Reverse
尤皮·埃克斯历险记(2)
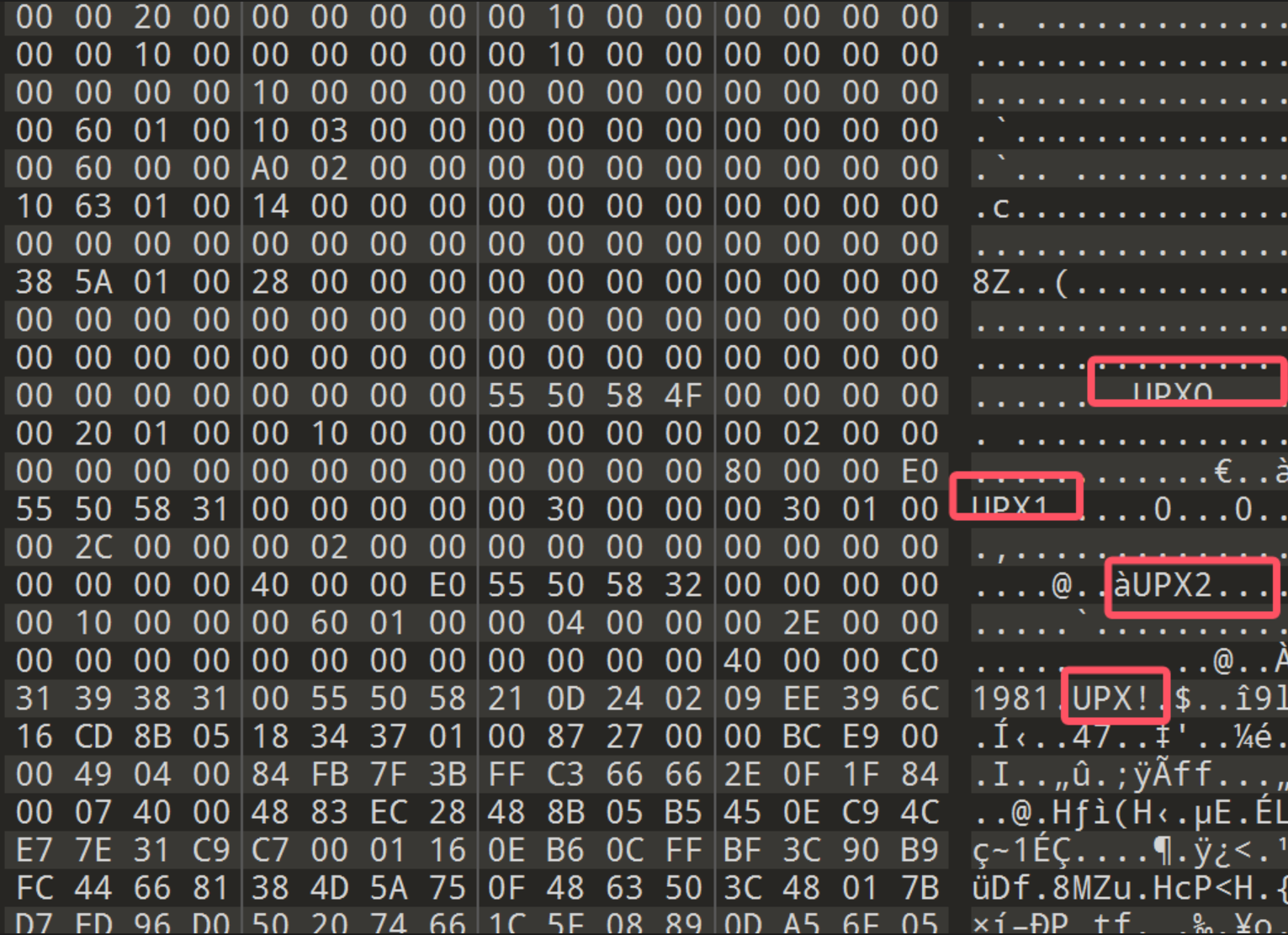
魔改UPX壳,010打开后把被魔改的标志位改回去即可
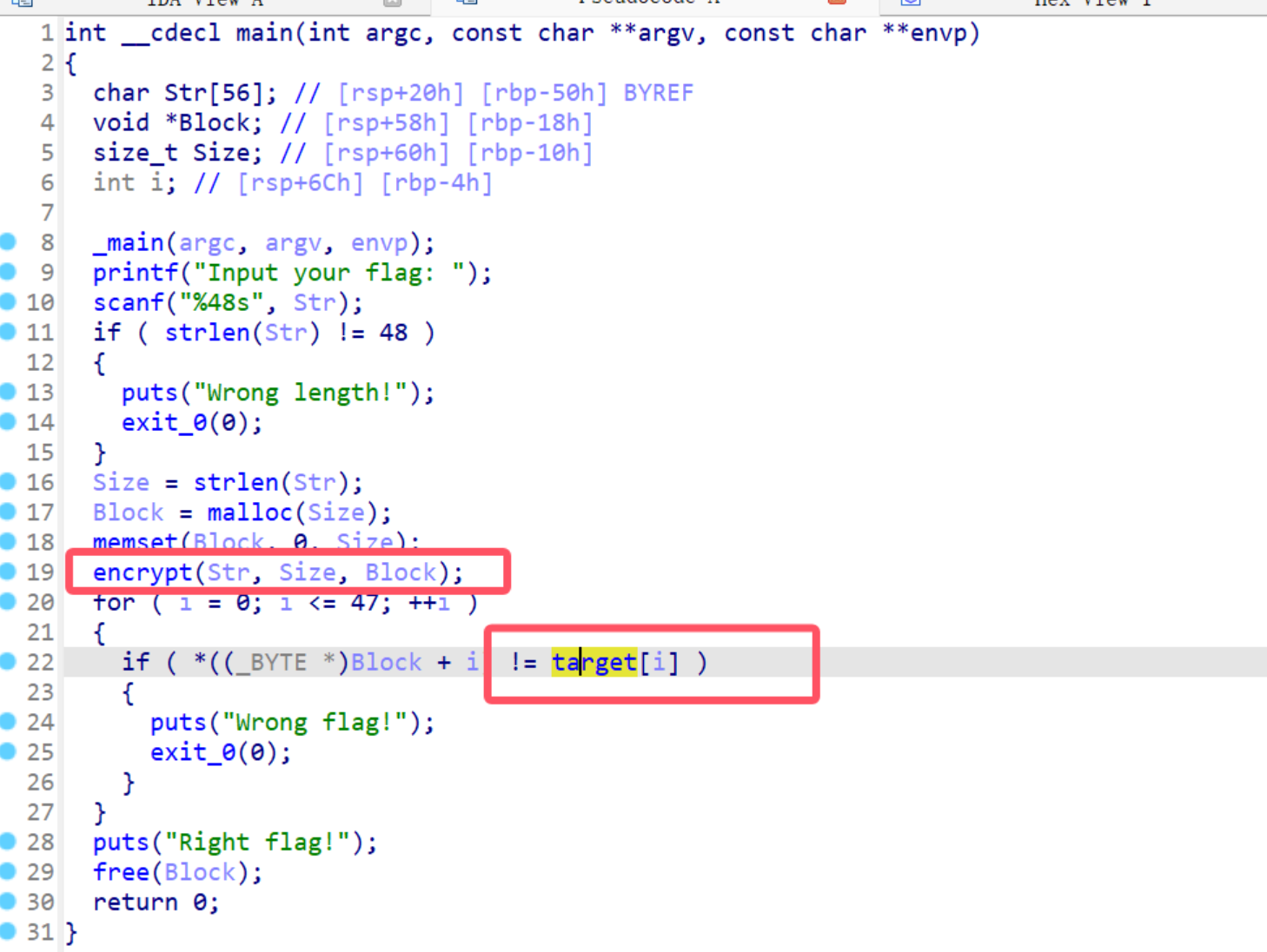
查看主函数,很容易发现是结果encrypt函数加密,然后加密结果和target比较
加密函数如下:
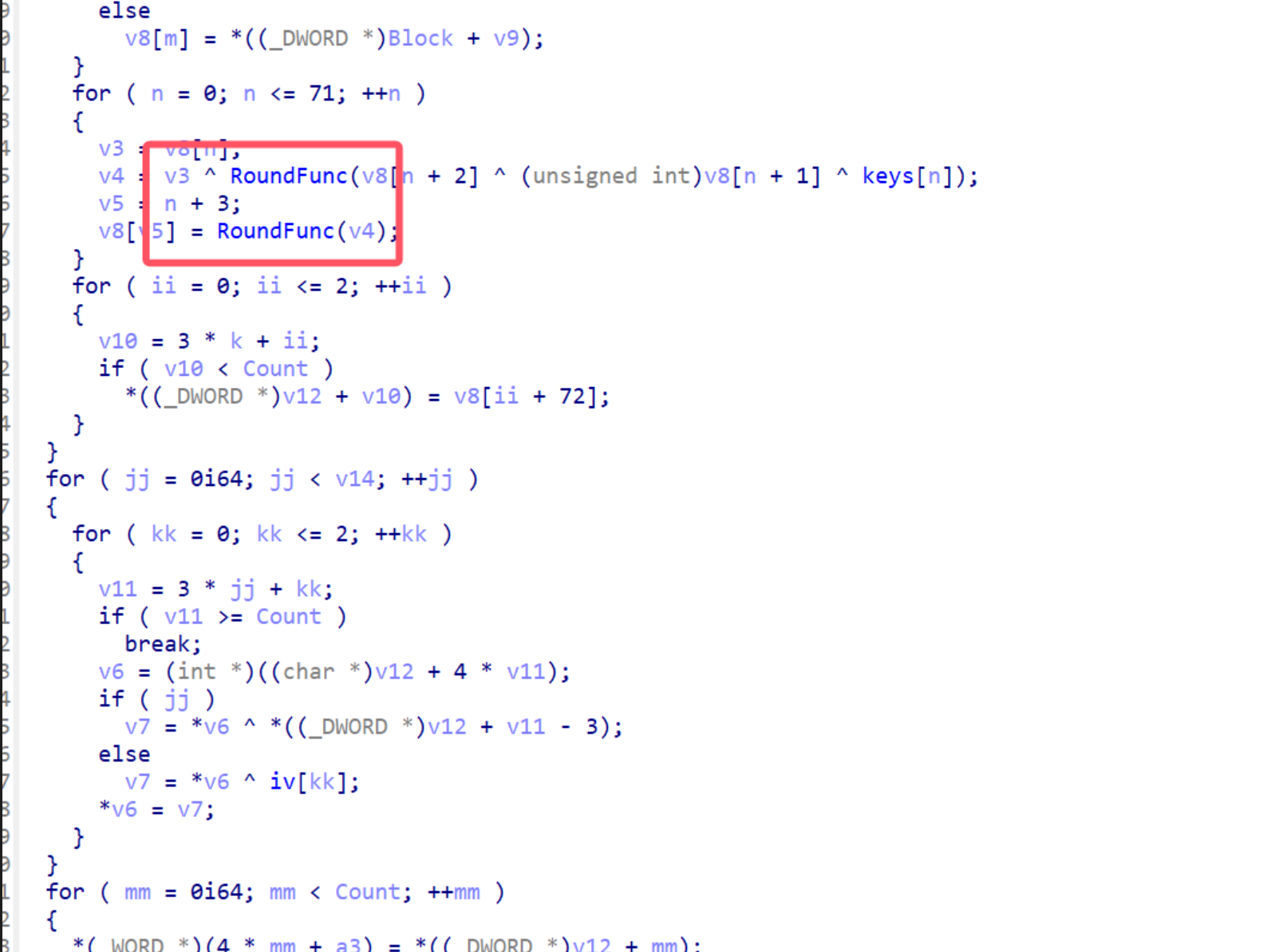
重点是那个RoundFunc函数,看名字像是轮加密
跟进发现平坦化
使用D810去平坦化
得到结果
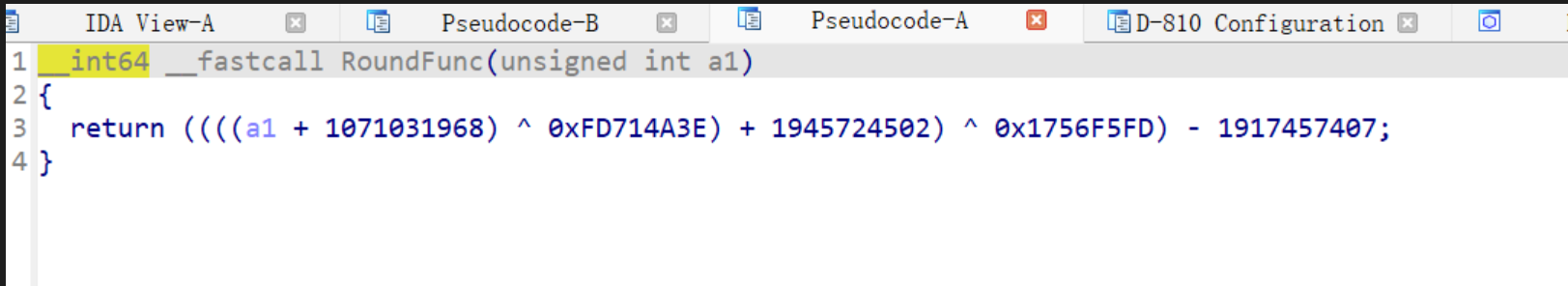
明显可逆
python
# -*- coding: utf-8 -*-
import struct
# 从你提供的 rdata 中提取出的 72 个 keys(低 32 位)
keys_hex = [
"0D344FC67","2210BDB7","76BB9C00","53F1B5DE","821A977F","0F5B01673","2A406627","935F493C","0B98347C1",
"0E1AD274A","0F68B39CE","0BCB77109","0AE8207AF","54F52F5A","2487ACB7","2BAA52BD","0D7A45B9F","0B93D82C7",
"77FBF041","1747530C","7EA63DEE","8BAD0343","38822BD3","806B9E9D","242525CF","1F5D96BE","1ADB4554",
"47B628D0","77C9A358","3C43D913","711165D3","1AFDEA6E","57EF6F26","75CDB37E","0F08680DE","7EAAD562",
"7ABA9243","45AF3320","0F7F816B2","3DD5C8D1","6D8251F6","7606E5D0","38DCED31","7FA1260B","0BAEFF202",
"0D9D85E1D","5E583700","35DFCC5F","1B689ABB","1B2BBB67","0CF506375","3A3D4268","46A5141B","7FE3136C",
"3E86F672","8A0B8EEE","33D87CD7","0D4A50EA9","0C77AFCDD","0CDC0D74D","0E0B6F0BC","66C0E9C7","0D494B811",
"9D1D8A81","147C00B6","0DF60C3E4","5FA112F8","7186229A","7FDCDC37","1435FE6B","0F97112A5","0EA79306C"
]
keys = [int(x,16) & 0xffffffff for x in keys_hex]
# iv(程序中定义的)
iv = [0xBE87E8B2, 0x88E9F392, 0x16FB40C3]
# target(rdata 中的 48 字节)
target_bytes = bytes([
0xC7,0xC9,0x4C,0x95,0x6F,0xBF,0xC9,0xF4,0xC4,0x86,0xA4,0x20,0x57,0x55,0x6B,0xE2,
0xEA,0xDC,0xB7,0x3F,0x9C,0x42,0x1E,0xE1,0x72,0x82,0x0D,0x93,0xB3,0xF9,0xD0,0x35,
0x93,0x70,0xFF,0x44,0x72,0x61,0x55,0xF8,0xEC,0xDA,0xFB,0x6E,0xA8,0xA6,0xCB,0x9E
])
# RoundFunc 与其逆函数(与二进制代码一模一样的算术/XOR 顺序)
def RoundFunc(a1):
a1 &= 0xffffffff
v = (a1 + 1071031968) & 0xffffffff
v ^= 0xFD714A3E
v = (v + 1945724502) & 0xffffffff
v ^= 0x1756F5FD
v = (v - 1917457407) & 0xffffffff
return v
def InvRoundFunc(v):
v &= 0xffffffff
v = (v + 1917457407) & 0xffffffff
v ^= 0x1756F5FD
v = (v - 1945724502) & 0xffffffff
v ^= 0xFD714A3E
v = (v - 1071031968) & 0xffffffff
return v
# 步骤 1: target_bytes -> 12 个小端 uint32(Count = 12)
Count = len(target_bytes)//4
v12_final = [ struct.unpack_from('<I', target_bytes, 4*i)[0] for i in range(Count) ]
# 步骤 2: 逆 CBC(恢复每组的 round 输出 v8[72..74])
v14 = (Count + 2)//3
v12_pre = [0]*Count
for jj in range(v14):
for kk in range(3):
v11 = 3*jj + kk
if v11 >= Count:
break
if jj == 0:
pre = v12_final[v11] ^ iv[kk]
else:
pre = v12_final[v11] ^ v12_final[v11 - 3]
v12_pre[v11] = pre & 0xffffffff
# 步骤 3: 对每组(3 个 uint32)做 72 轮的逆运算,得到原始 X0,X1,X2
flag_bytes = bytearray()
for k in range(v14):
out3 = v12_pre[3*k:3*k+3]
# X array,设置 X[72..74] = out3,向前反推到 X[0..2]
X = [0]*75
X[72], X[73], X[74] = out3[0], out3[1], out3[2]
for n in range(71, -1, -1):
tmp = InvRoundFunc(X[n+3])
X[n] = (tmp ^ RoundFunc((X[n+2] ^ X[n+1] ^ keys[n]) & 0xffffffff)) & 0xffffffff
# 把 X0,X1,X2 转为小端字节追加
flag_bytes += struct.pack('<I', X[0])
flag_bytes += struct.pack('<I', X[1])
flag_bytes += struct.pack('<I', X[2])
print(flag_bytes.decode('ascii', errors='replace'))采一朵花,送给艾达(2)
IDA打开发现大量爆红,大概率是花指令
基本上都是这种简单结构的花指令,直接去除即可
去除完毕,恢复主函数如下
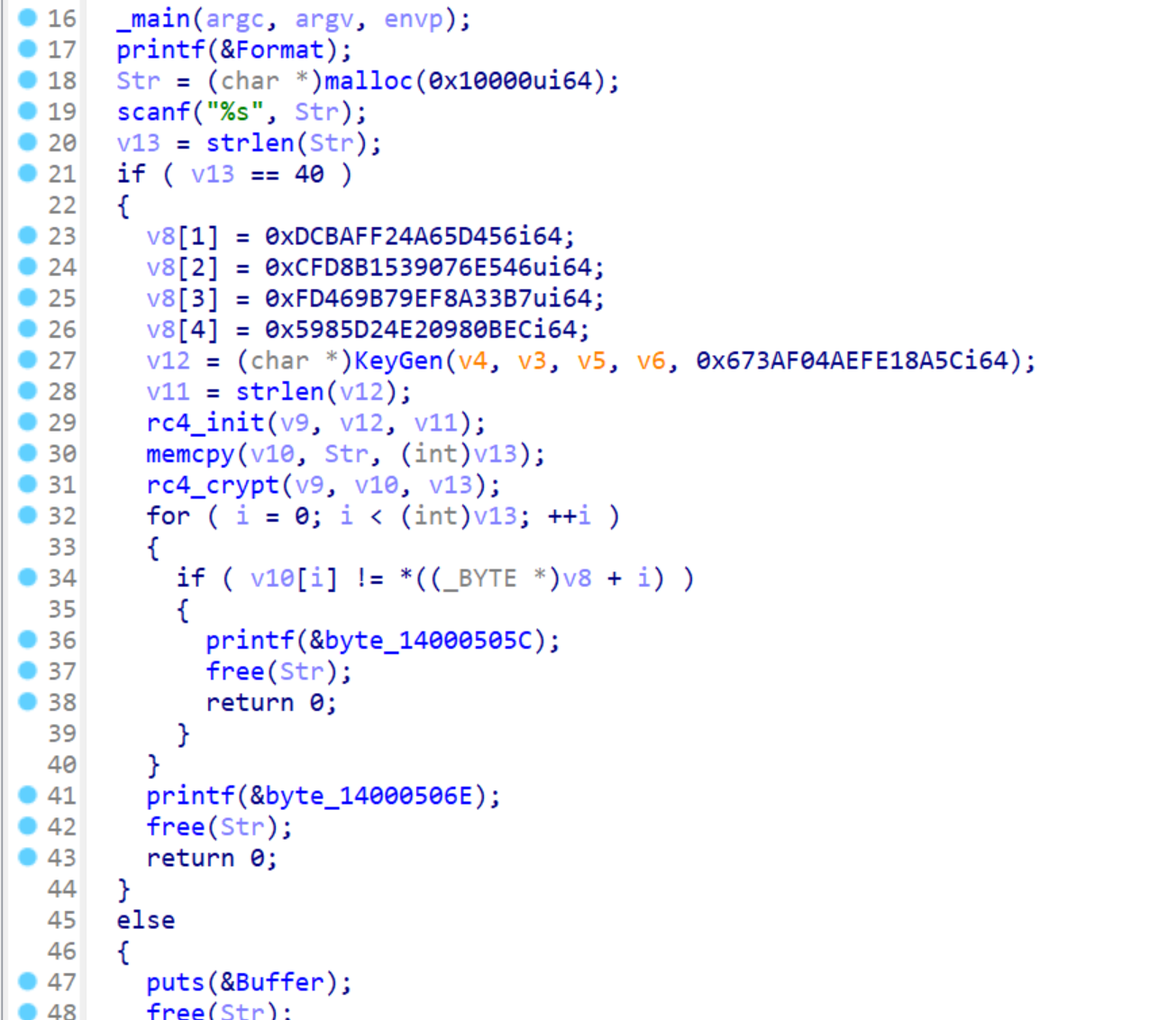
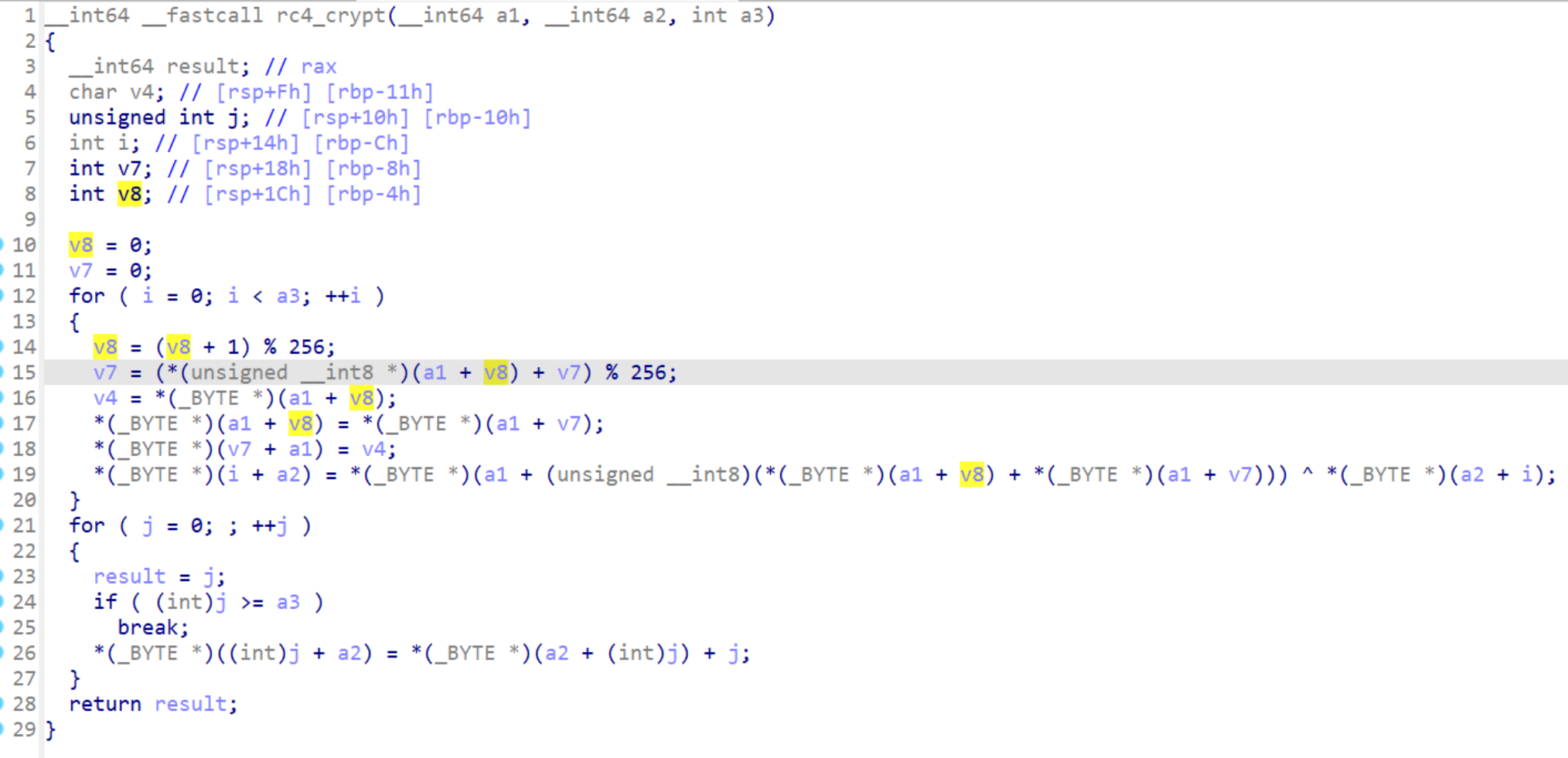
很明显的RC4,但是被魔改了
写脚本解密即可
python
s=[ 0xA2, 0x6F, 0x4F, 0xE8, 0x21, 0xE9, 0x9A, 0xBA, 0x66, 0x79,
0x2B, 0xD1, 0x98, 0xB6, 0xF0, 0x28, 0xDC, 0xA0, 0xDB, 0x2D,
0xE2, 0xA5, 0xC4, 0x35, 0xAC, 0x47, 0x40, 0xFB, 0x52, 0xFC,
0x8A, 0xF1, 0xB5, 0xB2, 0xBC, 0xD5, 0x5F, 0xC7, 0x26, 0x69,
0xDA, 0xD6, 0xC2, 0x2F, 0xD4, 0x97, 0xAD, 0xA6, 0x59, 0xC6,
0x5C, 0x64, 0x90, 0xE3, 0x07, 0x8D, 0xB3, 0x56, 0x19, 0x76,
0x05, 0x70, 0xC8, 0x85, 0x3B, 0x77, 0x60, 0x6A, 0xDE, 0xBE,
0x9B, 0x93, 0xE5, 0x54, 0x88, 0x4C, 0x4A, 0x91, 0x74, 0xC0,
0x2A, 0x20, 0x22, 0xFE, 0xFF, 0xDD, 0x99, 0xF4, 0x51, 0x11,
0x5E, 0x24, 0x71, 0xB7, 0xCB, 0x37, 0xC9, 0xEE, 0x44, 0x13,
0x7F, 0x06, 0x17, 0x0A, 0x23, 0x62, 0x7B, 0x68, 0xE0, 0x5A,
0x10, 0x3E, 0xA1, 0x89, 0x42, 0x65, 0x6D, 0x3D, 0x41, 0x58,
0x95, 0x34, 0x0E, 0xE1, 0xFD, 0x31, 0x4B, 0x92, 0x39, 0xB4,
0x1A, 0x7E, 0xC3, 0x57, 0x78, 0x9D, 0xD3, 0xF8, 0xCF, 0x3C,
0x1C, 0xC1, 0x7C, 0x96, 0x1F, 0x55, 0x7D, 0xBD, 0xF3, 0x8E,
0x04, 0x94, 0x25, 0x73, 0x7A, 0xFA, 0xEC, 0x46, 0x6C, 0x8F,
0x1D, 0xA9, 0x43, 0x80, 0x1E, 0xA8, 0x5D, 0xCD, 0xF2, 0x53,
0x9C, 0xD2, 0x4D, 0x3A, 0x01, 0xD0, 0x8C, 0x48, 0x30, 0x18,
0xBB, 0x75, 0xE7, 0xBF, 0xEA, 0x36, 0xAE, 0x0D, 0x27, 0x87,
0xF9, 0x2E, 0x02, 0xD9, 0xE4, 0xF5, 0xF6, 0x61, 0xAA, 0xB0,
0x38, 0xD7, 0x49, 0x15, 0xD8, 0xB9, 0xE6, 0x6E, 0x81, 0x8B,
0x67, 0xB8, 0x72, 0xEB, 0xA4, 0x6B, 0x32, 0xED, 0x5B, 0x84,
0xEF, 0x12, 0x08, 0x2C, 0x86, 0x50, 0x3F, 0x4E, 0x83, 0x9E,
0xCA, 0x0B, 0x0C, 0x29, 0x9F, 0xAB, 0x82, 0xCC, 0xCE, 0x33,
0x0F, 0xA3, 0xF7, 0xDF, 0xB1, 0x03, 0x00, 0x09, 0xAF, 0x16,
0xA7, 0x1B, 0xC5, 0x14, 0x45, 0x63]
# -*- coding: utf-8 -*-
# 魔改 RC4 解密脚本
# 已知:加密后的数据 cipher_bytes, 以及初始 S 盒 S_box (256字节)
def rc4_decrypt_mod(cipher_bytes, S_box):
"""魔改 RC4 解密:撤销 +i,再执行 RC4"""
data = list(cipher_bytes)
S = list(S_box)
# Step 1: 撤销 "+i"
for i in range(len(data)):
data[i] = (data[i] - i) & 0xFF
# Step 2: 标准 RC4 PRGA
i = j = 0
for k in range(len(data)):
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
data[k] ^= S[(S[i] + S[j]) % 256]
return bytes(data)
# ===========================
# 在这里填入你的数据
# ===========================
# 示例:密文和 S盒 都是字节序列(可以从内存dump出)
cipher_hex = [
0x50, 0x59, 0xA2, 0x94, 0x2E, 0x8E, 0x5C, 0x95, 0x79, 0x16,
0xE5, 0x36, 0x60, 0xC7, 0xE8, 0x06, 0x33, 0x78, 0xF0, 0xD0,
0x36, 0xC8, 0x73, 0x1B, 0x65, 0x40, 0xB5, 0xD4, 0xE8, 0x9C,
0x65, 0xF4, 0xBA, 0x62, 0xD0
]
from struct import pack
def rc4_decrypt_mod(cipher_bytes, S_box):
"""魔改RC4解密:撤销+i,再标准RC4"""
data = list(cipher_bytes)
S = list(S_box)
# Step 1: 撤销 "+i"
for i in range(len(data)):
data[i] = (data[i] - i) & 0xFF
# Step 2: 标准 RC4 PRGA
i = j = 0
for k in range(len(data)):
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
data[k] ^= S[(S[i] + S[j]) % 256]
return bytes(data)
# ===========================
# 密文(按小端拼接)
# ===========================
v5 = [
0x673AF04AEFE18A5C,
0xDCBAFF24A65D456,
0xCFD8B1539076E546,
0xFD469B79EF8A33B7,
0x5985D24E20980BEC
]
cipher_bytes = b''.join(pack("<Q", x) for x in v5) # 小端序拼接
# ===========================
# 执行解密
# ===========================
plaintext = rc4_decrypt_mod(cipher_bytes, s)
print("解密结果字节:", plaintext)
try:
print("可读字符串:", plaintext.decode(errors="ignore"))
except:
passpyz3
python打包的文件,用pyinstxtractor解包
解这个pyc文件
得到源码如下:
python
# Source Generated with Decompyle++
# File: task.pyc (Python 3.12)
def check(flag):
if 47 * flag[0] + 41 * flag[1] + 32 * flag[2] + 56 * flag[3] + 52 * flag[4] + 67 * flag[5] + 13 * flag[6] + 25 * flag[7] + 20 * flag[8] + 98 * flag[9] + 88 * flag[10] + 65 * flag[11] + 82 * flag[12] + 92 * flag[13] + 3 * flag[14] + 29 * flag[15] + 93 * flag[16] + 88 * flag[17] + 45 * flag[18] + 58 * flag[19] + 40 * flag[20] + 72 * flag[21] + 99 * flag[22] + 10 * flag[23] + 94 * flag[24] + 62 * flag[25] + 82 * flag[26] + 92 * flag[27] + 23 * flag[28] + 46 * flag[29] + 55 * flag[30] + 72 * flag[31] + 44 * flag[32] + 9 * flag[33] + 65 * flag[34] + 42 * flag[35] == 176386 and 10 * flag[0] + 98 * flag[1] + 5 * flag[2] + 28 * flag[3] + 68 * flag[4] + 20 * flag[5] + 2 * flag[6] + 22 * flag[7] + 65 * flag[8] + 44 * flag[9] + 85 * flag[10] + 97 * flag[11] + 33 * flag[12] + 74 * flag[13] + 93 * flag[14] + 74 * flag[15] + 41 * flag[16] + 65 * flag[17] + 32 * flag[18] + 93 * flag[19] + 22 * flag[20] + 69 * flag[21] + 68 * flag[22] + 57 * flag[23] + 47 * flag[24] + 29 * flag[25] + 74 * flag[26] + 54 * flag[27] + 91 * flag[28] + 90 * flag[29] + 26 * flag[30] + 11 * flag[31] + 89 * flag[32] + 57 * flag[33] + 100 * flag[34] + 95 * flag[35] == 186050 and 25 * flag[0] + 22 * flag[1] + 54 * flag[2] + 5 * flag[3] + 8 * flag[4] + 3 * flag[5] + 12 * flag[6] + 70 * flag[7] + 25 * flag[8] + 61 * flag[9] + 68 * flag[10] + 12 * flag[11] + 27 * flag[12] + 42 * flag[13] + 83 * flag[14] + 91 * flag[15] + 67 * flag[16] + 46 * flag[17] + 8 * flag[18] + 45 * flag[19] + 94 * flag[20] + 80 * flag[21] + 69 * flag[22] + 95 * flag[23] + 12 * flag[24] + 21 * flag[25] + 94 * flag[26] + 82 * flag[27] + 93 * flag[28] + 41 * flag[29] + 4 * flag[30] + 56 * flag[31] + 92 * flag[32] + 77 * flag[33] + 15 * flag[34] + 30 * flag[35] == 154690 and 33 * flag[0] + 49 * flag[1] + 56 * flag[2] + 40 * flag[3] + 90 * flag[4] + 59 * flag[5] + 82 * flag[6] + 6 * flag[7] + 81 * flag[8] + 32 * flag[9] + 23 * flag[10] + 76 * flag[11] + 93 * flag[12] + 83 * flag[13] + 10 * flag[14] + 44 * flag[15] + 58 * flag[16] + 33 * flag[17] + 79 * flag[18] + 77 * flag[19] + 82 * flag[20] + 56 * flag[21] + 70 * flag[22] + 34 * flag[23] + 45 * flag[24] + 76 * flag[25] + 57 * flag[26] + 43 * flag[27] + 100 * flag[28] + 19 * flag[29] + 11 * flag[30] + 90 * flag[31] + 3 * flag[32] + 60 * flag[33] + 57 * flag[34] + 23 * flag[35] == 172116 and 65 * flag[0] + 70 * flag[1] + 20 * flag[2] + 32 * flag[3] + 75 * flag[4] + 30 * flag[5] + 3 * flag[6] + 78 * flag[7] + 35 * flag[8] + 45 * flag[9] + 95 * flag[10] + 93 * flag[11] + 52 * flag[12] + 32 * flag[13] + 88 * flag[14] + 94 * flag[15] + 67 * flag[16] + 34 * flag[17] + 91 * flag[18] + 88 * flag[19] + 31 * flag[20] + 61 * flag[21] + 17 * flag[22] + 99 * flag[23] + 100 * flag[24] + 49 * flag[25] + 4 * flag[26] + 60 * flag[27] + 81 * flag[28] + 88 * flag[29] + 43 * flag[30] + 34 * flag[31] + 30 * flag[32] + 52 * flag[33] + 18 * flag[34] + 100 * flag[35] == 190544 and 81 * flag[0] + 42 * flag[1] + 28 * flag[2] + 98 * flag[3] + 31 * flag[4] + 46 * flag[5] + 64 * flag[6] + 15 * flag[7] + 49 * flag[8] + 13 * flag[9] + 100 * flag[10] + 81 * flag[11] + 32 * flag[12] + 52 * flag[13] + 59 * flag[14] + 24 * flag[15] + 94 * flag[16] + 32 * flag[17] + 93 * flag[18] + 32 * flag[19] + 13 * flag[20] + 89 * flag[21] + 37 * flag[22] + 30 * flag[23] + 78 * flag[24] + 81 * flag[25] + 9 * flag[26] + 45 * flag[27] + 93 * flag[28] + 100 * flag[29] + 97 * flag[30] + 10 * flag[31] + 80 * flag[32] + 54 * flag[33] + 88 * flag[34] + 85 * flag[35] == 190323 and 76 * flag[0] + 54 * flag[1] + 5 * flag[2] + 14 * flag[3] + 62 * flag[4] + 44 * flag[5] + 24 * flag[6] + 29 * flag[7] + 85 * flag[8] + 87 * flag[9] + 19 * flag[10] + 3 * flag[11] + 65 * flag[12] + 24 * flag[13] + 92 * flag[14] + 37 * flag[15] + 57 * flag[16] + 20 * flag[17] + 45 * flag[18] + 5 * flag[19] + 13 * flag[20] + 91 * flag[21] + 92 * flag[22] + 75 * flag[23] + 36 * flag[24] + 79 * flag[25] + 12 * flag[26] + 22 * flag[27] + 75 * flag[28] + 82 * flag[29] + 28 * flag[30] + 82 * flag[31] + 24 * flag[32] + 53 * flag[33] + 56 * flag[34] + 92 * flag[35] == 162017 and 53 * flag[0] + 52 * flag[1] + 72 * flag[2] + 23 * flag[3] + 26 * flag[4] + 13 * flag[5] + 62 * flag[6] + 96 * flag[7] + 67 * flag[8] + 96 * flag[9] + 66 * flag[10] + 41 * flag[11] + 5 * flag[12] + 18 * flag[13] + 37 * flag[14] + 13 * flag[15] + 61 * flag[16] + 71 * flag[17] + 91 * flag[18] + 96 * flag[19] + 56 * flag[20] + 3 * flag[21] + 65 * flag[22] + 14 * flag[23] + 57 * flag[24] + 69 * flag[25] + 75 * flag[26] + 68 * flag[27] + 10 * flag[28] + 60 * flag[29] + 62 * flag[30] + 95 * flag[31] + 53 * flag[32] + 19 * flag[33] + 7 * flag[34] + 56 * flag[35] == 165118 and 26 * flag[0] + 7 * flag[1] + 49 * flag[2] + 14 * flag[3] + 36 * flag[4] + 87 * flag[5] + 21 * flag[6] + 35 * flag[7] + 15 * flag[8] + 91 * flag[9] + 15 * flag[10] + 100 * flag[11] + 8 * flag[12] + 32 * flag[13] + 100 * flag[14] + 35 * flag[15] + 66 * flag[16] + 3 * flag[17] + 79 * flag[18] + 96 * flag[19] + 82 * flag[20] + 95 * flag[21] + 68 * flag[22] + 13 * flag[23] + 86 * flag[24] + 51 * flag[25] + 24 * flag[26] + 76 * flag[27] + 30 * flag[28] + 60 * flag[29] + 29 * flag[30] + 70 * flag[31] + 40 * flag[32] + 90 * flag[33] + 44 * flag[34] + 3 * flag[35] == 153332 and 47 * flag[0] + 19 * flag[1] + 37 * flag[2] + 93 * flag[3] + 73 * flag[4] + 30 * flag[5] + 45 * flag[6] + 47 * flag[7] + 72 * flag[8] + 85 * flag[9] + 37 * flag[10] + 68 * flag[11] + 89 * flag[12] + 34 * flag[13] + 4 * flag[14] + 50 * flag[15] + 87 * flag[16] + 33 * flag[17] + 87 * flag[18] + 43 * flag[19] + 9 * flag[20] + 61 * flag[21] + 93 * flag[22] + 49 * flag[23] + 74 * flag[24] + 49 * flag[25] + 68 * flag[26] + 29 * flag[27] + 54 * flag[28] + 54 * flag[29] + 37 * flag[30] + 79 * flag[31] + 33 * flag[32] + 65 * flag[33] + 59 * flag[34] + 15 * flag[35] == 168472 and 79 * flag[0] + 73 * flag[1] + 60 * flag[2] + 62 * flag[3] + 25 * flag[4] + 16 * flag[5] + 77 * flag[6] + 81 * flag[7] + 79 * flag[8] + 31 * flag[9] + 82 * flag[10] + 84 * flag[11] + 62 * flag[12] + 36 * flag[13] + 18 * flag[14] + 20 * flag[15] + 46 * flag[16] + 57 * flag[17] + 21 * flag[18] + 40 * flag[19] + 3 * flag[20] + 50 * flag[21] + 58 * flag[22] + 80 * flag[23] + 84 * flag[24] + 71 * flag[25] + 87 * flag[26] + 3 * flag[27] + 13 * flag[28] + 77 * flag[29] + 83 * flag[30] + 39 * flag[31] + 55 * flag[32] + 34 * flag[33] + 41 * flag[34] + 63 * flag[35] == 178706 and 7 * flag[0] + 50 * flag[1] + 26 * flag[2] + 79 * flag[3] + 21 * flag[4] + 42 * flag[5] + 83 * flag[6] + 94 * flag[7] + 63 * flag[8] + 83 * flag[9] + 3 * flag[10] + 68 * flag[11] + 25 * flag[12] + 91 * flag[13] + 3 * flag[14] + 5 * flag[15] + 17 * flag[16] + 61 * flag[17] + 3 * flag[18] + 40 * flag[19] + 87 * flag[20] + 11 * flag[21] + 27 * flag[22] + 74 * flag[23] + 73 * flag[24] + 21 * flag[25] + 56 * flag[26] + 46 * flag[27] + 36 * flag[28] + 24 * flag[29] + 14 * flag[30] + 63 * flag[31] + 21 * flag[32] + 71 * flag[33] + 30 * flag[34] + 53 * flag[35] == 143852 and 57 * flag[0] + 51 * flag[1] + 49 * flag[2] + 15 * flag[3] + 94 * flag[4] + 34 * flag[5] + 27 * flag[6] + 5 * flag[7] + 100 * flag[8] + 68 * flag[9] + 67 * flag[10] + 81 * flag[11] + 10 * flag[12] + 5 * flag[13] + 85 * flag[14] + 70 * flag[15] + 80 * flag[16] + 20 * flag[17] + 89 * flag[18] + 30 * flag[19] + 84 * flag[20] + 35 * flag[21] + 41 * flag[22] + 87 * flag[23] + 75 * flag[24] + 67 * flag[25] + 20 * flag[26] + 33 * flag[27] + 29 * flag[28] + 6 * flag[29] + 97 * flag[30] + 25 * flag[31] + 10 * flag[32] + 18 * flag[33] + 23 * flag[34] + 30 * flag[35] == 154052 and 97 * flag[0] + 93 * flag[1] + 10 * flag[2] + 44 * flag[3] + 28 * flag[4] + 22 * flag[5] + 17 * flag[6] + 41 * flag[7] + 47 * flag[8] + 62 * flag[9] + 42 * flag[10] + 47 * flag[11] + 61 * flag[12] + 32 * flag[13] + 31 * flag[14] + 52 * flag[15] + 47 * flag[16] + 92 * flag[17] + 42 * flag[18] + 37 * flag[19] + 7 * flag[20] + 40 * flag[21] + 48 * flag[22] + 40 * flag[23] + 11 * flag[24] + 96 * flag[25] + 51 * flag[26] + 42 * flag[27] + 66 * flag[28] + 8 * flag[29] + 89 * flag[30] + 64 * flag[31] + 30 * flag[32] + 11 * flag[33] + 8 * flag[34] + 83 * flag[35] == 147899 and 51 * flag[0] + 94 * flag[1] + 58 * flag[2] + 76 * flag[3] + 21 * flag[4] + 10 * flag[5] + 75 * flag[6] + 4 * flag[7] + 55 * flag[8] + 37 * flag[9] + 71 * flag[10] + 97 * flag[11] + 27 * flag[12] + 93 * flag[13] + 82 * flag[14] + 94 * flag[15] + 38 * flag[16] + 69 * flag[17] + 36 * flag[18] + 58 * flag[19] + 93 * flag[20] + 18 * flag[21] + 54 * flag[22] + 59 * flag[23] + 12 * flag[24] + 12 * flag[25] + 54 * flag[26] + 83 * flag[27] + 73 * flag[28] + 83 * flag[29] + 33 * flag[30] + 12 * flag[31] + 78 * flag[32] + 38 * flag[33] + 45 * flag[34] + 57 * flag[35] == 176754 and 78 * flag[0] + 29 * flag[1] + 8 * flag[2] + 47 * flag[3] + 48 * flag[4] + 88 * flag[5] + 18 * flag[6] + 88 * flag[7] + 50 * flag[8] + 58 * flag[9] + 36 * flag[10] + 88 * flag[11] + 9 * flag[12] + 74 * flag[13] + 85 * flag[14] + 5 * flag[15] + 91 * flag[16] + 58 * flag[17] + 85 * flag[18] + 46 * flag[19] + 89 * flag[20] + 76 * flag[21] + 61 * flag[22] + 6 * flag[23] + 61 * flag[24] + 78 * flag[25] + 4 * flag[26] + 48 * flag[27] + 50 * flag[28] + 69 * flag[29] + 23 * flag[30] + 70 * flag[31] + 23 * flag[32] + 15 * flag[33] + 22 * flag[34] + 68 * flag[35] == 171970 and 75 * flag[0] + 2 * flag[1] + 94 * flag[2] + 97 * flag[3] + 72 * flag[4] + 62 * flag[5] + 78 * flag[6] + 42 * flag[7] + 69 * flag[8] + 11 * flag[9] + 37 * flag[10] + 3 * flag[11] + 29 * flag[12] + 15 * flag[13] + 39 * flag[14] + 33 * flag[15] + 18 * flag[16] + 33 * flag[17] + 12 * flag[18] + 64 * flag[19] + 6 * flag[20] + 18 * flag[21] + 34 * flag[22] + 15 * flag[23] + 3 * flag[24] + 100 * flag[25] + 85 * flag[26] + 32 * flag[27] + 97 * flag[28] + 93 * flag[29] + 84 * flag[30] + 73 * flag[31] + 26 * flag[32] + 31 * flag[33] + 71 * flag[34] + 97 * flag[35] == 166497 and 59 * flag[0] + 26 * flag[1] + 48 * flag[2] + 86 * flag[3] + 58 * flag[4] + 70 * flag[5] + 61 * flag[6] + 100 * flag[7] + 63 * flag[8] + 74 * flag[9] + 26 * flag[10] + 38 * flag[11] + 24 * flag[12] + 45 * flag[13] + 52 * flag[14] + 32 * flag[15] + 91 * flag[16] + 89 * flag[17] + 19 * flag[18] + 59 * flag[19] + 87 * flag[20] + 5 * flag[21] + 15 * flag[22] + 68 * flag[23] + 72 * flag[24] + 67 * flag[25] + 2 * flag[26] + 65 * flag[27] + 46 * flag[28] + 10 * flag[29] + 33 * flag[30] + 79 * flag[31] + 11 * flag[32] + 16 * flag[33] + 73 * flag[34] + 53 * flag[35] == 173887 and 6 * flag[0] + 66 * flag[1] + 59 * flag[2] + 76 * flag[3] + 86 * flag[4] + 20 * flag[5] + 59 * flag[6] + 34 * flag[7] + 28 * flag[8] + 48 * flag[9] + 86 * flag[10] + 5 * flag[11] + 87 * flag[12] + 13 * flag[13] + 95 * flag[14] + 87 * flag[15] + 65 * flag[16] + 35 * flag[17] + 58 * flag[18] + 10 * flag[19] + 98 * flag[20] + 100 * flag[21] + 4 * flag[22] + 78 * flag[23] + 66 * flag[24] + 57 * flag[25] + 34 * flag[26] + 86 * flag[27] + 62 * flag[28] + 36 * flag[29] + 92 * flag[30] + 28 * flag[31] + 3 * flag[32] + 24 * flag[33] + 49 * flag[34] + 28 * flag[35] == 173189 and 25 * flag[0] + 48 * flag[1] + 44 * flag[2] + 16 * flag[3] + 99 * flag[4] + 100 * flag[5] + 69 * flag[6] + 26 * flag[7] + 65 * flag[8] + 32 * flag[9] + 18 * flag[10] + 65 * flag[11] + 58 * flag[12] + 72 * flag[13] + 61 * flag[14] + 56 * flag[15] + 10 * flag[16] + 78 * flag[17] + 93 * flag[18] + 98 * flag[19] + 39 * flag[20] + 43 * flag[21] + 87 * flag[22] + 12 * flag[23] + 42 * flag[24] + 100 * flag[25] + 100 * flag[26] + 47 * flag[27] + 31 * flag[28] + 51 * flag[29] + 75 * flag[30] + 10 * flag[31] + 63 * flag[32] + 48 * flag[33] + 22 * flag[34] + 87 * flag[35] == 174138 and 61 * flag[0] + 13 * flag[1] + 100 * flag[2] + 59 * flag[3] + 31 * flag[4] + 9 * flag[5] + 28 * flag[6] + 7 * flag[7] + 27 * flag[8] + 63 * flag[9] + 11 * flag[10] + 57 * flag[11] + 95 * flag[12] + 79 * flag[13] + 21 * flag[14] + 30 * flag[15] + 60 * flag[16] + 81 * flag[17] + 43 * flag[18] + 32 * flag[19] + 30 * flag[20] + 34 * flag[21] + 80 * flag[22] + 53 * flag[23] + 28 * flag[24] + 39 * flag[25] + 74 * flag[26] + 21 * flag[27] + 18 * flag[28] + 92 * flag[29] + 73 * flag[30] + 60 * flag[31] + 21 * flag[32] + 69 * flag[33] + 76 * flag[34] + 84 * flag[35] == 157623 and 22 * flag[0] + 62 * flag[1] + 61 * flag[2] + 20 * flag[3] + 66 * flag[4] + 2 * flag[5] + 11 * flag[6] + 82 * flag[7] + 93 * flag[8] + 13 * flag[9] + 69 * flag[10] + 37 * flag[11] + 92 * flag[12] + 80 * flag[13] + 66 * flag[14] + 47 * flag[15] + 28 * flag[16] + 14 * flag[17] + 62 * flag[18] + 56 * flag[19] + 89 * flag[20] + 29 * flag[21] + 39 * flag[22] + 38 * flag[23] + 46 * flag[24] + 10 * flag[25] + 6 * flag[26] + 82 * flag[27] + 77 * flag[28] + 78 * flag[29] + 45 * flag[30] + 50 * flag[31] + 5 * flag[32] + 73 * flag[33] + 17 * flag[34] + 65 * flag[35] == 154943 and 5 * flag[0] + 84 * flag[1] + 83 * flag[2] + 77 * flag[3] + 76 * flag[4] + 60 * flag[5] + 20 * flag[6] + 48 * flag[7] + 53 * flag[8] + 14 * flag[9] + 98 * flag[10] + 50 * flag[11] + 37 * flag[12] + 15 * flag[13] + 31 * flag[14] + 69 * flag[15] + 55 * flag[16] + 37 * flag[17] + 64 * flag[18] + 35 * flag[19] + 26 * flag[20] + 20 * flag[21] + 18 * flag[22] + 67 * flag[23] + 50 * flag[24] + 57 * flag[25] + 60 * flag[26] + 71 * flag[27] + 4 * flag[28] + 35 * flag[29] + 23 * flag[30] + 52 * flag[31] + 11 * flag[32] + 15 * flag[33] + 83 * flag[34] + 51 * flag[35] == 156078 and 33 * flag[0] + 47 * flag[1] + 89 * flag[2] + 52 * flag[3] + 89 * flag[4] + 55 * flag[5] + 98 * flag[6] + 28 * flag[7] + 48 * flag[8] + 90 * flag[9] + 69 * flag[10] + 29 * flag[11] + 68 * flag[12] + 24 * flag[13] + 19 * flag[14] + 18 * flag[15] + 44 * flag[16] + 27 * flag[17] + 14 * flag[18] + 64 * flag[19] + 15 * flag[20] + 31 * flag[21] + 23 * flag[22] + 2 * flag[23] + 36 * flag[24] + 45 * flag[25] + 37 * flag[26] + 71 * flag[27] + 61 * flag[28] + 92 * flag[29] + 28 * flag[30] + 64 * flag[31] + 13 * flag[32] + 66 * flag[33] + 98 * flag[34] + 3 * flag[35] == 156158 and 80 * flag[0] + 88 * flag[1] + 68 * flag[2] + 66 * flag[3] + 46 * flag[4] + 75 * flag[5] + 32 * flag[6] + 19 * flag[7] + 36 * flag[8] + 83 * flag[9] + 63 * flag[10] + 86 * flag[11] + 79 * flag[12] + 30 * flag[13] + 61 * flag[14] + 50 * flag[15] + 100 * flag[16] + 52 * flag[17] + 66 * flag[18] + 30 * flag[19] + 20 * flag[20] + 97 * flag[21] + 45 * flag[22] + 46 * flag[23] + 38 * flag[24] + 21 * flag[25] + 32 * flag[26] + 79 * flag[27] + 68 * flag[28] + 43 * flag[29] + 65 * flag[30] + 47 * flag[31] + 86 * flag[32] + 30 * flag[33] + 74 * flag[34] + 18 * flag[35] == 181770 and 11 * flag[0] + 58 * flag[1] + 95 * flag[2] + 67 * flag[3] + 96 * flag[4] + 74 * flag[5] + 60 * flag[6] + 11 * flag[7] + 21 * flag[8] + 14 * flag[9] + 100 * flag[10] + 60 * flag[11] + 70 * flag[12] + 92 * flag[13] + 92 * flag[14] + 39 * flag[15] + 43 * flag[16] + 52 * flag[17] + 5 * flag[18] + 22 * flag[19] + 90 * flag[20] + 70 * flag[21] + 12 * flag[22] + 52 * flag[23] + 36 * flag[24] + 21 * flag[25] + 45 * flag[26] + 59 * flag[27] + 74 * flag[28] + 46 * flag[29] + 11 * flag[30] + 60 * flag[31] + 8 * flag[32] + 52 * flag[33] + 14 * flag[34] + 77 * flag[35] == 173577 and 57 * flag[0] + 37 * flag[1] + 94 * flag[2] + 43 * flag[3] + 53 * flag[4] + 55 * flag[5] + 7 * flag[6] + 83 * flag[7] + 91 * flag[8] + 61 * flag[9] + 86 * flag[10] + 6 * flag[11] + 44 * flag[12] + 87 * flag[13] + 61 * flag[14] + 92 * flag[15] + 24 * flag[16] + 74 * flag[17] + 100 * flag[18] + 22 * flag[19] + 12 * flag[20] + 68 * flag[21] + 19 * flag[22] + 88 * flag[23] + 81 * flag[24] + 83 * flag[25] + 70 * flag[26] + 39 * flag[27] + 30 * flag[28] + 82 * flag[29] + 30 * flag[30] + 35 * flag[31] + 55 * flag[32] + 18 * flag[33] + 27 * flag[34] + 80 * flag[35] == 180922 and 80 * flag[0] + 14 * flag[1] + 5 * flag[2] + 89 * flag[3] + 71 * flag[4] + 82 * flag[5] + 44 * flag[6] + 8 * flag[7] + 33 * flag[8] + 26 * flag[9] + 77 * flag[10] + 49 * flag[11] + 36 * flag[12] + 90 * flag[13] + 73 * flag[14] + 71 * flag[15] + 66 * flag[16] + 4 * flag[17] + 37 * flag[18] + 78 * flag[19] + 38 * flag[20] + 18 * flag[21] + 15 * flag[22] + 79 * flag[23] + 6 * flag[24] + 74 * flag[25] + 18 * flag[26] + 85 * flag[27] + 56 * flag[28] + 53 * flag[29] + 90 * flag[30] + 75 * flag[31] + 52 * flag[32] + 2 * flag[33] + 13 * flag[34] + 54 * flag[35] == 158596 and 96 * flag[0] + 29 * flag[1] + 37 * flag[2] + 70 * flag[3] + 92 * flag[4] + 80 * flag[5] + 24 * flag[6] + 36 * flag[7] + 32 * flag[8] + 29 * flag[9] + 78 * flag[10] + 45 * flag[11] + 58 * flag[12] + 55 * flag[13] + 16 * flag[14] + 92 * flag[15] + 71 * flag[16] + 82 * flag[17] + 86 * flag[18] + 23 * flag[19] + 4 * flag[20] + 58 * flag[21] + 16 * flag[22] + 18 * flag[23] + 38 * flag[24] + 53 * flag[25] + 82 * flag[26] + 76 * flag[27] + 83 * flag[28] + 73 * flag[29] + 87 * flag[30] + 36 * flag[31] + 61 * flag[32] + 85 * flag[33] + 61 * flag[34] + 69 * flag[35] == 181072 and 14 * flag[0] + 71 * flag[1] + 53 * flag[2] + 46 * flag[3] + 59 * flag[4] + 53 * flag[5] + 22 * flag[6] + 69 * flag[7] + 67 * flag[8] + 43 * flag[9] + 23 * flag[10] + 14 * flag[11] + 77 * flag[12] + 95 * flag[13] + 19 * flag[14] + 83 * flag[15] + 79 * flag[16] + 41 * flag[17] + 12 * flag[18] + 53 * flag[19] + 3 * flag[20] + 4 * flag[21] + 65 * flag[22] + 92 * flag[23] + 64 * flag[24] + 52 * flag[25] + 3 * flag[26] + 59 * flag[27] + 89 * flag[28] + 75 * flag[29] + 12 * flag[30] + 46 * flag[31] + 61 * flag[32] + 53 * flag[33] + 97 * flag[34] + 43 * flag[35] == 163777 and 57 * flag[0] + 99 * flag[1] + 49 * flag[2] + 100 * flag[3] + 68 * flag[4] + 99 * flag[5] + 26 * flag[6] + 65 * flag[7] + 47 * flag[8] + 65 * flag[9] + 90 * flag[10] + 68 * flag[11] + 84 * flag[12] + 4 * flag[13] + 9 * flag[14] + 43 * flag[15] + 88 * flag[16] + 33 * flag[17] + 48 * flag[18] + 88 * flag[19] + 37 * flag[20] + 31 * flag[21] + 21 * flag[22] + 94 * flag[23] + 22 * flag[24] + 93 * flag[25] + 70 * flag[26] + 14 * flag[27] + 13 * flag[28] + 28 * flag[29] + 83 * flag[30] + 12 * flag[31] + 80 * flag[32] + 58 * flag[33] + 43 * flag[34] + 97 * flag[35] == 187620 and 33 * flag[0] + 94 * flag[1] + 56 * flag[2] + 48 * flag[3] + 13 * flag[4] + 44 * flag[5] + 81 * flag[6] + 42 * flag[7] + 19 * flag[8] + 96 * flag[9] + 67 * flag[10] + 79 * flag[11] + 12 * flag[12] + 67 * flag[13] + 34 * flag[14] + 72 * flag[15] + 45 * flag[16] + 48 * flag[17] + 24 * flag[18] + 71 * flag[19] + 65 * flag[20] + 13 * flag[21] + 32 * flag[22] + 97 * flag[23] + 48 * flag[24] + 42 * flag[25] + 65 * flag[26] + 95 * flag[27] + 54 * flag[28] + 9 * flag[29] + 35 * flag[30] + 57 * flag[31] + 18 * flag[32] + 20 * flag[33] + 83 * flag[34] + 76 * flag[35] == 169266 and 31 * flag[0] + 38 * flag[1] + 83 * flag[2] + 45 * flag[3] + 28 * flag[4] + 97 * flag[5] + 54 * flag[6] + 11 * flag[7] + 80 * flag[8] + 45 * flag[9] + 92 * flag[10] + 13 * flag[11] + 52 * flag[12] + 94 * flag[13] + 51 * flag[14] + 30 * flag[15] + 11 * flag[16] + 61 * flag[17] + 46 * flag[18] + 10 * flag[19] + 28 * flag[20] + 72 * flag[21] + 20 * flag[22] + 95 * flag[23] + 90 * flag[24] + 39 * flag[25] + 32 * flag[26] + 95 * flag[27] + 19 * flag[28] + 3 * flag[29] + 65 * flag[30] + 71 * flag[31] + 73 * flag[32] + 80 * flag[33] + 23 * flag[34] + 71 * flag[35] == 162587 and 9 * flag[0] + 81 * flag[1] + 80 * flag[2] + 37 * flag[3] + 96 * flag[4] + 72 * flag[5] + 95 * flag[6] + 93 * flag[7] + 26 * flag[8] + 98 * flag[9] + 50 * flag[10] + 79 * flag[11] + 57 * flag[12] + 13 * flag[13] + 49 * flag[14] + 96 * flag[15] + 82 * flag[16] + 84 * flag[17] + 89 * flag[18] + 40 * flag[19] + 38 * flag[20] + 66 * flag[21] + 81 * flag[22] + 81 * flag[23] + 79 * flag[24] + 77 * flag[25] + 86 * flag[26] + 68 * flag[27] + 26 * flag[28] + 37 * flag[29] + 15 * flag[30] + 56 * flag[31] + 13 * flag[32] + 17 * flag[33] + 50 * flag[34] + 37 * flag[35] == 198705 and 82 * flag[0] + 57 * flag[1] + 33 * flag[2] + 32 * flag[3] + 79 * flag[4] + 25 * flag[5] + 54 * flag[6] + 27 * flag[7] + 50 * flag[8] + 14 * flag[9] + 72 * flag[10] + 31 * flag[11] + 28 * flag[12] + 66 * flag[13] + 4 * flag[14] + 6 * flag[15] + 48 * flag[16] + 34 * flag[17] + 63 * flag[18] + 51 * flag[19] + 12 * flag[20] + 21 * flag[21] + 73 * flag[22] + 66 * flag[23] + 53 * flag[24] + 38 * flag[25] + 54 * flag[26] + 59 * flag[27] + 76 * flag[28] + 63 * flag[29] + 61 * flag[30] + 30 * flag[31] + 84 * flag[32] + 80 * flag[33] + 98 * flag[34] + 46 * flag[35] == 160349 and 69 * flag[0] + 15 * flag[1] + 23 * flag[2] + 8 * flag[3] + 46 * flag[4] + 55 * flag[5] + 21 * flag[6] + 91 * flag[7] + 37 * flag[8] + 9 * flag[9] + 61 * flag[10] + 20 * flag[11] + 23 * flag[12] + 96 * flag[13] + 28 * flag[14] + 67 * flag[15] + 19 * flag[16] + 50 * flag[17] + 18 * flag[18] + 71 * flag[19] + 30 * flag[20] + 14 * flag[21] + 10 * flag[22] + 24 * flag[23] + 100 * flag[24] + 15 * flag[25] + 91 * flag[26] + 15 * flag[27] + 93 * flag[28] + 24 * flag[29] + 46 * flag[30] + 61 * flag[31] + 67 * flag[32] + 60 * flag[33] + 56 * flag[34] + 81 * flag[35] == 148095:
return True
return False
def main():
flag = str(input('Input your flag: ')).encode()
res = check(flag)
if res:
print('Right flag!')
return None
print('Wrong flag!')
if __name__ == '__main__':
main()
return None很明显一大堆约束条件,直接用z3求解即可
python
from z3 import *
# 提取所有方程的系数和常数项
# 每一行是一个方程:coeffs[0]*f0 + coeffs[1]*f1 + ... + coeffs[35]*f35 == const
equations = [
# 第一个方程
([47, 41, 32, 56, 52, 67, 13, 25, 20, 98, 88, 65, 82, 92, 3, 29, 93, 88, 45, 58, 40, 72, 99, 10, 94, 62, 82, 92, 23, 46, 55, 72, 44, 9, 65, 42], 176386),
([10, 98, 5, 28, 68, 20, 2, 22, 65, 44, 85, 97, 33, 74, 93, 74, 41, 65, 32, 93, 22, 69, 68, 57, 47, 29, 74, 54, 91, 90, 26, 11, 89, 57, 100, 95], 186050),
([25, 22, 54, 5, 8, 3, 12, 70, 25, 61, 68, 12, 27, 42, 83, 91, 67, 46, 8, 45, 94, 80, 69, 95, 12, 21, 94, 82, 93, 41, 4, 56, 92, 77, 15, 30], 154690),
([33, 49, 56, 40, 90, 59, 82, 6, 81, 32, 23, 76, 93, 83, 10, 44, 58, 33, 79, 77, 82, 56, 70, 34, 45, 76, 57, 43, 100, 19, 11, 90, 3, 60, 57, 23], 172116),
([65, 70, 20, 32, 75, 30, 3, 78, 35, 45, 95, 93, 52, 32, 88, 94, 67, 34, 91, 88, 31, 61, 17, 99, 100, 49, 4, 60, 81, 88, 43, 34, 30, 52, 18, 100], 190544),
([81, 42, 28, 98, 31, 46, 64, 15, 49, 13, 100, 81, 32, 52, 59, 24, 94, 32, 93, 32, 13, 89, 37, 30, 78, 81, 9, 45, 93, 100, 97, 10, 80, 54, 88, 85], 190323),
([76, 54, 5, 14, 62, 44, 24, 29, 85, 87, 19, 3, 65, 24, 92, 37, 57, 20, 45, 5, 13, 91, 92, 75, 36, 79, 12, 22, 75, 82, 28, 82, 24, 53, 56, 92], 162017),
([53, 52, 72, 23, 26, 13, 62, 96, 67, 96, 66, 41, 5, 18, 37, 13, 61, 71, 91, 96, 56, 3, 65, 14, 57, 69, 75, 68, 10, 60, 62, 95, 53, 19, 7, 56], 165118),
([26, 7, 49, 14, 36, 87, 21, 35, 15, 91, 15, 100, 8, 32, 100, 35, 66, 3, 79, 96, 82, 95, 68, 13, 86, 51, 24, 76, 30, 60, 29, 70, 40, 90, 44, 3], 153332),
([47, 19, 37, 93, 73, 30, 45, 47, 72, 85, 37, 68, 89, 34, 4, 50, 87, 33, 87, 43, 9, 61, 93, 49, 74, 49, 68, 29, 54, 54, 37, 79, 33, 65, 59, 15], 168472),
([79, 73, 60, 62, 25, 16, 77, 81, 79, 31, 82, 84, 62, 36, 18, 20, 46, 57, 21, 40, 3, 50, 58, 80, 84, 71, 87, 3, 13, 77, 83, 39, 55, 34, 41, 63], 178706),
([7, 50, 26, 79, 21, 42, 83, 94, 63, 83, 3, 68, 25, 91, 3, 5, 17, 61, 3, 40, 87, 11, 27, 74, 73, 21, 56, 46, 36, 24, 14, 63, 21, 71, 30, 53], 143852),
([57, 51, 49, 15, 94, 34, 27, 5, 100, 68, 67, 81, 10, 5, 85, 70, 80, 20, 89, 30, 84, 35, 41, 87, 75, 67, 20, 33, 29, 6, 97, 25, 10, 18, 23, 30], 154052),
([97, 93, 10, 44, 28, 22, 17, 41, 47, 62, 42, 47, 61, 32, 31, 52, 47, 92, 42, 37, 7, 40, 48, 40, 11, 96, 51, 42, 66, 8, 89, 64, 30, 11, 8, 83], 147899),
([51, 94, 58, 76, 21, 10, 75, 4, 55, 37, 71, 97, 27, 93, 82, 94, 38, 69, 36, 58, 93, 18, 54, 59, 12, 12, 54, 83, 73, 83, 33, 12, 78, 38, 45, 57], 176754),
([78, 29, 8, 47, 48, 88, 18, 88, 50, 58, 36, 88, 9, 74, 85, 5, 91, 58, 85, 46, 89, 76, 61, 6, 61, 78, 4, 48, 50, 69, 23, 70, 23, 15, 22, 68], 171970),
([75, 2, 94, 97, 72, 62, 78, 42, 69, 11, 37, 3, 29, 15, 39, 33, 18, 33, 12, 64, 6, 18, 34, 15, 3, 100, 85, 32, 97, 93, 84, 73, 26, 31, 71, 97], 166497),
([59, 26, 48, 86, 58, 70, 61, 100, 63, 74, 26, 38, 24, 45, 52, 32, 91, 89, 19, 59, 87, 5, 15, 68, 72, 67, 2, 65, 46, 10, 33, 79, 11, 16, 73, 53], 173887),
([6, 66, 59, 76, 86, 20, 59, 34, 28, 48, 86, 5, 87, 13, 95, 87, 65, 35, 58, 10, 98, 100, 4, 78, 66, 57, 34, 86, 62, 36, 92, 28, 3, 24, 49, 28], 173189),
([25, 48, 44, 16, 99, 100, 69, 26, 65, 32, 18, 65, 58, 72, 61, 56, 10, 78, 93, 98, 39, 43, 87, 12, 42, 100, 100, 47, 31, 51, 75, 10, 63, 48, 22, 87], 174138),
([61, 13, 100, 59, 31, 9, 28, 7, 27, 63, 11, 57, 95, 79, 21, 30, 60, 81, 43, 32, 30, 34, 80, 53, 28, 39, 74, 21, 18, 92, 73, 60, 21, 69, 76, 84], 157623),
([22, 62, 61, 20, 66, 2, 11, 82, 93, 13, 69, 37, 92, 80, 66, 47, 28, 14, 62, 56, 89, 29, 39, 38, 46, 10, 6, 82, 77, 78, 45, 50, 5, 73, 17, 65], 154943),
([5, 84, 83, 77, 76, 60, 20, 48, 53, 14, 98, 50, 37, 15, 31, 69, 55, 37, 64, 35, 26, 20, 18, 67, 50, 57, 60, 71, 4, 35, 23, 52, 11, 15, 83, 51], 156078),
([33, 47, 89, 52, 89, 55, 98, 28, 48, 90, 69, 29, 68, 24, 19, 18, 44, 27, 14, 64, 15, 31, 23, 2, 36, 45, 37, 71, 61, 92, 28, 64, 13, 66, 98, 3], 156158),
([80, 88, 68, 66, 46, 75, 32, 19, 36, 83, 63, 86, 79, 30, 61, 50, 100, 52, 66, 30, 20, 97, 45, 46, 38, 21, 32, 79, 68, 43, 65, 47, 86, 30, 74, 18], 181770),
([11, 58, 95, 67, 96, 74, 60, 11, 21, 14, 100, 60, 70, 92, 92, 39, 43, 52, 5, 22, 90, 70, 12, 52, 36, 21, 45, 59, 74, 46, 11, 60, 8, 52, 14, 77], 173577),
([57, 37, 94, 43, 53, 55, 7, 83, 91, 61, 86, 6, 44, 87, 61, 92, 24, 74, 100, 22, 12, 68, 19, 88, 81, 83, 70, 39, 30, 82, 30, 35, 55, 18, 27, 80], 180922),
([80, 14, 5, 89, 71, 82, 44, 8, 33, 26, 77, 49, 36, 90, 73, 71, 66, 4, 37, 78, 38, 18, 15, 79, 6, 74, 18, 85, 56, 53, 90, 75, 52, 2, 13, 54], 158596),
([96, 29, 37, 70, 92, 80, 24, 36, 32, 29, 78, 45, 58, 55, 16, 92, 71, 82, 86, 23, 4, 58, 16, 18, 38, 53, 82, 76, 83, 73, 87, 36, 61, 85, 61, 69], 181072),
([14, 71, 53, 46, 59, 53, 22, 69, 67, 43, 23, 14, 77, 95, 19, 83, 79, 41, 12, 53, 3, 4, 65, 92, 64, 52, 3, 59, 89, 75, 12, 46, 61, 53, 97, 43], 163777),
([57, 99, 49, 100, 68, 99, 26, 65, 47, 65, 90, 68, 84, 4, 9, 43, 88, 33, 48, 88, 37, 31, 21, 94, 22, 93, 70, 14, 13, 28, 83, 12, 80, 58, 43, 97], 187620),
([33, 94, 56, 48, 13, 44, 81, 42, 19, 96, 67, 79, 12, 67, 34, 72, 45, 48, 24, 71, 65, 13, 32, 97, 48, 42, 65, 95, 54, 9, 35, 57, 18, 20, 83, 76], 169266),
([31, 38, 83, 45, 28, 97, 54, 11, 80, 45, 92, 13, 52, 94, 51, 30, 11, 61, 46, 10, 28, 72, 20, 95, 90, 39, 32, 95, 19, 3, 65, 71, 73, 80, 23, 71], 162587),
([9, 81, 80, 37, 96, 72, 95, 93, 26, 98, 50, 79, 57, 13, 49, 96, 82, 84, 89, 40, 38, 66, 81, 81, 79, 77, 86, 68, 26, 37, 15, 56, 13, 17, 50, 37], 198705),
([82, 57, 33, 32, 79, 25, 54, 27, 50, 14, 72, 31, 28, 66, 4, 6, 48, 34, 63, 51, 12, 21, 73, 66, 53, 38, 54, 59, 76, 63, 61, 30, 84, 80, 98, 46], 160349),
([69, 15, 23, 8, 46, 55, 21, 91, 37, 9, 61, 20, 23, 96, 28, 67, 19, 50, 18, 71, 30, 14, 10, 24, 100, 15, 91, 15, 93, 24, 46, 61, 67, 60, 56, 81], 148095)
]
# 创建 Z3 变量:flag[0] 到 flag[35]
flag = [Int(f'f{i}') for i in range(36)]
# 创建求解器
solver = Solver()
# 添加约束:每个 flag[i] 是可打印 ASCII 字符 (32-126),或者根据题目可能是 33-126 或包含 '{' '}')
for i in range(36):
solver.add(And(flag[i] >= 32, flag[i] <= 126))
# 添加所有线性方程约束
for coeffs, const in equations:
equation = Sum([coeffs[i] * flag[i] for i in range(36)]) == const
solver.add(equation)
# 检查是否有解
if solver.check() == sat:
model = solver.model()
# 提取 flag 的值
flag_bytes = bytes([model.evaluate(flag[i]).as_long() for i in range(36)])
print("Flag found:")
print(flag_bytes.decode('utf-8'))
else:
print("No solution found.")
print(solver.unsat_core())Dancing Functions
IDA分析主函数
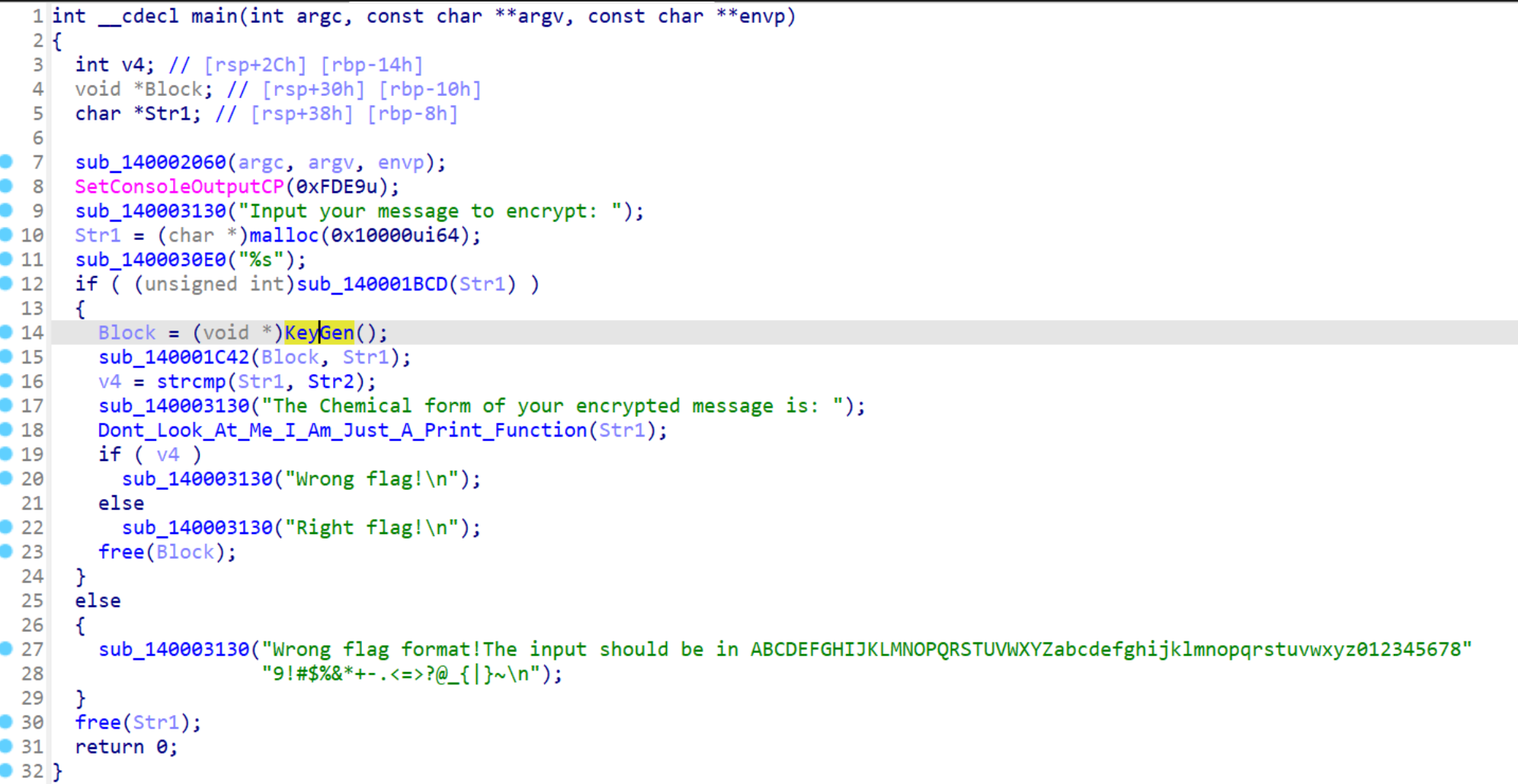
发现KeyGen是生成密钥的函数
查看交叉引用,发现keygen还有别的实现方式
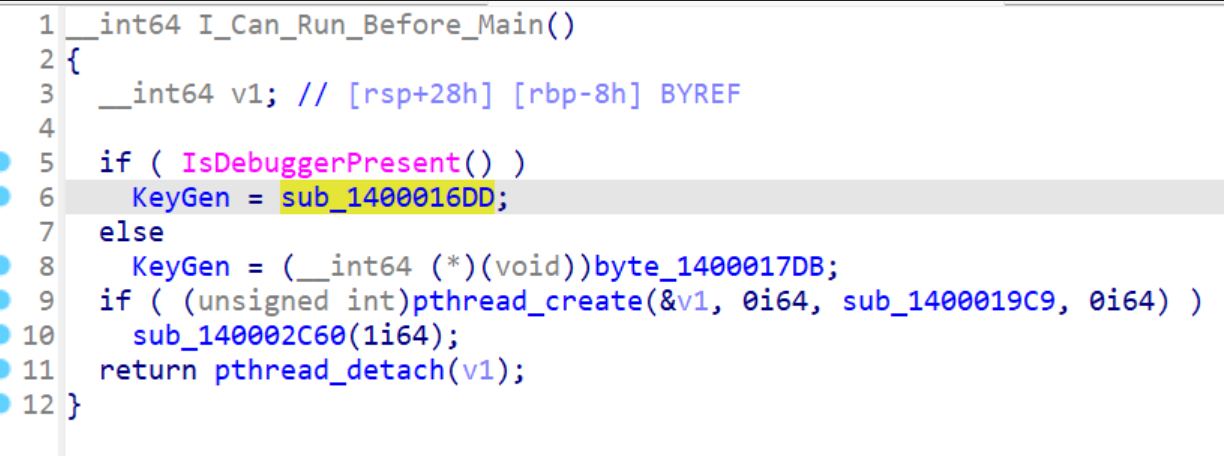
查看byte
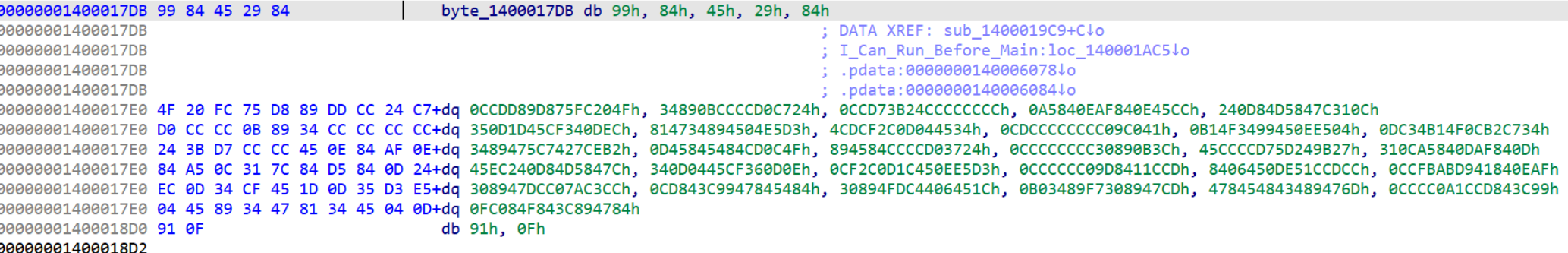
发现很像SMC,看一下交叉引用
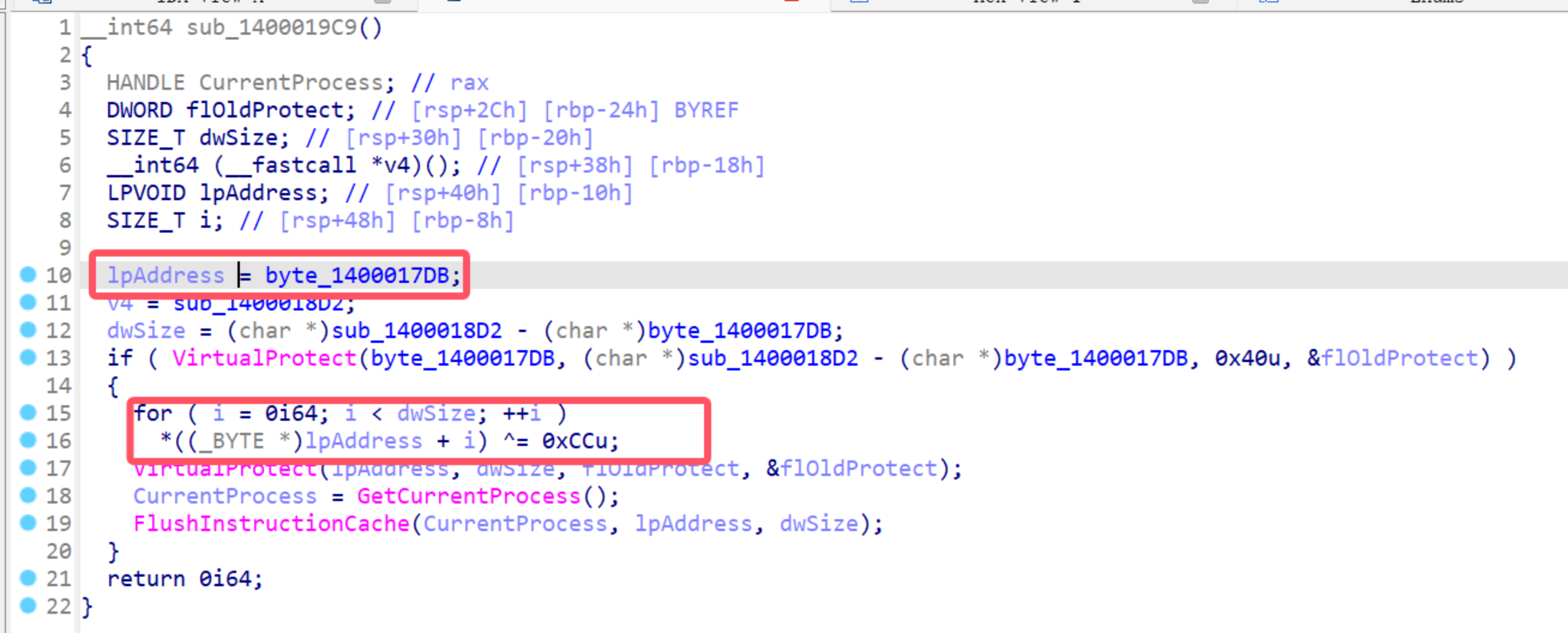
确认是SMC,在解密之后下断点,再去查看keygen函数
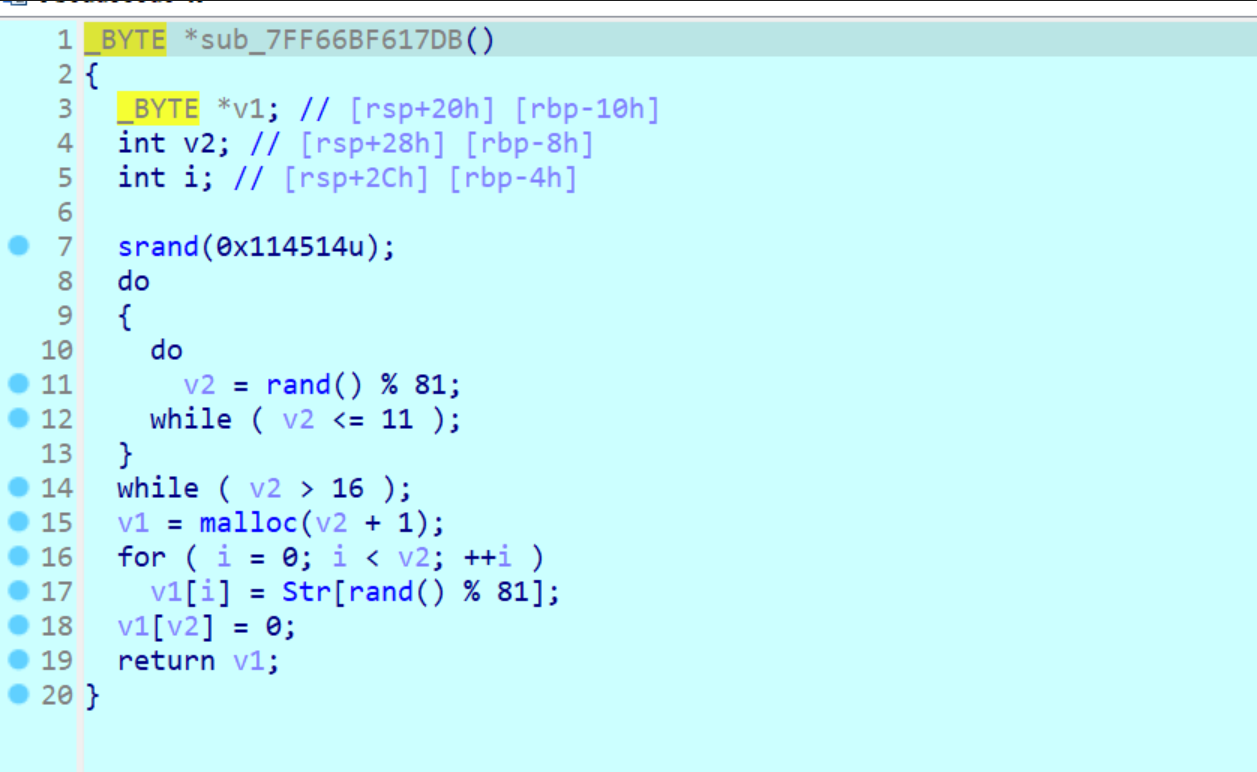
发现是用0x114514作为随机数种子去获取key,懒得写脚本复现,直接动调到key初始化s_box之后
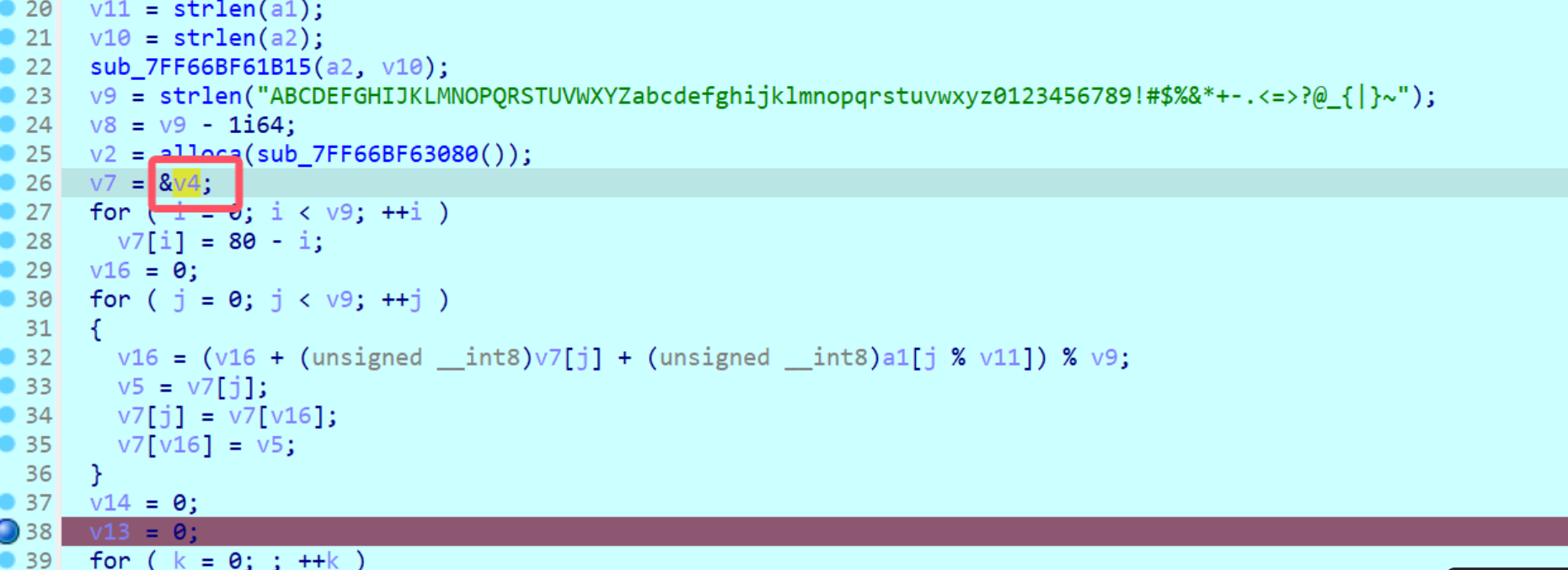
提取s_box
# Str: 字符表,长度 v9
# v7: S盒(长度 v9),初始 v7[i] = 80 - i
# key = a1 (字节数组), keylen = v11
# KSA(打乱 v7)
v16 = 0
for j in range(0, v9):
v16 = (v16 + v7[j] + key[j % keylen]) % v9
swap(v7[j], v7[v16])
# PRGA & 加密
v14 = 0 # 类似 RC4 的 i
v13 = 0 # 类似 RC4 的 j
for k in range(0, text_len):
v14 = (v13 ^ v14) % v9 # <-- 非标准:用 XOR 更新 i(或叫 v14)
v13 = (v13 + v7[v14]) % v9 # <-- v13 类似 RC4 的 j,累加 v7[v14]
swap(v7[v14], v7[v13])
t = v7[(v7[v14] ^ v7[v13]) % v9] # <-- 非标准输出:用 v7[v14]^v7[v13] 的结果作为索引
enc_idx = (plain_idx + t) % v9
enc_char = Str[enc_idx]解密脚本
python
#!/usr/bin/env python3
# decrypt_rc4_variant.py
# Reproduce the decryption for the RC4-like routine from the CTF.
# Modes:
# - USE_PROVIDED_V7 = True: use the post-KSA v7 array you provided.
# - USE_PROVIDED_V7 = False: supply key_str to derive v7 with the same KSA.
Str = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789!#$%&*+-.<=>?@_{|}~"
v9 = len(Str) # 81 for the provided Str
# --- Configuration ---
USE_PROVIDED_V7 = True
# Provided v7 (post-KSA) - replace if you have a different array
provided_v7 = [
0x21, 0x46, 0x4A, 0x31, 0x40, 0x38, 0x4E, 0x3B, 0x08, 0x41,
0x20, 0x28, 0x3E, 0x39, 0x50, 0x09, 0x02, 0x4F, 0x10, 0x13,
0x35, 0x22, 0x43, 0x27, 0x45, 0x4D, 0x17, 0x44, 0x04, 0x29,
0x0F, 0x3F, 0x2D, 0x36, 0x3A, 0x0B, 0x01, 0x49, 0x0D, 0x1A,
0x33, 0x1C, 0x3D, 0x2B, 0x0A, 0x2F, 0x42, 0x19, 0x4C, 0x25,
0x4B, 0x32, 0x07, 0x14, 0x1B, 0x24, 0x18, 0x03, 0x26, 0x0C,
0x3C, 0x2C, 0x06, 0x48, 0x12, 0x1F, 0x15, 0x30, 0x47, 0x1E,
0x2E, 0x37, 0x11, 0x00, 0x05, 0x2A, 0x34, 0x23, 0x1D, 0x0E,
0x16
]
# If you want to derive v7 from a key (KSA), set USE_PROVIDED_V7 = False and fill key_str:
key_str = "replace_with_key_if_you_have_it"
# Ciphertext from the CTF
cipher_text = ".sBtQ=0JEhC#sbw=Q-Y*3h-PGpcvZ9SbU+9F5tH96e>-5hMF"
# ---------- functions ----------
def ksa_from_key(key_str):
"""Recreate v7 from the key using the exact KSA seen in the binary."""
key_bytes = [b for b in key_str.encode()]
if len(key_bytes) == 0:
raise ValueError("key_str empty")
v7 = [80 - i for i in range(v9)]
v16 = 0
for j in range(v9):
v16 = (v16 + v7[j] + key_bytes[j % len(key_bytes)]) % v9
v7[j], v7[v16] = v7[v16], v7[j]
return v7
def decrypt_with_v7(v7, cipher_text):
"""Run the PRGA as in the decompiled function and recover initial a2 indices and mapped chars."""
# operate on a copy because the PRGA mutates v7 via swaps
v7 = list(v7)
indices_cipher = [Str.index(c) for c in cipher_text]
v14 = 0
v13 = 0
plain_indices = []
for k, enc_idx in enumerate(indices_cipher):
v14 = (v13 ^ v14) % v9
v13 = (v13 + v7[v14]) % v9
v7[v14], v7[v13] = v7[v13], v7[v14]
t = v7[(v7[v14] ^ v7[v13]) % v9]
dec_idx = (enc_idx - t) % v9
plain_indices.append(dec_idx)
plain_chars = "".join(Str[i] for i in plain_indices)
return plain_indices, plain_chars
# ---------- main ----------
if __name__ == "__main__":
if USE_PROVIDED_V7:
v7 = provided_v7
if len(v7) != v9:
raise SystemExit(f"Provided v7 length {len(v7)} != expected {v9}")
else:
if key_str == "replace_with_key_if_you_have_it":
raise SystemExit("Set key_str or switch to USE_PROVIDED_V7 = True")
v7 = ksa_from_key(key_str)
plain_indices, plain_chars = decrypt_with_v7(v7, cipher_text)
print("Ciphertext:", cipher_text)
print("Str length (v9):", v9)
print("\nRecovered initial a2 indices (decimal):")
print(", ".join(str(x) for x in plain_indices))
print("\nRecovered initial a2 indices (hex):")
print(", ".join(hex(x) for x in plain_indices))
print("\nRecovered initial a2 mapped to Str (plaintext):")
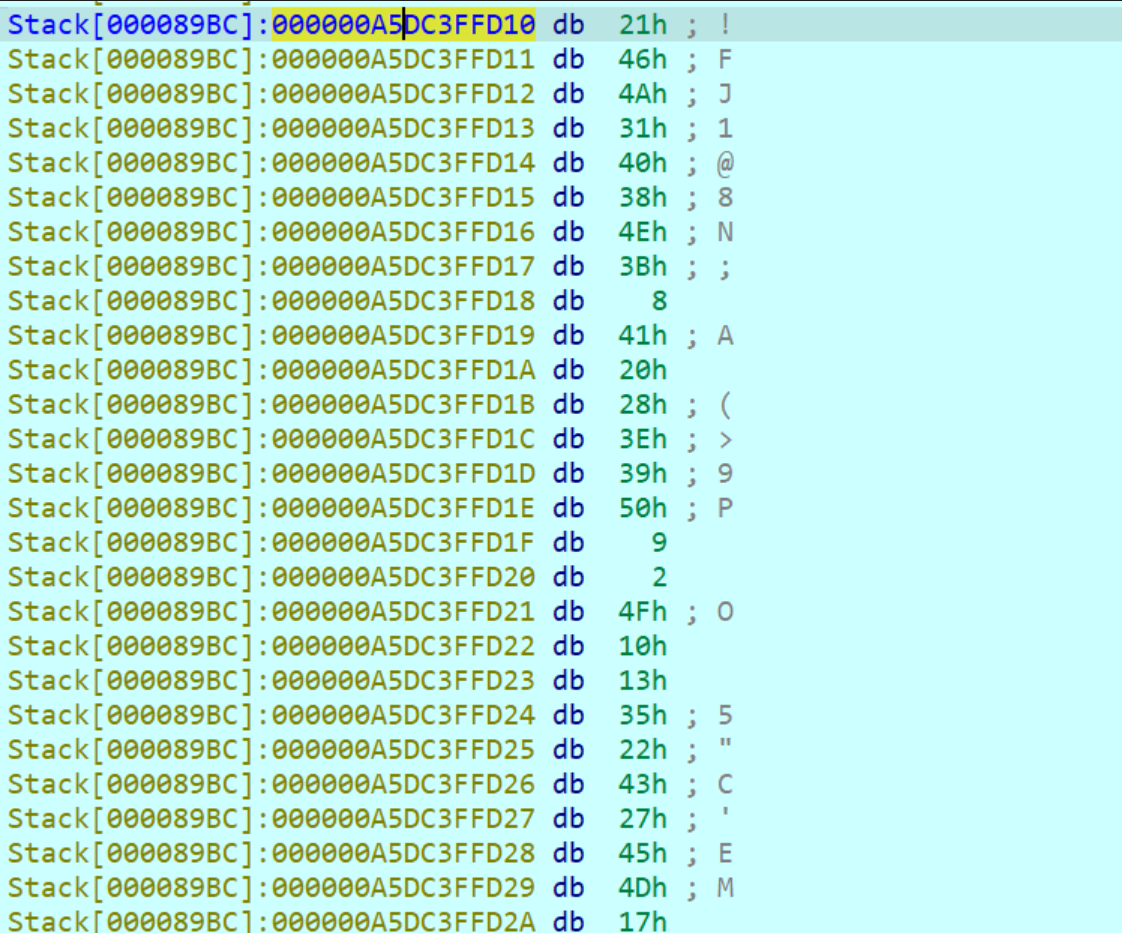
print(plain_chars)谁改了我的密钥啊
JADX查看MainActivity,发现是把输入传入native层的checkflag,同时要求输入为12位
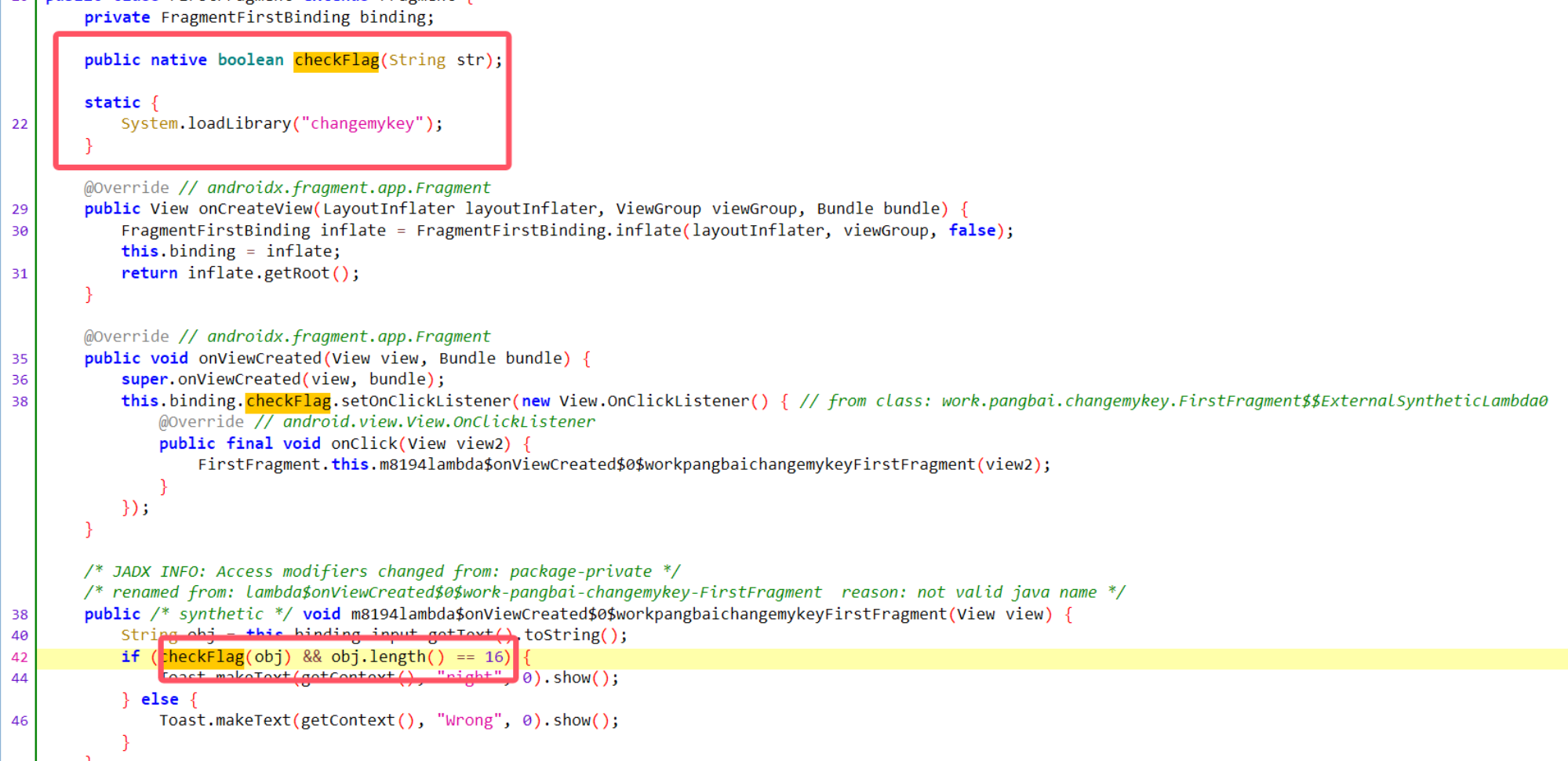
查看so文件中的checkflag
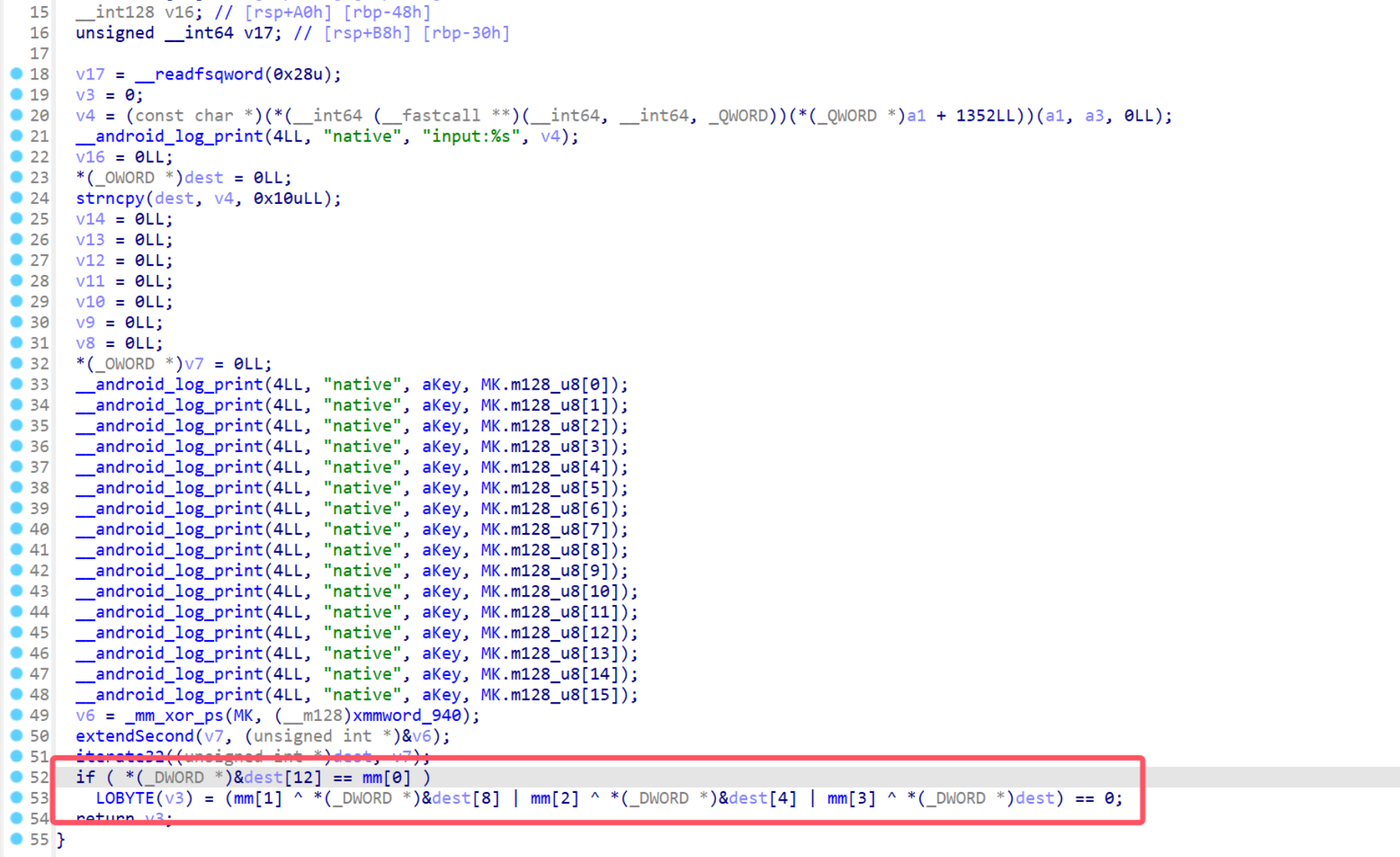
最下面这个是把dest和mm进行比较(逆序)
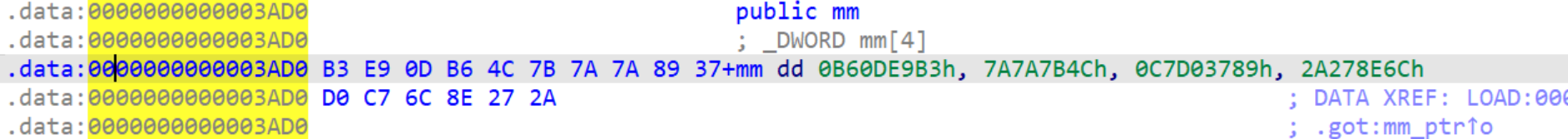
mm数据为:
上面还有个打印
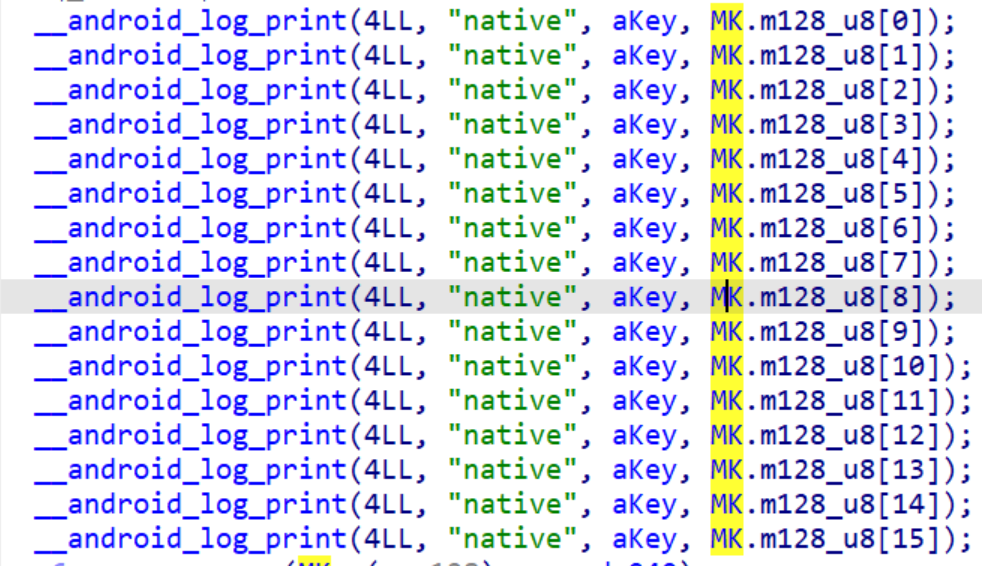
是把MK的内容打印出来
根据左侧函数名,怀疑是SM4加密
用signsrch查一下
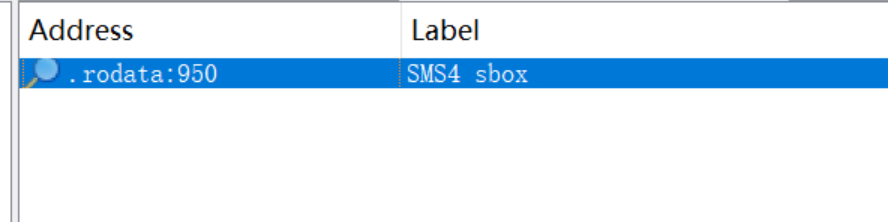
找到了SM4的s_box
在加密函数中也能找到很明显的SM4加密特征
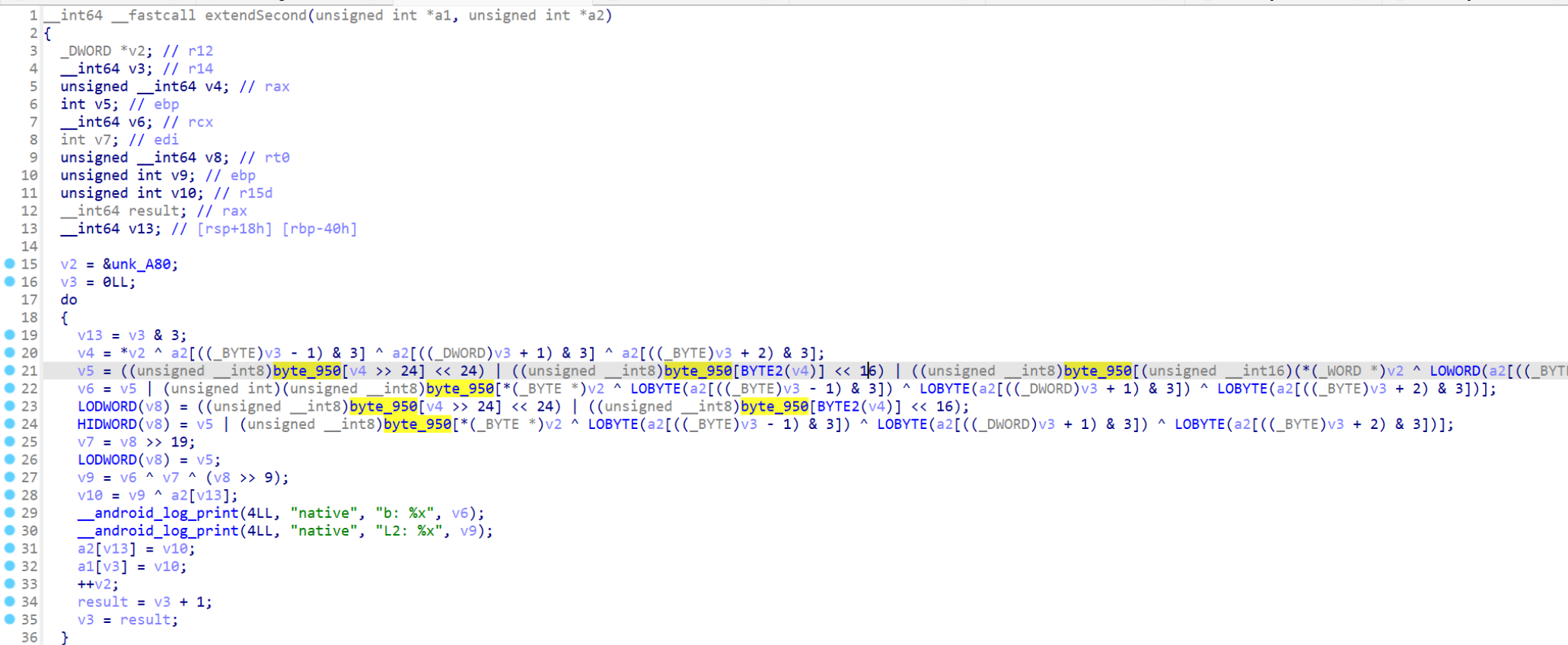
自己撕不明白,丢GPT,GPT最终解决如下:
🧩 一、整体框架
该题的 so 文件或 ELF 程序中存在一段加密逻辑,用于生成 MM = [0xB60DE9B3, 0x7A7A7B4C, 0xC7D03789, 0x2A278E6C]。
最终程序会比较解密结果与这个 MM 是否一致,以验证输入是否合法(通常就是 flag)。
IDA 里核心函数的伪代码逻辑结构大致如下:
PYTHON
void encrypt_func(uint32_t *input, uint32_t *output)
{
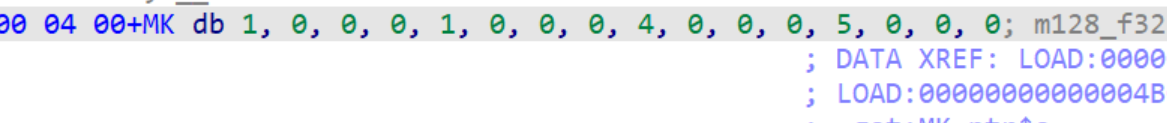
uint32_t MK[4] = {1,0,0,0,1,0,0,0,4,0,0,0,5,0,0,0}; // 实际按 4 个 word 使用
uint32_t K[36];
uint32_t X[36];
int i;
// Step 1: 初始化轮密钥
for (i = 0; i < 4; i++)
K[i] = MK[i] ^ FK[i]; // FK为SM4常量数组
// Step 2: 生成32轮轮密钥
for (i = 0; i < 32; i++)
K[i + 4] = K[i] ^ T_prime(K[i+1] ^ K[i+2] ^ K[i+3] ^ CK[i]);
// Step 3: 输入明文4个word
for (i = 0; i < 4; i++)
X[i] = input[i];
// Step 4: 主加密循环(32轮)
for (i = 0; i < 32; i++)
X[i+4] = X[i] ^ T(X[i+1] ^ X[i+2] ^ X[i+3] ^ K[i+4]);
// Step 5: 输出(逆序)
for (i = 0; i < 4; i++)
output[i] = X[35 - i];
}此函数就是标准的 SM4 加密算法 实现,只是部分细节(轮函数写法、常量表、输入输出顺序)在实现上略有变化。
🔍 二、关键组成部分
1️⃣ 常量表
SBOX[]:标准 SM4 S 盒,用于非线性替换。
CK[32]:常量加法表(每轮不同)。
FK[4]:系统参数(固定值 A3B1BAC6, 56AA3350, 677D9197, B27022DC)。
2️⃣ 非线性与线性变换
两类核心函数:
T_prime(X) = L_prime(τ(X))
T(X) = L(τ(X))
其中:
τ(X) 表示对 X 的每个字节应用 SBOX。
L_prime() 是轮密钥生成阶段的线性变换(含左移 13, 23 位的 XOR)。
L() 是加密阶段的线性变换(含左移 2, 10, 18, 24 位的 XOR)。
这与标准 SM4 完全一致。
🧠 三、数据流与加密方向
1️⃣ 输入:
明文(4×32-bit = 16 字节),即用户输入或 flag 经过拆分后的值。
2️⃣ 轮密钥生成阶段:
使用 MK(主密钥)和 FK 生成 36 个 K 值(前 4 个直接异或,后 32 个通过非线性迭代)。
3️⃣ 加密阶段:
每轮更新 X[i+4] = X[i] ^ T(X[i+1] ^ X[i+2] ^ X[i+3] ^ K[i+4])
共 32 轮。
4️⃣ 输出阶段(逆序存储):
输出为 X[35], X[34], X[33], X[32]
即最终输出顺序是逆序(这是 SM4 的标准输出规则)。
🔄 四、加密流程图简化
输入明文 M0 M1 M2 M3
↓
轮密钥生成 (MK, FK, CK, SBOX)
↓
32 轮加密循环:
Xi+4 = Xi ⊕ T(Xi+1 ⊕ Xi+2 ⊕ Xi+3 ⊕ K[i])
↓
逆序输出:
Cipher = X35 X34 X33 X32
💡 五、题目在校验时的逆向逻辑
程序中保存的 MM 实际上是加密结果。
校验逻辑为:
python
encrypt_func(input, output);
if (memcmp(output, MM, 16) == 0)
success();所以我们要逆向解密,即:
decrypt(MM) -> 明文 = flag
在解密时,轮密钥顺序反向使用即可(SM4 解密即逆序轮密钥)。
🧩 六、逆序比对细节
你注意到的非常关键的点是:
MM 与输出顺序是逆序对应的。
的确,SM4 输出时做了 B = [X35, X34, X33, X32],而代码中比较时是 if (MM == B)。
如果我们从文件直接提取的 MM 是 [0xB60DE9B3, 0x7A7A7B4C, 0xC7D03789, 0x2A278E6C],那么:
实际加密输出顺序可能是逆的(即 MM[::-1])。
这会影响解密阶段输入密文的排列。
🔓 七、总结结论
阶段 操作说明 备注
1 使用主密钥 MK(四个 word)和常量 FK 生成初始密钥数组 SM4 标准
2 经过 32 轮密钥扩展,生成 K[36] 每轮依赖前 3 个
3 明文经过 32 轮迭代变换 包含 SBOX 和线性扩散
4 输出按逆序排列(X35, X34, X33, X32) 与 MM 对应
5 校验时比较 output 与 MM 若一致则 flag 正确
6 因此解密时需:
(a) 将 MM 逆序排列为输入;
(b) 用相同轮密钥反序加密得到明文。
✅ 最终结论
该题实现的是标准 SM4 加密算法,区别在于:
主密钥 MK 由常量 [1,0,0,0,1,0,0,0,4,0,0,0,5,0,0,0] 组成;
输出逆序;
程序校验时直接比较加密结果数组;
MM 实际上是加密结果(需要逆序输入才能正确解密)。
GPT给出的脚本如下
python
from typing import List
import struct
U32 = int
MASK32 = 0xFFFFFFFF
def u32(x: int) -> U32:
return x & MASK32
def pair_shift(hi: int, lo: int, n: int) -> int:
"""实现 (__PAIR64__(hi, lo) >> n) & 0xFFFFFFFF"""
v = ((hi & MASK32) << 32) | (lo & MASK32)
return u32(v >> n)
def be32_to_u32s(b16: bytes) -> List[U32]:
"""将16字节拆成4个小端u32"""
assert len(b16) == 16
return list(struct.unpack('<4I', b16))
# ======== 常量 =========
MK_16 = bytes.fromhex("01000000010000000400000005000000")
XMM_940 = bytes.fromhex("C6BAB1A35033AA5697917D67DC2270B2")
A80_32 = [
0x00070E15, 0x1C232A31, 0x383F464D, 0x545B6269,
0x70777E85, 0x8C939AA1, 0xA8AFB6BD, 0xC4CBD2D9,
0xE0E7EEF5, 0xFC030A11, 0x181F262D, 0x343B4249,
0x50575E65, 0x6C737A81, 0x888F969D, 0xA4ABB2B9,
0xC0C7CED5, 0xDCE3EAF1, 0xF8FF060D, 0x141B2229,
0x30373E45, 0x4C535A61, 0x686F767D, 0x848B9299,
0xA0A7AEB5, 0xBCC3CAD1, 0xD8DFE6ED, 0xF4FB0209,
0x10171E25, 0x2C333A41, 0x484F565D, 0x646B7279,
]
SBOX = [
0xD6, 0x90, 0xE9, 0xFE, 0xCC, 0xE1, 0x3D, 0xB7, 0x16, 0xB6,
0x14, 0xC2, 0x28, 0xFB, 0x2C, 0x05, 0x2B, 0x67, 0x9A, 0x76,
0x2A, 0xBE, 0x04, 0xC3, 0xAA, 0x44, 0x13, 0x26, 0x49, 0x86,
0x06, 0x99, 0x9C, 0x42, 0x50, 0xF4, 0x91, 0xEF, 0x98, 0x7A,
0x33, 0x54, 0x0B, 0x43, 0xED, 0xCF, 0xAC, 0x62, 0xE4, 0xB3,
0x1C, 0xA9, 0xC9, 0x08, 0xE8, 0x95, 0x80, 0xDF, 0x94, 0xFA,
0x75, 0x8F, 0x3F, 0xA6, 0x47, 0x07, 0xA7, 0xFC, 0xF3, 0x73,
0x17, 0xBA, 0x83, 0x59, 0x3C, 0x19, 0xE6, 0x85, 0x4F, 0xA8,
0x68, 0x6B, 0x81, 0xB2, 0x71, 0x64, 0xDA, 0x8B, 0xF8, 0xEB,
0x0F, 0x4B, 0x70, 0x56, 0x9D, 0x35, 0x1E, 0x24, 0x0E, 0x5E,
0x63, 0x58, 0xD1, 0xA2, 0x25, 0x22, 0x7C, 0x3B, 0x01, 0x21,
0x78, 0x87, 0xD4, 0x00, 0x46, 0x57, 0x9F, 0xD3, 0x27, 0x52,
0x4C, 0x36, 0x02, 0xE7, 0xA0, 0xC4, 0xC8, 0x9E, 0xEA, 0xBF,
0x8A, 0xD2, 0x40, 0xC7, 0x38, 0xB5, 0xA3, 0xF7, 0xF2, 0xCE,
0xF9, 0x61, 0x15, 0xA1, 0xE0, 0xAE, 0x5D, 0xA4, 0x9B, 0x34,
0x1A, 0x55, 0xAD, 0x93, 0x32, 0x30, 0xF5, 0x8C, 0xB1, 0xE3,
0x1D, 0xF6, 0xE2, 0x2E, 0x82, 0x66, 0xCA, 0x60, 0xC0, 0x29,
0x23, 0xAB, 0x0D, 0x53, 0x4E, 0x6F, 0xD5, 0xDB, 0x37, 0x45,
0xDE, 0xFD, 0x8E, 0x2F, 0x03, 0xFF, 0x6A, 0x72, 0x6D, 0x6C,
0x5B, 0x51, 0x8D, 0x1B, 0xAF, 0x92, 0xBB, 0xDD, 0xBC, 0x7F,
0x11, 0xD9, 0x5C, 0x41, 0x1F, 0x10, 0x5A, 0xD8, 0x0A, 0xC1,
0x31, 0x88, 0xA5, 0xCD, 0x7B, 0xBD, 0x2D, 0x74, 0xD0, 0x12,
0xB8, 0xE5, 0xB4, 0xB0, 0x89, 0x69, 0x97, 0x4A, 0x0C, 0x96,
0x77, 0x7E, 0x65, 0xB9, 0xF1, 0x09, 0xC5, 0x6E, 0xC6, 0x84,
0x18, 0xF0, 0x7D, 0xEC, 0x3A, 0xDC, 0x4D, 0x20, 0x79, 0xEE,
0x5F, 0x3E, 0xD7, 0xCB, 0x39, 0x48
]
MM = [0xB60DE9B3, 0x7A7A7B4C, 0xC7D03789, 0x2A278E6C]
# ======== Key 扩展 ========
def extend_second(out32: List[int], seed4: List[int]) -> None:
a2 = seed4[:]
for r in range(32):
i = r & 3
im1 = (r - 1) & 3
ip1 = (r + 1) & 3
ip2 = (r + 2) & 3
t = u32(A80_32[r] ^ a2[im1] ^ a2[ip1] ^ a2[ip2])
b0 = SBOX[(t >> 24) & 0xFF]
b1 = SBOX[(t >> 16) & 0xFF]
half = ((A80_32[r] & 0xFFFF) ^ (a2[im1] & 0xFFFF) ^
(a2[ip1] & 0xFFFF) ^ (a2[ip2] & 0xFFFF)) >> 8
b2 = SBOX[half & 0xFF]
loidx = (A80_32[r] & 0xFF) ^ (a2[im1] & 0xFF) ^ (a2[ip1] & 0xFF) ^ (a2[ip2] & 0xFF)
b3 = SBOX[loidx & 0xFF]
v4 = u32((b0 << 24) | (b1 << 16))
v5 = u32(v4 | (b2 << 8))
v6 = u32(v5 | b3)
t1 = pair_shift(v6, v4, 19)
t2 = pair_shift(v6, v5, 9)
v9 = u32(v6 ^ t1 ^ t2)
res = u32(v9 ^ a2[i])
a2[i] = res
out32[r] = res
# ======== 解密主过程 ========
def iterate32_decrypt(block4: List[int], rk32: List[int]) -> None:
for rr in range(31, -1, -1):
r = rr
i = r & 3
im1 = (i - 1) & 3
ip1 = (i + 1) & 3
ip2 = (i + 2) & 3
v3 = u32(rk32[r] ^ block4[im1] ^ block4[ip1] ^ block4[ip2])
b0 = SBOX[(v3 >> 24) & 0xFF]
b1 = SBOX[(v3 >> 16) & 0xFF]
b2 = SBOX[(v3 >> 8) & 0xFF]
v4 = u32(b0 << 24)
v5 = u32(v4 | (b1 << 16))
v6 = u32(v5 | (b2 << 8))
v11 = SBOX[((rk32[r] & 0xFF) ^ (block4[im1] & 0xFF) ^
(block4[ip1] & 0xFF) ^ (block4[ip2] & 0xFF))]
hi = u32(v11 + v6)
F = u32(
pair_shift(hi, v6, 14)
^ pair_shift(hi, v5, 22)
^ pair_shift(hi, v4, 30)
^ pair_shift(v11, v6, 8)
)
block4[i] = u32(block4[i] ^ hi ^ F)
# ======== 顶层入口 ========
def solve_plain_input():
seed = bytes(x ^ y for x, y in zip(MK_16, XMM_940))
seed4 = be32_to_u32s(seed)
rk32 = [0] * 32
extend_second(rk32, seed4)
# 注意逆序:MM[3], MM[2], MM[1], MM[0]
blk = [MM[3], MM[2], MM[1], MM[0]]
iterate32_decrypt(blk, rk32)
plain16 = struct.pack('<4I', *blk)
try:
s = plain16.decode('utf-8')
except UnicodeDecodeError:
s = plain16.hex()
print(f"[+] 解出的16字节:{plain16.hex()}")
print(f"[+] 作为字符串显示:{s}")
return plain16, s
if __name__ == "__main__":
solve_plain_input()flag{1n1t_@rr@y}