登录功能实现深度解析:从会话管理到安全校验全流程指南
大家好,我是凯哥Java
本文标签:登录验证流程、过滤器与拦截器、安全防护措施
简介
本文深入探讨了从登录功能实现到会话管理和安全校验的全流程,包括参数校验、身份验证、令牌生成和存储等关键步骤。通过比较主流的会话技术(如Cookie、Session和JWT),并详细讲解过滤器与拦截器的区别及其应用场景,提供了构建高性能、高安全性Web应用的具体指导。
一、登录功能核心实现流程
1.1 登录流程图解
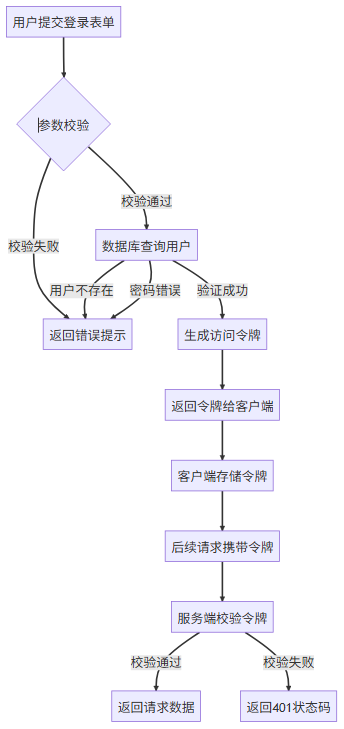
1.2 关键实现步骤
-
参数校验层:验证用户名/邮箱格式、密码强度
-
身份验证层:数据库查询+密码哈希比对
-
令牌生成层:使用JWT生成访问令牌和刷新令牌
-
令牌存储层:Redis缓存令牌实现快速验证
-
安全传输层:HTTPS+HttpOnly Cookie保障传输安全
二、会话跟踪技术深度对比
2.1 主流会话技术对比
| 技术类型 | Cookie | Session | JWT |
|---|---|---|---|
| 存储位置 | 客户端 | 服务端 | 客户端 |
| 安全性 | 较低 | 较高 | 较高(需HTTPS) |
| 扩展性 | 单域限制 | 集群部署需同步 | 天然支持分布式 |
| 性能开销 | 低 | 中等 | 低 |
| 典型应用场景 | 简单状态保持 | 传统Web应用 | 前后端分离/移动端 |
2.2 JWT令牌技术详解
令牌结构示例:
// Header
{
"alg": "HS256",
"typ": "JWT"
}
// Payload
{
"sub": "1234567890",
"name": "John Doe",
"iat": 1516239022,
"exp": 1516242622
}
// Signature
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
secret)
Java生成JWT示例:
public String generateToken(UserDetails userDetails) {
Map<String, Object> claims = new HashMap<>();
claims.put("roles", userDetails.getAuthorities());
return Jwts.builder()
.setClaims(claims)
.setSubject(userDetails.getUsername())
.setIssuedAt(new Date(System.currentTimeMillis()))
.setExpiration(new Date(System.currentTimeMillis() + 3600 * 1000))
.signWith(SignatureAlgorithm.HS256, secretKey)
.compact();
}
三、安全校验实现方案
3.1 过滤器(Filter)实现方案
public class JwtFilter implements Filter {
@Override
public void doFilter(ServletRequest req, ServletResponse res, FilterChain chain)
throws IOException, ServletException {
HttpServletRequest request = (HttpServletRequest) req;
String token = resolveToken(request);
if (StringUtils.hasText(token) && validateToken(token)) {
Authentication auth = parseAuthentication(token);
SecurityContextHolder.getContext().setAuthentication(auth);
}
chain.doFilter(req, res);
}
private String resolveToken(HttpServletRequest request) {
String bearerToken = request.getHeader("Authorization");
if (StringUtils.hasText(bearerToken) && bearerToken.startsWith("Bearer ")) {
return bearerToken.substring(7);
}
return null;
}
}
3.2 拦截器(Interceptor)实现方案
public class JwtInterceptor implements HandlerInterceptor {
@Override
public boolean preHandle(HttpServletRequest request, HttpServletResponse response, Object handler)
throws Exception {
if (!(handler instanceof HandlerMethod)) return true;
String token = getTokenFromRequest(request);
if (token == null || !jwtProvider.validateToken(token)) {
throw new AuthenticationException("Invalid JWT token");
}
setAuthentication(token);
return true;
}
private String getTokenFromRequest(HttpServletRequest request) {
// 从Cookie或Header获取令牌
}
}
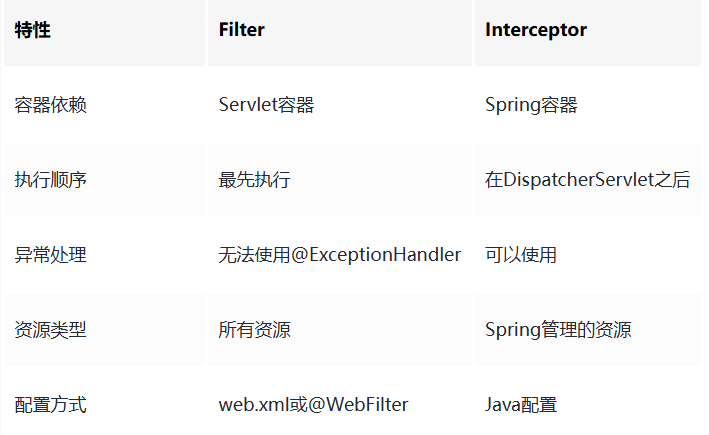
3.3 过滤器与拦截器对比
四、全局异常处理机制
4.1 异常处理类实现
@RestControllerAdvice
public class GlobalExceptionHandler {
@ExceptionHandler(AuthenticationException.class)
public ResponseEntity<ErrorResponse> handleAuthException(AuthenticationException ex) {
ErrorResponse error = new ErrorResponse();
error.setStatus(HttpStatus.UNAUTHORIZED.value());
error.setMessage("Authentication failed: " + ex.getMessage());
error.setTimestamp(LocalDateTime.now());
return new ResponseEntity<>(error, HttpStatus.UNAUTHORIZED);
}
@ExceptionHandler(AccessDeniedException.class)
public ResponseEntity<ErrorResponse> handleAccessDenied(AccessDeniedException ex) {
ErrorResponse error = new ErrorResponse();
error.setStatus(HttpStatus.FORBIDDEN.value());
error.setMessage("Access denied: " + ex.getMessage());
return new ResponseEntity<>(error, HttpStatus.FORBIDDEN);
}
}
4.2 错误响应DTO
@Data
@AllArgsConstructor
@NoArgsConstructor
public class ErrorResponse {
private int status;
private String message;
private LocalDateTime timestamp;
private String path;
public ErrorResponse(HttpStatus status, String message, String path) {
this.status = status.value();
this.message = message;
this.timestamp = LocalDateTime.now();
this.path = path;
}
}
五、安全增强最佳实践
5.1 令牌刷新机制
public TokenPair refreshToken(String refreshToken) {
if (!validateRefreshToken(refreshToken)) {
throw new InvalidTokenException("Invalid refresh token");
}
String username = parseUsername(refreshToken);
UserDetails user = userService.loadUserByUsername(username);
String newAccessToken = generateAccessToken(user);
String newRefreshToken = generateRefreshToken(user);
redisTemplate.delete(refreshToken);
redisTemplate.opsForValue().set(newRefreshToken, username, REFRESH_EXPIRE);
return new TokenPair(newAccessToken, newRefreshToken);
}
5.2 并发登录控制
public void handleConcurrentLogin(String username, String newSessionId) {
String oldSession = redisTemplate.opsForValue().get("user:" + username);
if (StringUtils.hasText(oldSession)) {
// 1. 发送下线通知
messagingTemplate.convertAndSendToUser(oldSession, "/queue/logout", "forced_logout");
// 2. 清除旧令牌
redisTemplate.delete(oldSession);
}
// 3. 存储新会话
redisTemplate.opsForValue().set("user:" + username, newSessionId);
}
六、性能优化方案
6.1 令牌验证优化
public boolean validateToken(String token) {
// 先检查黑名单
if (redisTemplate.hasKey("token:blacklist:" + token)) {
return false;
}
// 快速过期检查
if (Jwts.parser().parseClaimsJws(token).getBody().getExpiration().before(new Date())) {
return false;
}
// 详细验证
try {
Jwts.parser().setSigningKey(secretKey).parseClaimsJws(token);
return true;
} catch (JwtException e) {
return false;
}
}
6.2 缓存策略设计
@Cacheable(value = "userDetails", key = "#username")
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
User user = userRepository.findByUsername(username)
.orElseThrow(() -> new UsernameNotFoundException("User not found"));
return new CustomUserDetails(
user.getUsername(),
user.getPassword(),
getAuthorities(user.getRoles())
);
}
@CacheEvict(value = "userDetails", key = "#user.username")
public void updateUser(User user) {
userRepository.save(user);
}
七、安全防护措施
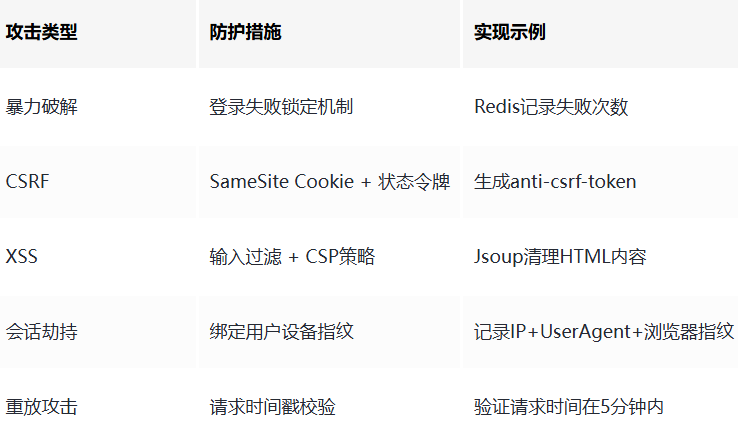
7.1 常见攻击防护
7.2 安全头配置
@Configuration
public class SecurityHeaderConfig implements WebMvcConfigurer {
@Override
public void addCorsMappings(CorsRegistry registry) {
registry.addMapping("/**")
.allowedOrigins("https://yourdomain.com")
.allowedMethods("GET", "POST")
.allowCredentials(true);
}
@Bean
public FilterRegistrationBean<HeaderFilter> securityHeadersFilter() {
FilterRegistrationBean<HeaderFilter> registration = new FilterRegistrationBean<>();
registration.setFilter(new HeaderFilter());
registration.addUrlPatterns("/*");
return registration;
}
private static class HeaderFilter extends OncePerRequestFilter {
@Override
protected void doFilterInternal(HttpServletRequest request, HttpServletResponse response,
FilterChain filterChain) throws ServletException, IOException {
response.setHeader("X-Content-Type-Options", "nosniff");
response.setHeader("X-Frame-Options", "DENY");
response.setHeader("X-XSS-Protection", "1; mode=block");
response.setHeader("Content-Security-Policy", "default-src 'self'");
filterChain.doFilter(request, response);
}
}
}
八、监控与日志
8.1 登录审计日志
@Aspect
@Component
public class LoginAuditAspect {
@Autowired
private AuditLogService auditLogService;
@AfterReturning(pointcut = "execution(* AuthController.login(..))", returning = "result")
public void logSuccessLogin(JoinPoint joinPoint, Object result) {
Object[] args = joinPoint.getArgs();
String username = (String) args[0];
auditLogService.log(username, "LOGIN_SUCCESS", "User logged in successfully");
}
@AfterThrowing(pointcut = "execution(* AuthController.login(..))", throwing = "ex")
public void logFailedLogin(JoinPoint joinPoint, Exception ex) {
Object[] args = joinPoint.getArgs();
String username = (String) args[0];
auditLogService.log(username, "LOGIN_FAILED", ex.getMessage());
}
}
8.2 监控指标
@Configuration
public class SecurityMetricsConfig {
@Bean
public MeterRegistryCustomizer<MeterRegistry> metricsCommonTags() {
return registry -> registry.config().commonTags(
"application", "auth-service",
"region", System.getenv("REGION")
);
}
@Bean
public TimedAspect timedAspect(MeterRegistry registry) {
return new TimedAspect(registry);
}
@Bean
public Counter loginAttemptCounter(MeterRegistry registry) {
return Counter.builder("auth.login.attempts")
.description("Total login attempts")
.register(registry);
}
}
九、总结与选型建议
9.1 技术选型矩阵
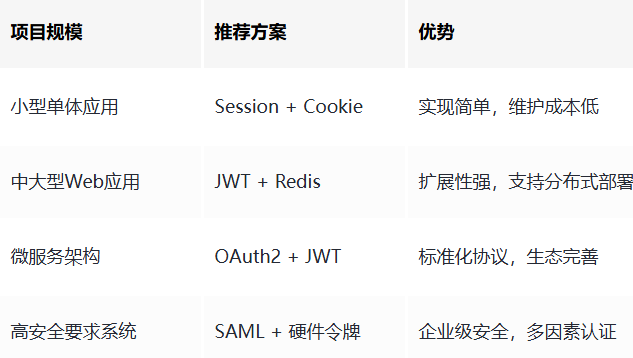
9.2 性能优化checklist
-
启用JWT压缩(特别是包含大量claims时)
-
使用非对称加密算法(RS256)替代HS256
-
实现令牌黑名单的自动过期清理
-
配置合理的会话超时时间
-
启用HTTP/2提升传输效率
-
使用CDN加速静态资源访问
通过本文的详细实现方案,大家可以构建出更加安全可靠、高性能的登录认证系统。建议根据实际业务需求选择合适的会话管理方案,并持续监控系统安全指标。
-
JWT令牌生成指南
-
Redis在会话管理中的作用
-
Spring Security过滤器配置
-
Web应用常见攻击防御策略
-
基于OAuth2的微服务认证
作者:凯哥Java
日期:2025年07月17日
标签:登录验证流程、令牌管理与安全、会话跟踪技术、过滤器与拦截器、安全防护措施