一、修改kubelet的config.yaml文件
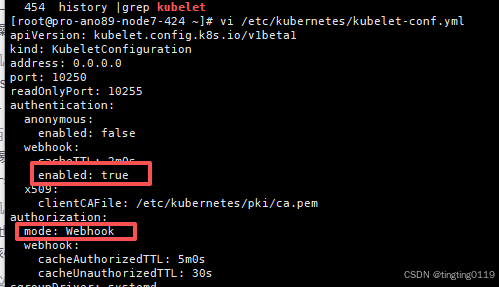
修改成:
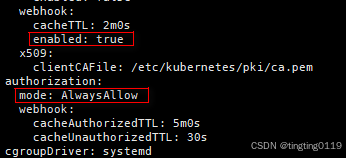
二、找到证书<本文使用的pem证书>
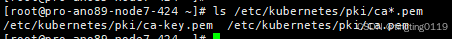
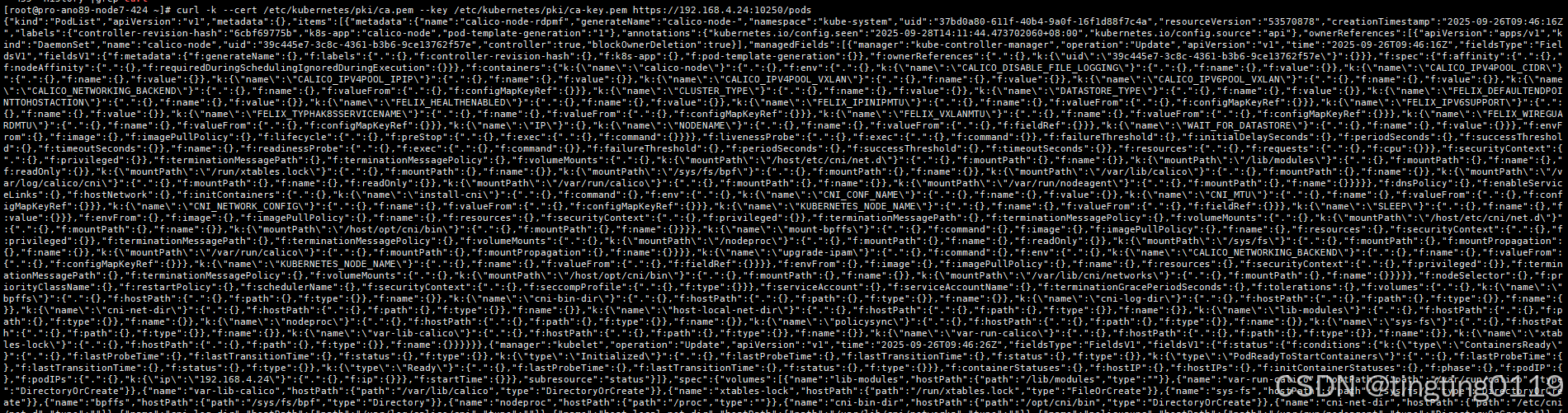
三、测试
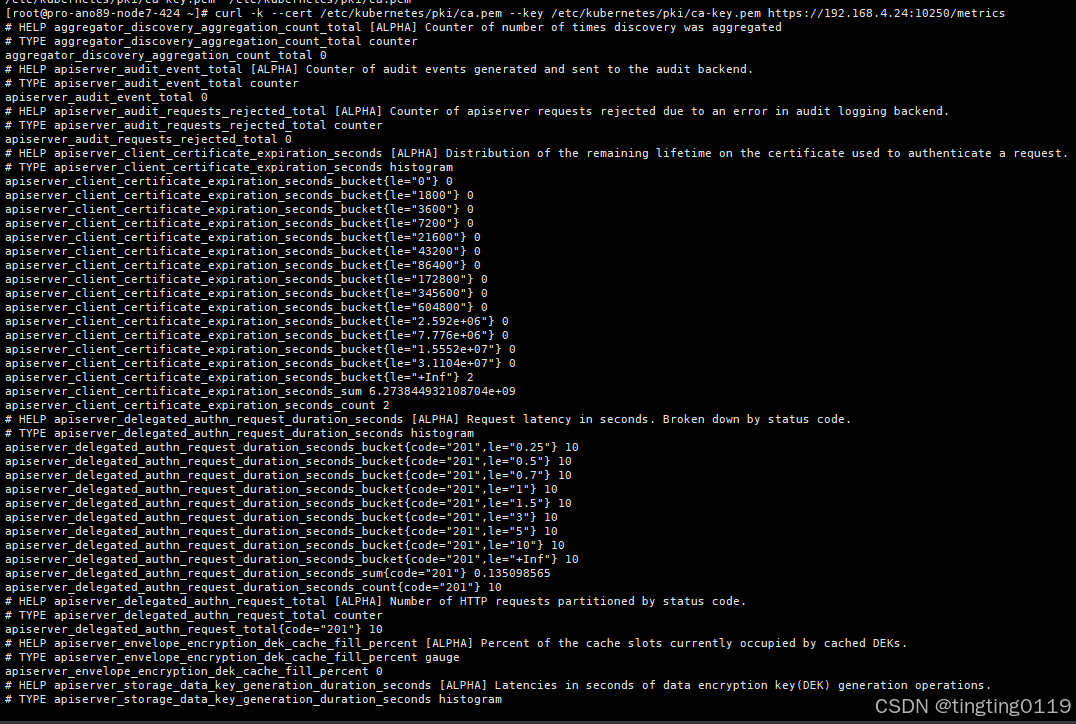
curl -k --cert /etc/kubernetes/pki/ca.pem --key /etc/kubernetes/pki/ca-key.pem https://192.168.4.24:10250/pods
curl -k --cert /etc/kubernetes/pki/ca.pem --key /etc/kubernetes/pki/ca-key.pem https://192.168.4.24:10250/metrics
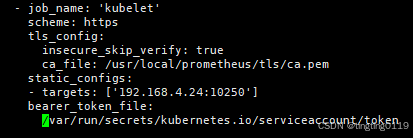
五、prometheus配置
5.1 metrics配置
5.2 pem文件转crt
pem转pem编码CRT,保留abse64格式
openssl x509 -in ca.pem -out ca.crt
pem转DER编码CRT(二进制格式),若目标系统要求crt文件为二进制DER格式:
openssl x509 -outform der -in ca.pem -out ca.crt
5.3 token生成
创建ServiceAccount和RABC
# prometheus-rbac.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: prometheus
namespace: monitoring
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: prometheus
rules:
- apiGroups: [""]
resources:
- nodes
- nodes/proxy
- services
- endpoints
- pods
verbs: ["get", "list", "watch"]
- apiGroups:
- extensions
resources:
- ingresses
verbs: ["get", "list", "watch"]
- nonResourceURLs: ["/metrics"]
verbs: ["get"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: prometheus
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: prometheus
subjects:
- kind: ServiceAccount
name: prometheus
namespace: monitoring
为prometheus创建专用的kubelet访问token:
# prometheus-kubelet-token.yaml
apiVersion: v1
kind: Secret
metadata:
name: prometheus-kubelet-token
namespace: monitoring
annotations:
kubernetes.io/service-account.name: prometheus
type: kubernetes.io/service-account-token
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: prometheus-kubelet-access
rules:
- apiGroups: [""]
resources: ["nodes", "nodes/proxy", "nodes/metrics"]
verbs: ["get", "list", "watch"]
- nonResourceURLs: ["/metrics", "/metrics/cadvisor", "/metrics/probes"]
verbs: ["get"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: prometheus-kubelet-access
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: prometheus-kubelet-access
subjects:
- kind: ServiceAccount
name: prometheus
namespace: monitoring
检查kuelet服务状态;
# systemctl status kubelet
检查防火墙规则:
# iptables -L |grep 10250 #iptables关闭则忽略
验证:
# kubectl describe secrets -n monitoring prometheus-kubelet-token
检查RABC权限;
# kubectl auth can-i get nodes --as=system:serviceaccount:monitoring:prometheus
查看证书有效期:
openssl x509 -in /etc/kubernetes/pki/ca.crt -noout -dates
token转base64:
# kubectl get secret -n monitoring prometheus-kubelet-token -o jsonpath='{.data.token}' | base64 --decode