1.实验要求
配置一个基于nginx的web服务器要求如下:
1、该web服务器使用主机名www.example.com来访问
2、该主机名由本地提供的DNS服务进行解析,并且提供反向解析
3、该DNS服务器应该还有一个从服务器
4、该web服务器访问应使用端口9093
5、该web服务器的内容页面应存放在/u01/www/目录下
6、该web服务器需要从Windows主机直接访问 9093 防火墙放行
7、系统上的防火墙和SELinux服务必须正常运行
8、该web服务器在系统重启后,依然可以正常访问。
2.实验过程
yum install -y bind bind-utils nginx policycoreutils-python-utils
systemctl start firewalld && systemctl enable firewalld
setenforce 1
getenforce
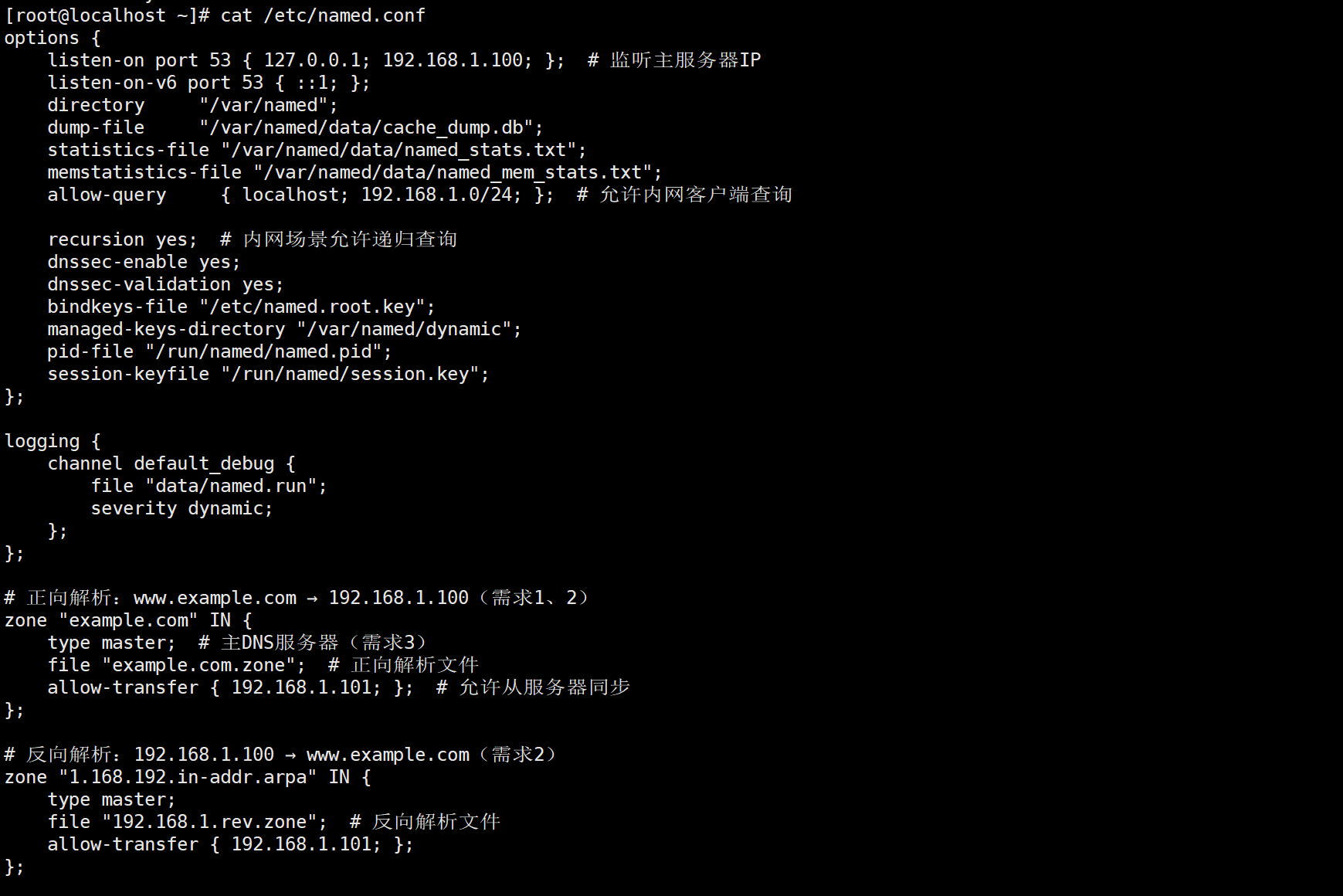
vim /etc/named.conf
options {
listen-on port 53 { 127.0.0.1; 192.168.1.100; }; # 监听主服务器IP
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { localhost; 192.168.1.0/24; }; # 允许内网客户端查询
recursion yes; # 内网场景允许递归查询
dnssec-enable yes;
dnssec-validation yes;
bindkeys-file "/etc/named.root.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
正向解析:www.example.com → 192.168.1.100(需求1、2)
zone "example.com" IN {
type master; # 主DNS服务器(需求3)
file "example.com.zone"; # 正向解析文件
allow-transfer { 192.168.1.101; }; # 允许从服务器同步
};
反向解析:192.168.1.100 → www.example.com(需求2)
zone "1.168.192.in-addr.arpa" IN {
type master;
file "192.168.1.rev.zone"; # 反向解析文件
allow-transfer { 192.168.1.101; };
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
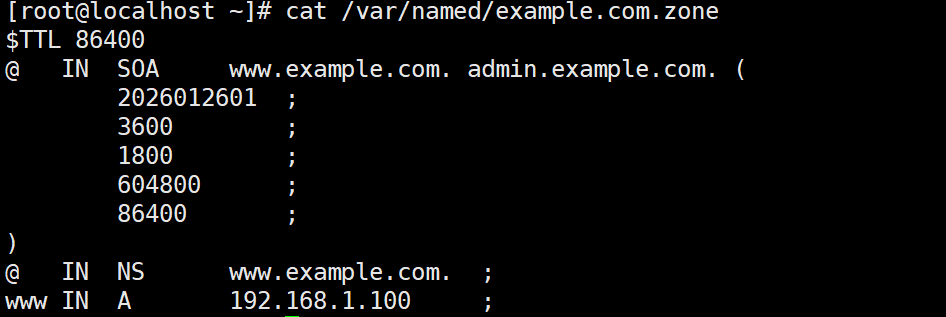
vim /var/named/example.com.zone
$TTL 86400
@ IN SOA www.example.com. admin.example.com. (
2026012601 ; 序列号
3600 ; 刷新时间(从服务器同步间隔)
1800 ; 重试时间
604800 ; 过期时间
86400 ; 最小TTL
)
@ IN NS www.example.com. # 主DNS服务器
www IN A 192.168.1.100 ; 正向解析核心记录
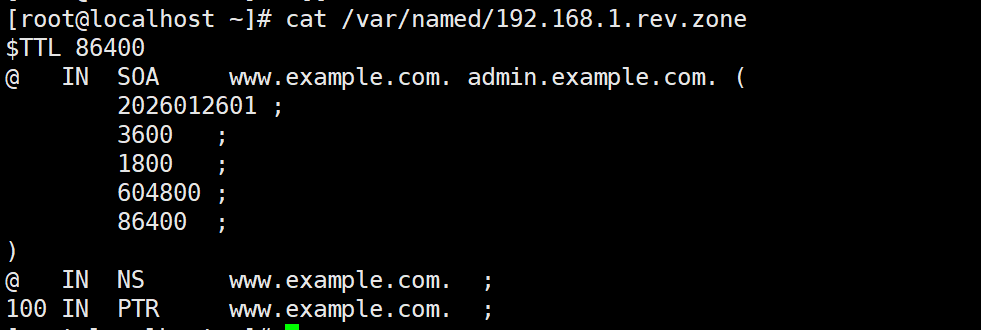
vim /var/named/192.168.1.rev.zone
$TTL 86400
@ IN SOA www.example.com. admin.example.com. (
2026012601
3600
1800
604800
86400
)
@ IN NS www.example.com.
100 IN PTR www.example.com. # 反向解析核心记录(192.168.1.100 → www.example.com)
chown named:named /var/named/example.com.zone chown named:named /var/named/192.168.1.rev.zone chmod 640 /var/named/example.com.zone chmod 640 /var/named/192.168.1.rev.zone
systemctl enable --now named
systemctl status named
vim /etc/named.conf
options {
listen-on port 53 { 127.0.0.1; 192.168.1.101; };
allow-query { localhost; 192.168.1.0/24; };
recursion yes;
};
正向解析(从服务器)
zone "example.com" IN {
type slave; # 从DNS服务器(需求3)
file "slaves/example.com.zone"; # 同步文件存放路径
masters { 192.168.1.100; }; # 指向主DNS服务器
};
反向解析(从服务器)
zone "1.168.192.in-addr.arpa" IN {
type slave;
file "slaves/192.168.1.rev.zone";
masters { 192.168.1.100; };
};
systemctl enable --now named
ls /var/named/slaves/
mkdir -p /u01/www
echo "<h1>Welcome to www.example.com:9093</h1>" > /u01/www/index.html
chown -R nginx:nginx /u01/www
chmod -R 755 /u01/www
vim /etc/nginx/conf.d/example.conf
server {
listen 9093; # 监听9093端口(需求4)
server_name www.example.com; # 绑定主机名(需求1)
root /u01/www; # 网页根目录(需求5)
index index.html index.htm;
日志配置(可选)
access_log /var/log/nginx/example_access.log;
error_log /var/log/nginx/example_error.log;
location / {
try_files uri uri/ =404;
}
}
nginx -t
systemctl enable --now nginx
semanage fcontext -a -t httpd_sys_content_t "/u01/www(/.*)?"
restorecon -Rv /u01/www
semanage port -a -t http_port_t -p tcp 9093
getenforce
firewall-cmd --permanent --add-port=53/tcp
firewall-cmd --permanent --add-port=53/udp
firewall-cmd --permanent --add-port=9093/tcp
firewall-cmd --permanent --add-port=22/tcp
firewall-cmd --reload
firewall-cmd --list-ports
systemctl enable named nginx firewalld
systemctl list-unit-files | grep -E "named|nginx|firewalld"
nslookup www.example.com
nslookup 192.168.1.100
reboot
systemctl status named nginx firewalld
3.实验结果