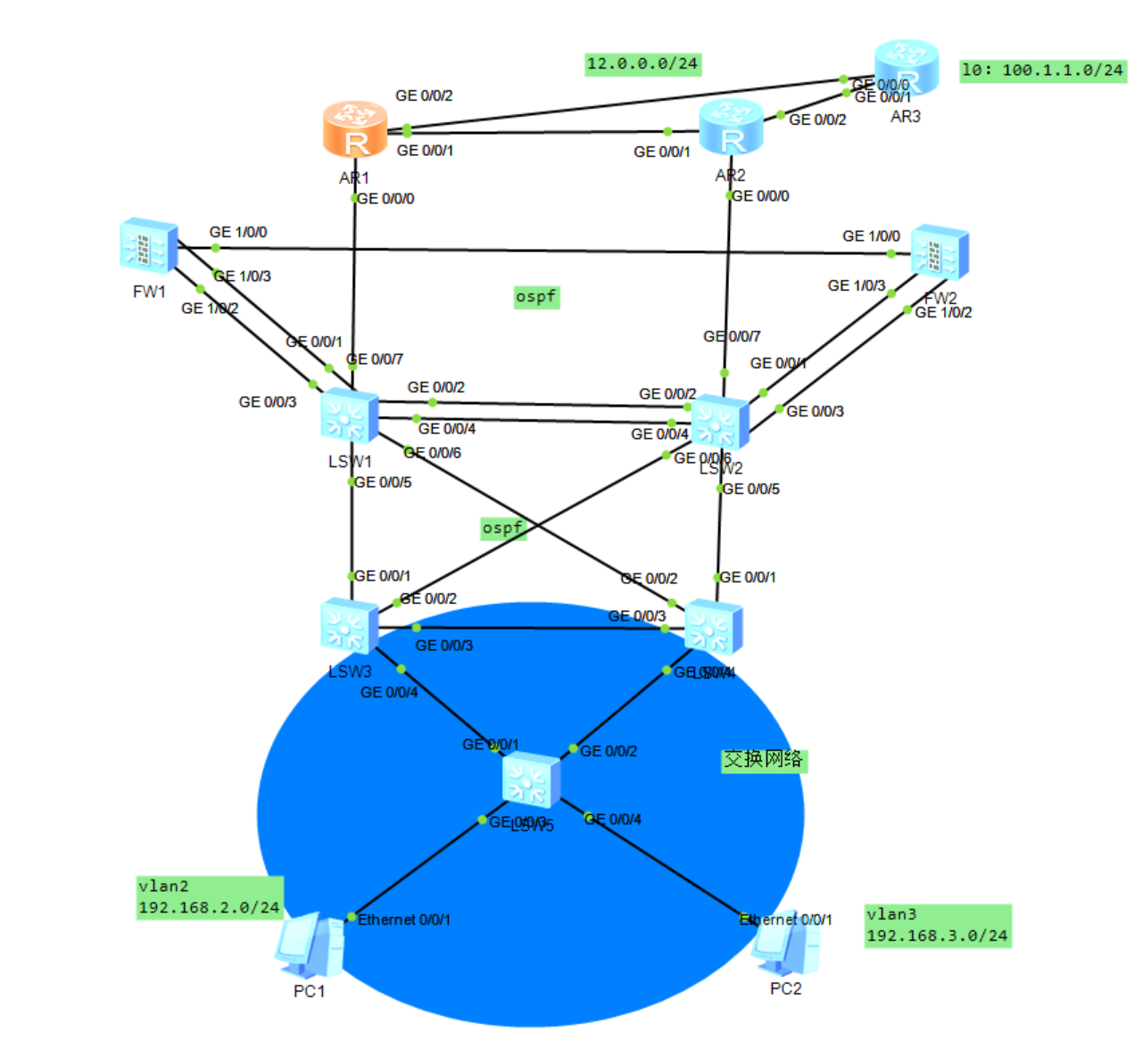
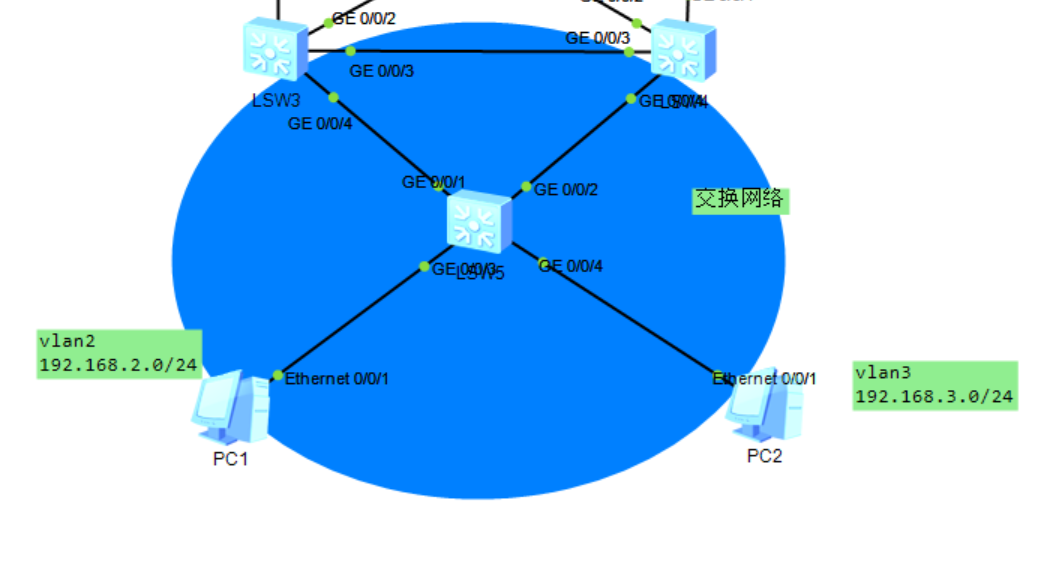
MSTP+VRRP架构
sw3为vlan2主网关,vlan3的备网关
SW4为VLAN 3主网关,VLAN 2的备网关
运行MSTP
实例1 ------ VLAN 2
实例2 ------ VLAN 3
bash
[SW3]vlan batch 2 3
[SW3-GigabitEthernet0/0/3]port link-type trunk
[SW3-GigabitEthernet0/0/3]port trunk allow-pass vlan 2 3
[SW3-GigabitEthernet0/0/4]port link-type trunk
[SW3-GigabitEthernet0/0/4]port trunk allow-pass vlan 2 3
#生成树
[SW3]stp region-configuration
[SW3-mst-region]region-name aa
#实例1有vlan2
[SW3-mst-region]instance 1 vlan 2
[SW3-mst-region]instance 2 vlan 3
#激活实例
[SW3-mst-region]active region-configuration
#让SW3做实例1的主根,实例2的备份跟
[SW3]stp instance 1 root primary
[SW3]stp instance 2 root secondary
#vrrp
[SW3]interface Vlanif 2
[SW3-Vlanif2]ip address 192.168.2.1 24
[SW3-Vlanif2]vrrp vrid 1 virtual-ip 192.168.2.254
[SW3-Vlanif2]vrrp vrid 1 priority 120
[SW3-Vlanif2]vrrp vrid 1 preempt-mode timer delay 20
#主备切换监控
[SW3-Vlanif2]vrrp vrid 1 track interface GigabitEthernet 0/0/1 reduced 15
[SW3-Vlanif2]vrrp vrid 1 track interface GigabitEthernet 0/0/2 reduced 15
[SW3]interface Vlanif 3
[SW3-Vlanif3]ip address 192.168.3.1 24
[SW3-Vlanif3]vrrp vrid 1 virtual-ip 192.168.3.254SW4与SW3的差异
bash
[SW4]stp instance 1 root secondary
[SW4]stp instance 2 root primary
[SW4-Vlanif2]ip address 192.168.2.2 24
[SW4-Vlanif2]vrrp vrid 1 virtual-ip 192.168.2.254
[SW4-Vlanif3]ip address 192.168.3.2 24
[SW4-Vlanif3]vrrp vrid 1 virtual-ip 192.168.3.254
[SW4-Vlanif3]vrrp vrid 1 priority 120
[SW4-Vlanif3]vrrp vrid 1 preempt-mode timer delay 20
[SW4-Vlanif3]vrrp vrid 1 track interface GigabitEthernet 0/0/1 reduced 15
[SW4-Vlanif3]vrrp vrid 1 track interface GigabitEthernet 0/0/2 reduced 15SW5
bash
[SW5]vlan batch 2 3
[SW5]interface GigabitEthernet 0/0/3
[SW5-GigabitEthernet0/0/3]port link-type access
[SW5-GigabitEthernet0/0/3]port link-type access
[SW5-GigabitEthernet0/0/3]port default vlan 2
[SW5-GigabitEthernet0/0/1]port link-type trunk
[SW5-GigabitEthernet0/0/1]port trunk allow-pass vlan 2 3
[SW5]stp region-configuration
[SW5-mst-region]region-name aa
[SW5-mst-region]instance 1 vlan 2
[SW5-mst-region]instance 2 vlan 3
[SW5-mst-region]active region-configuration
#查看生成树角色
[SW3]display stp brief汇聚层到核心路由配置
SW1-SW2:VLAN 102 --- 10.10.2.0/24
SW1-SW3:VLAN 103 --- 10.10.3.0/24
SW1-SW4:VLAN 104 --- 10.10.4.0/24
SW2-SW3:VLAN 203 --- 10.20.3.0/24
SW2-SW4:VLAN 204 --- 10.20.4.0/24
bash
#SW3
[SW3]vlan batch 103 203
[SW3-GigabitEthernet0/0/1]port link-type access
[SW3-GigabitEthernet0/0/1]port default vlan 103
[SW3-GigabitEthernet0/0/1]undo stp enable
[SW3-GigabitEthernet0/0/2]port link-type access
[SW3-GigabitEthernet0/0/2]port default vlan 203
[SW3-GigabitEthernet0/0/2]undo stp enable
[SW3-Vlanif103]ip address 10.10.3.3 24
[SW3-Vlanif203]ip address 10.20.3.3 24
[SW3]ospf 1 router-id 3.3.3.3
[SW3-ospf-1]a 0
[SW3-ospf-1-area-0.0.0.0]network 10.10.3.3 0.0.0.0
[SW3-ospf-1-area-0.0.0.0]network 10.20.3.3 0.0.0.0
#SW4
[SW4]vlan batch 104 204
[SW4-GigabitEthernet0/0/1]port link-type access
[SW4-GigabitEthernet0/0/1]port default vlan 204
[SW4-GigabitEthernet0/0/1]undo stp enable
[SW4-GigabitEthernet0/0/2]port link-type access
[SW4-GigabitEthernet0/0/2]undo stp enable
[SW4-GigabitEthernet0/0/2]port link-type access
[SW4-GigabitEthernet0/0/2]port default vlan 104
[SW4-GigabitEthernet0/0/2]undo stp enable
[SW4-Vlanif104]ip address 10.10.4.4 24
[SW4-Vlanif204]ip address 10.20.4.4 24
[SW4]ospf 1 router-id 4.4.4.4
[SW4-ospf-1]area 0
[SW4-ospf-1-area-0.0.0.0]network 10.10.4.4 0.0.0.0
[SW4-ospf-1-area-0.0.0.0]network 10.20.4.4 0.0.0.0 因为SW1和SW2需要被分割为两台设备,分别与上下行链路设备连接,故需要先创建VRF空间
其中GE0/0/3---GE0/0/6接口属于该VRF空间
VRF空间配置
名称:VRF
RD:100:1
RT:100:1
bash
[SW1]ip vpn-instance VRF
[SW1-vpn-instance-VRF]route-distinguisher 100:1
[SW1-vpn-instance-VRF]route-distinguisher 100:1
#SW2同样此配置
[SW1]vlan batch 102 103 104
[SW1-GigabitEthernet0/0/5]port link-type access
[SW1-GigabitEthernet0/0/5]port default vlan 103
[SW1-GigabitEthernet0/0/5]undo stp enable
[SW1-GigabitEthernet0/0/6]port link-type access
[SW1-GigabitEthernet0/0/6]port default vlan 104
[SW1-GigabitEthernet0/0/6]undo stp enable
[SW1-GigabitEthernet0/0/4]port link-type trunk
[SW1-GigabitEthernet0/0/4]port trunk allow-pass vlan 102
[SW1-GigabitEthernet0/0/4]undo port trunk allow-pass vlan 1
[SW1-GigabitEthernet0/0/4]undo stp enable
[SW2]vlan batch 102 203 204
[SW2-GigabitEthernet0/0/5]port link-type access
[SW2-GigabitEthernet0/0/5]port default vlan 204
[SW2-GigabitEthernet0/0/5]undo stp enable
[SW2-GigabitEthernet0/0/6]port link-type access
[SW2-GigabitEthernet0/0/6]port default vlan 203
[SW2-GigabitEthernet0/0/6]undo stp enable
#删去access配置
SW2-GigabitEthernet0/0/4]undo port default vlan
[SW2-GigabitEthernet0/0/4]port trunk allow-pass vlan
[SW2-GigabitEthernet0/0/4]port trunk allow-pass vlan 102
[SW2-GigabitEthernet0/0/4]undo port trunk allow-pass vlan 1
#将该接口绑定到名称为VRF的vpn空间
[SW1-Vlanif102]ip binding vpn-instance VRF
[SW1-Vlanif102]ip address 10.10.2.1 24
[SW1-Vlanif103]ip binding vpn-instance VRF
[SW1-Vlanif103]ip address 10.10.3.1 24
[SW1-Vlanif104]ip binding vpn-instance VRF
[SW1-Vlanif104]ip address 10.10.4.1 24
[SW2-Vlanif102]ip binding vpn-instance VRF
[SW2-Vlanif102]ip address 10.10.2.2 24
[SW2-Vlanif203]ip binding vpn-instance VRF
[SW2-Vlanif203]ip address 10.20.3.2 24
[SW2-Vlanif204]ip binding vpn-instance VRF
[SW2-Vlanif204]ip address 10.20.4.2 24
#将ospf1与VRF空间绑定
[SW1]ospf 1 router-id 1.1.1.1 vpn-instance VRF
[SW1-ospf-1]area 0
[SW1-ospf-1-area-0.0.0.0]network 10.10.2.1 0.0.0.0
[SW1-ospf-1-area-0.0.0.0]network 10.10.3.1 0.0.0.0
[SW1-ospf-1-area-0.0.0.0]network 10.10.4.1 0.0.0.0
#sw2也宣告
[SW3-Vlanif203]ospf cost 5 #sw4同理SW1:
去往192.168.2.0/24,发送给SW3,备份为SW4
去往192.168.3.0/24,发送给SW4,备份为SW3
bash
[SW3]ip ip-prefix aa permit 192.168.3.0 24
[SW3]ip ip-prefix bb permit 192.168.2.0 24
[SW3]route-policy aa permit node 10
[SW3-route-policy]if-match ip-prefix aa
[SW3-route-policy]apply cost 5
[sw3]route-policy aa permit node 20
[sw3-route-policy]if-match ip-prefix bb
[sw3-ospf-1]import-route direct route-policy aaVRF交换机与防火墙
bash
[SW1]vlan batch 401 402
[SW1-GigabitEthernet0/0/3]port link-type trunk
[SW1-GigabitEthernet0/0/3]port trunk allow-pass vlan 401 402
[SW1-GigabitEthernet0/0/4]port link-type trunk
[SW1-GigabitEthernet0/0/4]port trunk allow-pass vlan 401 402
[SW1-Vlanif401]ip binding vpn-instance VRF
[SW1-Vlanif401]ip address 10.40.1.1 24
[SW1-Vlanif401]vrrp vrid 1 virtual-ip 10.40.1.100
[SW1-Vlanif401]vrrp vrid 1 priority 120
[SW1-Vlanif401]vrrp vrid 1 preempt-mode timer delay 60
[SW1-Vlanif401]vrrp vrid 1 track interface GigabitEthernet 0/0/3 reduced 30
[SW1-Vlanif402]ip binding vpn-instance VRF
[SW1-Vlanif402]ip address 10.40.2.1 24
[SW1-Vlanif402]vrrp vrid 2 virtual-ip 10.40.2.100
#SW2同理