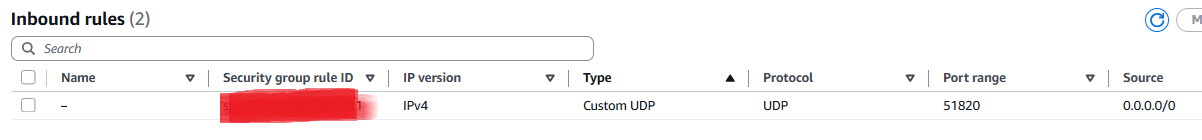
示例脚本在AWS EC2实例(Debian和Ubuntu)上均测试验证通过。
示例脚本中使用的公私密钥仅为展示之用,实际部署时,务必更换密钥且妥善保存。
该脚本用于在 Debian 系统(专为 EC2 优化)上自动化部署 WireGuard VPN 服务器,并预置两个客户端配置。主要功能包括:
· 自动检测:获取主网络接口(如 eth0/ens5)和 EC2 实例的公网 IP。
· 环境准备:更新软件包,安装 WireGuard,开启 IPv4 转发。
· 密钥配置:使用脚本内固定的私钥/公钥对,为服务器和两名客户端预定义身份。
· 服务器设置:生成 /etc/wireguard/wg0.conf,配置 VPN 网段 10.0.0.1/24,监听 51820 端口,通过 iptables 实现 NAT 流量转发,并添加两个客户端对等体。
· 客户端配置:在 /root/ 下创建 client1.conf 和 client2.conf,包含客户端私钥、分配地址、DNS 以及指向服务器公网 IP 的端点。
· 服务管理:启用并启动 wg-quick@wg0 服务。
· 输出反馈:显示服务器公网 IP 及客户端配置文件路径。
整个流程无需人工干预,脚本执行完毕后 VPN 服务器即可运行,客户端配置文件可直接分发使用。
bash
#!/bin/bash
set -e
echo "=== Installing WireGuard Server on Debian ==="
###############################################
# Detect primary network interface (ens5/eth0)
###############################################
IFACE=$(ip route get 8.8.8.8 | awk -- '{print $5; exit}')
echo "Detected network interface: $IFACE"
###############################################
# Install WireGuard
###############################################
apt update
apt install -y wireguard
###############################################
# Enable ipv4 forwarding
sudo sysctl -w net.ipv4.ip_forward=1
###############################################
# Use fixed keys provided by the user
###############################################
SERVER_PRIV="cDx7g/B77vfohzopZrDCD2QOsowxrbTzi5k3D9dGXV8="
SERVER_PUB="+tD1Ok8m85VI30jaHvAP9TsmWoKFBzNWNca9t5v9SiQ="
CLIENT1_PRIV="GAnR28Ee3O/hwoERyCSXWjBKzq8z7DIW3ZCr1Opau0Q="
CLIENT1_PUB="tdpAAwY2NuY4lm6OG3Wq6Qr6zSJm6Bwd4HFcUhS0GXc="
CLIENT2_PRIV="WPGxp47vsDJR+kNOEWUWQaefnr2K6Y2LtMCl5kfMEmc="
CLIENT2_PUB="n1tqZOpwvHWmQK5/kFpj+mG7VeqNXoy0mLby48saszI="
###############################################
# Determine EC2 public IP
###############################################
PUBLIC_IP=$(curl -s http://169.254.169.254/latest/meta-data/public-ipv4)
echo "EC2 Public IP = $PUBLIC_IP"
###############################################
# Write the WireGuard server config
###############################################
mkdir -p /etc/wireguard
chmod 700 /etc/wireguard
cat > /etc/wireguard/wg0.conf <<EOF
[Interface]
Address = 10.0.0.1/24
ListenPort = 51820
PrivateKey = $SERVER_PRIV
# NAT all client traffic
PostUp = iptables -t nat -A POSTROUTING -o $IFACE -j MASQUERADE
PostUp = iptables -A FORWARD -i wg0 -j ACCEPT
PostUp = iptables -A FORWARD -o wg0 -j ACCEPT
PostDown = iptables -t nat -D POSTROUTING -o $IFACE -j MASQUERADE
PostDown = iptables -D FORWARD -i wg0 -j ACCEPT
PostDown = iptables -D FORWARD -o wg0 -j ACCEPT
# Client 1
[Peer]
PublicKey = $CLIENT1_PUB
AllowedIPs = 10.0.0.2/32
# Client 2
[Peer]
PublicKey = $CLIENT2_PUB
AllowedIPs = 10.0.0.3/32
EOF
chmod 600 /etc/wireguard/wg0.conf
###############################################
# Create Client 1 config
###############################################
cat > /root/client1.conf <<EOF
[Interface]
PrivateKey = $CLIENT1_PRIV
Address = 10.0.0.2/24
DNS = 1.1.1.1
[Peer]
PublicKey = $SERVER_PUB
Endpoint = $PUBLIC_IP:51820
AllowedIPs = 0.0.0.0/0
PersistentKeepalive = 25
EOF
###############################################
# Create Client 2 config
###############################################
cat > /root/client2.conf <<EOF
[Interface]
PrivateKey = $CLIENT2_PRIV
Address = 10.0.0.3/24
DNS = 1.1.1.1
[Peer]
PublicKey = $SERVER_PUB
Endpoint = $PUBLIC_IP:51820
AllowedIPs = 0.0.0.0/0
PersistentKeepalive = 25
EOF
chmod 600 /root/client*.conf
###############################################
# Start and enable WireGuard
###############################################
systemctl enable wg-quick@wg0
systemctl restart wg-quick@wg0
echo ""
echo "=================================================="
echo " WireGuard Installed & Running"
echo " Server public IP: $PUBLIC_IP"
echo " Client configs created:"
echo " /root/client1.conf"
echo " /root/client2.conf"
echo "=================================================="
echo ""Remark: AWS EC2的安全组中需要增加一条入栈规则配合使用:允许UDP 51820 from 0.0.0.0