一、防火墙
1.firewalld和iptables都是防火墙的工具,用于修改防火墙的防御策略
2.netfilter:真正实施策略的防火墙主题(会自动将设置好的策略进行执行)
防火墙不能杀毒或清除木马病毒,也无法阻止来自内部LAN的攻击
3.iptables执行原则:防火墙会从上到下的顺序来读取配置的策略规则
4.iptables流量处理动作
ACCEPT:允许流量通过
REJECT:拒绝流量通过
LOG:记录日志信息
DROP:拒绝流量通过,流量丢失不响应
5.规则(四表五链)
(1)四表
Filter表(过滤):INPUT链,OUTPUT链,FORWARD链
NAT表(转发):PREROUTING链,POSTROUTING链,OUTPUT链
Mangle表:PREROUTING链,POSTROUTING链,INPUT链,OUTPUT链,FORWARD链
Raw表:PREROUTING链,OUTPUT链
(2)五链
INPUT链:数据包流入(数据包从内核空间流入到用户空间)
OUTPUT链:数据包流出(数据包从用户空间流出到内核空间)
FORWARD链:数据包转发(在内核空间,从一个网络接口进入到另一个网络接口去)
PREROUTING链:在对数据包做路由选择之前(互联网进入局域网)
POSTROUTING链:在对数据包做路由选择之后(局域网进入互联网)
6.安装iptables
root@Server \~\]# dnf install iptables-nft-services -y #安装iptables \[root@Server \~\]# systemctl stop firewalld #关闭firewalld \[root@Server \~\]# systemctl restart iptables #重启iptables \[root@Server \~\]# systemctl status iptables.service #查看iptables状态 ● iptables.service - IPv4 firewall with iptables Loaded: loaded (/usr/lib/systemd/system/iptables.service; disabled; preset: disabl\> Active: active (exited) since Wed 2025-04-30 15:15:35 CST; 1min 21s ago Process: 33157 ExecStart=/usr/libexec/iptables/iptables.init start (code=exited, st\> Main PID: 33157 (code=exited, status=0/SUCCESS) CPU: 9ms ······ \[root@Server \~\]# iptables -nL -t filter #查看过滤表详情(可以不写'-t filter',默认查看filter表) Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED #已经链接当前系统的请求 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 #允许任意设备去ping任意设备 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 #允许任意设备通讯到任意设备 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 #允许任意设备到任意设备的ssh服务 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited #以上没有被允许的都会被拒绝,并返回信息 #行为 协议 源地址 目标地址 Chain FORWARD (policy ACCEPT) target prot opt source destination REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) target prot opt source destination 二、修改filter表(编辑iptables策略) 编辑iptables策略时一定要先开启iptables服务 (1)添加nginx的80端口 \[root@Server \~\]# vim /etc/nginx/nginx.conf #编辑nginx的配置文件 38 server { 39 listen 80; 40 listen \[::\]:80; 41 server_name _; 42 root /usr/share/nginx/html; \[root@Server \~\]# systemctl restart nginx.service #重启nginx服务 \[root@Server \~\]# iptables -t filter -A INPUT -p tcp --dport 80 -j ACCEPT #'-t filter'给filter表添加(可以不写,默认filter表),'-A INPUT'给INPUT添加,'-p tcp'指定tcp协议,'--dport 80'指定80端口,'-j ACCEPT'允许(如果写REJECT就是拒绝),按顺序添加命令 \[root@Server \~\]# iptables -nL Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited #在此行前没有的都拒绝 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 #允许任意设备到任意设备的http服务 Chain FORWARD (policy ACCEPT) target prot opt source destination REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) target prot opt source destination 访问http://192.168.153.100,因为防火墙是按顺序执行命令,拒绝命令在允许http服务命令前,所以没有访问成功 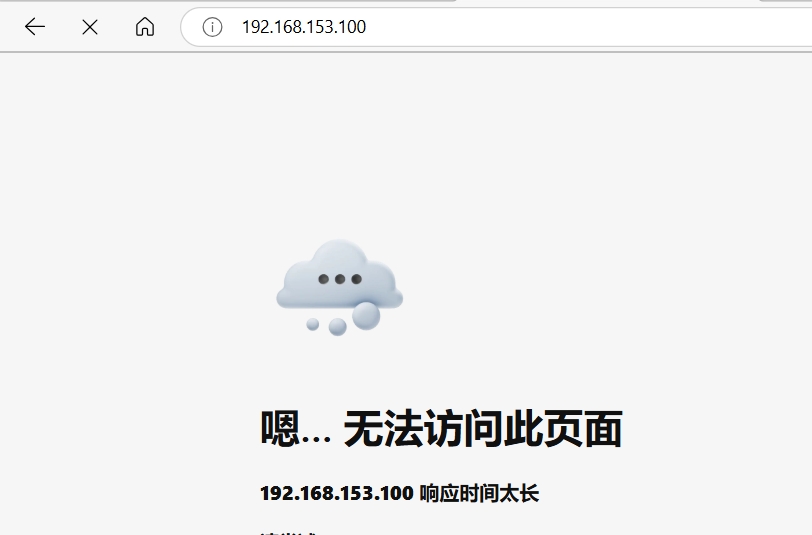 (2)插入命令 \[root@Server \~\]# iptables -D INPUT 6 #'-D'删除;删除INPUT的第6条命令 \[root@Server \~\]# iptables -nL --line-numbers #'--line-numbres'显示行号;显示过滤表详情 Chain INPUT (policy ACCEPT) num target prot opt source destination 1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 2 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 3 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 4 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 5 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT) num target prot opt source destination 1 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) num target prot opt source destination \[root@Server \~\]# iptables -I INPUT 5 -p tcp --dport 80 -j ACCEPT #'-I INPUT 5'插入INPUT链的第5条命令 \[root@Server \~\]# iptables -nL --line-numbers Chain INPUT (policy ACCEPT) num target prot opt source destination 1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 2 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 3 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 4 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 5 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 6 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT) num target prot opt source destination 1 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) num target prot opt source destination 再次访问http://192.168.153.100 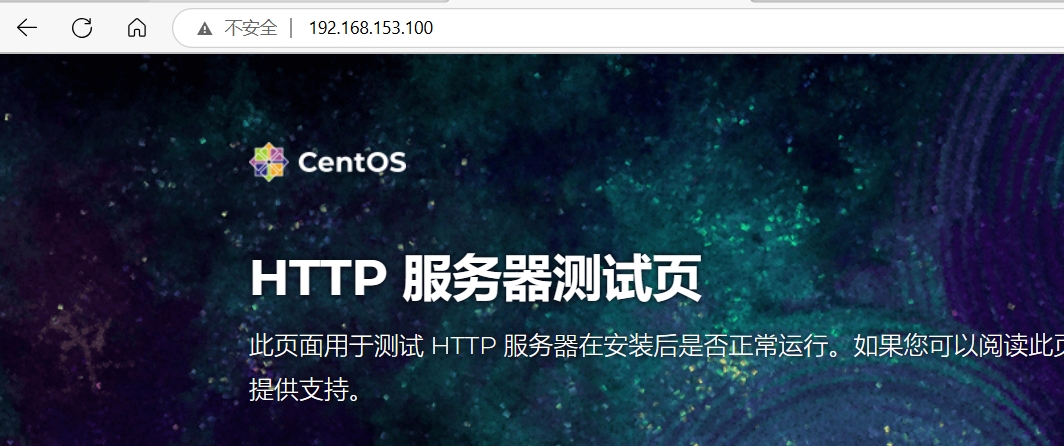 (3)修改命令 \[root@Server \~\]# iptables -R INPUT 6 -p all -j ACCEPT #'-R'修改;修改INPUT链第6行允许所有设备通讯 \[root@Server \~\]# iptables -nL --line-numbers Chain INPUT (policy ACCEPT) num target prot opt source destination 1 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 2 ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 3 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 4 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 5 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:80 6 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 Chain FORWARD (policy ACCEPT) num target prot opt source destination 1 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) num target prot opt source destination \[root@Server \~\]# iptables -nvL #'-v'显示详细信息 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 1816 **105K** ACCEPT all -- \* \* 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- \* \* 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo \* 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- \* \* 0.0.0.0/0 0.0.0.0/0 \[root@Server \~\]# iptables -nvxL #'-x'取消单位 Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 1846 **107117** ACCEPT all -- \* \* 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- \* \* 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo \* 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- \* \* 0.0.0.0/0 0.0.0.0/0 \[root@Server \~\]# iptables -F #'-F'清空所有规则 \[root@Server \~\]# iptables -nL Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination (4)允许192.168.153.200使用ssh远程登录 \[root@Server \~\]# iptables -A INPUT -s 192.168.153.200 -p tcp --dport 22 -j ACCEPT #'-s'指定192.168.153.200地址;允许客户端使用ssh远程登录 \[root@Server \~\]# iptables -A INPUT -p all -j REJECT #拒绝所有人登录 \[root@Client \~\]# ssh root@192.168.153.100 #从客户端登录服务器 \[root@Server \~\]# (5)iptables的配置文件 \[root@Server \~\]# vim /etc/sysconfig/iptables #编辑iptables的规则配置文件。只有在配置文件中加入的规则才是永久的 ······ 4 \*filter 5 :INPUT ACCEPT \[0:0
6 :FORWARD ACCEPT [0:0]
7 :OUTPUT ACCEPT [0:0]
8 -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
9 -A INPUT -p icmp -j ACCEPT
10 -A INPUT -i lo -j ACCEPT
11 -A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
12 -A INPUT -j REJECT --reject-with icmp-host-prohibited
13 -A FORWARD -j REJECT --reject-with icmp-host-prohibited
14 COMMIT
root@Server \~\]# iptables -I INPUT 5 -p tcp --dport 80 -j ACCEPT \[root@Server \~\]# service iptables save #将当前iptables的配置信息保存到配置文件中 \[root@Server \~\]# vim /etc/sysconfig/iptables 17 \*filter 18 :INPUT ACCEPT \[0:0
19 :FORWARD ACCEPT [0:0]
20 :OUTPUT ACCEPT [202:27474]
21 -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
22 -A INPUT -p icmp -j ACCEPT
23 -A INPUT -i lo -j ACCEPT
24 -A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
25 -A INPUT -p tcp -m tcp --dport 80 -j ACCEPT #插入http服务的命令以保存到配置文件中
26 -A INPUT -j REJECT --reject-with icmp-host-prohibited
27 -A FORWARD -j REJECT --reject-with icmp-host-prohibited
28 COMMIT
三、NAT(地址转换)
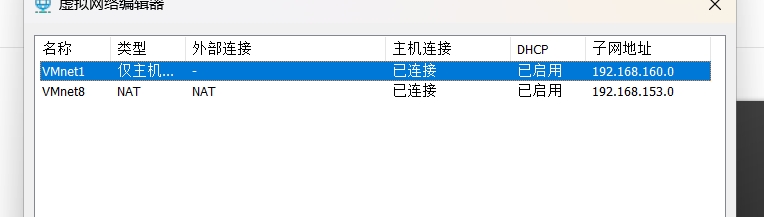
1.创建3个主机------client_nat(NAT模式),client_hostonly(仅主机模式),server_nat_hostonly(拥有NAT和仅主机网卡的服务器)
然后可自由修改网段
(1)配置client_nat
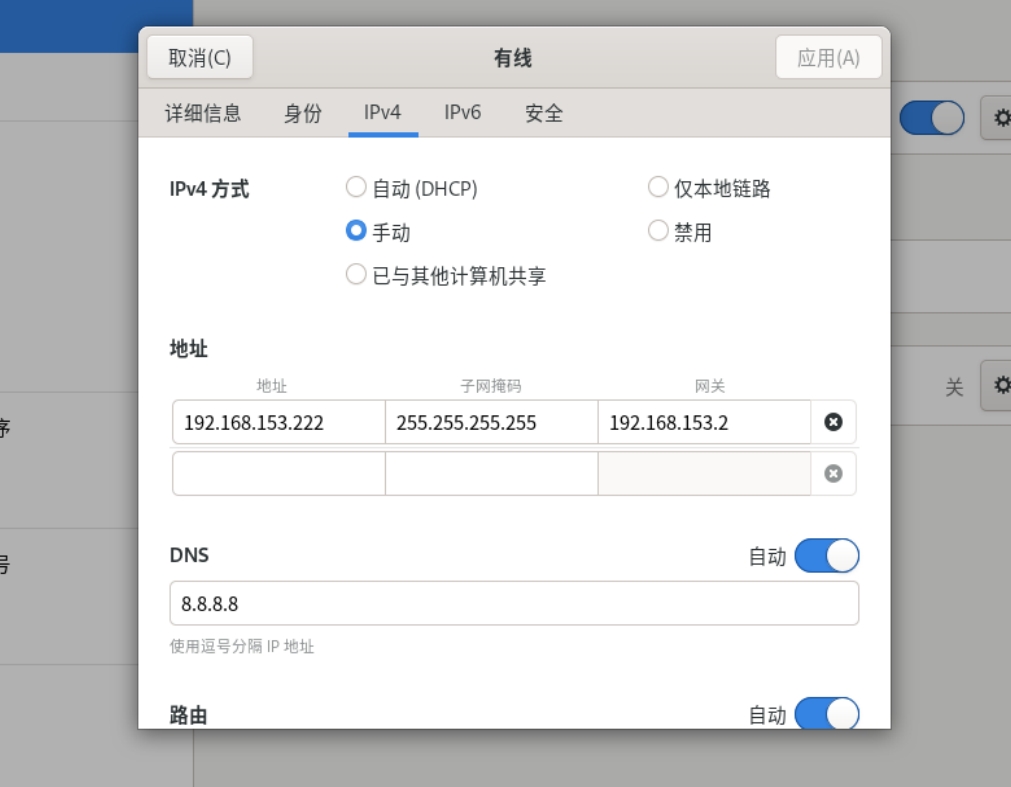
root@clientnat \~\]# nmcli connection modify ens160 ipv4.addresses 192.168.153.222 ipv4.gateway 192.168.153.2 ipv4.dns 8.8.8.8 #设置client_nat的ip、掩码、网关和dns
\[root@clientnat \~\]# nmcli connection reload
\[root@clientnat \~\]# nmcli connection up ens160
(2)配置client_hostonly
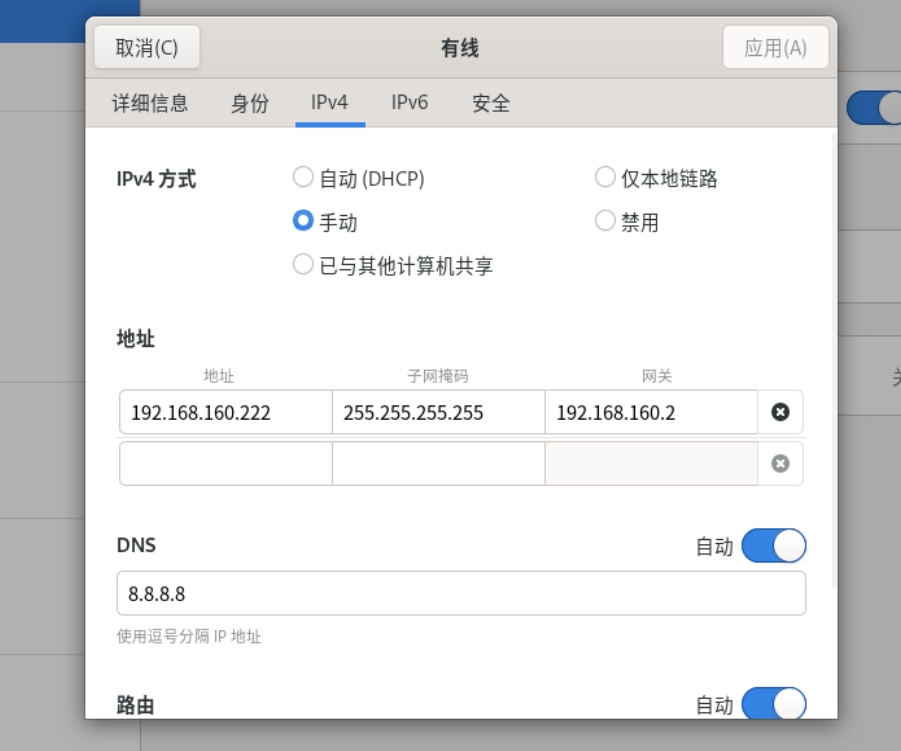
\[root@clienthostonly \~\]# nmcli connection modify ens160 ipv4.addresses 192.168.160.222 ipv4.gateway 192.168.160.2 ipv4.dns 8.8.8.8 #设置client_hostonly的ip、掩码、网关和dns
\[root@clienthostonly \~\]# nmcli connection reload
\[root@clienthostonly \~\]# nmcli connection up ens160
(3)配置server_nat_hostonly
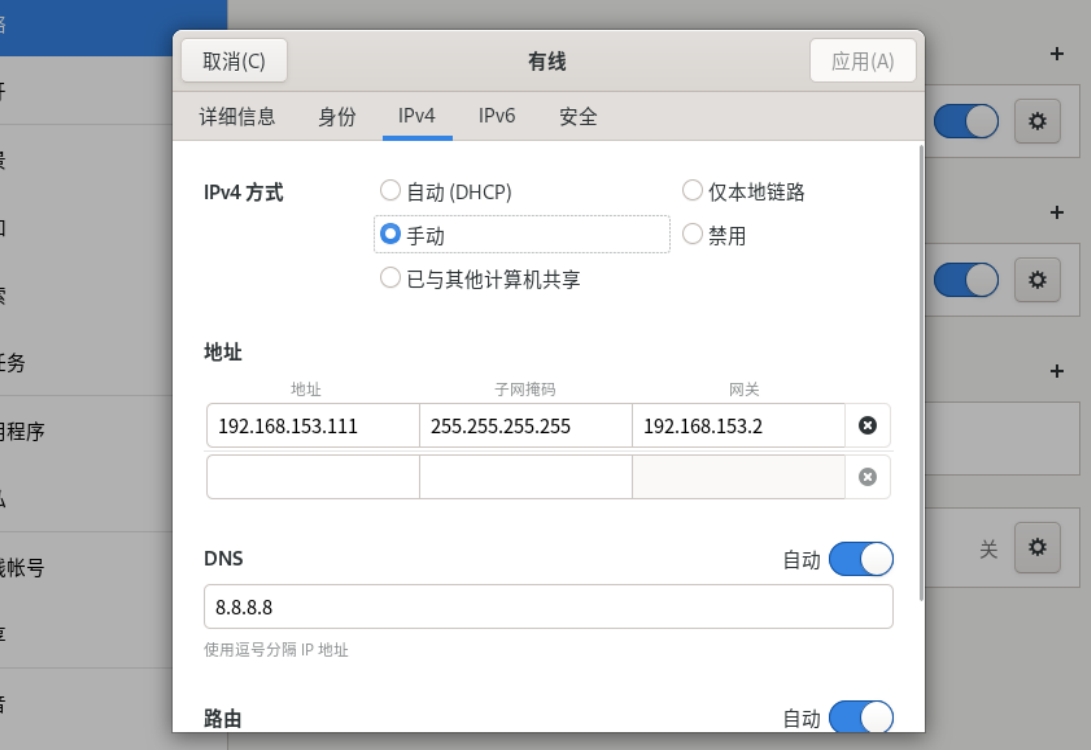
######
\[root@servernathost \~\]# nmcli device disconnect ens224 #断开网卡
成功断开设备 "ens224"。
\[root@servernathost \~\]# nmcli device #查看网卡
DEVICE TYPE STATE CONNECTION
ens160 ethernet 已连接 ens160
lo loopback 连接(外部) lo
ens224 ethernet 已断开 --
\[root@servernathost \~\]# nmcli device up ens224 #激活网卡
设备 "ens224" 成功以 "886fb7e3-07a0-47d2-885d-90298c6aadd2" 激活。
\[root@servernathost \~\]# nmcli device
DEVICE TYPE STATE CONNECTION
ens160 ethernet 已连接 ens160
ens224 ethernet 已连接 有线连接 1
lo loopback 连接(外部) lo
2.在服务器上开启路由转发
\[root@servernathost \~\]# sysctl -a \|grep ip_forward #查看ip_forward(转发)的内核功能
net.ipv4.ip_forward = 0 #转发功能关闭
net.ipv4.ip_forward_update_priority = 1
net.ipv4.ip_forward_use_pmtu = 0
\[root@servernathost \~\]# vim /etc/sysctl.conf #编辑sysctl的配置文件
11 net.ipv4.ip_forward=1 #开启转发
\[root@servernathost \~\]# sysctl -p #重新加载
net.ipv4.ip_forward = 1
\[root@servernathost \~\]# sysctl -a \|grep ip_forward
net.ipv4.ip_forward = 1 #转发已开启
net.ipv4.ip_forward_update_priority = 1
net.ipv4.ip_forward_use_pmtu = 0
3.源地址修改
源地址修改的是主动连接的地址,在路由后(POSTROUTING链)修改
(1)
\[root@servernathost \~\]# dnf install iptables-nft-services -y #安装iptables服务
\[root@servernathost \~\]# systemctl stop firewalld.service #关闭firewalld
\[root@servernathost \~\]# systemctl mask firewalld.service #掩住
Created symlink /etc/systemd/system/firewalld.service → /dev/null.
\[root@servernathost \~\]# systemctl restart iptables.service #重启iptables
\[root@servernathost \~\]# iptables -nL #查看filter表
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0
ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited #禁止路由转发
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
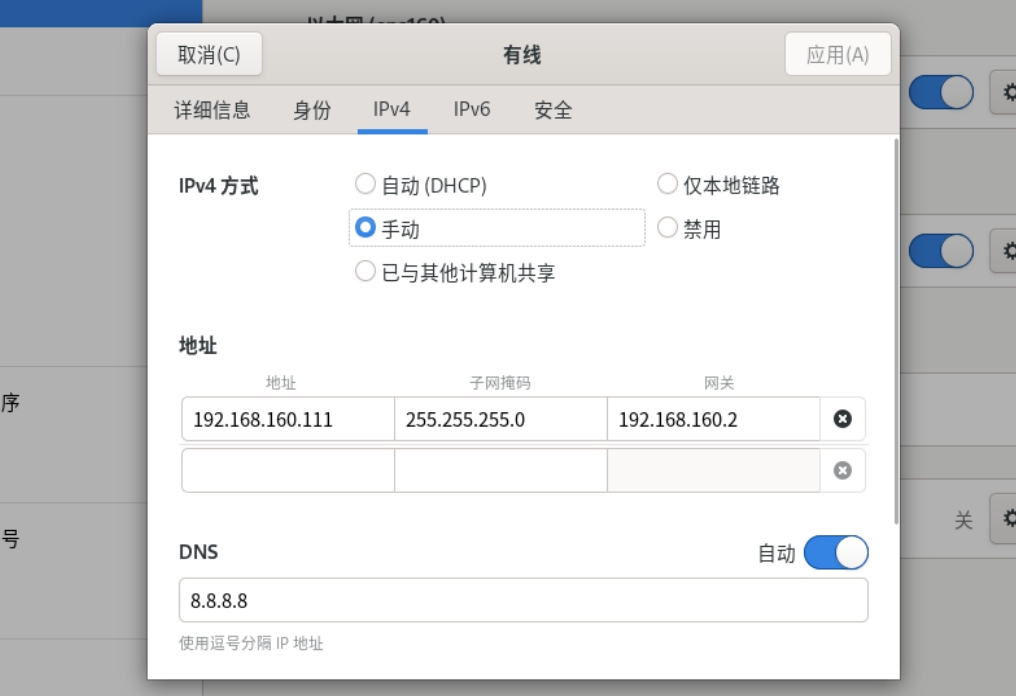
\[root@servernathost \~\]# iptables -t nat -A POSTROUTING -o ens160 -j SNAT --to-source 192.168.160.111
#'-A POSTROUTING'向POSTROUTING链添加,'-o ens160'POSTROUTING链指定连接的网卡,'SNAT'源地址,'--to-source'修改POSTROUTING链的源地址
\[root@servernathost \~\]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 0.0.0.0/0 0.0.0.0/0 to:192.168.160.111
\[root@servernathost \~\]# iptables (-t filter) -F #清空filter表,即删除filter表中禁止路由转发
(2)
\[root@clientnat \~\]# nmcli connection modify ens160 ipv4.gateway 192.168.153.111 #修改网关为服务器地址,使能连接到路由器(服务器)
\[root@clientnat \~\]# nmcli connection reload
\[root@clientnat \~\]# nmcli connection up ens160
连接已成功激活(D-Bus 活动路径:/org/freedesktop/NetworkManager/ActiveConnection/4)
\[root@clientnat \~\]# route -n #查看网关配置信息
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.153.111 0.0.0.0 UG 100 0 0 ens160
192.168.153.0 0.0.0.0 255.255.255.0 U 100 0 0 ens160
# client_nat ping client_host
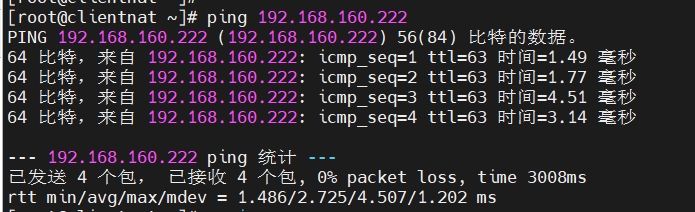
\[root@clientnat \~\]# ssh root@192.168.160.222 #连接client_host
\[root@clienthost \~\]# w -i #查看连接线路
17:10:22 up 1:51, 2 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
root pts/0 192.168.160.1 15:55 9:56 0.14s 0.14s -bash
root pts/1 192.168.160.111 17:10 4.00s 0.01s 0.01s w -i #client_nat以192.168.160.111身份连接进来
4.修改目标地址
目标地址修改的是被连接的地址,在路由前(PREROUTING链)修改
\[root@servernathost \~\]# iptables -t nat -A PREROUTING -i ens224 -j DNAT --to-dest 192.168.153.222
#'-A PREROUTING'向PREROUTING链添加,'-i ens224'指定PREROUTING链的网卡,'DNAT'目标地址,'--to-dest'修改PREROUTING链的目标地址
\[root@servernathost \~\]# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
DNAT all -- 0.0.0.0/0 0.0.0.0/0 to:192.168.153.222
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
SNAT all -- 0.0.0.0/0 0.0.0.0/0 to:192.168.160.111
#client_host ping client_nat
\[root@clienthost \~\]# ssh root@192.168.160.111 #连接服务器
\[root@clientnat \~\]# ip a #因为目标地址改为192.168.153.222,所以连到client_nat
1: lo: \