master,再重启data
#7,通过ES接口,验证证书有效期
GET _ssl/certificates
[
{
"path" : "/opt/elasticsearch/config/es-cert.p12",
"format" : "PKCS12",
"alias" : "instance",
"subject_dn" : "CN=instance",
"serial_number" : "99147c0f3486f356bae9873b873ad57f2f79f3cb",
"has_private_key" : true,
"expiry" : "2028-08-27T02:10:49.000Z"
},
....