Nginx 核心安全配置总结
Nginx 的三大核心安全及监控配置展开,包括访问控制、用户认证和 HTTPS 配置,以下是详细总结:
一、Nginx 访问控制
访问控制通过allow和deny指令实现,仅作用于location段,用于限制主机对特定资源的访问权限
1. 核心指令
- allow :设定允许访问的主机,多个 IP 以空格分隔,默认值为
allow all(允许所有主机访问) - deny:设定禁止访问的主机,多个 IP 以空格分隔
2. 配置规则与示例
-
规则优先级:指令按配置顺序生效,先匹配的规则优先执行
-
示例 1:拒绝特定主机访问状态页面
比如:
allow 192.168.100.20 192.168.100.30;
deny all;
[root@syf nginx-1.24.0]# vim /usr/local/nginx/conf/nginx.conf
location /status {
echo "shenyi";
deny 192.168.100.20;
}
[root@syf nginx-1.24.0]# nginx -s reload
[root@syf2 ~]# ip a
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:86:4f:27 brd ff:ff:ff:ff:ff:ff
inet 192.168.100.20/24 brd 192.168.100.255 scope global noprefixroute ens33
[root@syf2 ~]# curl http://192.168.100.10/status
<html>
<head><title>403 Forbidden</title></head>
<body>
<center><h1>403 Forbidden</h1></center>
<hr><center>nginx/1.24.0</center>
</body>
</html>cmd:
C:\Users\34734>curl http://192.168.100.10/status
shenyi开启stub_status模块:
stub_status模块主要作用于查看nginx的一些状态信息:
[root@syf nginx-1.24.0]# vim /usr/local/nginx/conf/nginx.conf
location /status {
echo "shenyi";
stub_status on;
}
[root@syf nginx-1.24.0]# nginx -s reload
[root@syf2 ~]# curl http://192.168.100.10/status
Active connections: 1
server accepts handled requests
5 5 5
Reading: 0 Writing: 1 Waiting: 0 Active connections:当前nginx正在处理的活动连接数
Server accepts handled requests:nginx总共处理了63个连接,成功创建63次握手,总共处理了62个请求
Reading:nginx读取到客户端的Header信息数
Writing:nginx返回给客户端的Header信息数
Waiting:开启的情况下,这个值等于(),意思就是已经处理完成,正在等候下一次请求指令的驻留连接。所以,在访问效率高、请求很快就被处理完毕的情况下,数比较多是正常的。如果数较多,则说明并发访问量非常大,正在处理过程中
当allow和deny同时存在时:
[root@syf nginx-1.24.0]# vim /usr/local/nginx/conf/nginx.conf
location /status {
stub_status on;
allow 192.168.100.1;
deny all;
}
[root@syf nginx-1.24.0]# nginx -s reload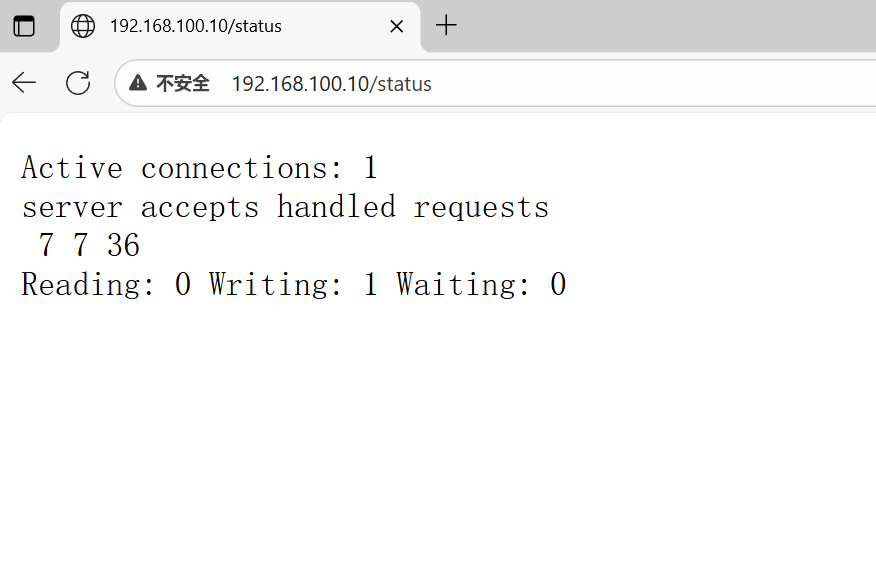
默认是allow all:
只允许指定的IP访问,禁止其他IP访问:
[root@syf nginx-1.24.0]# vim /usr/local/nginx/conf/nginx.conf
location /status {
echo "shenyi";
allow 192.168.100.20;
deny all;
}
[root@syf nginx-1.24.0]# nginx -s reload
[root@syf2 ~]# curl http://192.168.100.10/status
shenyicmd:
C:\Users\34734>curl http://192.168.100.10/status
<html>
<head><title>403 Forbidden</title></head>
<body>
<center><h1>403 Forbidden</h1></center>
<hr><center>nginx/1.24.0</center>
</body>
</html>只禁止指定的IP访问,允许其他IP访问:
[root@syf nginx-1.24.0]# vim /usr/local/nginx/conf/nginx.conf
location /status {
echo "shenyi";
deny 192.168.100.20;
allow all;
}
[root@syf nginx-1.24.0]# nginx -s reload
[root@syf2 ~]# curl http://192.168.100.10/status
<html>
<head><title>403 Forbidden</title></head>
<body>
<center><h1>403 Forbidden</h1></center>
<hr><center>nginx/1.24.0</center>
</body>
</html>cmd:
C:\Users\34734>curl http://192.168.100.10/status
shenyi用户认证:
授权用户:
安装httpd-tools软件包:
[root@syf ~]# yum -y install httpd-tools创建用户密钥文件:(密码:redhat)
[root@syf ~]# cd /usr/local/nginx/conf/
[root@syf conf]# htpasswd -c -m .user_auth_file shenyi
New password:
Re-type new password:
Adding password for user shenyi
[root@syf conf]# cat .user_auth_file
shenyi:$apr1$ceKy5cw3$FZHYQz7DcQVXlYIhULW7Q.配置nginx(注意auth_basic_user_file必须用绝对路径)
[root@syf conf]# vim nginx.conf
location /status {
stub_status on;
auth_basic "Welcome to luoqi";
auth_basic_user_file "/usr/local/nginx/conf/.user_auth_file";
}测试配置文件并重载配置文件:
[root@syf conf]# nginx -t
nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful
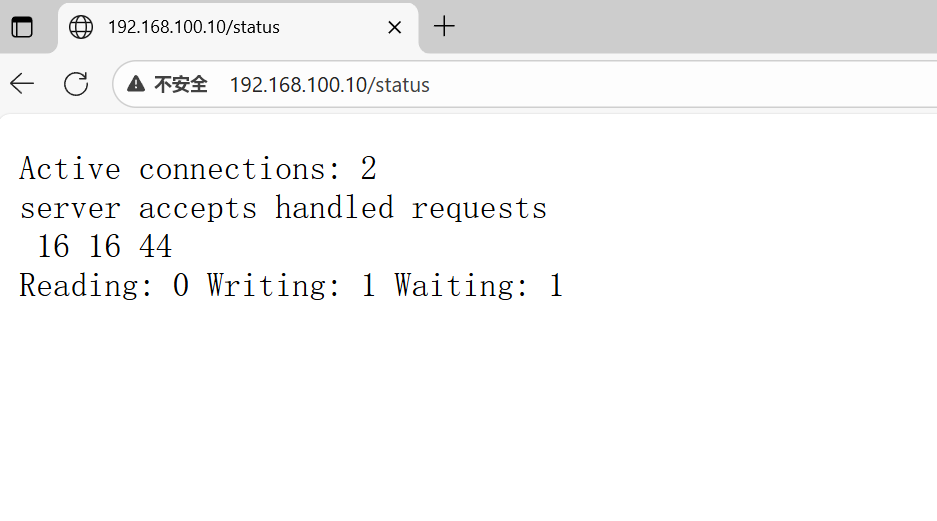
[root@syf conf]# nginx -s reload验证测试:
https配置:
nginx:192.168.100.10
CA:192.168.100.20
在CA服务器中生成一对密钥:
[root@ca ~]# mkdir -p /etc/pki/CA/private
[root@ca ~]# cd /etc/pk
pkcs11/ pki/
[root@ca ~]# cd /etc/pki/CA/
[root@ca CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048)
Generating RSA private key, 2048 bit long modulus
........................................................................................+++
.......................................................+++
e is 65537 (0x10001)
[root@ca CA]# openssl rsa -in private/cakey.pem -pubout
writing RSA key
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEArf5bzKJqEJfkP+gWEyak
Xje/lF6NeKHyjBgX9XuOc53JQBW/fLldCutLZ5q1p0bvLFu1PHqhPyLZwkYbNkQn
/1hX9jlNdVwnQkQgEvQjAlzSxqdLlW2d4DEeH/uSwjkg7mdkXAPOc3sSIQ9xVMQQ
m2erjMmUIEPuF2HGRoylvKU/14u+UnmSut5ujpZrjHPnINsYyHyHc6E46o0o7ojj
v9VdfvHGbKvA1nNKfzMkX9zQNlvDHnt0tAYfe/7udVKOKdN2Xkk5jimriqaIEbo2
8Y2NVEjS2RJNIjHQQmTuVaVzXahvGsAQ3g9J+O/10tC75U8Fa5J5tHfKgQ5n0iZe
vQIDAQAB
-----END PUBLIC KEY-----
[root@ca CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 1024
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:LQ
Organizational Unit Name (eg, section) []:linux
Common Name (eg, your name or your server's hostname) []:shenyi
Email Address []:sy@example.com在nginx中生成证书签署请求,发送给CA:
[root@syf ~]# cd /usr/local/nginx/conf/
[root@syf conf]# (umask 077;openssl genrsa -out httpd.key 2048)
Generating RSA private key, 2048 bit long modulus
.........................................................+++
....+++
e is 65537 (0x10001)
[root@syf conf]# openssl req -new -key httpd.key -days 1024 -out httpd.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:LQ
Organizational Unit Name (eg, section) []:linux
Common Name (eg, your name or your server's hostname) []:shenyi
Email Address []:sy@example.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@syf conf]# ls
fastcgi.conf koi-utf scgi_params
fastcgi.conf.default koi-win scgi_params.default
fastcgi_params mime.types uwsgi_params
fastcgi_params.default mime.types.default uwsgi_params.default
httpd.csr nginx.conf win-utf
httpd.key nginx.conf.default
[root@syf conf]# scp httpd.csr root@192.168.100.20:/root/
The authenticity of host '192.168.100.20 (192.168.100.20)' can't be established.
ECDSA key fingerprint is SHA256:UN0UZbtBfFQeLR3836aFd9k4cm9na95JOPqBnPk05VU.
ECDSA key fingerprint is MD5:20:05:39:25:84:f6:1b:bb:8b:b3:ed:b9:bf:96:99:ba.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.100.20' (ECDSA) to the list of known hosts.
root@192.168.100.20's password:
httpd.csr 100% 1021 871.7KB/s 00:00 在CA主机中查看:
[root@ca ~]# ls
anaconda-ks.cfg httpd.csr mysql.sh Videos
Desktop initial-setup-ks.cfg Pictures
Documents Music Public
Downloads mysql-5.7.37-linux-glibc2.12-x86_64.tar.gz TemplatesCA签署证书并发送给nginx:
[root@ca ~]# mkdir /etc/pki/CA/newcerts/
[root@ca ~]# cd /etc/pki/CA/
[root@ca CA]# ls
cacert.pem certs crl newcerts private
[root@ca ~]# touch /etc/pki/CA/index.txt
[root@ca ~]# echo "01" > /etc/pki/CA/serial
[root@ca ~]# openssl ca -in httpd.csr -out httpd.crt -days 1024
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Sep 27 13:58:09 2025 GMT
Not After : Jul 17 13:58:09 2028 GMT
Subject:
countryName = CN
stateOrProvinceName = HB
organizationName = LQ
organizationalUnitName = linux
commonName = shenyi
emailAddress = sy@example.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
8C:F1:F7:92:BC:C3:FE:49:82:E9:71:76:66:FC:51:AC:8F:B6:7F:45
X509v3 Authority Key Identifier:
keyid:D3:7C:3C:3A:EA:5D:AF:27:B3:57:BB:F7:C9:AC:42:1A:AE:21:B2:1D
Certificate is to be certified until Jul 17 13:58:09 2028 GMT (1024 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@ca ~]# ls
anaconda-ks.cfg httpd.csr Pictures
Desktop initial-setup-ks.cfg Public
Documents Music Templates
Downloads mysql-5.7.37-linux-glibc2.12-x86_64.tar.gz Videos
httpd.crt mysql.sh将CA签署的证书httpd.crt和服务器的证书cacert.pem发送给nginx:
[root@ca ~]# scp httpd.crt root@192.168.100.10:/usr/local/nginx/conf/
The authenticity of host '192.168.100.10 (192.168.100.10)' can't be established.
ECDSA key fingerprint is SHA256:UN0UZbtBfFQeLR3836aFd9k4cm9na95JOPqBnPk05VU.
ECDSA key fingerprint is MD5:20:05:39:25:84:f6:1b:bb:8b:b3:ed:b9:bf:96:99:ba.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.100.10' (ECDSA) to the list of known hosts.
root@192.168.100.10's password:
httpd.crt 100% 4517 3.3MB/s 00:00
[root@ca ~]# scp /etc/pki/CA/cacert.pem root@192.168.100.10:/usr/local/nginx/conf/root@192.168.100.10's password:
Permission denied, please try again.
root@192.168.100.10's password:
cacert.pem 100% 1354 1.3MB/s 00:00 nginx配置https:
先备份:
[root@syf ~]# cd /usr/local/nginx/conf/
[root@syf conf]# ls
cacert.pem httpd.crt mime.types scgi_params.default
fastcgi.conf httpd.csr mime.types.default uwsgi_params
fastcgi.conf.default httpd.key nginx.conf uwsgi_params.default
fastcgi_params koi-utf nginx.conf.default win-utf
fastcgi_params.default koi-win scgi_params
[root@syf conf]# cp nginx.conf nginx.conf.bak
[root@syf conf]# vim nginx.conf
server {
listen 443 ssl;
server_name localhost;
ssl_certificate httpd.crt; //////
ssl_certificate_key httpd.key; //////
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
root html;
index index.html index.htm;
}
}
}
~ 测试配置文件:
[root@syf conf]# nginx -t
nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful编辑测试网页,重载服务,验证:
[root@syf conf]# cd /usr/local/nginx/html/
[root@syf html]# echo "shenyi" > inex.html
[root@syf html]# nginx -s reload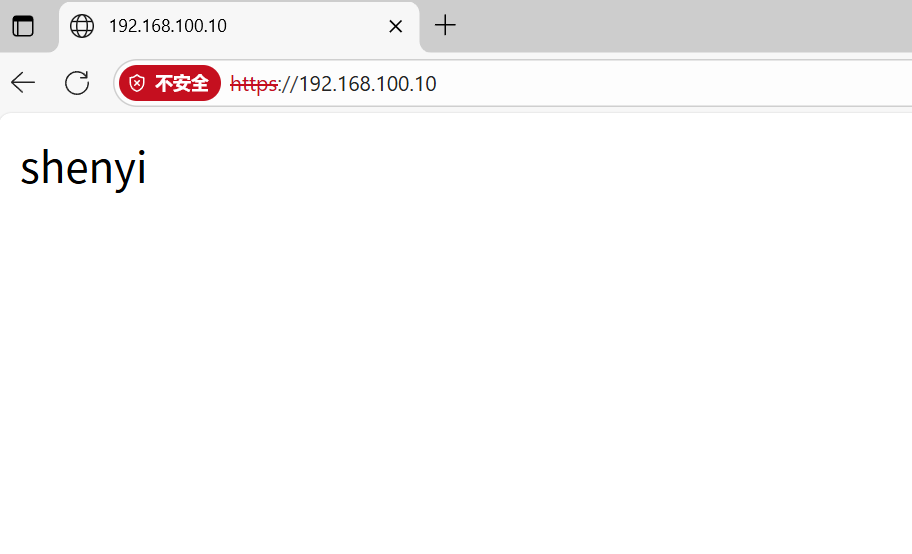
cmd:
C:\Users\34734>curl -k https://192.168.100.10
shenyi